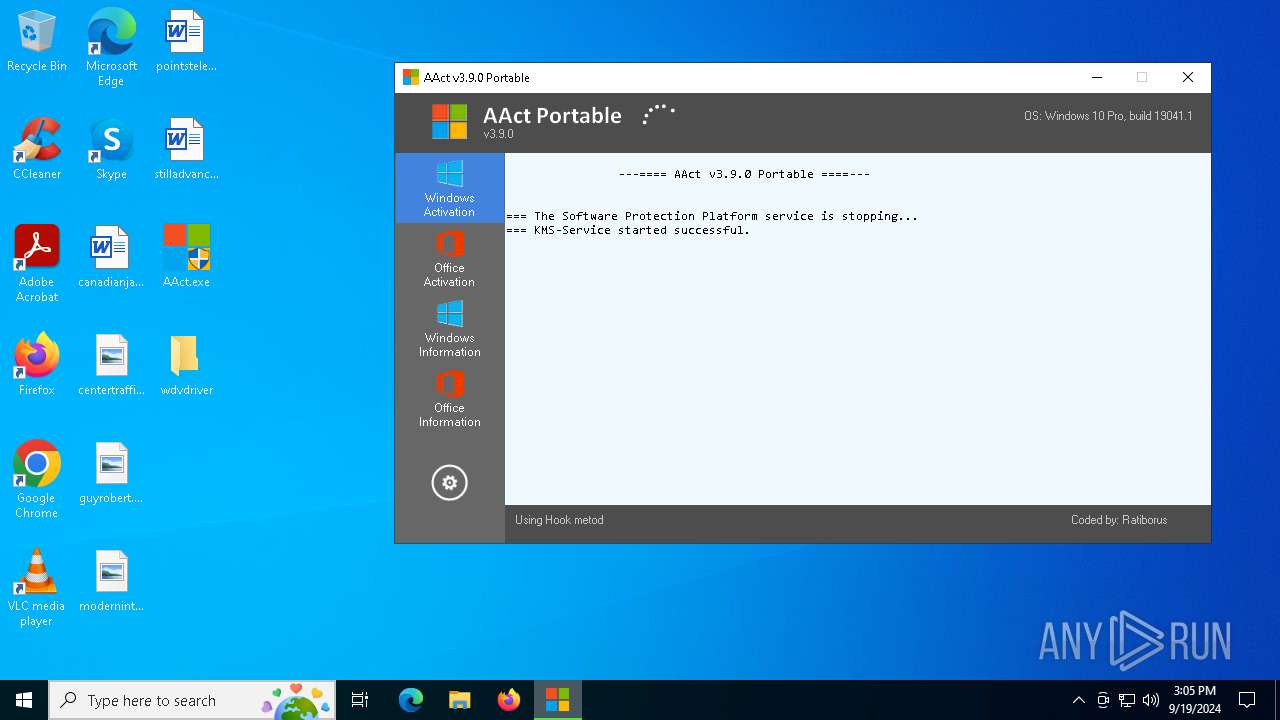
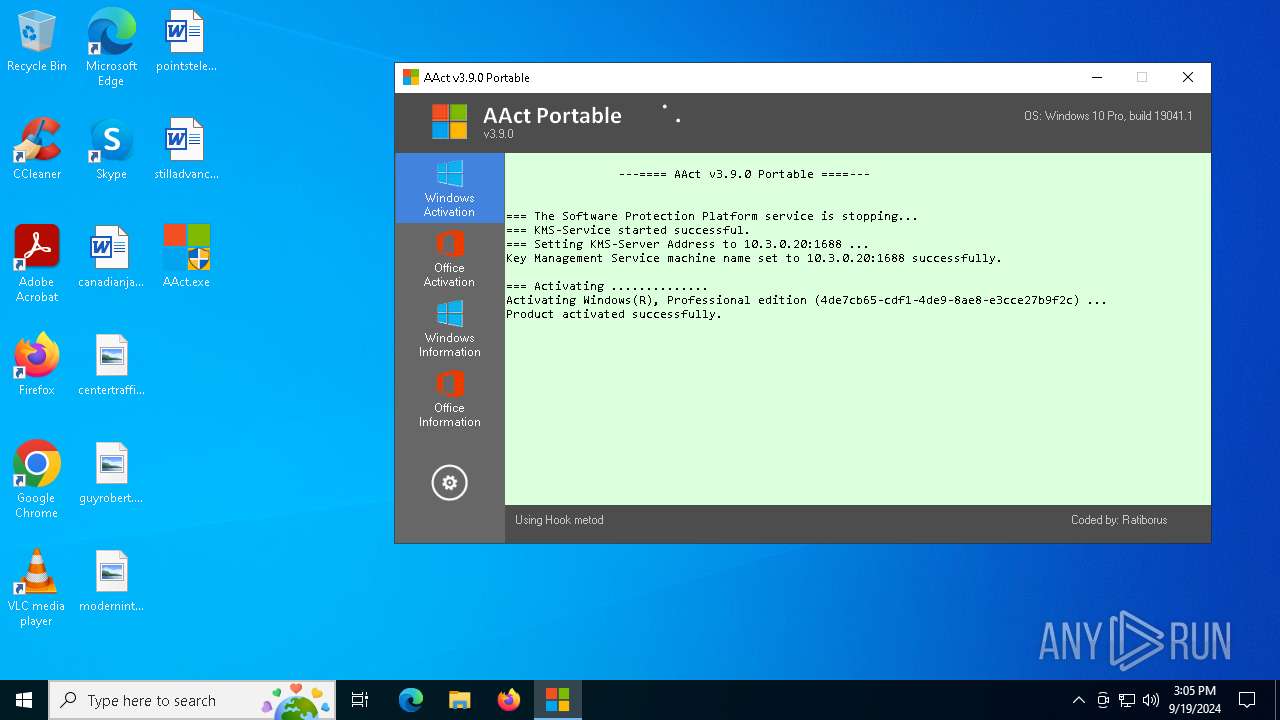
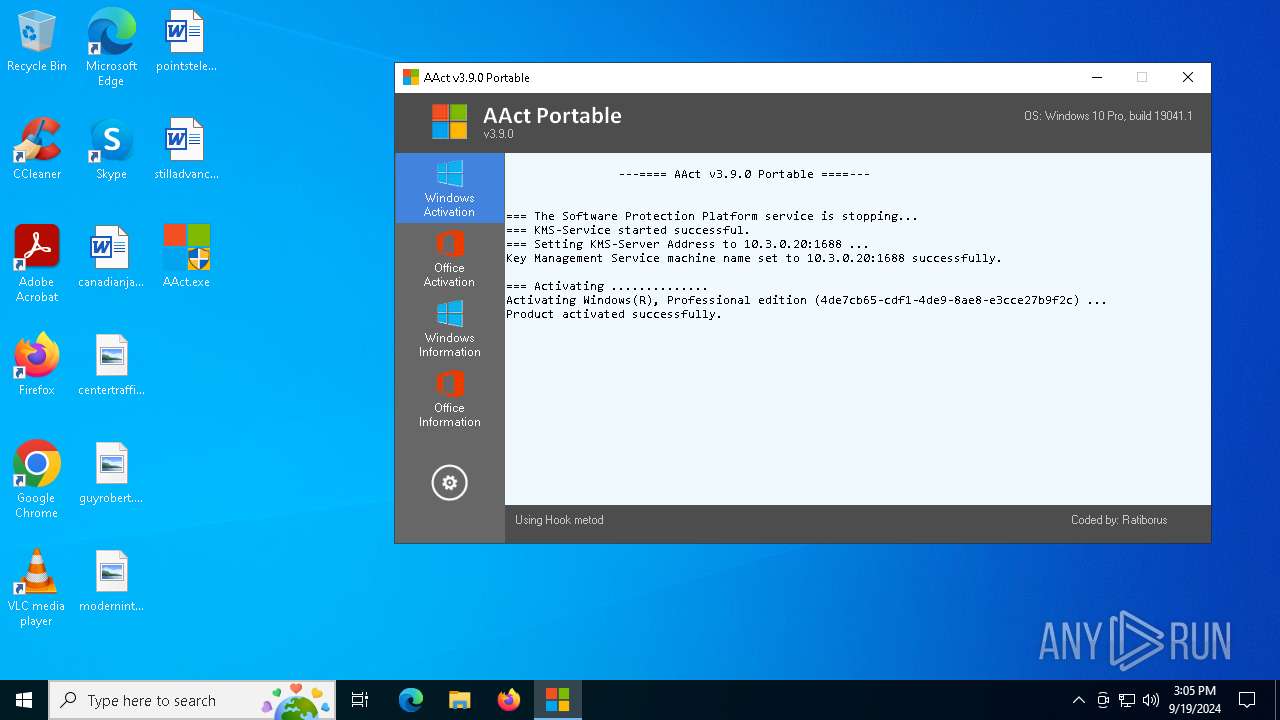
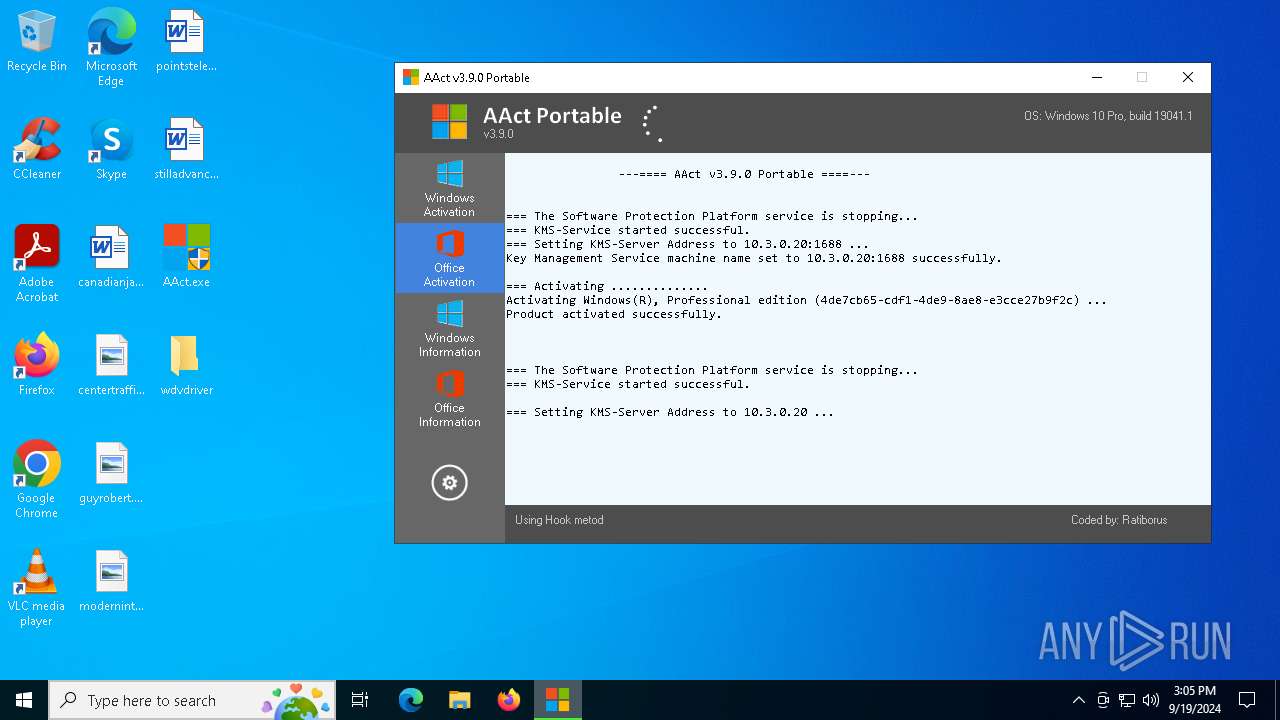
| File name: | AAct.exe |
| Full analysis: | https://app.any.run/tasks/388db31e-ed29-4c39-b509-ced60cc0cebd |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2024, 15:04:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 23465FCDEC49D71AFB6AF505DCFBC09F |
| SHA1: | FA7F58BF05FADAC32E77DB031C354FA7608D9709 |
| SHA256: | EE3A632FF9BF3324AE854DAEB820F65D5AF939EA29B55F2E61BFB1D01B270A65 |
| SSDEEP: | 49152:fF0dfWOyjwEufjEWrRYi+Jwdh1VnzC6BMkpkYMLVh/NkzS+xEAAtULsBYDIkjGEq:6eOyjwpEWr2itBzC6BRpc+txEAAgJycW |
MALICIOUS
Changes image file execution options
- reg.exe (PID: 6636)
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 5028)
- cscript.exe (PID: 6052)
- cscript.exe (PID: 4152)
- cscript.exe (PID: 6492)
Starts NET.EXE for service management
- cmd.exe (PID: 376)
- net.exe (PID: 1148)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6652)
- cmd.exe (PID: 4524)
- cmd.exe (PID: 964)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 360)
- AAct.exe (PID: 6696)
- cmd.exe (PID: 4604)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 6360)
- cmd.exe (PID: 6772)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 1940)
- cmd.exe (PID: 6288)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 1148)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 6956)
- cmd.exe (PID: 2572)
Starts SC.EXE for service management
- cmd.exe (PID: 4152)
- cmd.exe (PID: 6332)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 1940)
- cmd.exe (PID: 1940)
- cmd.exe (PID: 736)
- cmd.exe (PID: 2964)
Executable content was dropped or overwritten
- AAct.exe (PID: 6696)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1644)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 6424)
- cmd.exe (PID: 6284)
- cmd.exe (PID: 5736)
- cmd.exe (PID: 1948)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 1636)
Hides command output
- cmd.exe (PID: 4152)
- cmd.exe (PID: 6332)
Starts CMD.EXE for commands execution
- AAct.exe (PID: 6696)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 6332)
- cscript.exe (PID: 4528)
- cscript.exe (PID: 5028)
- cscript.exe (PID: 4152)
- cscript.exe (PID: 6052)
- cscript.exe (PID: 4540)
- cscript.exe (PID: 6492)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4528)
- cscript.exe (PID: 5028)
- cscript.exe (PID: 6332)
- cscript.exe (PID: 6052)
- cscript.exe (PID: 4152)
- cscript.exe (PID: 6492)
- cscript.exe (PID: 4540)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 4528)
- cscript.exe (PID: 6332)
- cscript.exe (PID: 5028)
- cscript.exe (PID: 4152)
- cscript.exe (PID: 6052)
- cscript.exe (PID: 4540)
- cscript.exe (PID: 6492)
The process executes VB scripts
- cmd.exe (PID: 1944)
- cmd.exe (PID: 6328)
- cmd.exe (PID: 6020)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 5540)
- cmd.exe (PID: 4476)
- cmd.exe (PID: 4732)
- cmd.exe (PID: 376)
- cmd.exe (PID: 2944)
- cmd.exe (PID: 1952)
- cmd.exe (PID: 5924)
Starts application with an unusual extension
- AAct.exe (PID: 6696)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 2772)
- cmd.exe (PID: 1952)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 6588)
INFO
UPX packer has been detected
- AAct.exe (PID: 6696)
Reads security settings of Internet Explorer
- cscript.exe (PID: 6332)
- cscript.exe (PID: 5028)
- cscript.exe (PID: 4528)
- cscript.exe (PID: 6052)
- cscript.exe (PID: 4152)
- cscript.exe (PID: 6492)
- cscript.exe (PID: 4540)
Checks supported languages
- AAct.dll (PID: 2264)
Reads the machine GUID from the registry
- AAct.dll (PID: 2264)
Reads the computer name
- AAct.dll (PID: 2264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.5) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:07:14 09:58:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 1400832 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | 1277952 |
| EntryPoint: | 0x28e040 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.9.0.0 |
| ProductVersionNumber: | 3.9.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | AAct x86 |
Total processes
280
Monitored processes
153
Malicious processes
8
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
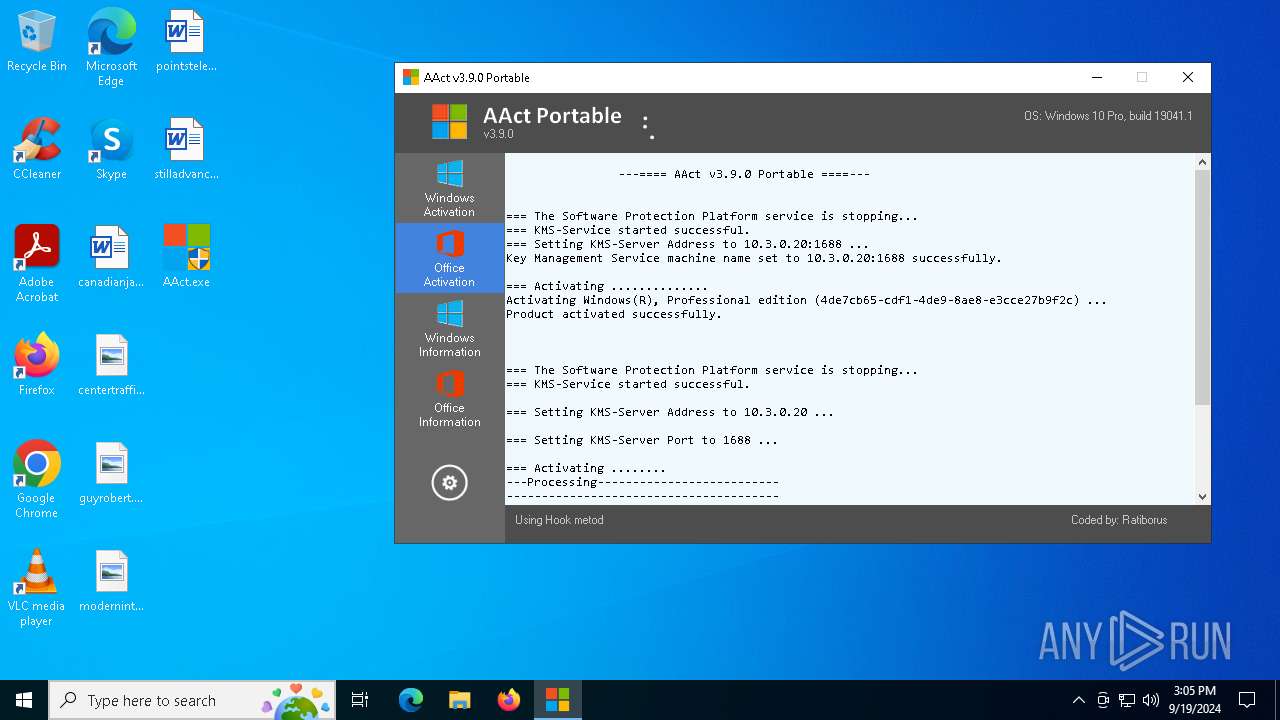
| 360 | "C:\WINDOWS\Sysnative\cmd.exe" /c reg.exe delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe" /f /v "Debugger" | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | "C:\WINDOWS\Sysnative\cmd.exe" /c net.exe stop sppsvc /y | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
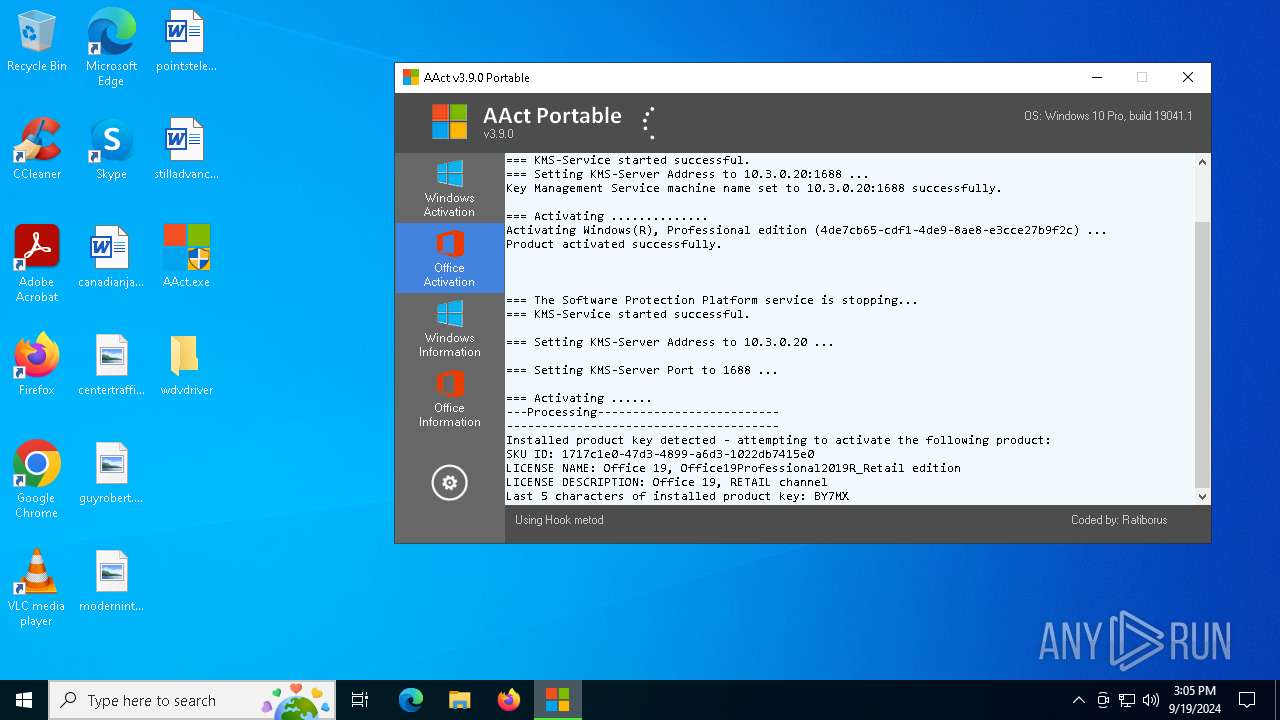
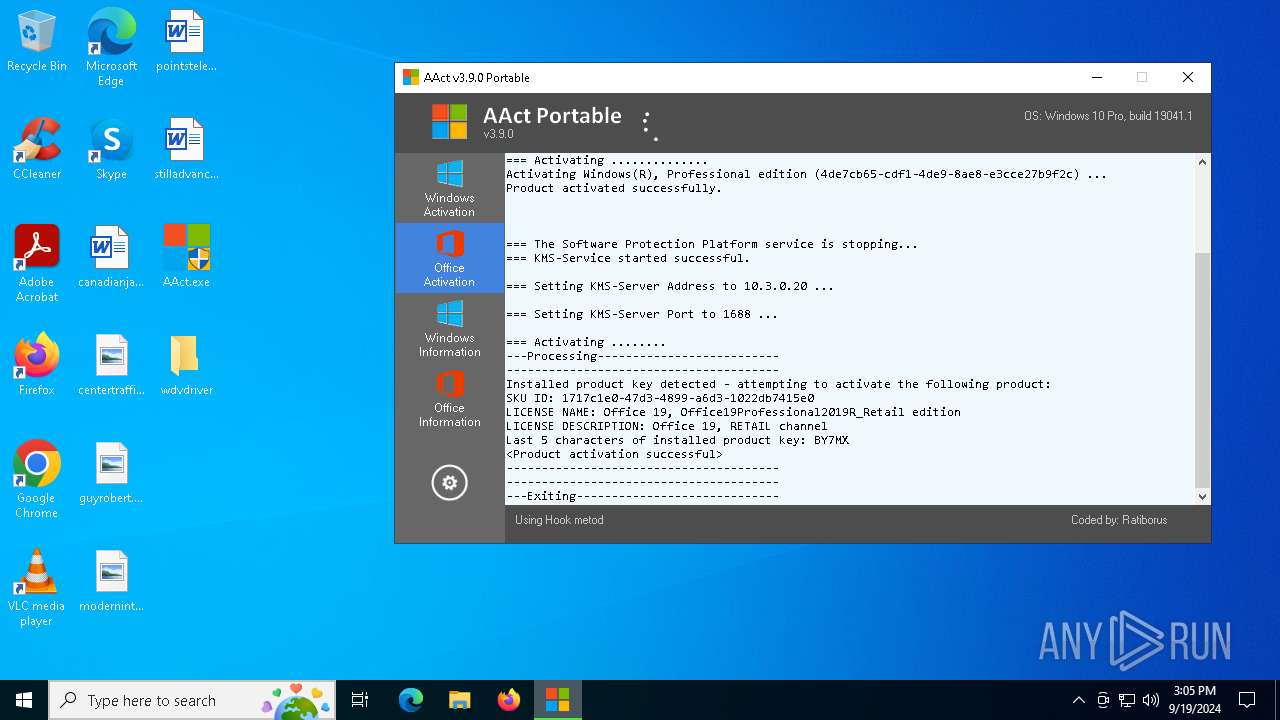
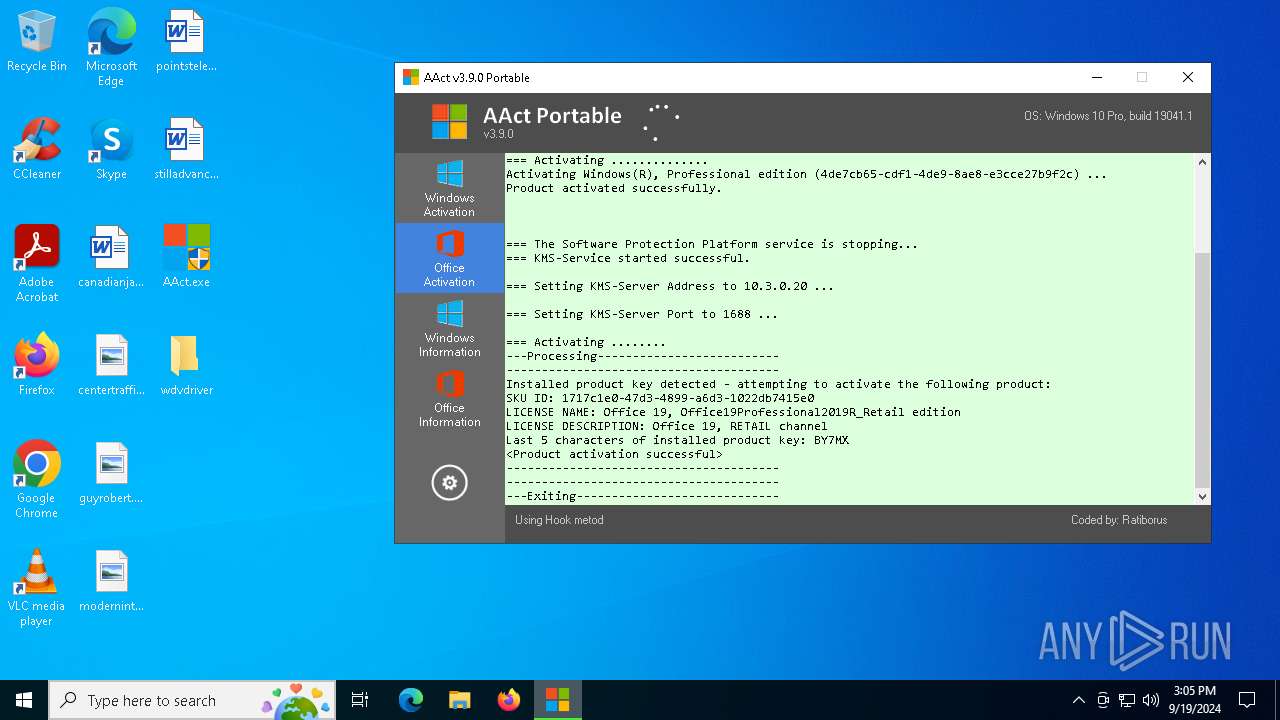
| 376 | "C:\WINDOWS\Sysnative\cmd.exe" /c cscript.exe "C:\Program Files\Microsoft Office\Office16\OSPP.VBS" //NoLogo /setprt:1688 | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\WINDOWS\Sysnative\cmd.exe" /c Netsh.exe Advfirewall Firewall delete rule name=0pen_Port_KMS protocol=TCP | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | reg.exe delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe" /f /v "Debugger" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | "C:\WINDOWS\Sysnative\cmd.exe" /c reg.exe delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe" /f | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 793
Read events
22 777
Write events
10
Delete events
6
Modification events
| (PID) Process: | (6636) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | Debugger |
Value: SppExtComObjPatcher.exe | |||
| (PID) Process: | (6588) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 0 | |||
| (PID) Process: | (1360) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | delete value | Name: | Debugger |
Value: SppExtComObjPatcher.exe | |||
| (PID) Process: | (4652) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | delete value | Name: | KMS_Emulation |
Value: | |||
| (PID) Process: | (1948) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6696) AAct.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: | |||
| (PID) Process: | (6696) AAct.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: | |||
| (PID) Process: | (6696) AAct.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (5400) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | Debugger |
Value: SppExtComObjPatcher.exe | |||
| (PID) Process: | (7108) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | KMS_Emulation |
Value: 0 | |||
Executable files
3
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6696 | AAct.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:E3281CD3A5293B962683B5AB4AD49309 | SHA256:26AE72400087F417ACCEDB8F68F1E7DF88A7B0B5904A17AC6FCB1D54E9B29980 | |||
| 6696 | AAct.exe | C:\Windows\System32\SppExtComObjPatcher.exe | executable | |
MD5:3D062A5923050F0885AA5E4882096744 | SHA256:68B536FB2A6A8C9A2B36E17EAD46343D156020C75C559ED068483ECF5BC3F060 | |||
| 1680 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:C7D1234376F3389D6C220F0DCF24341B | SHA256:F67F7E62B47D1C4D9059F9F01FF40D52044EE81F594C5B8C8925C254381061E5 | |||
| 1680 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:8B1B91C6848D6286221DC146C4D1BE97 | SHA256:1C86072097099DB23A73BCE044C6143F9FE53D19225F3F453A174ABDCFD8F905 | |||
| 6696 | AAct.exe | C:\Users\admin\Desktop\wdvdriver\AAct.dll | executable | |
MD5:124BA791D8C28151ABCD27D3D81E820B | SHA256:AFD72E00B8B6021CBD104D2CDF59FD9B58D245205D4E72E5D8BD8D75B88CCE48 | |||
| 1680 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:DDF4DE0DC1AC39C22F605957A1FE614B | SHA256:0ACF9791F2CBBF8330653DF8D90E760108DD7ED3B5DB03C4DE164BD5047E4D4A | |||
| 1680 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:202F9981C788E495E4734A8D97C38697 | SHA256:11E7765AAA8EB14E32FEAF0C66B88EA3DAF11DFA8CAD6CBD5B9602D146F687D7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
904 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2508 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2508 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1680 | cscript.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
1680 | cscript.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 52.191.219.104:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 52.191.219.104:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
904 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
904 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5816 | svchost.exe | 52.137.106.217:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5336 | SearchApp.exe | 52.168.117.174:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |