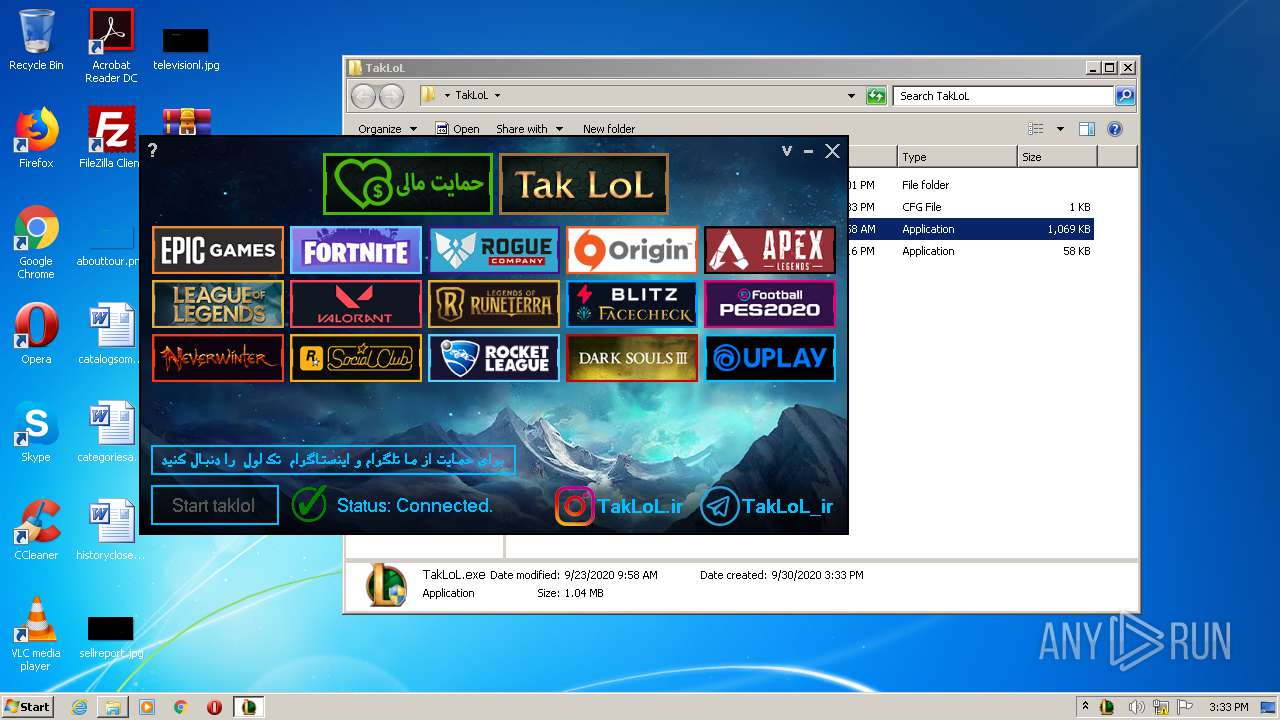
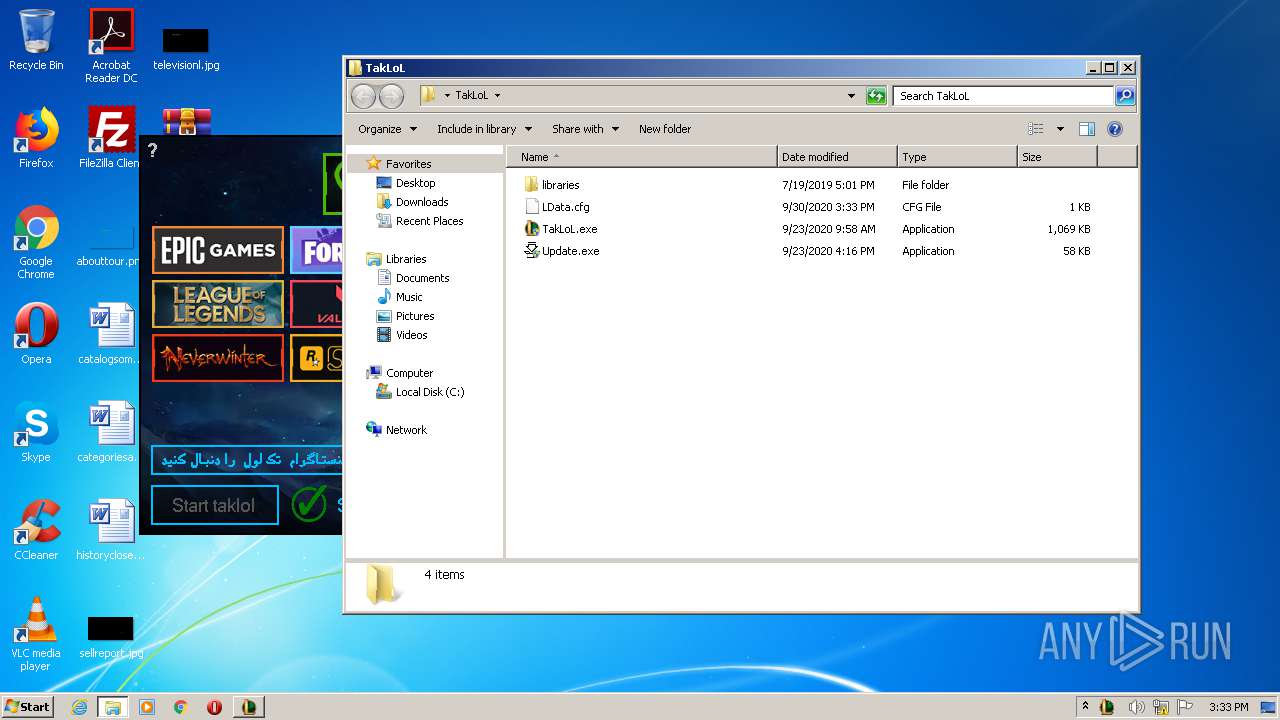
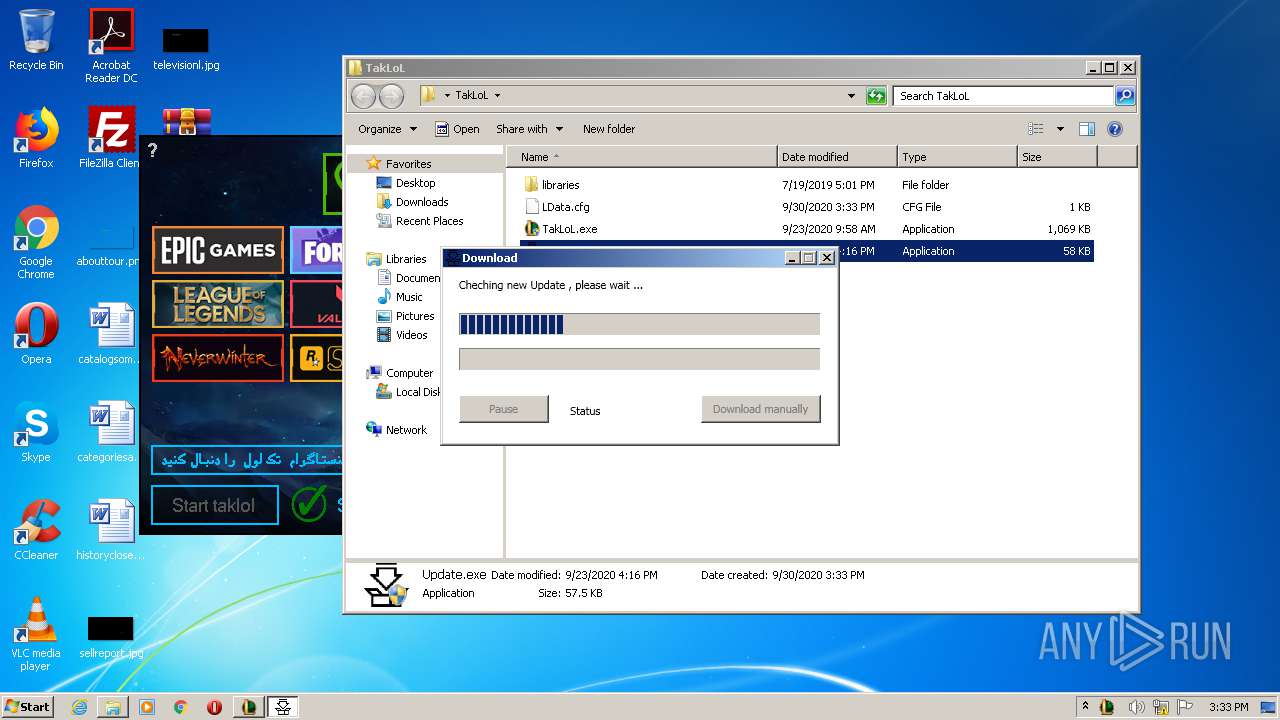
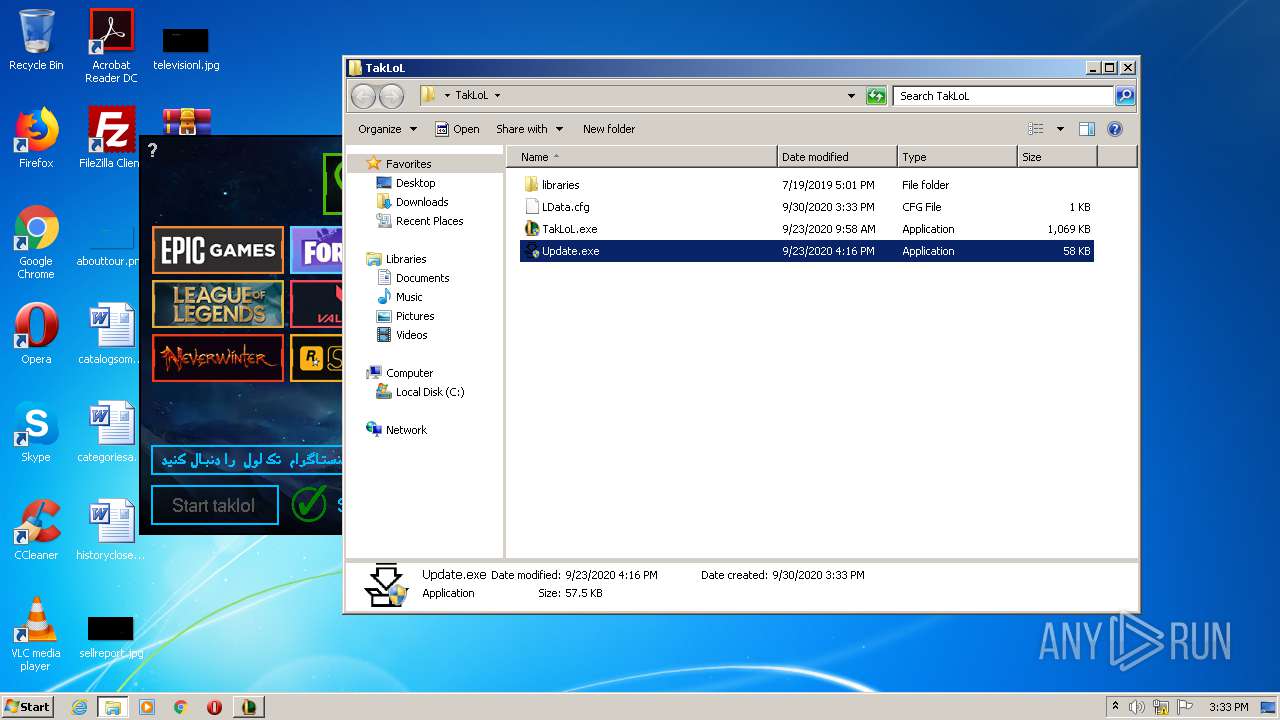
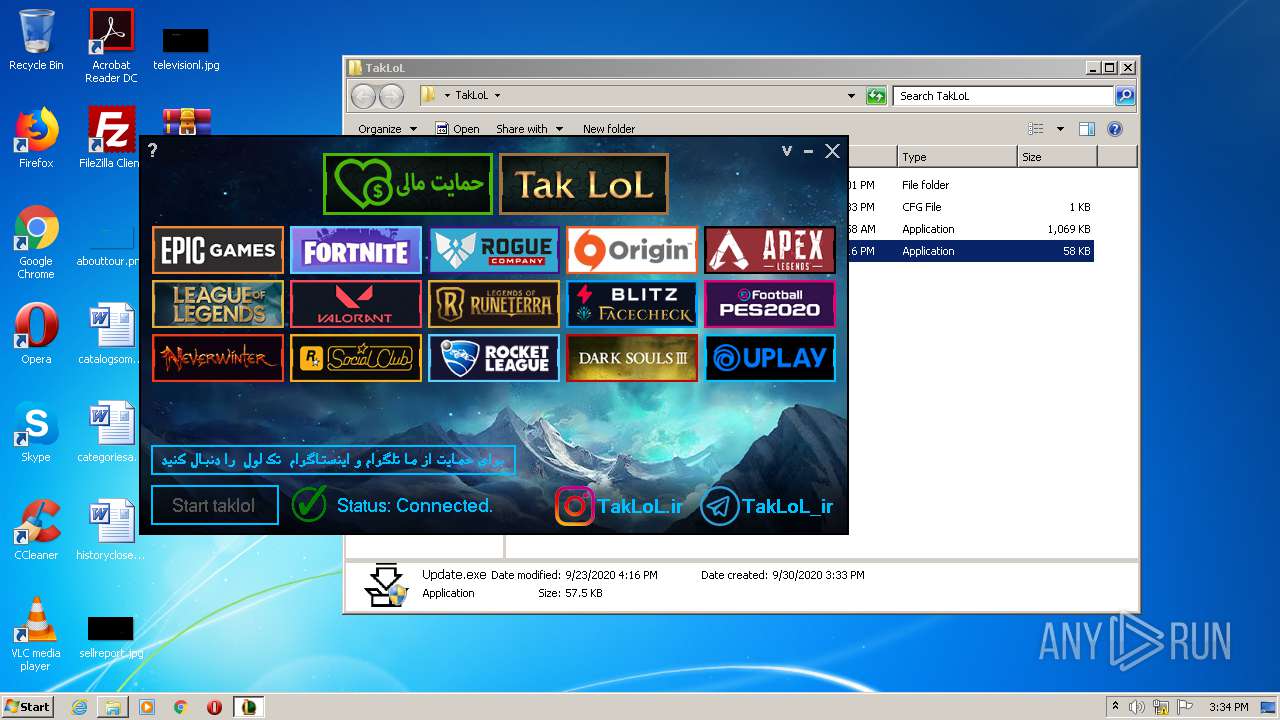
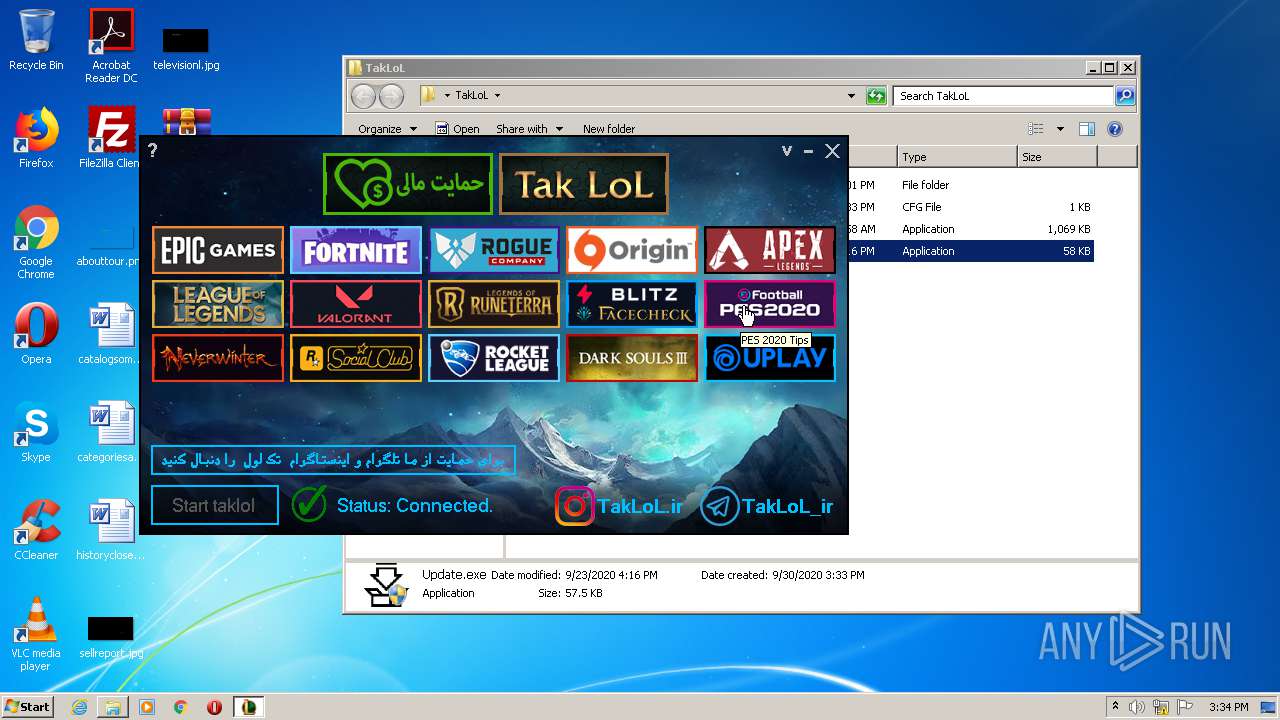
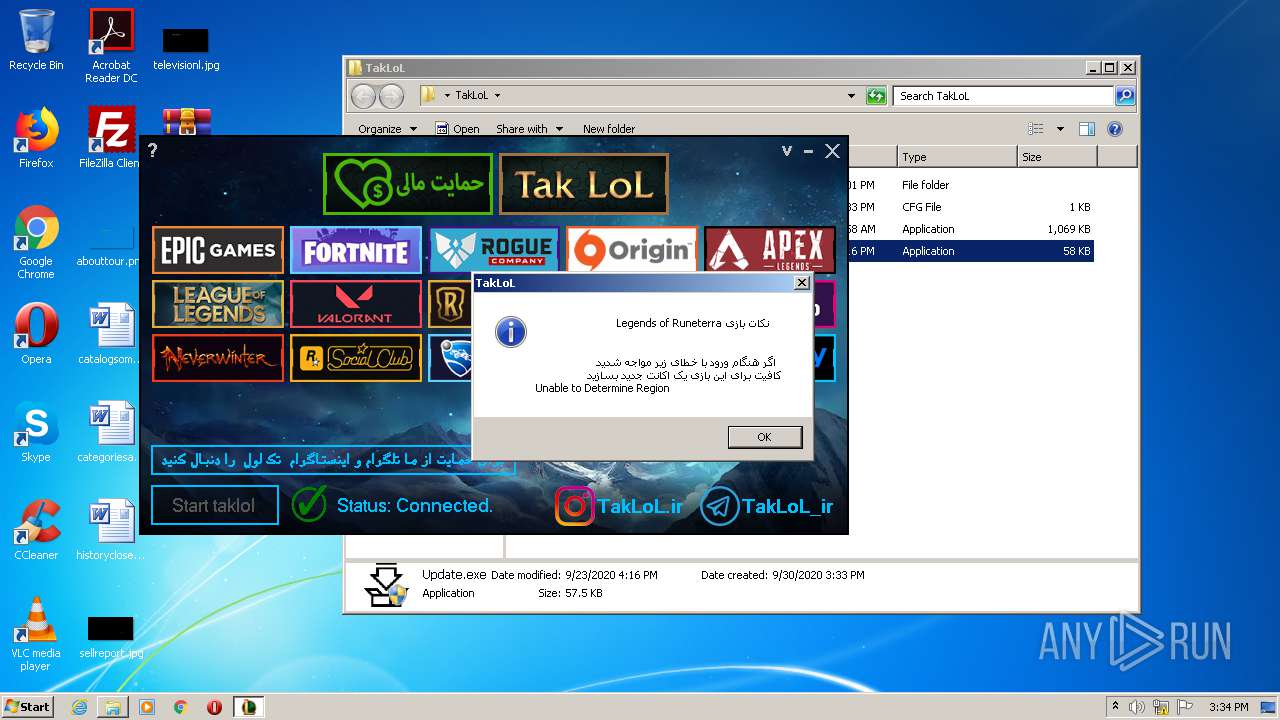
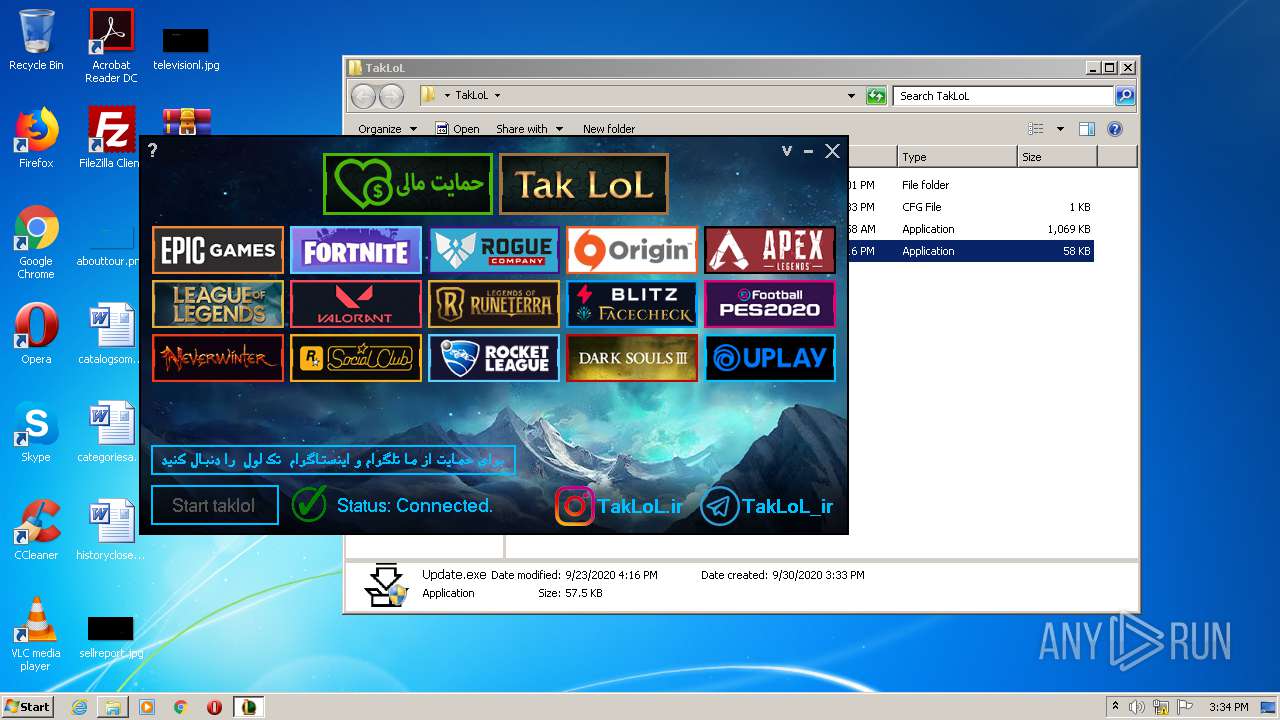
| File name: | taklol.zip |
| Full analysis: | https://app.any.run/tasks/25bf33d4-7bf2-40f5-9bfa-69ebe4b75194 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 14:32:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 73A47DDC9A9EB18A72E4B81B3A05BCE2 |
| SHA1: | 3860060CEC8974948C91BBFC73F41F477D9230A4 |
| SHA256: | EEAB2E0C590B21C7A4579B7D01E2F2543DB3F3D8B78D648F3C6380857EBF3963 |
