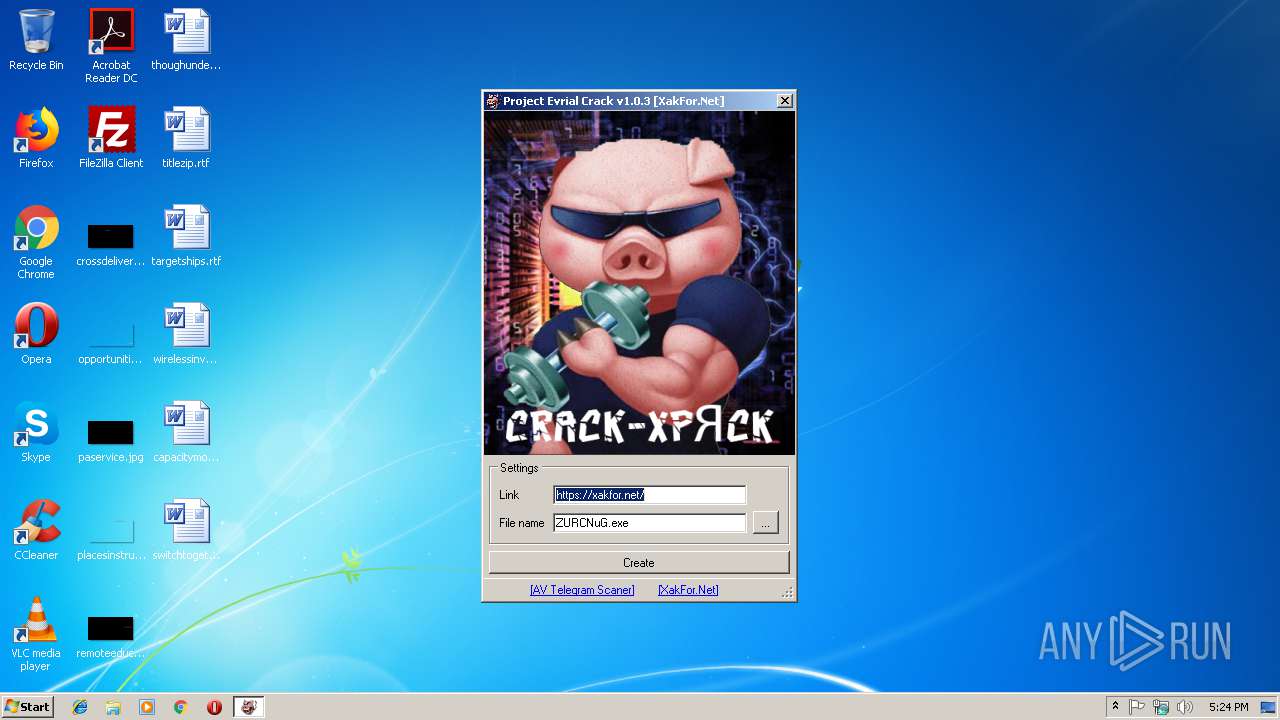
| File name: | Project Evrial Crack Crack [XakFor.Net].exe |
| Full analysis: | https://app.any.run/tasks/0523cd15-2544-48e9-8945-6cf30223a969 |
| Verdict: | No threats detected |
| Analysis date: | January 11, 2019, 17:24:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | A6D7DA47C7C96E1BA0B0347830564D10 |
| SHA1: | A8934F1A202C8FE9530FE6211E2070111794C11C |
| SHA256: | EE5168F91DFBE023A0A0AB9070159517E466F1C28DE6DDE40639884FB9AFBB37 |
| SSDEEP: | 12288:iEKkKKxdxOY9wYCTgVwbCeHZVy6lYvzh+leFZ9X5C7AnVPj73QYIN:PKY779wYAlbCmZY6lazh+IZ9s0nxjm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Project Evrial Crack Crack [XakFor.Net].exe (PID: 3076)
INFO
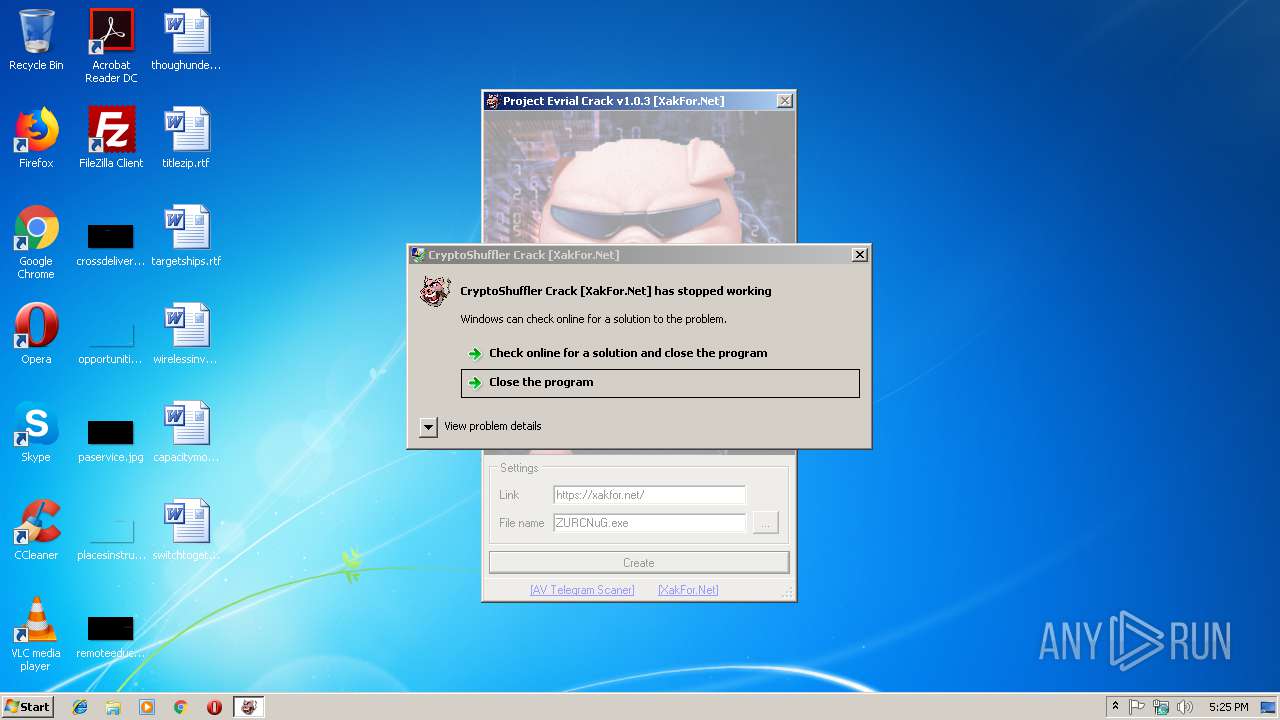
Application was crashed
- Project Evrial Crack Crack [XakFor.Net].exe (PID: 3076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:07 19:46:06+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 32256 |
| InitializedDataSize: | 842752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xda00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Microsoft |
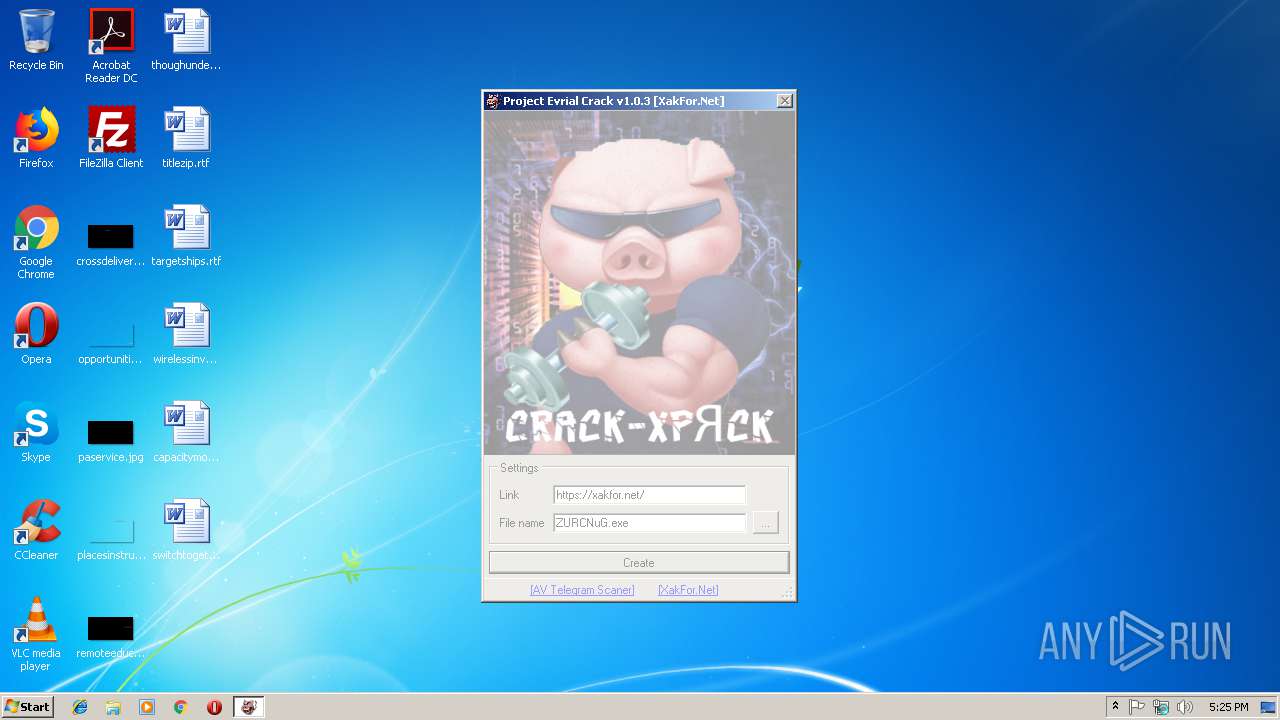
| FileDescription: | CryptoShuffler Crack [XakFor.Net] |
| FileVersion: | 1.0.0.0 |
| InternalName: | Project Evrial Crack Crack [XakFor.Net].exe |
| LegalCopyright: | Copyright © Microsoft 2018 |
| LegalTrademarks: | - |
| OriginalFileName: | Project Evrial Crack Crack [XakFor.Net].exe |
| ProductName: | CryptoShuffler Crack [XakFor.Net] |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Feb-2018 18:46:06 |
| Comments: | - |
| CompanyName: | Microsoft |
| FileDescription: | CryptoShuffler Crack [XakFor.Net] |
| FileVersion: | 1.0.0.0 |
| InternalName: | Project Evrial Crack Crack [XakFor.Net].exe |
| LegalCopyright: | Copyright © Microsoft 2018 |
| LegalTrademarks: | - |
| OriginalFilename: | Project Evrial Crack Crack [XakFor.Net].exe |
| ProductName: | CryptoShuffler Crack [XakFor.Net] |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 07-Feb-2018 18:46:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
#"NU38<`\xe0\xb8\x08 | 0x00002000 | 0x0008B8E0 | 0x0008BA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99965 |
.text | 0x0008E000 | 0x00007AC0 | 0x00007C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.30207 |
.rsrc | 0x00096000 | 0x00041F58 | 0x00042000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.90399 |
.reloc | 0x000D8000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0980042 |
0x000DA000 | 0x00000010 | 0x00000200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0.142636 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
32512 | 2.16096 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
32
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3076 | "C:\Users\admin\AppData\Local\Temp\Project Evrial Crack Crack [XakFor.Net].exe" | C:\Users\admin\AppData\Local\Temp\Project Evrial Crack Crack [XakFor.Net].exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: CryptoShuffler Crack [XakFor.Net] Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
653
Read events
609
Write events
41
Delete events
3
Modification events
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 2 |
Value: 500072006F006A006500630074002000450076007200690061006C00200043007200610063006B00200043007200610063006B0020005B00580061006B0046006F0072002E004E00650074005D002E006500780065000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000020000000700000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000020000000400000003000000FFFFFFFF | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0\0\1 |
| Operation: | write | Name: | MRUListEx |
Value: 00000000030000000200000001000000FFFFFFFF | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\39\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | 0 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D19002F433A5C000000000000000000000000000000000000007400310000000000454B314E1100557365727300600008000400EFBEEE3AA314454B314E2A0000005A01000000000100000000000000000036000000000055007300650072007300000040007300680065006C006C00330032002E0064006C006C002C002D0032003100380031003300000014004C003100000000001C4D9960100061646D696E00380008000400EFBE454B804A1C4D99602A0000002D000000000004000000000000000000000000000000610064006D0069006E00000014005200310000000000454B814A122041707044617461003C0008000400EFBE454B814A454B814A2A0000007C0100000000020000000000000000000000000000004100700070004400610074006100000016004C00310000000000294D987B10204C6F63616C00380008000400EFBE454B814A294D987B2A0000008F0100000000020000000000000000000000000000004C006F00630061006C00000014004A003100000000002B4E108B102054656D700000360008000400EFBE454B814A2B4E108B2A00000090010000000002000000000000000000000000000000540065006D007000000014005600320000000000000000008000536869742E65786500003E0008000400EFBE00000000000000002A0000000000000000000000000000000000000000000000000053006800690074002E00650078006500000018000000 | |||
| (PID) Process: | (3076) Project Evrial Crack Crack [XakFor.Net].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
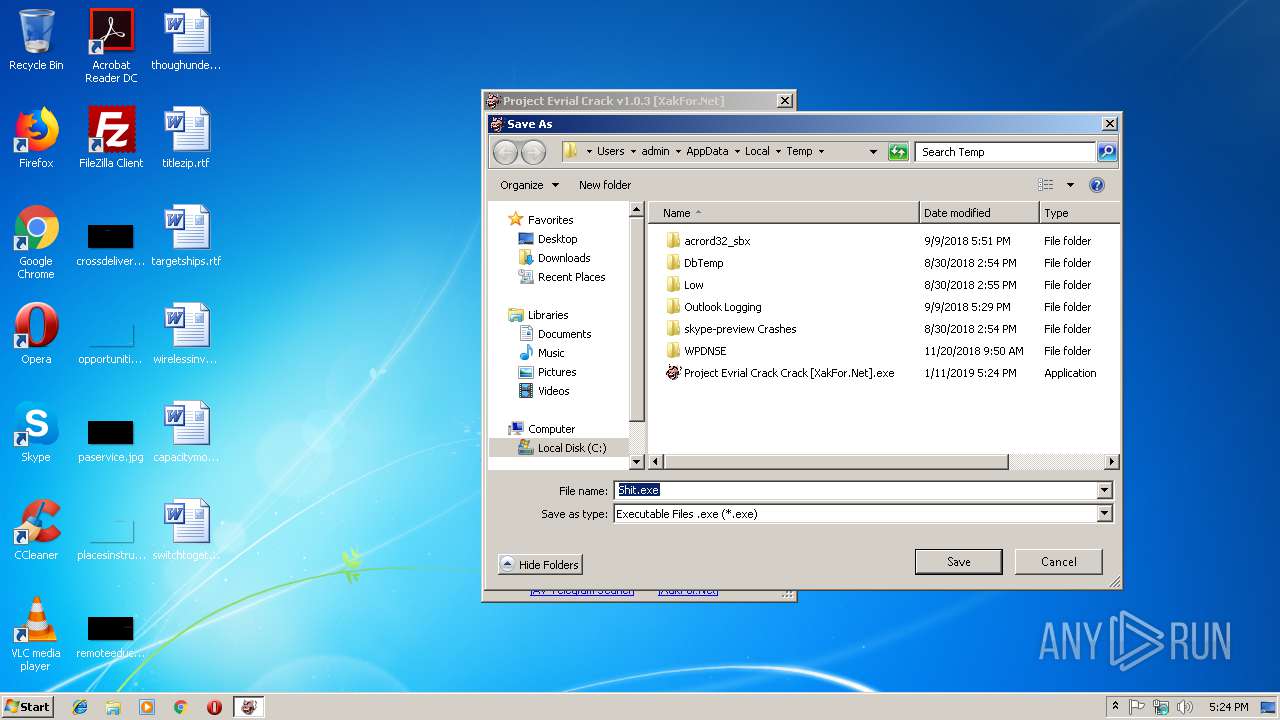
| 3076 | Project Evrial Crack Crack [XakFor.Net].exe | C:\Users\admin\AppData\Local\Temp\stub.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report