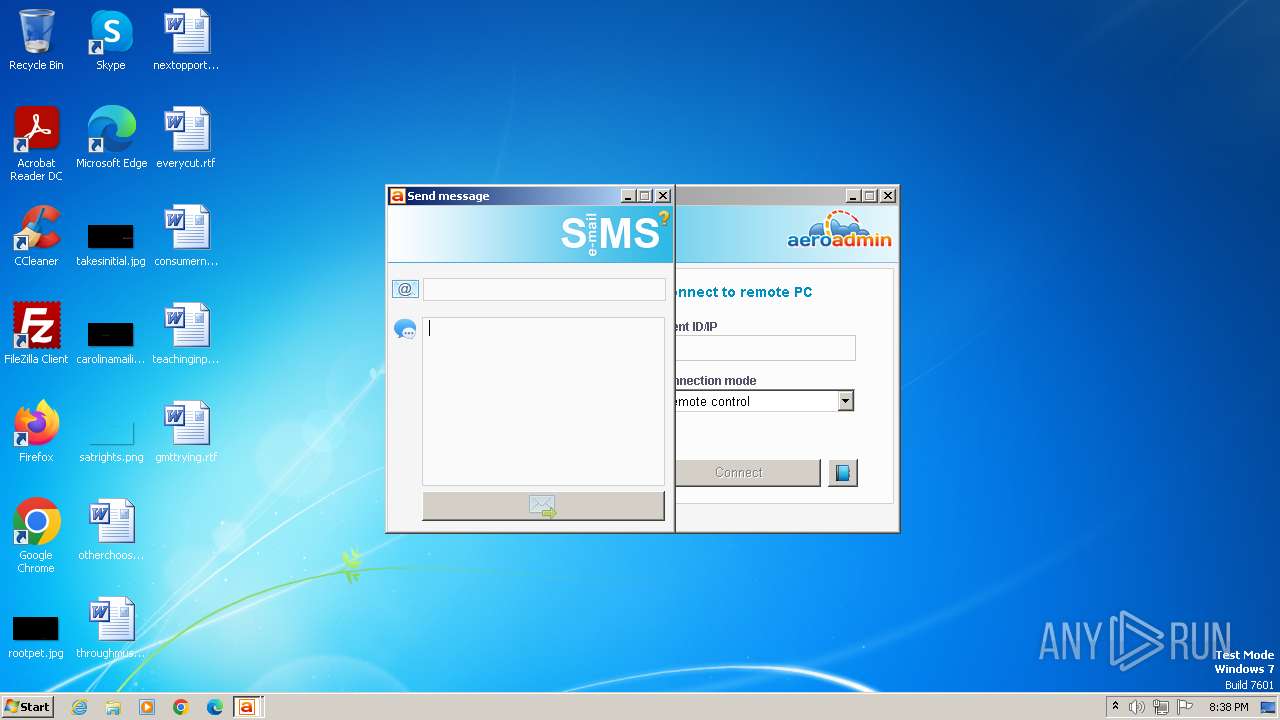
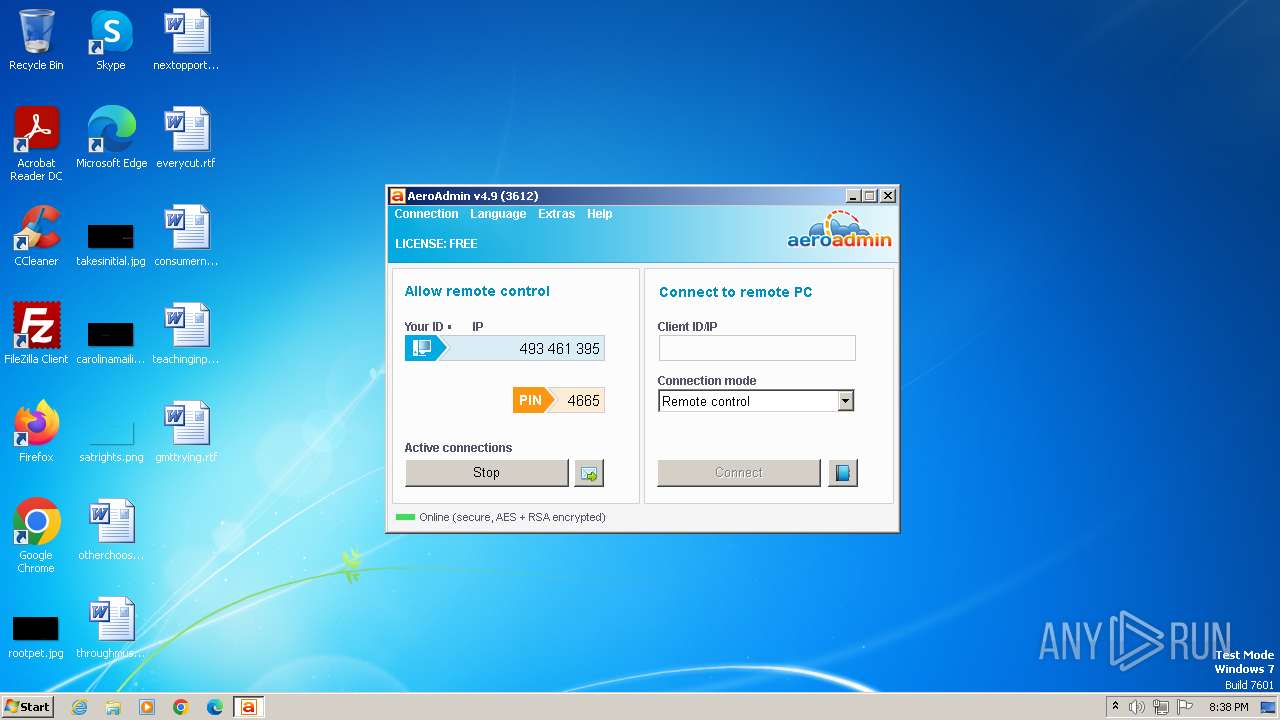
| File name: | AeroAdmin.exe |
| Full analysis: | https://app.any.run/tasks/3b9046ec-980f-4cfd-866e-bea92ed0a677 |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2024, 20:34:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FA6AD2E8EEF98ABC0BBB252FF994A38D |
| SHA1: | B54CC9383C67A5C90F74E07D0A3203CC4DC1756C |
| SHA256: | EE54577067550559C4711C9E5E10435807F9DEEE9A5ADB4409CB60A6B0108700 |
| SSDEEP: | 49152:OxuXwMnQUnvoA4N1015+pTAg6NTkGCgOOxQTYywC8PSJzNBUkpijZMI9n3:xg2Qw4PCNT49eBGQ |
MALICIOUS
Drops the executable file immediately after the start
- AeroAdmin.exe (PID: 116)
Creates a writable file in the system directory
- AeroAdmin.exe (PID: 572)
SUSPICIOUS
Application launched itself
- AeroAdmin.exe (PID: 116)
- AeroAdmin.exe (PID: 1344)
Reads the Internet Settings
- AeroAdmin.exe (PID: 116)
Executes as Windows Service
- AeroAdmin.exe (PID: 1344)
Connects to unusual port
- AeroAdmin.exe (PID: 572)
Checks Windows Trust Settings
- AeroAdmin.exe (PID: 572)
INFO
Reads the computer name
- AeroAdmin.exe (PID: 116)
- AeroAdmin.exe (PID: 668)
- AeroAdmin.exe (PID: 1344)
- AeroAdmin.exe (PID: 572)
Checks supported languages
- AeroAdmin.exe (PID: 116)
- AeroAdmin.exe (PID: 668)
- AeroAdmin.exe (PID: 1344)
- AeroAdmin.exe (PID: 572)
Creates files in the program directory
- AeroAdmin.exe (PID: 116)
- AeroAdmin.exe (PID: 1344)
- AeroAdmin.exe (PID: 572)
Reads the machine GUID from the registry
- AeroAdmin.exe (PID: 572)
Process checks computer location settings
- AeroAdmin.exe (PID: 572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:07 10:49:40+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.32 |
| CodeSize: | 1871872 |
| InitializedDataSize: | 1304576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x184096 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.6.1.2 |
| ProductVersionNumber: | 4.9.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | AeroAdmin LLC |
| FileDescription: | AeroAdmin |
| FileVersion: | 3.6.1.2 |
| InternalName: | AeroAdmin.exe |
| LegalCopyright: | AeroAdmin LLC |
| LegalTrademarks: | AeroAdmin |
| OriginalFileName: | AeroAdmin.exe |
| ProductName: | AeroAdmin |
| ProductVersion: | v4.9 |
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Downloads\AeroAdmin.exe" | C:\Users\admin\Downloads\AeroAdmin.exe | explorer.exe | ||||||||||||
User: admin Company: AeroAdmin LLC Integrity Level: MEDIUM Description: AeroAdmin Exit code: 0 Version: 3.6.1.2 Modules
| |||||||||||||||
| 572 | "C:\Users\admin\Downloads\AeroAdmin.exe" a -sid 1 | C:\Users\admin\Downloads\AeroAdmin.exe | AeroAdmin.exe | ||||||||||||
User: SYSTEM Company: AeroAdmin LLC Integrity Level: SYSTEM Description: AeroAdmin Exit code: 0 Version: 3.6.1.2 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\Downloads\AeroAdmin.exe" z z | C:\Users\admin\Downloads\AeroAdmin.exe | AeroAdmin.exe | ||||||||||||
User: admin Company: AeroAdmin LLC Integrity Level: HIGH Description: AeroAdmin Exit code: 0 Version: 3.6.1.2 Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\Downloads\AeroAdmin.exe" s -sid 1 | C:\Users\admin\Downloads\AeroAdmin.exe | services.exe | ||||||||||||
User: SYSTEM Company: AeroAdmin LLC Integrity Level: SYSTEM Description: AeroAdmin Exit code: 0 Version: 3.6.1.2 Modules
| |||||||||||||||
Total events
5 696
Read events
5 665
Write events
31
Delete events
0
Modification events
| (PID) Process: | (116) AeroAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) AeroAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) AeroAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) AeroAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (572) AeroAdmin.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (572) AeroAdmin.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (572) AeroAdmin.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (572) AeroAdmin.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000000900000009000000000000000000000000000000040000000000000000000000000000000000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (572) AeroAdmin.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (572) AeroAdmin.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
8
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 572 | AeroAdmin.exe | C:\ProgramData\Aeroadmin\settings.bin | binary | |
MD5:7AEEFC947249D9CCDFB54014975E32DD | SHA256:8B6DA6102E5F5ACDC0A358F0106691F170E082AD9D112CBDFDE40A8DB81B0873 | |||
| 116 | AeroAdmin.exe | C:\ProgramData\Aeroadmin\log.txt | text | |
MD5:D7586E1899616920A3622A343CECC139 | SHA256:A994D62922980FD5242C94503ACDF620551234D531215D86C8791F00E7647E3F | |||
| 572 | AeroAdmin.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:11B5DB5BFDF6911B4F7E3F3989BE3992 | SHA256:EAF976866B4CAE502BEEA5310ACE2A1DC7D532DBAC78EDC76394F9C0BE676F2D | |||
| 572 | AeroAdmin.exe | C:\ProgramData\Aeroadmin\guid.bin | binary | |
MD5:06CE9AB135654A5167E8CC0FC2EFBAF5 | SHA256:082652E8B982C37A3C19FE61055050C9B03B630A8D85F3CAC10FD31263949E4B | |||
| 116 | AeroAdmin.exe | C:\ProgramData\Aeroadmin\config | binary | |
MD5:8E79D7C00351F3F5120F78694809BD13 | SHA256:F25F2E593B23683B4E53AB529EA665A80E350EBF82515E378A056D0274C67A64 | |||
| 572 | AeroAdmin.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:A1B6EDD77FEEB98CE1D93C17FEF4FFBE | SHA256:FCB936E5EAA5B8F84382FB82CE6BB1AA92D1779EBCADAFE3EFB7655A4627CAD3 | |||
| 572 | AeroAdmin.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:3EF3F437336696998B4EF381E2DFC612 | SHA256:747626A425C8B89C40F76DDC1C289CA968E7C0EA710321403F84CBBAEF440175 | |||
| 572 | AeroAdmin.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:FF5797A33A1AE6AD5A2412B55DA0FEA5 | SHA256:831FE509E9E0D8DDB266DB677C55834F9EF4F636154BE6099E98669E5279DF2D | |||
| 572 | AeroAdmin.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 1344 | AeroAdmin.exe | C:\ProgramData\Aeroadmin\log.json | text | |
MD5:FF8B9A5CABD629C5DA3013944109B493 | SHA256:A917AD2F5D20619CCBB6DA2F091098589CA11216B9E05EAE26E09365BE8866AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
572 | AeroAdmin.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?20233f32f8180128 | unknown | — | — | unknown |
572 | AeroAdmin.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
572 | AeroAdmin.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
572 | AeroAdmin.exe | 188.114.97.3:443 | ulm.aeroadmin.com | CLOUDFLARENET | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
572 | AeroAdmin.exe | 89.40.115.70:5665 | auth11.aeroadmin.com | Aruba SAS | FR | unknown |
572 | AeroAdmin.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
572 | AeroAdmin.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ulm.aeroadmin.com |
| unknown |
auth11.aeroadmin.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
572 | AeroAdmin.exe | Misc activity | ET POLICY PTsecurity Remote Desktop AeroAdmin Server Hello |
572 | AeroAdmin.exe | Misc activity | ET POLICY PTsecurity Remote Desktop AeroAdmin handshake |
Process | Message |
|---|---|
AeroAdmin.exe | Info: [20:34:35 / AeroAdmin.cpp 1010] Start
|
AeroAdmin.exe | Info: [20:34:35 / AeroAdmin.cpp 1120] mode: 0
|
AeroAdmin.exe | 20240119 20:34:36 [116 / Service.cpp:735] RestartAsAdmin: z , res = 1
|
AeroAdmin.exe | 20240119 20:34:36 [668 / Service.cpp:597] !hService
|
AeroAdmin.exe | Info: [20:34:36 / AeroAdmin.cpp 1010] Start
|
AeroAdmin.exe | 20240119 20:34:36 [668 / Service.cpp:529] Installing service: "C:\Users\admin\Downloads\AeroAdmin.exe" s -sid 1
|
AeroAdmin.exe | Info: [20:34:36 / AeroAdmin.cpp 915] start service as args: "s -sid 1 "
|
AeroAdmin.exe | Info: [20:34:36 / AeroAdmin.cpp 902] run_as_admin: 1, Removing service
|
AeroAdmin.exe | Info: [20:34:36 / AeroAdmin.cpp 1120] mode: "z"
|
AeroAdmin.exe | 20240119 20:34:37 [1344 / Service.cpp:384] server started
|