| File name: | SetupYabe_v1.3.1.exe |
| Full analysis: | https://app.any.run/tasks/8dc07be5-0fea-463d-9f5c-f46abd65851d |
| Verdict: | Malicious activity |
| Analysis date: | October 18, 2023, 10:24:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 594C8516E75EB1AFDF0FCF50C6F0CA12 |
| SHA1: | EEC82306958AE309C028AB24D09B0A82EE4D1843 |
| SHA256: | EE18E81AB4AD6C05E86135FCA8F5DBA3CE78883A85A6DC4F3408673B0295FDE6 |
| SSDEEP: | 98304:FbUHt7LANowzTRB2kc64CCX0ngOj9U9NNDH3EJommwduYMkkff0ZLqXjOA7ftjo5:UWfgmN |
MALICIOUS
Drops the executable file immediately after the start
- SetupYabe_v1.3.1.exe (PID: 3828)
- SetupYabe_v1.3.1.exe (PID: 396)
- SetupYabe_v1.3.1.tmp (PID: 2288)
Application was dropped or rewritten from another process
- Yabe.exe (PID: 2088)
Loads dropped or rewritten executable
- Yabe.exe (PID: 2088)
SUSPICIOUS
Reads the Windows owner or organization settings
- SetupYabe_v1.3.1.tmp (PID: 2288)
Reads the Internet Settings
- Yabe.exe (PID: 2088)
INFO
Checks supported languages
- SetupYabe_v1.3.1.exe (PID: 3828)
- SetupYabe_v1.3.1.exe (PID: 396)
- SetupYabe_v1.3.1.tmp (PID: 2288)
- SetupYabe_v1.3.1.tmp (PID: 3900)
- Yabe.exe (PID: 2088)
Reads the computer name
- SetupYabe_v1.3.1.tmp (PID: 3900)
- SetupYabe_v1.3.1.tmp (PID: 2288)
- Yabe.exe (PID: 2088)
Create files in a temporary directory
- SetupYabe_v1.3.1.exe (PID: 3828)
- SetupYabe_v1.3.1.exe (PID: 396)
Application was dropped or rewritten from another process
- SetupYabe_v1.3.1.tmp (PID: 2288)
- SetupYabe_v1.3.1.tmp (PID: 3900)
Creates files in the program directory
- SetupYabe_v1.3.1.tmp (PID: 2288)
Reads the machine GUID from the registry
- Yabe.exe (PID: 2088)
Creates files or folders in the user directory
- Yabe.exe (PID: 2088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:12 13:15:57+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 682496 |
| InitializedDataSize: | 37888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7ed0 |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Yabe Authors |
| FileDescription: | Yabe Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Yabe |
| ProductVersion: | 1.3.1 |
Total processes
44
Monitored processes
5
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | "C:\Users\admin\AppData\Local\Temp\SetupYabe_v1.3.1.exe" /SPAWNWND=$A01D0 /NOTIFYWND=$6035E | C:\Users\admin\AppData\Local\Temp\SetupYabe_v1.3.1.exe | SetupYabe_v1.3.1.tmp | ||||||||||||
User: admin Company: Yabe Authors Integrity Level: HIGH Description: Yabe Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Yabe\Yabe.exe" | C:\Program Files\Yabe\Yabe.exe | SetupYabe_v1.3.1.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Yabe Exit code: 0 Version: 1.3.1 Modules
| |||||||||||||||
| 2288 | "C:\Users\admin\AppData\Local\Temp\is-10442.tmp\SetupYabe_v1.3.1.tmp" /SL5="$1301AA,1798376,721408,C:\Users\admin\AppData\Local\Temp\SetupYabe_v1.3.1.exe" /SPAWNWND=$A01D0 /NOTIFYWND=$6035E | C:\Users\admin\AppData\Local\Temp\is-10442.tmp\SetupYabe_v1.3.1.tmp | — | SetupYabe_v1.3.1.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3828 | "C:\Users\admin\AppData\Local\Temp\SetupYabe_v1.3.1.exe" | C:\Users\admin\AppData\Local\Temp\SetupYabe_v1.3.1.exe | — | explorer.exe | |||||||||||
User: admin Company: Yabe Authors Integrity Level: MEDIUM Description: Yabe Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3900 | "C:\Users\admin\AppData\Local\Temp\is-CLK1F.tmp\SetupYabe_v1.3.1.tmp" /SL5="$6035E,1798376,721408,C:\Users\admin\AppData\Local\Temp\SetupYabe_v1.3.1.exe" | C:\Users\admin\AppData\Local\Temp\is-CLK1F.tmp\SetupYabe_v1.3.1.tmp | — | SetupYabe_v1.3.1.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
