| File name: | Trojan.VBS.Bolbi.v2.vbs |
| Full analysis: | https://app.any.run/tasks/8262a060-e4c9-48f6-b43f-cb369e772058 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2019, 12:13:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 584F03161A17B36B2F5163DD85BC0B77 |
| SHA1: | 04DAD07D0146FF09C0DACC3F248DBDA16055A609 |
| SHA256: | EE2A2B418E82683DE196BEB5D4F6CB213E7579D783B06B9949F4A988F515B324 |
| SSDEEP: | 24576:gjSdueeKiZeXA940z802o5mNBriKgcdgUixQsUgk:gjSduKCeA2oqdJqfk |
MALICIOUS
Changes the autorun value in the registry
- wscript.exe (PID: 2664)
SUSPICIOUS
Application launched itself
- WScript.exe (PID: 2984)
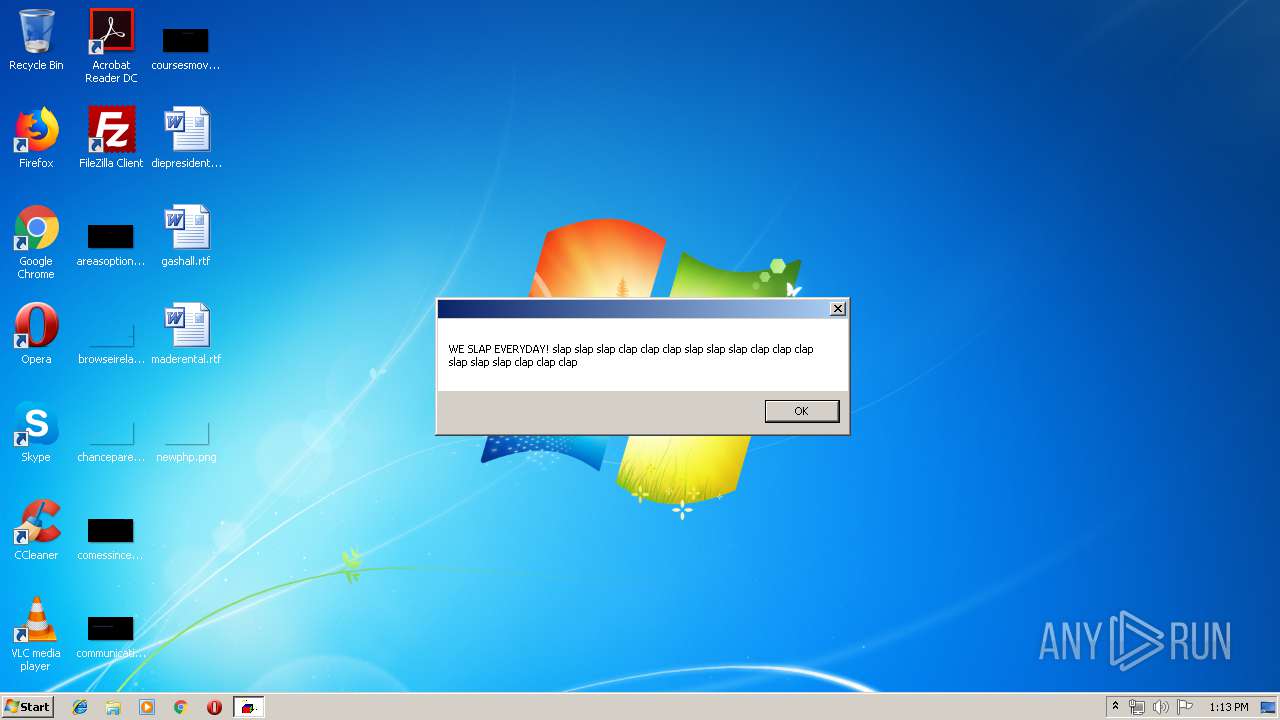
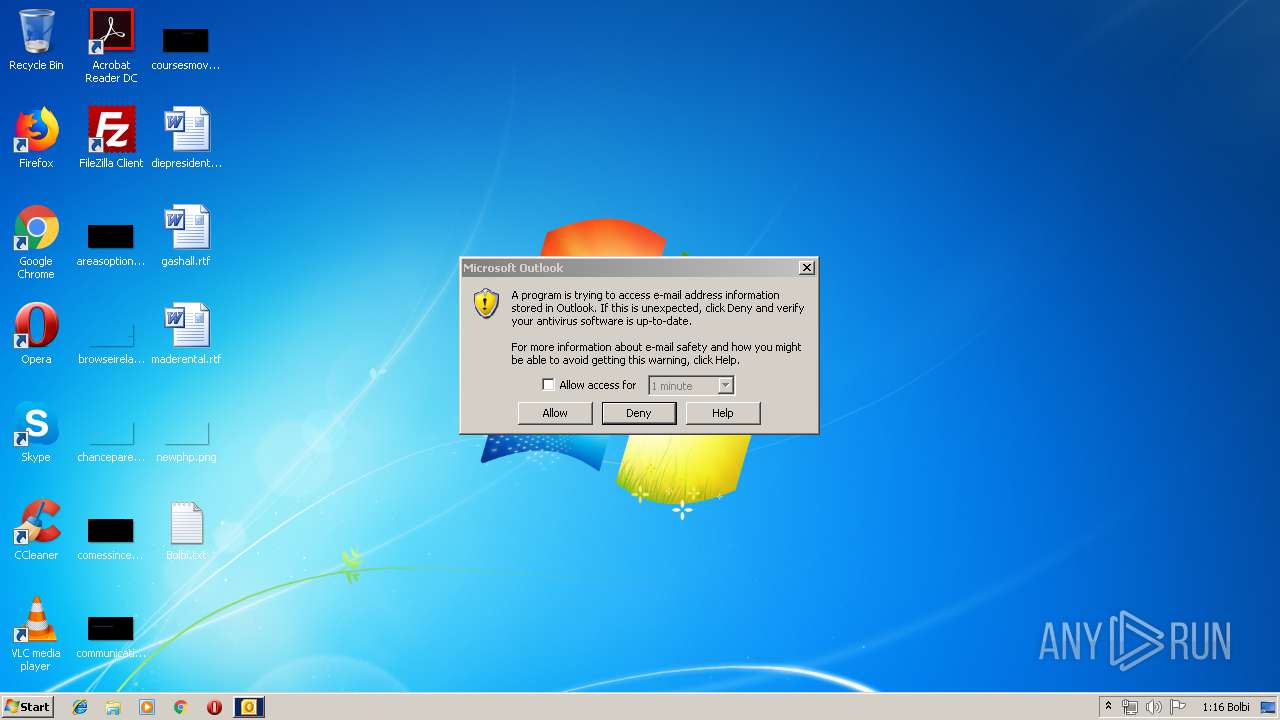
Changes the desktop background image
- wscript.exe (PID: 2664)
Executes scripts
- WScript.exe (PID: 2984)
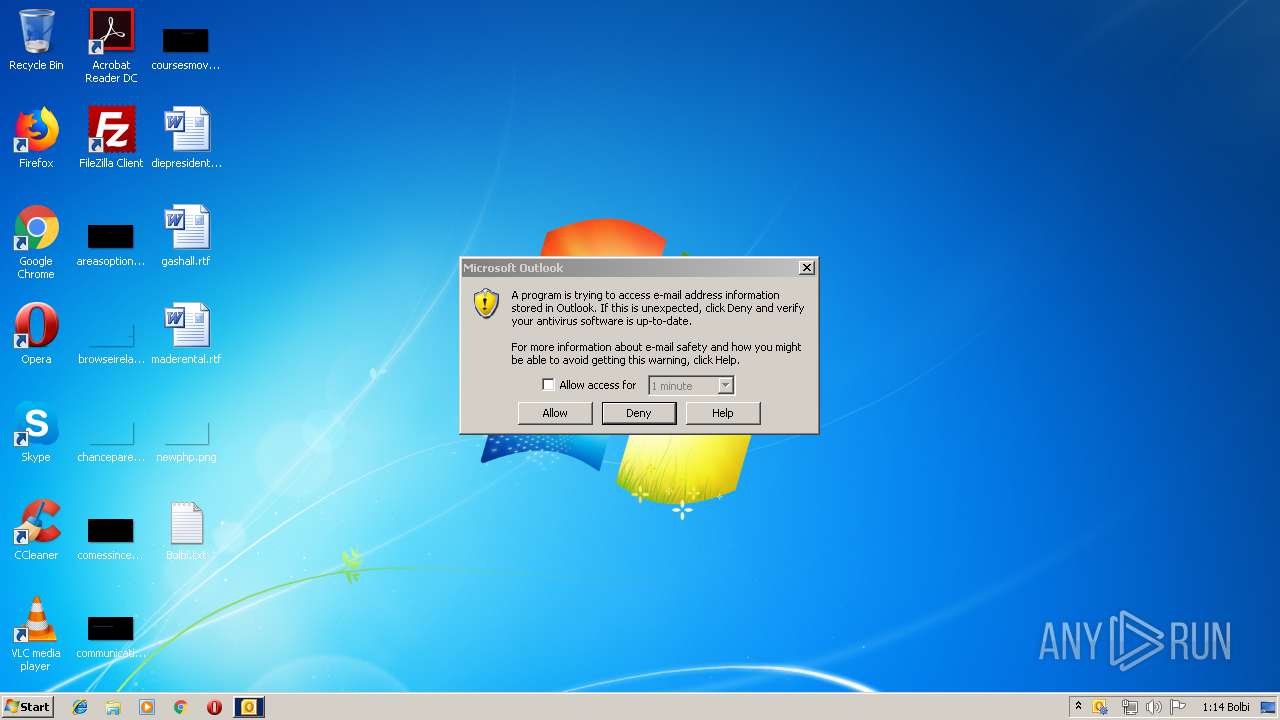
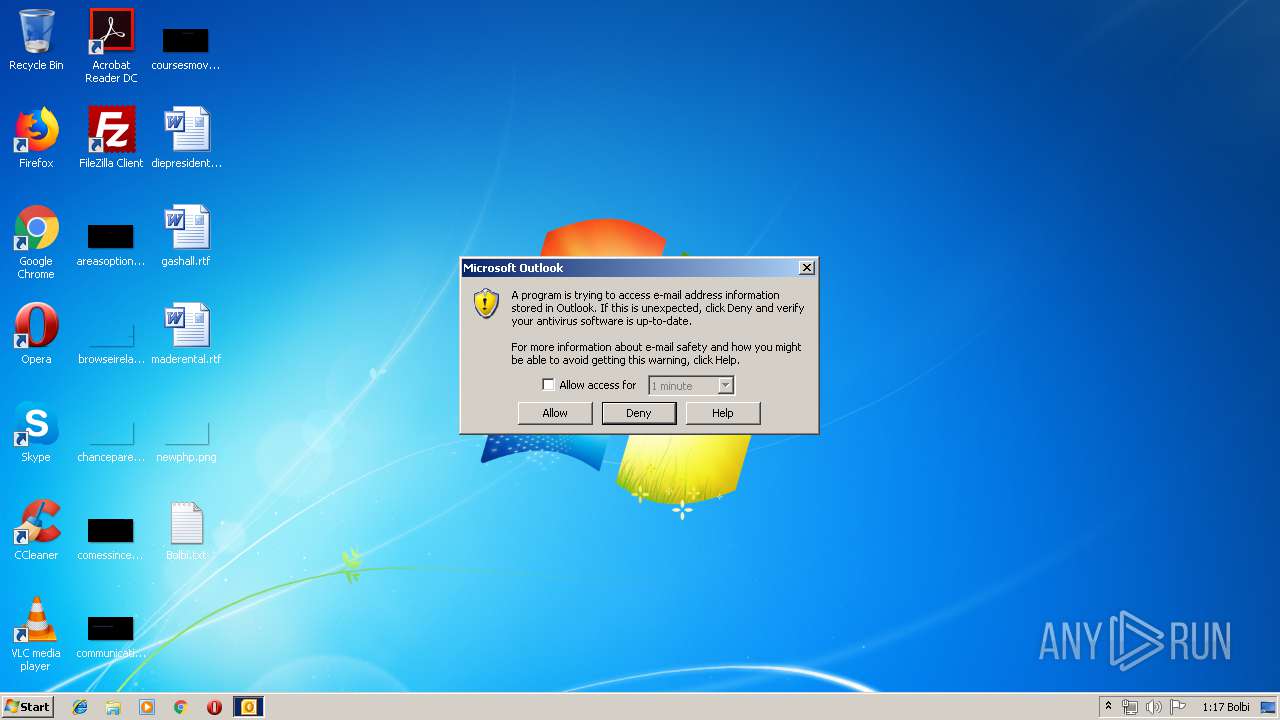
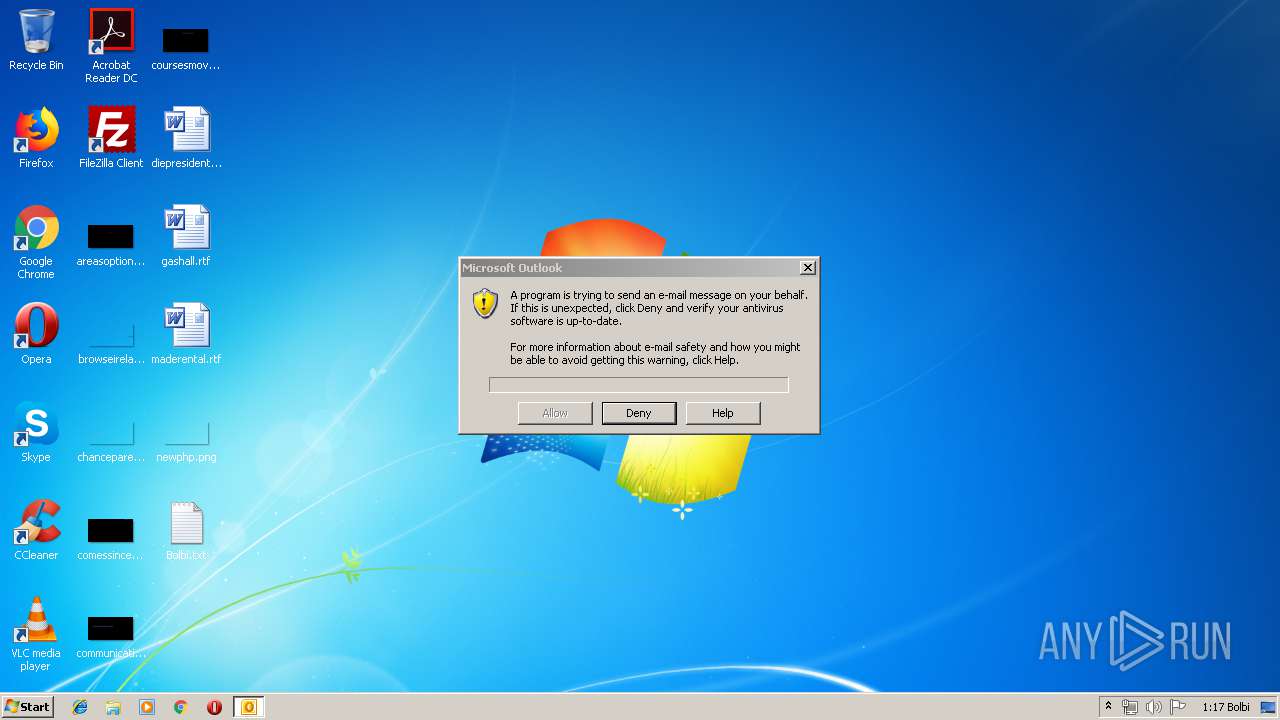
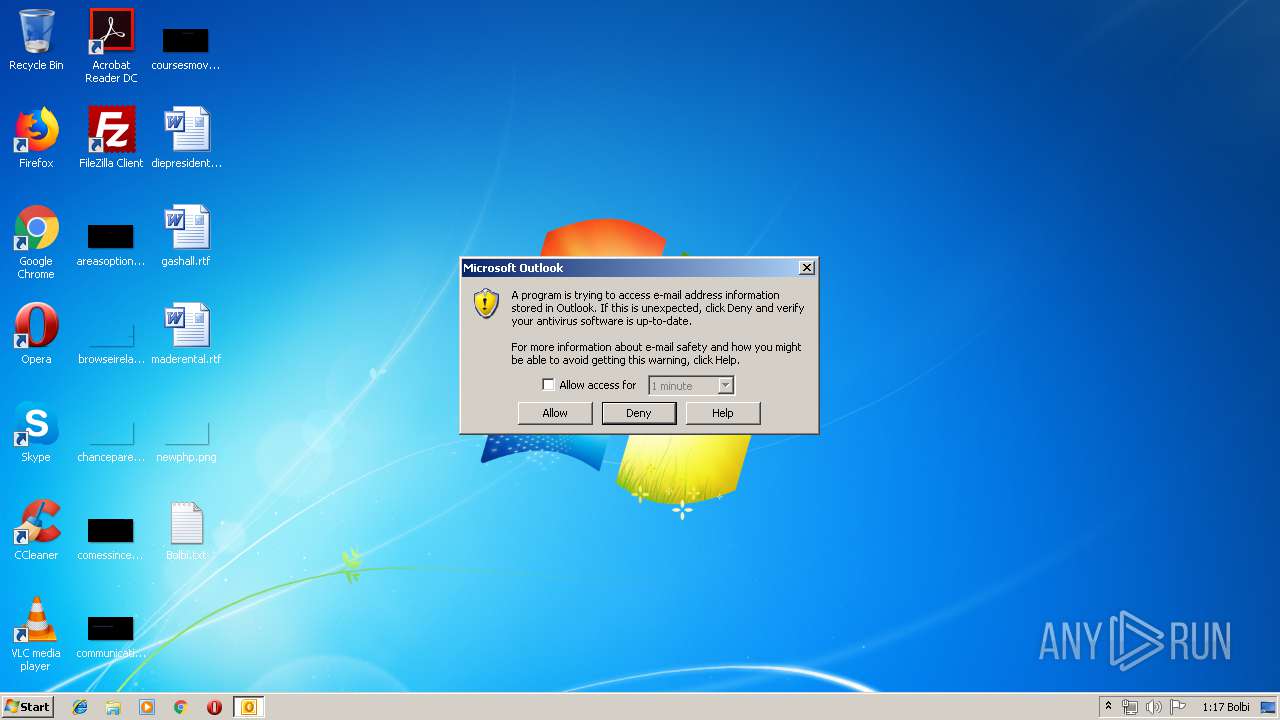
Executed via COM
- OUTLOOK.EXE (PID: 3408)
Executable content was dropped or overwritten
- wscript.exe (PID: 2664)
Creates files in the Windows directory
- OUTLOOK.EXE (PID: 3408)
Removes files from Windows directory
- OUTLOOK.EXE (PID: 3408)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3408)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3408)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2664 | "C:\Windows\System32\wscript.exe" "C:\Users\admin\AppData\Local\Temp\Trojan.VBS.Bolbi.v2.vbs" /elevated | C:\Windows\System32\wscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2984 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Trojan.VBS.Bolbi.v2.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
1 472
Read events
1 359
Write events
101
Delete events
12
Modification events
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2984) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\Public\ghostroot\god.bmp | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | OriginalWallpaper |
Value: C:\Users\Public\ghostroot\god.bmp | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\Public\ghostroot\god.bmp | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | WallpaperStyle |
Value: 2 | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Bolbi |
Value: C:\Users\Public\Ghostroot\Just For You.jpg.vbs | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Bolbi |
Value: C:\Users\Public\Ghostroot\Just For You.jpg.vbs | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot |
| Operation: | write | Name: | AlternateShell |
Value: notepad.exe | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ActiveComputerName |
| Operation: | write | Name: | ComputerName |
Value: Bolbi | |||
Executable files
1
Suspicious files
3
Text files
31
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3408 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRAB38.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3408 | OUTLOOK.EXE | C:\Windows\system32\PerfStringBackup.TMP | — | |
MD5:— | SHA256:— | |||
| 3408 | OUTLOOK.EXE | C:\Windows\system32\PerfStringBackup.INI | binary | |
MD5:— | SHA256:— | |||
| 3408 | OUTLOOK.EXE | C:\Windows\system32\perfc009.dat | binary | |
MD5:— | SHA256:— | |||
| 3408 | OUTLOOK.EXE | C:\Windows\system32\perfh009.dat | binary | |
MD5:— | SHA256:— | |||
| 2664 | wscript.exe | C:\Users\Public\ghostroot\Message.vbs | text | |
MD5:302E08C86880A39CA55F21CABFA7C5DE | SHA256:65CFB12BAAA6F5891BCD7FDA727933A4A12F6DBFA9A6717549EACC6DEE9436C7 | |||
| 2664 | wscript.exe | C:\Users\Public\ghostroot\god.bmp | image | |
MD5:D81B39D90FD06AB2C25C9CD1E192124E | SHA256:1BB633ABA7732A3AE144802130B6176EF526ED4772C2169775B1B300B11082FD | |||
| 2664 | wscript.exe | C:\Users\admin\Desktop\Bolbi.txt | text | |
MD5:B37ED35EF479E43F406429BC36E68EC4 | SHA256:CC2B26F9E750E05CD680EF5721D9269FE4C8D23CABF500A2FF9065B6B4F7E08C | |||
| 3408 | OUTLOOK.EXE | C:\Windows\inf\Outlook\outlperf.h | text | |
MD5:BC71FF7DA14ECA943FA0AD815F72B8CB | SHA256:48E537902C03A3EEE4790FC97EE072CDDC7C1A90122702DD18243D8C12A0D99A | |||
| 3408 | OUTLOOK.EXE | C:\Windows\inf\Outlook\0009\outlperf.ini | text | |
MD5:509A7197AE66401D1DA76F4BAC1DD0A8 | SHA256:EE9E288C3495FD548FD49095BE08807F215FC0780064E179011098C0C7461A34 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3408 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3408 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |