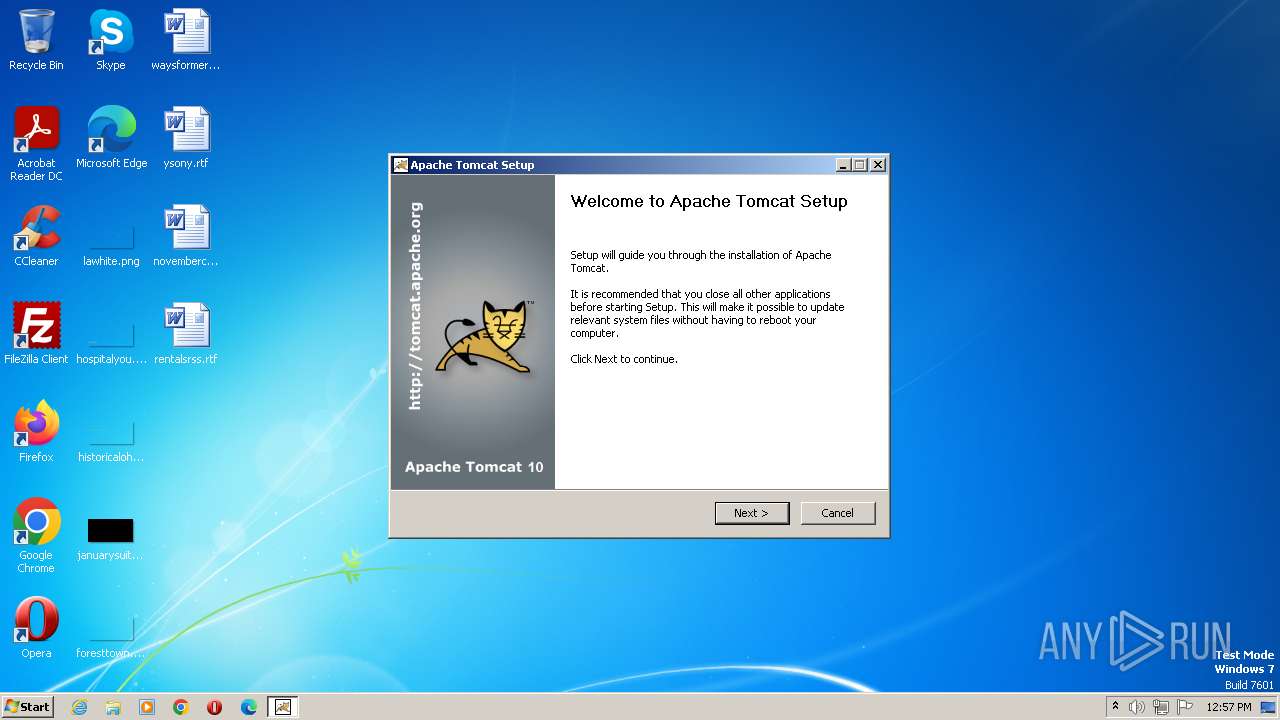
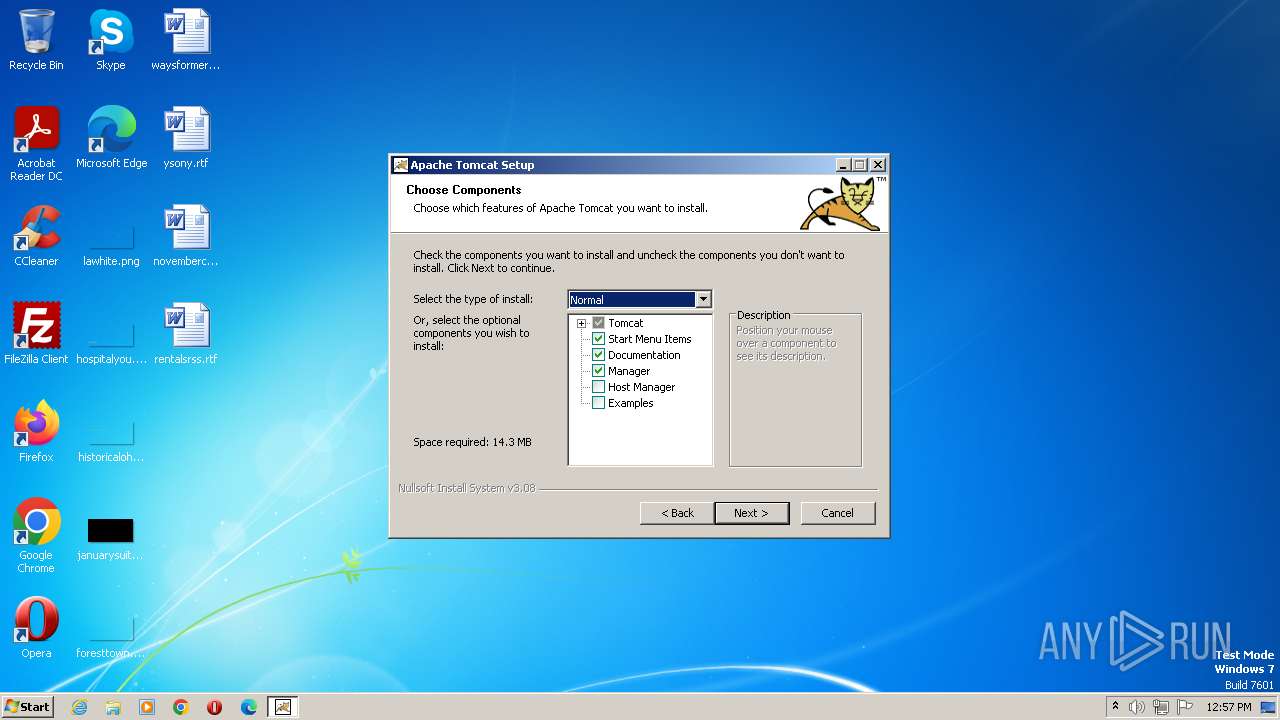
| File name: | apache-tomcat-10.1.11.exe |
| Full analysis: | https://app.any.run/tasks/f5b7d72b-29e7-4c8a-812b-19d36323587d |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2023, 11:56:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | DE2E4687E9E0C5101B2C345F9F4F15B1 |
| SHA1: | DF1E17EA714AFF3AB32ED3A9FD161F79962E1485 |
| SHA256: | EDB87BC6A1094708F5AA89F65A50016894164D76F301E16C96BB5C68F6587CAE |
| SSDEEP: | 393216:TqaT84OTndjSkWY+UYUCoVrue47gsurqZ23ZnVI402aFX4Xfp1B3:TqaQjfYUCoVtkZ2pnVO27Tt |
MALICIOUS
Application was dropped or rewritten from another process
- Tomcat10w.exe (PID: 1236)
- Tomcat10.exe (PID: 2472)
- Tomcat10.exe (PID: 2100)
- Tomcat10.exe (PID: 3852)
- Tomcat10.exe (PID: 2356)
- Tomcat10.exe (PID: 2808)
- Tomcat10.exe (PID: 1412)
Loads dropped or rewritten executable
- apache-tomcat-10.1.11.exe (PID: 540)
SUSPICIOUS
Starts application with an unusual extension
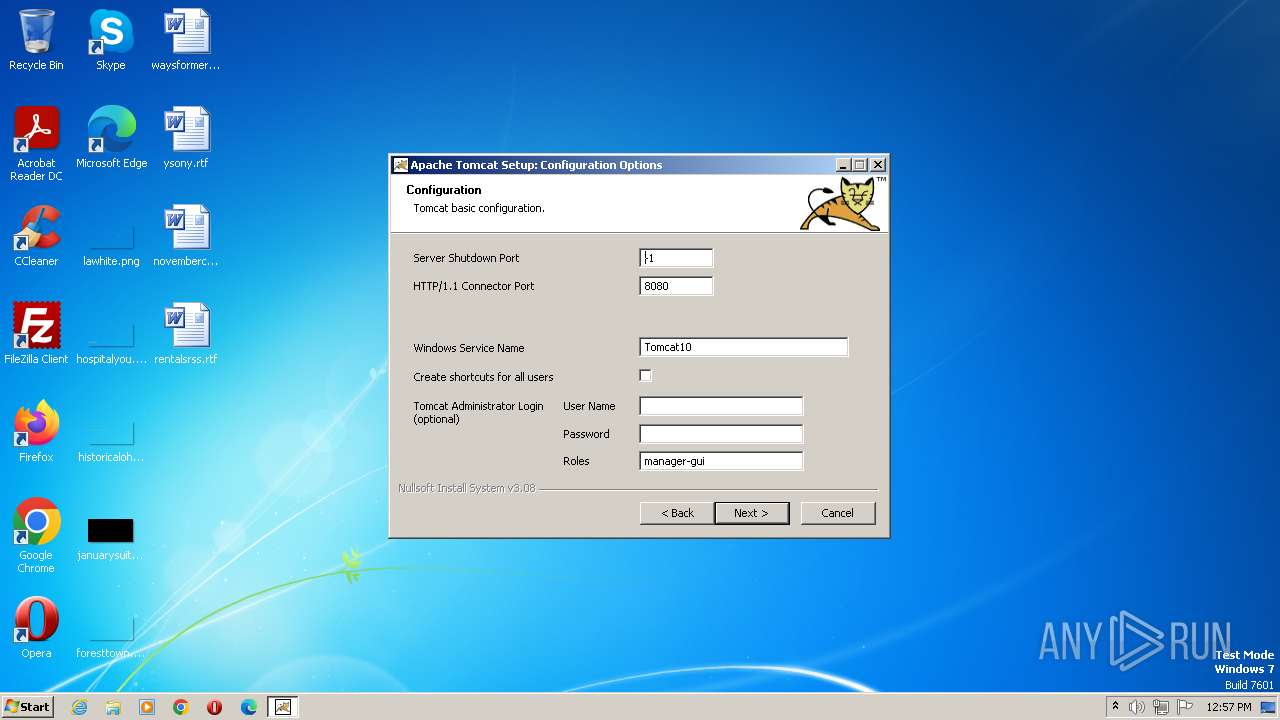
- apache-tomcat-10.1.11.exe (PID: 540)
The process creates files with name similar to system file names
- apache-tomcat-10.1.11.exe (PID: 540)
Executable content was dropped or overwritten
- apache-tomcat-10.1.11.exe (PID: 540)
Checks for Java to be installed
- apache-tomcat-10.1.11.exe (PID: 540)
Reads the Internet Settings
- apache-tomcat-10.1.11.exe (PID: 540)
Uses ICACLS.EXE to modify access control lists
- nsC3BC.tmp (PID: 2364)
- nsC43A.tmp (PID: 1832)
- nsC4B8.tmp (PID: 2124)
Executes as Windows Service
- Tomcat10.exe (PID: 2808)
INFO
The process checks LSA protection
- Tomcat10.exe (PID: 2100)
- Tomcat10.exe (PID: 2472)
- apache-tomcat-10.1.11.exe (PID: 540)
- Tomcat10.exe (PID: 3852)
- Tomcat10.exe (PID: 1412)
- Tomcat10.exe (PID: 2356)
- icacls.exe (PID: 2692)
- icacls.exe (PID: 3240)
- icacls.exe (PID: 3404)
- icacls.exe (PID: 1856)
Reads the computer name
- Tomcat10.exe (PID: 2472)
- apache-tomcat-10.1.11.exe (PID: 540)
- Tomcat10.exe (PID: 3852)
- Tomcat10.exe (PID: 2356)
- Tomcat10.exe (PID: 2100)
- Tomcat10.exe (PID: 1412)
- Tomcat10w.exe (PID: 1236)
- Tomcat10.exe (PID: 2808)
Checks supported languages
- nsBCC2.tmp (PID: 1140)
- Tomcat10.exe (PID: 2472)
- nsC147.tmp (PID: 3052)
- nsC1C5.tmp (PID: 2564)
- apache-tomcat-10.1.11.exe (PID: 540)
- nsC234.tmp (PID: 3516)
- Tomcat10.exe (PID: 1412)
- nsC2A2.tmp (PID: 1052)
- Tomcat10.exe (PID: 2356)
- nsC43A.tmp (PID: 1832)
- nsC3BC.tmp (PID: 2364)
- nsC4B8.tmp (PID: 2124)
- Tomcat10w.exe (PID: 1236)
- Tomcat10.exe (PID: 2808)
- Tomcat10.exe (PID: 2100)
- Tomcat10.exe (PID: 3852)
Create files in a temporary directory
- apache-tomcat-10.1.11.exe (PID: 540)
Creates files in the program directory
- apache-tomcat-10.1.11.exe (PID: 540)
- Tomcat10.exe (PID: 2808)
Creates files or folders in the user directory
- apache-tomcat-10.1.11.exe (PID: 540)
Manual execution by a user
- WINWORD.EXE (PID: 3388)
- WINWORD.EXE (PID: 3844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (52.5) |
|---|---|---|
| .scr | | | Windows screen saver (22) |
| .dll | | | Win32 Dynamic Link Library (generic) (11) |
| .exe | | | Win32 Executable (generic) (7.5) |
| .exe | | | Generic Win/DOS Executable (3.3) |
EXIF
EXE
| ProductVersion: | 10.1.11 |
|---|---|
| ProductName: | Apache Tomcat |
| LegalCopyright: | Copyright (c) 1999-2023 The Apache Software Foundation |
| InternalName: | apache-tomcat-10.1.11.exe |
| FileVersion: | 2 |
| FileDescription: | Apache Tomcat Installer |
| CompanyName: | Apache Software Foundation |
| Comments: | tomcat.apache.org |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 10.1.11.0 |
| FileVersionNumber: | 10.1.11.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x3640 |
| UninitializedDataSize: | 2048 |
| InitializedDataSize: | 141824 |
| CodeSize: | 26624 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| TimeStamp: | 2021:09:25 21:56:47+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 25-Sep-2021 21:56:47 |
| Detected languages: |
|
| Comments: | tomcat.apache.org |
| CompanyName: | Apache Software Foundation |
| FileDescription: | Apache Tomcat Installer |
| FileVersion: | 2.0 |
| InternalName: | apache-tomcat-10.1.11.exe |
| LegalCopyright: | Copyright (c) 1999-2023 The Apache Software Foundation |
| ProductName: | Apache Tomcat |
| ProductVersion: | 10.1.11 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 25-Sep-2021 21:56:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006676 | 0x00006800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.41746 |
.rdata | 0x00008000 | 0x0000139A | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.14107 |
.data | 0x0000A000 | 0x00020378 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.11058 |
.ndata | 0x0002B000 | 0x0003A000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00065000 | 0x00006D98 | 0x00006E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.38582 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28834 | 1070 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.58585 | 3752 | UNKNOWN | English - United States | RT_ICON |
3 | 4.1463 | 3240 | UNKNOWN | English - United States | RT_ICON |
4 | 3.71606 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 2.64646 | 1640 | UNKNOWN | English - United States | RT_ICON |
6 | 2.71436 | 1384 | UNKNOWN | English - United States | RT_ICON |
7 | 4.23914 | 872 | UNKNOWN | English - United States | RT_ICON |
8 | 2.95894 | 744 | UNKNOWN | English - United States | RT_ICON |
9 | 2.78721 | 296 | UNKNOWN | English - United States | RT_ICON |
102 | 2.71813 | 180 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
71
Monitored processes
23
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\AppData\Local\Temp\apache-tomcat-10.1.11.exe" | C:\Users\admin\AppData\Local\Temp\apache-tomcat-10.1.11.exe | explorer.exe | ||||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Apache Tomcat Installer Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsC2A2.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe" //US//Tomcat10 --StdOutput auto --StdError auto --JvmMs 128 --JvmMx 256 | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsC2A2.tmp | — | apache-tomcat-10.1.11.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsBCC2.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe" //IS//Tomcat10 --DisplayName "Apache Tomcat 10.1 Tomcat10" --Description "Apache Tomcat 10.1.11 Server - https://tomcat.apache.org/" --LogPath "C:\Program Files\Apache Software Foundation\Tomcat 10.1\logs" --Install "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe" --Jvm "C:\Program Files\Java\jre1.8.0_271\bin\client\jvm.dll" --StartPath "C:\Program Files\Apache Software Foundation\Tomcat 10.1" --StopPath "C:\Program Files\Apache Software Foundation\Tomcat 10.1" | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsBCC2.tmp | — | apache-tomcat-10.1.11.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10w.exe" //MR//Tomcat10 | C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10w.exe | — | apache-tomcat-10.1.11.exe | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Apache Commons Daemon Service Manager Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
| 1412 | "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe" //US//Tomcat10 --JvmOptions9 "--add-opens=java.base/java.lang=ALL-UNNAMED#--add-opens=java.base/java.io=ALL-UNNAMED#--add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED" | C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe | — | nsC234.tmp | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Apache Commons Daemon Service Runner Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsC43A.tmp" icacls "C:\Program Files\Apache Software Foundation\Tomcat 10.1\tomcat.ico" /inheritance:e /grant *S-1-5-11:(R) | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsC43A.tmp | — | apache-tomcat-10.1.11.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1856 | icacls "C:\Program Files\Apache Software Foundation\Tomcat 10.1\tomcat.ico" /inheritance:e /grant *S-1-5-11:(R) | C:\Windows\System32\icacls.exe | — | nsC43A.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe" //US//Tomcat10 --JvmOptions "-Dcatalina.home=C:\Program Files\Apache Software Foundation\Tomcat 10.1#-Dcatalina.base=C:\Program Files\Apache Software Foundation\Tomcat 10.1#-Djava.io.tmpdir=C:\Program Files\Apache Software Foundation\Tomcat 10.1\temp#-Djava.util.logging.manager=org.apache.juli.ClassLoaderLogManager#-Djava.util.logging.config.file=C:\Program Files\Apache Software Foundation\Tomcat 10.1\conf\logging.properties" | C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe | — | nsC1C5.tmp | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Apache Commons Daemon Service Runner Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsC4B8.tmp" icacls "C:\Program Files\Apache Software Foundation\Tomcat 10.1\Uninstall.exe" /inheritance:e /grant *S-1-5-11:(RX) | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\nsC4B8.tmp | — | apache-tomcat-10.1.11.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe" //US//Tomcat10 --StdOutput auto --StdError auto --JvmMs 128 --JvmMx 256 | C:\Program Files\Apache Software Foundation\Tomcat 10.1\bin\Tomcat10.exe | — | nsC2A2.tmp | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Apache Commons Daemon Service Runner Exit code: 0 Version: 1.3.4.0 Modules
| |||||||||||||||
Total events
6 044
Read events
5 695
Write events
74
Delete events
275
Modification events
| (PID) Process: | (540) apache-tomcat-10.1.11.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (540) apache-tomcat-10.1.11.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (540) apache-tomcat-10.1.11.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (540) apache-tomcat-10.1.11.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3388) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
Executable files
51
Suspicious files
5
Text files
194
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\LICENSE | text | |
MD5:6A6F8BDE24E7FC53AE56DB0DDFBDC76A | SHA256:EBE598B4197B0EA1DD24A8569A3865B6B622E3C2DB47BDD61CF1F4B35CF54038 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\modern-wizard.bmp | image | |
MD5:E8F7993C6AC99314393499863E18B4C7 | SHA256:9E700B8009506B81EEAB6EB9D2AA55954CB28750B550563792BF59A603B17BD5 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Users\admin\AppData\Local\Temp\nsh9841.tmp\modern-header.bmp | image | |
MD5:46F339AA9B187E4B5736DEA11883AEB6 | SHA256:82F819B9281F6A7799A3A000F03555B52E6AF990E2D9B2F68A5A82045681951A | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\lib\jasper.jar | java | |
MD5:C52C65D8AA8DE2229B7EB5B2CC0C01D1 | SHA256:906E8622C5EDB1520FB390778D1FA8F8EEC91837C59465BE1851016E99993AD0 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\lib\catalina-ssi.jar | java | |
MD5:D55E6085210571C5862D68877C4948CD | SHA256:74262301AF02D0BF569518EA84BC454FBDC9CCC2723857198171CC5AEFBADA01 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\lib\catalina-tribes.jar | java | |
MD5:187B94D156DDC8DD90169CCD1053CE9A | SHA256:B29767E1FF066CEACB9FD8B251F63D19AD6398BF326E070177D248B78F32BFF5 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\lib\el-api.jar | java | |
MD5:801B21074610B1C451B011E9CAD509FB | SHA256:D1DCE4ADFEDC9EBF11D2AB39AA90A09BC355B2761C3D0BC1E045DB492DB0577B | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\lib\jakartaee-migration-1.0.7-shaded.jar | java | |
MD5:378EEDA7171284210688349F31E60E73 | SHA256:AF4108610B27BB1ECBE706182EB3AB7A7D250565D4F4663DF05DE787E90B4D81 | |||
| 540 | apache-tomcat-10.1.11.exe | C:\Program Files\Apache Software Foundation\Tomcat 10.1\lib\annotations-api.jar | java | |
MD5:C3AA77835F973109752DD241EB98F450 | SHA256:9C54DD7A920D502390526F425EF3F9B30C06AB59819E56ECA2C0122F44EAC48D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |