| File name: | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch |
| Full analysis: | https://app.any.run/tasks/d4ab714f-0b23-45ad-bc10-462cd8bf26da |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | March 24, 2025, 18:12:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 8 sections |
| MD5: | 355093473251545C6EDB50AAB21A5774 |
| SHA1: | 7B43F1D12102CE80B71222594FFBD324EE75C74B |
| SHA256: | EE818D0DC6FF205EC678A47AA586DD9642C71C4D13F45772DAE5C1EFA1B59C7C |
| SSDEEP: | 98304:Ictab6NLs+o/rlNnTcVoOFt7L8Uzi4faOhgkzajJjQ7nDkHlMPz9Ijlr0/zS14W/:T4 |
MALICIOUS
Bypass User Account Control (Modify registry)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
SKULD has been detected
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Bypass User Account Control (fodhelper)
- fodhelper.exe (PID: 7084)
Adds path to the Windows Defender exclusion list
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Changes the autorun value in the registry
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
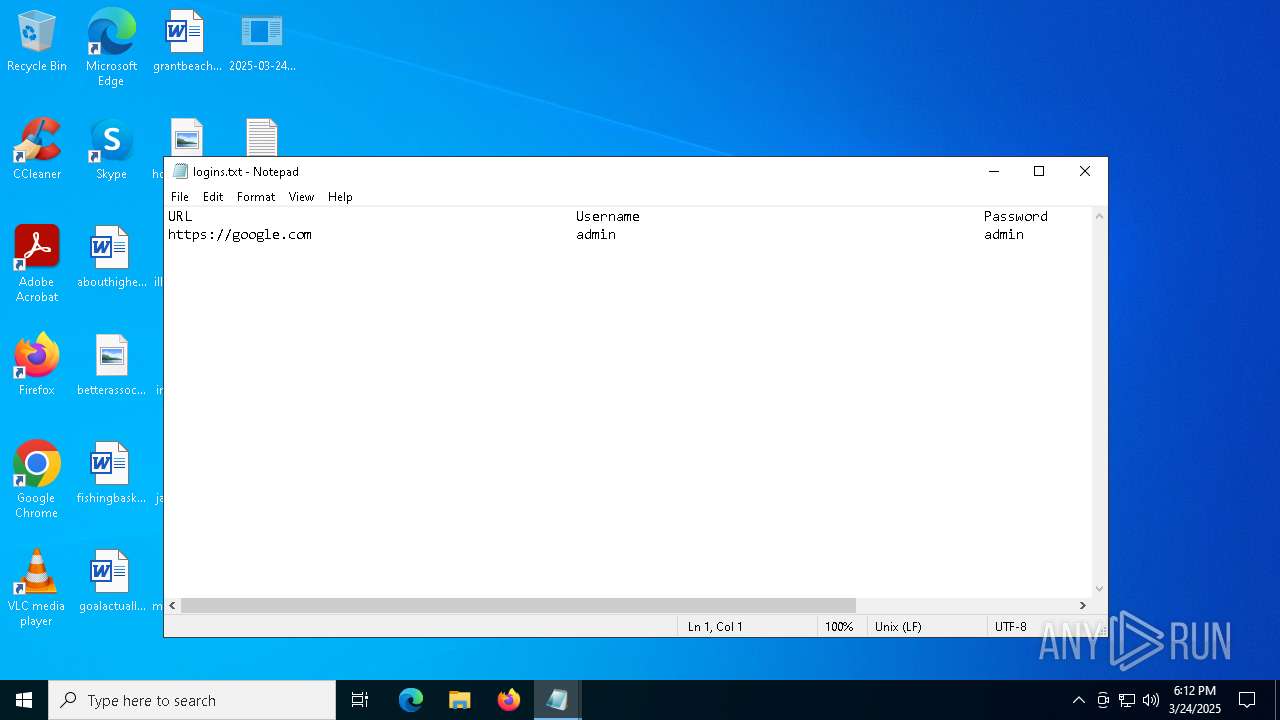
Steals credentials from Web Browsers
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Actions looks like stealing of personal data
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Changes Windows Defender settings
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Bypass execution policy to execute commands
- powershell.exe (PID: 4108)
Changes powershell execution policy (Bypass)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 6972)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 6972)
Changes Controlled Folder Access settings
- powershell.exe (PID: 6972)
Changes settings for real-time protection
- powershell.exe (PID: 6972)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 6972)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 6972)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 6972)
SKULD has been detected (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
DISCORDGRABBER has been detected (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
SUSPICIOUS
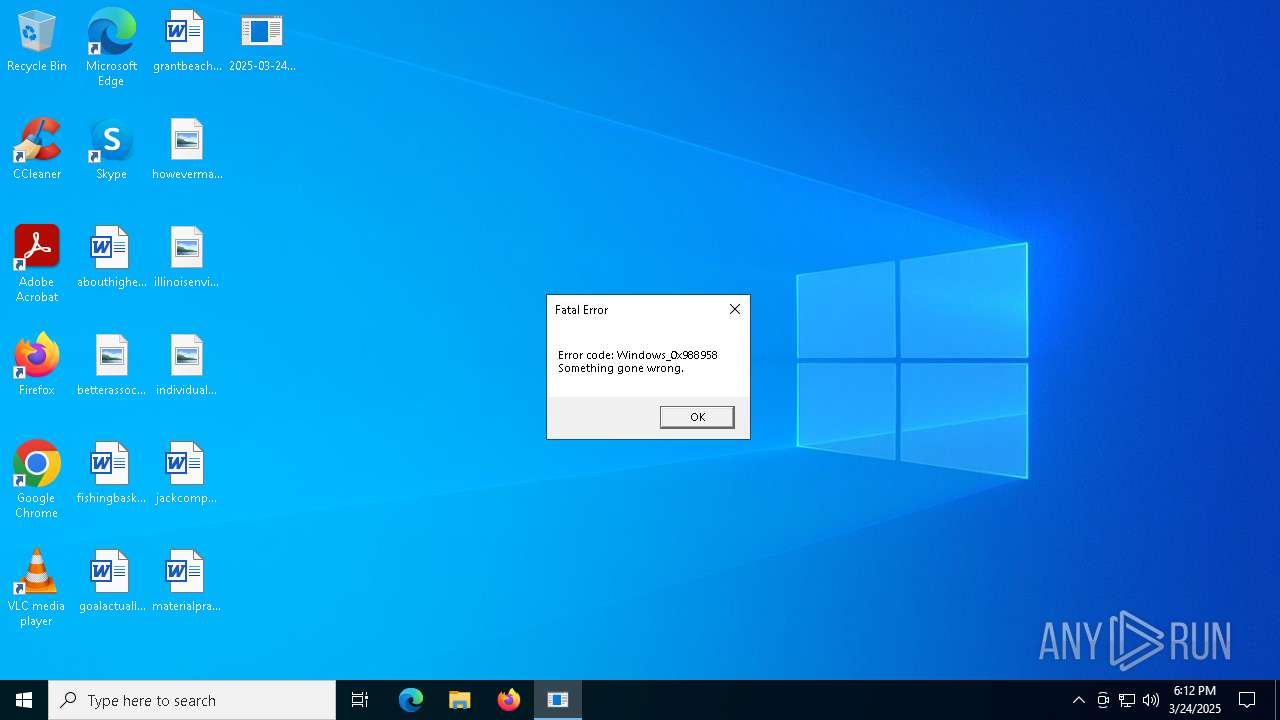
Changes default file association
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
Starts CMD.EXE for commands execution
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 1164)
- WMIC.exe (PID: 3332)
Uses WMIC.EXE to obtain operating system information
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Read disk information to detect sandboxing environments
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 5720)
- WMIC.exe (PID: 2516)
Creates or modifies Windows services
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Executable content was dropped or overwritten
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
- csc.exe (PID: 5960)
Uses WMIC.EXE to obtain Windows Installer data
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Uses ATTRIB.EXE to modify file attributes
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1276)
Uses WMIC.EXE to obtain CPU information
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Checks for external IP
- svchost.exe (PID: 2196)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Uses WMIC.EXE to obtain a list of video controllers
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Starts POWERSHELL.EXE for commands execution
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Script adds exclusion path to Windows Defender
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Base64-obfuscated command line is found
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
BASE64 encoded PowerShell command has been detected
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Script disables Windows Defender's IPS
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Script disables Windows Defender's real-time protection
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Uses NETSH.EXE to obtain data on the network
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
The process bypasses the loading of PowerShell profile settings
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 4108)
CSC.EXE is used to compile C# code
- csc.exe (PID: 5960)
Modifies hosts file to alter network resolution
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Possible usage of Discord/Telegram API has been detected (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Multiple wallet extension IDs have been found
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Found regular expressions for crypto-addresses (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
There is functionality for taking screenshot (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
There is functionality for capture public ip (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
INFO
Checks supported languages
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
- csc.exe (PID: 5960)
- cvtres.exe (PID: 2420)
Reads the computer name
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Drops encrypted JS script (Microsoft Script Encoder)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 5892)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Reads security settings of Internet Explorer
- fodhelper.exe (PID: 7084)
- WMIC.exe (PID: 1164)
- WMIC.exe (PID: 5720)
- WMIC.exe (PID: 7036)
- WMIC.exe (PID: 2516)
- WMIC.exe (PID: 1276)
- WMIC.exe (PID: 3332)
- notepad.exe (PID: 6576)
- notepad.exe (PID: 5964)
- notepad.exe (PID: 900)
Creates files or folders in the user directory
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Reads the machine GUID from the registry
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
- csc.exe (PID: 5960)
Reads the software policy settings
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
- slui.exe (PID: 856)
Create files in a temporary directory
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
- csc.exe (PID: 5960)
- cvtres.exe (PID: 2420)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 6972)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 6972)
Manual execution by a user
- notepad.exe (PID: 6576)
- notepad.exe (PID: 5964)
- notepad.exe (PID: 900)
Application based on Golang
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Detects GO elliptic curve encryption (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Found Base64 encoded reflection usage via PowerShell (YARA)
- 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe (PID: 4300)
Checks proxy server information
- slui.exe (PID: 856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(4300) 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe
Discord-Webhook-Tokens (1)1350895550920134686/ueTgZjJrTMbN9wj5aMIyqvGWMRilKU2UI-mtdLnGPvg91h2YDqcdLgVuOI2VjBG_iGT1
Discord-Info-Links
1350895550920134686/ueTgZjJrTMbN9wj5aMIyqvGWMRilKU2UI-mtdLnGPvg91h2YDqcdLgVuOI2VjBG_iGT1
Get Webhook Infohttps://discord.com/api/webhooks/1350895550920134686/ueTgZjJrTMbN9wj5aMIyqvGWMRilKU2UI-mtdLnGPvg91h2YDqcdLgVuOI2VjBG_iGT1
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 5198848 |
| InitializedDataSize: | 568832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x77c60 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
149
Monitored processes
29
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | cmd.exe /C fodhelper | C:\Windows\System32\cmd.exe | — | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\logins.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | fodhelper | C:\Windows\System32\fodhelper.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Features On Demand Helper Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "C:\WINDOWS\system32\fodhelper.exe" | C:\Windows\System32\fodhelper.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Features On Demand Helper Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | wmic csproduct get UUID | C:\Windows\System32\wbem\WMIC.exe | — | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | attrib +h +s C:\Users\admin\AppData\Roaming\Microsoft\Protect\SecurityHealthSystray.exe | C:\Windows\System32\attrib.exe | — | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 483
Read events
25 475
Write events
7
Delete events
1
Modification events
| (PID) Process: | (5892) 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (5892) 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete value | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (7084) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7084) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7084) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7084) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4300) 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\partmgr |
| Operation: | write | Name: | EnableCounterForIoctl |
Value: 1 | |||
| (PID) Process: | (4300) 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Realtek HD Audio Universal Service |
Value: C:\Users\admin\AppData\Roaming\Microsoft\Protect\SecurityHealthSystray.exe | |||
Executable files
2
Suspicious files
7
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4380 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1541rqj5.ulz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Local\Temp\commonfiles.zip | compressed | |
MD5:F2025C1C2CD8209C5F041FEE90F84496 | SHA256:CA582F42C4B5DB9A35DFBD30E5457DC20D7068437399CC238CEF2A320E8AC5A8 | |||
| 4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Local\Temp\browsers-temp\admin\Firefox\9kie7cg6.default-release\logins.txt | text | |
MD5:3ABC2B9ECCDC1C9E0199A80659C0090F | SHA256:8ED25C40A8274013F5EC722DE7B1306751426F04FD138944FE2DBD083AD802DA | |||
| 4108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\l4j3as1r\l4j3as1r.0.cs | text | |
MD5:C76055A0388B713A1EABE16130684DC3 | SHA256:8A3CD008E86A3D835F55F8415F5FD264C6DACDF0B7286E6854EA3F5A363390E7 | |||
| 4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Microsoft\Protect\SecurityHealthSystray.exe | executable | |
MD5:355093473251545C6EDB50AAB21A5774 | SHA256:EE818D0DC6FF205EC678A47AA586DD9642C71C4D13F45772DAE5C1EFA1B59C7C | |||
| 4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Local\Temp\browsers-temp\admin\Edge\Default\cookies.txt | text | |
MD5:4E7E979B554CE1F04144AAF6C5F6A321 | SHA256:DAA03BBC2A5969DD0129DD53FC3FA889BC1938DB3622C1C1B8DA9AA951401C73 | |||
| 4108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hhwbnhra.e1s.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4380 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yhjjty5s.qzf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Local\Temp\browsers.zip | compressed | |
MD5:91CCE39DE82F6B8B6E3A39EE0E990AC5 | SHA256:8B68EAC50D5DB06A5AB81DBA89E0E1E0008B452073D721134181D67599A0AA89 | |||
| 4108 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vnpliihx.qz3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
26
DNS requests
8
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | unknown |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
— | — | GET | 404 | 51.91.7.6:443 | https://api.gofile.io/getServer | unknown | text | 14 b | whitelisted |
— | — | POST | — | 162.159.136.232:443 | https://discord.com/api/webhooks/1350895550920134686/ueTgZjJrTMbN9wj5aMIyqvGWMRilKU2UI-mtdLnGPvg91h2YDqcdLgVuOI2VjBG_iGT1 | unknown | — | — | whitelisted |
— | — | POST | — | 162.159.136.232:443 | https://discord.com/api/webhooks/1350895550920134686/ueTgZjJrTMbN9wj5aMIyqvGWMRilKU2UI-mtdLnGPvg91h2YDqcdLgVuOI2VjBG_iGT1 | unknown | — | — | whitelisted |
— | — | POST | — | 162.159.128.233:443 | https://discord.com/api/webhooks/1350895550920134686/ueTgZjJrTMbN9wj5aMIyqvGWMRilKU2UI-mtdLnGPvg91h2YDqcdLgVuOI2VjBG_iGT1 | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 104.26.13.205:443 | https://api.ipify.org/ | unknown | text | 12 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | 104.26.12.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | 51.91.7.6:443 | api.gofile.io | OVH SAS | FR | unknown |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | unknown |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | 162.159.137.232:443 | discord.com | CLOUDFLARENET | — | unknown |
4424 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
856 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
api.ipify.org |
| unknown |
ip-api.com |
| unknown |
api.gofile.io |
| unknown |
discord.com |
| unknown |
activation-v2.sls.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |
— | — | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |
4300 | 2025-03-24_355093473251545c6edb50aab21a5774_frostygoop_knight_luca-stealer_ngrbot_poet-rat_sliver_snatch.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |