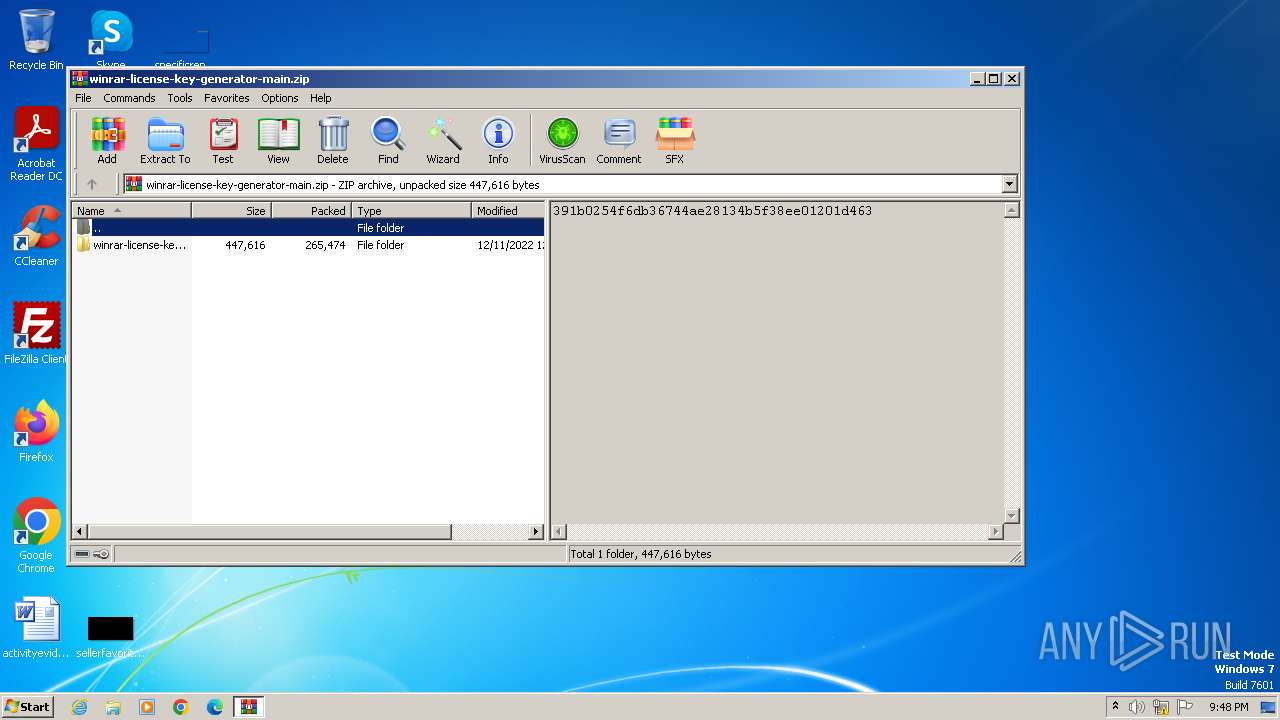
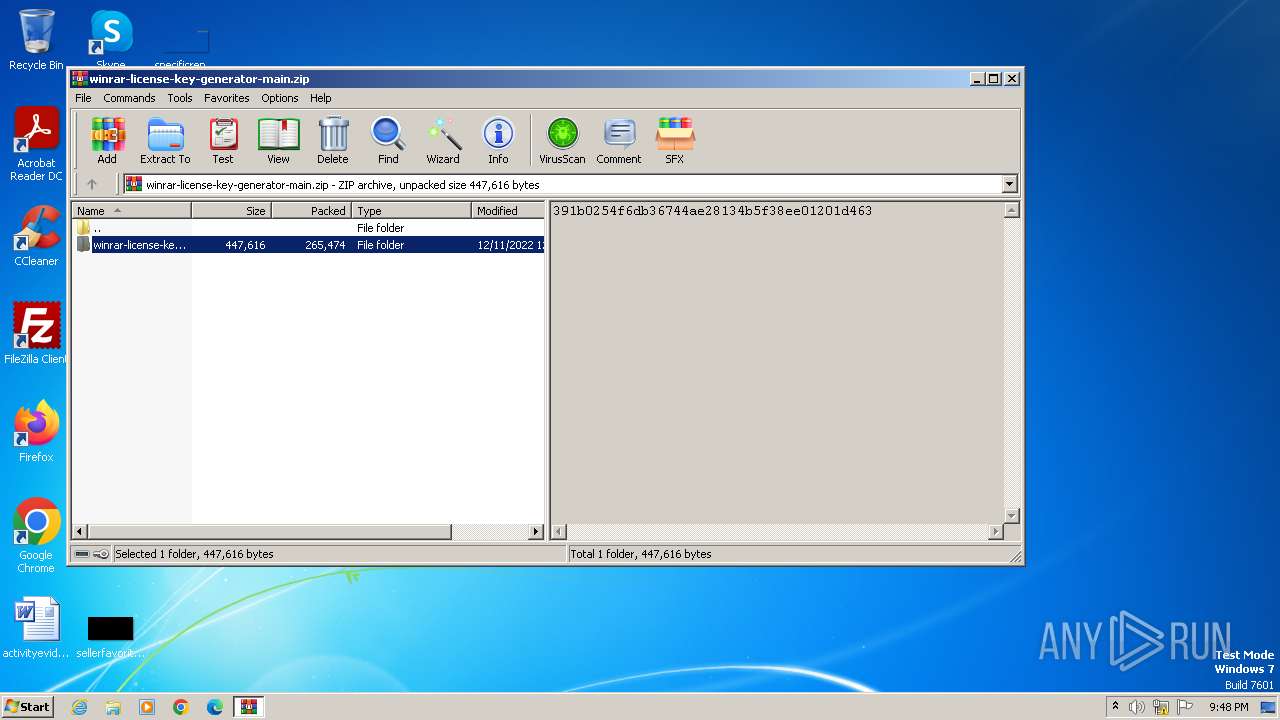
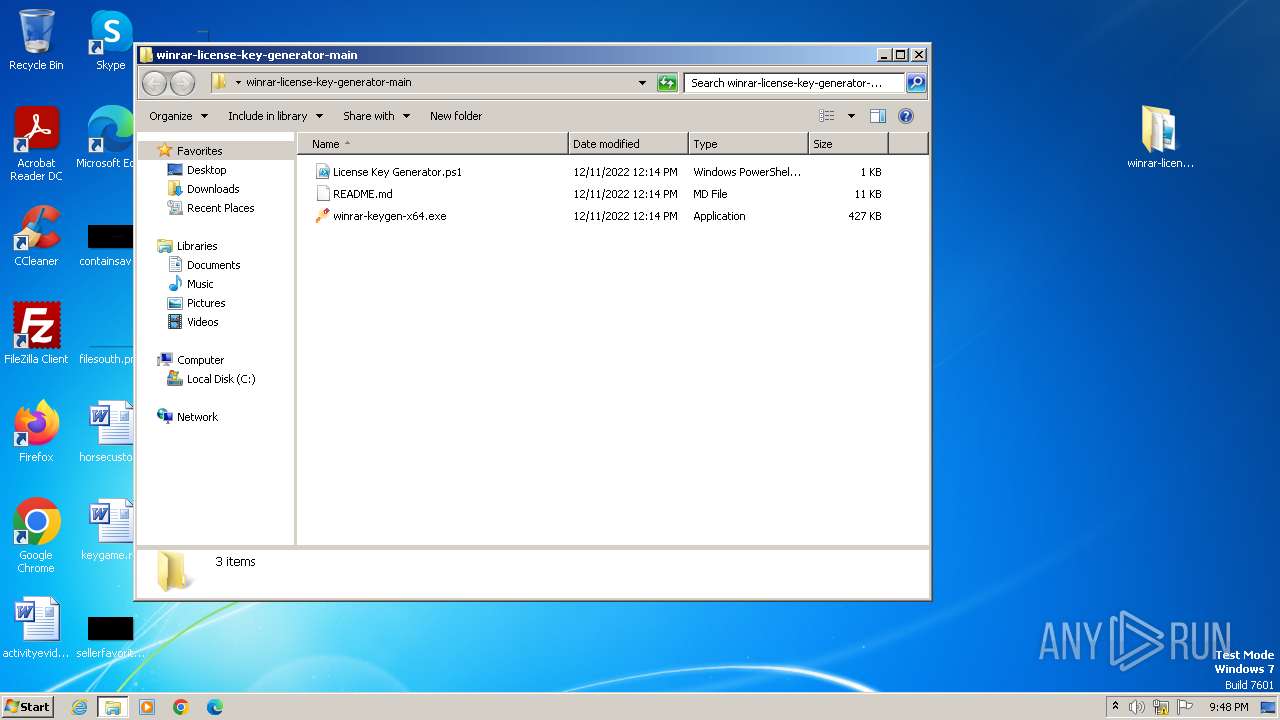
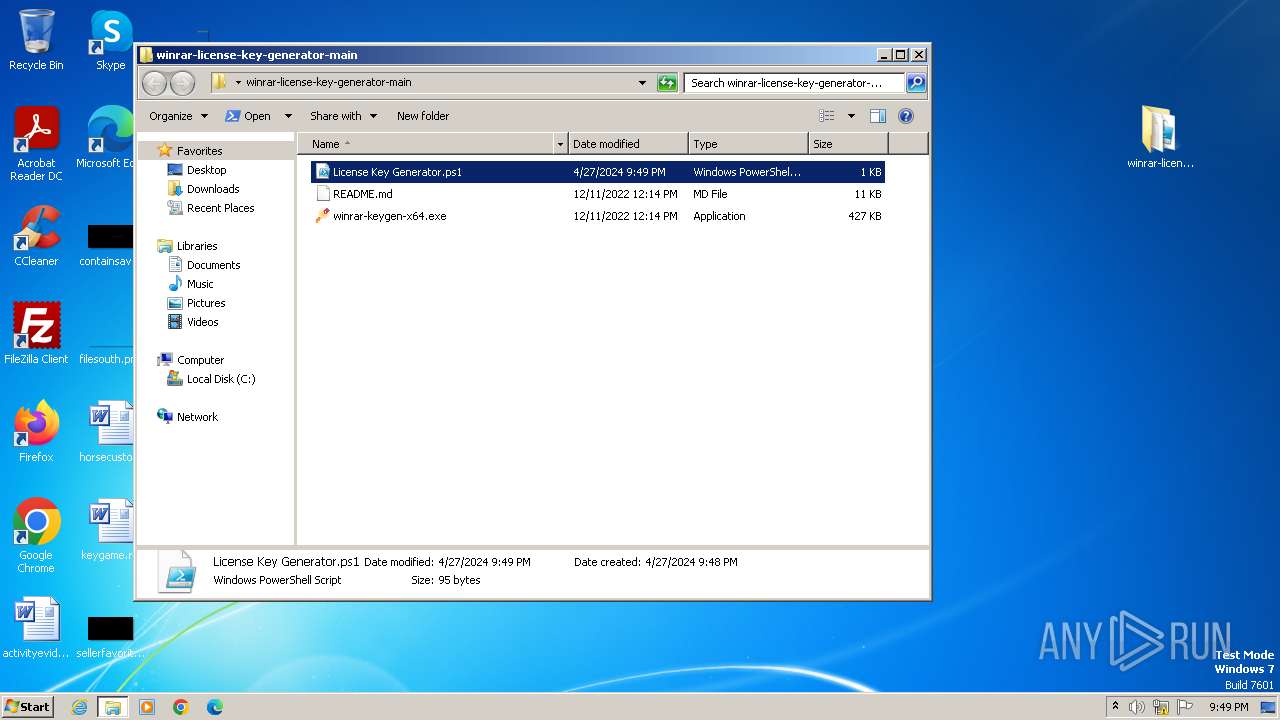
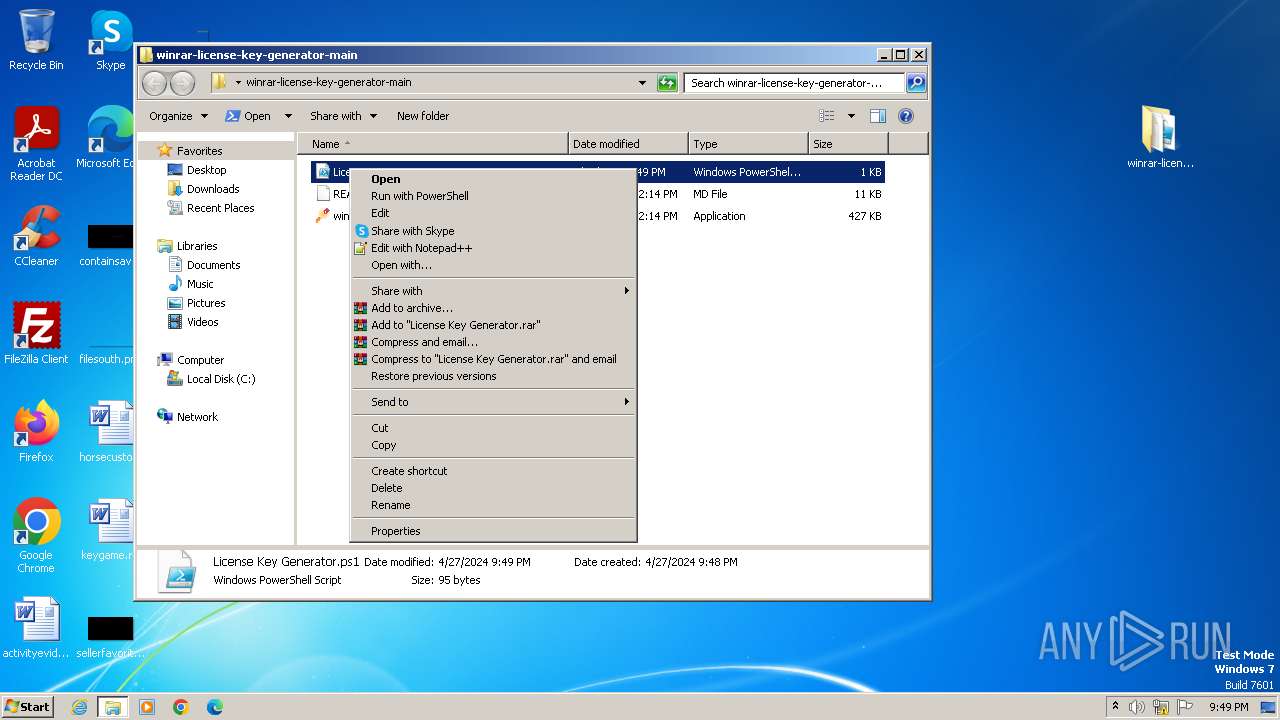
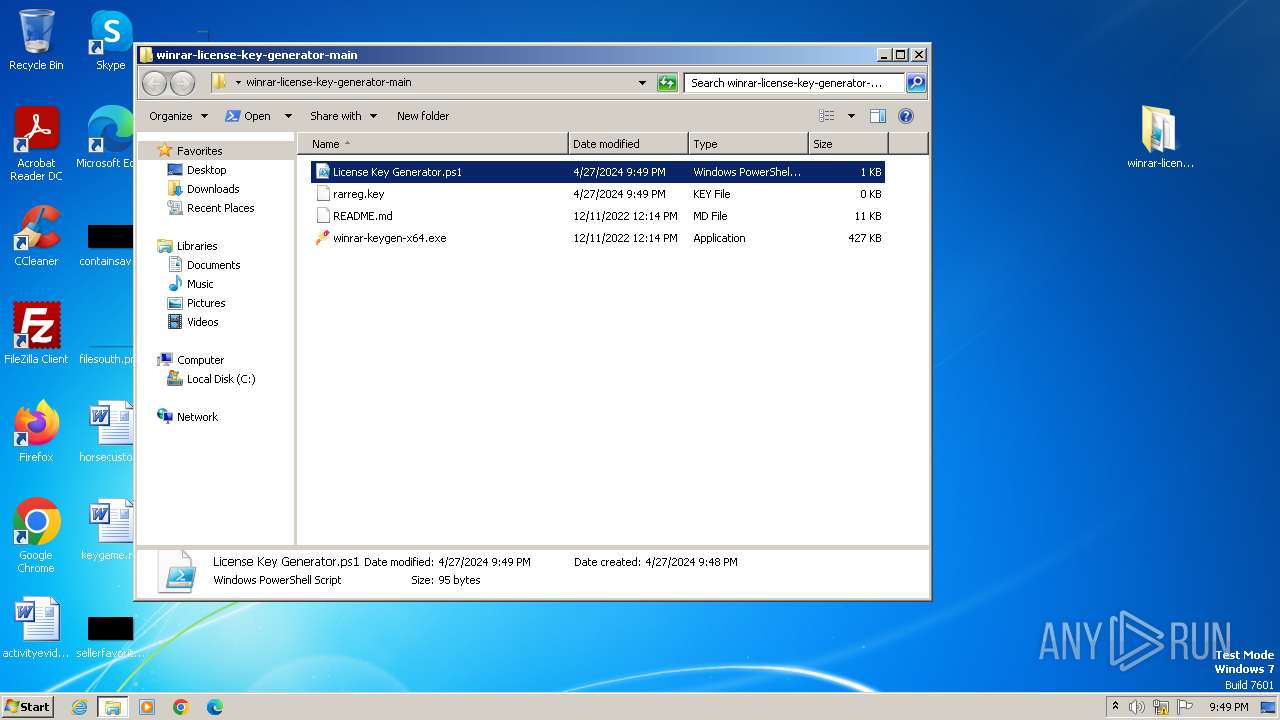
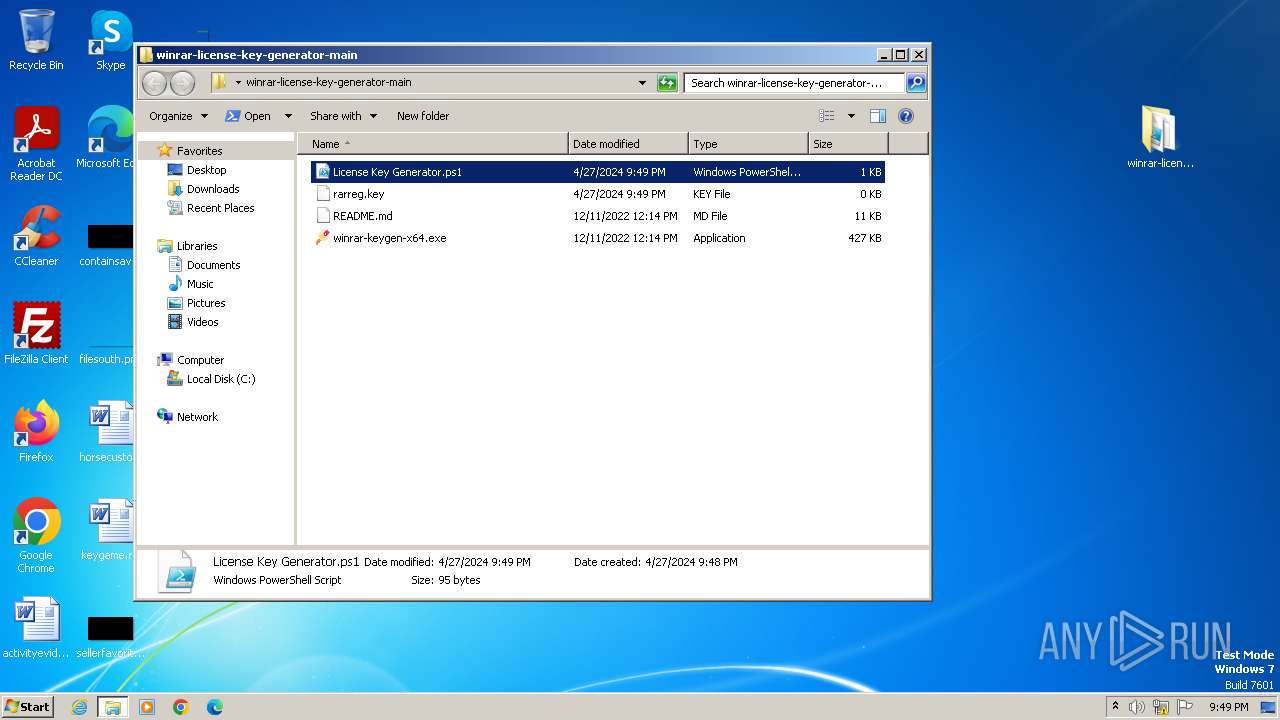
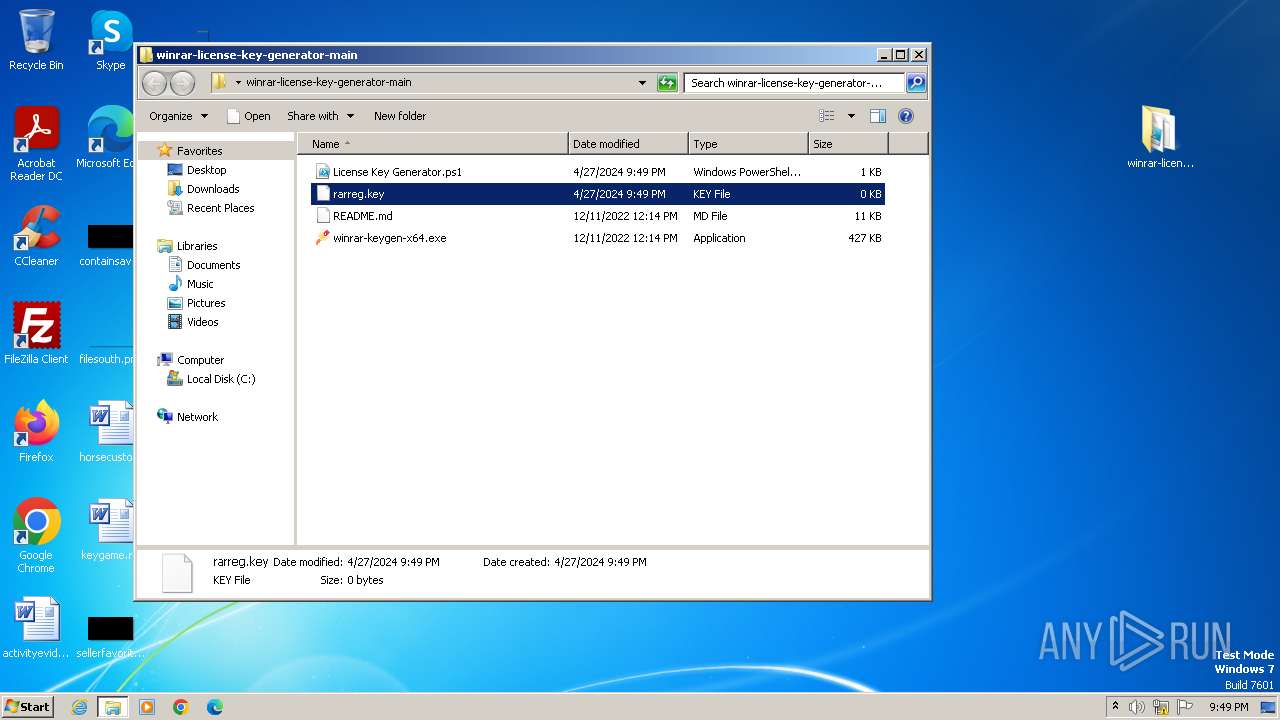
| File name: | winrar-license-key-generator-main.zip |
| Full analysis: | https://app.any.run/tasks/4065b82c-e7ac-406a-af1c-f85353b97549 |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2024, 20:48:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 5A31E8D21ADD1F01E571DA00E60B3269 |
| SHA1: | 8FFA88EA5B8766AE50DD626B713FB05CD6CEE423 |
| SHA256: | ED21EC273E491AC55843255F94E75EA4149C54DCCA75BA9A9C0F76F1979A91CA |
| SSDEEP: | 6144:IKznC/Vt6x7TH7ckFPOuBvFiBAKFTeauBto8o60AQDpjXw9zbWNscAoc:HznGVt6x7XloQFinJVeo+QDprwXWNuh |
MALICIOUS
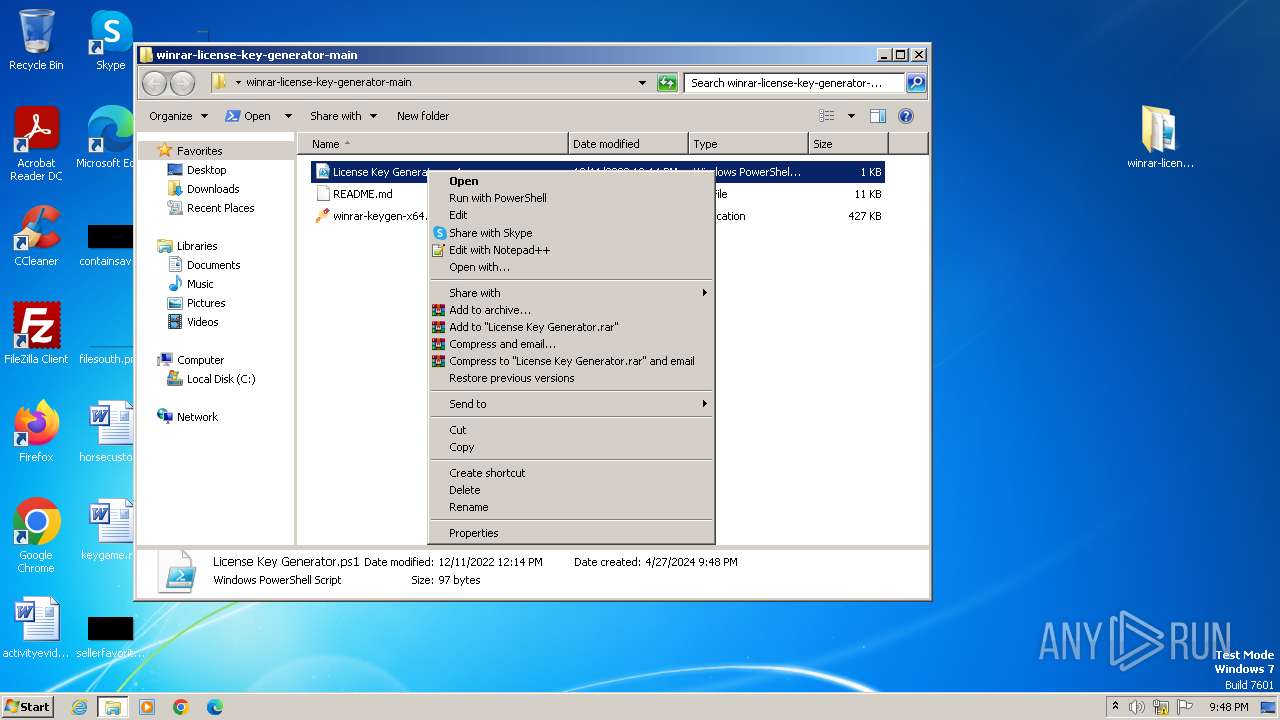
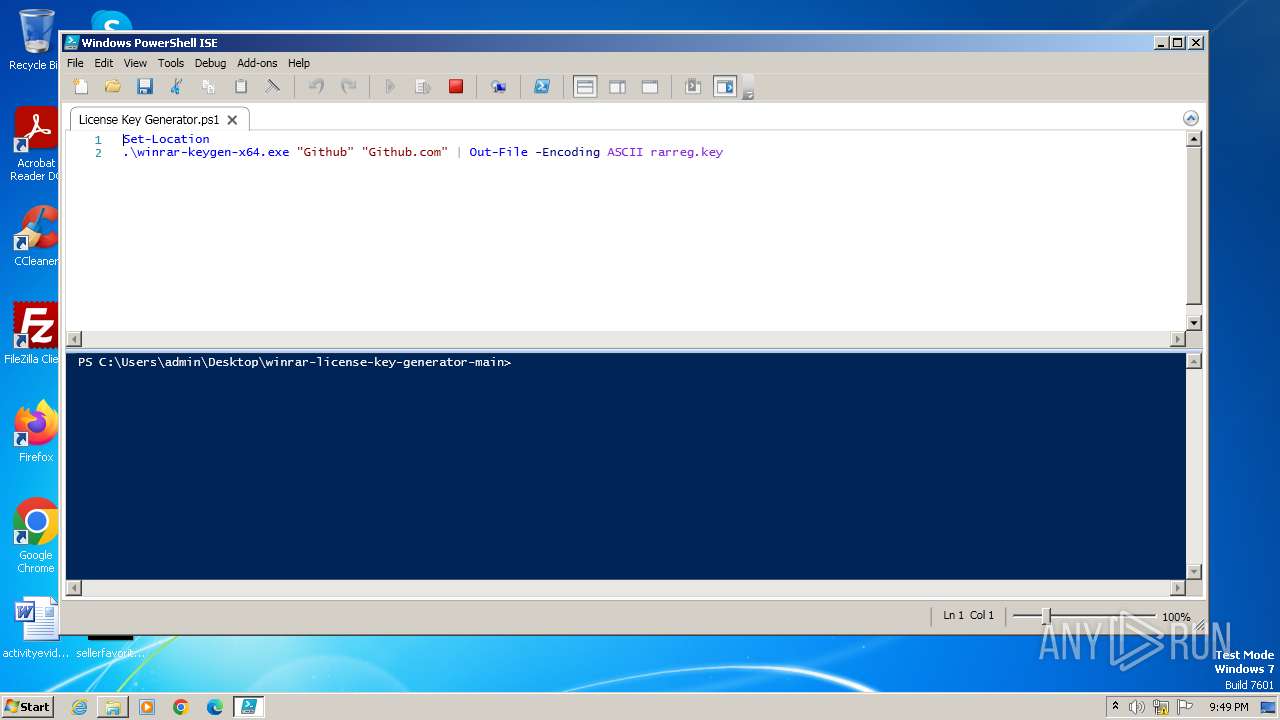
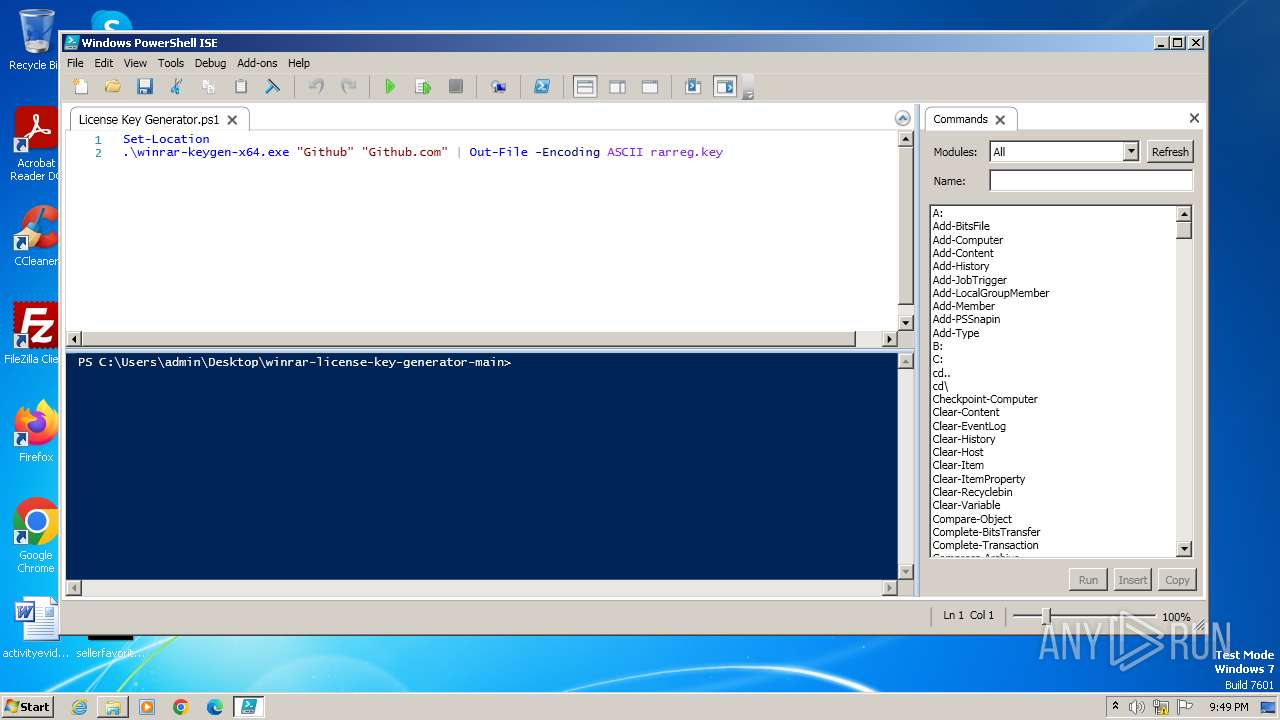
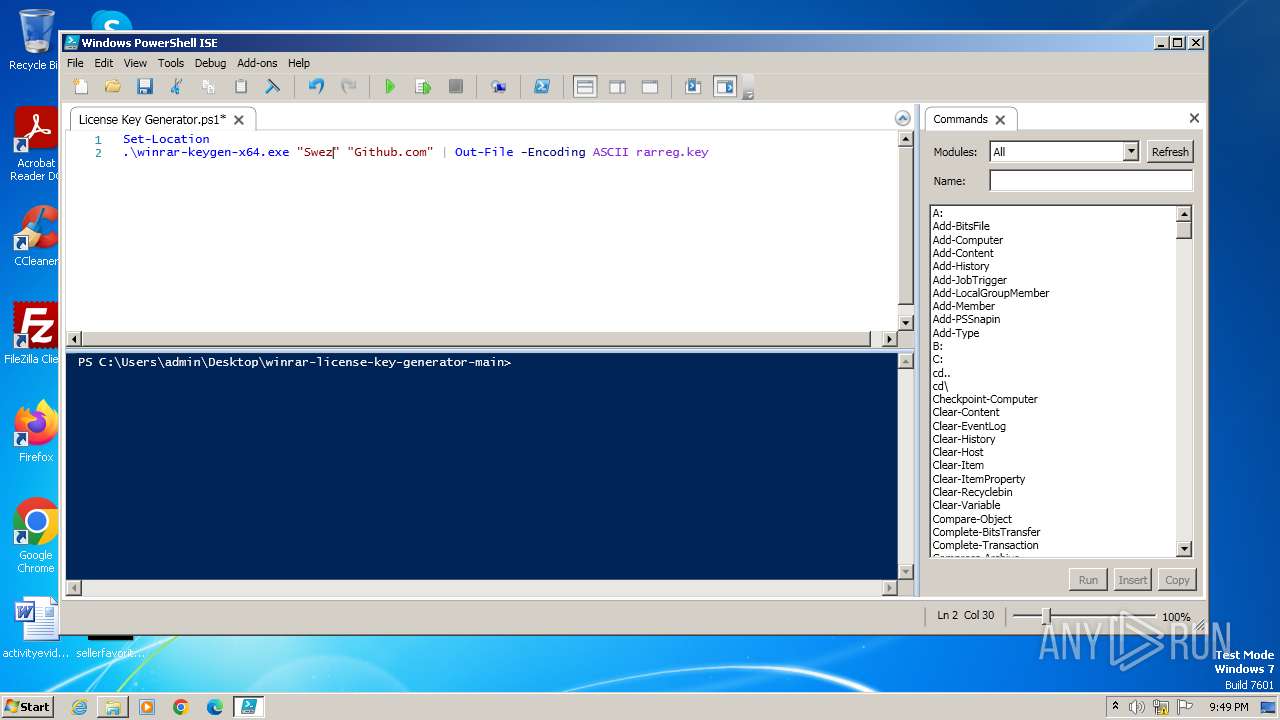
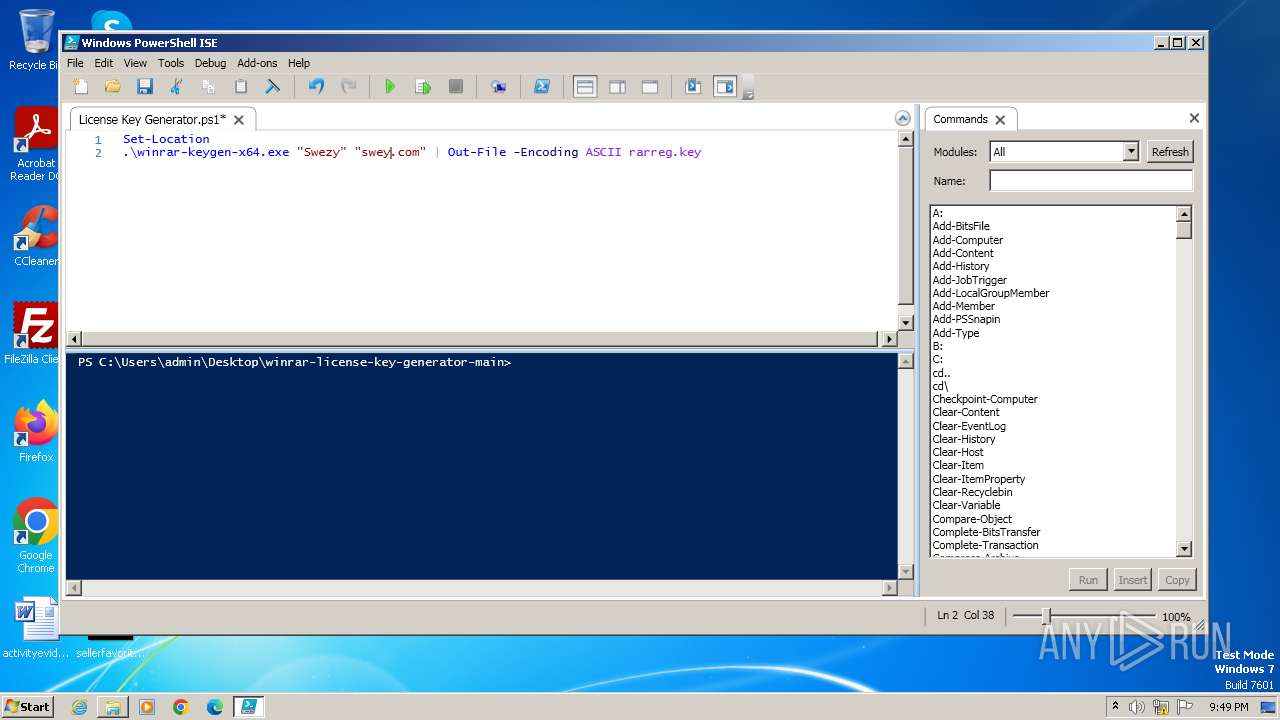
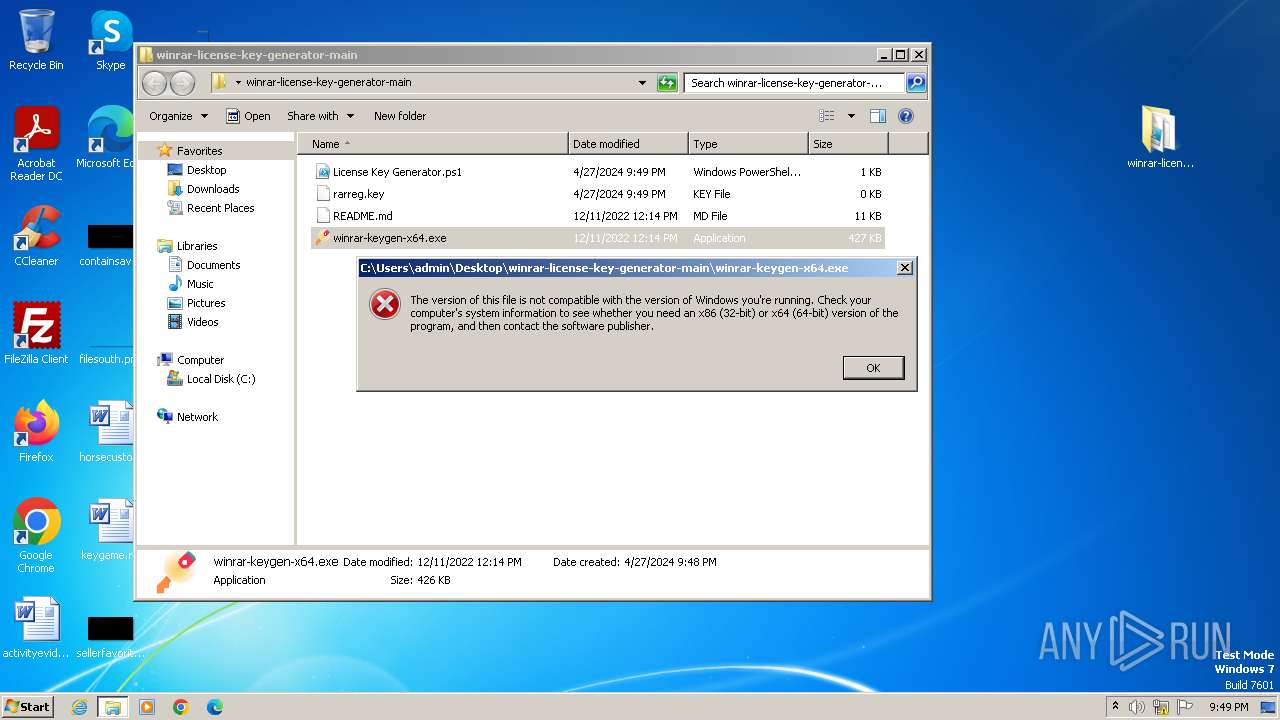
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
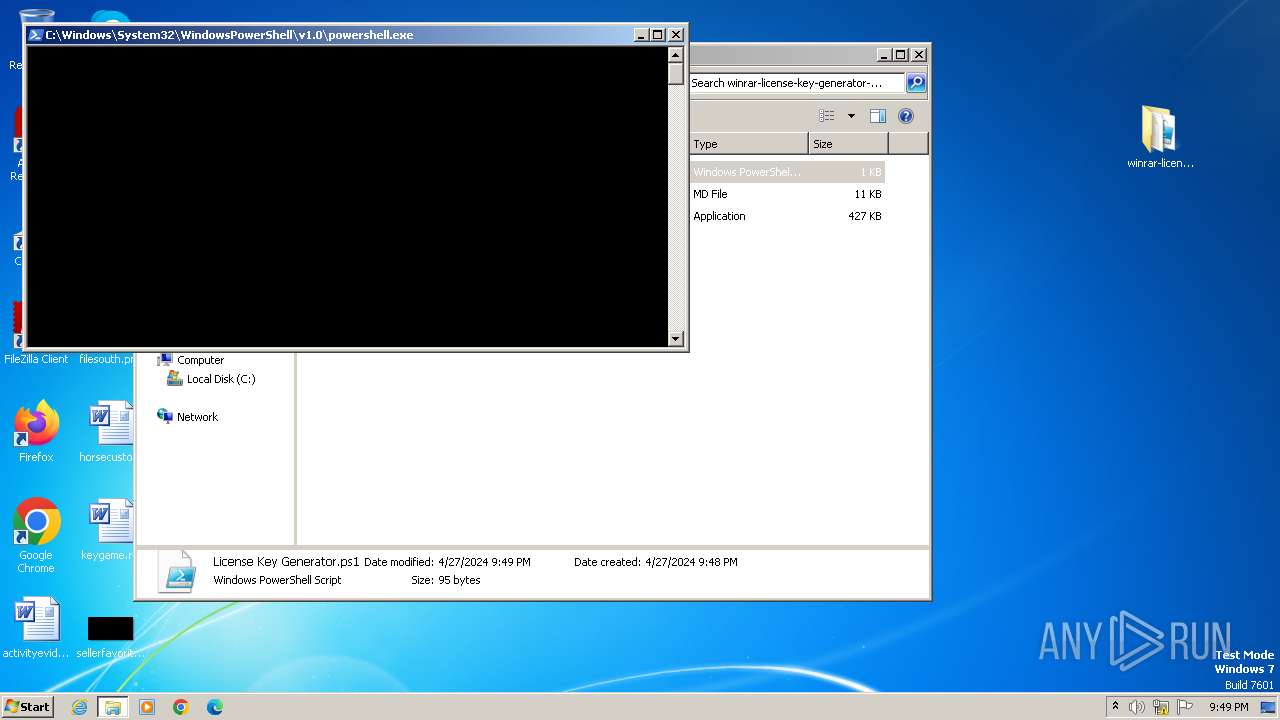
Bypass execution policy to execute commands
- powershell.exe (PID: 1856)
SUSPICIOUS
Reads the Internet Settings
- powershell_ise.exe (PID: 1020)
- powershell.exe (PID: 1856)
Reads settings of System Certificates
- powershell_ise.exe (PID: 1020)
INFO
Manual execution by a user
- powershell_ise.exe (PID: 1020)
- powershell.exe (PID: 1856)
- notepad++.exe (PID: 1932)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Creates files or folders in the user directory
- powershell_ise.exe (PID: 1020)
Create files in a temporary directory
- powershell_ise.exe (PID: 1020)
Reads the software policy settings
- powershell_ise.exe (PID: 1020)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 1020)
Checks current location (POWERSHELL)
- powershell_ise.exe (PID: 1020)
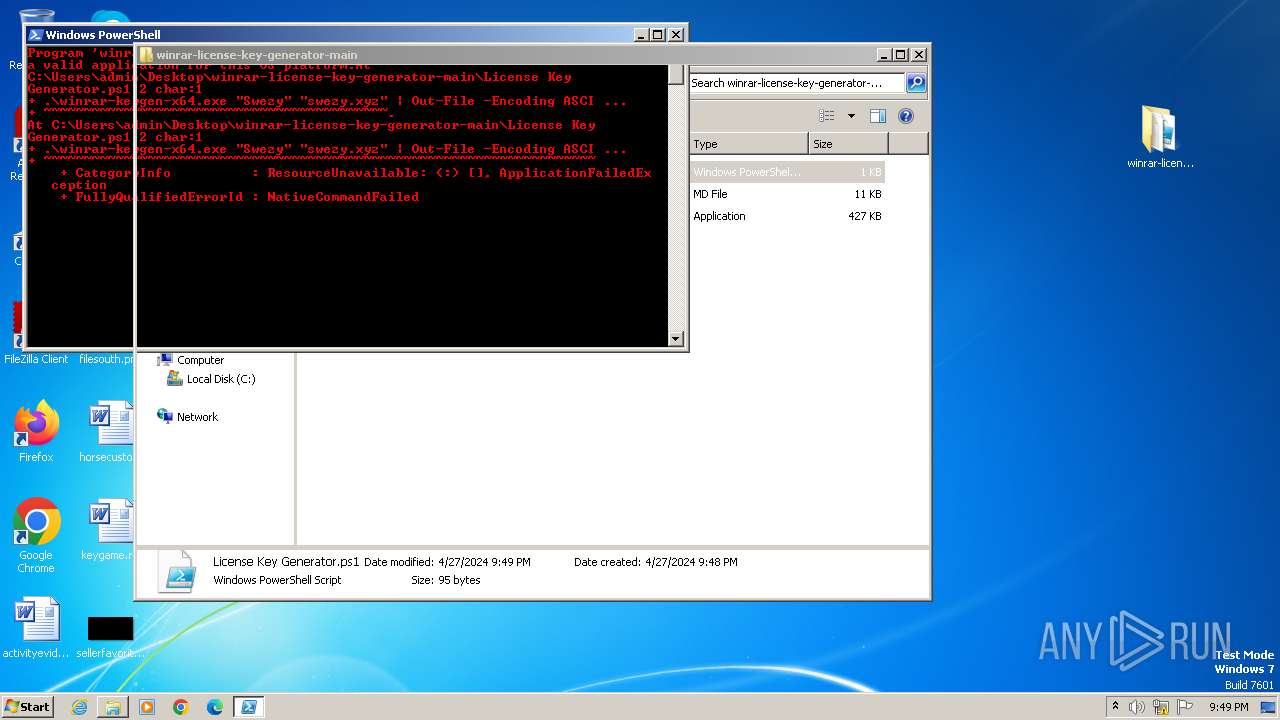
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:12:11 04:14:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | winrar-license-key-generator-main/ |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
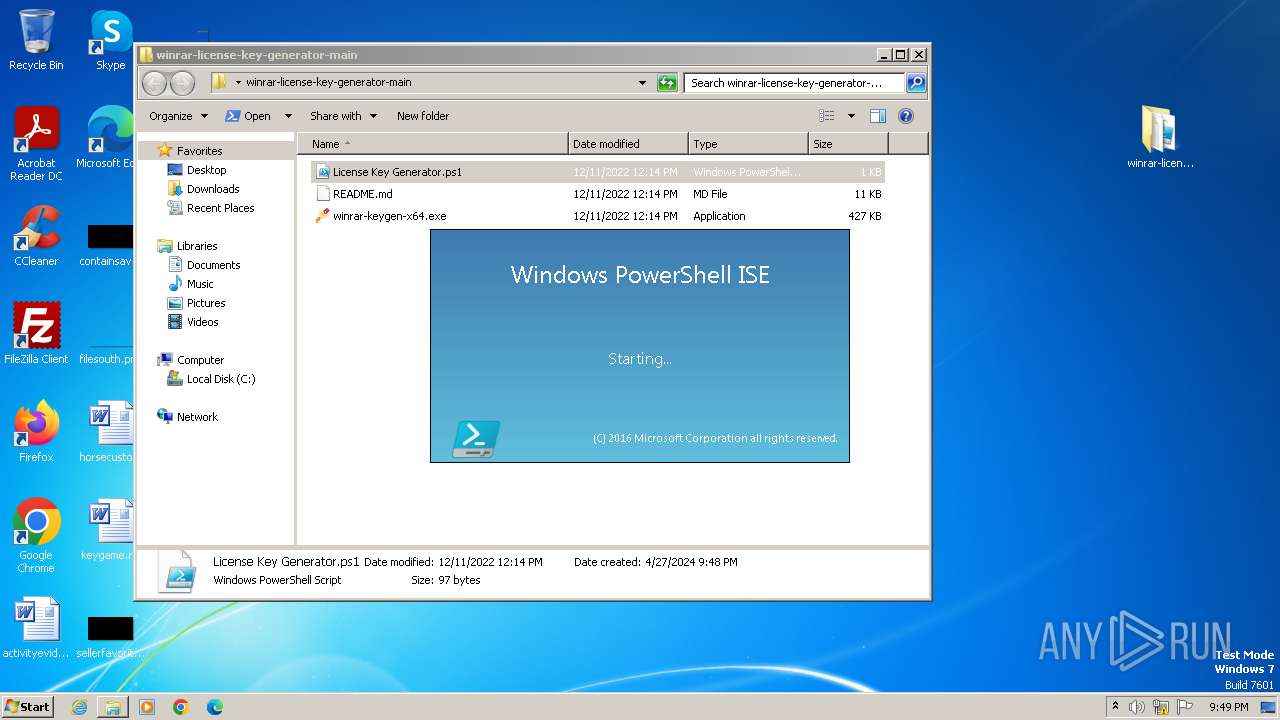
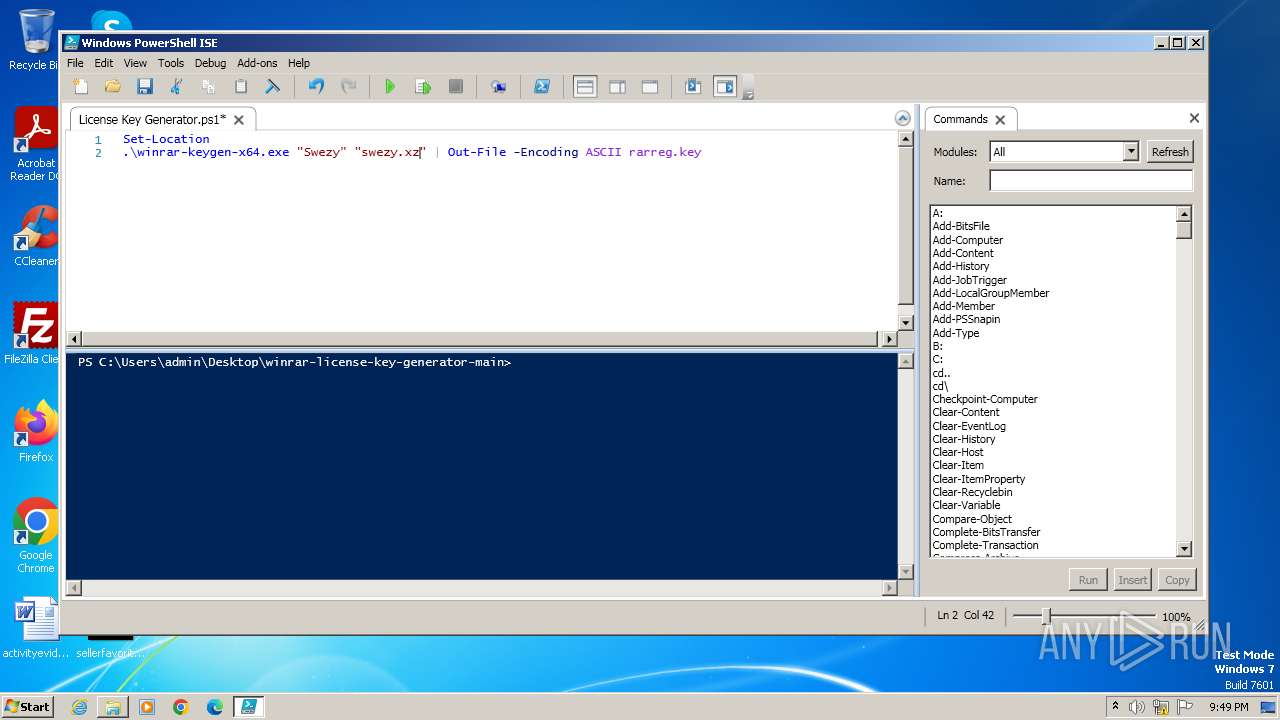
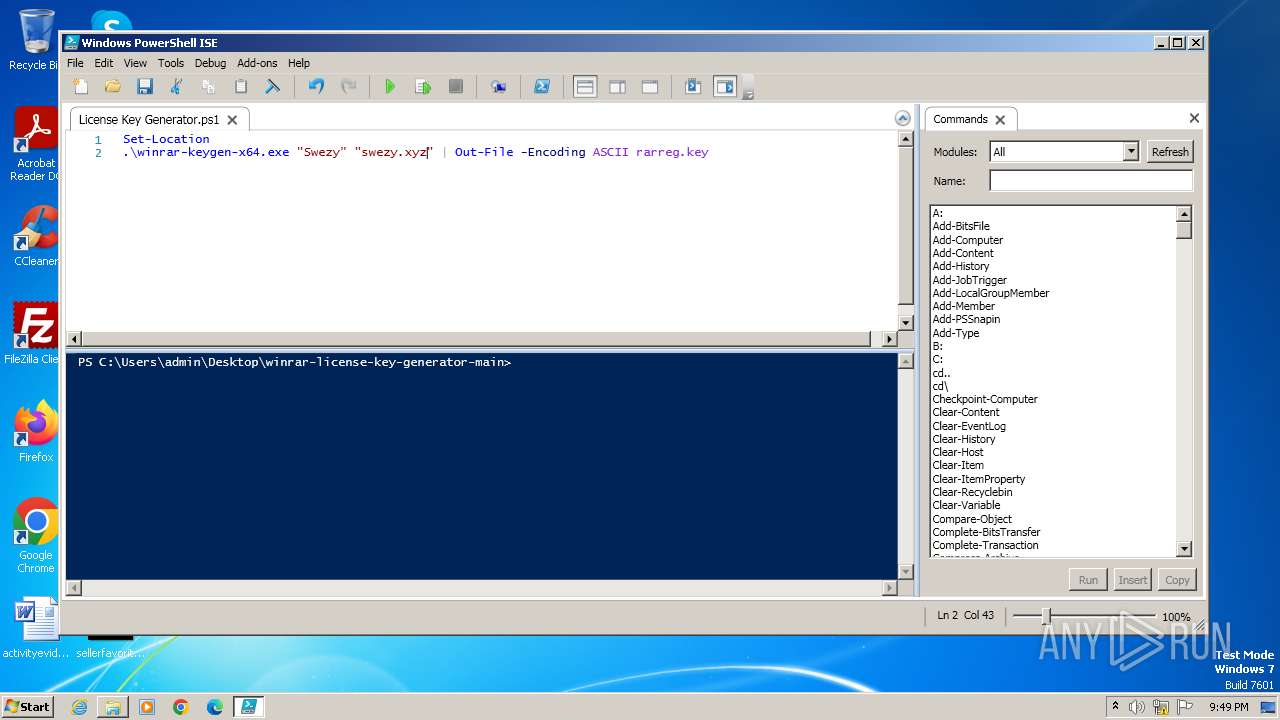
| 1020 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Users\admin\Desktop\winrar-license-key-generator-main\License Key Generator.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1856 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\winrar-license-key-generator-main\License Key Generator.ps1" "-Command" "if((Get-ExecutionPolicy ) -ne AllSigned) { Set-ExecutionPolicy -Scope Process Bypass }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
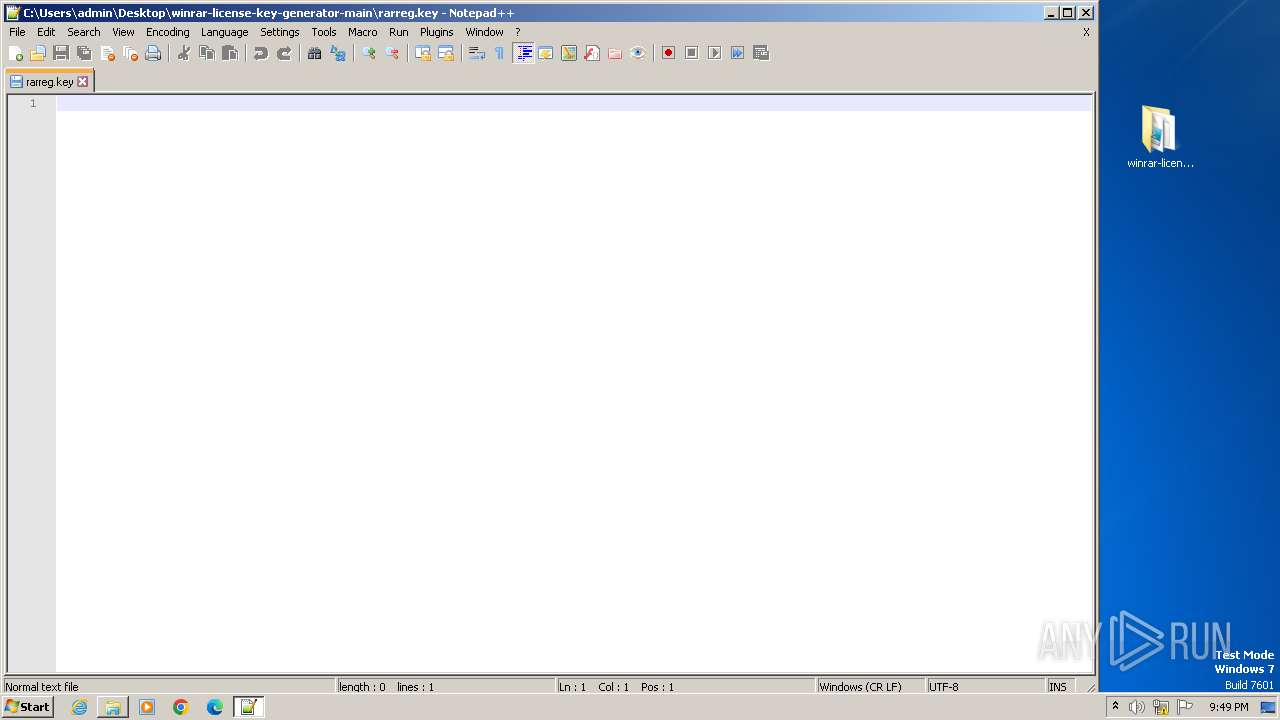
| 1932 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\winrar-license-key-generator-main\rarreg.key" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\winrar-license-key-generator-main.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
13 702
Read events
13 579
Write events
123
Delete events
0
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winrar-license-key-generator-main.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
4
Text files
6
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1020 | powershell_ise.exe | C:\Users\admin\AppData\Local\Microsoft_Corporation\powershell_ise.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\fjlvb3qg.newcfg | — | |
MD5:— | SHA256:— | |||
| 1020 | powershell_ise.exe | C:\Users\admin\AppData\Local\Temp\td5zkosh.ewd.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.24539\winrar-license-key-generator-main\README.md | html | |
MD5:59AFF9F7ECDD027A63BD7FB5A3B29A5E | SHA256:CD072B48A7BC4B2C2229F679515EE92099D8E1751490DECB2839A27C7093D887 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.24539\winrar-license-key-generator-main\License Key Generator.ps1 | text | |
MD5:4156FBCBDE42DDF803E0A21E352C4A72 | SHA256:39DC83E2B57F6EE88AF2A9BEEEF0777611A90D5CFAEDBA450A28F9E1ABB82FB4 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.24539\winrar-license-key-generator-main\winrar-keygen-x64.exe | executable | |
MD5:F98019E8C02240EB60A7B6274B7EB3DC | SHA256:0E4B425854D885A926BE699C28E002112409D571D06A88BB9E0B501AF0F6EBF9 | |||
| 1856 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bjzvpmun.ay0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IYPZZSZ4TJ5GDWTQV4OE.temp | binary | |
MD5:7B9FC8EDA8DFC3E128623081DB20030C | SHA256:81FB596D7C5C7C9264E891A660D7B00455DD9AC326B9B53816B1F2FE38F4FAED | |||
| 1020 | powershell_ise.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ISE\S-1-5-5-0-69873\PowerShellISEPipeName_0_b40380c0-c85a-4bcf-ad10-42e0007dce42 | text | |
MD5:A5EA0AD9260B1550A14CC58D2C39B03D | SHA256:F1B2F662800122BED0FF255693DF89C4487FBDCF453D3524A42D4EC20C3D9C04 | |||
| 1020 | powershell_ise.exe | C:\Users\admin\AppData\Local\Microsoft_Corporation\powershell_ise.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\user.config | xml | |
MD5:BA25F5812BABB2652BAAF71A84412454 | SHA256:9AAA220EE4D99E78D0248650E22CA42D078D406C8CF28A58865D13F5E8EF5645 | |||
| 1856 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|