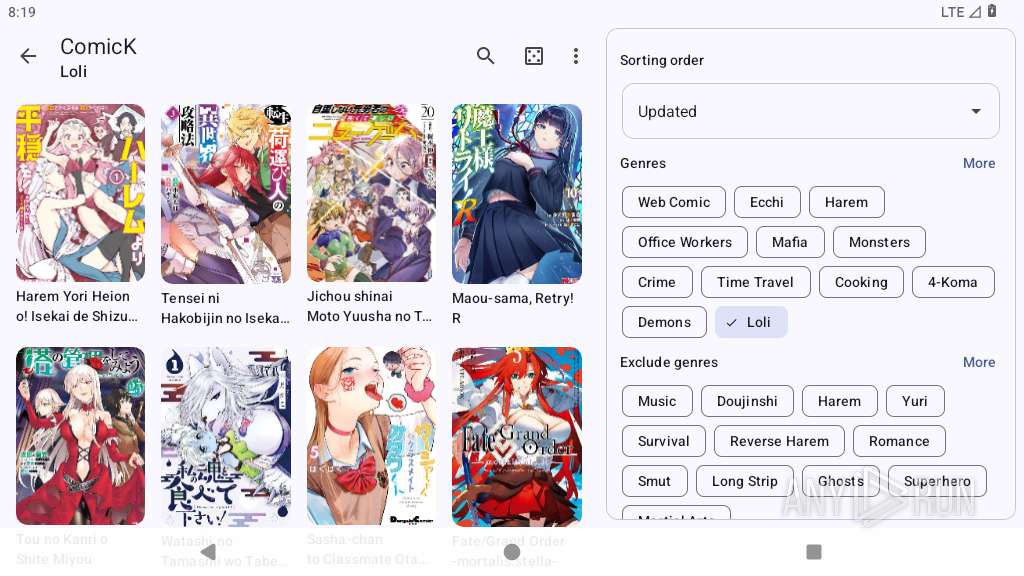
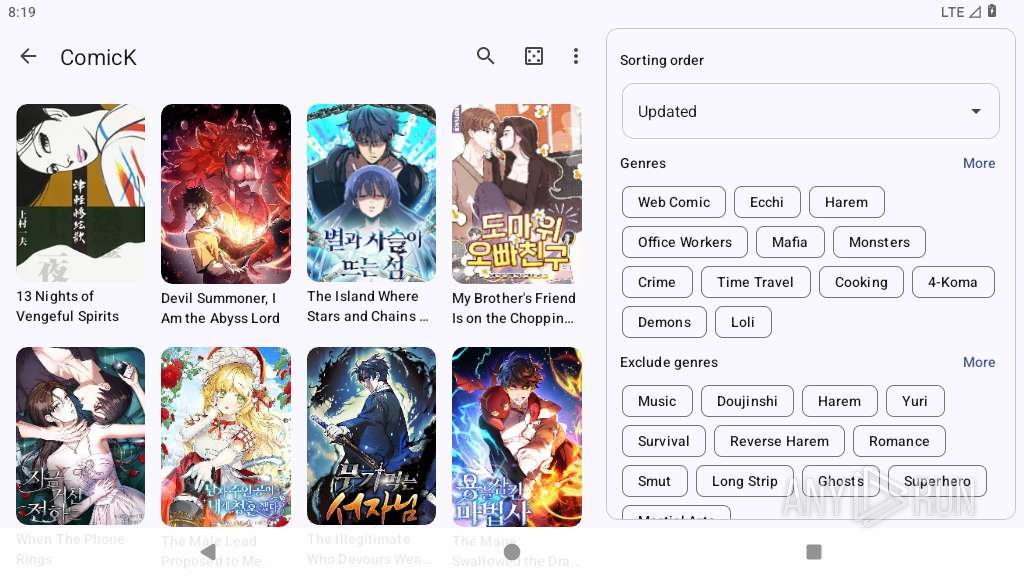
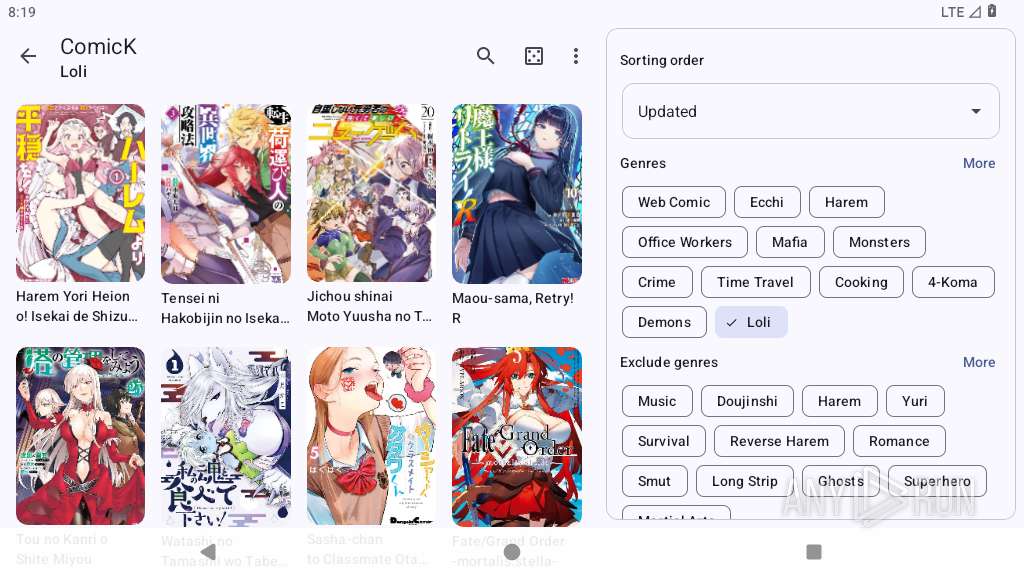
| File name: | kotatsu-9.0.1-release.apk |
| Full analysis: | https://app.any.run/tasks/a0f47130-c53e-4497-92c2-ca37e3333b1f |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2025, 08:17:21 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with gradle app-metadata.properties |
| MD5: | D0819FFE656C222703AC5272944B90F5 |
| SHA1: | 284FF25E3E90BEE279B33CCAF9D6AD675F1E8E26 |
| SHA256: | EE48ADB781119E123C02CEF7C356A44ED687C93C2D02CBB05F465F9F9E421F64 |
| SSDEEP: | 98304:v0LMeXxEbPDCm0SrVcz8X51p0YLNDMj04ONmj85hITctU1K44Nz+Iis1ouwT1U7l:L3oVM1ApSc0pkvcmMlbE5rUw4gSe+ |
MALICIOUS
Executes system commands or scripts
- app_process64 (PID: 2298)
SUSPICIOUS
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2298)
Launches a new activity
- app_process64 (PID: 2298)
Gets data of saved accounts
- app_process64 (PID: 2298)
Starts a service
- app_process64 (PID: 2298)
Accesses system-level resources
- app_process64 (PID: 2298)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2298)
INFO
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2298)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2298)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2298)
Verifies whether the device is connected to the internet
- app_process64 (PID: 2298)
Returns elapsed time since boot
- app_process64 (PID: 2298)
Gets file name without full path
- app_process64 (PID: 2298)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.8) |
|---|---|---|
| .jar | | | Java Archive (17.3) |
| .vym | | | VYM Mind Map (14.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | - |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1981:01:01 01:01:02 |
| ZipCRC: | 0x555cf04c |
| ZipCompressedSize: | 52 |
| ZipUncompressedSize: | 57 |
| ZipFileName: | META-INF/com/android/build/gradle/app-metadata.properties |
Total processes
130
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 339 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2298 | org.koitharu.kotatsu | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2348 | com.android.webview:webview_service | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2375 | getprop ro.miui.ui.version.name | /system/bin/toolbox | — | app_process64 |
User: u0_a108 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2486 | webview_zygote | /system/bin/app_process64 | — | app_process64 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2522 | <pre-initialized> | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
72
Text files
299
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2298 | app_process64 | /data/data/org.koitharu.kotatsu/no_backup/androidx.work.workdb-journal | binary | |
MD5:— | SHA256:— | |||
| 2298 | app_process64 | /data/data/org.koitharu.kotatsu/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2298 | app_process64 | /data/data/org.koitharu.kotatsu/databases/kotatsu-db-journal | binary | |
MD5:— | SHA256:— | |||
| 2298 | app_process64 | /data/data/org.koitharu.kotatsu/cache/oat_primary/arm64/base.2298.tmp | binary | |
MD5:— | SHA256:— | |||
| 2298 | app_process64 | /data/data/org.koitharu.kotatsu/shared_prefs/WebViewChromiumPrefs.xml | xml | |
MD5:— | SHA256:— | |||
| 2298 | app_process64 | /data/data/org.koitharu.kotatsu/shared_prefs/org.koitharu.kotatsu_preferences.xml | xml | |
MD5:— | SHA256:— | |||
| 2375 | toolbox | /data/data/org.koitharu.kotatsu/no_backup/androidx.work.workdb | binary | |
MD5:— | SHA256:— | |||
| 2375 | toolbox | /data/data/org.koitharu.kotatsu/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2375 | toolbox | /data/data/org.koitharu.kotatsu/no_backup/androidx.work.workdb-shm | binary | |
MD5:— | SHA256:— | |||
| 2375 | toolbox | /data/data/org.koitharu.kotatsu/databases/kotatsu-db-wal | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
69
DNS requests
51
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2298 | app_process64 | GET | 403 | 172.67.96.148:80 | http://es.ninemanga.com/ | unknown | — | — | whitelisted |
— | — | GET | 204 | 142.250.185.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
445 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.67:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.27.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
1793 | app_process64 | 185.199.108.153:443 | kotatsu.app | FASTLY | US | shared |
2348 | app_process64 | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2298 | app_process64 | 140.82.121.6:443 | api.github.com | GITHUB | US | whitelisted |
2298 | app_process64 | 94.102.49.153:443 | bato.to | IP Volume inc | NL | whitelisted |
2522 | app_process64 | 142.250.186.35:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
kotatsu.app |
| unknown |
clientservices.googleapis.com |
| whitelisted |
api.github.com |
| whitelisted |
bato.to |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
339 | netd | Potentially Bad Traffic | ET DNS Query for .to TLD |
339 | netd | Potentially Bad Traffic | ET DNS Query for .to TLD |
339 | netd | Potentially Bad Traffic | ET DNS Query for .to TLD |
339 | netd | Potentially Bad Traffic | ET DNS Query for .to TLD |
339 | netd | Potentially Bad Traffic | ET DNS Query for .cc TLD |