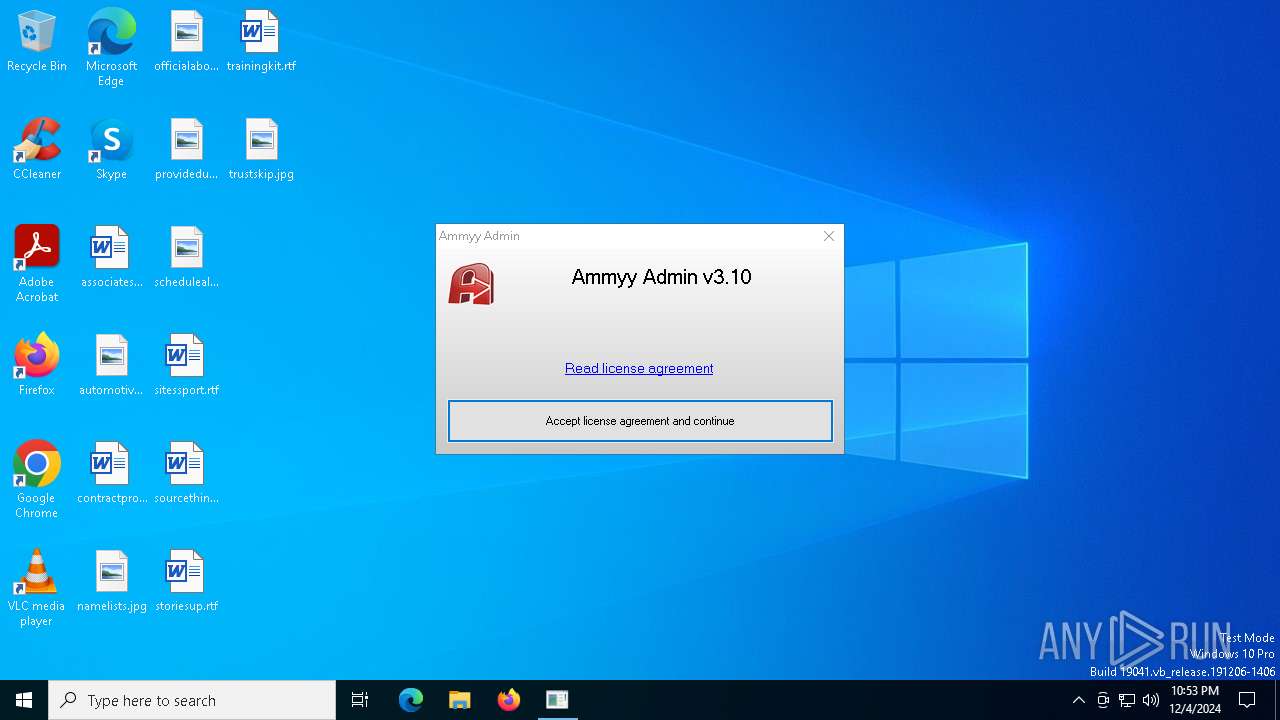
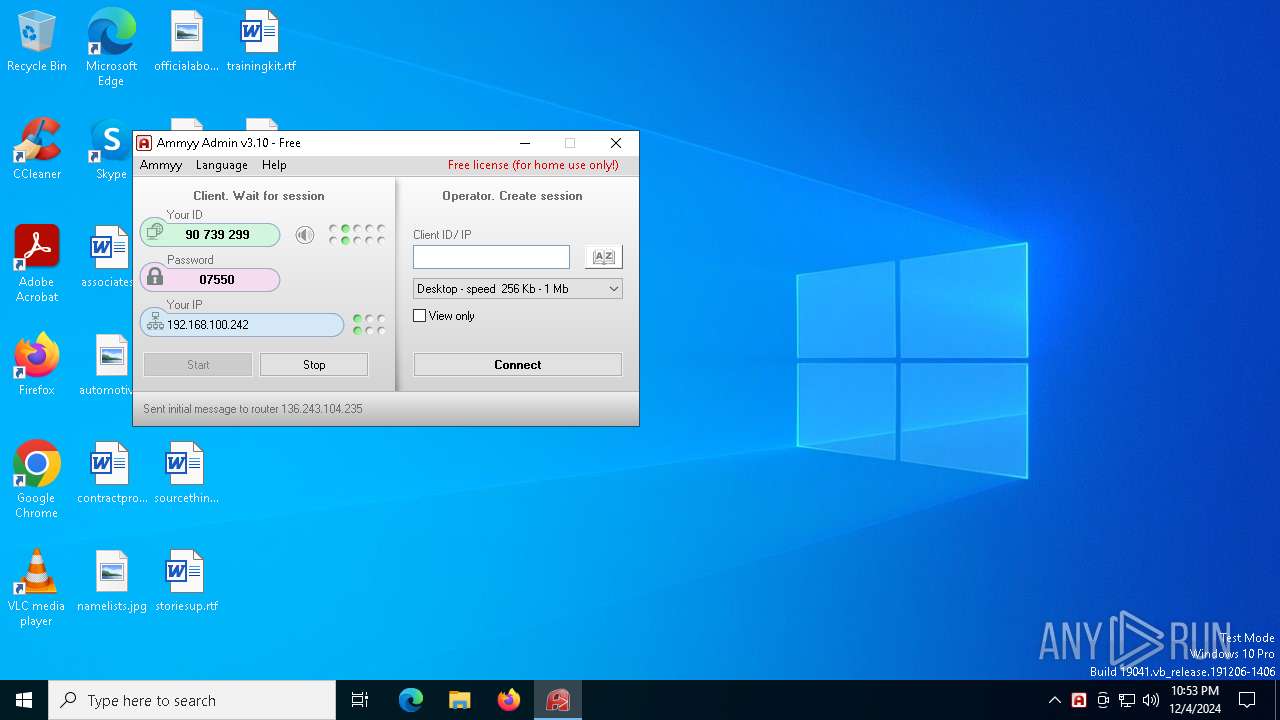
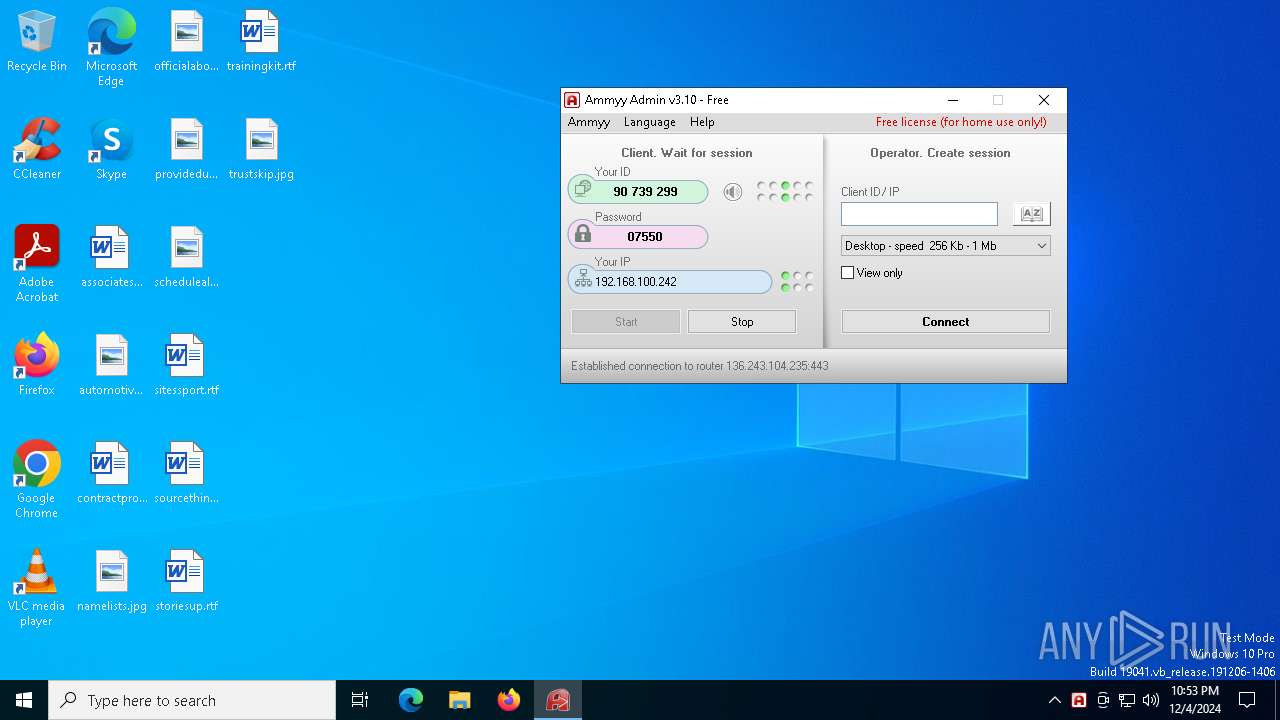
| File name: | AA.exe |
| Full analysis: | https://app.any.run/tasks/4774be09-f462-49ff-83ce-8b67cd7380e4 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2024, 22:52:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 90AADF2247149996AE443E2C82AF3730 |
| SHA1: | 050B7EBA825412B24E3F02D76D7DA5AE97E10502 |
| SHA256: | EE573647477339784DCEF81024DE1BE1762833A20E5CC2B89A93E47D05B86B6A |
| SSDEEP: | 24576:Uj0JJ4p/A4npt3XojeQG5EtzRtO7GvmDguXd:UjoJ4u4zojegylDN |
MALICIOUS
AMMYY has been detected (SURICATA)
- AA.exe (PID: 6936)
SUSPICIOUS
Application launched itself
- AA.exe (PID: 6512)
- AA.exe (PID: 6904)
Executes as Windows Service
- AA.exe (PID: 6904)
Executable content was dropped or overwritten
- AA.exe (PID: 6936)
Uses RUNDLL32.EXE to load library
- AA.exe (PID: 6936)
Potential Corporate Privacy Violation
- AA.exe (PID: 6936)
There is functionality for enable RDP (YARA)
- AA.exe (PID: 6936)
Checks for external IP
- AA.exe (PID: 6936)
There is functionality for taking screenshot (YARA)
- AA.exe (PID: 6936)
INFO
Creates files in the program directory
- AA.exe (PID: 6512)
Checks supported languages
- AA.exe (PID: 6512)
- AA.exe (PID: 6904)
- AA.exe (PID: 6756)
- AA.exe (PID: 6936)
Checks proxy server information
- AA.exe (PID: 6512)
Reads the computer name
- AA.exe (PID: 6904)
- AA.exe (PID: 6756)
- AA.exe (PID: 6936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:09:15 16:09:42+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 581632 |
| InitializedDataSize: | 258048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x86db8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.10.0.0 |
| ProductVersionNumber: | 3.10.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Ammyy LLC |
| FileDescription: | Ammyy Admin |
| FileVersion: | 3.1 |
| InternalName: | Ammyy Admin |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| PrivateBuild: | - |
| ProductName: | Ammyy Admin |
| ProductVersion: | 3.1 |
| SpecialBuild: | - |
Total processes
130
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6512 | "C:\Users\admin\AppData\Local\Temp\AA.exe" | C:\Users\admin\AppData\Local\Temp\AA.exe | — | explorer.exe | |||||||||||
User: admin Company: Ammyy LLC Integrity Level: MEDIUM Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 6740 | rundll32.exe "C:\ProgramData\AMMYY\aa_nts.dll",run | C:\Windows\System32\rundll32.exe | — | AA.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6756 | "C:\Users\admin\AppData\Local\Temp\AA.exe" -elevated | C:\Users\admin\AppData\Local\Temp\AA.exe | AA.exe | ||||||||||||
User: admin Company: Ammyy LLC Integrity Level: HIGH Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 6904 | "C:\Users\admin\AppData\Local\Temp\AA.exe" -service -lunch | C:\Users\admin\AppData\Local\Temp\AA.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Ammyy LLC Integrity Level: SYSTEM Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 6936 | "C:\Users\admin\AppData\Local\Temp\AA.exe" -elevated | C:\Users\admin\AppData\Local\Temp\AA.exe | AA.exe | ||||||||||||
User: SYSTEM Company: Ammyy LLC Integrity Level: SYSTEM Description: Ammyy Admin Version: 3.10 Modules
| |||||||||||||||
Total events
1 166
Read events
1 163
Write events
2
Delete events
1
Modification events
| (PID) Process: | (6756) AA.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\AmmyyAdmin_1A64 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6936) AA.exe | Key: | HKEY_USERS\.DEFAULT\Software\Ammyy\Admin |
| Operation: | write | Name: | hr3 |
Value: BB58F015B548C3034CAEB75387E8C77B8633D782EA4299405A8708463D4566DD5014ED143CBC7EE1312F24261F06B6DA91DDC3853CF0EAEF038B1286FCB3A4744B9BE3 | |||
| (PID) Process: | (6936) AA.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Ammyy\Admin |
| Operation: | write | Name: | hr3 |
Value: BB58F015B548C3034CAEB75387E8C77B8633D782EA4299405A8708463D4566DD5014ED143CBC7EE1312F24261F06B6DA91DDC3853CF0EAEF038B1286FCB3A4744B9BE3 | |||
Executable files
1
Suspicious files
7
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6936 | AA.exe | C:\ProgramData\AMMYY\aa_nts.msg | binary | |
MD5:2F0D446171630FBD6B6CC8D87EC6161E | SHA256:2635277B0926D9828A3FDAB2ABA6AEE78A615B78D6115EAF05EFC01A06B752D1 | |||
| 6936 | AA.exe | C:\Windows\SysWOW64\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 6936 | AA.exe | C:\Users\admin\AppData\Local\Temp\AA.log | text | |
MD5:6E064020CB4B0844C3E73FB649B42DFB | SHA256:AEF29A0C470D0A2025C237656D8EAE270239C1EEA4747C7979FB47E5BABAA984 | |||
| 6936 | AA.exe | C:\Windows\SysWOW64\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\34B6AF881B9D738561FC099B83DF3A01 | binary | |
MD5:2FAD71D10DA26615B6613B2172A53A58 | SHA256:A69C8B0AFFEFE7ABF8E294515F3B8078E41BD004AF7293C757951A2683611F3C | |||
| 6936 | AA.exe | C:\ProgramData\AMMYY\aa_nts.dll | executable | |
MD5:480A66902E6E7CDAFAA6711E8697FF8C | SHA256:7EAAAA6010BBCD6BB8C9AD08D4B0966C7AEDC9B2AC24758F170012AC36E508B5 | |||
| 6936 | AA.exe | C:\Windows\SysWOW64\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:2AAADC3D5F4544635258D099C95CB928 | SHA256:1E0239F73F571607BC7EA361F3E55862120454873D98A027E8FCE5873BA54D24 | |||
| 6512 | AA.exe | C:\ProgramData\AMMYY\settings3.bin | binary | |
MD5:B8946EDDA960DAD0F7438CD387BF1CF3 | SHA256:48149E6BED76634A06EA70DDC2CD48EA187CF4D6C98802FC31EE6291A82405B3 | |||
| 6936 | AA.exe | C:\ProgramData\AMMYY\hr3 | binary | |
MD5:F0E076EC5991B27DAA58B768A2661406 | SHA256:493B339AC3E5BD745D4318D8FCB808F18D231E005C9DA642CF43772DAD4329CD | |||
| 6936 | AA.exe | C:\Windows\SysWOW64\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\34B6AF881B9D738561FC099B83DF3A01 | binary | |
MD5:4CA197C700FD4ABFC2613F906D6D1A6B | SHA256:0B42D0D2E7824DEAF352CE51C2AE34C08483510F7A289D315CFD37717CC1E8D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
40
DNS requests
20
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6936 | AA.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6936 | AA.exe | POST | 200 | 188.42.129.148:80 | http://rl.ammyy.com/ | unknown | — | — | malicious |
6936 | AA.exe | GET | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgSfBEjCuhCXdl7Defz8ipA09g%3D%3D | unknown | — | — | whitelisted |
6936 | AA.exe | GET | 301 | 136.243.18.118:80 | http://www.ammyy.com/files/v8/aans64y2.gz | unknown | — | — | malicious |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.179:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
rl.ammyy.com |
| unknown |
www.ammyy.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6936 | AA.exe | Potential Corporate Privacy Violation | ET POLICY IP Check (rl. ammyy. com) |
1 ETPRO signatures available at the full report