1 311
Read events
1 297
Write events
8
Delete events
6
Modification events
| (PID) Process: | (2288) SetupYabe_v1.3.1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: 9DE312A77230FDA06020670E5ECD38EF079CF6AA3BB81175378284B7AD521F3E | |||
| (PID) Process: | (2288) SetupYabe_v1.3.1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\Yabe\Yabe.exe | |||
| (PID) Process: | (2288) SetupYabe_v1.3.1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2288) SetupYabe_v1.3.1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: BAE78E95761BFC24BFAA255B53EB8D001B272E88C49F6364C5428994C7FFE4F1 | |||
| (PID) Process: | (2288) SetupYabe_v1.3.1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: F0080000867A6253AD01DA01 | |||
| (PID) Process: | (2288) SetupYabe_v1.3.1.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2088) Yabe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2088) Yabe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2088) Yabe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2088) Yabe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
22
Suspicious files
16
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\Yabe.exe | executable | |
MD5:520C85A80E40F37AD1FFF402360BDE45 | SHA256:6682F787DB12C75B78D9478450A4E744965D001BDD374EE39C2C53BC8B50B41F | |||
| 3828 | SetupYabe_v1.3.1.exe | C:\Users\admin\AppData\Local\Temp\is-CLK1F.tmp\SetupYabe_v1.3.1.tmp | executable | |
MD5:84DB4B4205F705DA71471DC6ECC061F5 | SHA256:647983EBDE53E0501FF1AF8EF6190DFEEA5CCC64CAF7DCE808F1E3D98FB66A3C | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\ListOutOfService.dll | executable | |
MD5:66CDCDD23CAEA81BEDB146FF8CF93FEE | SHA256:3E7CDF1382CBC8CC54F430EDF8CCCC2B1638E12AB7DC635B751BFBFE8C510A3E | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\CheckStatusFlags.dll | executable | |
MD5:E27119029BD903EBC029D9022F09C92F | SHA256:60414AE77C965B8358AEB5E298272C24B38535316AEFC7C1309B027F187785EA | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\GlobalCommander.dll | executable | |
MD5:7DD63BA0ECEA2F8627800C9D435A2D7F | SHA256:BF008BF05DC6CE731C950DBD544C08AAE65BEFD6917F8C82A1FA28E1B821FAB7 | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\is-405FF.tmp | executable | |
MD5:66CDCDD23CAEA81BEDB146FF8CF93FEE | SHA256:3E7CDF1382CBC8CC54F430EDF8CCCC2B1638E12AB7DC635B751BFBFE8C510A3E | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\is-V7U95.tmp | executable | |
MD5:AFBE731F45838D9DD7E3B5CD99E7AC01 | SHA256:8022B149D07F9C7D34387619C76967D496C0BD54C488223D6B127CEF57F625C8 | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\is-98R4Q.tmp | text | |
MD5:E516052D8FDB16D60269D25097A11D9B | SHA256:5CAC3AE32E3349A29A3999974367EBA310E7C3BAEDDB3B4B52E7DDB851754077 | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\history.txt | text | |
MD5:F365502C95CE2026BC5C6AB8A2F01621 | SHA256:5F6448DDAA128B50ACB25127CAFA0DCA85FDDA81CE03BFA07E3C5C0E974FA98A | |||
| 2288 | SetupYabe_v1.3.1.tmp | C:\Program Files\Yabe\is-53RQG.tmp | text | |
MD5:F365502C95CE2026BC5C6AB8A2F01621 | SHA256:5F6448DDAA128B50ACB25127CAFA0DCA85FDDA81CE03BFA07E3C5C0E974FA98A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
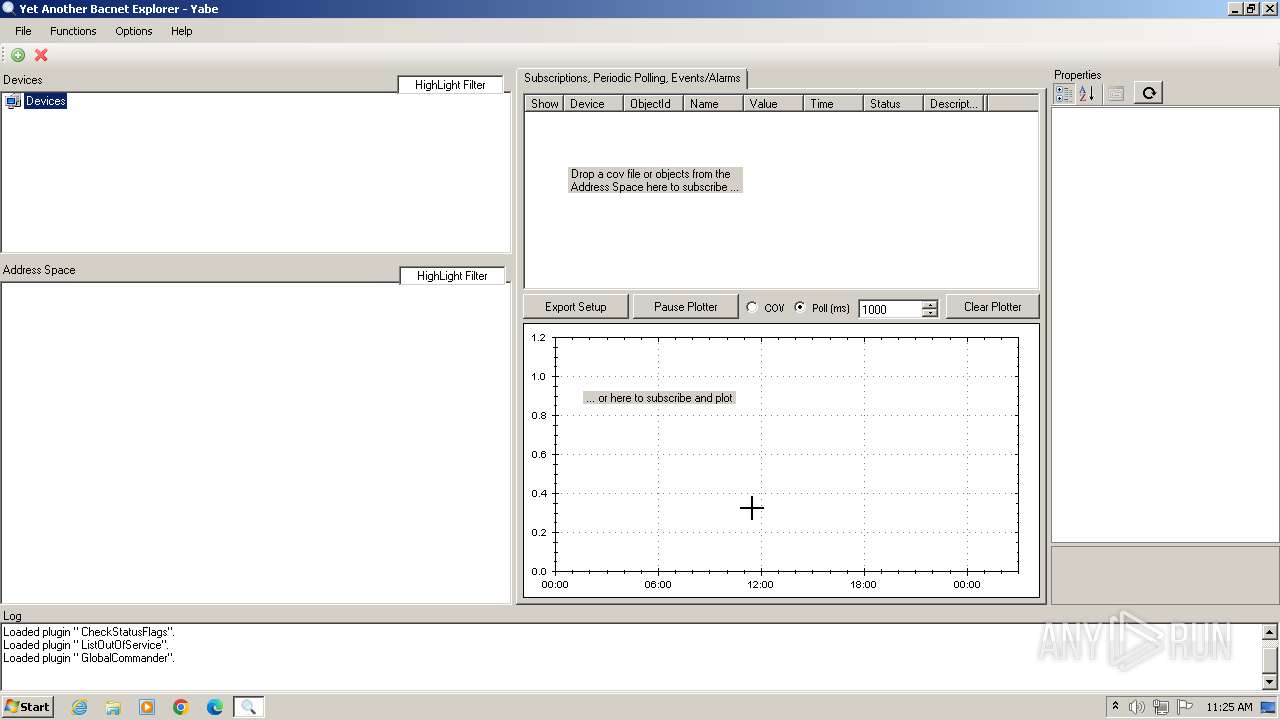
Yabe.exe | Loaded plugin "CheckReliability".
|
Yabe.exe | Loaded plugin " CheckStatusFlags".
|
Yabe.exe | Loaded plugin " ListOutOfService".
|
Yabe.exe | Loaded plugin " GlobalCommander".
|