| File name: | Support.ClientSetup.exe |
| Full analysis: | https://app.any.run/tasks/1ba3f576-6b01-498f-8c6a-c6855d09164c |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 07:02:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D566E8D666CB4D3AD96A9D1CFFE13FA3 |
| SHA1: | 579B4F0BFB9CA6A12FCE7C6087B6CFA2209373E9 |
| SHA256: | ED36741ACF9972521036673D90BC463976B5A2C15E6A09EF95B8AD67027FF982 |
| SSDEEP: | 98304:XWQhWmMdnP5szFOytH9awXB0DXe3S+5OmxlGwP3AW5JTGG0DR/W03h9/5QaWhbDA:f4gDAy8+w1L |
MALICIOUS
Drops the executable file immediately after the start
- Support.ClientSetup.exe (PID: 900)
- msiexec.exe (PID: 4636)
Creates a writable file in the system directory
- ScreenConnect.ClientService.exe (PID: 6752)
SUSPICIOUS
Reads security settings of Internet Explorer
- Support.ClientSetup.exe (PID: 900)
- ScreenConnect.ClientService.exe (PID: 6752)
- ScreenConnect.WindowsClient.exe (PID: 6848)
Reads the date of Windows installation
- Support.ClientSetup.exe (PID: 900)
Executable content was dropped or overwritten
- rundll32.exe (PID: 2328)
The process creates files with name similar to system file names
- msiexec.exe (PID: 4636)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 6752)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 4636)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 6752)
- VSSVC.exe (PID: 2832)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 6752)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4636)
INFO
Create files in a temporary directory
- Support.ClientSetup.exe (PID: 900)
- rundll32.exe (PID: 2328)
Checks supported languages
- Support.ClientSetup.exe (PID: 900)
- msiexec.exe (PID: 4636)
- msiexec.exe (PID: 5776)
- msiexec.exe (PID: 6676)
- ScreenConnect.WindowsClient.exe (PID: 6848)
- msiexec.exe (PID: 6720)
- ScreenConnect.ClientService.exe (PID: 6752)
Reads the computer name
- Support.ClientSetup.exe (PID: 900)
- msiexec.exe (PID: 4636)
- msiexec.exe (PID: 5776)
- msiexec.exe (PID: 6676)
- msiexec.exe (PID: 6720)
- ScreenConnect.ClientService.exe (PID: 6752)
- ScreenConnect.WindowsClient.exe (PID: 6848)
Reads the machine GUID from the registry
- Support.ClientSetup.exe (PID: 900)
- ScreenConnect.WindowsClient.exe (PID: 6848)
- ScreenConnect.ClientService.exe (PID: 6752)
Process checks computer location settings
- Support.ClientSetup.exe (PID: 900)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1540)
- msiexec.exe (PID: 4636)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1540)
- rundll32.exe (PID: 2328)
Creates a software uninstall entry
- msiexec.exe (PID: 4636)
Disables trace logs
- ScreenConnect.ClientService.exe (PID: 6752)
Reads Environment values
- ScreenConnect.ClientService.exe (PID: 6752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:18 20:10:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 45568 |
| InitializedDataSize: | 5512704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14ad |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
145
Monitored processes
13
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\Users\admin\AppData\Local\Temp\Support.ClientSetup.exe" | C:\Users\admin\AppData\Local\Temp\Support.ClientSetup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
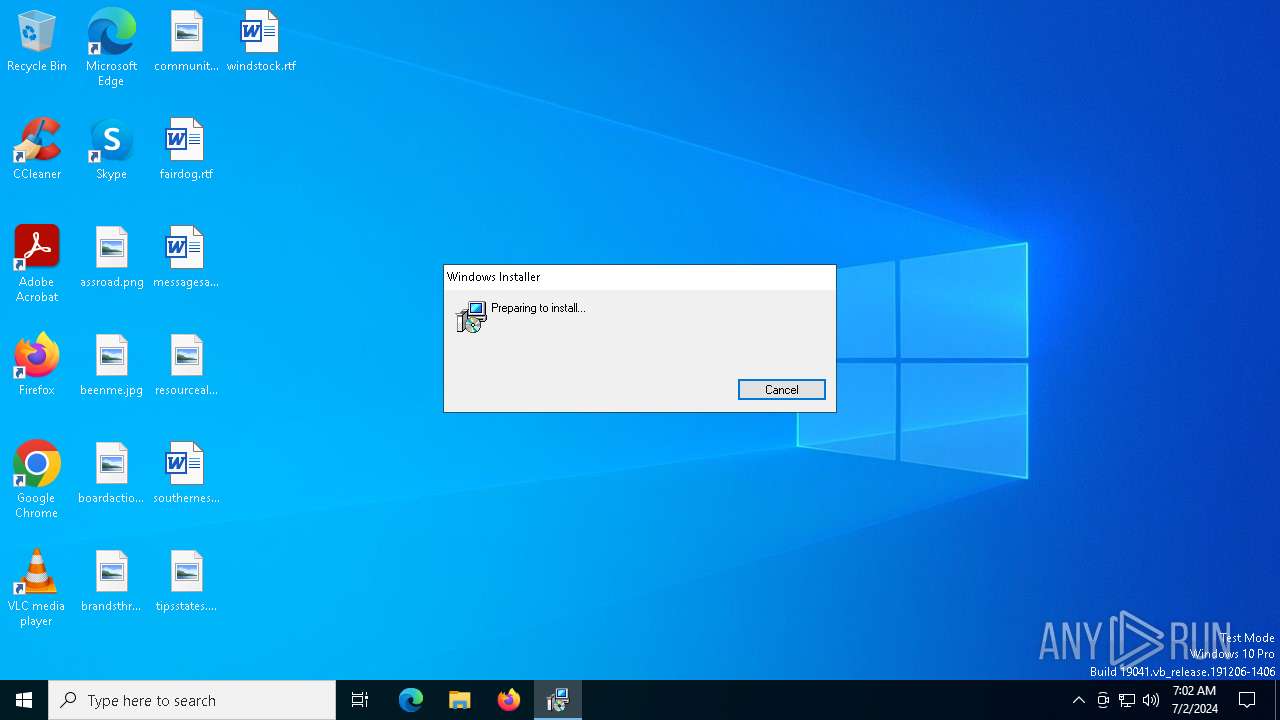
| 1540 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ScreenConnect\0b03fa83feb97678\setup.msi" | C:\Windows\SysWOW64\msiexec.exe | Support.ClientSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2328 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1765140 1 ScreenConnect.InstallerActions!ScreenConnect.ClientInstallerActions.FixupServiceArguments | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2832 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4532 | "C:\Users\admin\AppData\Local\Temp\Support.ClientSetup.exe" | C:\Users\admin\AppData\Local\Temp\Support.ClientSetup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4636 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | C:\Windows\syswow64\MsiExec.exe -Embedding CA35F8CAFC3546DCEE13C35F9456C29B C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6584 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | C:\Windows\syswow64\MsiExec.exe -Embedding A8A2B27C7529EA0FD1E0B94FD0EA9A94 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 342
Read events
7 012
Write events
311
Delete events
19
Modification events
| (PID) Process: | (900) Support.ClientSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (900) Support.ClientSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (900) Support.ClientSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (900) Support.ClientSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4636) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000ABE7A1CD4DCCDA011C12000034090000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4636) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000ABE7A1CD4DCCDA011C12000034090000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4636) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000677CDDCD4DCCDA011C12000034090000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4636) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000677CDDCD4DCCDA011C12000034090000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4636) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000B2E0DFCD4DCCDA011C12000034090000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4636) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000087A7E4CD4DCCDA011C12000034090000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
20
Suspicious files
18
Text files
21
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 900 | Support.ClientSetup.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\0b03fa83feb97678\setup.msi | — | |
MD5:— | SHA256:— | |||
| 2328 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:5EF88919012E4A3D8A1E2955DC8C8D81 | SHA256:3E54286E348EBD3D70EAED8174CCA500455C3E098CDD1FCCB167BC43D93DB29D | |||
| 4636 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4636 | msiexec.exe | C:\WINDOWS\Installer\1b1db6.msi | — | |
MD5:— | SHA256:— | |||
| 1540 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp | executable | |
MD5:5AA0850FA0802F435AD0305E96FF71B5 | SHA256:81C8EB2C3EFF9902C4A210D265ED7FC8ECB6619AEC3FBBCEDAED390E0F31C4AA | |||
| 2328 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp-\Microsoft.Deployment.WindowsInstaller.Package.dll | executable | |
MD5:A921A2B83B98F02D003D9139FA6BA3D8 | SHA256:548C551F6EBC5D829158A1E9AD1948D301D7C921906C3D8D6B6D69925FC624A1 | |||
| 2328 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp-\Microsoft.Deployment.Compression.dll | executable | |
MD5:4717BCC62EB45D12FFBED3A35BA20E25 | SHA256:E04DE7988A2A39931831977FA22D2A4C39CF3F70211B77B618CAE9243170F1A7 | |||
| 2328 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp-\ScreenConnect.Core.dll | executable | |
MD5:E8979681DECA8D48935A128D5C4789E4 | SHA256:289C9F6F4C91FF0774DE14BBCB637346CCB74ED676CB915376040674056271BC | |||
| 2328 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp-\Microsoft.Deployment.Compression.Cab.dll | executable | |
MD5:77BE59B3DDEF06F08CAA53F0911608A5 | SHA256:9D32032109FFC217B7DC49390BD01A067A49883843459356EBFB4D29BA696BF8 | |||
| 2328 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIEED6.tmp-\ScreenConnect.Windows.dll | executable | |
MD5:4BB96FA52684F734B8933900EAC0DC57 | SHA256:30A0135E30850D8D5A47AD868E1ACECA5D523E50E97298F57FD9B447384AE67C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
56
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
7072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4608 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
7072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6068 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.137:443 | — | Akamai International B.V. | DE | unknown |
1544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | unknown |
1060 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.168.112.67:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | — | EDGECAST | US | unknown |
6752 | ScreenConnect.ClientService.exe | 49.13.77.253:8041 | opensupcloud.pro | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
opensupcloud.pro |
| unknown |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |