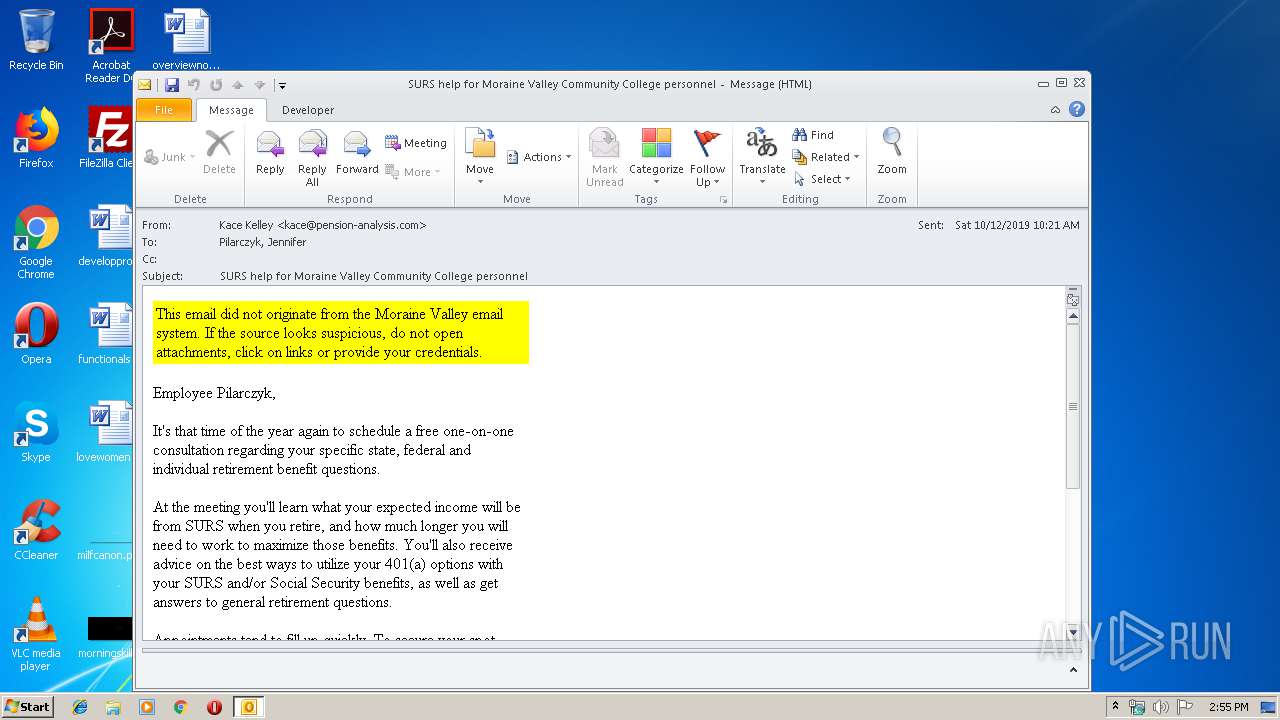
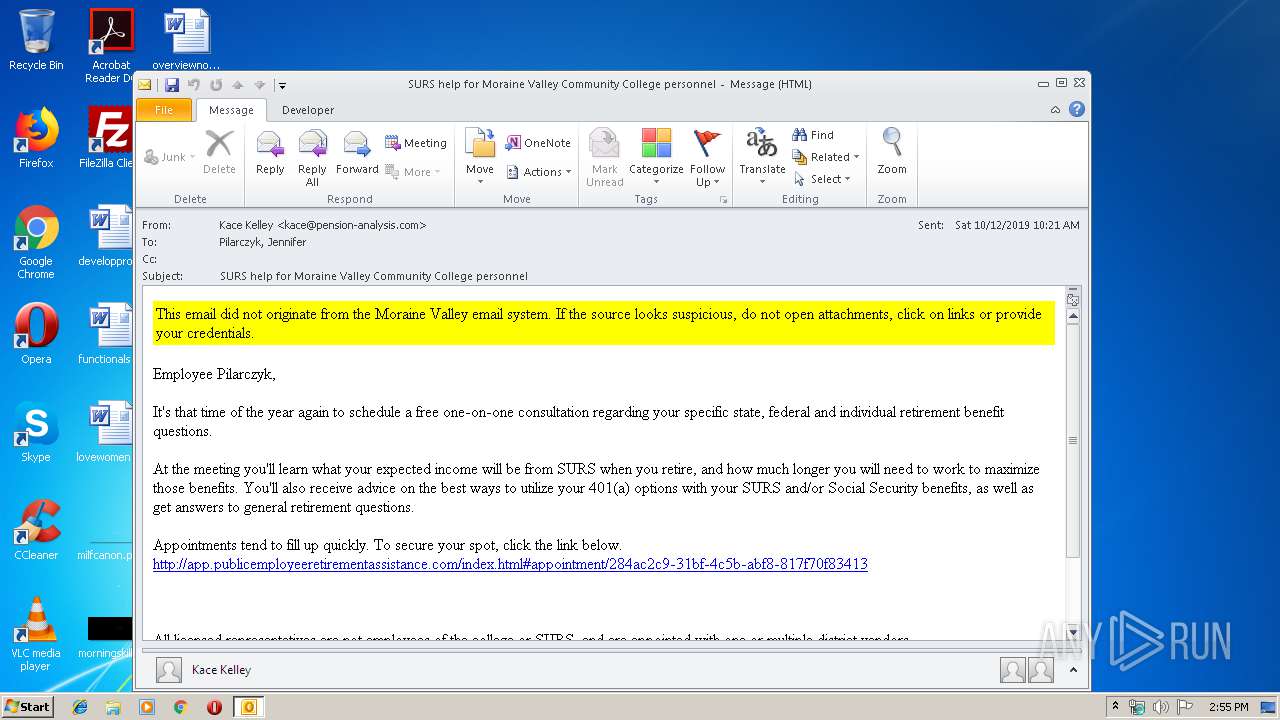
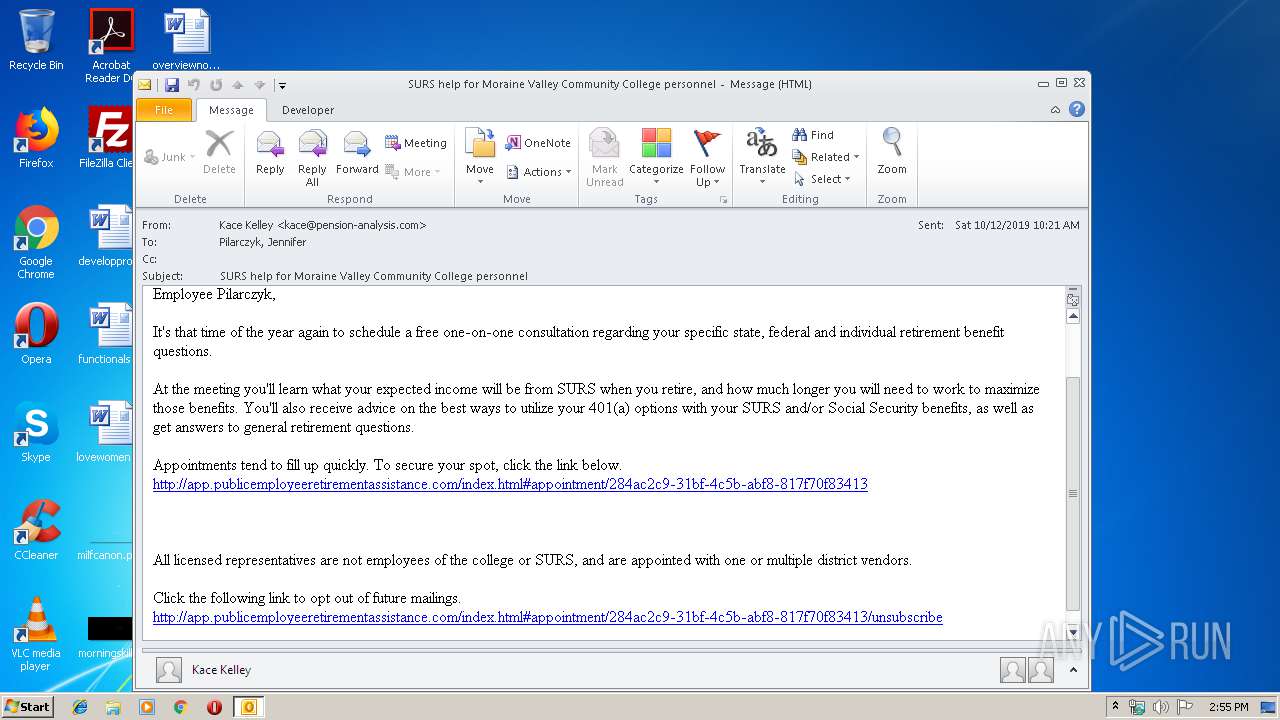
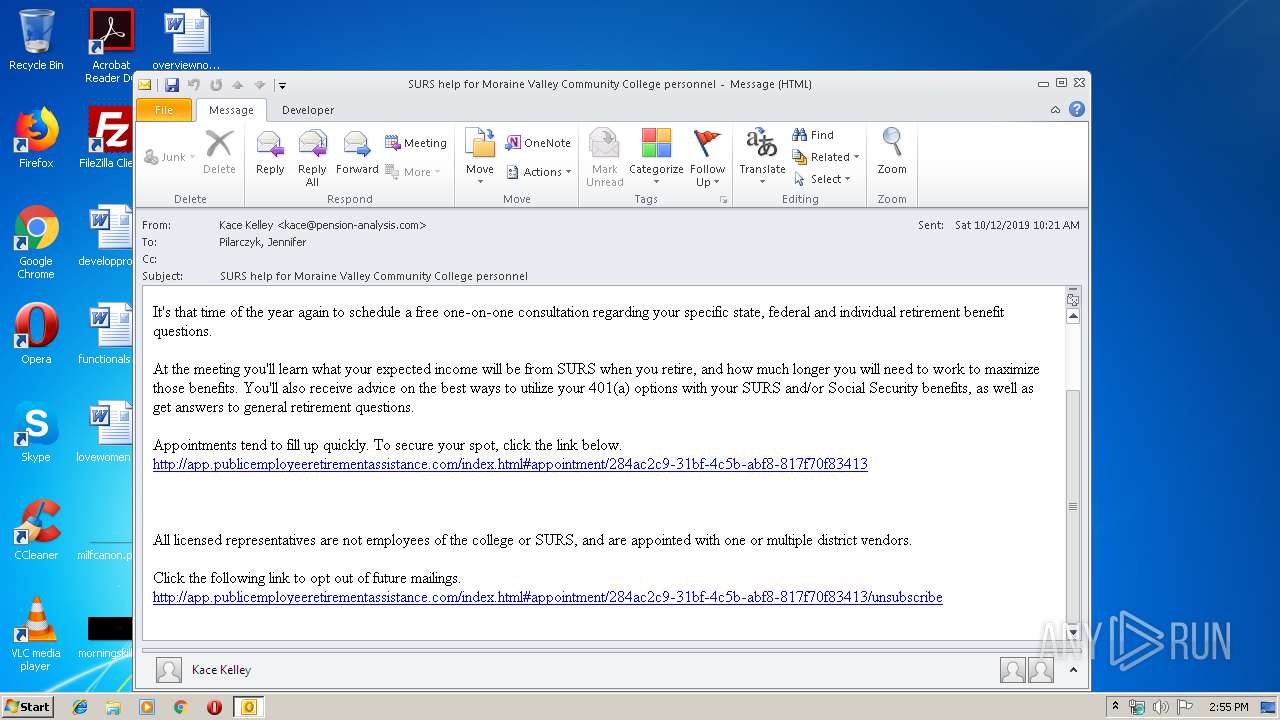
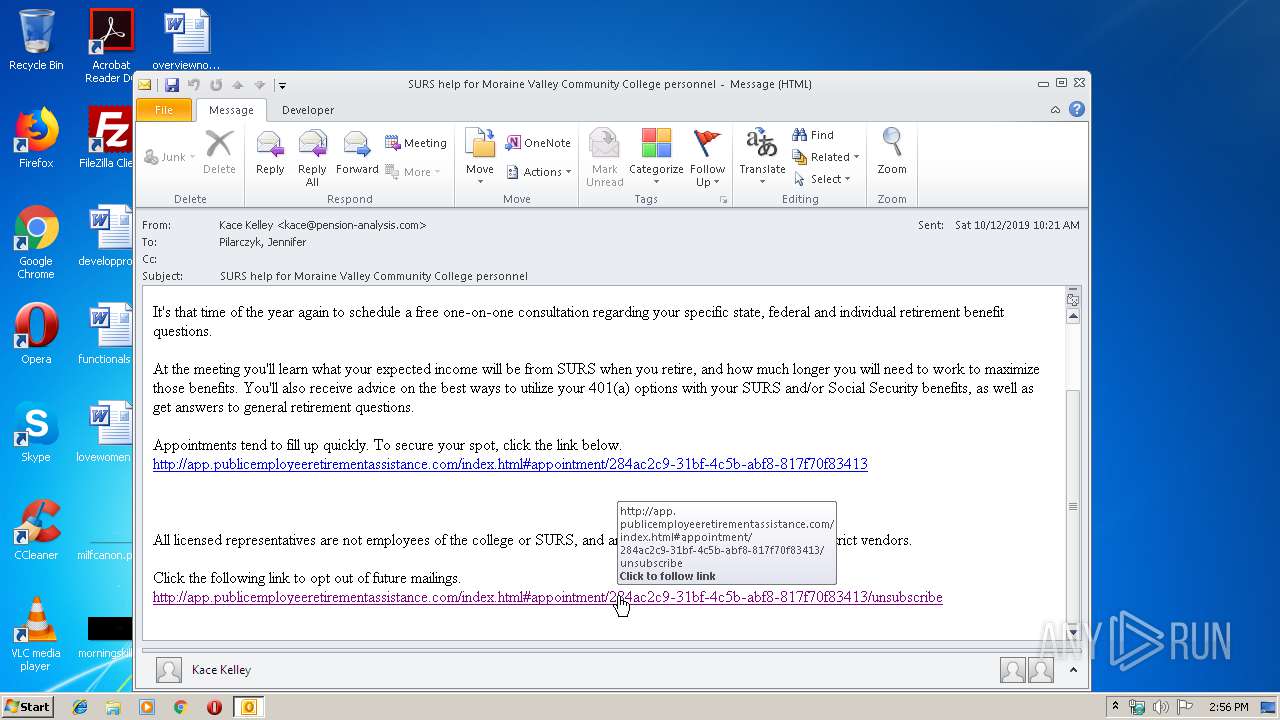
| File name: | SURS help for Moraine Valley Community College personnel.msg |
| Full analysis: | https://app.any.run/tasks/5d86b9ed-bd05-4aa1-b397-3bd8e8e961b8 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2019, 13:55:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 3821F7720E24D71BFB0ECB751F65CF12 |
| SHA1: | 1A9907011D75BF856FD1ABC9EA5571011958E772 |
| SHA256: | EE03C3897CC6A09D55CDAB6FE711BDE9002C7EB7426D1D4368B772144B40794E |
| SSDEEP: | 384:NRKLi/6aqysKysK73oUxdGdT0ZMWqzvIesPRtY7Ou+MmBZV:WVaqysKysK73oIrZMWqjIeyu+MmN |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2420)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2420)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2420)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2420)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1600)
Application launched itself
- iexplore.exe (PID: 1600)
Reads Internet Cache Settings
- iexplore.exe (PID: 3048)
Reads internet explorer settings
- iexplore.exe (PID: 3048)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1600 | "C:\Program Files\Internet Explorer\iexplore.exe" http://app.publicemployeeretirementassistance.com/index.html#appointment/284ac2c9-31bf-4c5b-abf8-817f70f83413/unsubscribe | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\SURS help for Moraine Valley Community College personnel.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3048 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1600 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 879
Read events
1 253
Write events
605
Delete events
21
Modification events
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330512052 | |||
| (PID) Process: | (2420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
0
Text files
83
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2420 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA4C6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1600 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1600 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2420 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2420 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\8JZUG7K0\index[1].htm | html | |
MD5:— | SHA256:— | |||
| 3048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\8JZUG7K0\css[1].txt | text | |
MD5:— | SHA256:— | |||
| 2420 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{0CEE44EA-0166-45D8-A474-94F21E837A0A}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:7D80C0A7E3849818695EAF4989186A3C | SHA256:72DC527D78A8E99331409803811CC2D287E812C008A1C869A6AEA69D7A44B597 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2420 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/index.html | US | html | 1.02 Kb | unknown |
3048 | iexplore.exe | GET | 200 | 172.217.23.138:80 | http://fonts.googleapis.com/css?family=Open+Sans:300italic,400italic,600italic,700italic,400,600,700,300&subset=latin | US | text | 167 b | whitelisted |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/assets/stylesheets/pages.min.css | US | text | 6.10 Kb | unknown |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/assets/stylesheets/pixel-admin.min.css | US | text | 41.7 Kb | unknown |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/assets/stylesheets/splash.css | US | text | 663 b | unknown |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/assets/stylesheets/themes.min.css | US | text | 24.2 Kb | unknown |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/assets/stylesheets/bootstrap.css | US | text | 18.0 Kb | unknown |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/lib/font-awesome/css/font-awesome.min.css | US | text | 5.26 Kb | unknown |
3048 | iexplore.exe | GET | 200 | 68.168.96.100:80 | http://app.publicemployeeretirementassistance.com/assets/stylesheets/fullcalendar.css | US | text | 7.42 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1600 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3048 | iexplore.exe | 68.168.96.100:80 | app.publicemployeeretirementassistance.com | Codero | US | unknown |
2420 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3048 | iexplore.exe | 172.217.23.138:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3048 | iexplore.exe | 172.217.23.163:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1600 | iexplore.exe | 68.168.96.100:80 | app.publicemployeeretirementassistance.com | Codero | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
app.publicemployeeretirementassistance.com |
| unknown |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
dns.msftncsi.com |
| shared |