| SSDEEP: | 98304:fy/yUb7vFeU0auScyLKZvf89PzkWt61/sq35A9+V:fy/yUb7vFeU0aufOKxfiPMsSom |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3844)
- pfier.exe (PID: 2808)
- explorer.exe (PID: 328)
- ctfmon.exe (PID: 612)
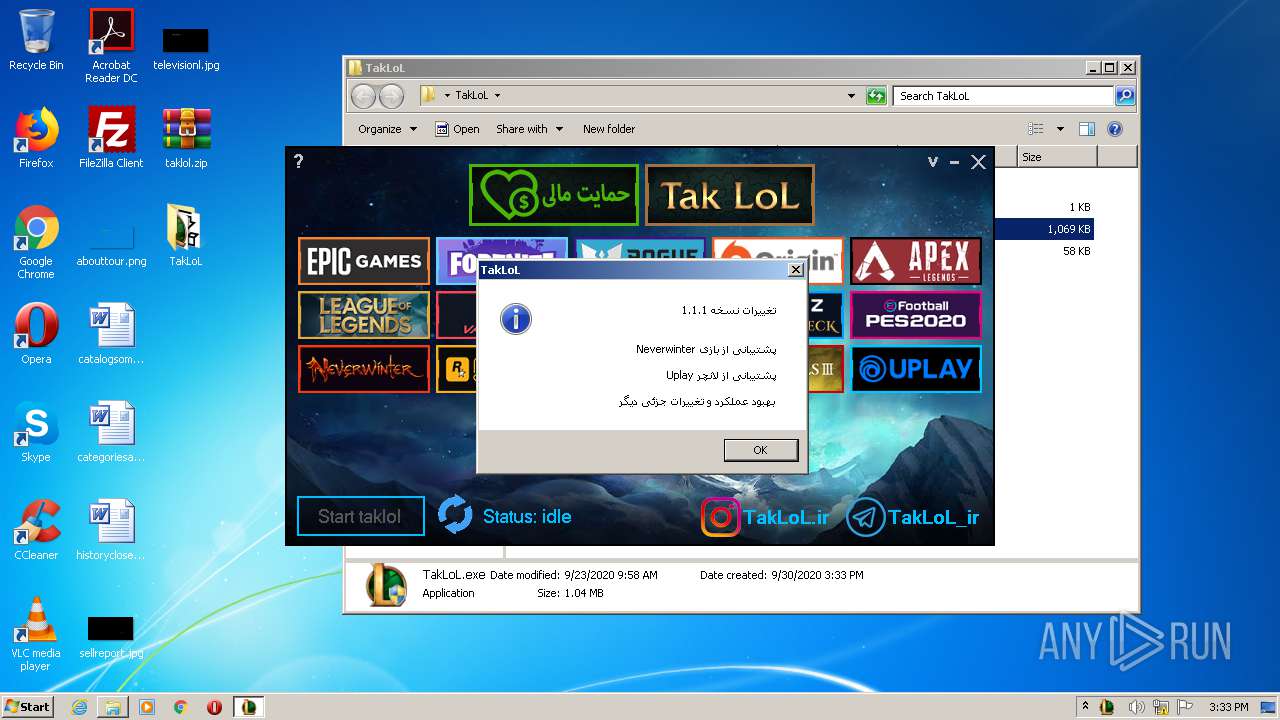
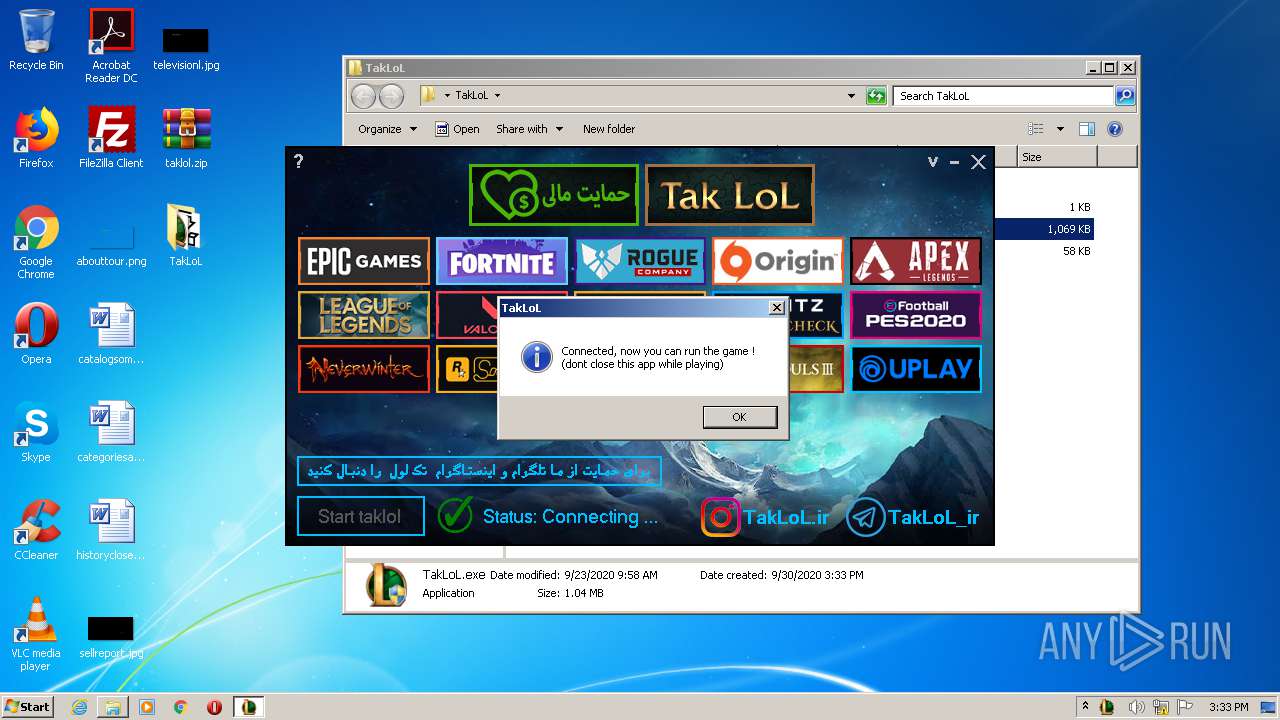
- TakLoL.exe (PID: 1720)
- Update.exe (PID: 2844)
Application was dropped or rewritten from another process
- TakLoL.exe (PID: 1720)
- pfier.exe (PID: 2808)
- Update.exe (PID: 2816)
- TakLoL.exe (PID: 3336)
- Update.exe (PID: 2844)
Writes to the hosts file
- TakLoL.exe (PID: 1720)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2852)
Creates files in the user directory
- explorer.exe (PID: 328)
Reads Environment values
- Update.exe (PID: 2844)
INFO
Manual execution by user
- WinRAR.exe (PID: 2852)
- TakLoL.exe (PID: 3336)
- TakLoL.exe (PID: 1720)
Reads the hosts file
- TakLoL.exe (PID: 1720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:09:23 18:50:27 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | TakLoL/ |
Total processes
48
Monitored processes
10
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 612 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1720 | "C:\Users\admin\Desktop\TakLoL\TakLoL.exe" | C:\Users\admin\Desktop\TakLoL\TakLoL.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: TakLoL Apps Exit code: 0 Version: 1.1.1.0 Modules
| |||||||||||||||
| 2752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\taklol.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2808 | "C:\Users\admin\Desktop\TakLoL\libraries\pfier\pfier.exe" | C:\Users\admin\Desktop\TakLoL\libraries\pfier\pfier.exe | — | TakLoL.exe | |||||||||||
User: admin Company: Initex Integrity Level: HIGH Description: Proxifier Portable Edition v3.42 Exit code: 0 Version: 3.42.0.1 Modules
| |||||||||||||||
| 2816 | "C:\Users\admin\Desktop\TakLoL\Update.exe" | C:\Users\admin\Desktop\TakLoL\Update.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TakLoL Updater Exit code: 3221226540 Version: 1.0.4.0 Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\Desktop\TakLoL\Update.exe" | C:\Users\admin\Desktop\TakLoL\Update.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: TakLoL Updater Exit code: 0 Version: 1.0.4.0 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\taklol.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\Desktop\TakLoL\TakLoL.exe" | C:\Users\admin\Desktop\TakLoL\TakLoL.