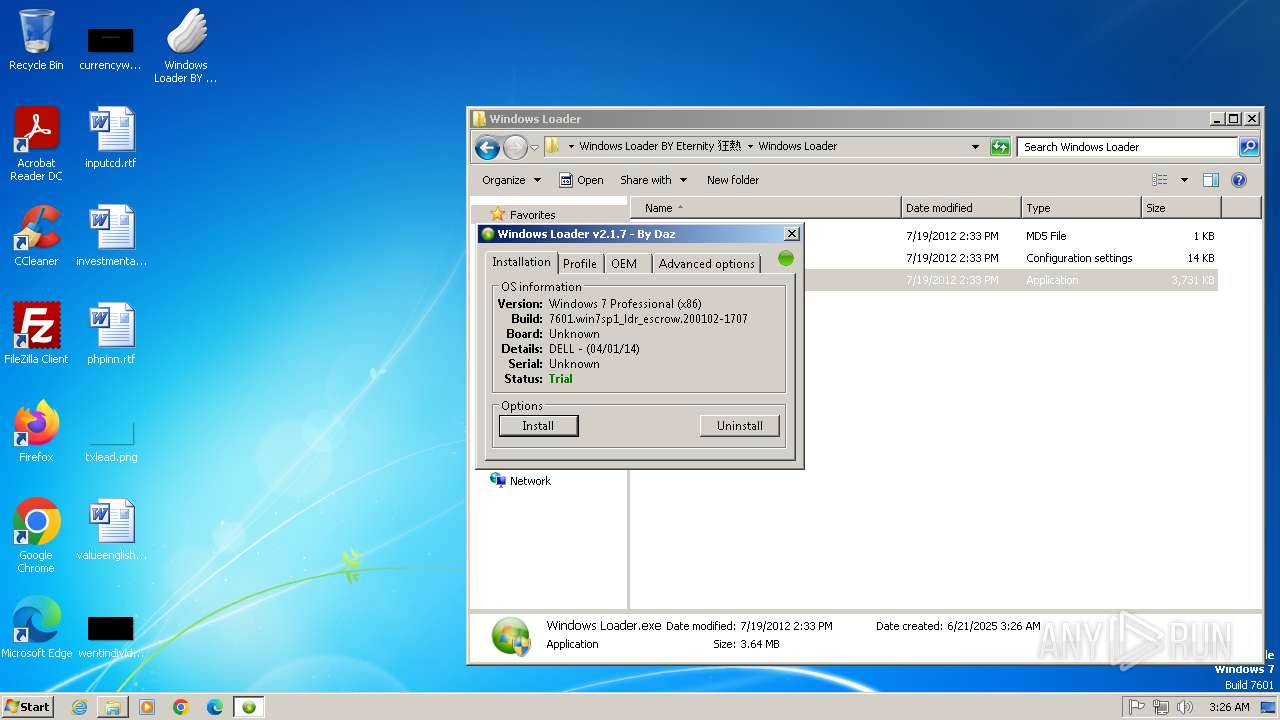
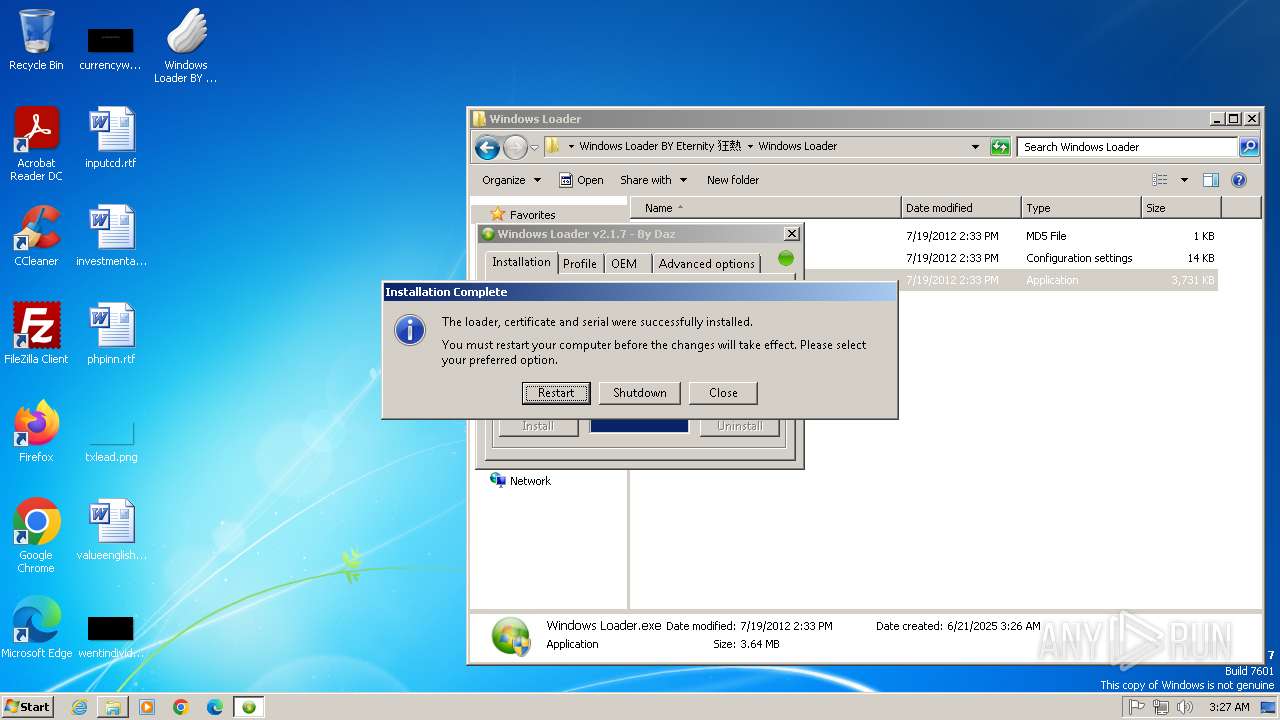
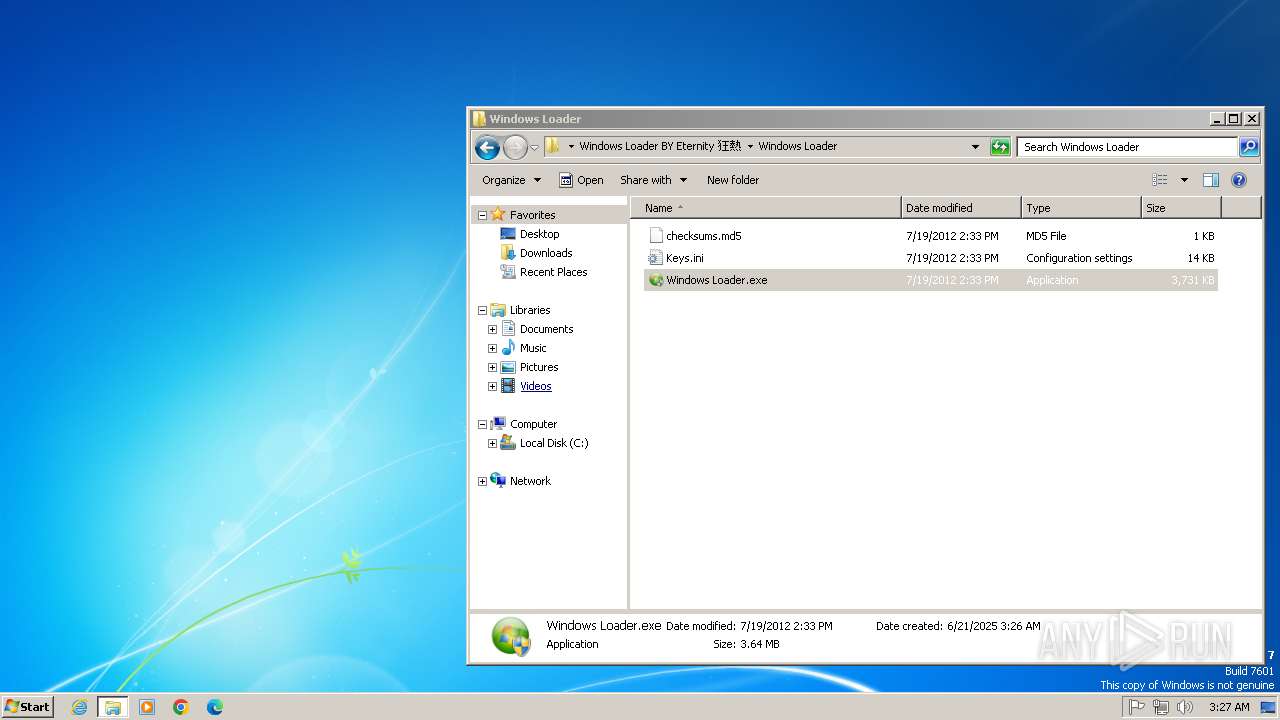
| File name: | Windows+Loader+BY+Eternity+狂熱.exe |
| Full analysis: | https://app.any.run/tasks/1a6ab79a-648f-4642-8131-bd1906a31996 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 02:26:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 394B21A2149C2520F48F854CC0B40E5F |
| SHA1: | 561143645CE8CC03B9F006317074823D4C838CED |
| SHA256: | ED4487EF82F1BED6B41B7D4BCE51D70A4D92EE4BE22510A33089009E59A4537F |
| SSDEEP: | 98304:Ef0KJvGpTwyx2W887PPDle3c7ISl73wgFDbhwp9Eig3C4z6ScESUKiuI9PG8Vvat:Jm |
MALICIOUS
Opens a text file (SCRIPT)
- cscript.exe (PID: 4016)
- cscript.exe (PID: 2012)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- Windows+Loader+BY+Eternity+狂熱.exe (PID: 2000)
Executable content was dropped or overwritten
- Windows+Loader+BY+Eternity+狂熱.exe (PID: 2000)
- Windows Loader.exe (PID: 1028)
Reads the BIOS version
- Windows Loader.exe (PID: 1028)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 2336)
- cmd.exe (PID: 3312)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1748)
- cmd.exe (PID: 1884)
The process executes VB scripts
- cmd.exe (PID: 1996)
- cmd.exe (PID: 2340)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4016)
- cscript.exe (PID: 2012)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 4016)
- cscript.exe (PID: 2012)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 4016)
- cscript.exe (PID: 2012)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4044)
- cmd.exe (PID: 2992)
- Windows Loader.exe (PID: 1028)
Application launched itself
- cmd.exe (PID: 4044)
- cmd.exe (PID: 2992)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 4016)
- cscript.exe (PID: 2012)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2012)
- cscript.exe (PID: 4016)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 2012)
- cscript.exe (PID: 4016)
There is functionality for communication over UDP network (YARA)
- Windows Loader.exe (PID: 1028)
There is functionality for taking screenshot (YARA)
- Windows Loader.exe (PID: 1028)
Process drops legitimate windows executable
- Windows Loader.exe (PID: 1028)
Changes charset (SCRIPT)
- cscript.exe (PID: 4016)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 4016)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 4016)
Creates file in the systems drive root
- cmd.exe (PID: 872)
- bootsect.exe (PID: 1164)
- Windows Loader.exe (PID: 1028)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1524)
- ctfmon.exe (PID: 1404)
The system shut down or reboot
- cmd.exe (PID: 3824)
Reads the Internet Settings
- sipnotify.exe (PID: 1524)
INFO
Manual execution by a user
- notepad.exe (PID: 2604)
- Windows Loader.exe (PID: 3288)
- Windows Loader.exe (PID: 1028)
- IMEKLMG.EXE (PID: 1204)
- IMEKLMG.EXE (PID: 888)
- msedge.exe (PID: 2436)
The sample compiled with english language support
- Windows+Loader+BY+Eternity+狂熱.exe (PID: 2000)
- Windows Loader.exe (PID: 1028)
Checks supported languages
- Windows+Loader+BY+Eternity+狂熱.exe (PID: 2000)
- Windows Loader.exe (PID: 1028)
- bootsect.exe (PID: 1164)
- IMEKLMG.EXE (PID: 1204)
- IMEKLMG.EXE (PID: 888)
Reads the computer name
- Windows+Loader+BY+Eternity+狂熱.exe (PID: 2000)
- Windows Loader.exe (PID: 1028)
- IMEKLMG.EXE (PID: 1204)
- IMEKLMG.EXE (PID: 888)
Reads the machine GUID from the registry
- Windows Loader.exe (PID: 1028)
Reads product name
- Windows Loader.exe (PID: 1028)
Reads Environment values
- Windows Loader.exe (PID: 1028)
Reads security settings of Internet Explorer
- cscript.exe (PID: 4016)
- cscript.exe (PID: 2012)
UPX packer has been detected
- Windows Loader.exe (PID: 1028)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 1204)
- IMEKLMG.EXE (PID: 888)
Application launched itself
- msedge.exe (PID: 2436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:06:27 07:06:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 70656 |
| InitializedDataSize: | 449536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11def |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.715 |
| ProductVersionNumber: | 1.2.0.715 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Oleg N. Scherbakov |
| FileDescription: | 7z Setup SFX |
| FileVersion: | 1, 2, 0, 715 |
| InternalName: | 7zSfxNew |
| LegalCopyright: | Copyright © 2005-2007 Oleg N. Scherbakov |
| LegalTrademarks: | - |
| OriginalFileName: | 7zSfxNew.exe |
| PrivateBuild: | July 14, 2007 |
| ProductName: | 7ZSfxNew |
| ProductVersion: | 1, 2, 0, 715 |
| SpecialBuild: | - |
Total processes
144
Monitored processes
49
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 872 | cmd.exe /A /C "C:\bootsect.exe /nt60 SYS /force" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 888 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\Desktop\Windows Loader BY Eternity 狂熱\Windows Loader\Windows Loader.exe" | C:\Users\admin\Desktop\Windows Loader BY Eternity 狂熱\Windows Loader\Windows Loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1164 | C:\bootsect.exe /nt60 SYS /force | C:\bootsect.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Sector Manipulation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1236 | icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1568 | icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | shutdown -r -t 0 | C:\Windows\System32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 017
Read events
5 966
Write events
44
Delete events
7
Modification events
| (PID) Process: | (1404) ctfmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | internat.exe |
Value: | |||
| (PID) Process: | (1204) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEJP\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (888) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEKR\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2436) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: B5EECF04A2962F00 | |||
Executable files
10
Suspicious files
162
Text files
206
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1164 | bootsect.exe | \Device\HarddiskVolume1 | — | |
MD5:— | SHA256:— | |||
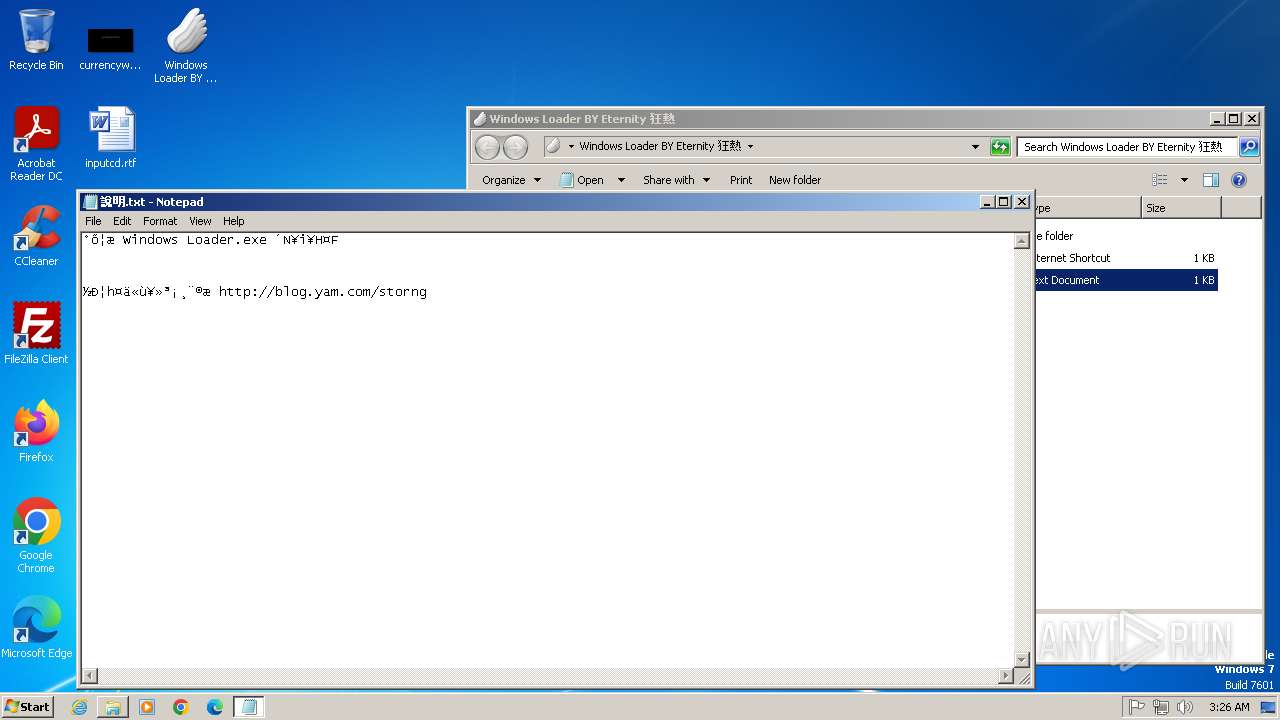
| 2000 | Windows+Loader+BY+Eternity+狂熱.exe | C:\Users\admin\Desktop\Windows Loader BY Eternity 狂熱\說明.txt | text | |
MD5:52E5E1659E410059BC81EB56A9C1114F | SHA256:C73D68D33F0293CE408F16DD51960F8925CFD50118DF616D2774677EE893957C | |||
| 1028 | Windows Loader.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\PNZJC | binary | |
MD5:5264783A779BC25387484A7B6226448D | SHA256:4349D3E5987C1A90EFF55AAC7471C7275C4B7EDE79283BE85142DA5595DF0C02 | |||
| 2000 | Windows+Loader+BY+Eternity+狂熱.exe | C:\Users\admin\Desktop\Windows Loader BY Eternity 狂熱\desktop.ini | text | |
MD5:5473A48A6EF26AD3305D16088F880F58 | SHA256:3F2C0A0CDDAC94C9C0A298BF1F71D3479E463B3822C11B1391B404A563AA543B | |||
| 1028 | Windows Loader.exe | C:\bootsect.dat | executable | |
MD5:FEDD5A91C577FA56507E820F3EF703C2 | SHA256:45109EE129C2AB2F34B6CD71C4A5F6C8FD31F8473D544FA08DB337B3C181891A | |||
| 2000 | Windows+Loader+BY+Eternity+狂熱.exe | C:\Users\admin\Desktop\Windows Loader BY Eternity 狂熱\Windows Loader\Keys.ini | text | |
MD5:E4D00F67799ECD5391509909DA36AE8A | SHA256:7CCB35334DF35B9CE6FB3191075689AA78698193980D7994B7C2C2061A3775A5 | |||
| 1524 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\default.cab | compressed | |
MD5:340674F6A3D1562E28A011EC11E40D83 | SHA256:259880E2346D986ABEED46AA9C2917C53E969AAE6927F2CA0A2AD0967736DF98 | |||
| 2000 | Windows+Loader+BY+Eternity+狂熱.exe | C:\Users\admin\Desktop\Windows Loader BY Eternity 狂熱\Eternity 狂熱.url | text | |
MD5:7A86774F39BC57030F30F4E32E0D609A | SHA256:8FD66391012E146220301DDC56432D2B6A24B072BBA01C05C482BE3A06475EC9 | |||
| 1524 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\en-us.html | html | |
MD5:5001C5247AF7E35AC35ACE61B87E8040 | SHA256:2920ED0DDFE475884703A5AE7B835F40398E509AA26B52A8DDD7F25DCD4B3D2E | |||
| 1028 | Windows Loader.exe | C:\Dell.XRM-MS | xml | |
MD5:18B1E45BF56F40C3C4BBE65831178216 | SHA256:D072A059D3ED3E75C98B85B41E4319E8D5CFAE0E0C239B62436A3AD34003AB4A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
69
DNS requests
88
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1524 | sipnotify.exe | HEAD | 503 | 104.102.43.250:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133949500878430000 | unknown | — | — | whitelisted |
2624 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://crt.sectigo.com/SectigoPublicServerAuthenticationRootR46.p7c | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1524 | sipnotify.exe | 104.102.43.250:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | whitelisted |
1112 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2624 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2436 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2624 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2624 | msedge.exe | 104.21.16.1:443 | blog.yam.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
blog.yam.com |
| whitelisted |
www.yam.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
code.jquery.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
weather.yam.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2624 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2624 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2624 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |