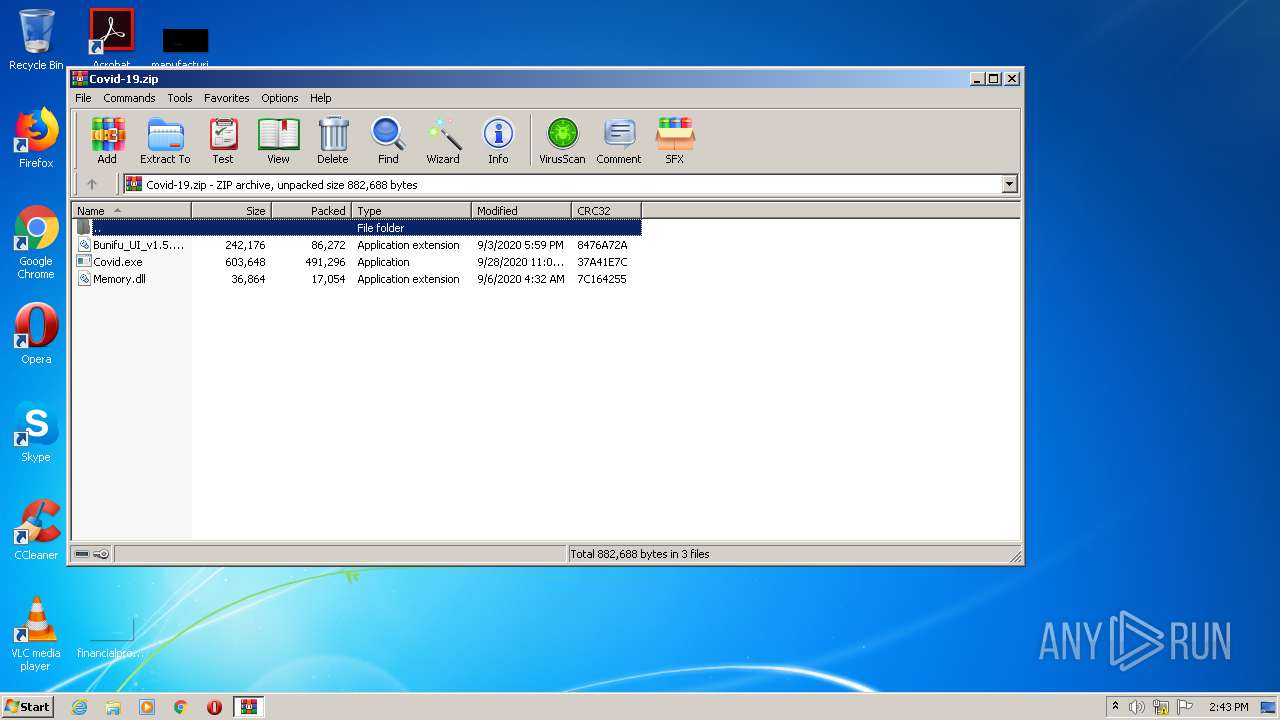
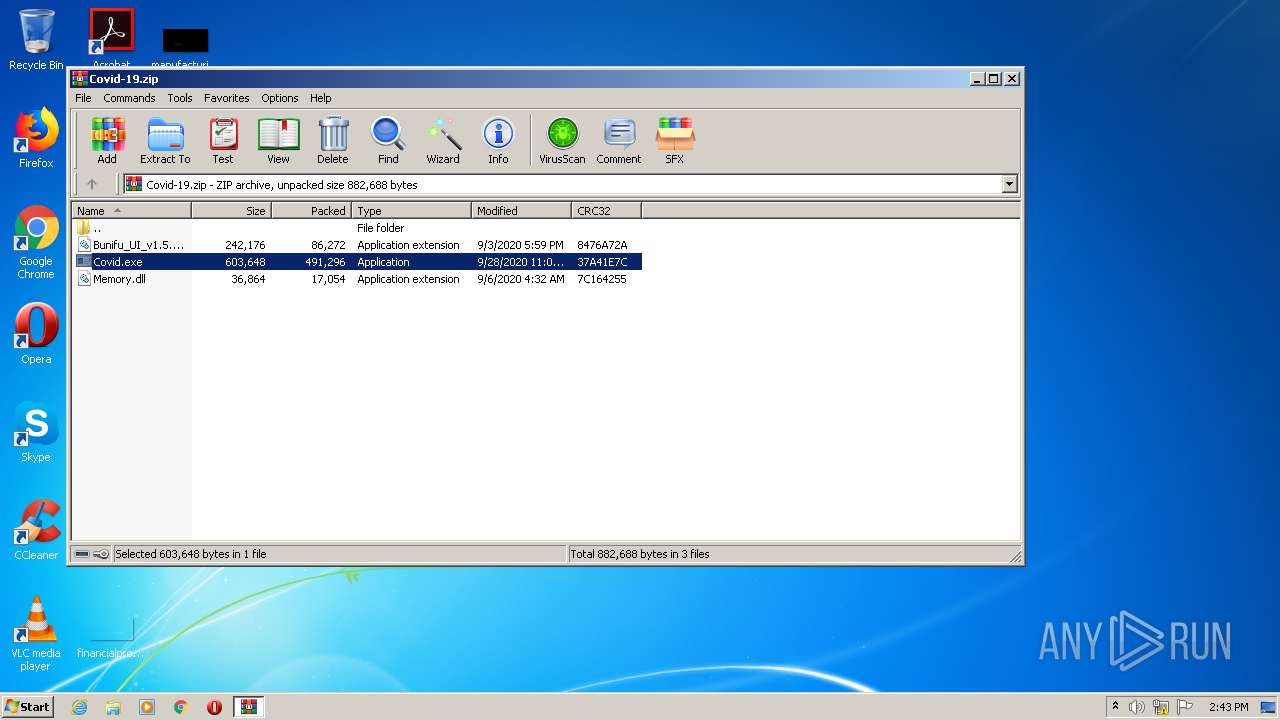
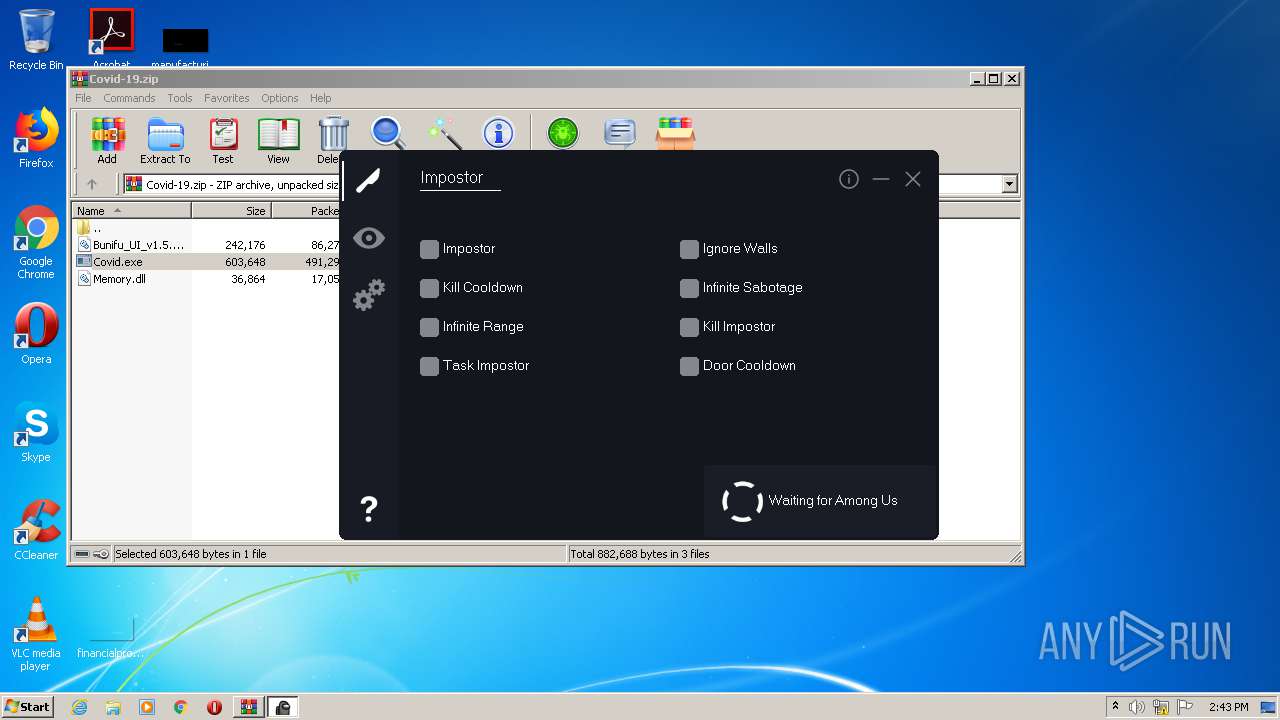
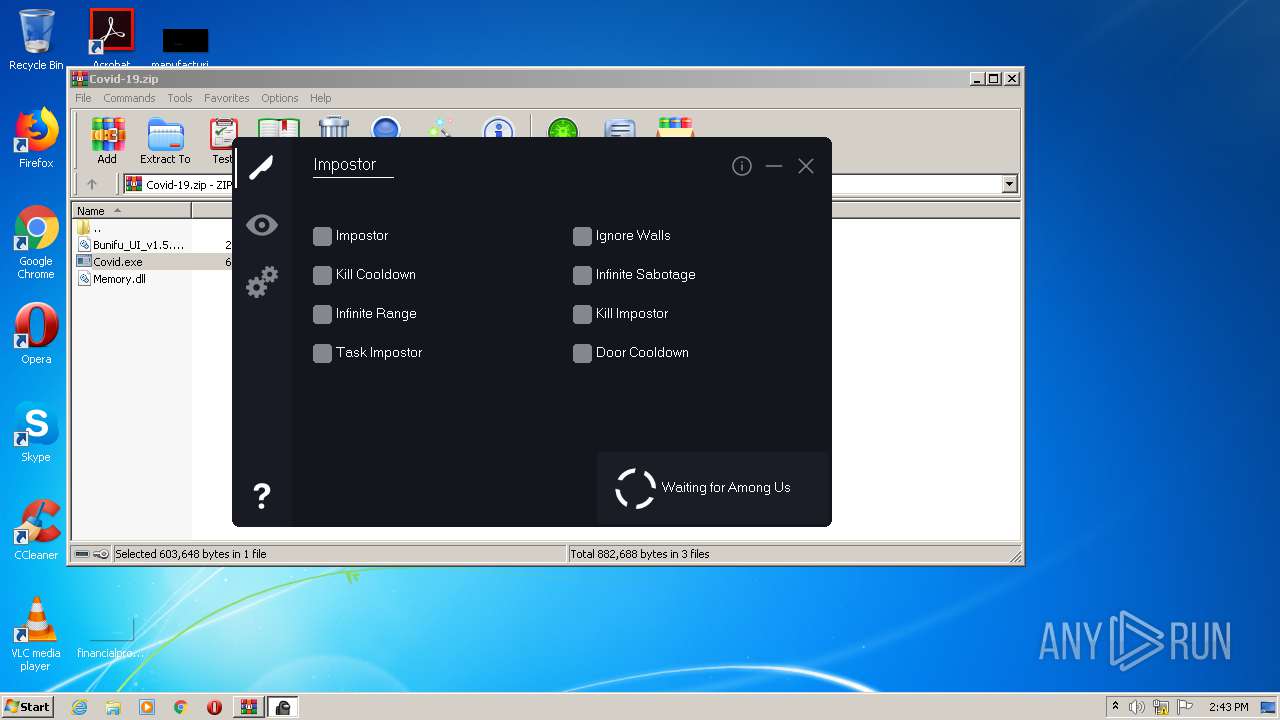
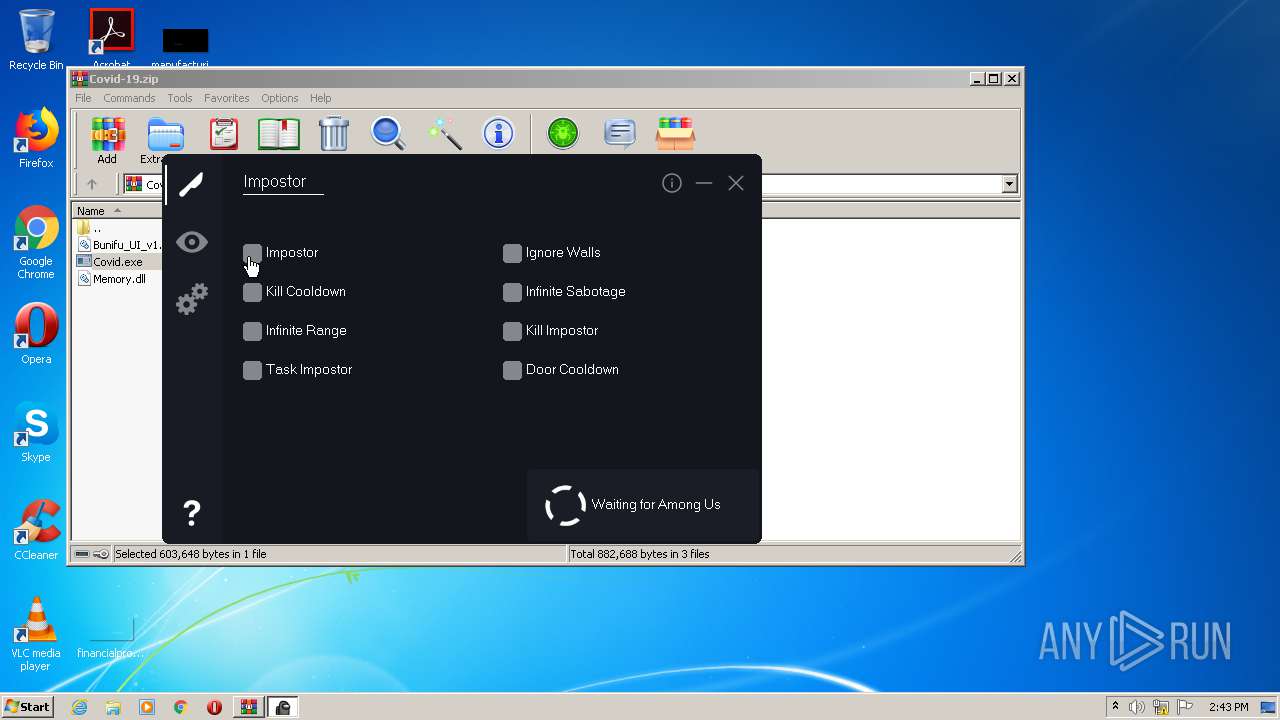
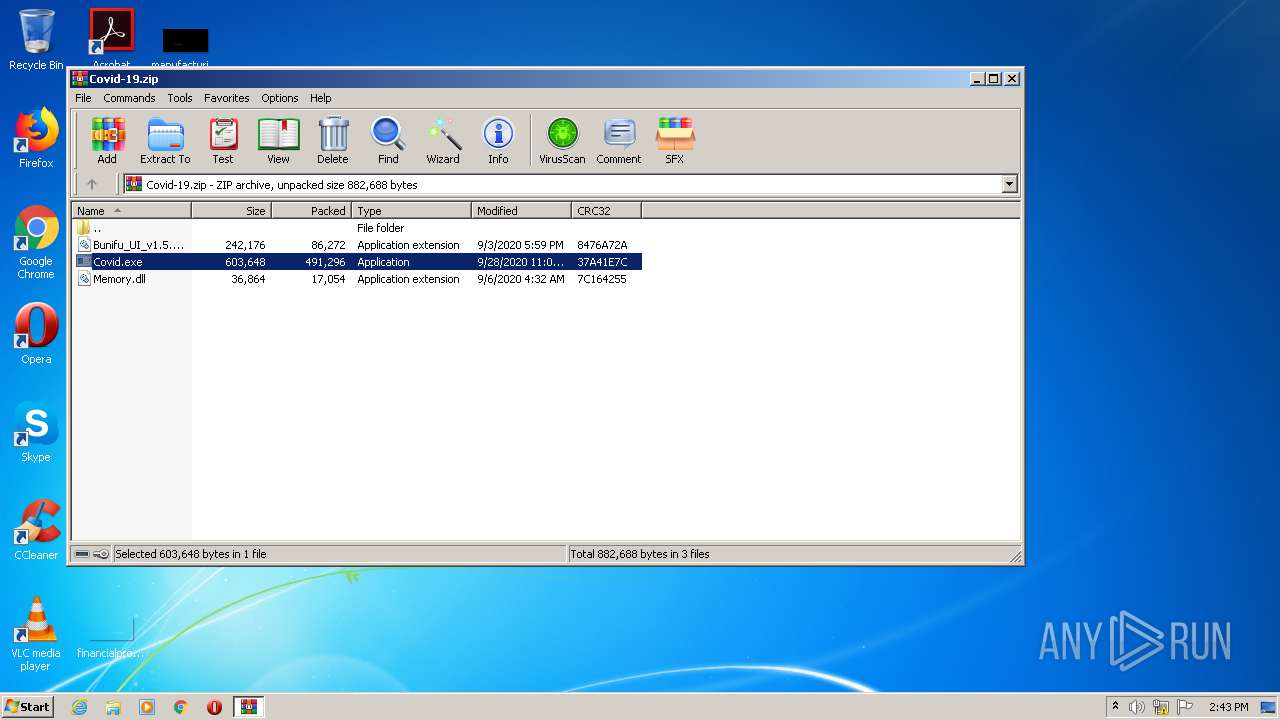
| File name: | Covid-19.zip |
| Full analysis: | https://app.any.run/tasks/5c69e343-0f3e-4495-8adf-0ae07336a3da |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 13:42:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 39B0F7B7D6BCA5F2A2EFB6CDDD3A8777 |
| SHA1: | BC5D4302F29CD754A00AD2D3B2EDF46FA31AA62A |
| SHA256: | ED2A7A23C31BEA565D49CD3DB0168973EDBB4CC0AD5F6C8DE59ED7203C711A47 |
| SSDEEP: | 12288:k+2S5dE9cnRnlxQsSi6duR3XTXEJhRCT/2m+A2cfm2v9sDVEMohijVSr0xPjI84:k+23Cn5lupWoJja2zA2cfb9wVohcVj/4 |
MALICIOUS
Loads dropped or rewritten executable
- Covid.exe (PID: 1860)
Application was dropped or rewritten from another process
- Covid.exe (PID: 1860)
- Covid.exe (PID: 3196)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 928)
INFO
Drops Coronavirus (possible) decoy
- WinRAR.exe (PID: 928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:09:03 17:59:13 |
| ZipCRC: | 0x8476a72a |
| ZipCompressedSize: | 86272 |
| ZipUncompressedSize: | 242176 |
| ZipFileName: | Bunifu_UI_v1.5.3.dll |
Total processes
39
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Covid-19.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Covid.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Covid.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Covid Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 3196 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Covid.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Covid.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Covid Exit code: 3221226540 Version: 1.0.0.2 Modules
| |||||||||||||||
Total events
462
Read events
450
Write events
12
Delete events
0
Modification events
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Covid-19.zip | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Bunifu_UI_v1.5.3.dll | executable | |
MD5:2ECB51AB00C5F340380ECF849291DBCF | SHA256:F1B3E0F2750A9103E46A6A4A34F1CF9D17779725F98042CC2475EC66484801CF | |||
| 928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Covid.exe | executable | |
MD5:— | SHA256:— | |||
| 928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa928.22916\Memory.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
Covid.exe | Adding Freezing Address GameAssembly.dll+01472280,24,5C,20,34,28 Value 1
|
Covid.exe | Module GameAssembly.dll was not found in module list!
|
Covid.exe | Modules:
|
Covid.exe | Module GameAssembly.dll was not found in module list!
|
Covid.exe | Modules:
|
Covid.exe | Modules:
|
Covid.exe | Modules:
|
Covid.exe | Modules:
|
Covid.exe | Module GameAssembly.dll was not found in module list!
|
Covid.exe | Module GameAssembly.dll was not found in module list!
|