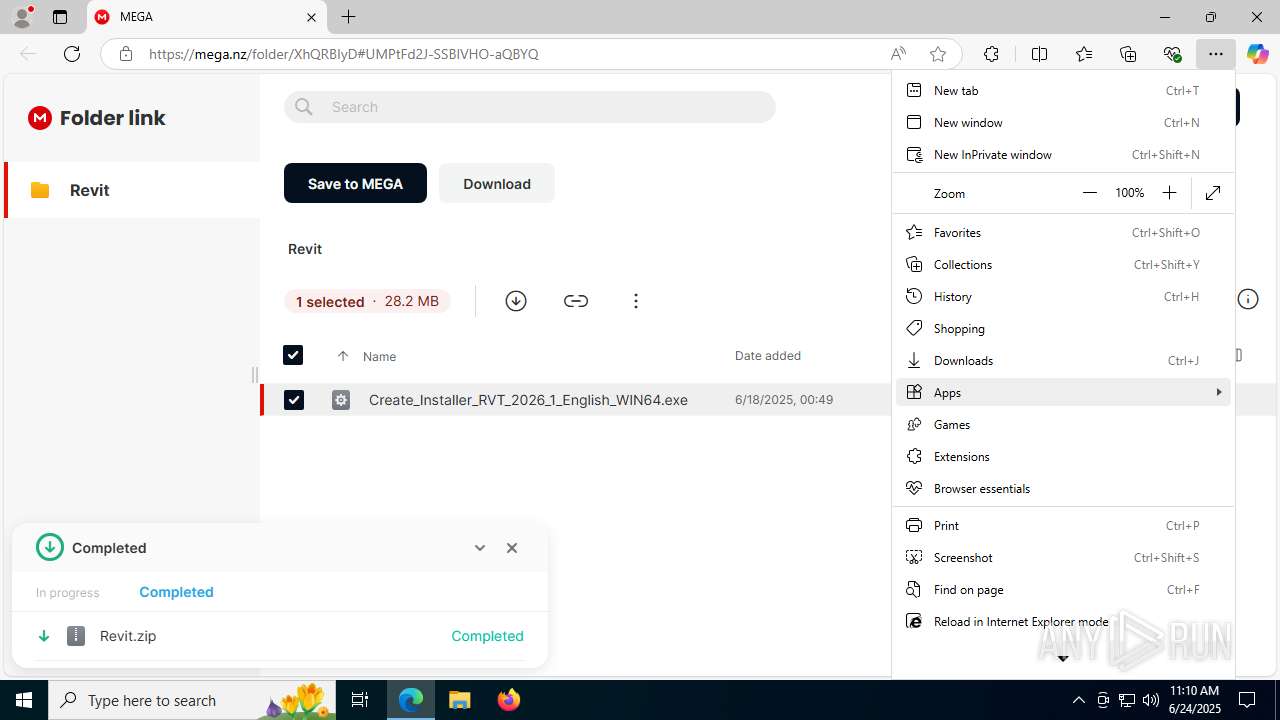
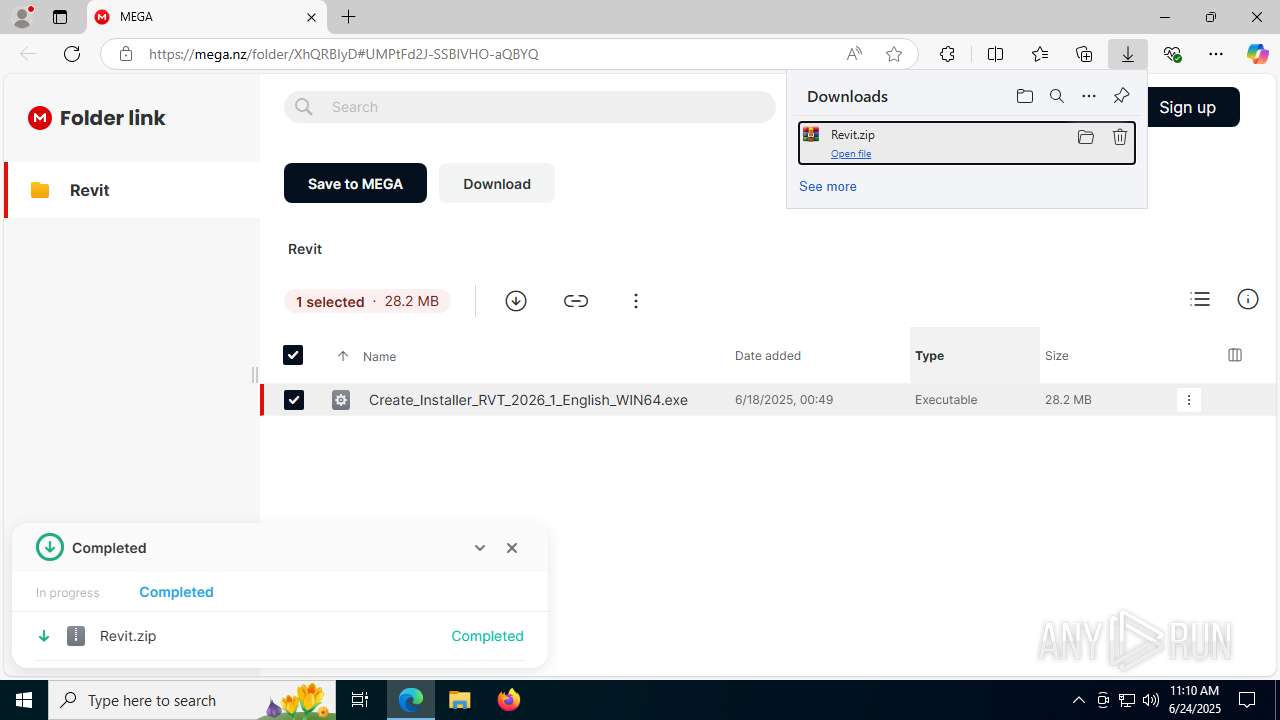
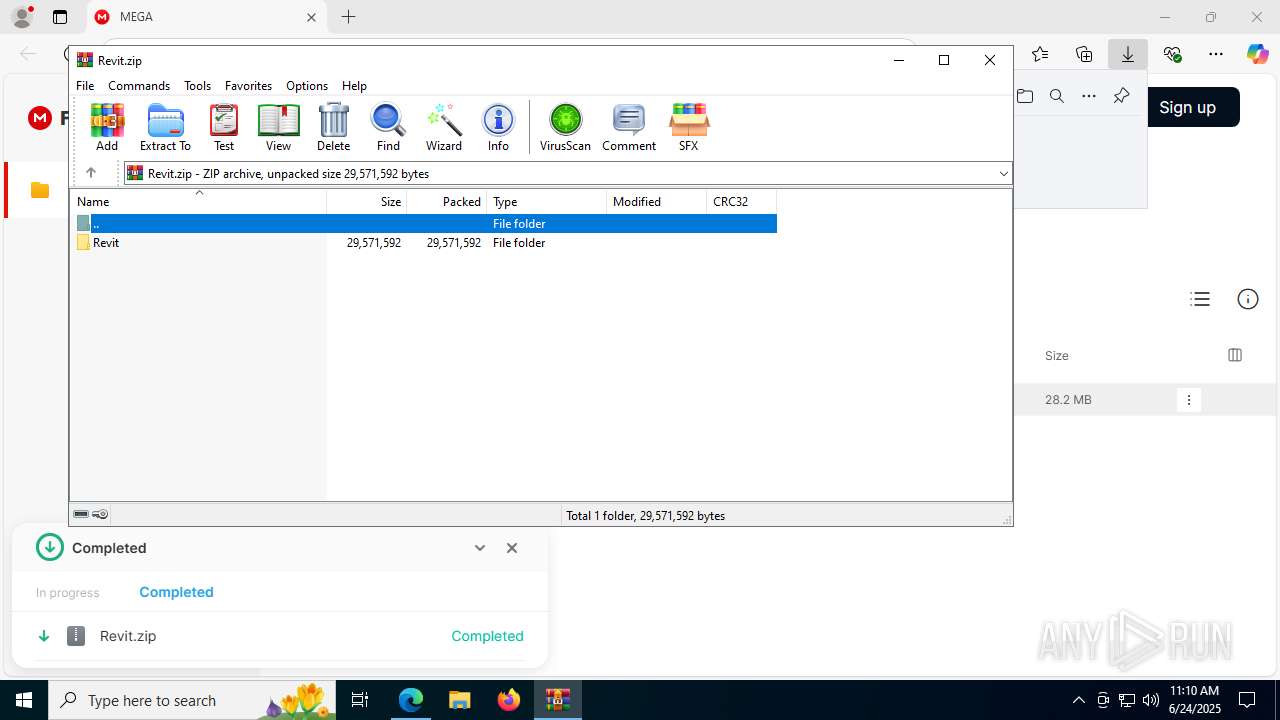
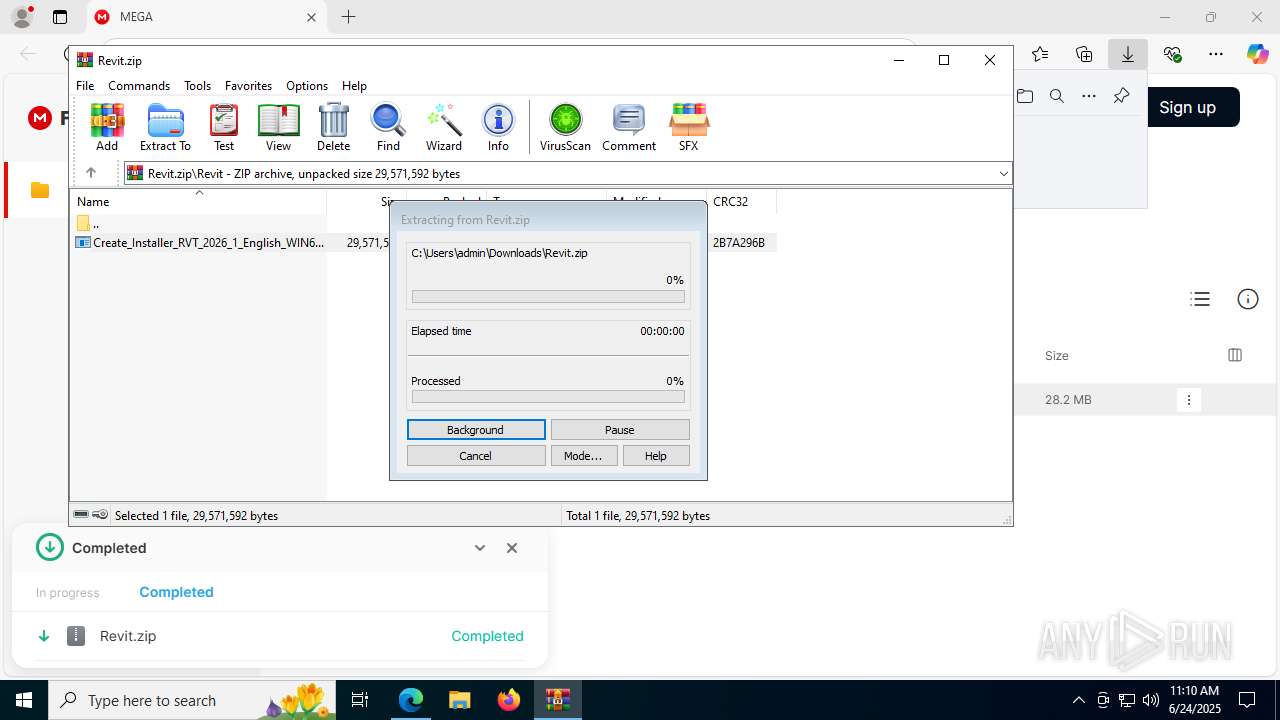
| URL: | https://mega.nz/folder/XhQRBIyD#UMPtFd2J-SSBlVHO-aQBYQ |
| Full analysis: | https://app.any.run/tasks/2cca7a51-9b57-44be-83ef-66852a85e8e1 |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2025, 11:09:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C2C002A02FD0318E554445F73CD317C3 |
| SHA1: | EA9E8F6813C8CFFE12AD039A14CA0632DD3F989E |
| SHA256: | EE49DF24BEA4E826CE2666C73EE547D7D81BDACF26DEF279C713EE753A82792C |
| SSDEEP: | 3:N8X/iuyKvKno7/I22Jztq5el:26To7A/Bn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8056)
- AdOdisDeployTool.exe (PID: 5920)
- ADPClientService.exe (PID: 5612)
- DownloadManager.exe (PID: 3624)
Executable content was dropped or overwritten
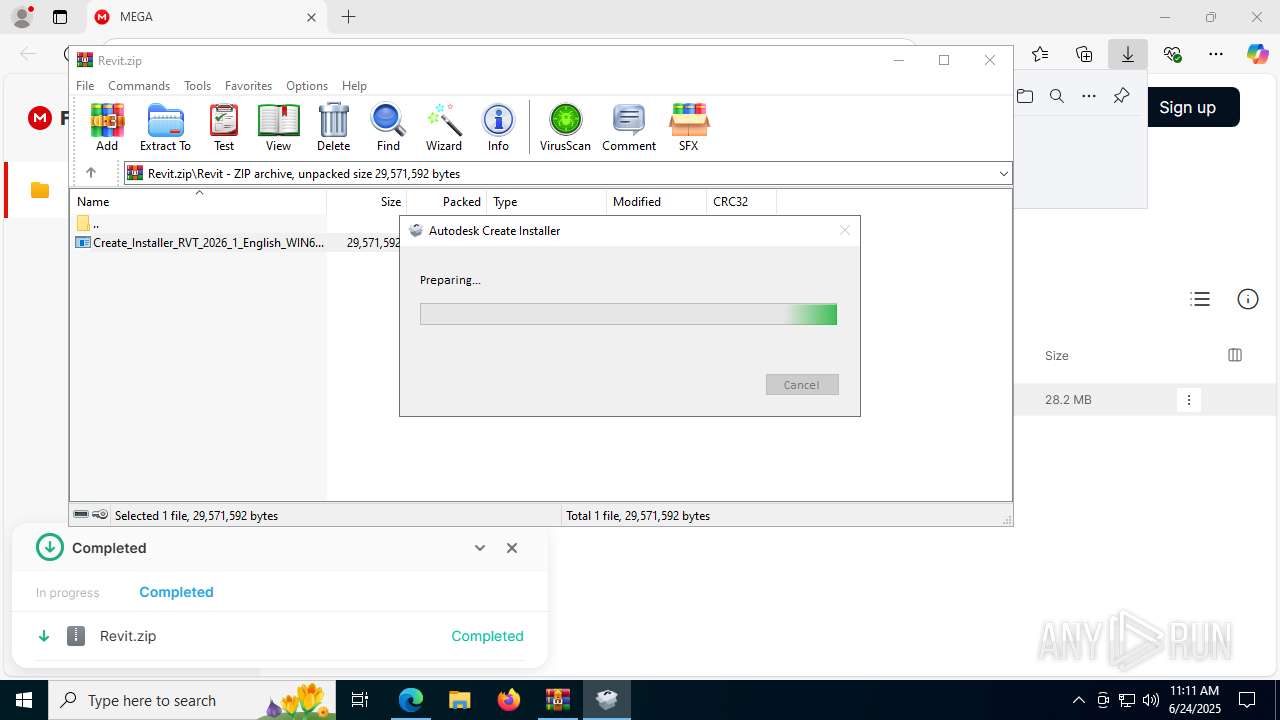
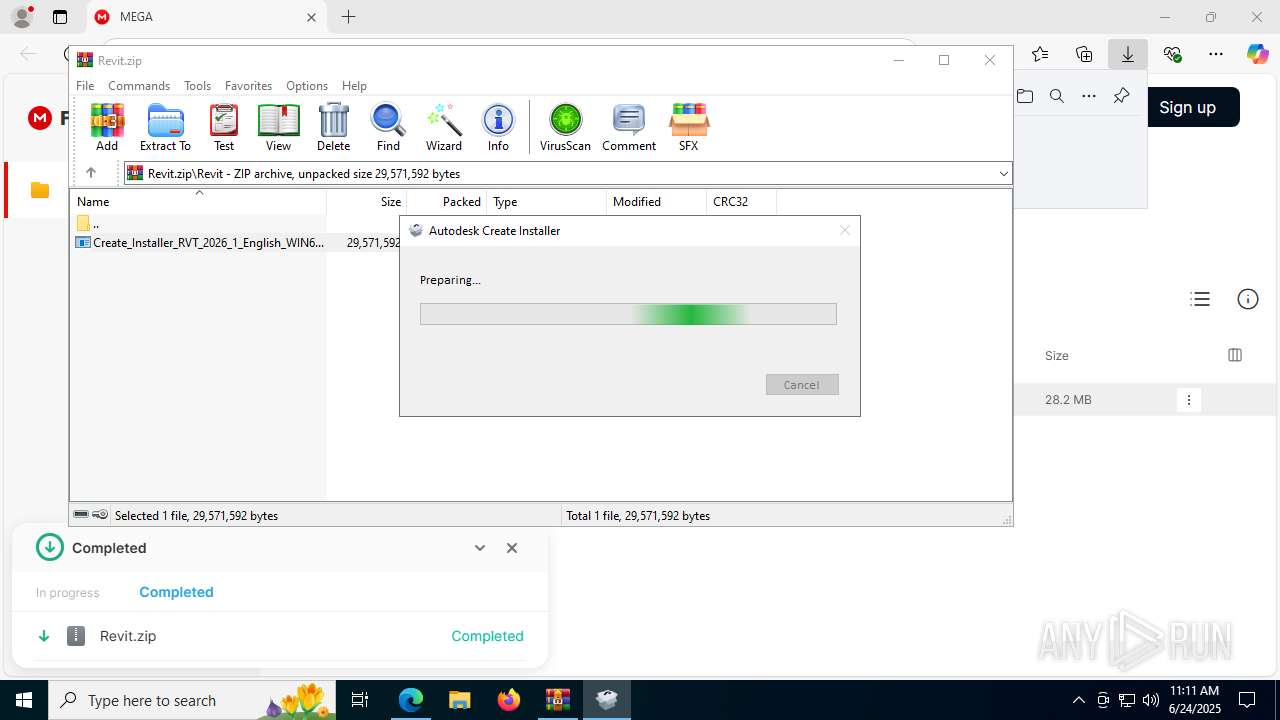
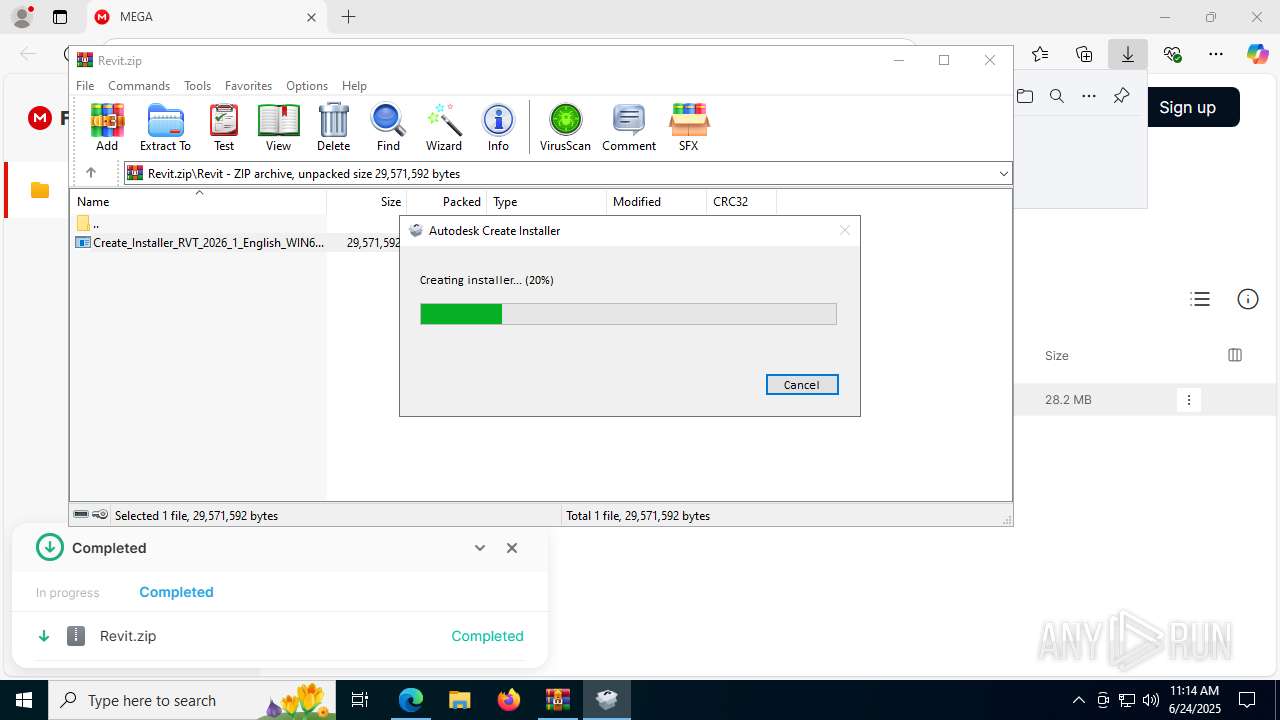
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
- 7za.exe (PID: 4044)
- 7za.exe (PID: 1740)
- 7za.exe (PID: 188)
Drops 7-zip archiver for unpacking
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
The process drops C-runtime libraries
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
Process drops legitimate windows executable
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
The process checks if it is being run in the virtual environment
- DownloadManager.exe (PID: 3624)
There is functionality for taking screenshot (YARA)
- AdOdisDeployTool.exe (PID: 5920)
INFO
Application launched itself
- msedge.exe (PID: 5808)
The sample compiled with english language support
- msedge.exe (PID: 5808)
- WinRAR.exe (PID: 8056)
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
- 7za.exe (PID: 4044)
- 7za.exe (PID: 7736)
- 7za.exe (PID: 188)
Reads the computer name
- identity_helper.exe (PID: 7508)
- identity_helper.exe (PID: 7820)
- upi.exe (PID: 7556)
- AdOdisDeployTool.exe (PID: 5920)
- DownloadManager.exe (PID: 3624)
- upi.exe (PID: 188)
- ADPClientService.exe (PID: 5612)
- 7za.exe (PID: 6492)
- 7za.exe (PID: 7240)
- 7za.exe (PID: 4324)
- 7za.exe (PID: 6320)
- 7za.exe (PID: 7292)
- 7za.exe (PID: 1208)
- 7za.exe (PID: 7500)
- 7za.exe (PID: 4044)
- 7za.exe (PID: 7220)
- 7za.exe (PID: 7508)
- 7za.exe (PID: 1740)
- 7za.exe (PID: 3900)
- 7za.exe (PID: 7736)
- 7za.exe (PID: 188)
- 7za.exe (PID: 3540)
- 7za.exe (PID: 3400)
- 7za.exe (PID: 6404)
- 7za.exe (PID: 6308)
- 7za.exe (PID: 1800)
- 7za.exe (PID: 7420)
- 7za.exe (PID: 7764)
- 7za.exe (PID: 5768)
- 7za.exe (PID: 8184)
- 7za.exe (PID: 8160)
- 7za.exe (PID: 7432)
- 7za.exe (PID: 2368)
- 7za.exe (PID: 7556)
