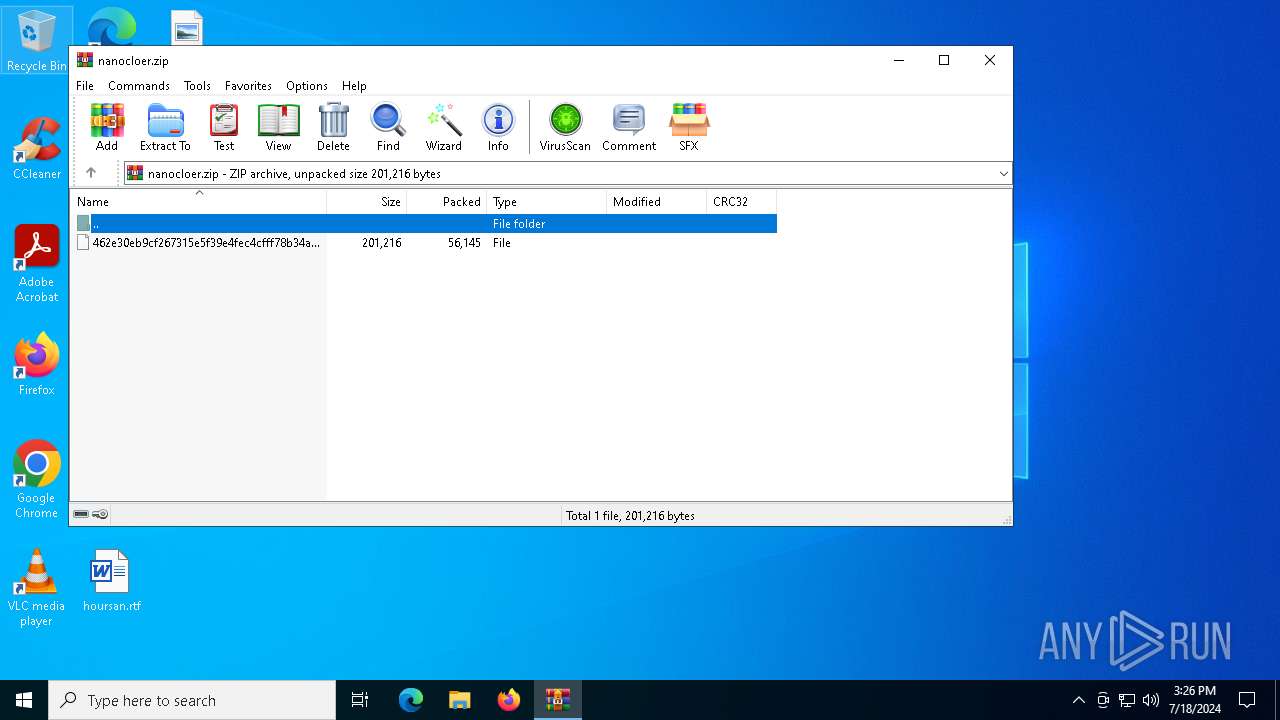
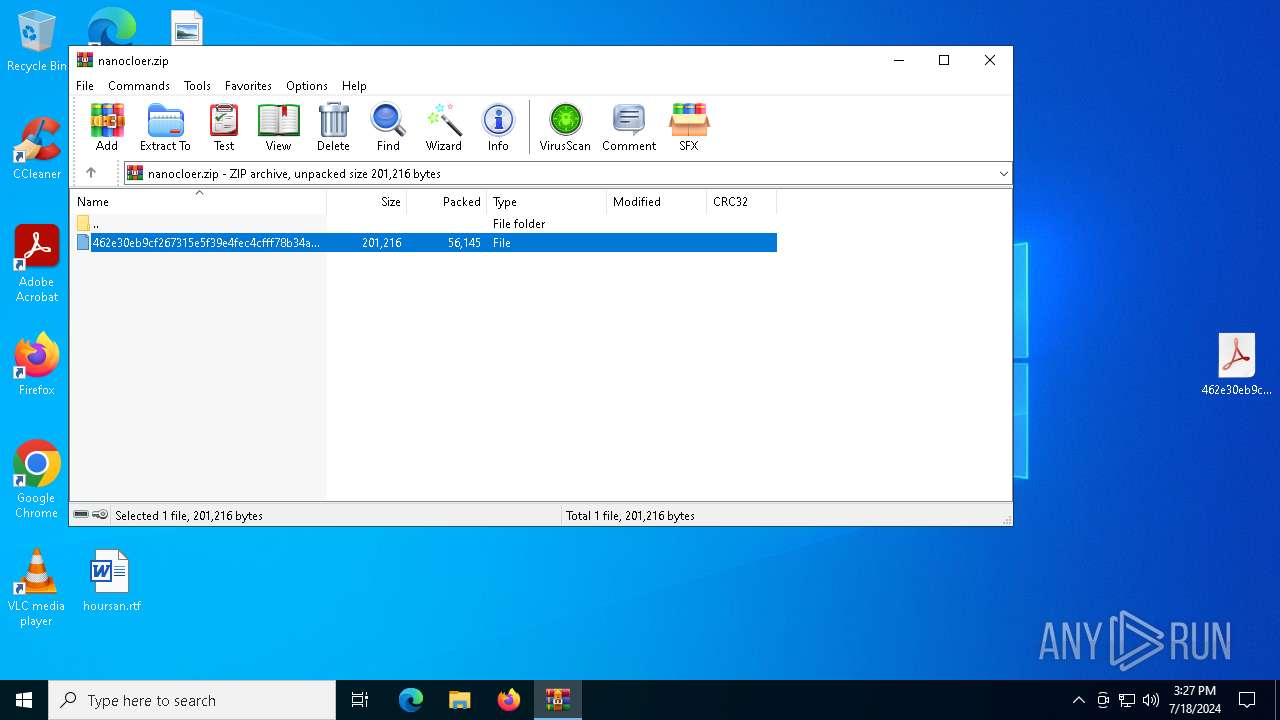
| File name: | nanocloer.zip |
| Full analysis: | https://app.any.run/tasks/3c1540cb-72ac-4669-a4ea-dd4b4942c841 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2024, 15:26:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
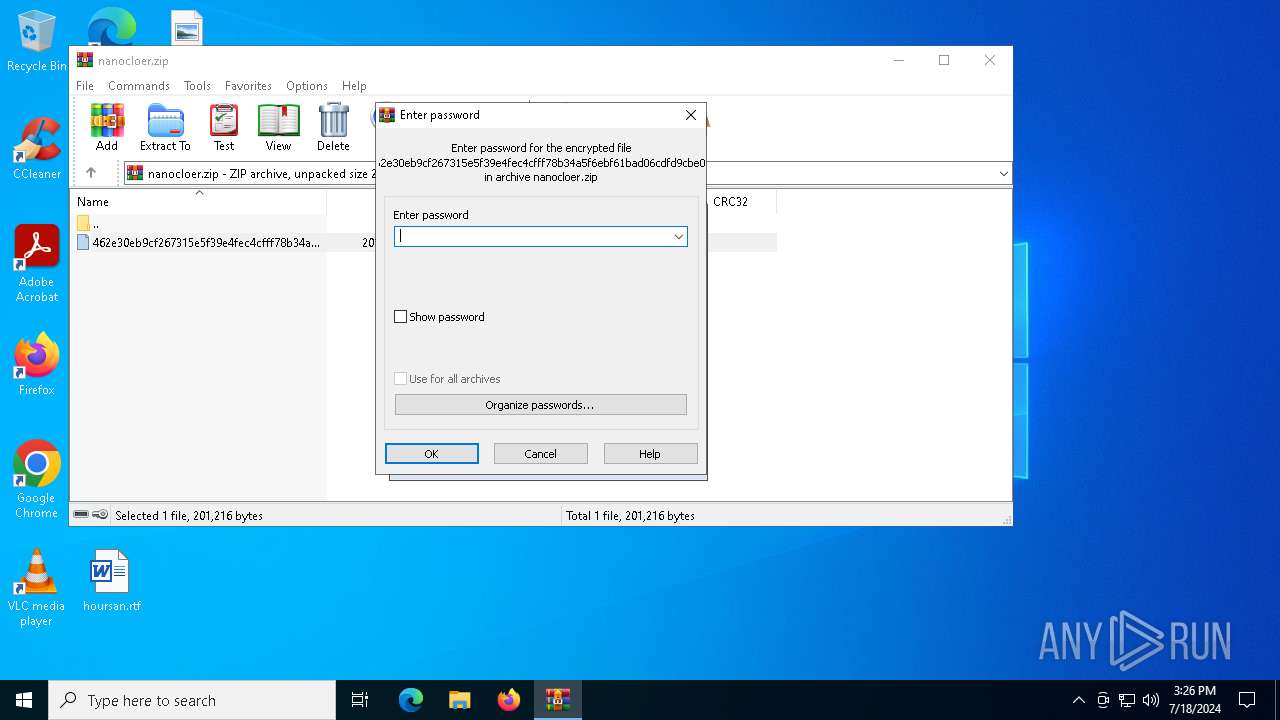
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | AFD8ED859CEF9F51B550C0A3D27A967E |
| SHA1: | 6E939E64DEB01C12D6976F7DFA39CD3F4175D505 |
| SHA256: | EDF2FEE744E8B3E86D1FF84D3602BA7030D86E3A899AAB7DCC2FF61B30FEE371 |
| SSDEEP: | 1536:6CbnZqgF9CvxV3SscbEhFkG0lIql8/y11wK3fC/d6C5:6CjZxmxQEhKG0uqcOwqC/n5 |
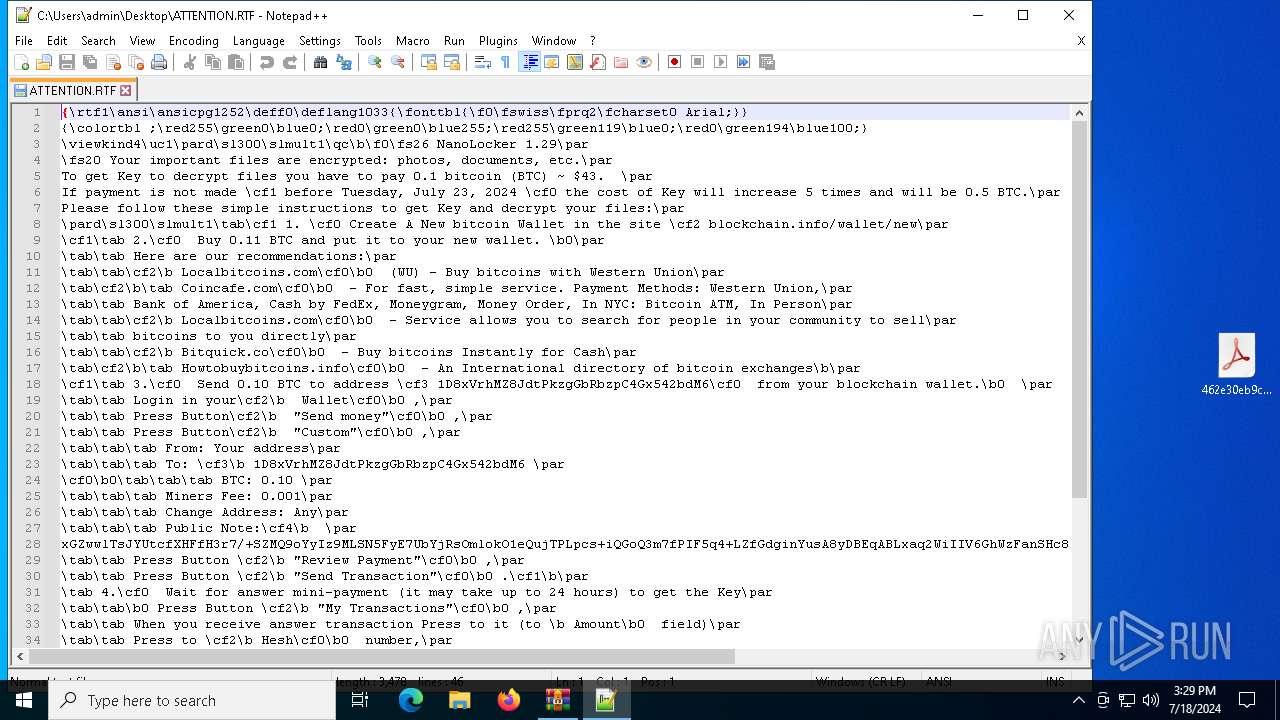
MALICIOUS
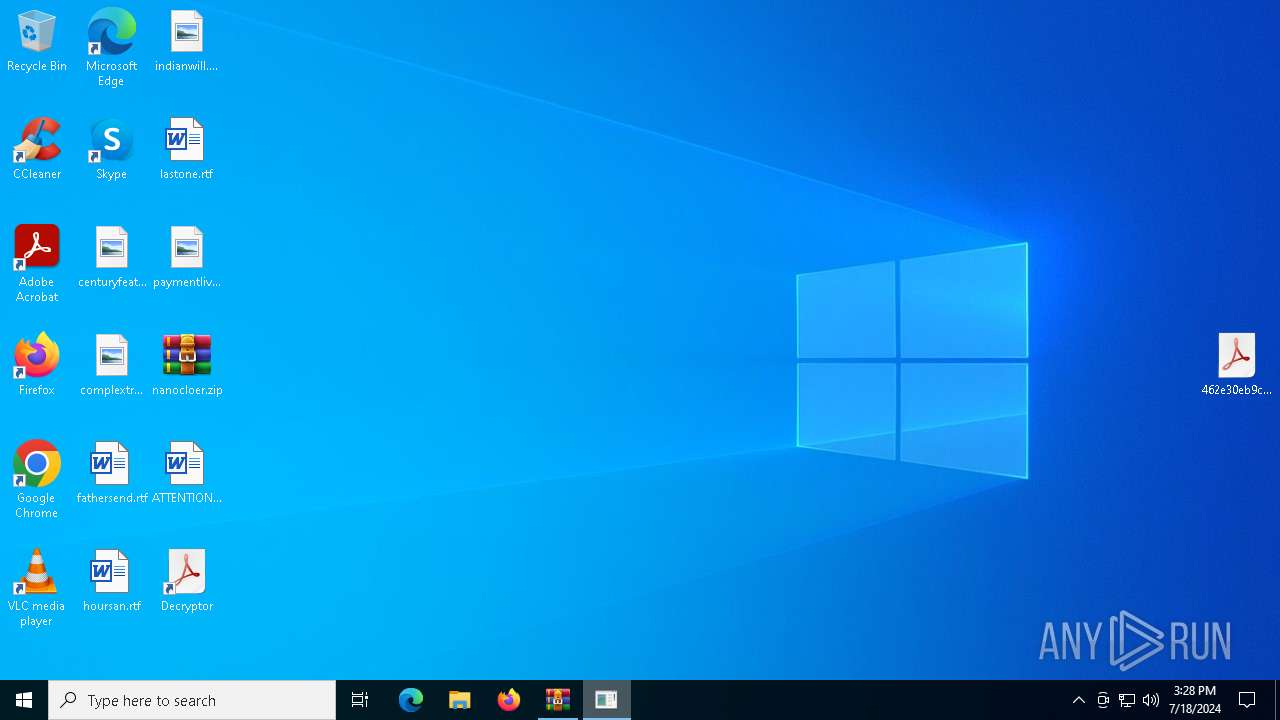
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7948)
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
Changes the autorun value in the registry
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
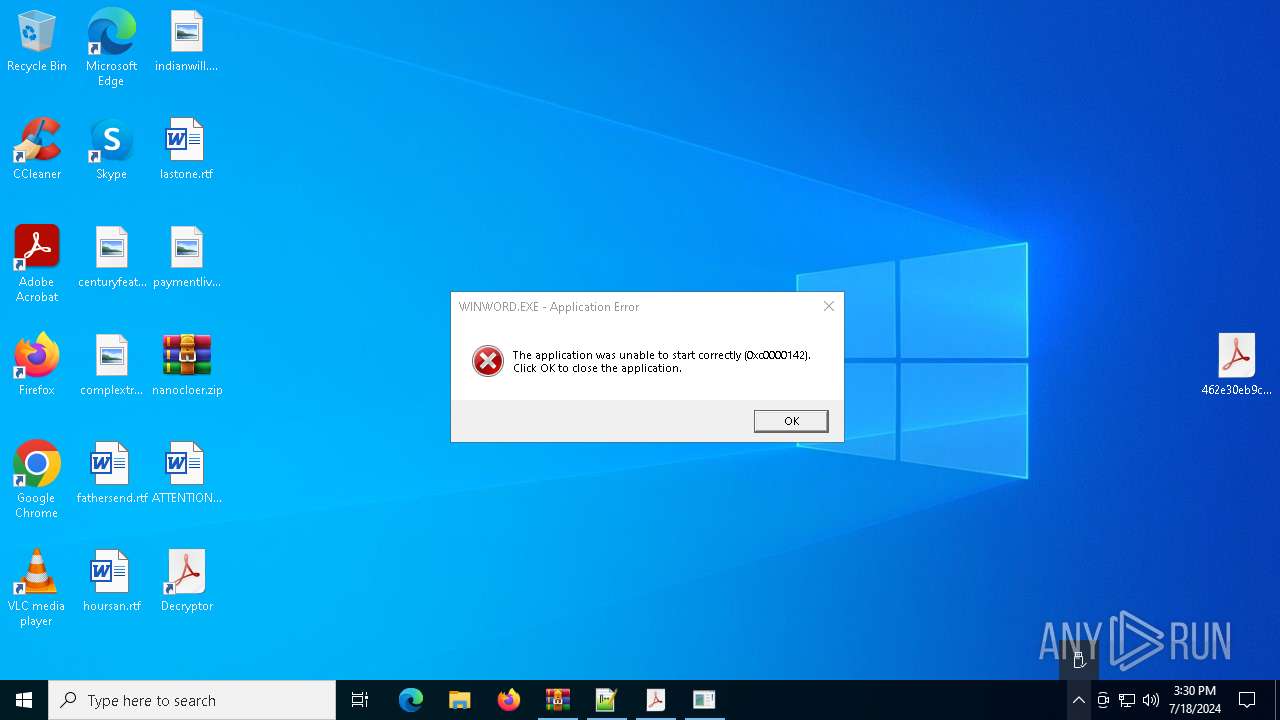
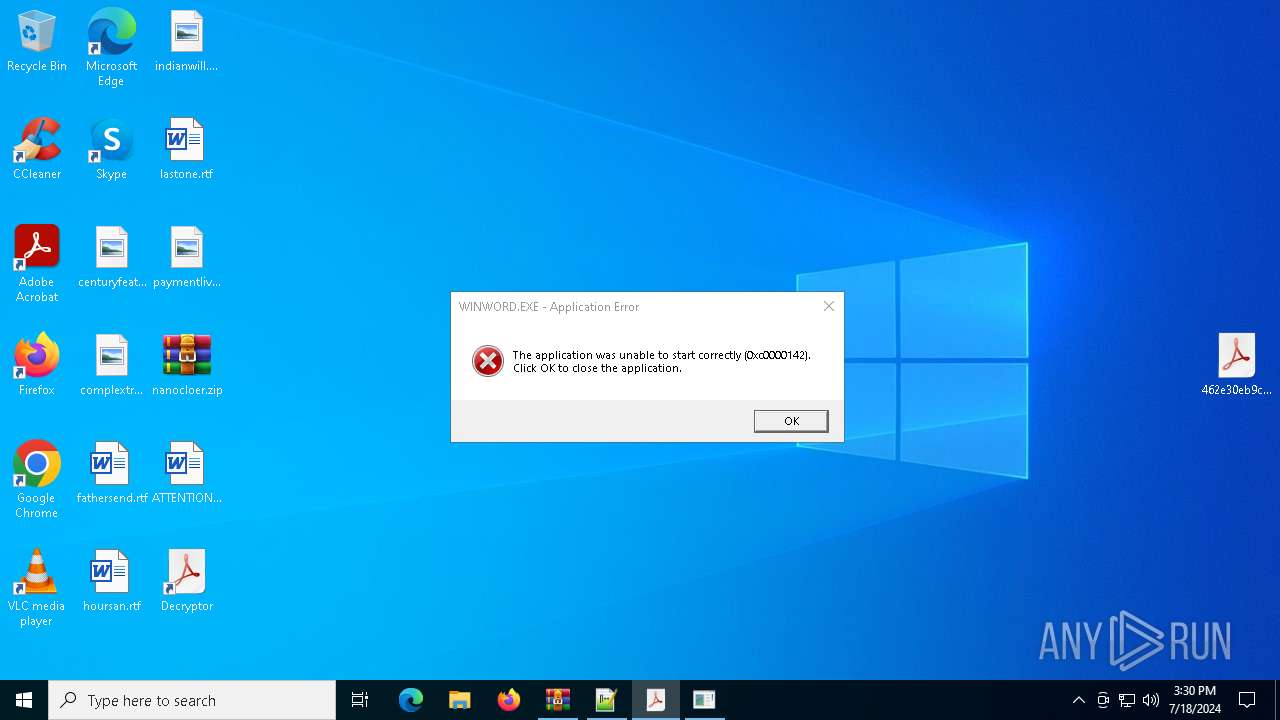
Unusual execution from MS Office
- WINWORD.EXE (PID: 7440)
- WINWORD.EXE (PID: 5244)
Actions looks like stealing of personal data
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
SUSPICIOUS
Executable content was dropped or overwritten
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 972)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7948)
Creates files or folders in the user directory
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
Checks supported languages
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
Manual execution by a user
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
- lansrv.exe (PID: 7224)
- WINWORD.EXE (PID: 5244)
- WINWORD.EXE (PID: 7440)
- lansrv.exe (PID: 4020)
- notepad++.exe (PID: 3836)
Reads the computer name
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
Reads the machine GUID from the registry
- 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe (PID: 7044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 56145 |
| ZipUncompressedSize: | 201216 |
| ZipFileName: | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a |
Total processes
133
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 972 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.16026.20140 | |||||||||||||||
| 1020 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3328 | OfficeC2RClient.exe /error PID=5244 ProcessName="Microsoft Word" UIType=3 ErrorSource=0x8b10082a ErrorCode=0xc00cee2d ShowUI=1 | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeC2RClient.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Click-to-Run Client Exit code: 0 Version: 16.0.16026.20140 | |||||||||||||||
| 3836 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\ATTENTION.RTF" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 | |||||||||||||||
| 4020 | "C:\Users\admin\AppData\Local\lansrv.exe" | C:\Users\admin\AppData\Local\lansrv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM | |||||||||||||||
| 5244 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\ATTENTION.RTF" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 3221225794 Version: 16.0.16026.20146 | |||||||||||||||
| 5492 | OfficeC2RClient.exe /error PID=7440 ProcessName="Microsoft Word" UIType=3 ErrorSource=0x8b10082a ErrorCode=0xc00cee2d ShowUI=1 | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeC2RClient.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Click-to-Run Client Exit code: 0 Version: 16.0.16026.20140 | |||||||||||||||
| 7044 | "C:\Users\admin\Desktop\462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe" | C:\Users\admin\Desktop\462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 7224 | "C:\Users\admin\AppData\Local\lansrv.exe" | C:\Users\admin\AppData\Local\lansrv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 656116 | |||||||||||||||
| 7440 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /vu "C:\Users\admin\Desktop\ATTENTION.RTF" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 | |||||||||||||||
Total events
3 641
Read events
3 631
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\nanocloer.zip | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7044) 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | LanmanServer |
Value: C:\Users\admin\AppData\Local\lansrv.exe | |||
Executable files
2
Suspicious files
522
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\lansrv.exe | executable | |
MD5:FCE023BE1FB28B656E419C5C817DEB73 | SHA256:462E30EB9CF267315E5F39E4FEC4CFFF78B34A5F6EBF61BAD06CDFD9CBE0A06A | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\lansrv.ini | binary | |
MD5:AC883E28369D8E13046CD5D7804080B0 | SHA256:4B3140E08AB9E8CA88A129E7DCA6C719D25C31770CBC7B249FAC71B5B8206532 | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Celestial_V2_960_1b011c282433a37463b96c8587dc3874.jpg | binary | |
MD5:B89936E610092604506442AD5D2E012C | SHA256:E53F3951F3C02C448C4169148E8ABFAB1CB8D5B7CA7BEDE5C8C2720C1AEA48D6 | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Fete_960_58955bd483e88501127f602a7272805b.jpg | binary | |
MD5:6E00056A7EEAE865359F14B49D1D03FE | SHA256:5B018323B0E0DA93007A37623F2E655BC62CE3CFAC905095FF4D7B1624F15F9D | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Fluent_2k_a1e4f5bb63098c45ac83afc5ed6e7c08.jpg | binary | |
MD5:C35B872AE282BCD9441CDBD19242F094 | SHA256:03EA96696F35069A4479E87C19B455A9743722C29F012069B5865CE17E6C73A3 | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\BoutiqueDark_960_2670632012cab762c1b532bbae7ce357.jpg | binary | |
MD5:5D77040EEB8F9C8C99F9997874E45334 | SHA256:985618F18CEF434445EA32442EF18278E8FE87C9111761503444EE1FC4FC12AC | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Bokeh_V2_960_4a9e6622fd62a84a258eb269895a094c.jpg | binary | |
MD5:537A81F259DCFBF94ABBA247AB72E286 | SHA256:3AC1B900A5D4688618540BFC58E82CEE46C558914D189D24F5BAC5371704052E | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Lucent_960_45a6dba5a0d070b7aa3cf5b8bea87687.jpg | binary | |
MD5:B2847046A441E094F0A7DCD36CC6CCFE | SHA256:D4720BA2D27BA7FD37E37B145CA6DA537A2319623332C2CB245CD6C8092677A3 | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Fluent_864_bf384ed42f878a0cff607687a6bb7590.jpg | binary | |
MD5:15CB3FF8E65D6D2B8FFB4A493EF41AE1 | SHA256:3CCE04FEA85281F5939D768EE5394AFF77FE315FD71EACA565E9593D175A0B15 | |||
| 7044 | 462e30eb9cf267315e5f39e4fec4cfff78b34a5f6ebf61bad06cdfd9cbe0a06a.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\4404078e2dabd634eb723d7c3b67cf69\PackageResources\OfflineFiles\Midtown_960_bb7c730287ec352c0c5ad6e32d882859.jpg | binary | |
MD5:FFD1FB1A278EC70A9C24B7E68F646185 | SHA256:103EA012B8F520F7CA790D7C60C9694AB4011E6324A0C91F91075C11A4BFB0AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
24
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7484 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4716 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7484 | backgroundTaskHost.exe | 20.223.36.55:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5948 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
arc.msn.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET MALWARE NanoLocker Check-in (ICMP) M1 |