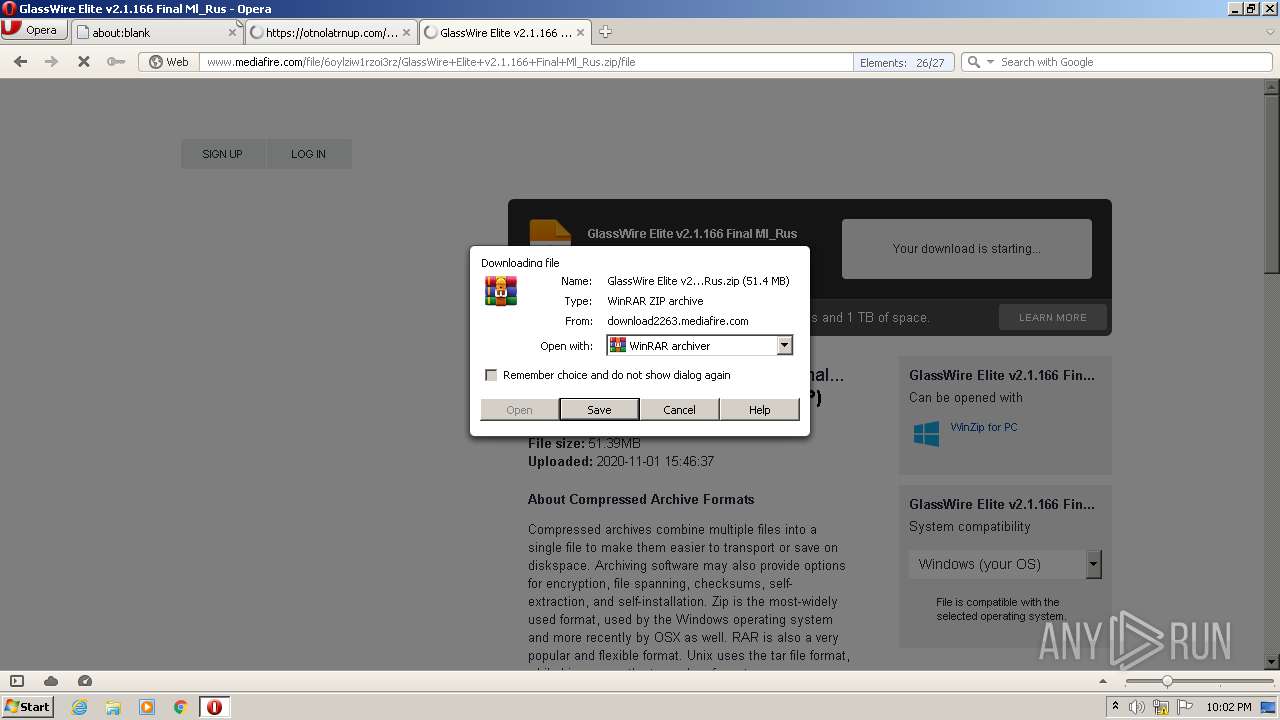
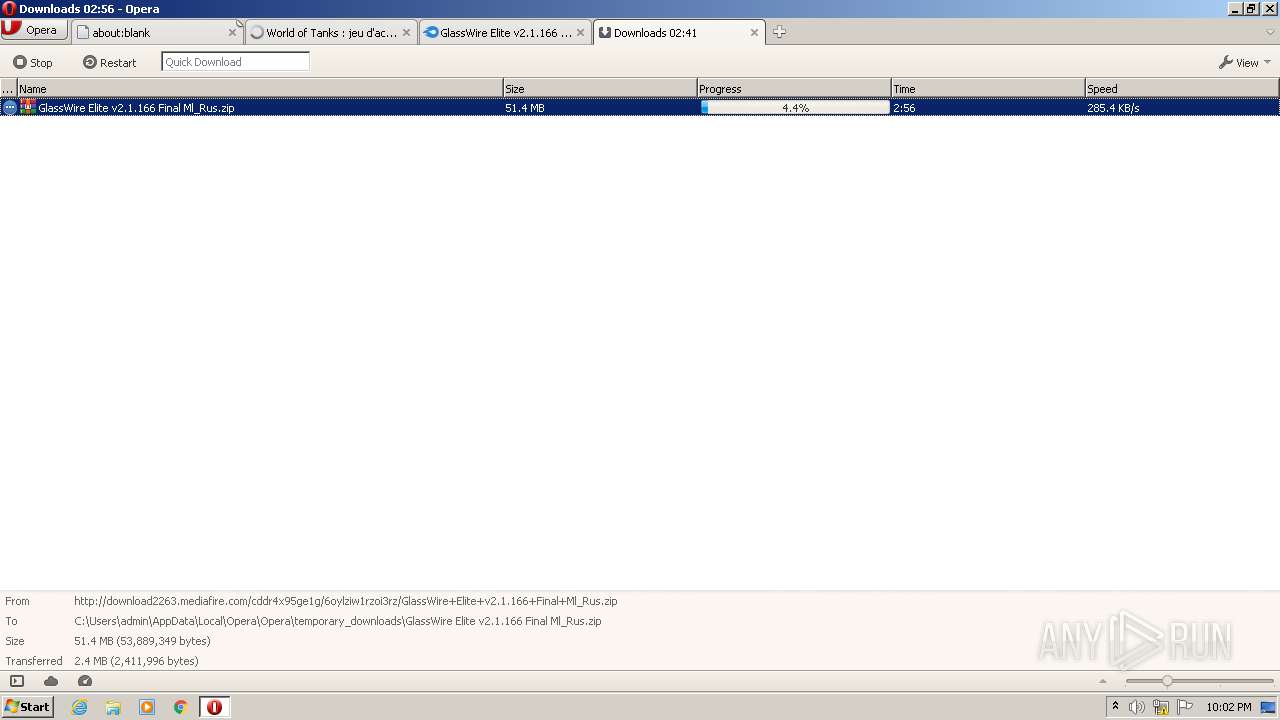
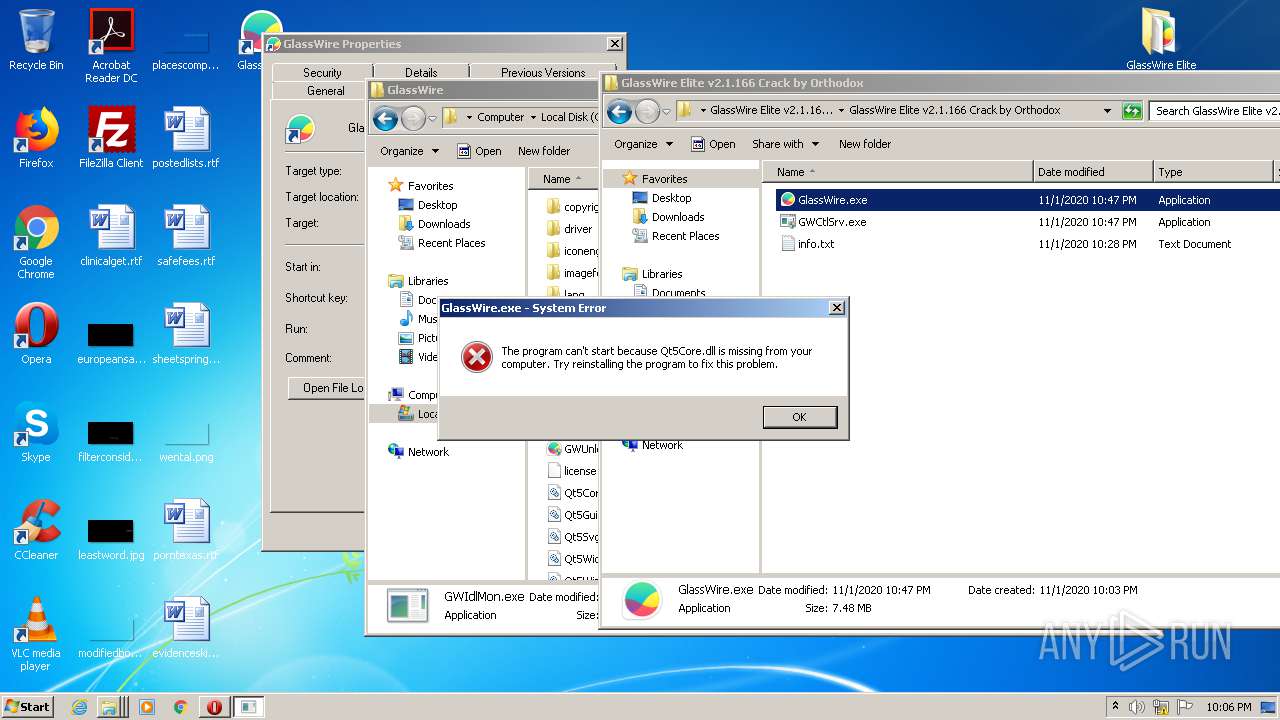
| URL: | http://www.mediafire.com/file/6oylziw1rzoi3rz/GlassWire+Elite+v2.1.166+Final+Ml_Rus.zip/file |
| Full analysis: | https://app.any.run/tasks/649cbf47-90c3-4c40-9125-405138f9cc59 |
| Verdict: | Malicious activity |
| Analysis date: | November 01, 2020, 22:01:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F6D9AC8B5D5956128F7F29F47395D2B2 |
| SHA1: | F9C1DB9F3BA237471A8B6D4DF5B76D191593644C |
| SHA256: | EE60B53998D141139B87B899DC08F02ADA67920D2561952D2F666A776925EF62 |
| SSDEEP: | 3:N1KJS4w3eGUoTK4i5JfbNm8X7fZgUHfMgx:Cc4w3eG3KxJffr6UHd |
MALICIOUS
Application was dropped or rewritten from another process
- GWInstSt.exe (PID: 3808)
- vc_redist.x86.exe (PID: 3320)
- vc_redist.x86.exe (PID: 760)
- ns8A35.tmp (PID: 2908)
- nsA36C.tmp (PID: 1740)
- nsA969.tmp (PID: 1896)
- nsA457.tmp (PID: 3736)
- GWCtlSrv.exe (PID: 2428)
- GWCtlSrv.exe (PID: 1500)
- GWIdlMon.exe (PID: 2180)
- GlassWire.exe (PID: 2824)
- GWUnlock.exe (PID: 3968)
- GWCtlSrv.exe (PID: 2436)
- GWUnlock.exe (PID: 3764)
- GlassWire.exe (PID: 2892)
- GWCtlSrv.exe (PID: 1736)
- GWCtlSrv.exe (PID: 3164)
Loads dropped or rewritten executable
- GlassWireSetup.exe (PID: 3820)
- vc_redist.x86.exe (PID: 3320)
- GWCtlSrv.exe (PID: 2436)
- GWCtlSrv.exe (PID: 1500)
- GWCtlSrv.exe (PID: 2428)
- GWIdlMon.exe (PID: 2180)
- GlassWire.exe (PID: 2824)
Changes settings of System certificates
- GWInstSt.exe (PID: 3808)
Starts NET.EXE for service management
- cmd.exe (PID: 1836)
- nsA36C.tmp (PID: 1740)
Changes the autorun value in the registry
- rundll32.exe (PID: 1052)
- GlassWireSetup.exe (PID: 3820)
SUSPICIOUS
Executable content was dropped or overwritten
- vc_redist.x86.exe (PID: 3320)
- WinRAR.exe (PID: 828)
- GlassWireSetup.exe (PID: 3820)
- cmd.exe (PID: 1836)
- rundll32.exe (PID: 1052)
- DllHost.exe (PID: 3300)
- DllHost.exe (PID: 3748)
Searches for installed software
- vc_redist.x86.exe (PID: 3320)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 1836)
Application launched itself
- vc_redist.x86.exe (PID: 760)
Starts CMD.EXE for commands execution
- ns8A35.tmp (PID: 2908)
Creates files in the program directory
- GlassWireSetup.exe (PID: 3820)
- GWCtlSrv.exe (PID: 1500)
Starts application with an unusual extension
- GlassWireSetup.exe (PID: 3820)
Reads Internet Cache Settings
- GWInstSt.exe (PID: 3808)
Creates files in the Windows directory
- cmd.exe (PID: 1836)
- rundll32.exe (PID: 1052)
Creates files in the driver directory
- cmd.exe (PID: 1836)
- rundll32.exe (PID: 1052)
Adds / modifies Windows certificates
- GWInstSt.exe (PID: 3808)
Creates a software uninstall entry
- GlassWireSetup.exe (PID: 3820)
Removes files from Windows directory
- rundll32.exe (PID: 1052)
Executed via COM
- explorer.exe (PID: 1012)
- DllHost.exe (PID: 3300)
- DllHost.exe (PID: 3748)
- DllHost.exe (PID: 1096)
Creates files in the user directory
- GlassWireSetup.exe (PID: 3820)
Executed as Windows Service
- GWCtlSrv.exe (PID: 1500)
INFO
Dropped object may contain Bitcoin addresses
- GlassWireSetup.exe (PID: 3820)
- opera.exe (PID: 2496)
Creates files in the user directory
- opera.exe (PID: 2496)
Manual execution by user
- GlassWireSetup.exe (PID: 1880)
- GlassWireSetup.exe (PID: 3820)
- GWUnlock.exe (PID: 3968)
- GWUnlock.exe (PID: 3764)
- GlassWire.exe (PID: 2892)
- GWCtlSrv.exe (PID: 3164)
- GWCtlSrv.exe (PID: 1736)
Reads the hosts file
- GWCtlSrv.exe (PID: 1500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
34
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 760 | "C:\Users\admin\AppData\Local\Temp\nspFF4.tmp\vc_redist.x86.exe" /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\nspFF4.tmp\vc_redist.x86.exe | — | GlassWireSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015 Redistributable (x86) - 14.0.23026 Exit code: 1638 Version: 14.0.23026.0 Modules
| |||||||||||||||
| 828 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\GlassWire Elite v2.1.166 Final Ml_Rus.zip" | C:\Program Files\WinRAR\WinRAR.exe | opera.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1012 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1052 | C:\Windows\System32\RunDLL32.Exe syssetup,SetupInfObjectInstallAction DefaultInstall 128 C:\Windows\System32\Drivers\gwdrv.inf | C:\Windows\System32\rundll32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1096 | C:\Windows\system32\DllHost.exe /Processid:{1F2E5C40-9550-11CE-99D2-00AA006E086C} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | C:\Windows\System32\net.exe start gwdrv | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1500 | "C:\Program Files\GlassWire\GWCtlSrv.exe" | C:\Program Files\GlassWire\GWCtlSrv.exe | services.exe | ||||||||||||
User: SYSTEM Company: SecureMix LLC Integrity Level: SYSTEM Description: GlassWire Control Service Exit code: 0 Version: 2.1.166.0 Modules
| |||||||||||||||
| 1624 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\system32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\Desktop\GlassWire Elite v2.1.166 Final Ml_Rus\GlassWire Elite v2.1.166 Crack by Orthodox\GWCtlSrv.exe" | C:\Users\admin\Desktop\GlassWire Elite v2.1.166 Final Ml_Rus\GlassWire Elite v2.1.166 Crack by Orthodox\GWCtlSrv.exe | — | explorer.exe | |||||||||||
User: admin Company: SecureMix LLC Integrity Level: MEDIUM Description: GlassWire Control Service Exit code: 3221226540 Version: 2.1.166.0 Modules
| |||||||||||||||
Total events
1 705
Read events
1 553
Write events
151
Delete events
1
Modification events
| (PID) Process: | (2496) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe "http://www.mediafire.com/file/6oylziw1rzoi3rz/GlassWire+Elite+v2.1.166+Final+Ml_Rus.zip/file" | |||
| (PID) Process: | (2496) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2496) opera.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2496) opera.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\GlassWire Elite v2.1.166 Final Ml_Rus.zip | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
36
Suspicious files
120
Text files
167
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprEED3.tmp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprEEE4.tmp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprEF23.tmp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KK3O06HD5HOODS6BNWJE.temp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprFDCA.tmp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr1A4C.tmp | — | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00002.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2496 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF14fae9.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
134
DNS requests
67
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2496 | opera.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDnJZWF0MyB9wgAAAAAXcDo | US | der | 472 b | whitelisted |
2496 | opera.exe | GET | 200 | 104.16.203.237:80 | http://www.mediafire.com/images/icons/svg_light/icons_sprite.svg | US | image | 8.24 Kb | shared |
2496 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
2496 | opera.exe | GET | 200 | 172.217.16.142:80 | http://translate.google.com/translate_a/element.js?cb=googFooterTranslate | US | text | 1.84 Kb | whitelisted |
2496 | opera.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDGiuZIk2yXOgIAAAAAfZgP | US | der | 472 b | whitelisted |
2496 | opera.exe | GET | 200 | 104.16.203.237:80 | http://www.mediafire.com/js/prebid2.44.1.js | US | text | 52.9 Kb | shared |
2496 | opera.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFTRO09rwWFMAgAAAAB9mA4%3D | US | der | 471 b | whitelisted |
2496 | opera.exe | GET | 200 | 104.16.203.237:80 | http://static.mediafire.com/images/filetype/file-zip-v3.png | US | image | 1.83 Kb | shared |
2496 | opera.exe | GET | 200 | 104.16.203.237:80 | http://www.mediafire.com/favicon.ico | US | image | 1.42 Kb | shared |
2496 | opera.exe | GET | 200 | 216.58.206.3:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 950 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2496 | opera.exe | 82.145.216.16:80 | sitecheck2.opera.com | Opera Software AS | — | suspicious |
2496 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2496 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2496 | opera.exe | 82.145.216.15:80 | sitecheck2.opera.com | Opera Software AS | — | suspicious |
2496 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2496 | opera.exe | 172.217.16.142:80 | fundingchoicesmessages.google.com | Google Inc. | US | whitelisted |
2496 | opera.exe | 172.217.16.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2496 | opera.exe | 64.233.166.155:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
2496 | opera.exe | 172.217.22.100:443 | www.google.com | Google Inc. | US | whitelisted |
2496 | opera.exe | 104.16.203.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
sitecheck2.opera.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
crl.pki.goog |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
static.mediafire.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2496 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2496 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2496 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2496 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
Process | Message |
|---|---|
GlassWire.exe | Empty color "graph_out_border_11"
|
GlassWire.exe | Empty color "legend_in_fill_10"
|
GlassWire.exe | Empty color "legend_in_fill_11"
|
GlassWire.exe | Empty color "legend_in_fill_2"
|
GlassWire.exe | Empty color "graph_out_border"
|
GlassWire.exe | Empty color "graph_out_border_11"
|
GlassWire.exe | Empty color "legend_in_fill_10"
VϬꅿ낚ǖϬEmpty color "legend_in_fill_10"
|
GlassWire.exe | Empty color "graph_out_border_7"
|
GlassWire.exe | Empty color "graph_in_border"
|
GlassWire.exe | Empty color "legend_in_fill_6"
|