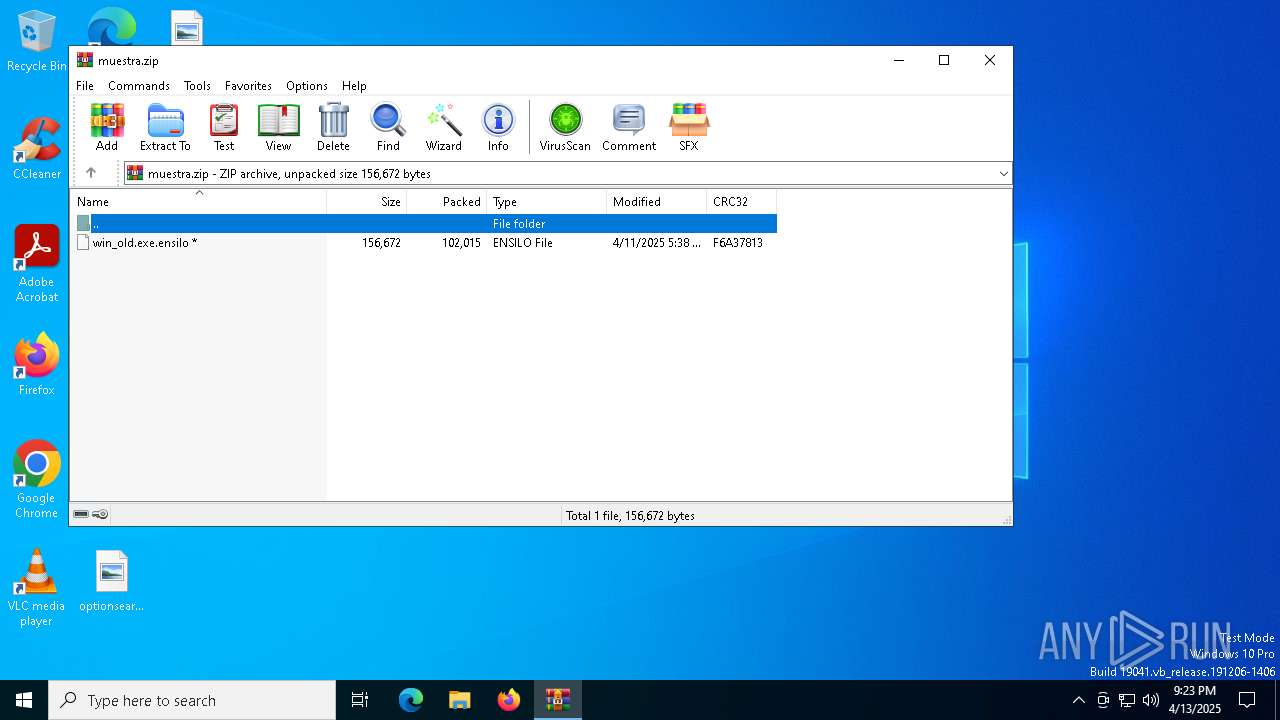
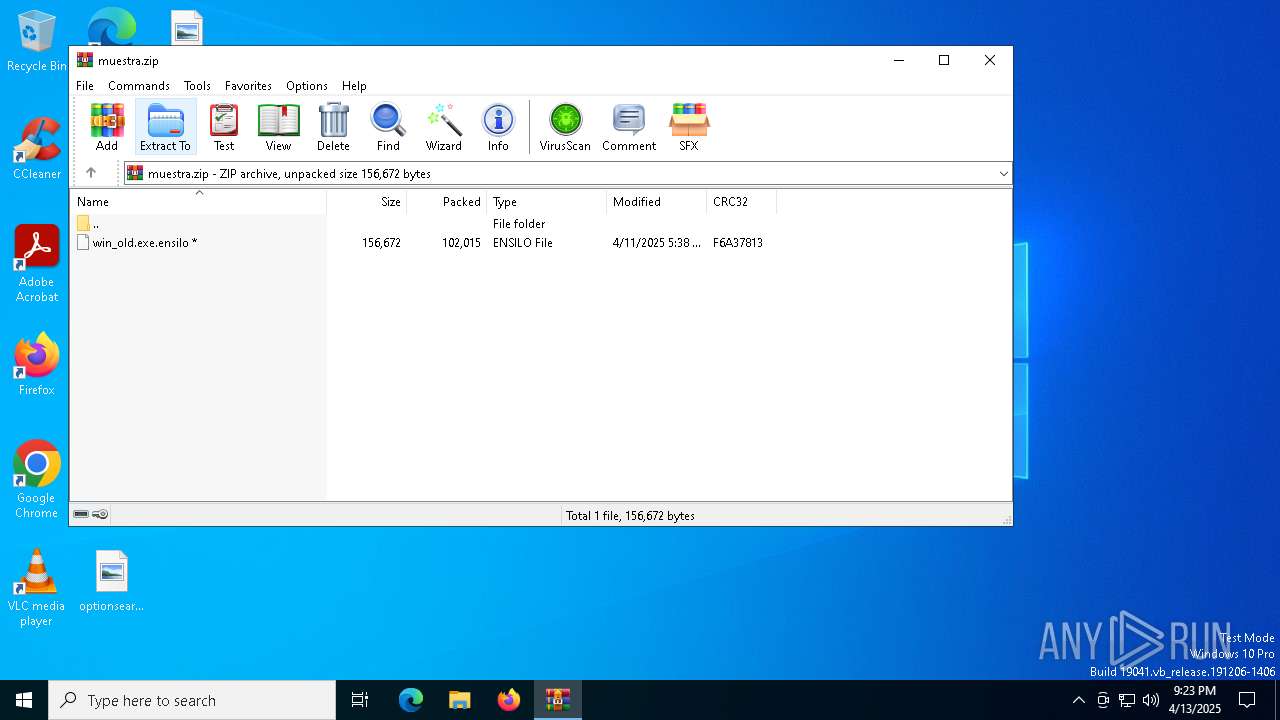
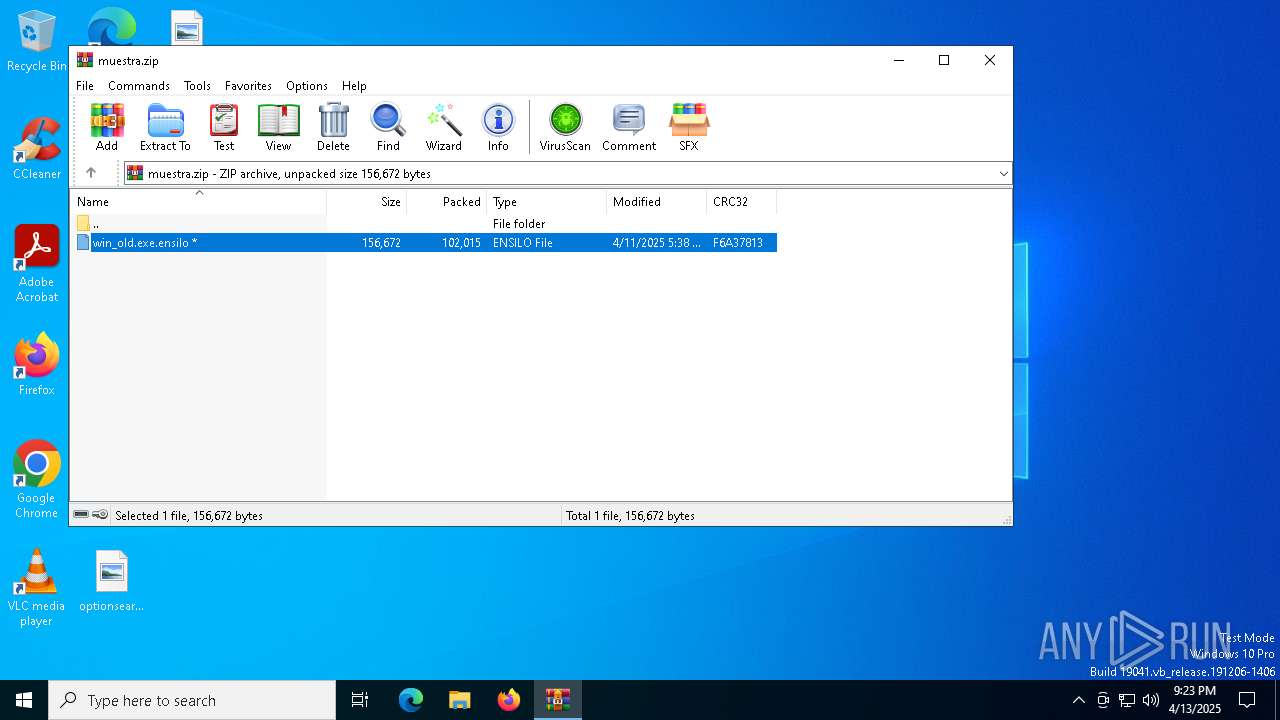
| File name: | muestra.zip |
| Full analysis: | https://app.any.run/tasks/8e0b1a38-a2e8-4bd6-b0d5-60b9b4bc575d |
| Verdict: | Malicious activity |
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | April 13, 2025, 21:22:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
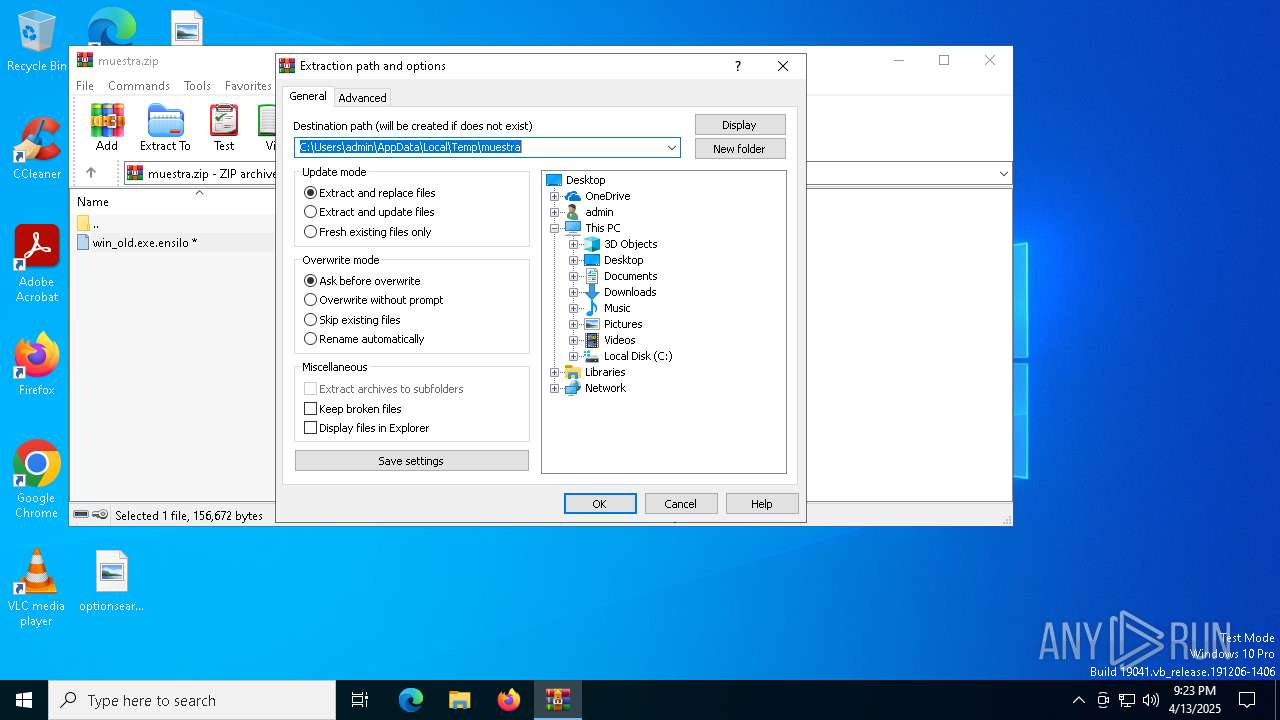
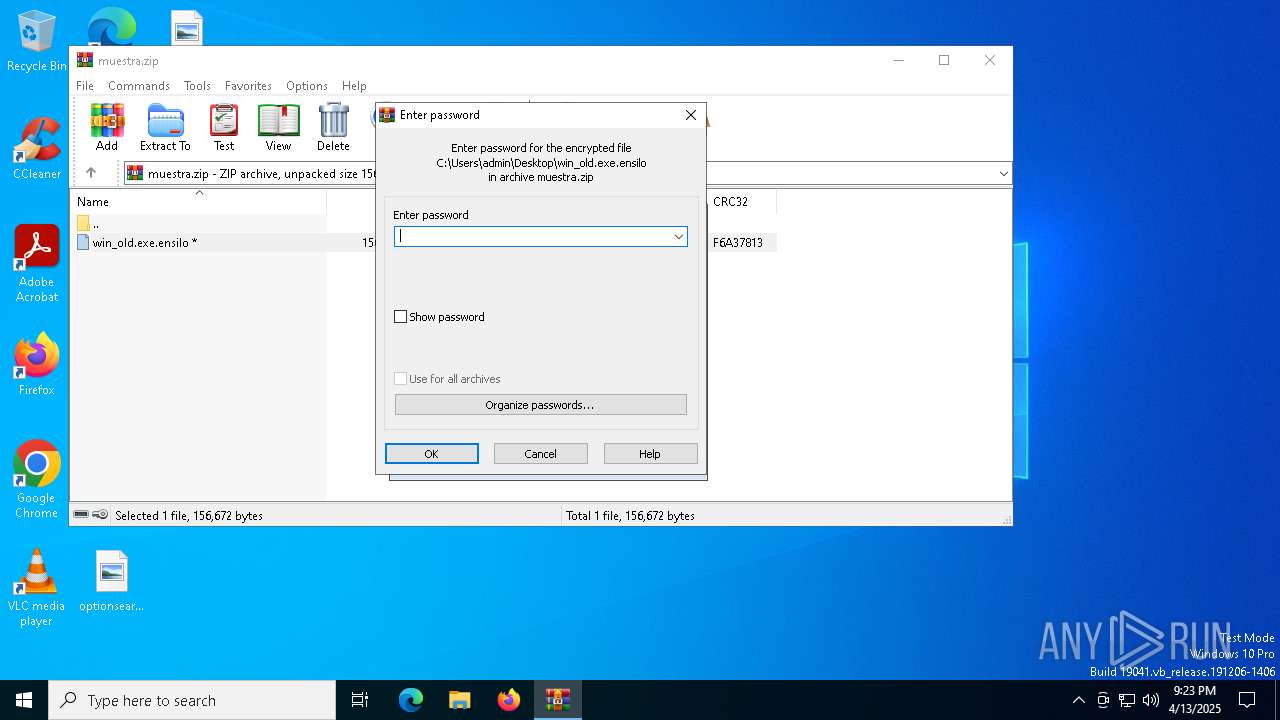
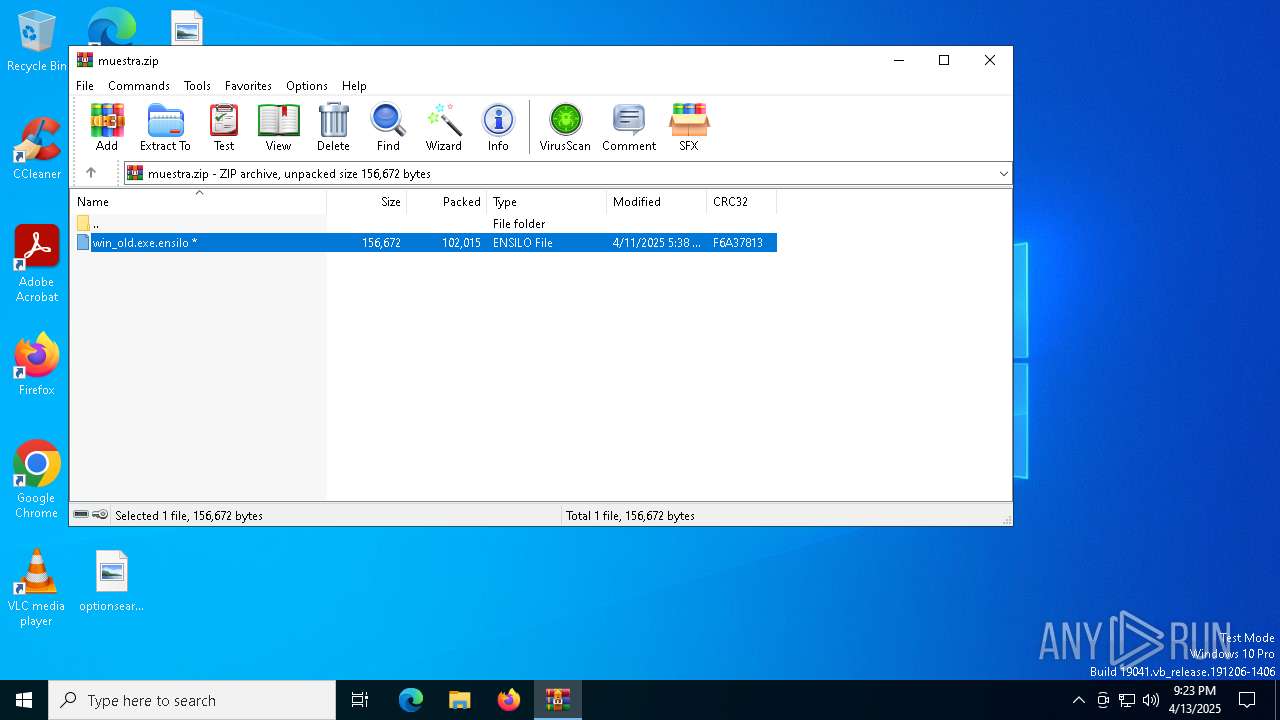
| File info: | Zip archive data, at least v4.5 to extract, compression method=AES Encrypted |
| MD5: | A2428D6F8DB171BCE63EA69597082F3D |
| SHA1: | 259E9202976D3DF7D54F6A05C1472BB49BBE6461 |
| SHA256: | ED933D1C58E398CD4AC9D9B5F3556A009FA025D5E156D5B60A3E345FE011F963 |
| SSDEEP: | 3072:xzDwPPE1q57bmO6pPPmAxcdsl9YxLC6Wb:hDYSq5nmOiPeAxGslmxLub |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 5204)
Renames files like ransomware
- win_old.exe (PID: 1812)
RANSOMWARE has been detected
- win_old.exe (PID: 1812)
[YARA] LockBit is detected
- win_old.exe (PID: 1812)
Steals credentials from Web Browsers
- win_old.exe (PID: 1812)
Actions looks like stealing of personal data
- win_old.exe (PID: 1812)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- win_old.exe (PID: 1812)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7012)
INFO
Reads the software policy settings
- slui.exe (PID: 5968)
- slui.exe (PID: 5436)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2908)
Checks proxy server information
- slui.exe (PID: 5436)
Checks supported languages
- win_old.exe (PID: 1812)
- win_old.exe (PID: 5576)
- ShellExperienceHost.exe (PID: 7012)
Reads the machine GUID from the registry
- win_old.exe (PID: 5576)
Reads the computer name
- win_old.exe (PID: 5576)
- win_old.exe (PID: 1812)
- ShellExperienceHost.exe (PID: 7012)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5204)
Manual execution by a user
- win_old.exe (PID: 5576)
Creates files or folders in the user directory
- win_old.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:11 17:38:16 |
| ZipCRC: | 0xf6a37813 |
| ZipCompressedSize: | 102015 |
| ZipUncompressedSize: | 156672 |
| ZipFileName: | win_old.exe.ensilo |
Total processes
144
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1812 | "C:\Users\admin\Desktop\win_old.exe" | C:\Users\admin\Desktop\win_old.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2908 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\muestra.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5204 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5436 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | "C:\Users\admin\Desktop\win_old.exe" | C:\Users\admin\Desktop\win_old.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5968 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5972 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7012 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 905
Read events
4 867
Write events
25
Delete events
13
Modification events
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\muestra.zip | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
9
Suspicious files
491
Text files
555
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\desktop.ini | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\CCCCCCCCCCC | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\GGGGGGGGGGG | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\EEEEEEEEEEE | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\HHHHHHHHHHH | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\DDDDDDDDDDD | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\FFFFFFFFFFF | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\KKKKKKKKKKK | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
| 1812 | win_old.exe | C:\$Recycle.Bin\S-1-5-18\NNNNNNNNNNN | binary | |
MD5:77F87982395075CCE83D552D1F115019 | SHA256:47F37EBF24EFAB7DC68EF2010C1093E77E03F72DBD6EED4F474F70E2205F8654 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4988 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4988 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |