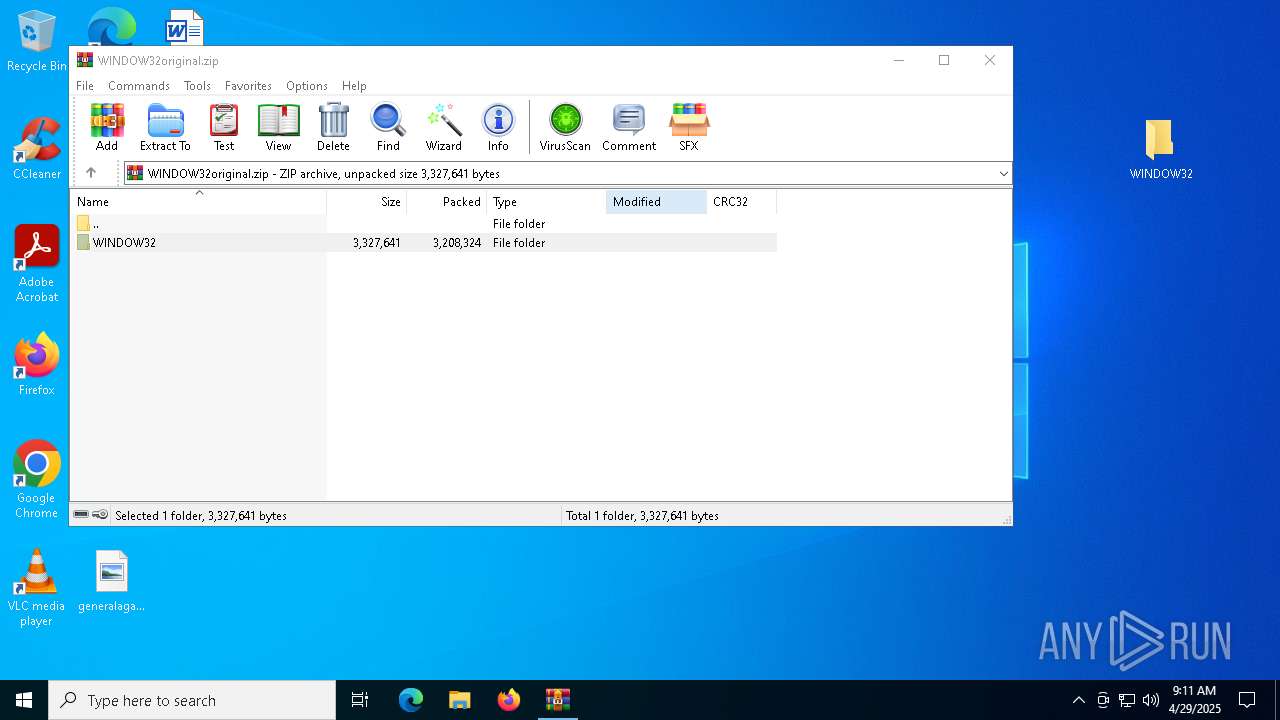
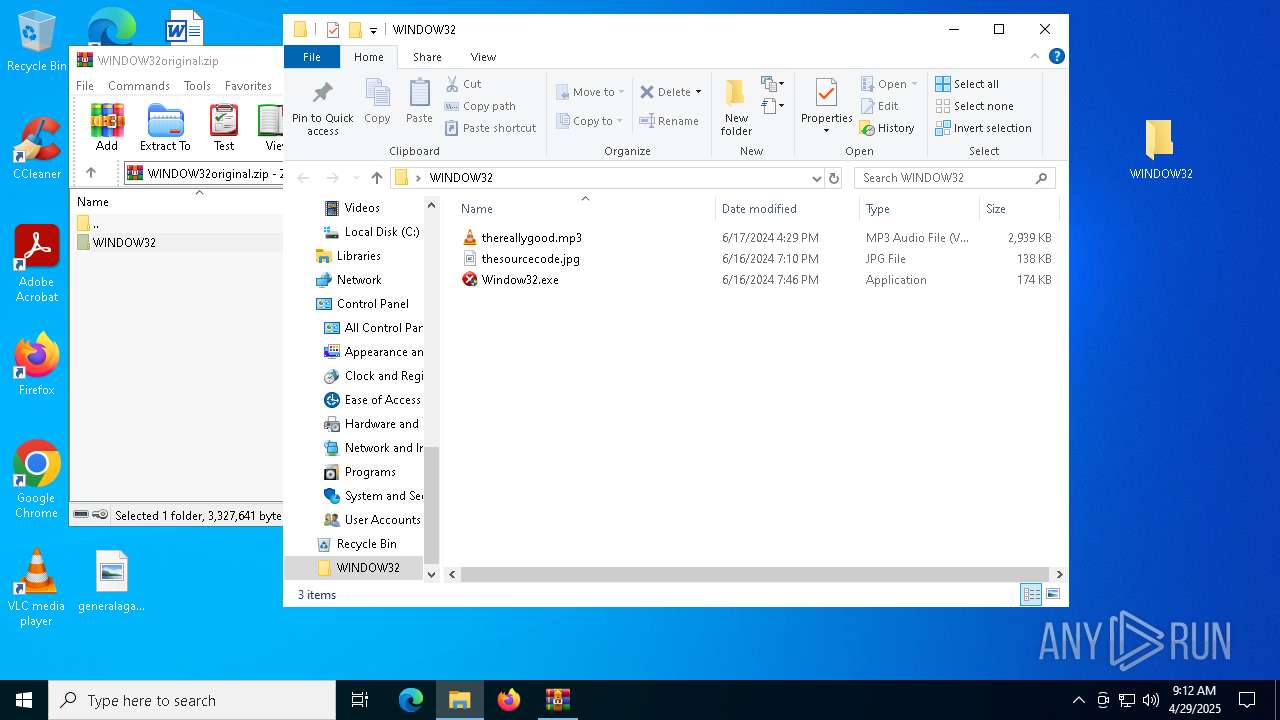
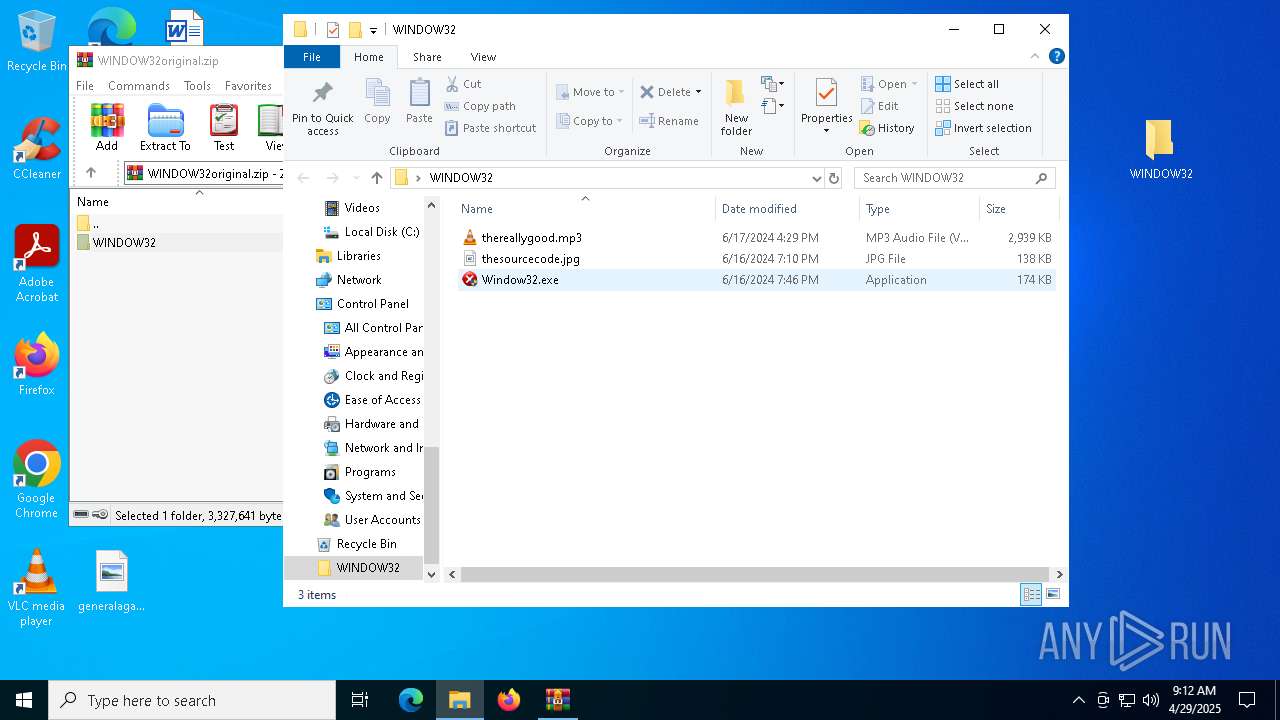
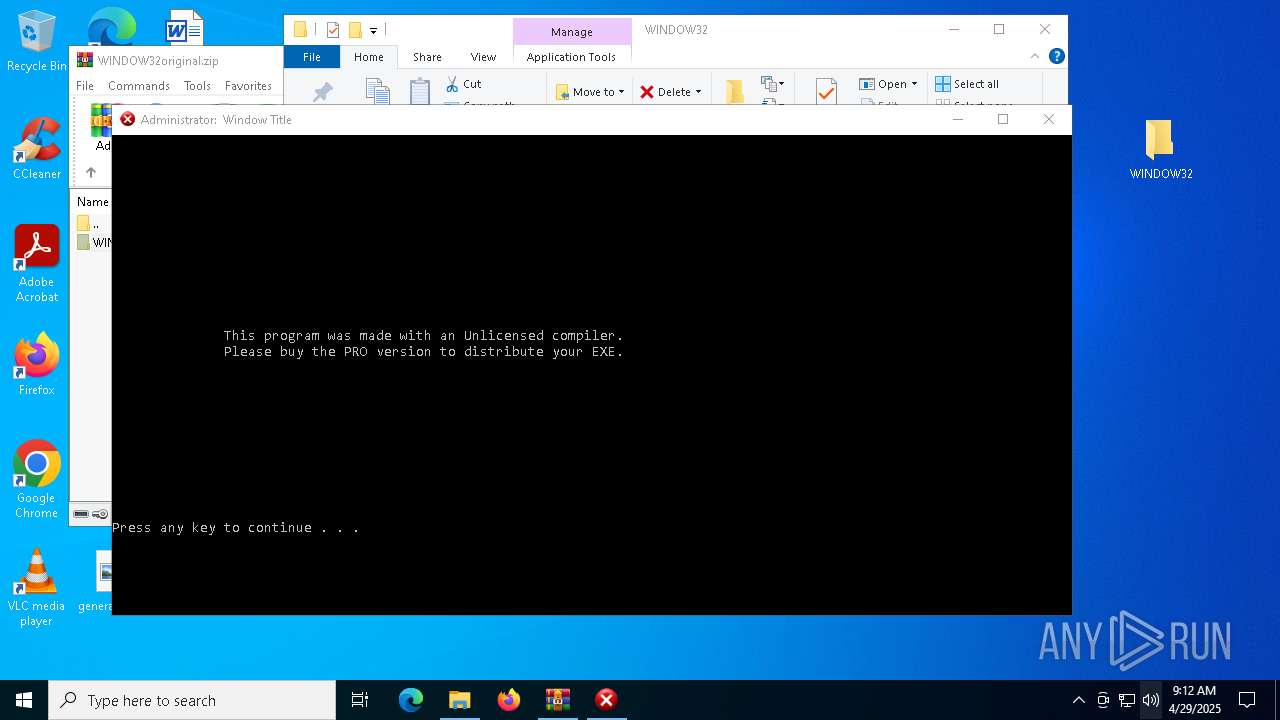
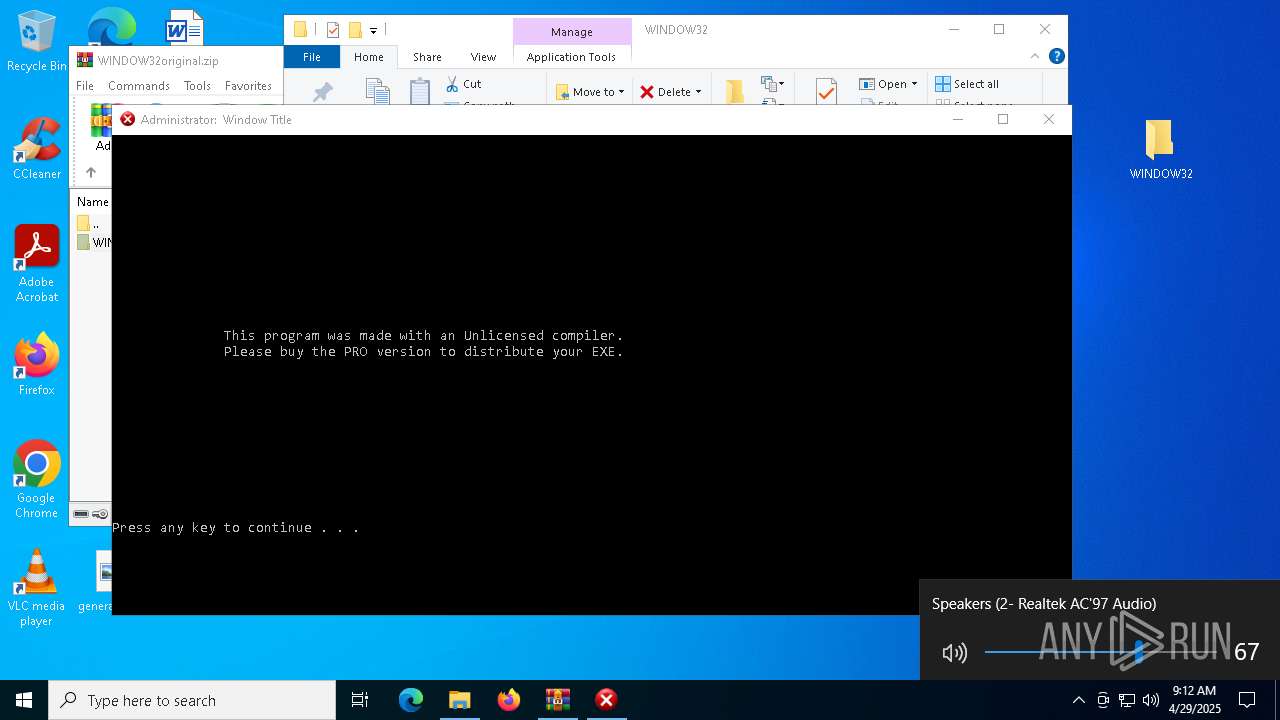
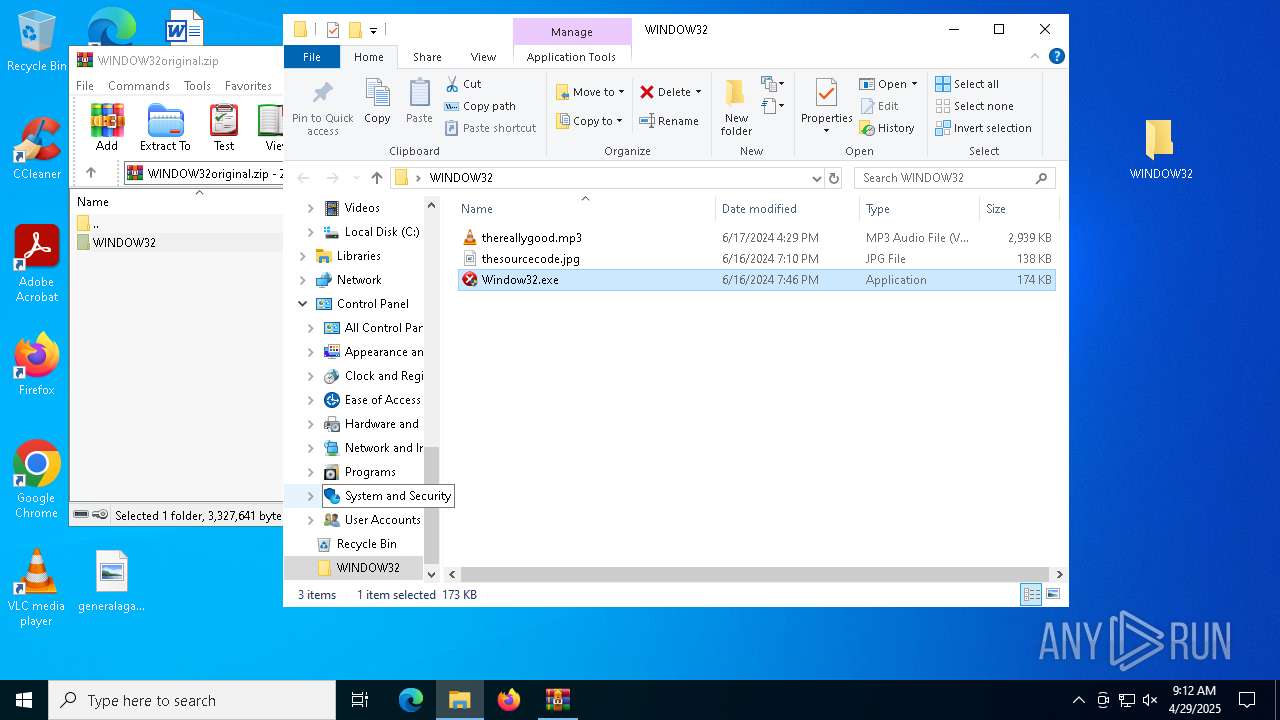
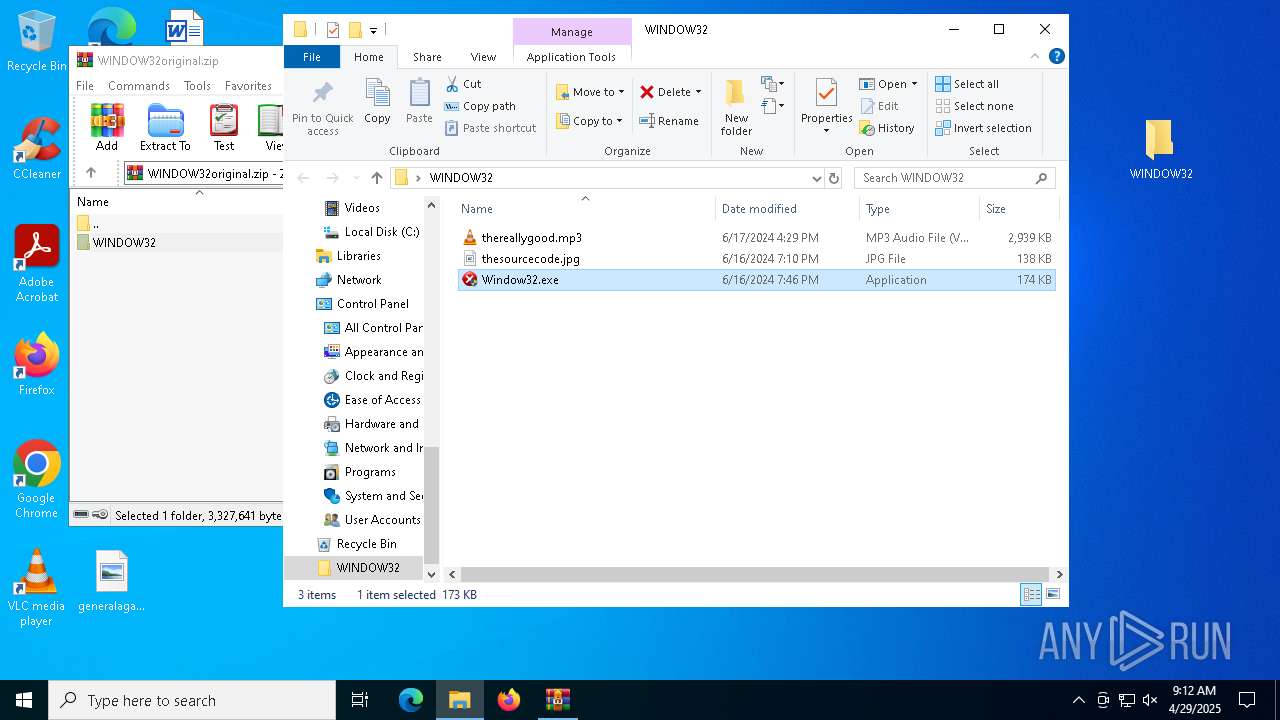
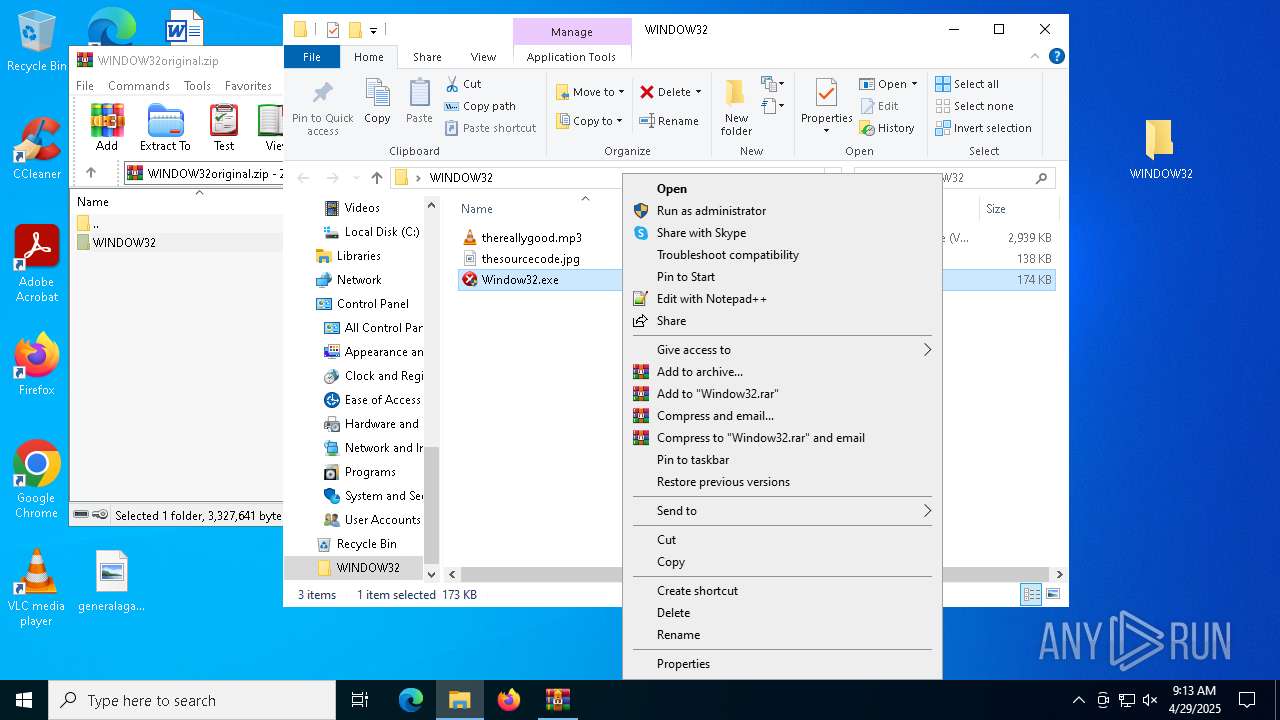
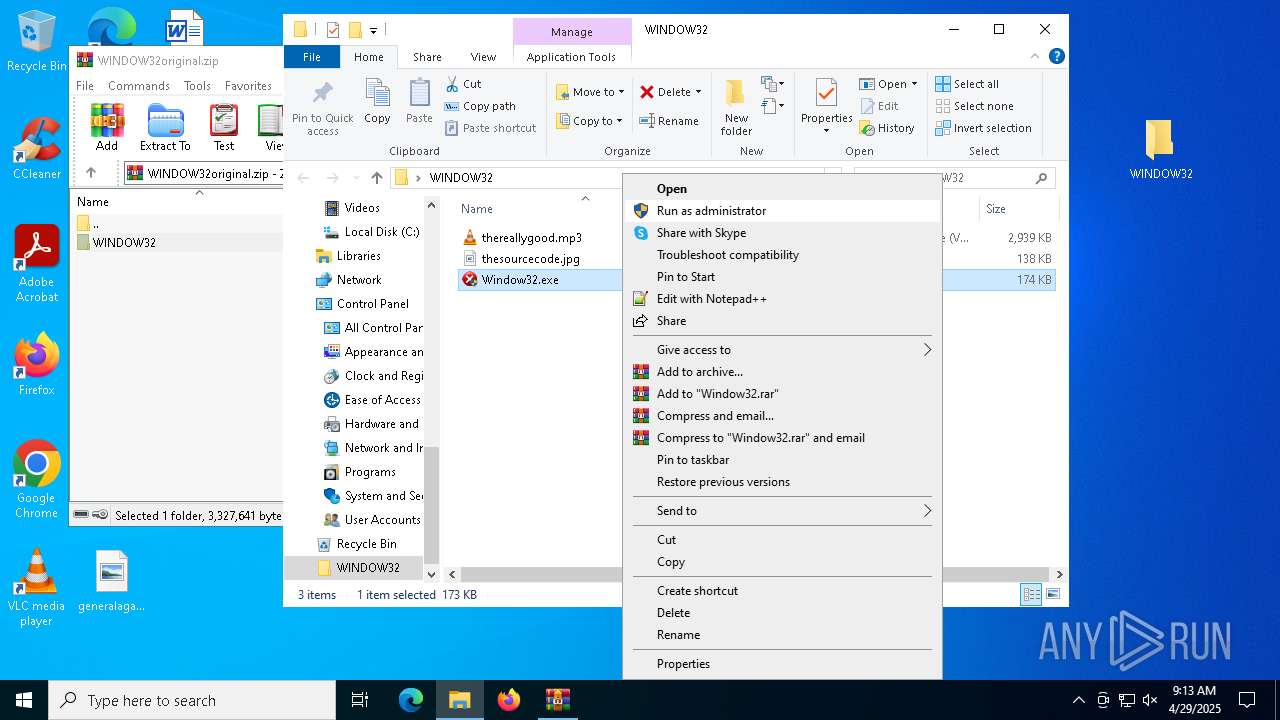
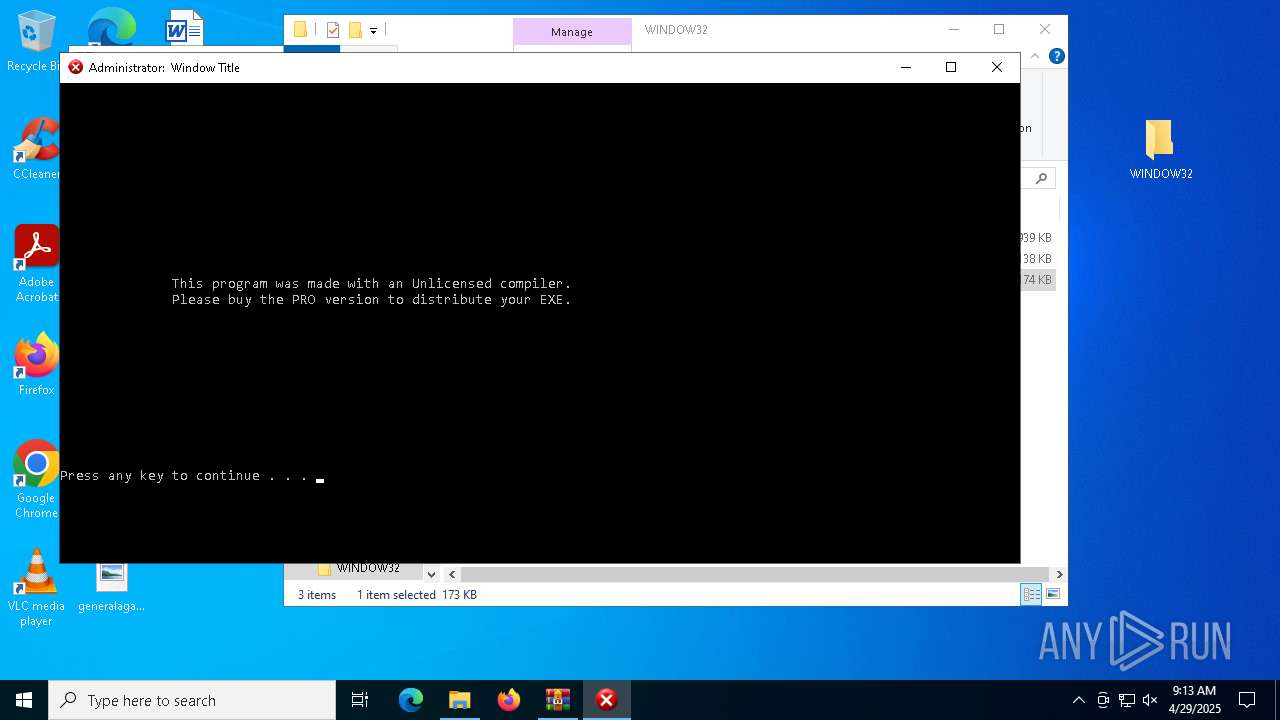
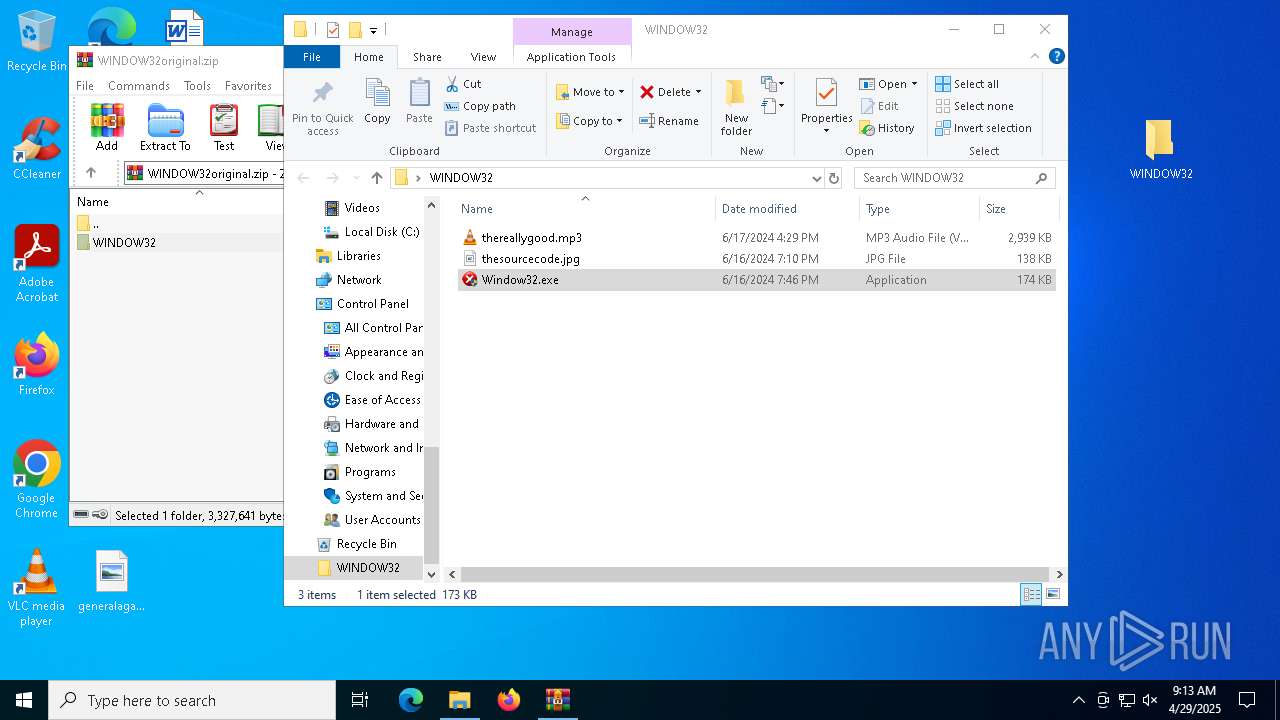
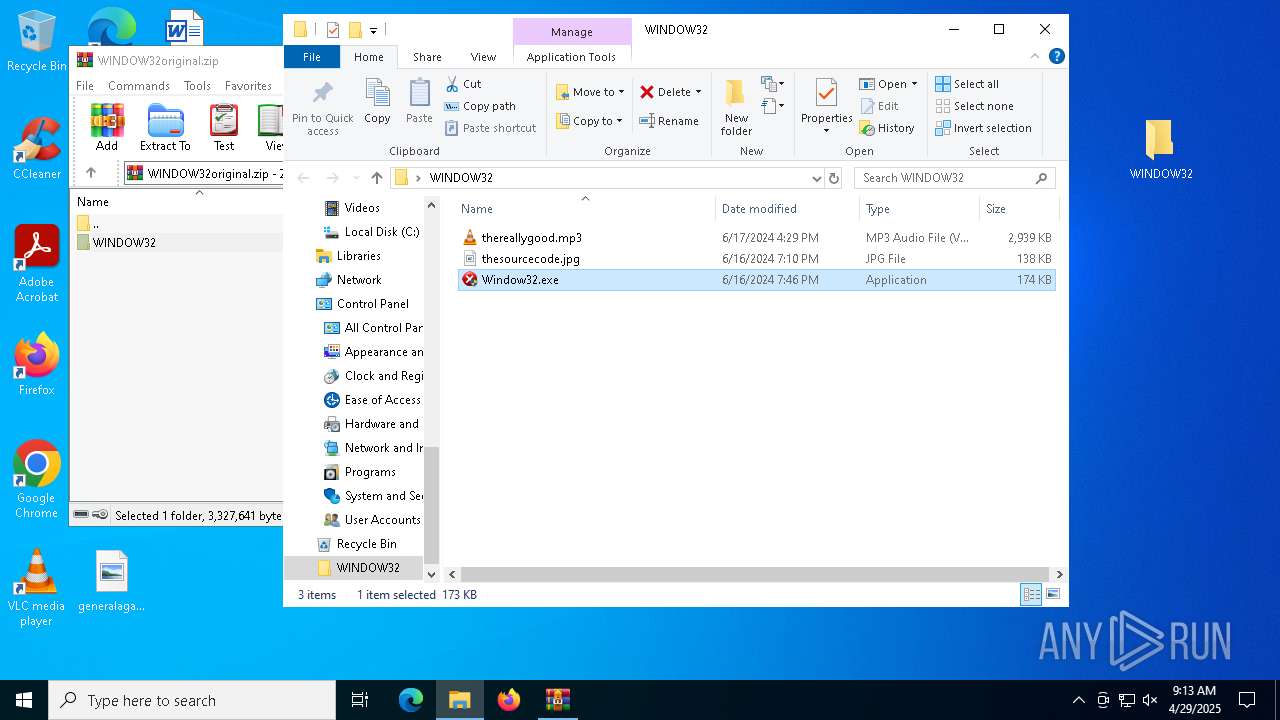
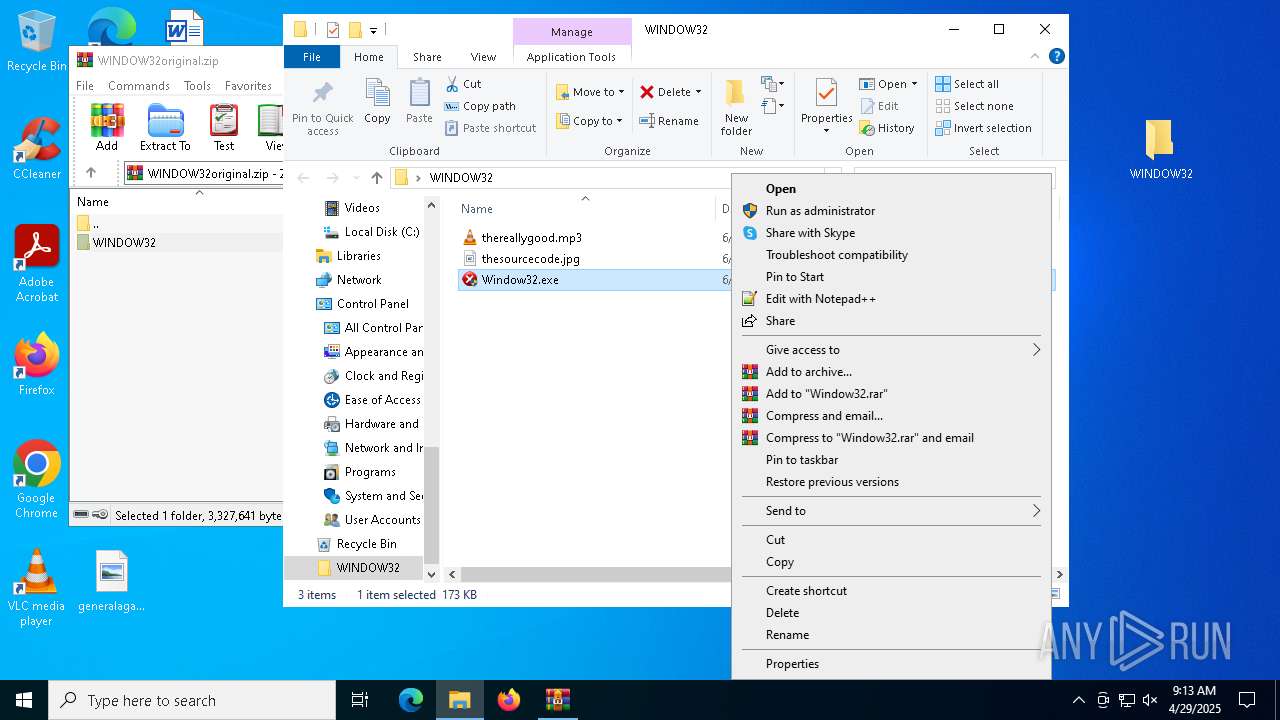
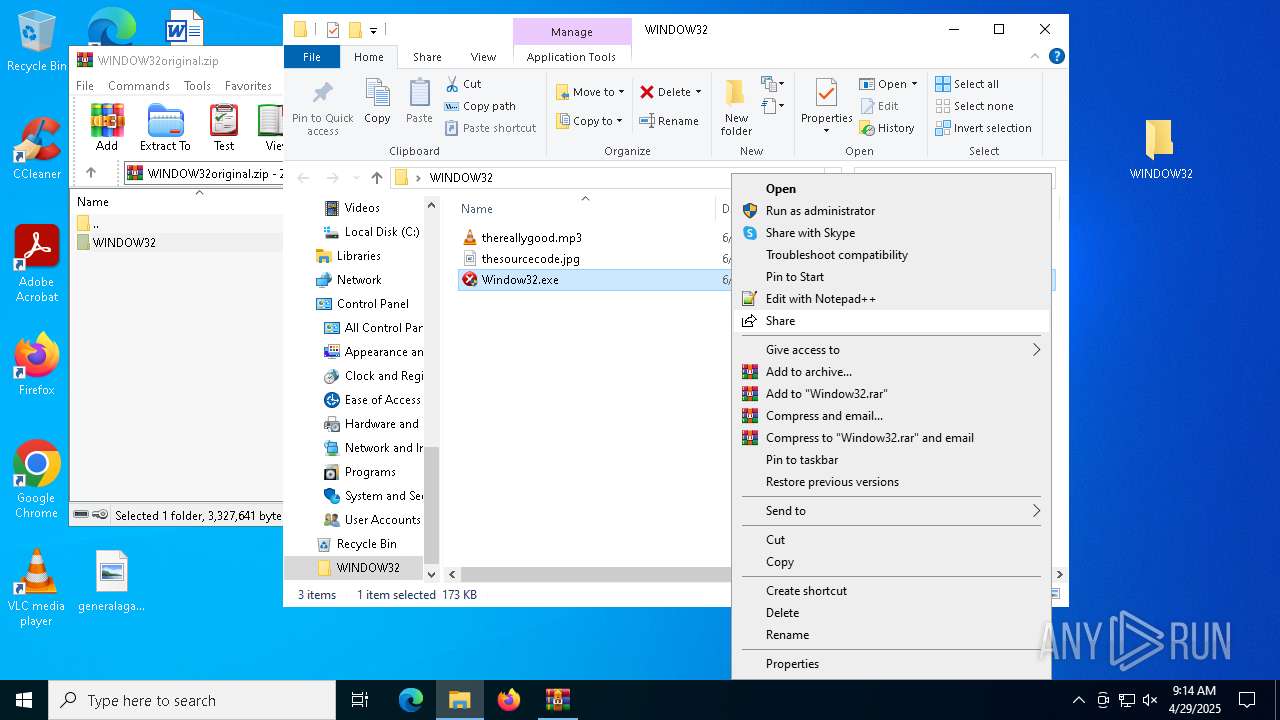
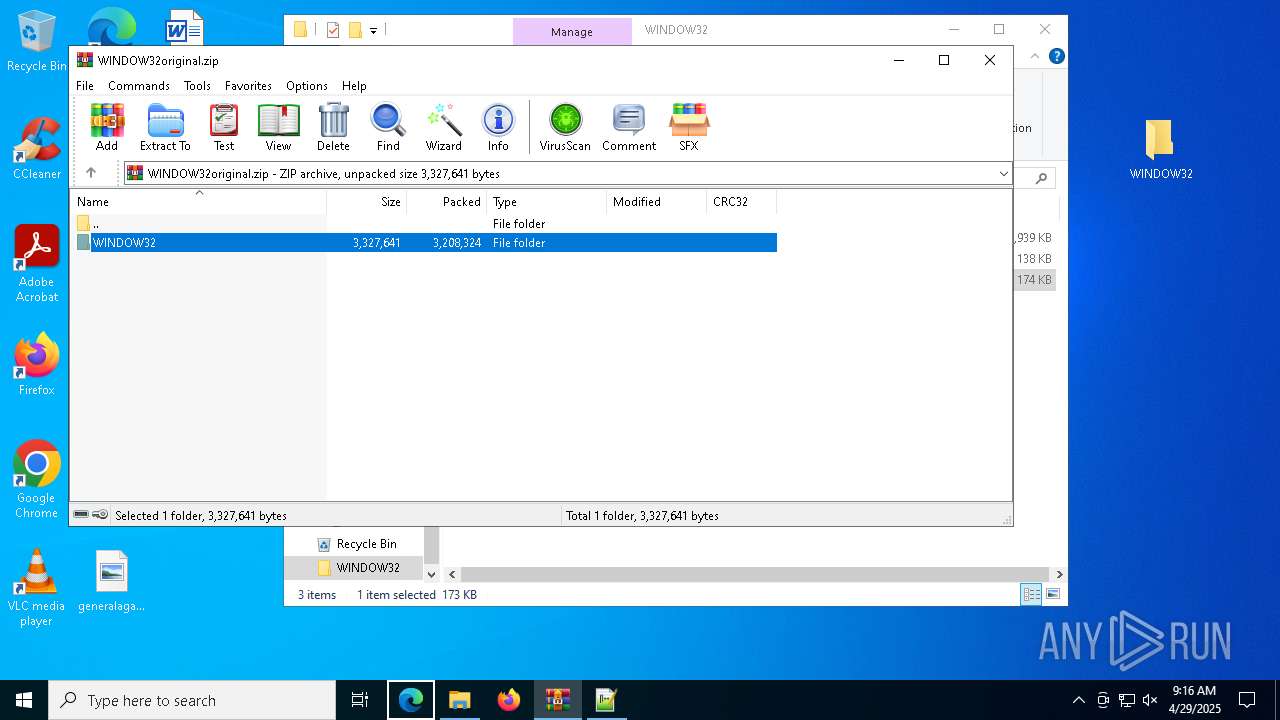
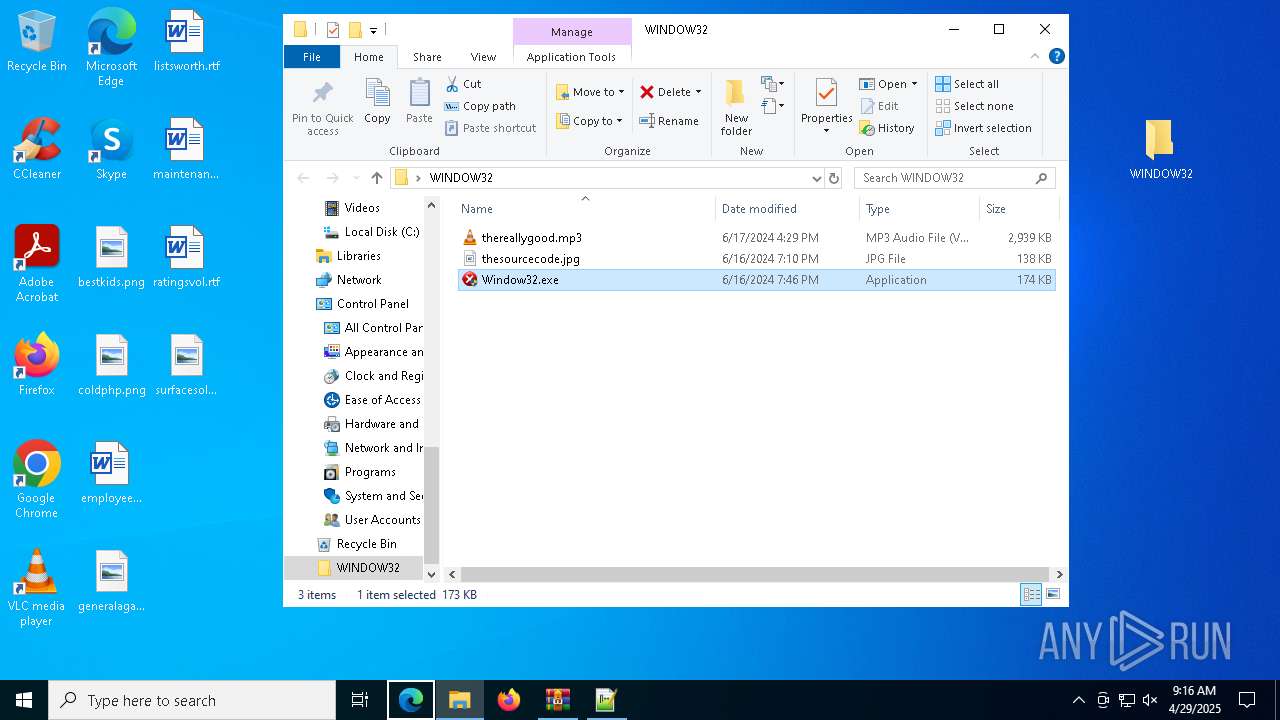
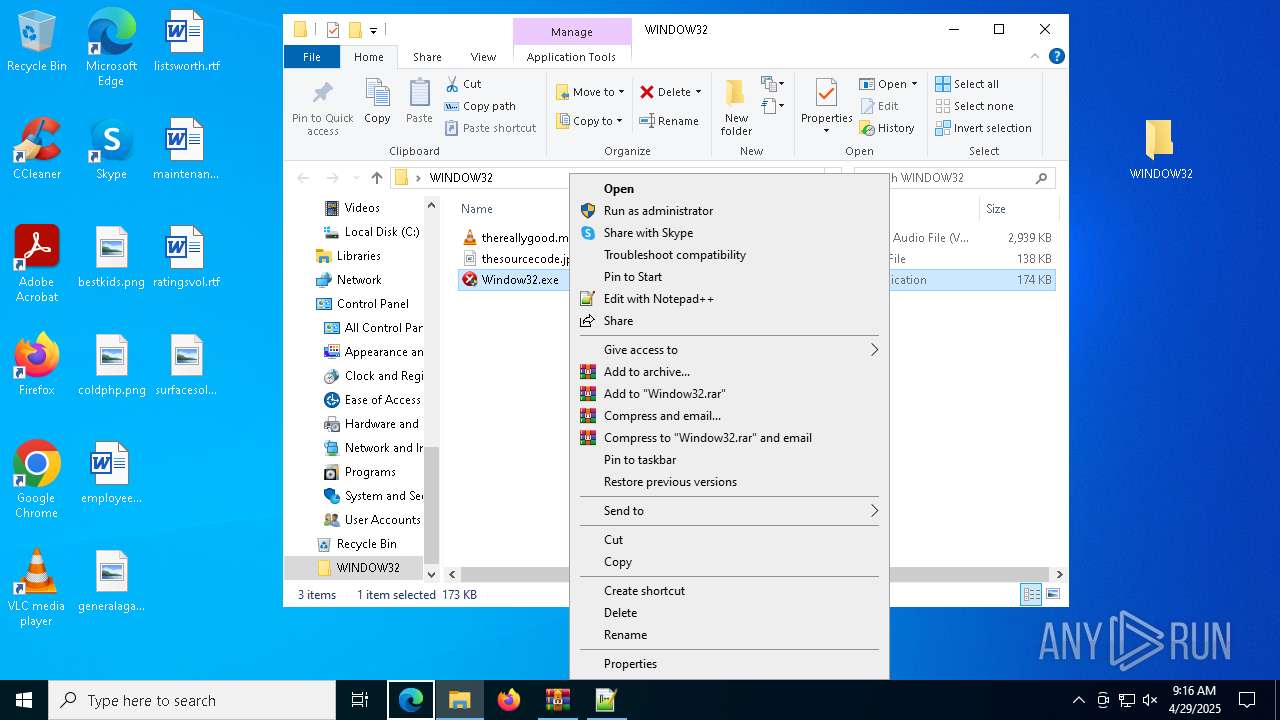
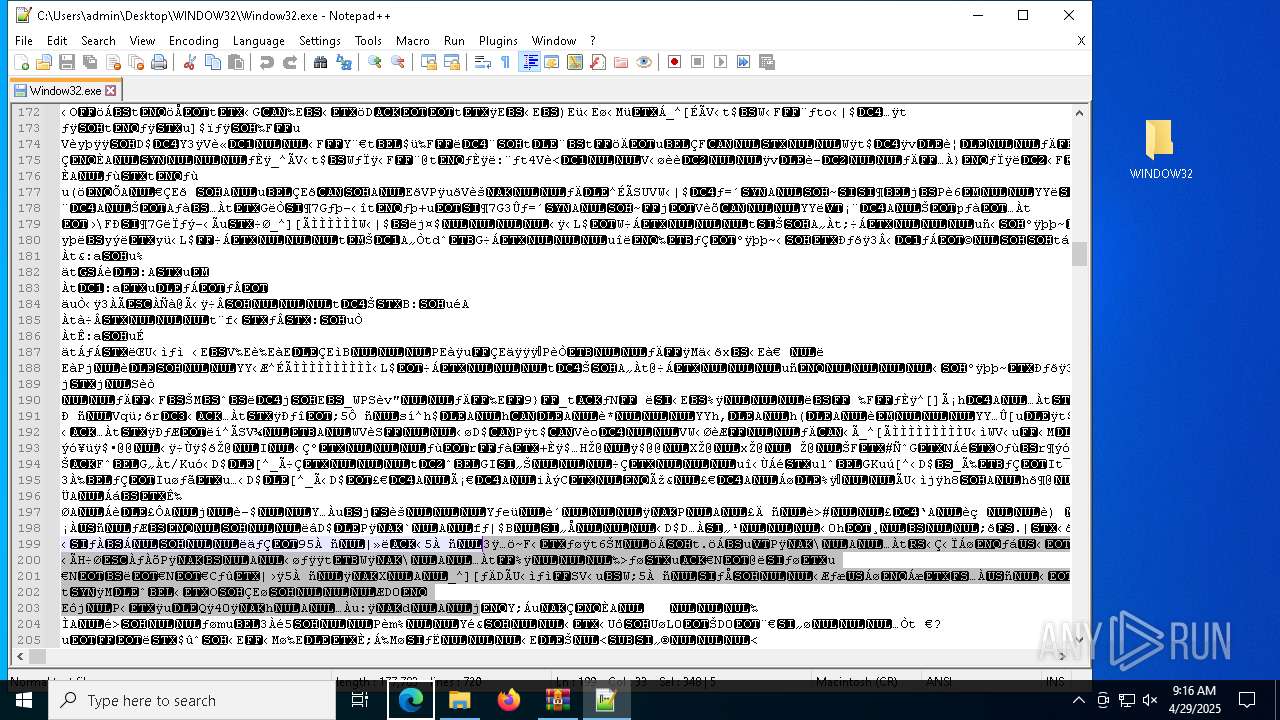
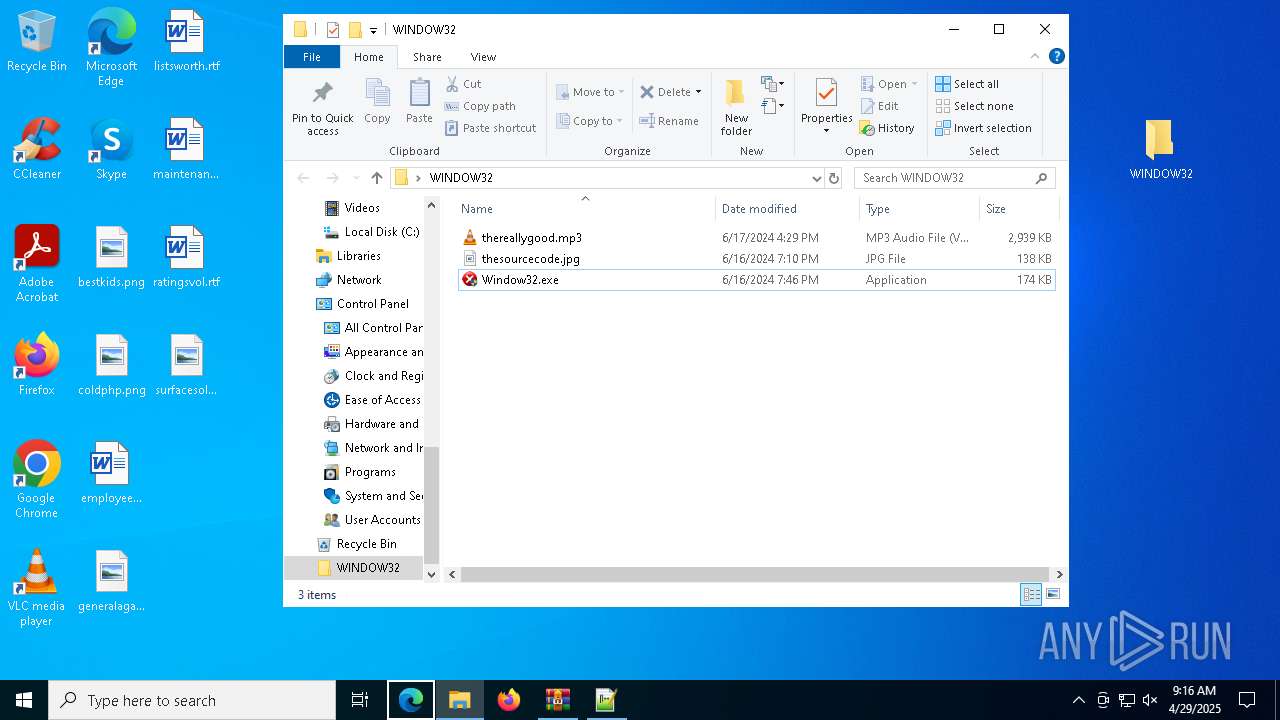
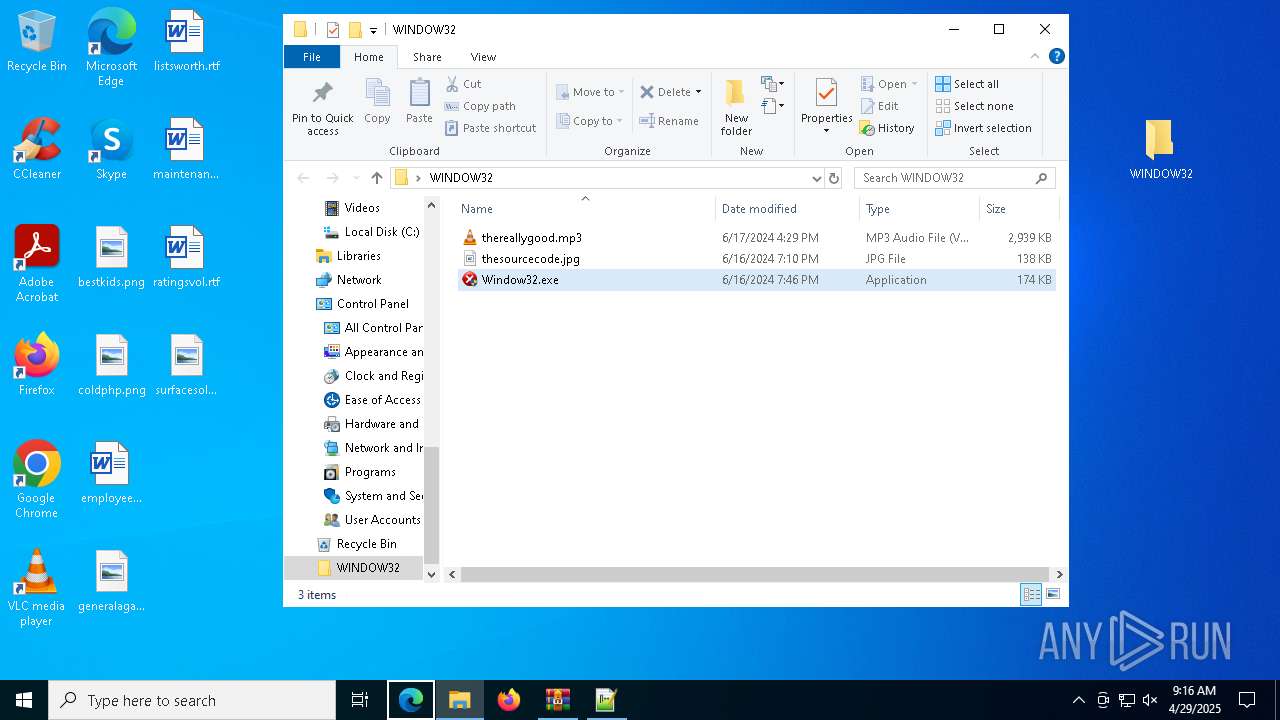
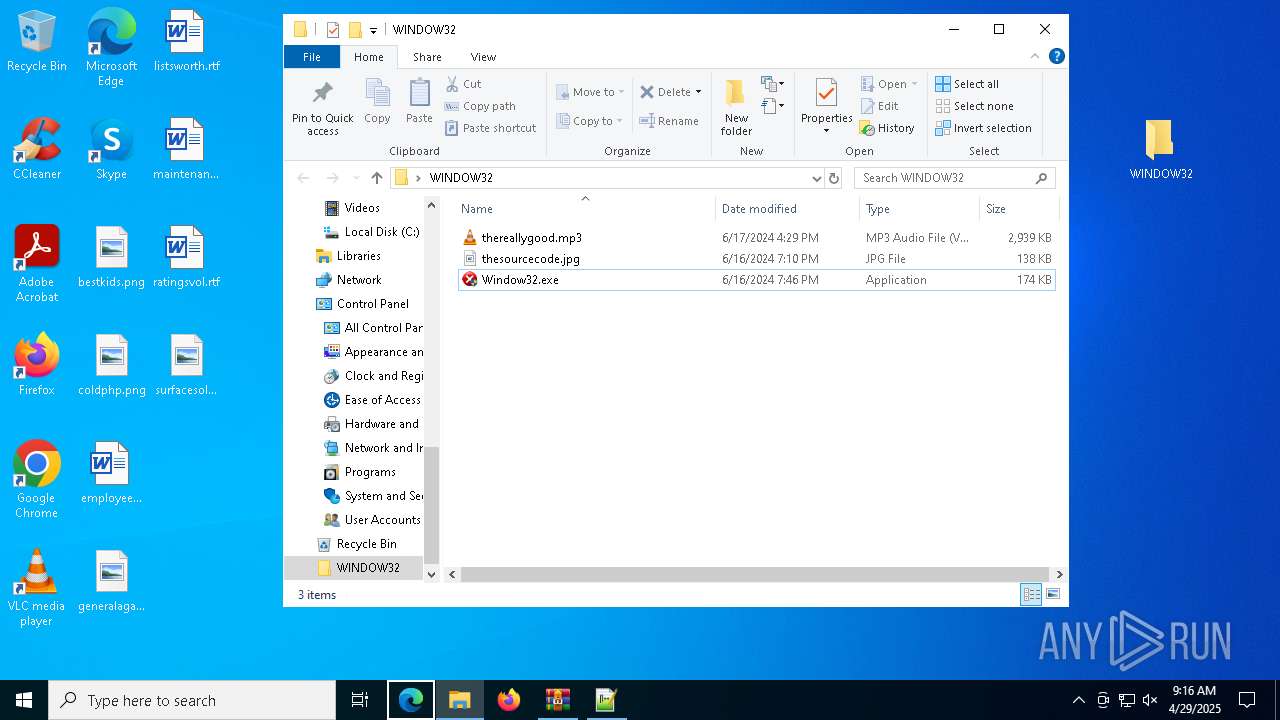
| File name: | WINDOW32original.zip |
| Full analysis: | https://app.any.run/tasks/746a8d1f-a70b-4df3-99b0-5418061953a5 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 09:11:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7B6E0AA039061CB5F634320E58163482 |
| SHA1: | 4C76D7812E046D6FB73185026D70A5BFBC916096 |
| SHA256: | EDFC95F8D981563EADC91A36A3D3A83AFF27018930E750CD8EFB5D726CB3B771 |
| SSDEEP: | 98304:XJSFwwrF5yvzJmWcRcBfhab+XnrFEagUC1rX2BzmX8SzpVxDwubG17XIFTN8BE3e:caQXikIV |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5556)
SUSPICIOUS
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6676)
- cmd.exe (PID: 6964)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 5972)
- cmd.exe (PID: 5384)
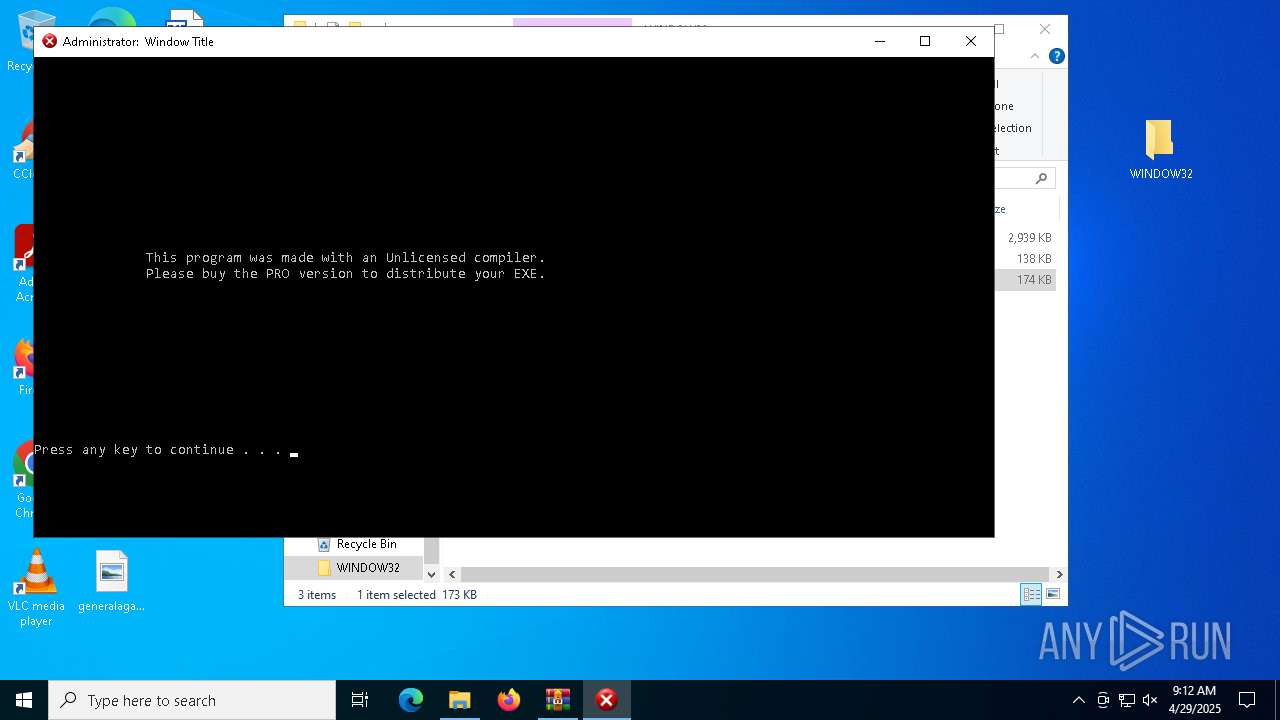
Starts CMD.EXE for commands execution
- Window32.exe (PID: 4448)
- Window32.exe (PID: 1052)
- Window32.exe (PID: 5776)
- Window32.exe (PID: 5228)
- Window32.exe (PID: 6972)
Executing commands from a ".bat" file
- Window32.exe (PID: 4448)
- Window32.exe (PID: 1052)
- Window32.exe (PID: 5228)
- Window32.exe (PID: 5776)
- Window32.exe (PID: 6972)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5244)
INFO
Creates a new folder
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 4944)
- cmd.exe (PID: 1512)
- cmd.exe (PID: 2100)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 6572)
Manual execution by a user
- Window32.exe (PID: 6800)
- Window32.exe (PID: 4448)
- Window32.exe (PID: 2772)
- Window32.exe (PID: 1052)
- Window32.exe (PID: 4408)
- Window32.exe (PID: 5776)
- Window32.exe (PID: 6972)
- Window32.exe (PID: 5376)
- Window32.exe (PID: 5228)
- notepad++.exe (PID: 6388)
- notepad++.exe (PID: 1280)
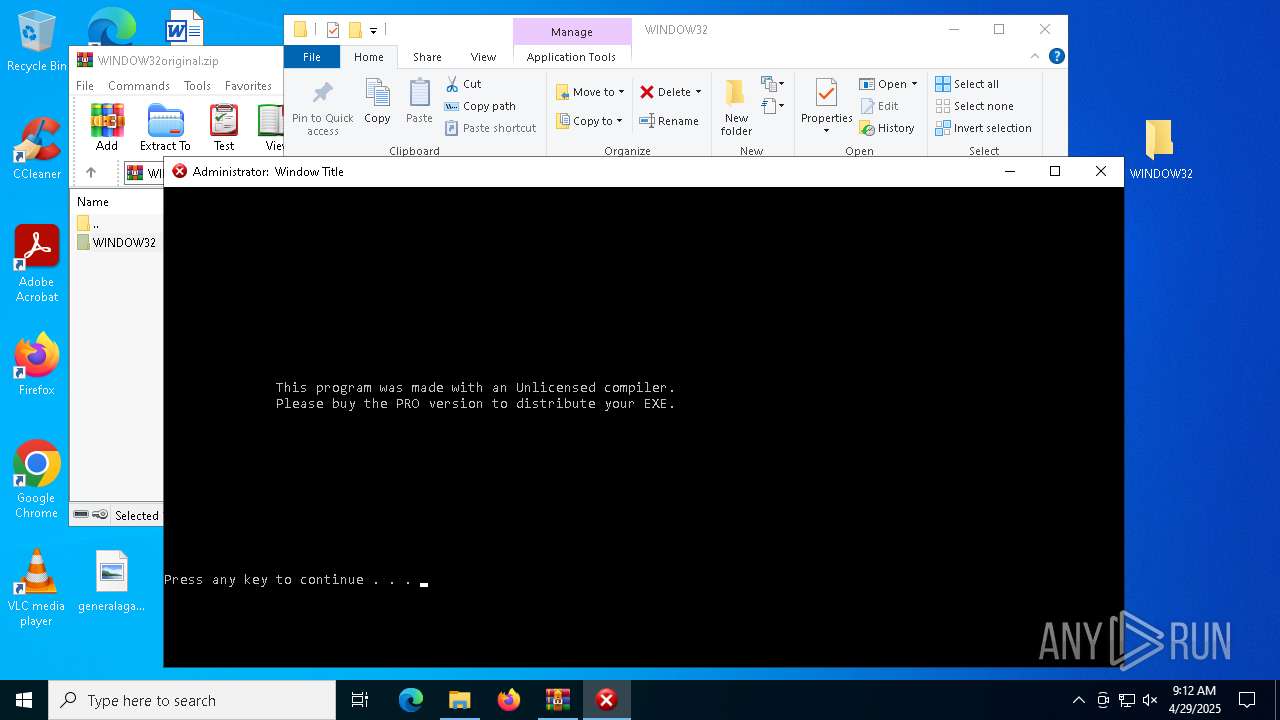
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5556)
Checks supported languages
- Window32.exe (PID: 4448)
- mode.com (PID: 900)
- ShellExperienceHost.exe (PID: 5244)
- Window32.exe (PID: 1052)
- mode.com (PID: 2852)
- mode.com (PID: 1328)
- Window32.exe (PID: 5776)
- mode.com (PID: 6752)
- Window32.exe (PID: 6972)
- Window32.exe (PID: 5228)
- mode.com (PID: 1188)
Starts MODE.COM to configure console settings
- mode.com (PID: 900)
- mode.com (PID: 2852)
- mode.com (PID: 1328)
- mode.com (PID: 6752)
- mode.com (PID: 1188)
Create files in a temporary directory
- Window32.exe (PID: 4448)
- Window32.exe (PID: 1052)
- Window32.exe (PID: 5228)
- Window32.exe (PID: 5776)
- Window32.exe (PID: 6972)
Reads the computer name
- ShellExperienceHost.exe (PID: 5244)
Reads the software policy settings
- slui.exe (PID: 2344)
- slui.exe (PID: 6032)
Checks proxy server information
- slui.exe (PID: 2344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:17 16:29:22 |
| ZipCRC: | 0xe9b03b5e |
| ZipCompressedSize: | 2976727 |
| ZipUncompressedSize: | 3009069 |
| ZipFileName: | WINDOW32/thereallygood.mp3 |
Total processes
219
Monitored processes
82
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Window32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | mode con:cols=0120 lines=0030 | C:\Windows\SysWOW64\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Window32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Desktop\WINDOW32\Window32.exe" | C:\Users\admin\Desktop\WINDOW32\Window32.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Window32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | C:\WINDOWS\system32\cmd.exe /c title Window Title | C:\Windows\SysWOW64\cmd.exe | — | Window32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | C:\WINDOWS\system32\cmd.exe /c if not exist "C:\Users\admin\AppData\Local\Temp\myfiles" mkdir "C:\Users\admin\AppData\Local\Temp\myfiles" | C:\Windows\SysWOW64\cmd.exe | — | Window32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | mode con:cols=0120 lines=0030 | C:\Windows\SysWOW64\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\WINDOW32\Window32.exe" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
Total events
4 740
Read events
4 732
Write events
8
Delete events
0
Modification events
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WINDOW32original.zip | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5556.22815\WINDOW32\thesourcecode.jpg | image | |
MD5:59DFD16D68640822293CC1071706BEBA | SHA256:60C823FF7B7050A6BA8939E325F3A2EAD4728FC79BDB8634F87A41592CB78A95 | |||
| 5556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5556.22815\WINDOW32\Window32.exe | executable | |
MD5:9E457094CE318629A2F49B820A9365A1 | SHA256:A2C7BF22C4D0DC62C2AFC24AD989892B1C3371FD3423DF86F099AB7E0C8D010D | |||
| 5556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5556.22815\WINDOW32\thereallygood.mp3 | binary | |
MD5:767DF561533B6E9307A3B16621D38445 | SHA256:6425FC44CED7735BC440AEB8FFBFF72A474A290A07DD1F4FE448DA35BD586C77 | |||
| 1852 | cmd.exe | C:\Users\admin\AppData\Local\Temp\i6.t | text | |
MD5:21438EF4B9AD4FC266B6129A2F60DE29 | SHA256:13BF7B3039C63BF5A50491FA3CFD8EB4E699D1BA1436315AEF9CBE5711530354 | |||
| 6388 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 5260 | cmd.exe | C:\Users\admin\AppData\Local\Temp\i6.f | text | |
MD5:FBB567216D6FA2A929F4FE2389740816 | SHA256:D10A6587021A36C1AF3B558DE7D5BDE0C047D0C494454C1ED08B6A19BBCF842A | |||
| 6388 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 4448 | Window32.exe | C:\Users\admin\AppData\Local\Temp\i6.bat | text | |
MD5:1AF1AB0E1E623C11529763D3016C0818 | SHA256:57F6713E8C793D5D81FBBF2E16DB7098B1D5A3A608915E62468F2435DAFBFD85 | |||
| 6388 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 6388 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.52.56.216:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6572 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6572 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.52.56.216:80 | ocsp.digicert.com | AKAMAI-AS | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6572 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |