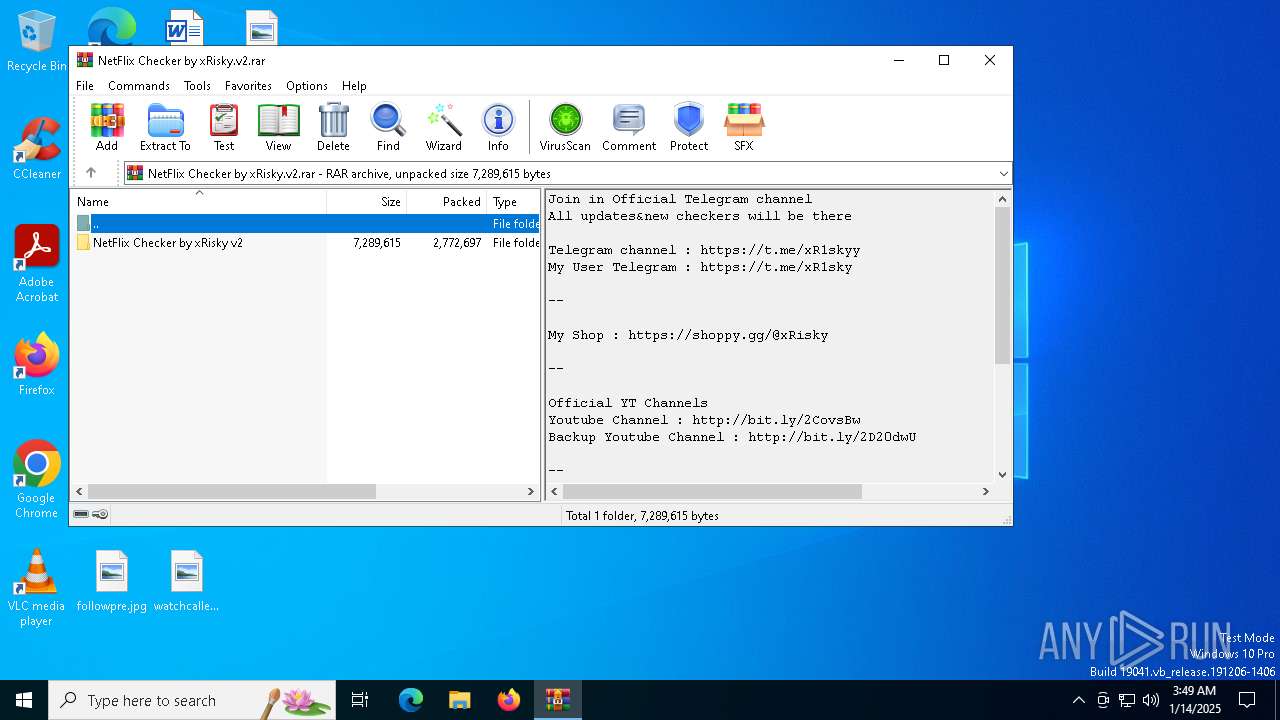
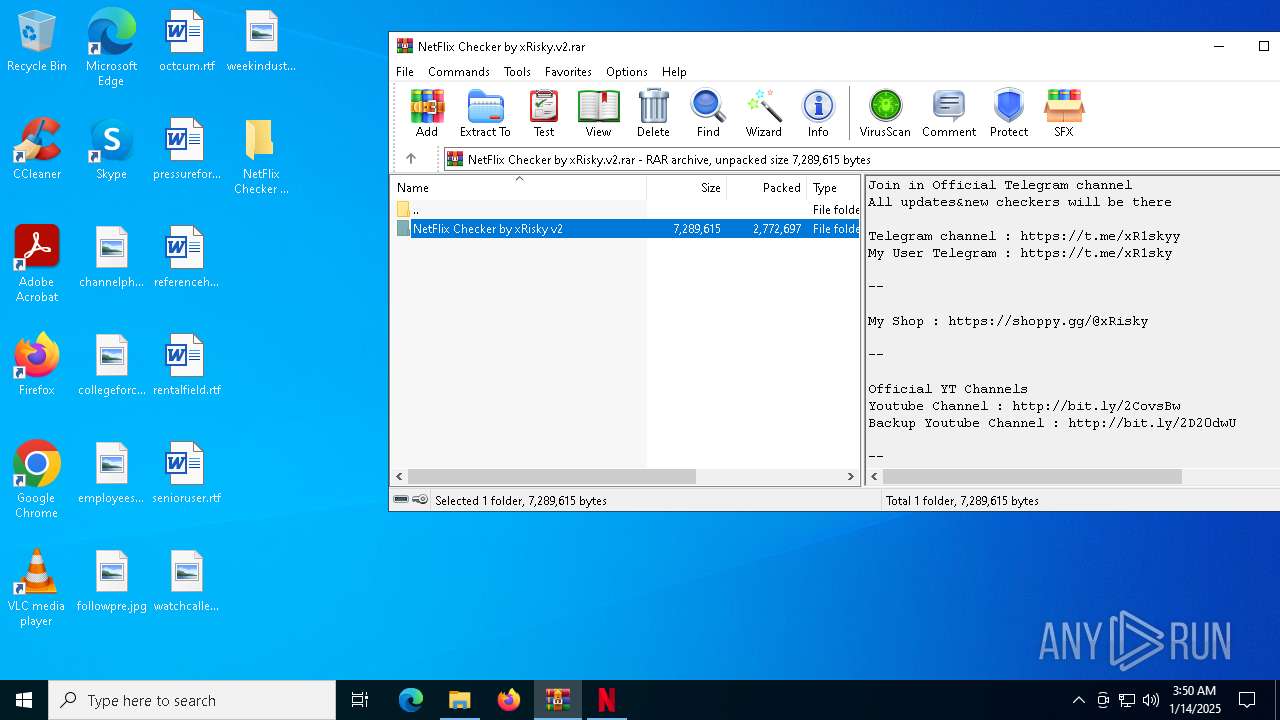
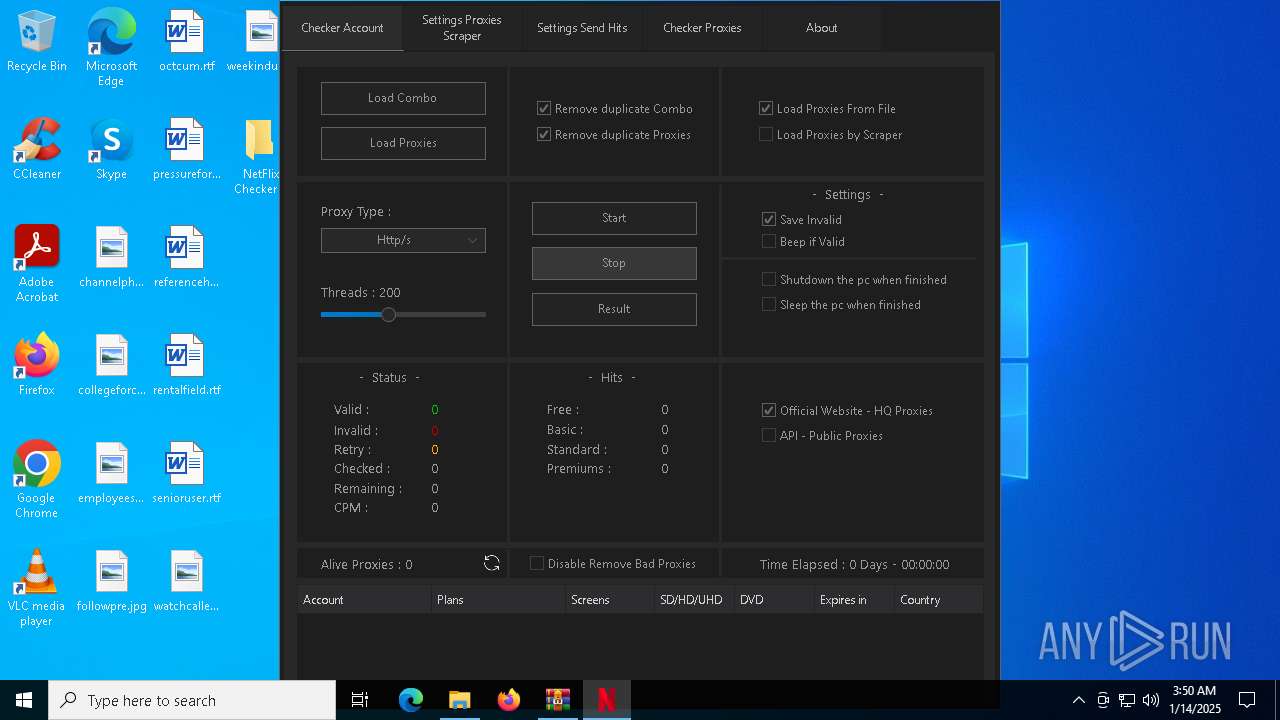
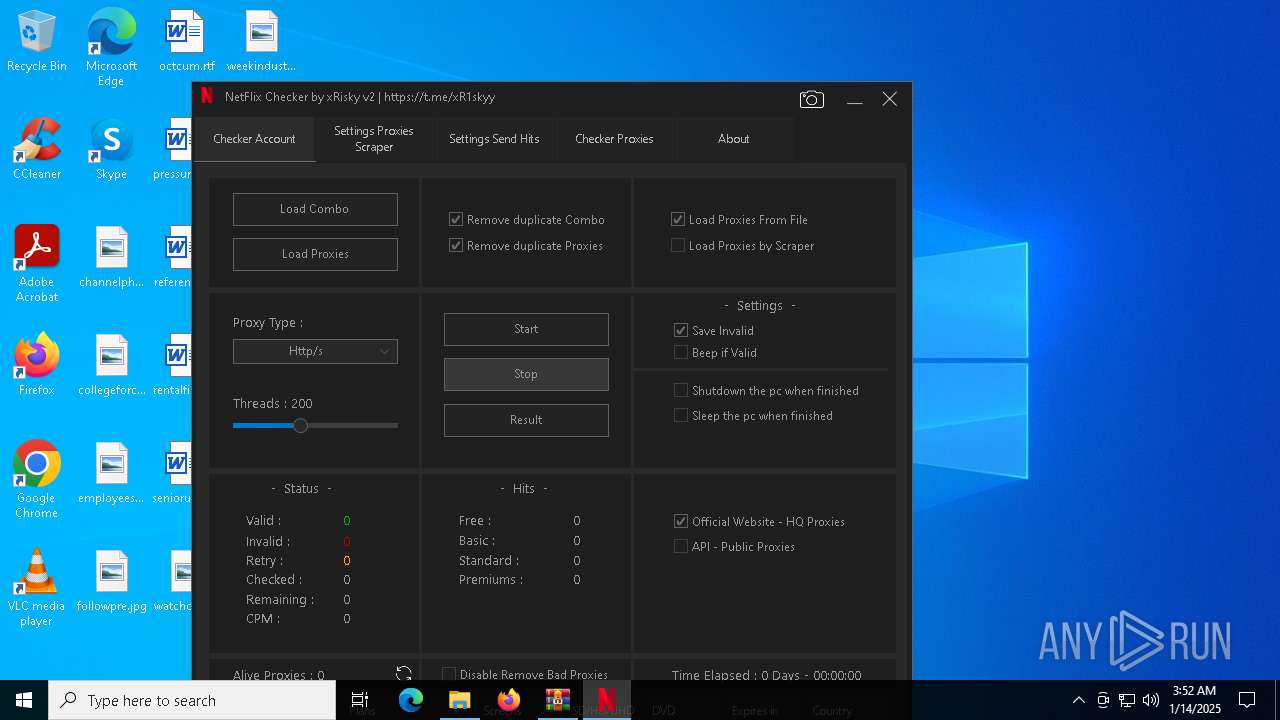
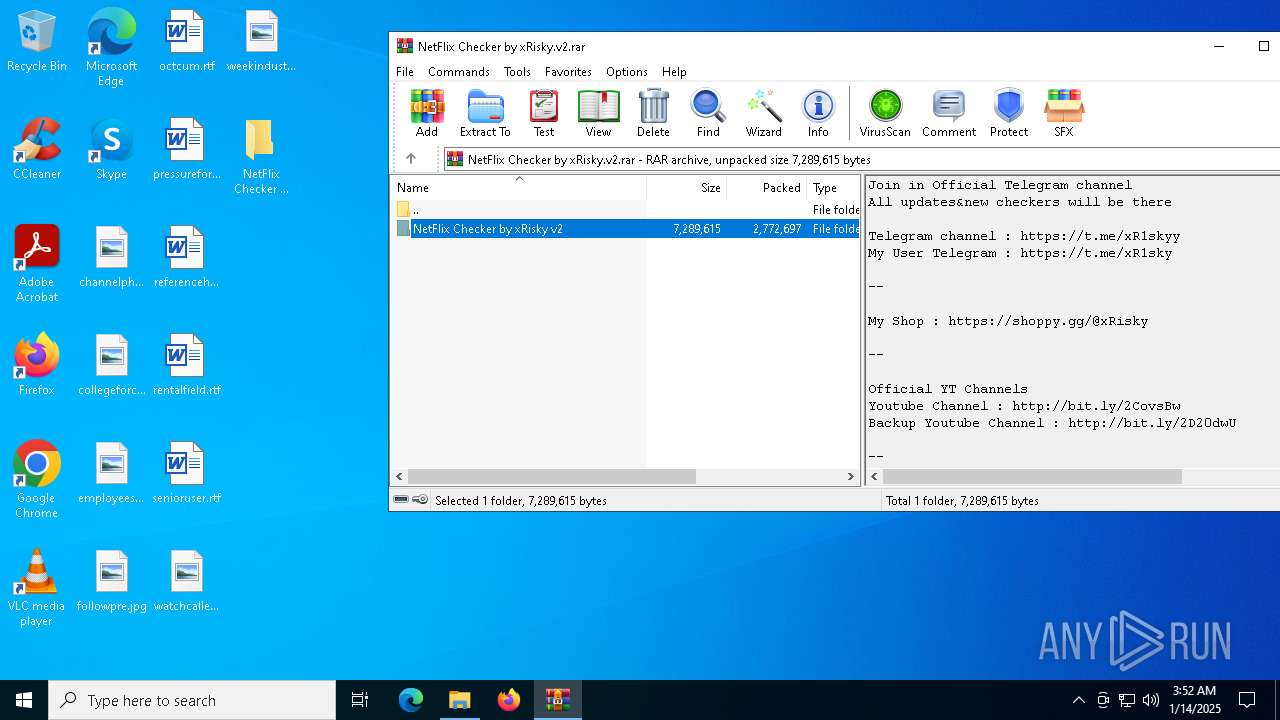
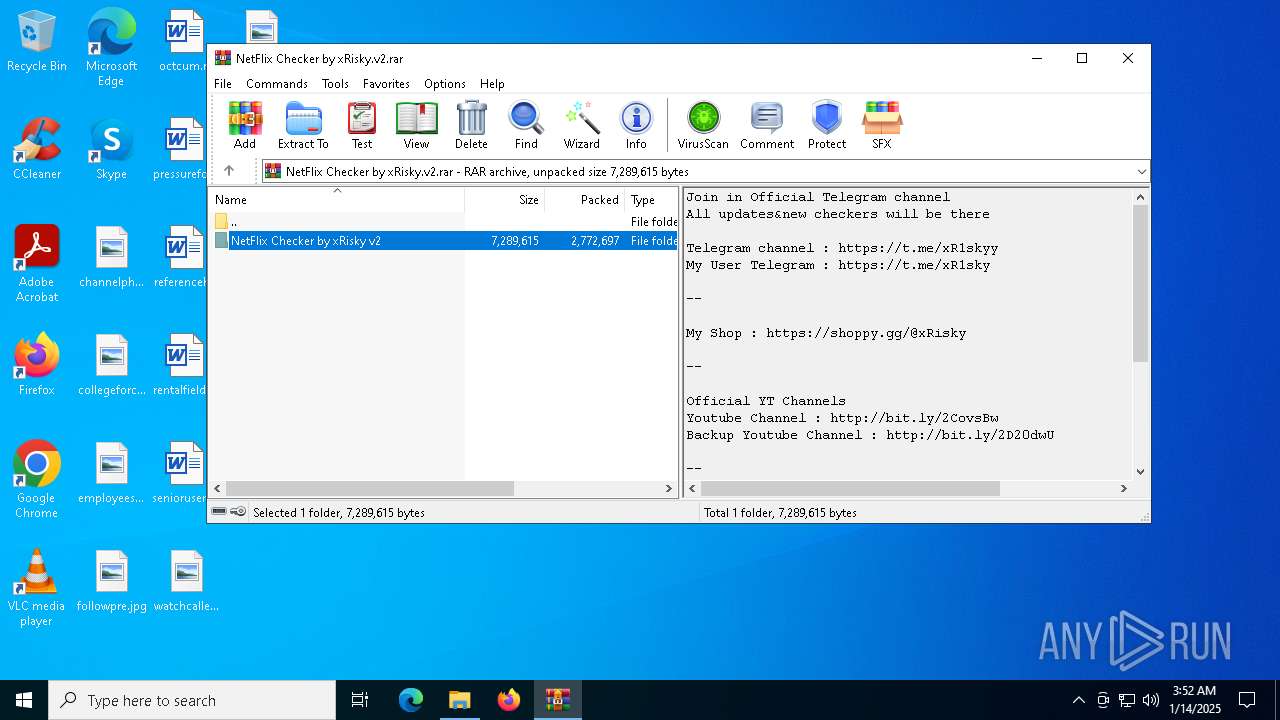
| File name: | NetFlix Checker by xRisky.v2.rar |
| Full analysis: | https://app.any.run/tasks/c0ca1f39-18bb-46e6-9a82-9449cbfad845 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2025, 03:49:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 84E344CAB1BFA4A206116B22617D6EB7 |
| SHA1: | F717059ACD2FF6A7C917F5A76D810A33CF593AAC |
| SHA256: | ED444CE779692ED42CF8104F93E594B23ECB4C8C80245FF194BAF402E1F098BD |
| SSDEEP: | 98304:8E28PS/G2nhTz2A0lXHiM7TV1TccfFjKMnGIkOrgH9UQGcY8rUUvqexpPH9YeWtT:KXXvK7 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2632)
XORed URL has been found (YARA)
- NetFlix Checker by xRisky v2.exe (PID: 4536)
SUSPICIOUS
Reads security settings of Internet Explorer
- NetFlix Checker by xRisky v2.exe (PID: 4536)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2632)
- NetFlix Checker by xRisky v2.exe (PID: 4536)
Reads the computer name
- NetFlix Checker by xRisky v2.exe (PID: 4536)
Reads the machine GUID from the registry
- NetFlix Checker by xRisky v2.exe (PID: 4536)
Confuser has been detected (YARA)
- NetFlix Checker by xRisky v2.exe (PID: 4536)
Checks supported languages
- NetFlix Checker by xRisky v2.exe (PID: 4536)
Manual execution by a user
- NetFlix Checker by xRisky v2.exe (PID: 4536)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(4536) NetFlix Checker by xRisky v2.exe
Decrypted-URLs (29)https://botostore.com/c/channelidbot/#
https://crack.sx/member.php?action=profile&uid=93#comments/1
https://crack.sx/member.php?action=profile&uid=93#comments/1Qw
https://crack.sx/member.php?action=register&referrer=93
https://crack.sx/member.php?action=register&referrer=93qmmij#66zkxzr7ja6t
https://cracked.to/member.php?action=profile&uid=18273M
https://cracked.to/member.php?action=profile&uid=18273osswt=((dufdlbc)sh(jbjebu)wow8fdsnhi:wuhankb!rnc:6?504J
https://cracked.to/member.php?action=register&referrer=18273
https://cracked.to/member.php?action=register&referrer=18273$
https://i.imgur.com/MkdCnW7.gif
https://i.imgur.com/MkdCnW7.gifF
https://i.imgur.com/MkdCnW7.gifH
https://shoppy.gg/user/xRisky
https://shoppy.gg/user/xRisky6**.-dqq-61..'p99q+-;,q&
https://t.me/xR1skyy
https://t.me/xR1skyyEYY]
https://t.me/xR1skyyy
https://twitter.com/c09e
https://www.file-up.org/users/xRisky/68193/Cracking%20Tools%20%7C%20by%20xRisky
https://www.file-up.org/users/xRisky/68193/Cracking%20Tools%20%7C%20by%20xRiskyI7l
https://www.netflix.com/Login
https://www.siteguarding.com/en/how-to-get-telegram-bot-api-token
https://www.up-4ever.net/users/xRisky/42448/Cracking%20Tools%20%7C%20by%20xRisky
https://www.up-4ever.net/users/xRisky/42448/Cracking%20Tools%20%7C%20by%20xRiskyuO
https://www.up-4ever.net/users/xRisky/45994/Combo%20List%20%7C%20by%20xRisky)5512
https://www.up-4ever.net/users/xRisky/45994/Combo%20List%20%7C%20by%20xRiskyIm
https://www.youtube.com/channel/UC4Qrk2izrHqCr6TuYfyWmig?guided_help_flow=3&disable_polymer=true
https://www.youtube.com/channel/UCsnpw8YMqjv9tkJSNuEzrfA?view_as=subscriber0
https://www.youtube.com/channel/UCsnpw8YMqjv9tkJSNuEzrfA?view_as=subscriberEYY]
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
130
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2632 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NetFlix Checker by xRisky.v2.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4536 | "C:\Users\admin\Desktop\NetFlix Checker by xRisky v2\NetFlix Checker by xRisky v2.exe" | C:\Users\admin\Desktop\NetFlix Checker by xRisky v2\NetFlix Checker by xRisky v2.exe | explorer.exe | ||||||||||||
User: admin Company: __xRisky__ Integrity Level: MEDIUM Description: NetFlix Checker by xRisky v2 Exit code: 4294967295 Version: 1.0.0.0 Modules
xor-url(PID) Process(4536) NetFlix Checker by xRisky v2.exe Decrypted-URLs (29)https://botostore.com/c/channelidbot/# https://crack.sx/member.php?action=profile&uid=93#comments/1 https://crack.sx/member.php?action=profile&uid=93#comments/1Qw https://crack.sx/member.php?action=register&referrer=93 https://crack.sx/member.php?action=register&referrer=93qmmij#66zkxzr7ja6t https://cracked.to/member.php?action=profile&uid=18273M https://cracked.to/member.php?action=profile&uid=18273osswt=((dufdlbc)sh(jbjebu)wow8fdsnhi:wuhankb!rnc:6?504J https://cracked.to/member.php?action=register&referrer=18273 https://cracked.to/member.php?action=register&referrer=18273$ https://i.imgur.com/MkdCnW7.gif https://i.imgur.com/MkdCnW7.gifF https://i.imgur.com/MkdCnW7.gifH https://shoppy.gg/user/xRisky https://shoppy.gg/user/xRisky6**.-dqq-61..'p99q+-;,q& https://t.me/xR1skyy https://t.me/xR1skyyEYY] https://t.me/xR1skyyy https://twitter.com/c09e https://www.file-up.org/users/xRisky/68193/Cracking%20Tools%20%7C%20by%20xRisky https://www.file-up.org/users/xRisky/68193/Cracking%20Tools%20%7C%20by%20xRiskyI7l https://www.netflix.com/Login https://www.siteguarding.com/en/how-to-get-telegram-bot-api-token https://www.up-4ever.net/users/xRisky/42448/Cracking%20Tools%20%7C%20by%20xRisky https://www.up-4ever.net/users/xRisky/42448/Cracking%20Tools%20%7C%20by%20xRiskyuO https://www.up-4ever.net/users/xRisky/45994/Combo%20List%20%7C%20by%20xRisky)5512 https://www.up-4ever.net/users/xRisky/45994/Combo%20List%20%7C%20by%20xRiskyIm https://www.youtube.com/channel/UC4Qrk2izrHqCr6TuYfyWmig?guided_help_flow=3&disable_polymer=true https://www.youtube.com/channel/UCsnpw8YMqjv9tkJSNuEzrfA?view_as=subscriber0 https://www.youtube.com/channel/UCsnpw8YMqjv9tkJSNuEzrfA?view_as=subscriberEYY] | |||||||||||||||
| 7064 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 836
Read events
1 817
Write events
19
Delete events
0
Modification events
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NetFlix Checker by xRisky.v2.rar | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Comment |
| Operation: | write | Name: | LeftBorder |
Value: 472 | |||
| (PID) Process: | (2632) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C00000000000000010000000083FFFF0083FFFFFFFFFFFFFFFFFFFFC70000002B0000008704000013020000 | |||
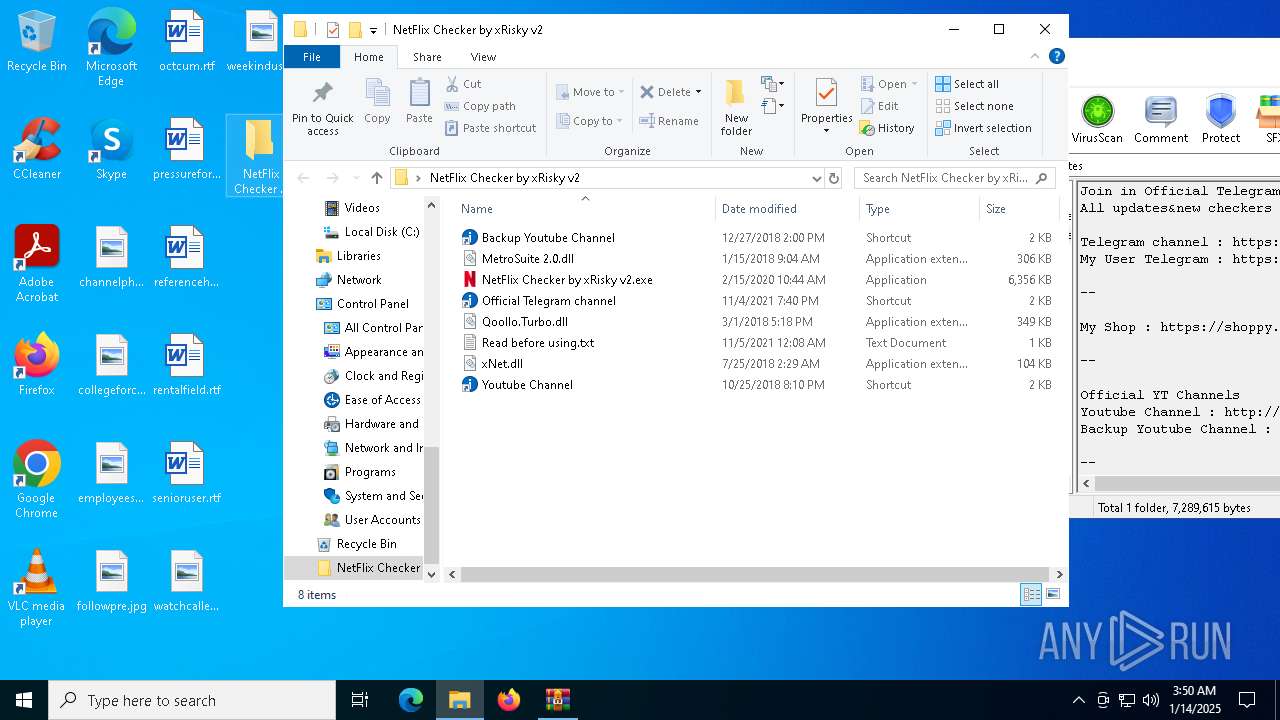
Executable files
4
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\Backup Youtube Channel.lnk | binary | |
MD5:DEB42BBEC322CD0B8319F788312E28C4 | SHA256:B3BB48A747CC7078D4C4C5BD872A270B59F328AE90A85EF3D955B8A4892BFF41 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\MetroSuite 2.0.dll | executable | |
MD5:0D30A398CEC0FF006B6EA2B52D11E744 | SHA256:8604BF2A1FE2E94DC1EA1FBD0CF54E77303493B93994DF48479DC683580AA654 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\xNet.dll | executable | |
MD5:158DEFD55A804AA8D4D67BFDF7A4AF9C | SHA256:6C7EC4CC31A2CE0B97703B7A42E3448E9B87D96DDA12761CA24D8787AC27CFF1 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\Official Telegram channel.lnk | binary | |
MD5:AD5DFDC516B8AD8ED2124669F079177F | SHA256:AB844B860BE797A453479A4271C873B14719F0D7094B927A254B178E2277CE71 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\Qoollo.Turbo.dll | executable | |
MD5:4E8246DF4EE956EC273C4BAA2054593C | SHA256:1172732FD0FE6B679F5C6BF750598133DC815622C55EF1FA84087087BF42B495 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\Youtube Channel.lnk | binary | |
MD5:C7056A1F92245EEC9E5CA71F406C4811 | SHA256:BDE117478E44D3AA7D55122CF450F10B5AF74CFB4CE82AE4FC6FB7DD414C2469 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\NetFlix Checker by xRisky v2.exe | executable | |
MD5:5767A86DEDD068E8F14F1570A9052303 | SHA256:CC815FCC20A41A0A2BF9C1574518004327EBB889E666D964E095482C5996EF11 | |||
| 2632 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2632.41742\NetFlix Checker by xRisky v2\Read before using.txt | text | |
MD5:59E08371620A829093CC8A6BC2A8C9E8 | SHA256:BBD6779158ACEA247E0B136A6869BDFF4707DD47FA03309BA9D17EE01351250E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6484 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1468 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.19.122.26:443 | — | Akamai International B.V. | DE | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1468 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |