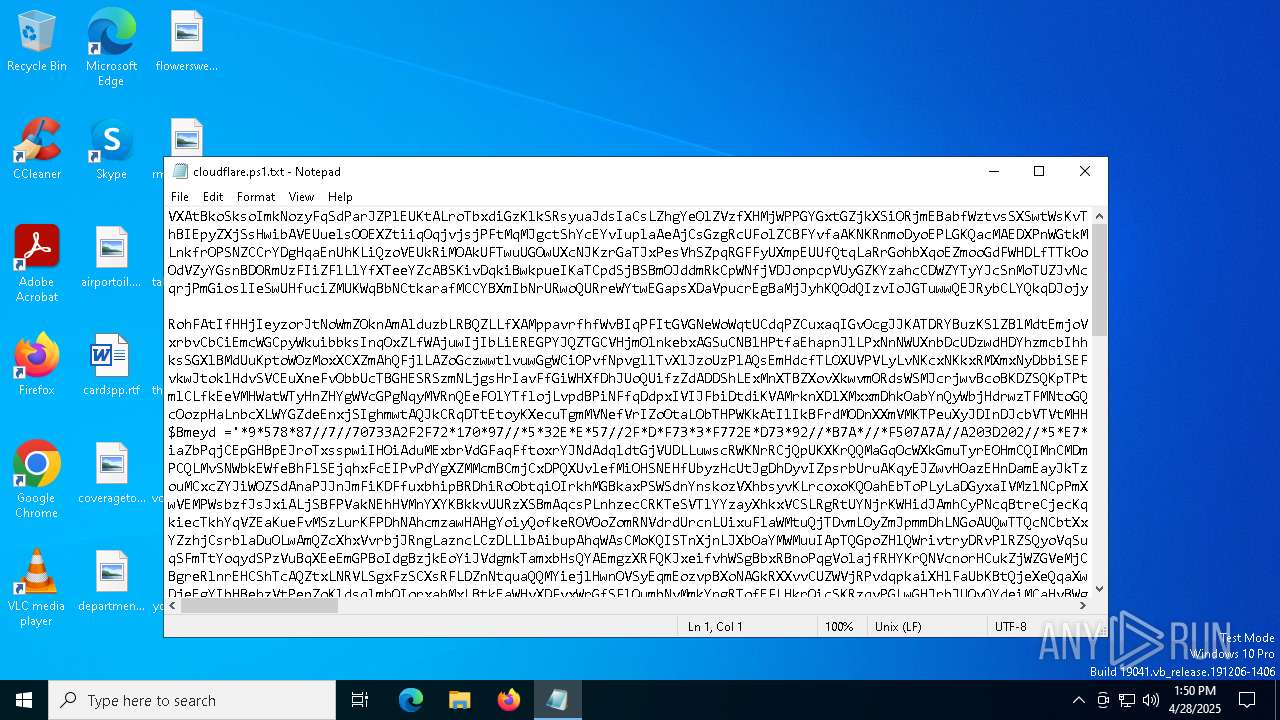
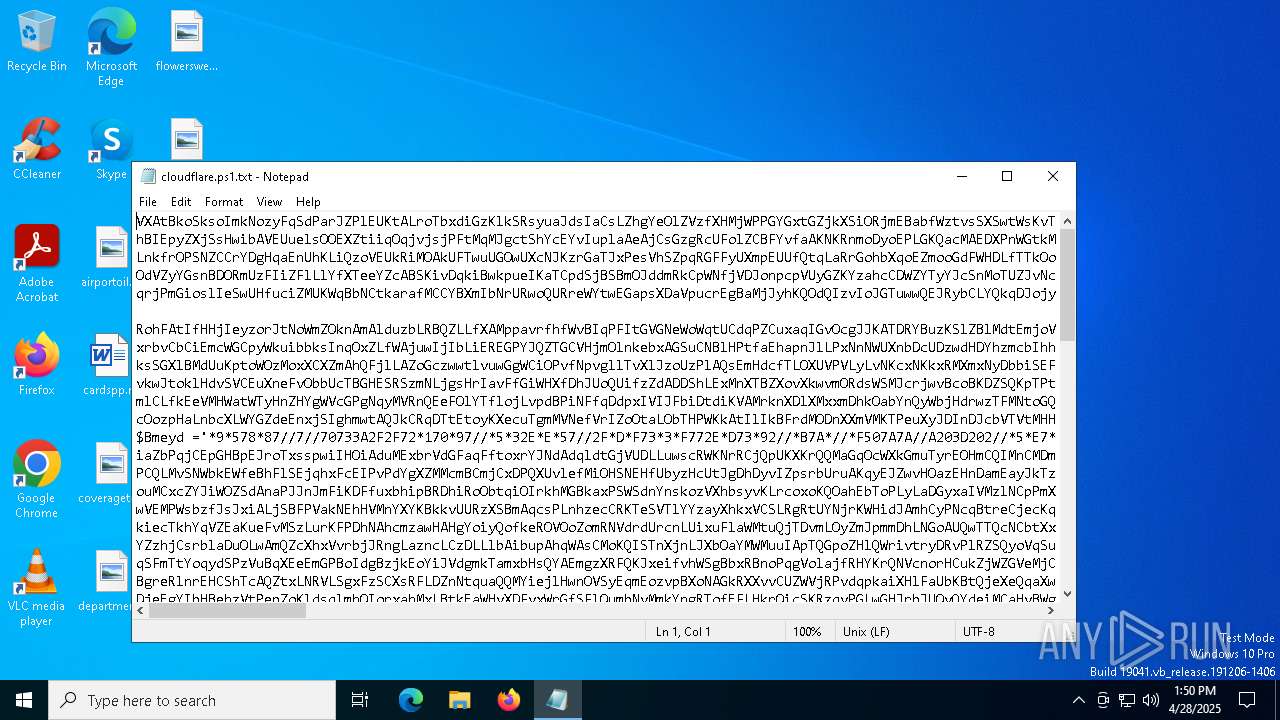
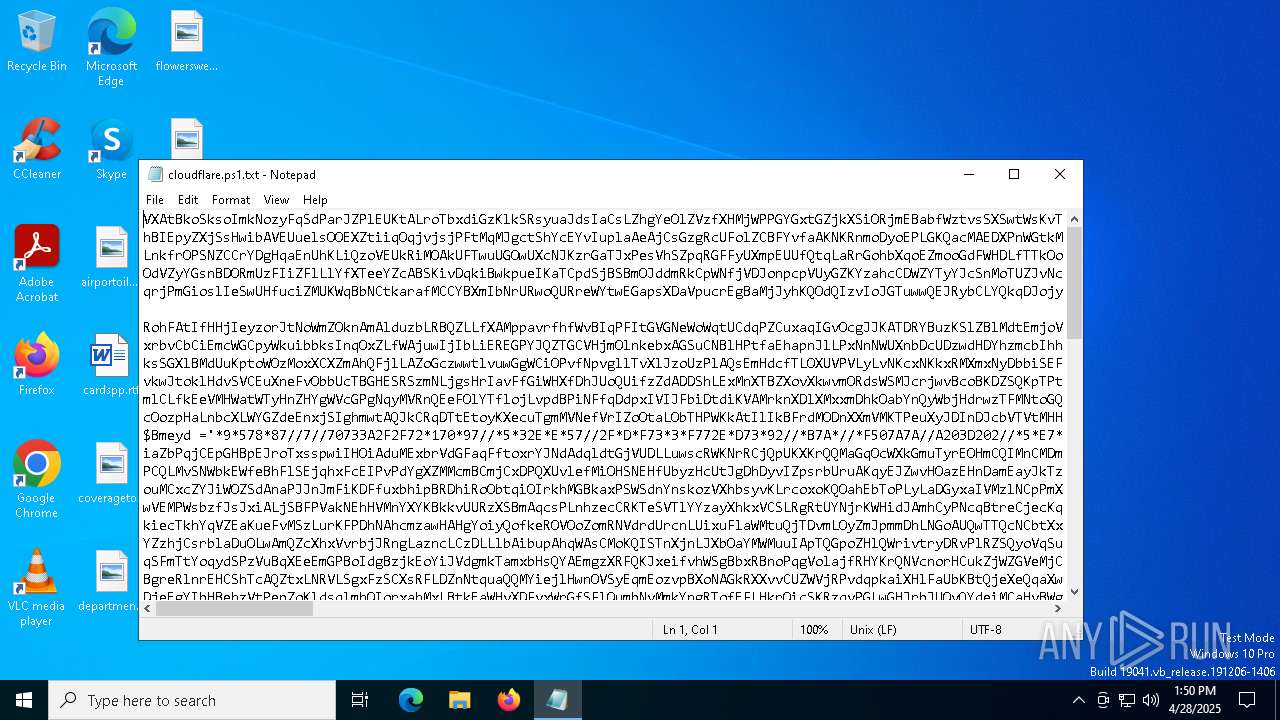
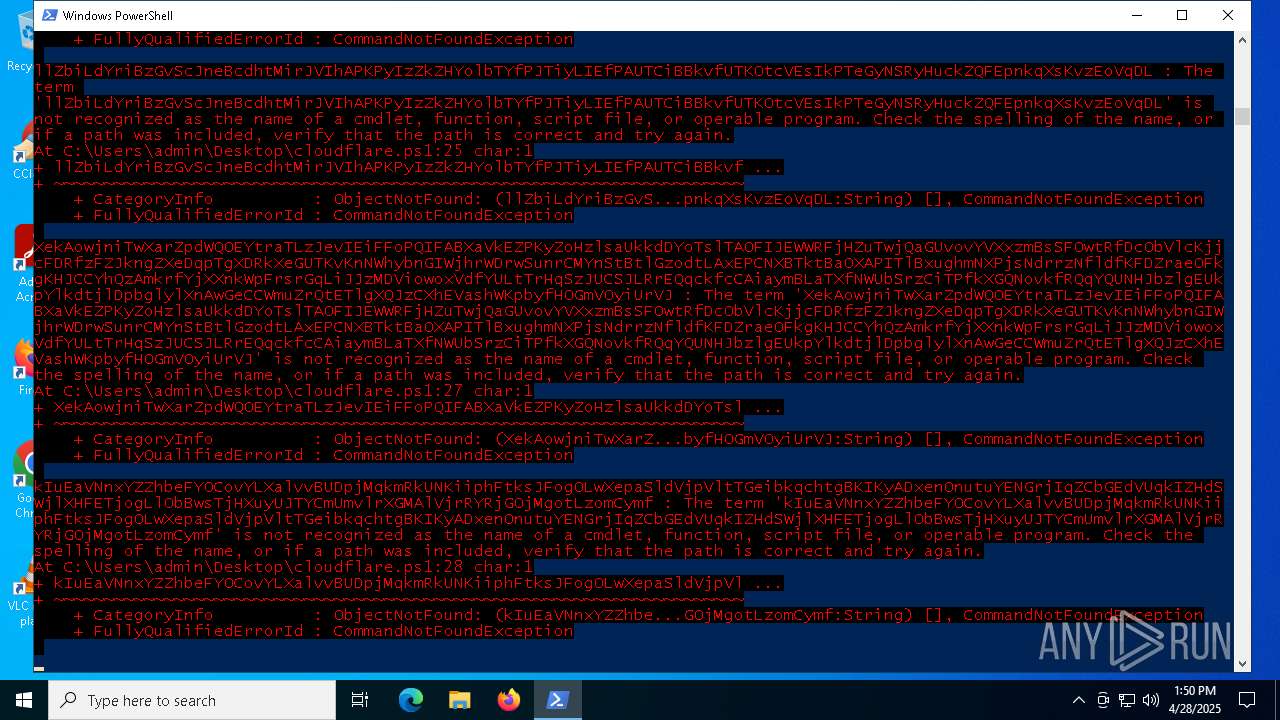
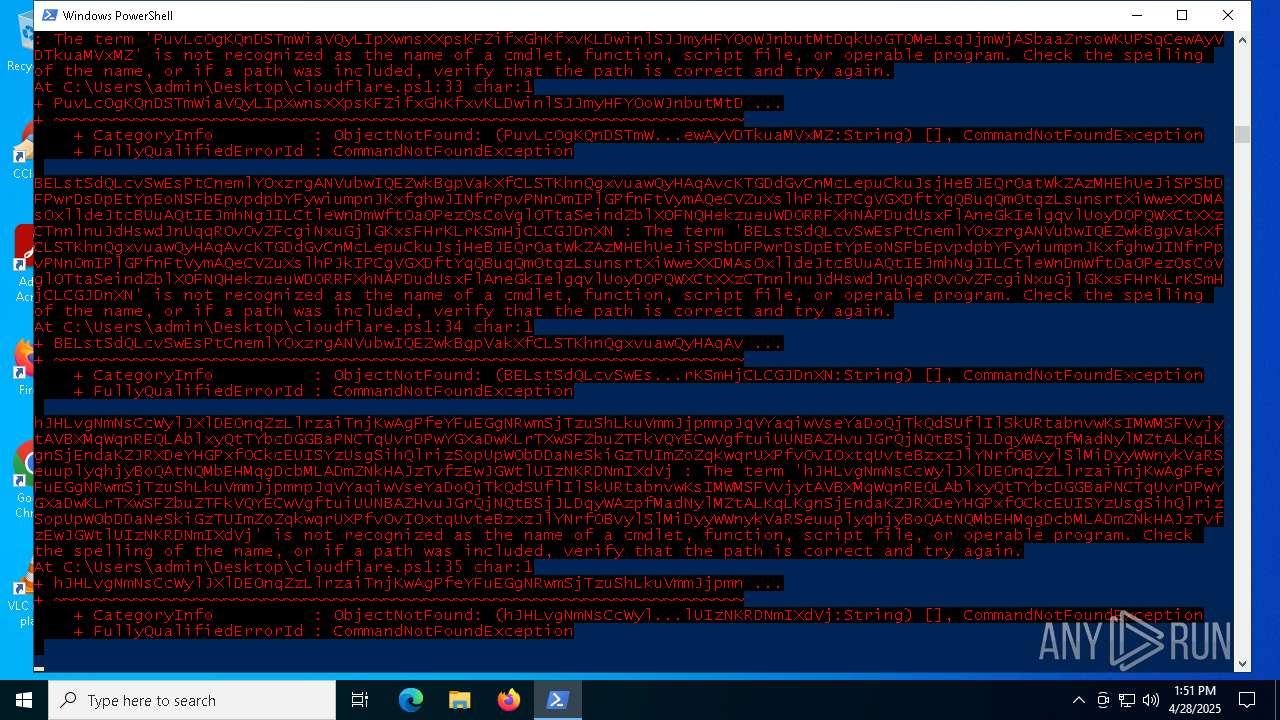
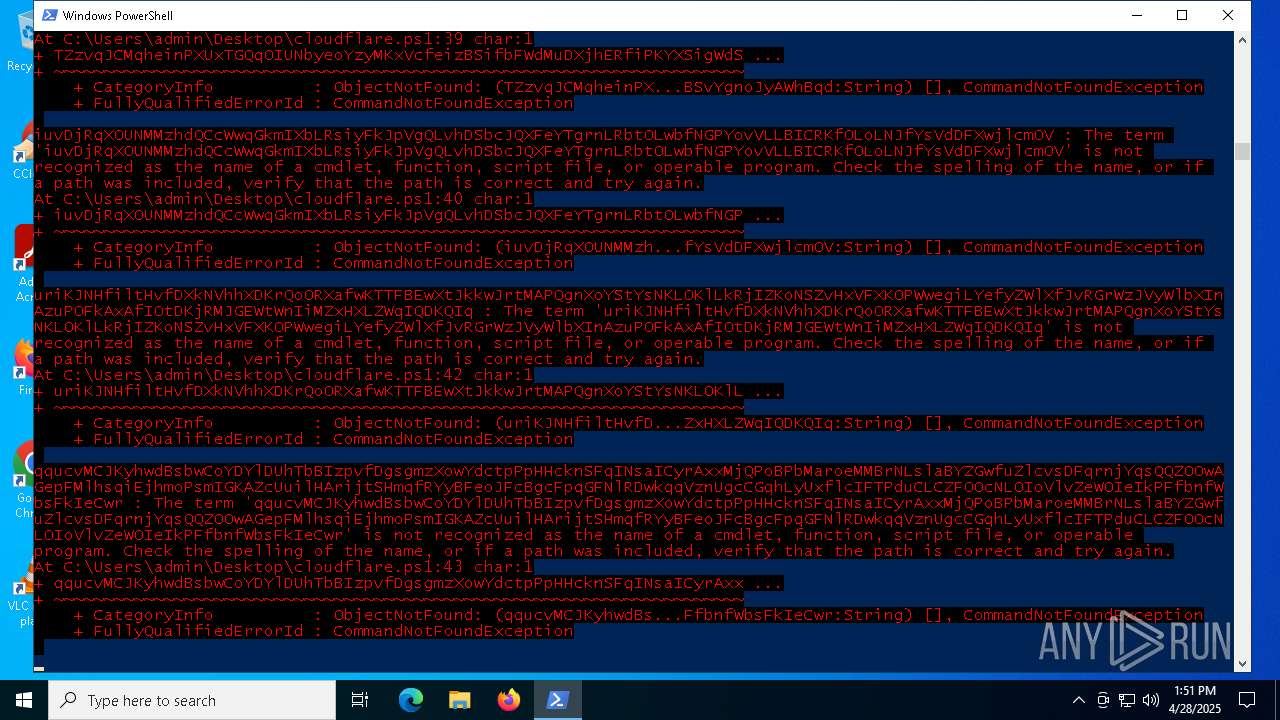
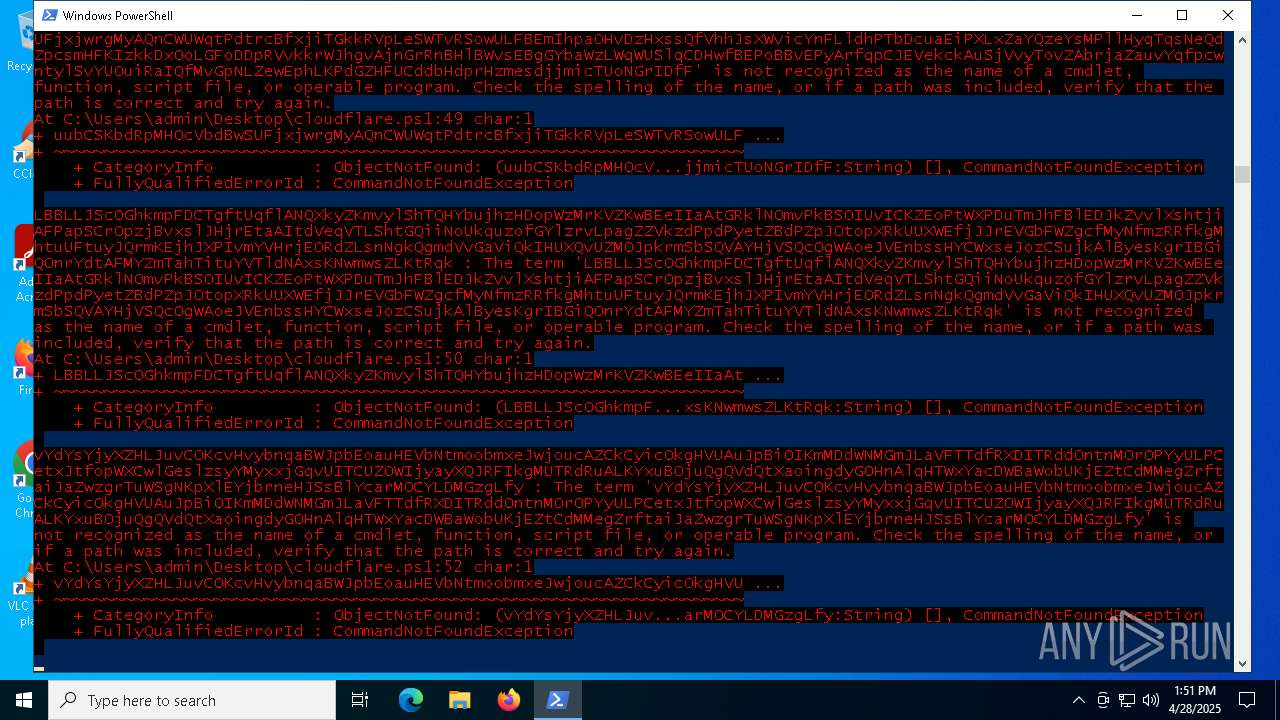
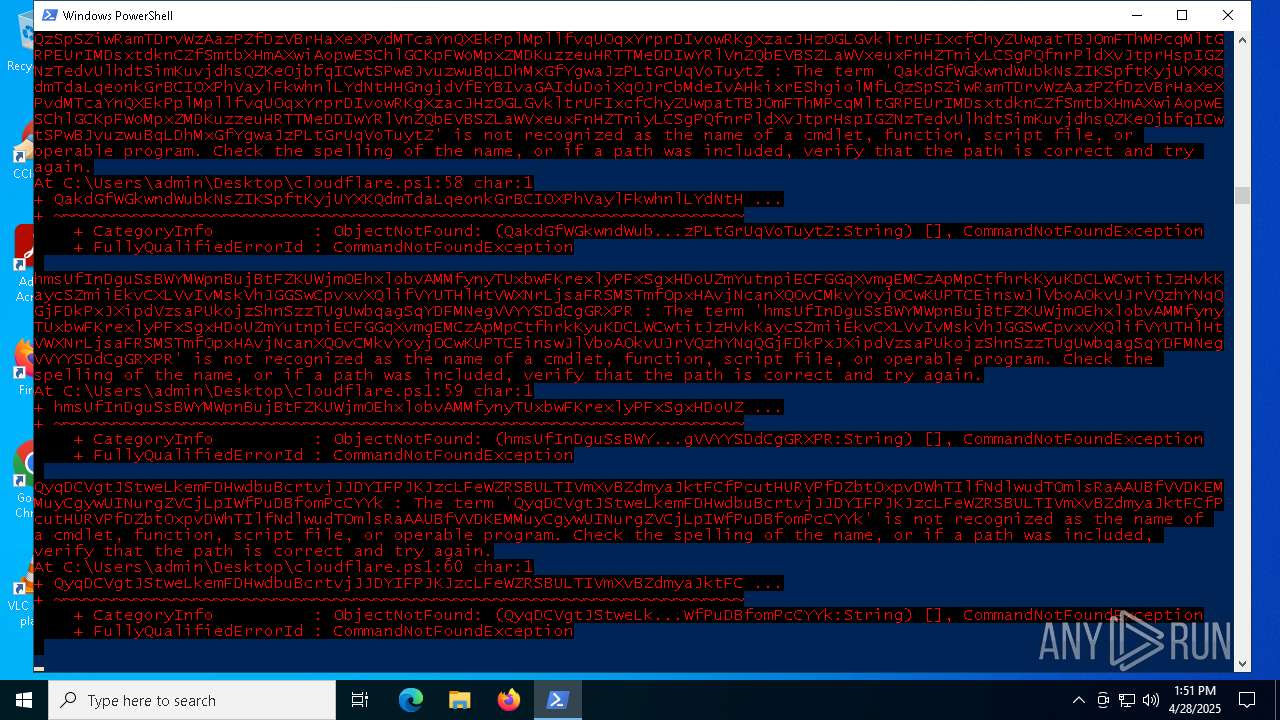
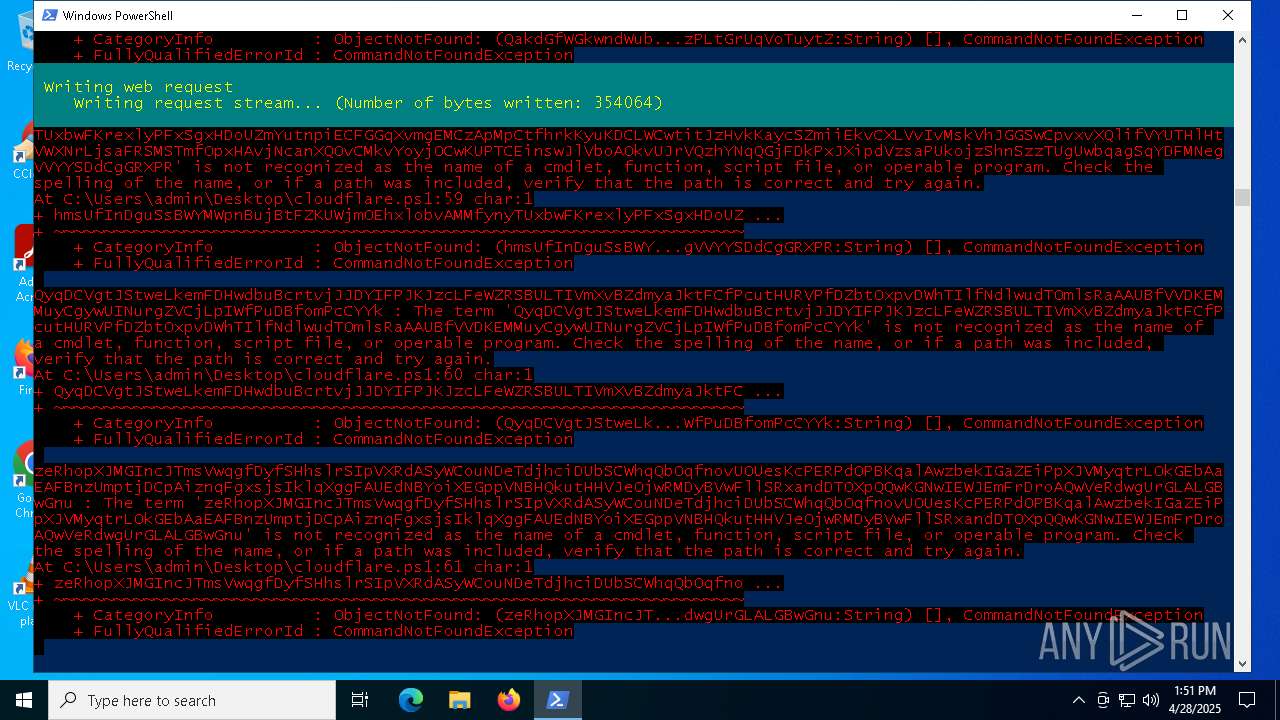
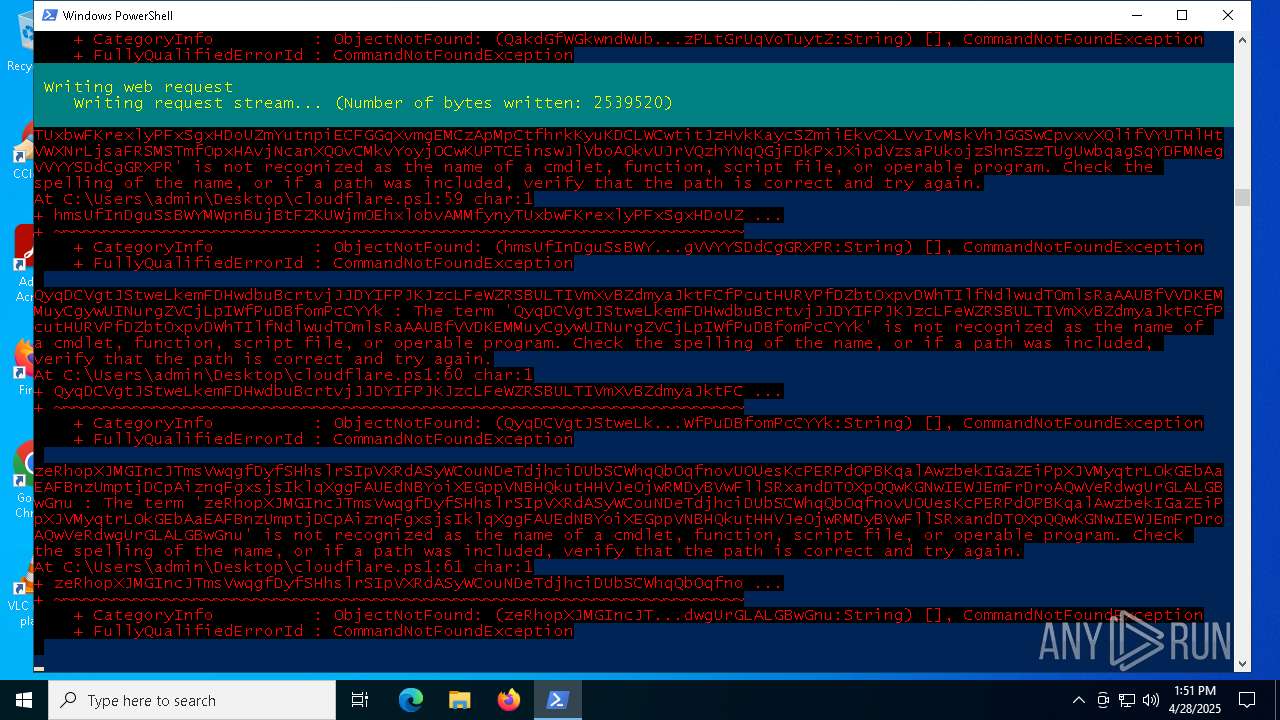
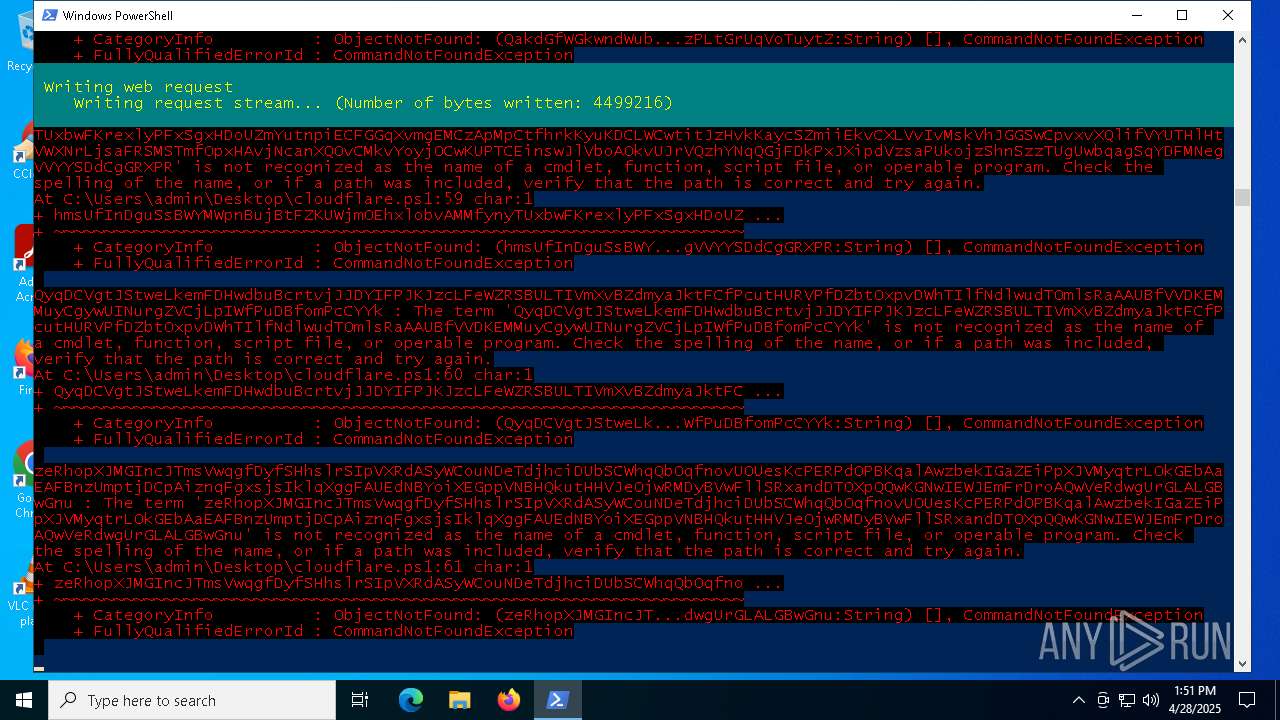
| File name: | cloudflare.ps1 |
| Full analysis: | https://app.any.run/tasks/c609476e-140e-44f1-a714-5a470d2f17b8 |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 13:50:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (652) |
| MD5: | 1AAE4C4BD73593E9359D1E685D2F9F4D |
| SHA1: | 3BE781F275D0606D111935031491D40FF309288F |
| SHA256: | ED90F038380683889F54E7A170EA0AC9616C4E2F276983079875246970F8CE79 |
| SSDEEP: | 384:a07MCg9m3ilgZ9vrmsvFdrnUf6hVwpsRcmJA2v2XNFZGqIa056NbXQWW41:9i9myiZ9DmE7TRFRdA2e9HGqS4Nbg/41 |
MALICIOUS
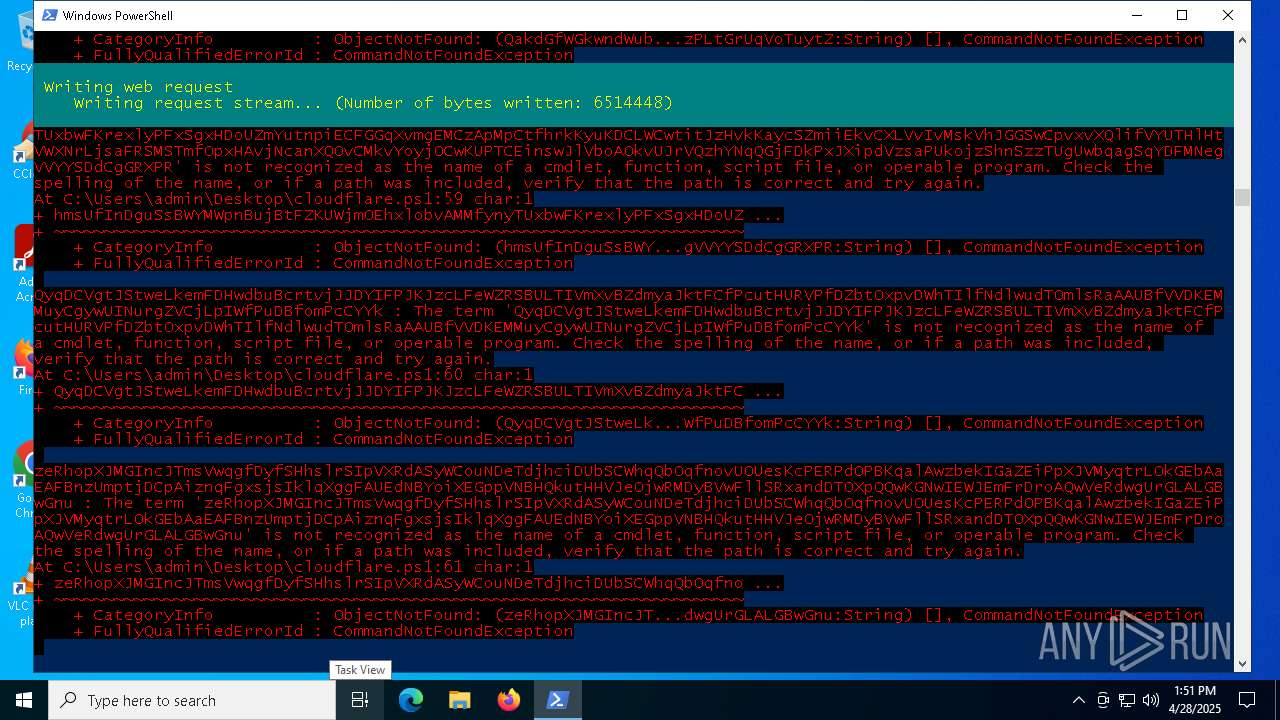
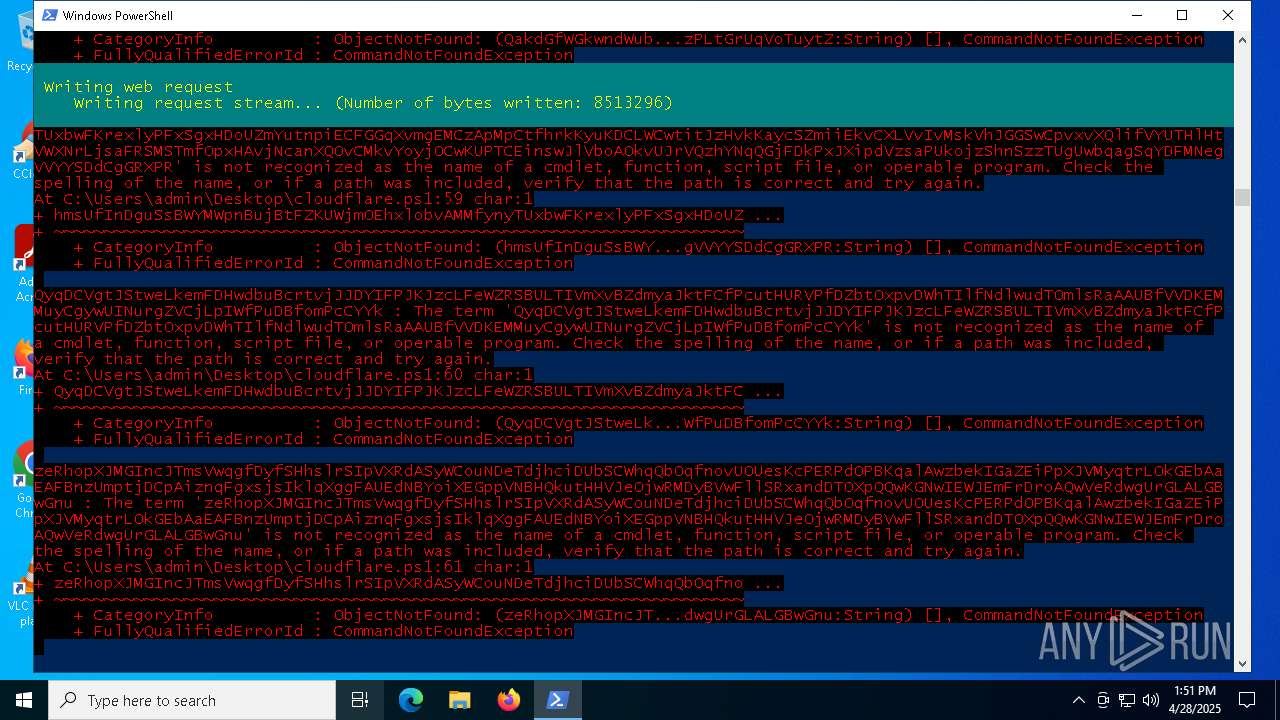
Bypass execution policy to execute commands
- powershell.exe (PID: 4776)
Executing a file with an untrusted certificate
- ISBEW64.exe (PID: 1180)
- ISBEW64.exe (PID: 900)
- ISBEW64.exe (PID: 4920)
- ISBEW64.exe (PID: 1512)
- ISBEW64.exe (PID: 7832)
- ISBEW64.exe (PID: 7720)
- ISBEW64.exe (PID: 7740)
- ISBEW64.exe (PID: 3096)
- ISBEW64.exe (PID: 7400)
- ISBEW64.exe (PID: 7884)
SUSPICIOUS
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 4776)
Executable content was dropped or overwritten
- ManaDigital.exe (PID: 7800)
- ManaDigital.exe (PID: 4268)
Starts itself from another location
- ManaDigital.exe (PID: 7800)
Starts CMD.EXE for commands execution
- ManaDigital.exe (PID: 4268)
Executes application which crashes
- Readersecurity.exe (PID: 7692)
INFO
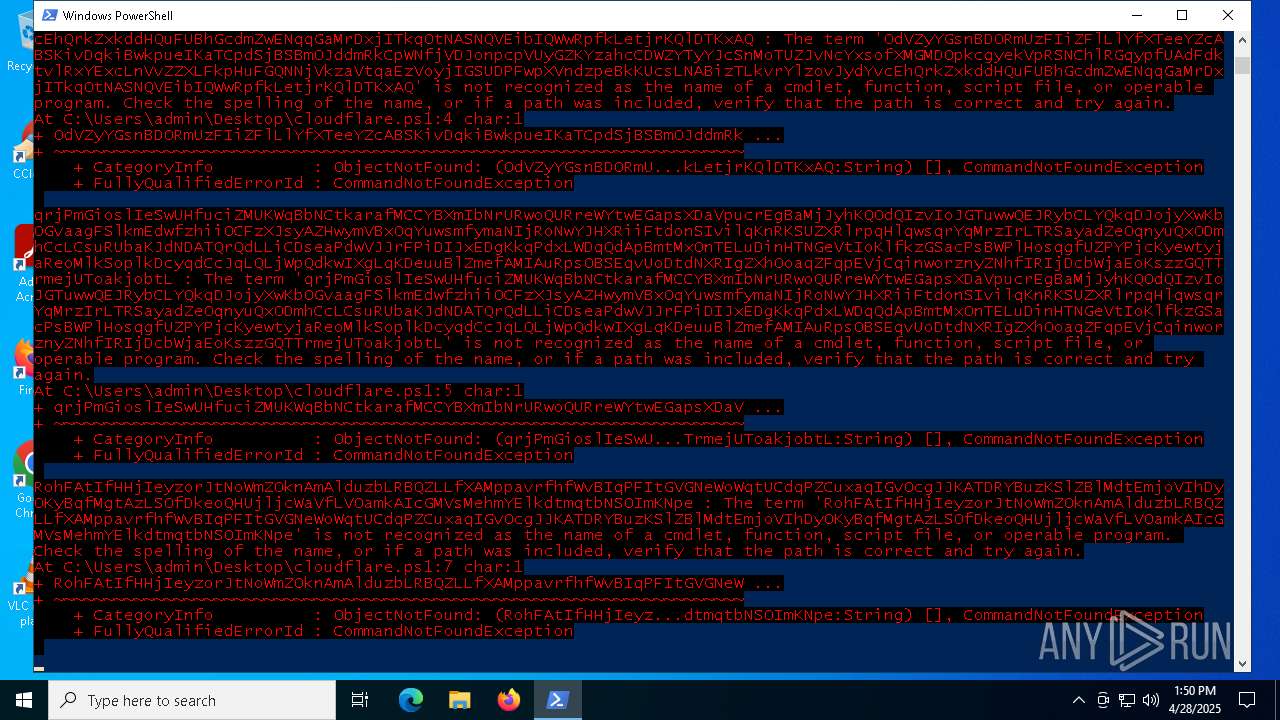
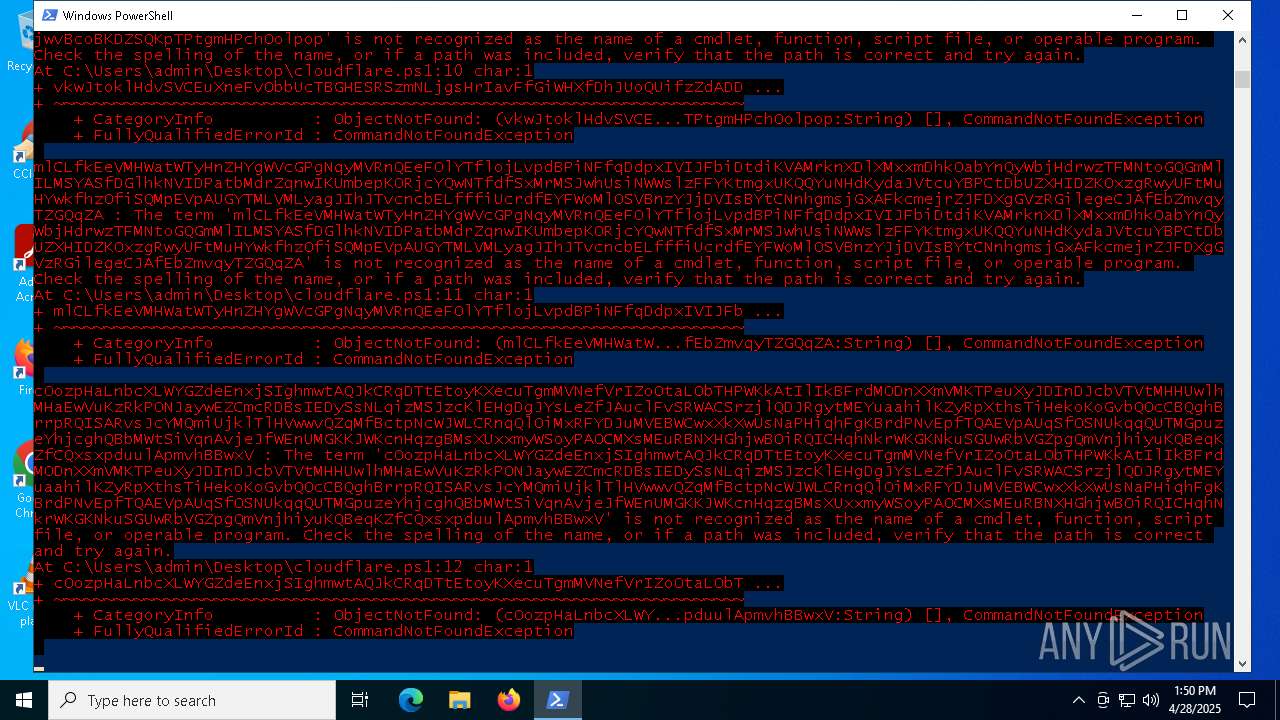
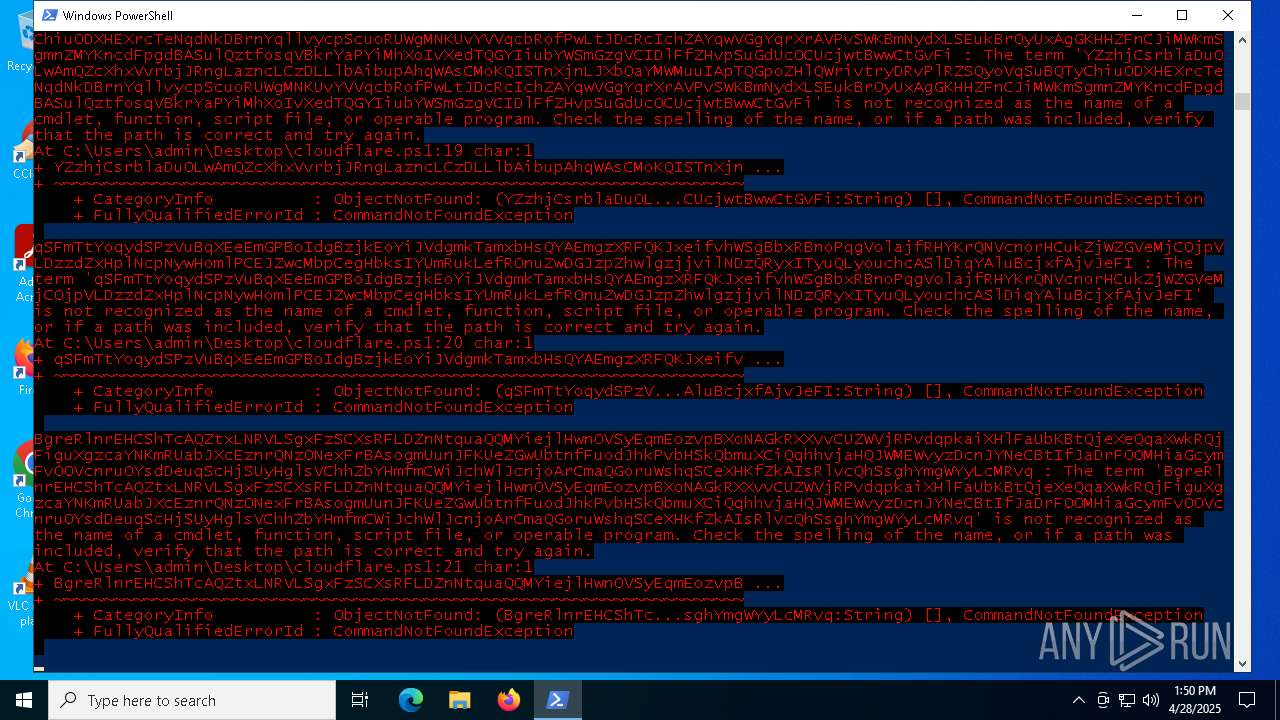
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4776)
Manual execution by a user
- powershell.exe (PID: 4776)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7412)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3240)
- msiexec.exe (PID: 6300)
The sample compiled with english language support
- msiexec.exe (PID: 3240)
- msiexec.exe (PID: 6300)
- ManaDigital.exe (PID: 7800)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4776)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4776)
Application launched itself
- msedge.exe (PID: 7956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
185
Monitored processes
49
Malicious processes
2
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1576 --field-trial-handle=2380,i,3473410126931511694,4623943628068869550,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{6A01B31B-81A9-4817-9FC5-FBA93C8716EF} | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe | — | msiexec.exe | |||||||||||
User: admin Company: Flexera Integrity Level: MEDIUM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.58 Modules
| |||||||||||||||
| 1180 | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{3C8B17BD-88F4-4A7E-8531-D42A64A7750A} | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe | — | msiexec.exe | |||||||||||
User: admin Company: Flexera Integrity Level: MEDIUM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.58 Modules
| |||||||||||||||
| 1512 | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{43F722A7-46B5-4F2D-A7DA-82D1DED39847} | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe | — | msiexec.exe | |||||||||||
User: admin Company: Flexera Integrity Level: MEDIUM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.58 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6504 --field-trial-handle=2380,i,3473410126931511694,4623943628068869550,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1532 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4140 --field-trial-handle=2380,i,3473410126931511694,4623943628068869550,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2376 --field-trial-handle=2380,i,3473410126931511694,4623943628068869550,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3028 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6068 --field-trial-handle=2380,i,3473410126931511694,4623943628068869550,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3096 | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{3A2251E7-E45D-4F3D-B2D3-B4EE5BEC84C4} | C:\Users\admin\AppData\Local\Temp\{4C8AEDAE-2013-4A85-A7CD-00BA0A43690A}\ISBEW64.exe | — | msiexec.exe | |||||||||||
User: admin Company: Flexera Integrity Level: MEDIUM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.58 Modules
| |||||||||||||||
| 3240 | C:\Windows\syswow64\MsiExec.exe -Embedding 845A12FBA89895632712E4CDA9C87634 C | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 765
Read events
17 677
Write events
85
Delete events
3
Modification events
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: A9870F6800000000 | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CIDSave\Modules\GlobalSettings\ProperTreeModuleInner |
| Operation: | write | Name: | ProperTreeModuleInner |
Value: 9C000000980000003153505305D5CDD59C2E1B10939708002B2CF9AE3B0000002A000000004E0061007600500061006E0065005F004300460044005F0046006900720073007400520075006E0000000B000000000000004100000030000000004E0061007600500061006E0065005F00530068006F0077004C00690062007200610072007900500061006E00650000000B000000FFFF00000000000000000000 | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (7412) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | FFlags |
Value: | |||
Executable files
52
Suspicious files
553
Text files
89
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4776 | powershell.exe | C:\Users\admin\AppData\Roaming\moscow.msi | — | |
MD5:— | SHA256:— | |||
| 3240 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{A58B6D50-83C0-4A68-B397-9847A3AB752E}\Shoundpeel.qqy | — | |
MD5:— | SHA256:— | |||
| 7412 | notepad.exe | C:\Users\admin\Desktop\cloudflare.ps1 | text | |
MD5:1AAE4C4BD73593E9359D1E685D2F9F4D | SHA256:ED90F038380683889F54E7A170EA0AC9616C4E2F276983079875246970F8CE79 | |||
| 6300 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA65F.tmp | executable | |
MD5:A0E940A3D3C1523416675125E3B0C07E | SHA256:B8FA7AA425E4084EA3721780A13D11E08B8D53D1C5414B73F22FAECA1BFD314F | |||
| 3240 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{A58B6D50-83C0-4A68-B397-9847A3AB752E}\ManaDigital.exe | executable | |
MD5:C7C95E2B4079DD79E0FC1087E3976450 | SHA256:3702F03CA6DE73D3909C9B1E02F319B94F51EA598E1693C1290899E2CA0FE485 | |||
| 3240 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{A58B6D50-83C0-4A68-B397-9847A3AB752E}\Krielstourtplool.ouq | binary | |
MD5:F03E9BB31D45D909C0448108680787E9 | SHA256:C03FAACFA01176BF5F86D5BA16B0DC3AB930F2EA55DB4B7C210F7262C7BC27A5 | |||
| 3240 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{A58B6D50-83C0-4A68-B397-9847A3AB752E}\bassmix.dll | executable | |
MD5:6CBD7A375E98420DC8CC2475B62C895B | SHA256:704BC9A084989871A567ABC638AEC57B3C6514EF1E31CEACD0FB347551A7AAF4 | |||
| 4776 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1136fb.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 4776 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\P3Z0SX4H95WIPPNCVV4W.temp | binary | |
MD5:41445F939E61B5E54F6D9E8D5BE347DE | SHA256:77166E0B6947B9C3A80C08D9CE6C87D335F72E5AFF124EAA08358515785C70F1 | |||
| 3240 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{A58B6D50-83C0-4A68-B397-9847A3AB752E}\basswma.dll | executable | |
MD5:D2177355BECCFDBC1E7B5C687DFBA290 | SHA256:A844247B7CDCAC1A5F61C604E4DB111B274616C0EB19A70CDFB073C8C2F3B375 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
79
DNS requests
75
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8144 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8144 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8144 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
rapitec.net |
| unknown |