- 7za.exe (PID: 5172)
- 7za.exe (PID: 6756)
- 7za.exe (PID: 7712)
- 7za.exe (PID: 5132)
- 7za.exe (PID: 8072)
Checks supported languages
- identity_helper.exe (PID: 7508)
- identity_helper.exe (PID: 7820)
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
- AdOdisDeployTool.exe (PID: 5920)
- upi.exe (PID: 7556)
- upi.exe (PID: 304)
- DownloadManager.exe (PID: 3624)
- upi.exe (PID: 7940)
- 7za.exe (PID: 4044)
- 7za.exe (PID: 6492)
- ADPClientService.exe (PID: 5612)
- upi.exe (PID: 188)
- 7za.exe (PID: 6320)
- 7za.exe (PID: 7220)
- 7za.exe (PID: 7240)
- 7za.exe (PID: 7292)
- 7za.exe (PID: 4324)
- 7za.exe (PID: 1208)
- 7za.exe (PID: 3400)
- 7za.exe (PID: 7500)
- 7za.exe (PID: 7508)
- 7za.exe (PID: 1740)
- 7za.exe (PID: 3900)
- 7za.exe (PID: 7736)
- 7za.exe (PID: 188)
- 7za.exe (PID: 3540)
- 7za.exe (PID: 7420)
- 7za.exe (PID: 6308)
- 7za.exe (PID: 6404)
- 7za.exe (PID: 5768)
- 7za.exe (PID: 7764)
- 7za.exe (PID: 1800)
- 7za.exe (PID: 8184)
- 7za.exe (PID: 8160)
- 7za.exe (PID: 7432)
- 7za.exe (PID: 2368)
- 7za.exe (PID: 7556)
- 7za.exe (PID: 5172)
- 7za.exe (PID: 8072)
- 7za.exe (PID: 6756)
- 7za.exe (PID: 7712)
- 7za.exe (PID: 5132)
Launching a file from the Downloads directory
- msedge.exe (PID: 5808)
Reads Environment values
- identity_helper.exe (PID: 7508)
- identity_helper.exe (PID: 7820)
Reads Microsoft Office registry keys
- msedge.exe (PID: 5808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8056)
Create files in a temporary directory
- Create_Installer_RVT_2026_1_English_WIN64.exe (PID: 424)
- upi.exe (PID: 7556)
- upi.exe (PID: 304)
- AdOdisDeployTool.exe (PID: 5920)
- upi.exe (PID: 188)
- DownloadManager.exe (PID: 3624)
- ADPClientService.exe (PID: 5612)
- upi.exe (PID: 7940)
Creates files or folders in the user directory
- upi.exe (PID: 7556)
- AdOdisDeployTool.exe (PID: 5920)
- DownloadManager.exe (PID: 3624)
- ADPClientService.exe (PID: 5612)
Reads the software policy settings
- AdOdisDeployTool.exe (PID: 5920)
- DownloadManager.exe (PID: 3624)
- slui.exe (PID: 4500)
Checks proxy server information
- AdOdisDeployTool.exe (PID: 5920)
- DownloadManager.exe (PID: 3624)
- slui.exe (PID: 4500)
Creates files in the program directory
- AdOdisDeployTool.exe (PID: 5920)
Reads the machine GUID from the registry
- DownloadManager.exe (PID: 3624)
- AdOdisDeployTool.exe (PID: 5920)
Reads Windows Product ID
- ADPClientService.exe (PID: 5612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
232
Monitored processes
84
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\CER\CER\upi.exe" --cmd=get-device-id C:\Users\admin\AppData\Local\Temp\upi_deviceid2 | C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\CER\CER\upi.exe | — | DownloadManager.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Autodesk Upi Exit code: 0 Version: 7.1.8.876 Modules
| |||||||||||||||
| 188 | "C:\Users\admin\AppData\Local\Temp\7zSD793.tmp/7za.exe" x -ttar -si -aoa -bsp2 -o"C:\Users\admin\Downloads/Autodesk\Revit 2026 - (EN)\image\RVT_2026_en-US" | C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\7za.exe | DownloadManager.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 304 | "C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\CER\CER\upi.exe" C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\CER\upiconfig.xml C:\Users\admin\AppData\Local\Temp\upi_info.xml | C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\CER\CER\upi.exe | — | AdOdisDeployTool.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Autodesk Upi Exit code: 0 Version: 7.1.8.876 Modules
| |||||||||||||||
| 424 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.23783\Revit\Create_Installer_RVT_2026_1_English_WIN64.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8056.23783\Revit\Create_Installer_RVT_2026_1_English_WIN64.exe | WinRAR.exe | ||||||||||||
User: admin Company: Autodesk Integrity Level: HIGH Description: Autodesk Create Installer Version: 19.00 Modules
| |||||||||||||||
| 760 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5880,i,5315695111535456285,3389086131839936575,262144 --variations-seed-version --mojo-platform-channel-handle=6272 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7872,i,5315695111535456285,3389086131839936575,262144 --variations-seed-version --mojo-platform-channel-handle=5892 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1208 | "C:\Users\admin\AppData\Local\Temp\7zSD793.tmp/7za.exe" x -ttar -si -aoa -bsp2 -o"C:\Users\admin\Downloads/Autodesk\Revit 2026 - (EN)\image\RVT_2026_en-US" | C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\7za.exe | — | DownloadManager.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 1216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=1492,i,5315695111535456285,3389086131839936575,262144 --variations-seed-version --mojo-platform-channel-handle=7480 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --always-read-main-dll --field-trial-handle=7008,i,5315695111535456285,3389086131839936575,262144 --variations-seed-version --mojo-platform-channel-handle=6876 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\AppData\Local\Temp\7zSD793.tmp/7za.exe" x -ttar -si -aoa -bsp2 -o"C:\Users\admin\Downloads/Autodesk\Revit 2026 - (EN)\image\RVT_2026_en-US" | C:\Users\admin\AppData\Local\Temp\7zSD793.tmp\7za.exe | DownloadManager.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
Total events
27 832
Read events
27 792
Write events
40
Delete events
0
Modification events
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {99E8E058-A7A5-4820-B067-6D8D0703F801} | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {538C07C5-B399-49A0-8C27-CCB2D3FAB337} | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8F0EE2A6E5962F00 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FC4F7EC1-619F-41E4-BEA1-ED33B498FA3D} | |||
Executable files
32
Suspicious files
515
Text files
200
Unknown types
91
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1757d4.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1757d4.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1757e4.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1757e4.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1757f3.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
764
DNS requests
104
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1984 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:J7Ucri9D-mgQSd-nKJ9aiEu2GuJQ-K-zF-KUTzCXfVY&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1700 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7920 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7920 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5920 | AdOdisDeployTool.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5920 | AdOdisDeployTool.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
5920 | AdOdisDeployTool.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAeptFiyZgHlRihbErle10o%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 18.173.189.168:80 | http://ocsp.rootca3.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRkNawYMzz%2BjKSfYbTyFR0AXuhs6QQUq7bb1waeN6wwhgeRcMecxBmxeMACEwdzEnA9eVH9TrLXPKuCavuqCA0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5876 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1984 | msedge.exe | 31.216.145.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | whitelisted |
1984 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1984 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1984 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1984 | msedge.exe | 2.16.204.153:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
mega.nz |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
eu.static.mega.co.nz |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
g.api.mega.co.nz |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
1984 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
Process | Message |
|---|---|
AdOdisDeployTool.exe | QLayout: Attempting to add QLayout "" to AppDialog "", which already has a layout
|