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TakLoL Apps Exit code: 3221226540 Version: 1.1.1.0 Modules
| |||||||||||||||
| 3844 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 407
Read events
5 232
Write events
175
Delete events
0
Modification events
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {B41DB860-8EE4-11D2-9906-E49FADC173CA} {00000122-0000-0000-C000-000000000046} 0xFFFF |
Value: 010000000000000042FE6F953697D601 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs |
| Operation: | write | Name: | 9 |
Value: 740061006B006C006F006C002E007A00690070000000680032000000000000000000000074616B6C6F6C2E7A69702E6C6E6B00004A0008000400EFBE00000000000000002A00000000000000000000000000000000000000000000000000740061006B006C006F006C002E007A00690070002E006C006E006B0000001E000000 | |||
| (PID) Process: | (328) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.zip |
| Operation: | write | Name: | 0 |
Value: 740061006B006C006F006C002E007A00690070000000680032000000000000000000000074616B6C6F6C2E7A69702E6C6E6B00004A0008000400EFBE00000000000000002A00000000000000000000000000000000000000000000000000740061006B006C006F006C002E007A00690070002E006C006E006B0000001E000000 | |||
Executable files
6
Suspicious files
0
Text files
73
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 328 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 328 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\taklol.zip.lnk | lnk | |
MD5:— | SHA256:— | |||
| 328 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\Settings.ini | text | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\Helper64.exe | executable | |
MD5:F31A68F82B76E14E097BD2EE6161A36D | SHA256:AD0C6EE03AE8F82B2512DA839BB89C1D2A28416189B71262D8ED2B3218DB7F5D | |||
| 2808 | pfier.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\Profiles\Default.ppx | xml | |
MD5:— | SHA256:— | |||
| 2852 | WinRAR.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\PrxDrvPE.dll | executable | |
MD5:D3DA1003323423DA89AF2C83E5E2B40A | SHA256:44243F0D0102D654C5CAD1AC3826B52DA9454D4AF99D9A417CEB6AE4DDDA71F0 | |||
| 1720 | TakLoL.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\Settings.ini | text | |
MD5:— | SHA256:— | |||
| 2808 | pfier.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\Settings.ini | text | |
MD5:— | SHA256:— | |||
| 1720 | TakLoL.exe | C:\Users\admin\Desktop\TakLoL\libraries\pfier\Profiles\Default.ppx | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1720 | TakLoL.exe | POST | 200 | 104.24.113.121:80 | http://taklol.ir/update/getlast5 | US | text | 3.68 Kb | suspicious |
1720 | TakLoL.exe | POST | 200 | 104.24.112.121:80 | http://taklol.taklol.ir/update/getlast5 | US | text | 3.68 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1720 | TakLoL.exe | 104.24.113.121:80 | taklol.ir | Cloudflare Inc | US | shared |
1720 | TakLoL.exe | 104.24.112.121:80 | taklol.ir | Cloudflare Inc | US | shared |
2844 | Update.exe | 172.67.146.87:80 | taklol.ir | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
taklol.ir |
| suspicious |
taklol.taklol.ir |
| suspicious |
www.google.com |
| malicious |