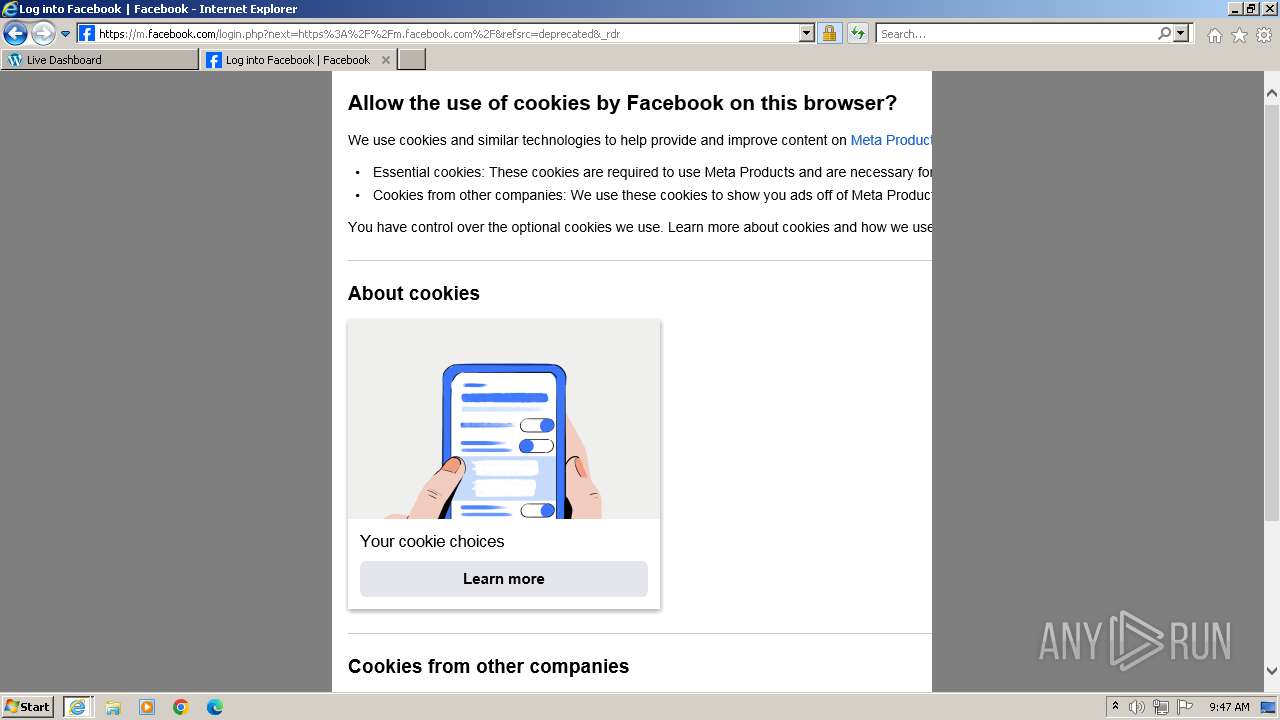
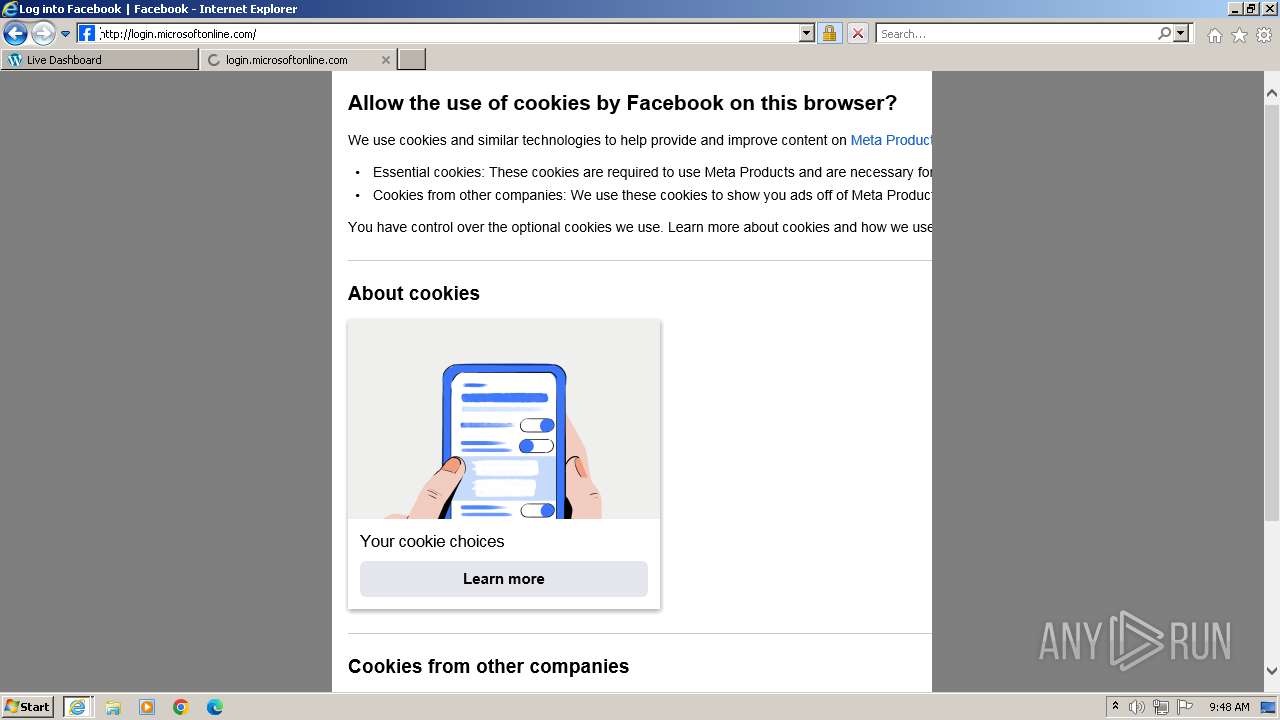
| URL: | https://rubiconcm.digitaleast.mobi |
| Full analysis: | https://app.any.run/tasks/b196396d-c71f-4164-9199-45f485f7eb0a |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2024, 08:43:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E8A9FA8B2886BA23245A37D010AEFC53 |
| SHA1: | 9EBAABE819630A51407AD1125A27E597CE196D9F |
| SHA256: | EE93927C56A593D3880FDCA6BB08187DECEEB62120A1BF605F8E58B6BE3FDC8C |
| SSDEEP: | 3:N8RJfGpECRjMn:2z2w |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3968)
Reads the computer name
- wmpnscfg.exe (PID: 1768)
Manual execution by a user
- wmpnscfg.exe (PID: 1768)
Checks supported languages
- wmpnscfg.exe (PID: 1768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3968 CREDAT:3544342 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://rubiconcm.digitaleast.mobi" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3968 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
46 238
Read events
44 769
Write events
765
Delete events
704
Modification events
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 849398928 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31108132 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31108132 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
55
Text files
122
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:38195CD46C7D42A982965EAE72D825BB | SHA256:944E2CA83DED3683849674B9FC9905AD4B531D8403A4196B8B0051CE6AA0CF80 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_C39E9DBC666D19C07EEE7CD1E11AF8BE | binary | |
MD5:A147E8BD4A72D18FB03C31C092557E8D | SHA256:CCFEFD69A2439B1D2B8D516C4B37085D391145BB64F990202A0FBFD41E3DF682 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:297E436E44E7AEE231E646750A3FF109 | SHA256:F464FD1F8E56DA81C4025674E3ABD10C75D427E43F7332AD7B8627C07B7C1A39 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:62305222640307D73E13D9C4FE9287BF | SHA256:9157259B161696FDD2227B12A0E83263FCE38AE4D1DC53598E98579BF9A8B352 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\G4Y292H9.txt | text | |
MD5:4DD11A185044B07FE9B562F769D88147 | SHA256:0685ADAF78270422FA096C785AE187CE6513EEB70AB100E548AC74195E2C8304 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\773CFF2C7835D48C4E76FE153DBA9F81_670D6BFEED73E88C5B8E11FC9F5F4787 | der | |
MD5:D90FDAF6764C7B23FF82D8DA0EC6CCC0 | SHA256:ECDE21BA00538BDD4316092B983FA196D4E98AC50927EDA022E88748D70A25FC | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\XBX56UXN.txt | text | |
MD5:97CB991A93B694C225218FCC1F5B6D68 | SHA256:B5B09ACDD52A7EDB2B2DA7D0021D985CC5D140A0CA64F760846B7E71BAF2A90E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
117
DNS requests
83
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
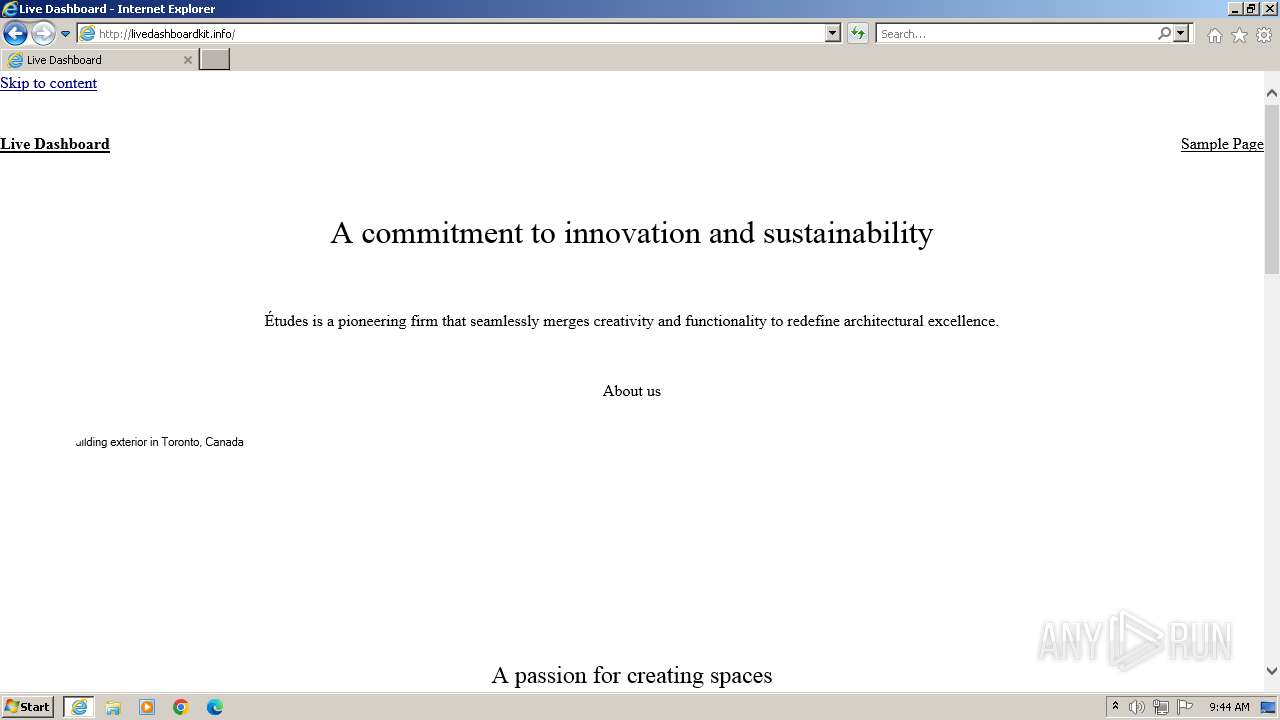
4028 | iexplore.exe | GET | — | 172.67.166.199:80 | http://livedashboardkit.info/wp-content/themes/twentytwentyfour/assets/images/tourist-and-building.webp | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 172.67.166.199:80 | http://livedashboardkit.info/wp-includes/blocks/navigation/view.min.js?ver=6.5.3 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | — | 172.67.166.199:80 | http://livedashboardkit.info/wp-content/themes/twentytwentyfour/assets/images/building-exterior.webp | unknown | — | — | unknown |
4028 | iexplore.exe | GET | — | 172.67.166.199:80 | http://livedashboardkit.info/wp-content/themes/twentytwentyfour/assets/images/windows.webp | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?068eb670bb243701 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9b5f474efa3999f3 | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJiUKgT2m88fZ4nxc1Lu6M%2FjvkagQUDNtsgkkPSmcKuBTuesRIUojrVjgCEATUIeDfYIYoOvpiK%2BEA3YU%3D | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7d495c908dca8b32 | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?375896791b56e52b | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4028 | iexplore.exe | 34.95.81.168:443 | rubiconcm.digitaleast.mobi | GOOGLE-CLOUD-PLATFORM | US | unknown |
4028 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
4028 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3968 | iexplore.exe | 2.16.27.215:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
3968 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3968 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3968 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rubiconcm.digitaleast.mobi |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.rapidssl.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
livedashboardkit.info |
| unknown |
s.ad.smaato.net |
| whitelisted |