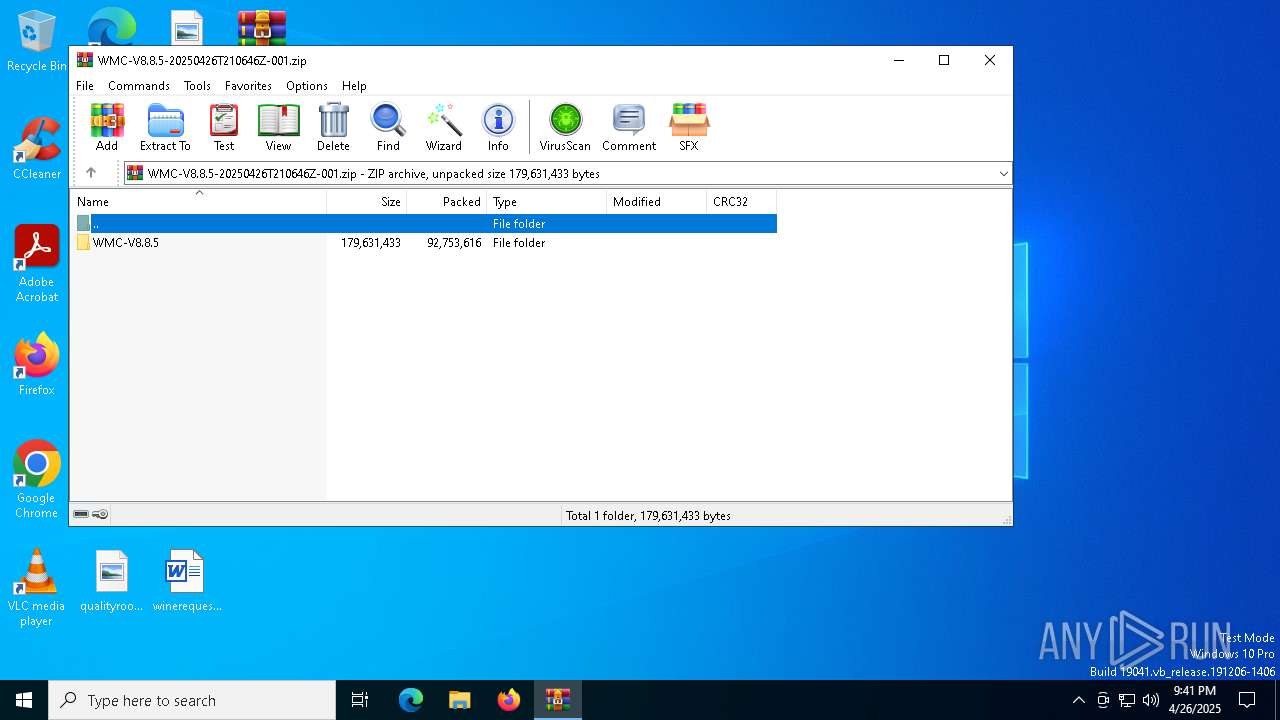
| File name: | WMC-V8.8.5-20250426T210646Z-001.zip |
| Full analysis: | https://app.any.run/tasks/e533f7b7-c0ce-49cc-a714-3894d42c32c2 |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2025, 21:41:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E4CFB4A1BA9F3A9E330F7E112F2C679D |
| SHA1: | C5A0D2DCDB49CE4F46DE9ADAF126626C7B844266 |
| SHA256: | EE9DA2F27F2DA6D11641F520FC8AB5F6C7562565297C7B95C1368E3399E86AE7 |
| SSDEEP: | 1572864:5vAhXMKez+7DBXAOTibZzIB4VjIrAwUAW:5vAh8Kez+nBXAOmbZxFIMwW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5064)
Reads security settings of Internet Explorer
- wmplayer.exe (PID: 6108)
SQL CE related mutex has been found
- unregmp2.exe (PID: 5244)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5344)
- wscript.exe (PID: 5868)
- wscript.exe (PID: 2420)
- wscript.exe (PID: 4932)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 6136)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 4268)
- cmd.exe (PID: 4200)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 4756)
- cmd.exe (PID: 5972)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 3132)
- cmd.exe (PID: 2904)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4200)
- cmd.exe (PID: 5972)
- cmd.exe (PID: 2244)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5868)
- wscript.exe (PID: 5344)
- wscript.exe (PID: 4932)
- wscript.exe (PID: 2420)
- cmd.exe (PID: 2244)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 6136)
The process executes VB scripts
- cmd.exe (PID: 4268)
- cmd.exe (PID: 4756)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 2984)
Executing commands from ".cmd" file
- wscript.exe (PID: 5868)
- wscript.exe (PID: 5344)
- wscript.exe (PID: 4932)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 2420)
- wscript.exe (PID: 6136)
Application launched itself
- cmd.exe (PID: 2244)
INFO
Process checks computer location settings
- wmplayer.exe (PID: 6108)
- setup_wm.exe (PID: 728)
Manual execution by a user
- wmplayer.exe (PID: 6108)
- wscript.exe (PID: 6372)
- cmd.exe (PID: 4268)
- cmd.exe (PID: 4756)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 5244)
- OpenWith.exe (PID: 3332)
- OpenWith.exe (PID: 1272)
- OpenWith.exe (PID: 1276)
The sample compiled with french language support
- WinRAR.exe (PID: 5064)
Reads the computer name
- wmplayer.exe (PID: 6108)
- setup_wm.exe (PID: 728)
Checks supported languages
- wmplayer.exe (PID: 6108)
- setup_wm.exe (PID: 728)
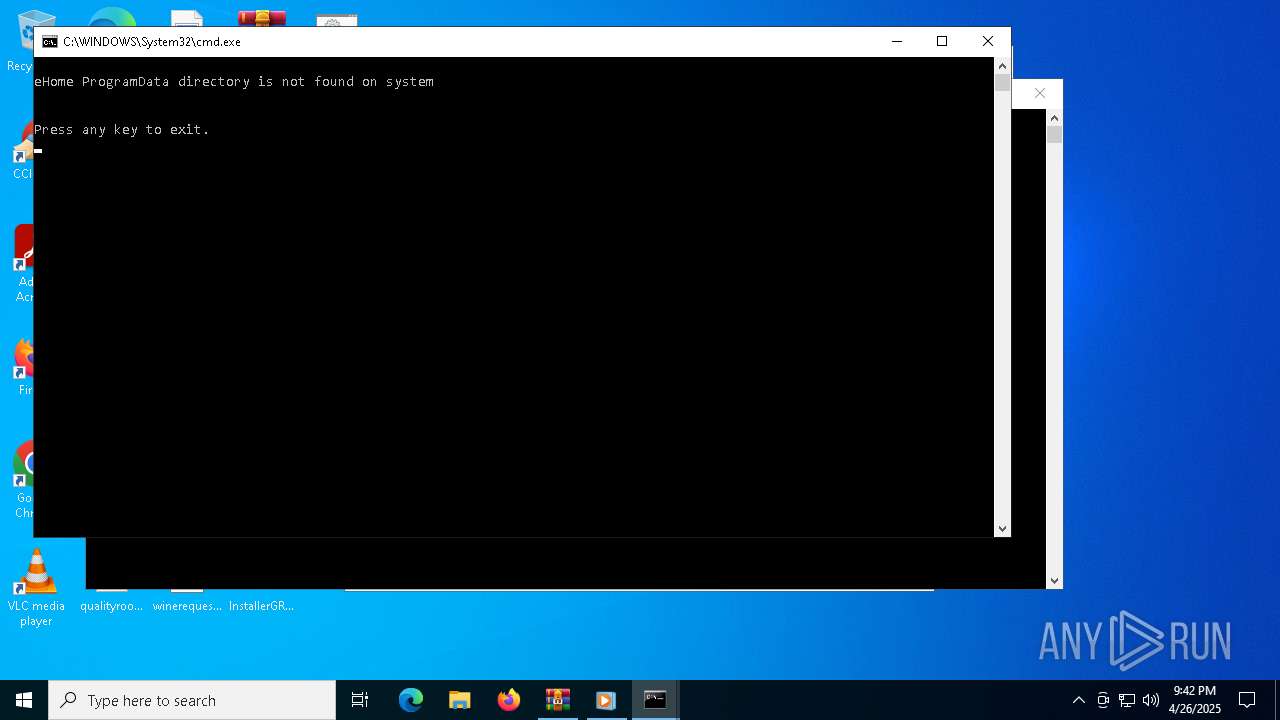
Create files in a temporary directory
- unregmp2.exe (PID: 4944)
Reads security settings of Internet Explorer
- unregmp2.exe (PID: 4944)
Creates files or folders in the user directory
- unregmp2.exe (PID: 5244)
Checks operating system version
- cmd.exe (PID: 2244)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3332)
- OpenWith.exe (PID: 1272)
- OpenWith.exe (PID: 1276)
Checks proxy server information
- slui.exe (PID: 5352)
Reads the software policy settings
- slui.exe (PID: 5352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x75003b2d |
| ZipCompressedSize: | 437 |
| ZipUncompressedSize: | 740 |
| ZipFileName: | WMC-V8.8.5/ResetSettings.cmd |
Total processes
190
Monitored processes
65
Malicious processes
1
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\System32\reg.exe add HKU\.DEFAULT\Console\%SystemRoot%_system32_cmd.exe /v ScreenBufferSize /t REG_DWORD /d 19660880 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
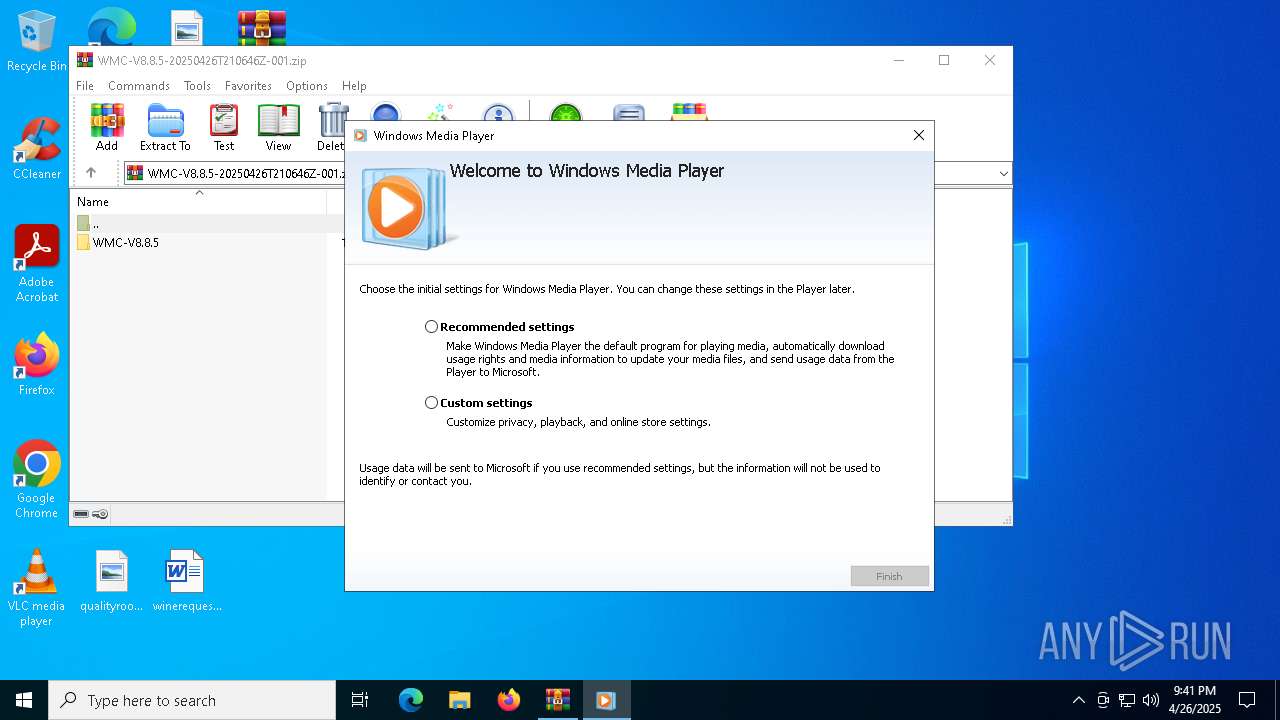
| 728 | "C:\Program Files (x86)\Windows Media Player\setup_wm.exe" /RunOnce:"C:\Program Files (x86)\Windows Media Player\wmplayer.exe" /layout:C:\Users\admin\Desktop\MCSkin.wms | C:\Program Files (x86)\Windows Media Player\setup_wm.exe | — | wmplayer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Configuration Utility Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
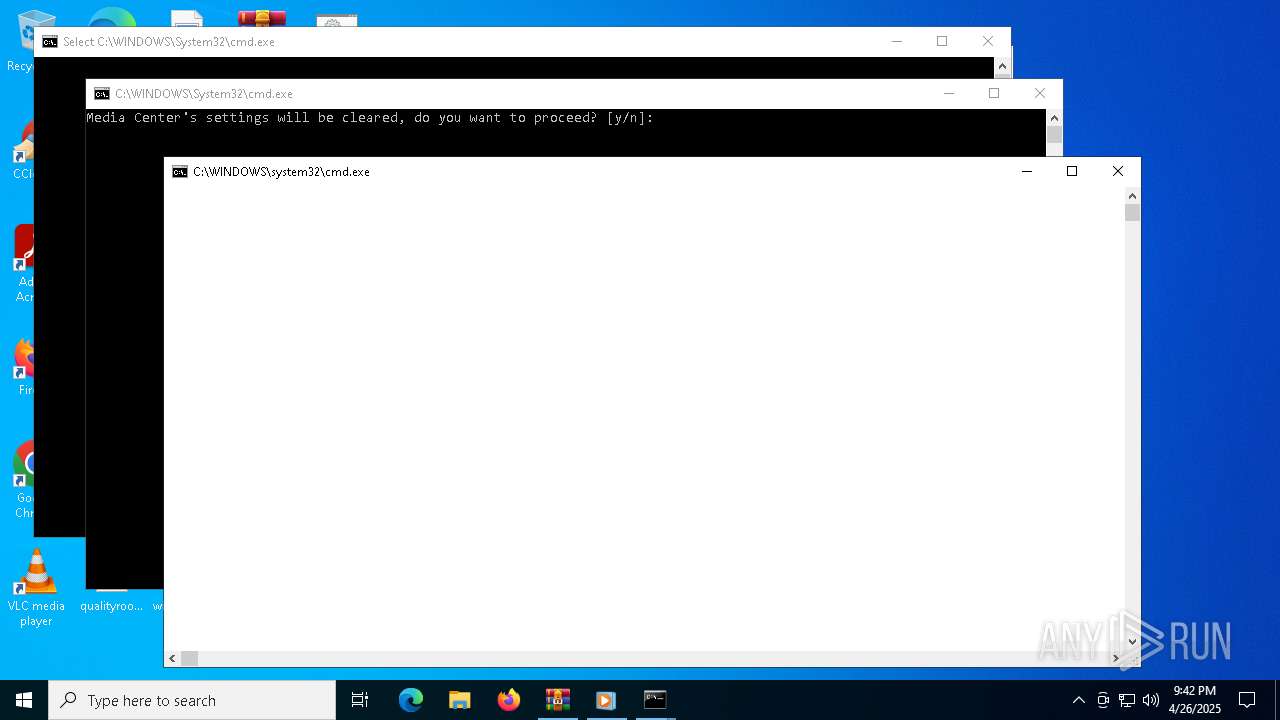
| 1132 | choice /C YN /N /M "Media Center's settings will be cleared, do you want to proceed? [y/n]: " | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\System32\reg.exe add HKU\.DEFAULT\Console\%SystemRoot%_system32_cmd.exe /v ScreenBufferSize /t REG_DWORD /d 19660880 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 006
Read events
14 896
Write events
104
Delete events
6
Modification events
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WMC-V8.8.5-20250426T210646Z-001.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6372) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: FD0C110000000000 | |||
| (PID) Process: | (728) setup_wm.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\ActiveMovie\devenum\{4EFE2452-168A-11D1-BC76-00C04FB9453B}\Default MidiOut Device |
| Operation: | write | Name: | FriendlyName |
Value: Default MidiOut Device | |||
Executable files
0
Suspicious files
2
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5244 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\CurrentDatabase_400.wmdb | binary | |
MD5:79AEACC048DB9CA31E1BAF148FFC66C6 | SHA256:9974FC100ABF3300E5EBCAB88D7BA8F66158429E8EBB155F7118AECCC062FFF7 | |||
| 5244 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 5244 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | text | |
MD5:A9B5DA9AEC61657B32393D96217165F0 | SHA256:9F4611369CF65B33D886489B2486FCA7B1E83E0DC998D35B15B3AA4C8478A28D | |||
| 5244 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML.bak | text | |
MD5:7050D5AE8ACFBE560FA11073FEF8185D | SHA256:CB87767C4A384C24E4A0F88455F59101B1AE7B4FB8DE8A5ADB4136C5F7EE545B | |||
| 4944 | unregmp2.exe | C:\Users\admin\AppData\Local\Temp\wmsetup.log | text | |
MD5:4DDA843465C61DF6199472905DEC7F55 | SHA256:6A4BB69C7537604783B1391611C7974EF9D7C8BF69FF89E401A94E63DA418666 | |||
| 5244 | unregmp2.exe | C:\Users\admin\AppData\Local\Microsoft\Media Player\LocalMLS_3.wmdb | binary | |
MD5:A05115DB8C37F459D8CE3D4E9C63AC8F | SHA256:6736105E83F6AD17A69AAA521A5BEB4B35C0BAF6EE9F705DEB24EF9F8B0625F6 | |||
| 4268 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:DC566B93004DDCA03A480CBDDB1A329F | SHA256:7F256D9562232830F8ACD58B65A311E81FC67B7BFE8726E211796D5F9CF46568 | |||
| 4756 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:DC566B93004DDCA03A480CBDDB1A329F | SHA256:7F256D9562232830F8ACD58B65A311E81FC67B7BFE8726E211796D5F9CF46568 | |||
| 5048 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:DC566B93004DDCA03A480CBDDB1A329F | SHA256:7F256D9562232830F8ACD58B65A311E81FC67B7BFE8726E211796D5F9CF46568 | |||
| 6824 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:DC566B93004DDCA03A480CBDDB1A329F | SHA256:7F256D9562232830F8ACD58B65A311E81FC67B7BFE8726E211796D5F9CF46568 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
496 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5352 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |