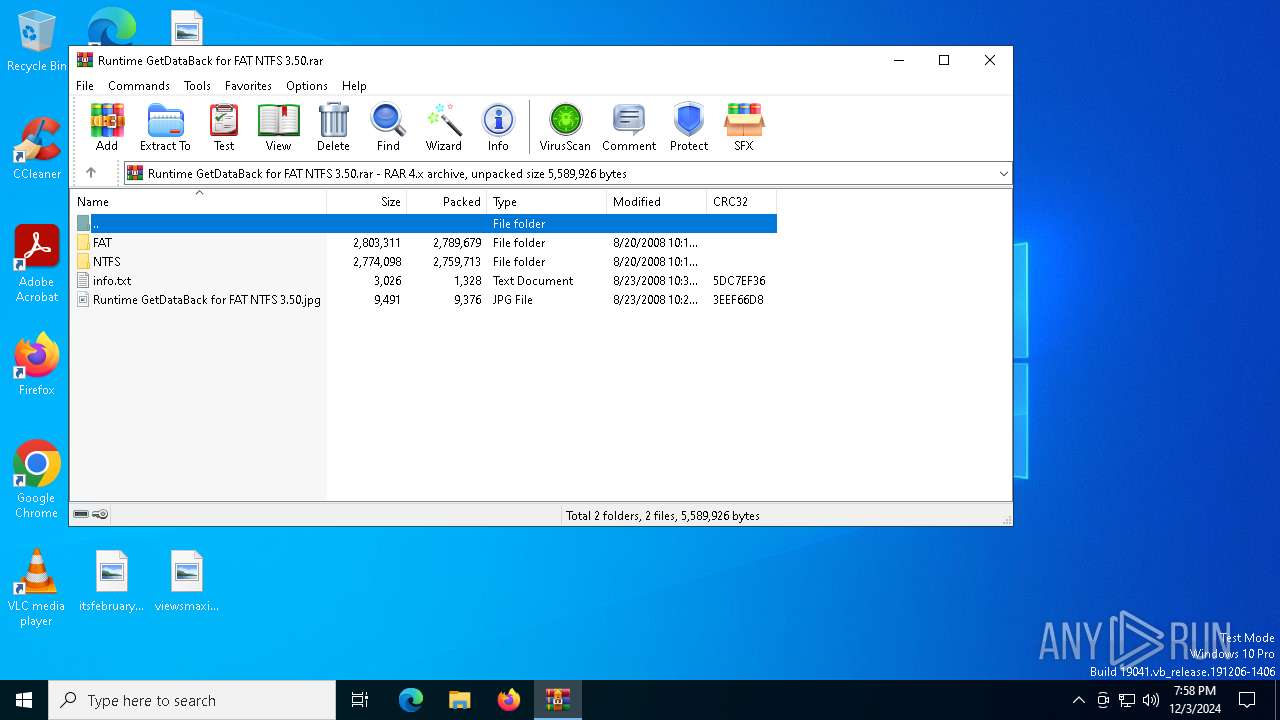
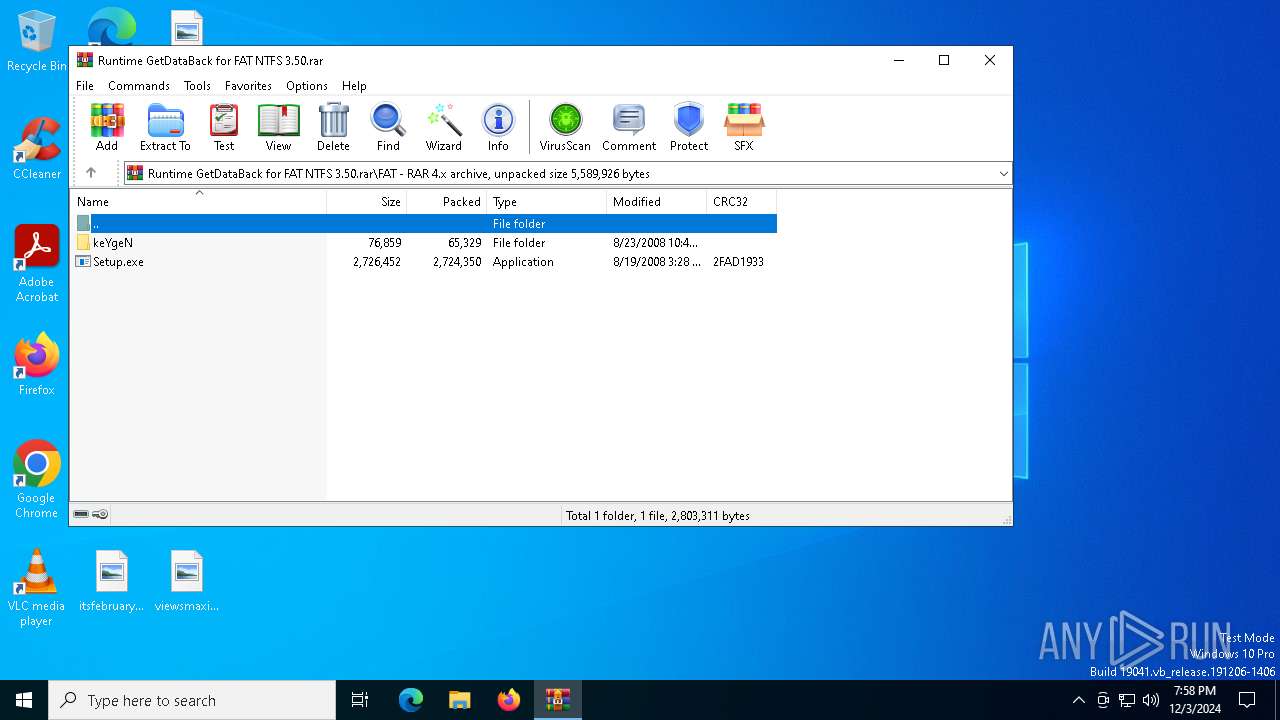
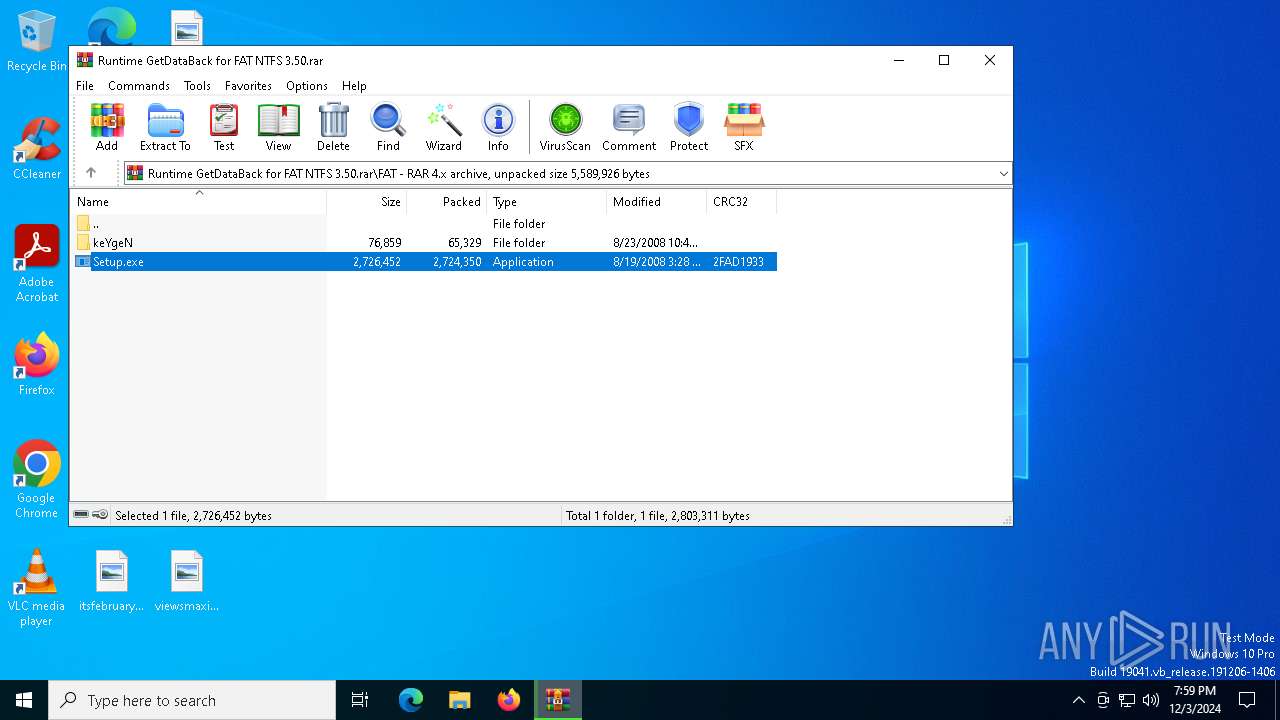
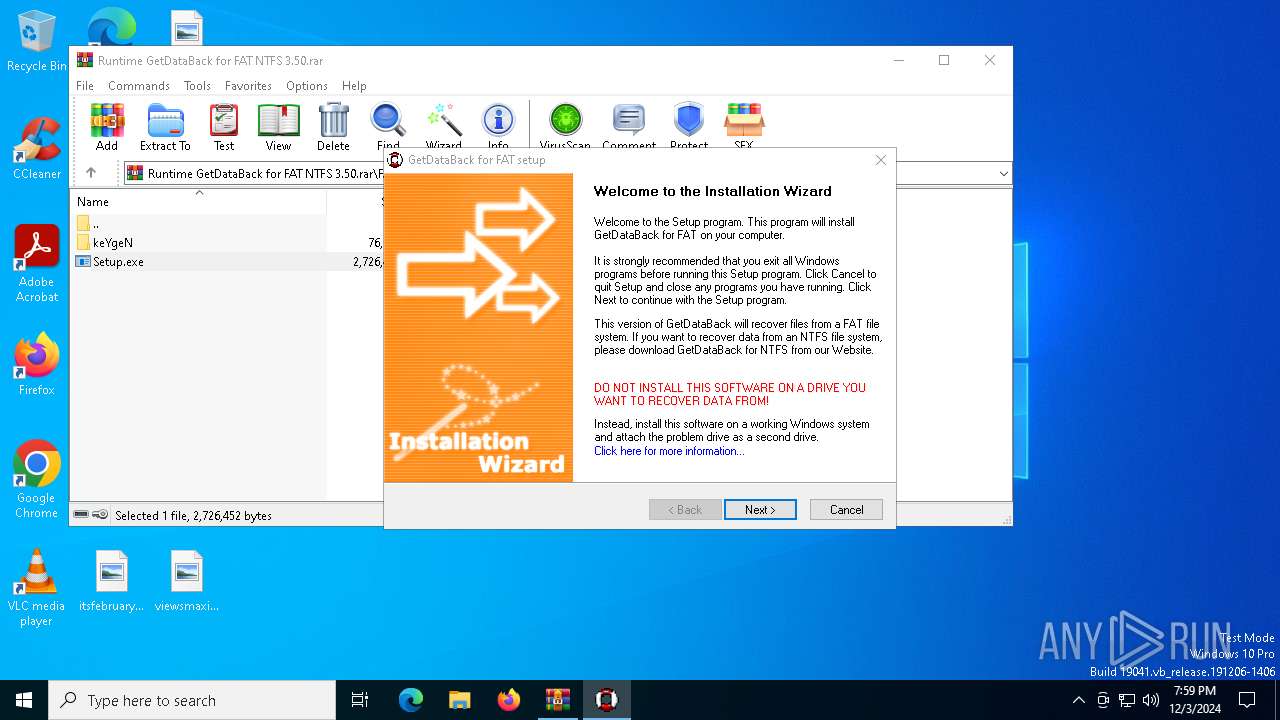
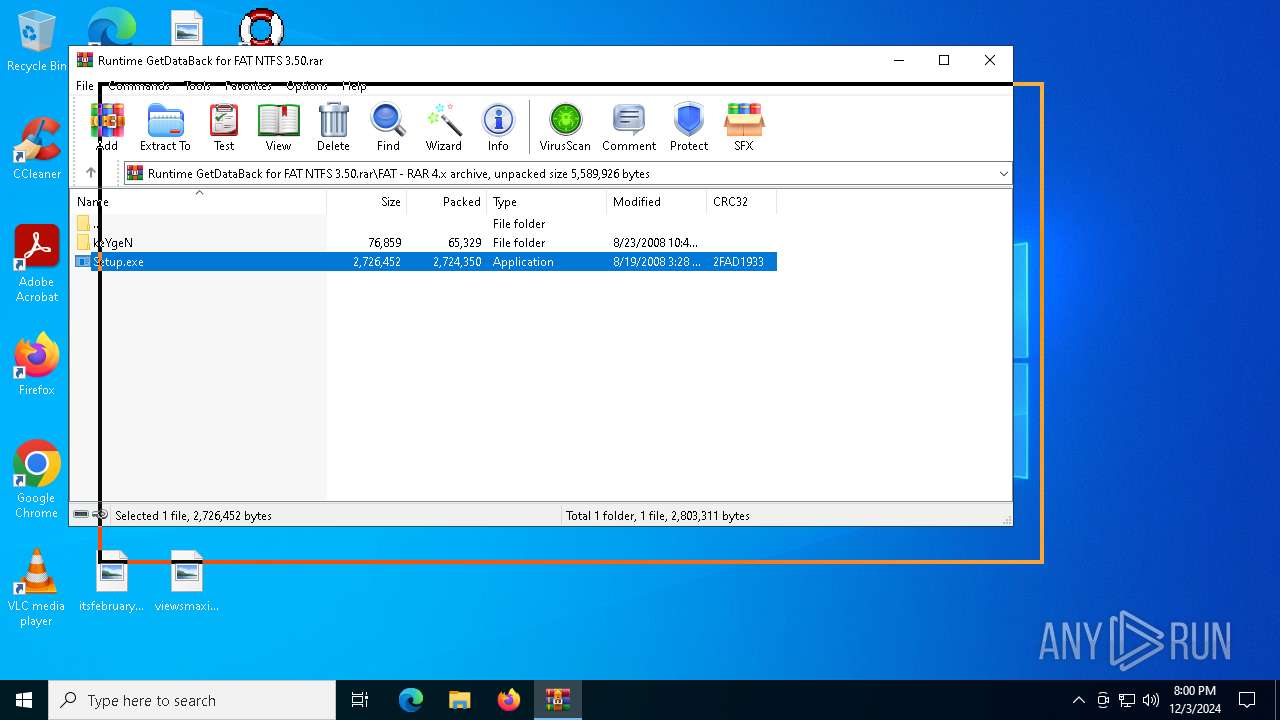
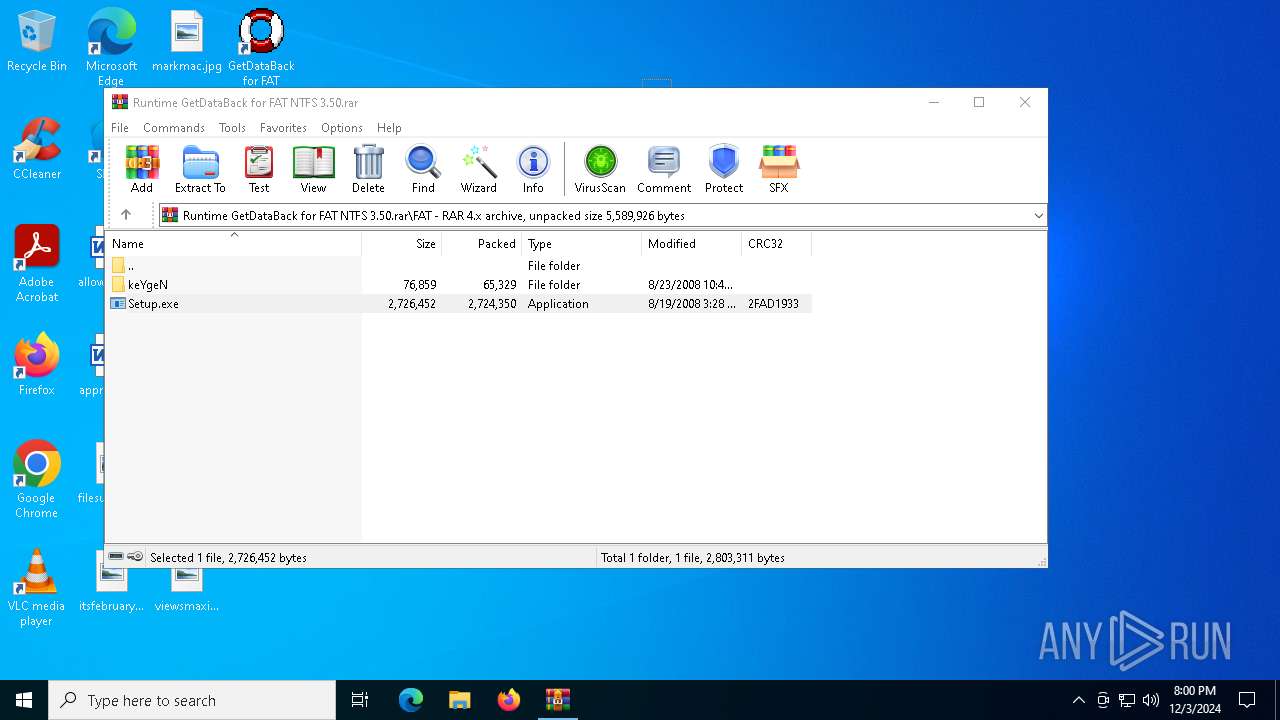
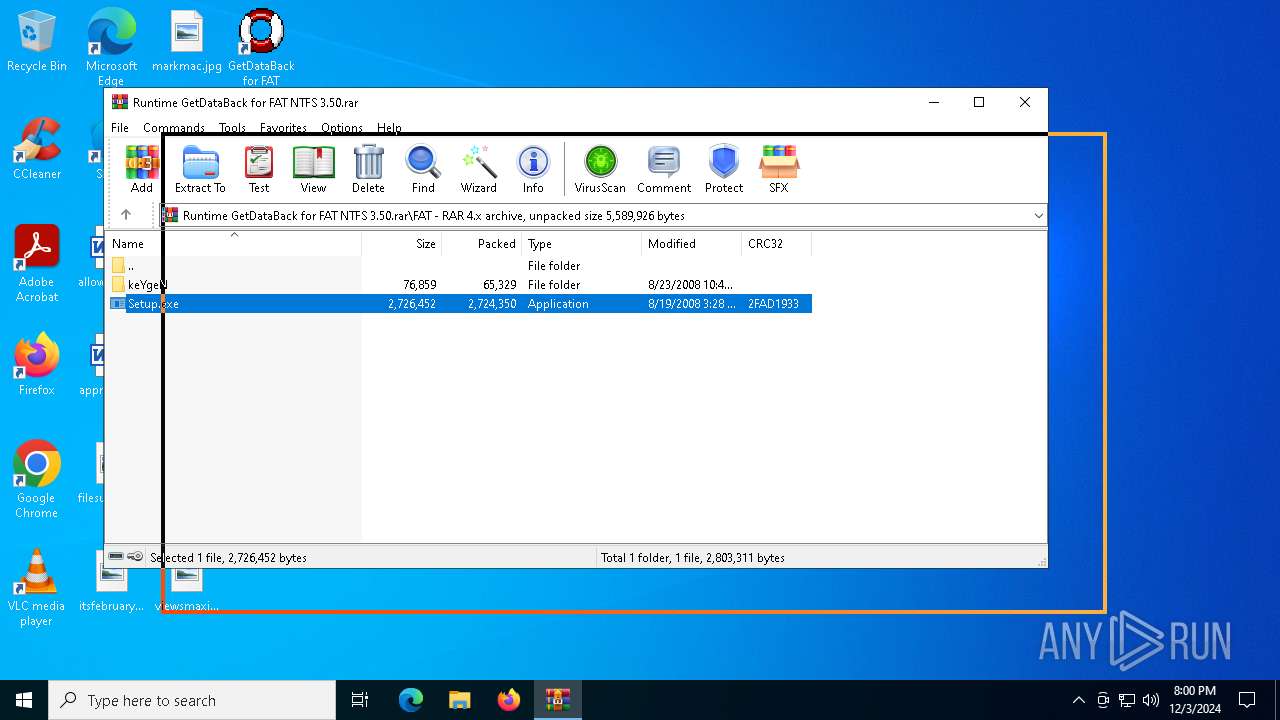
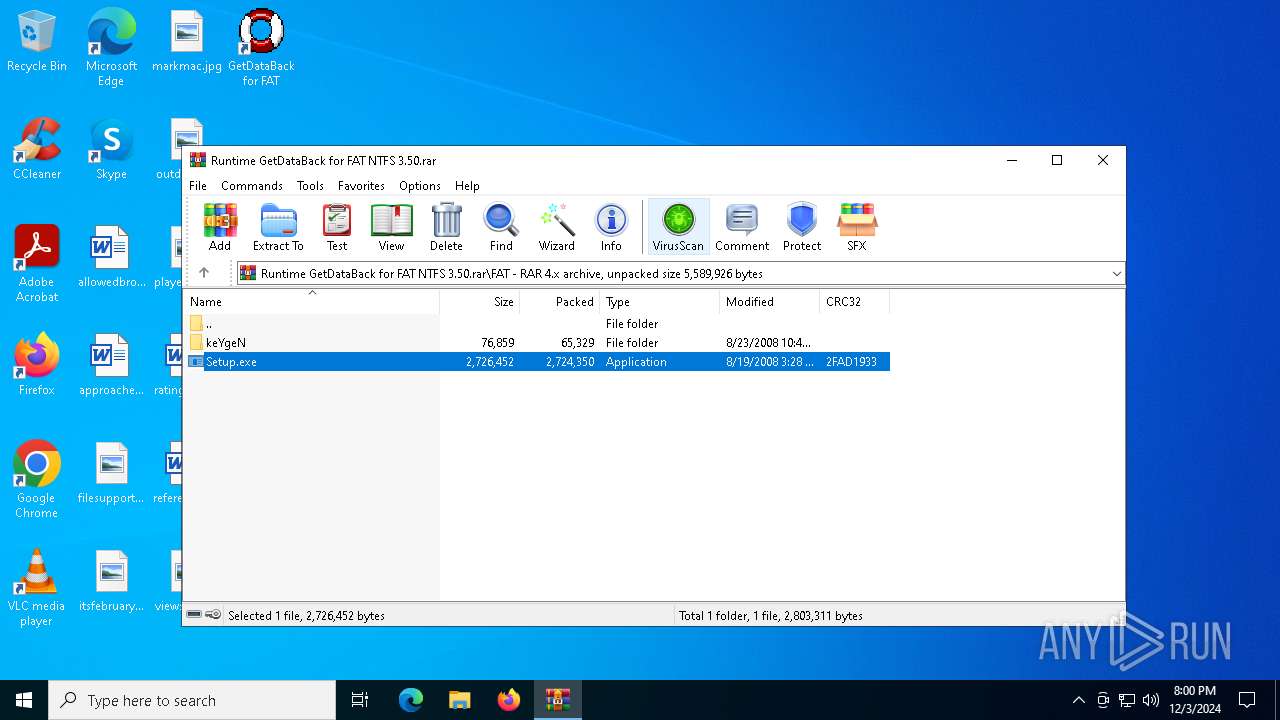
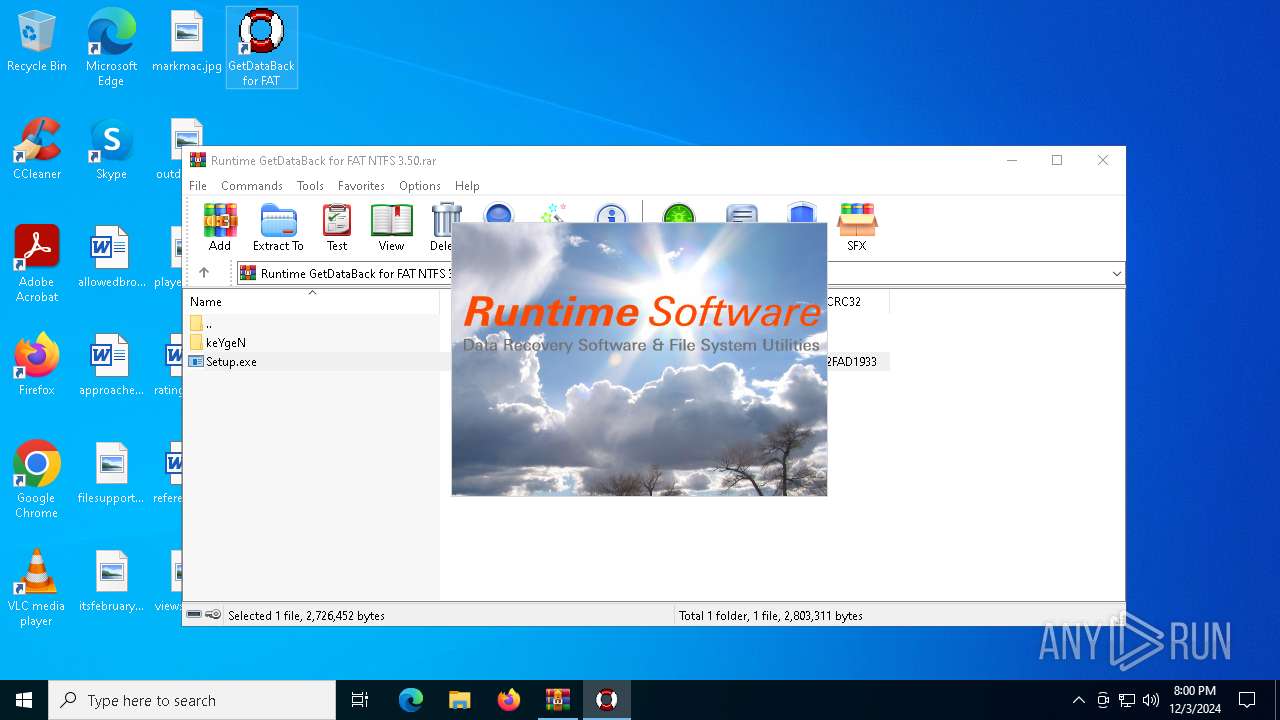
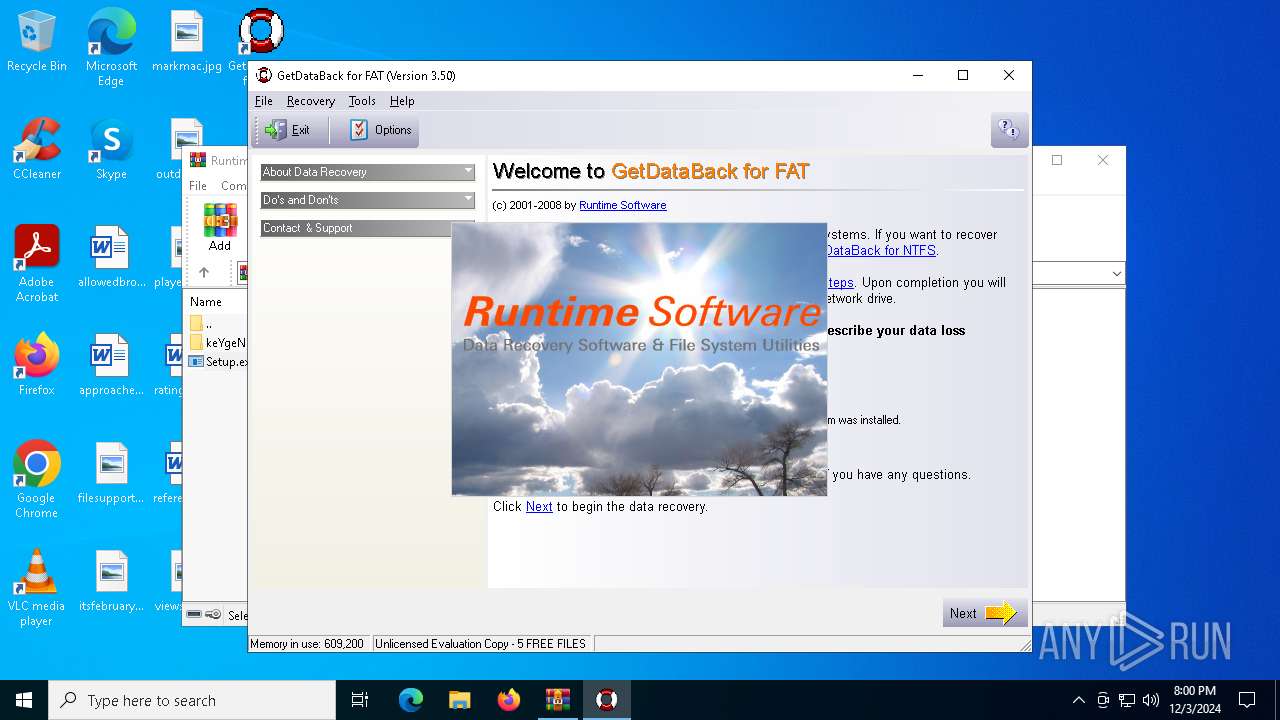
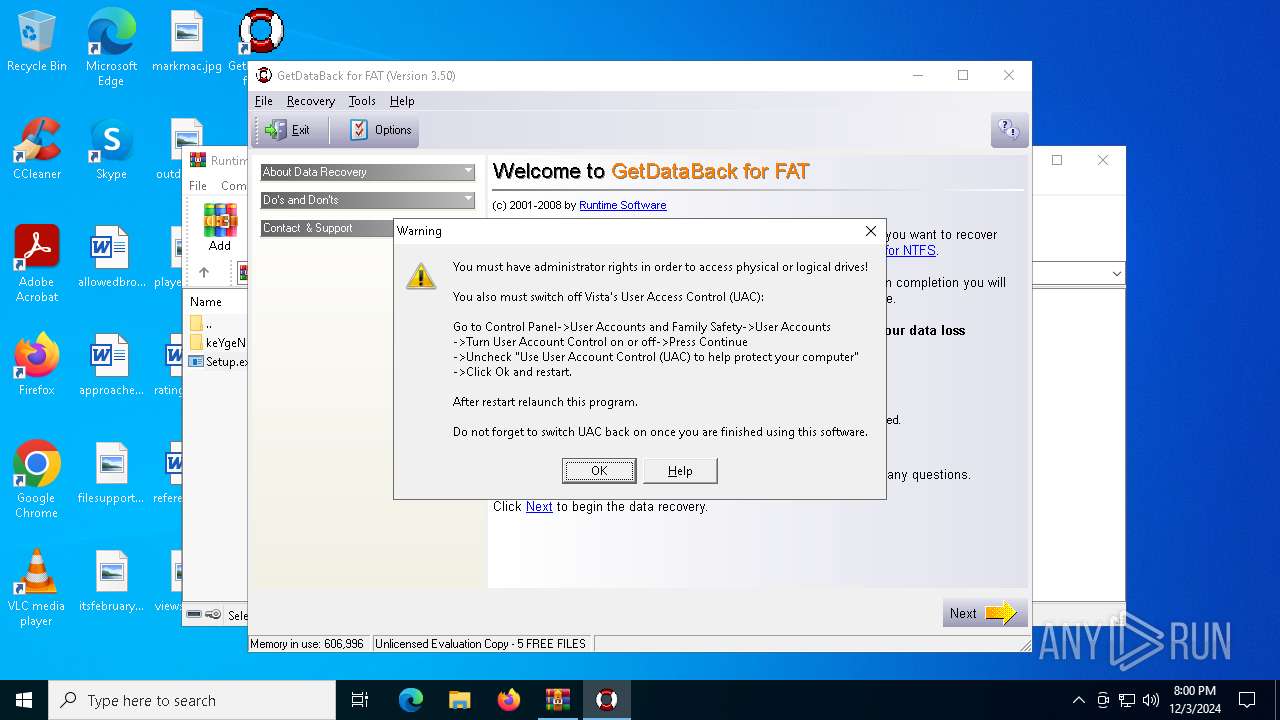
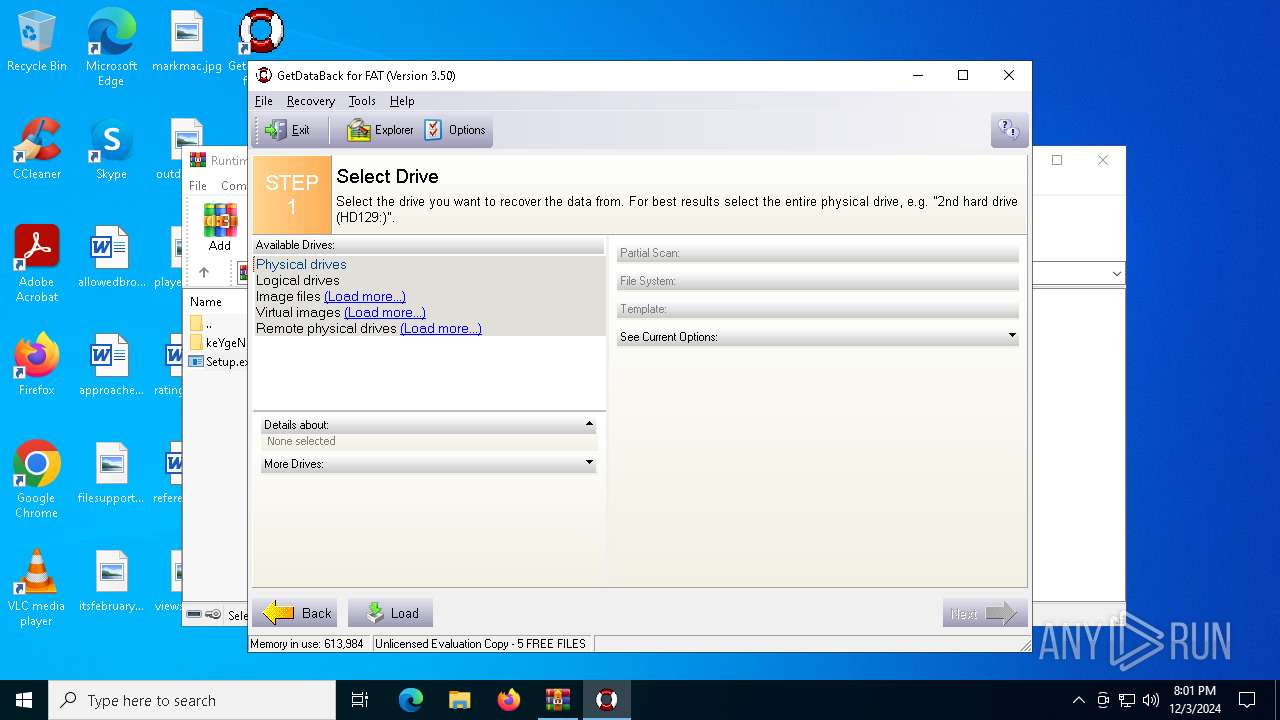
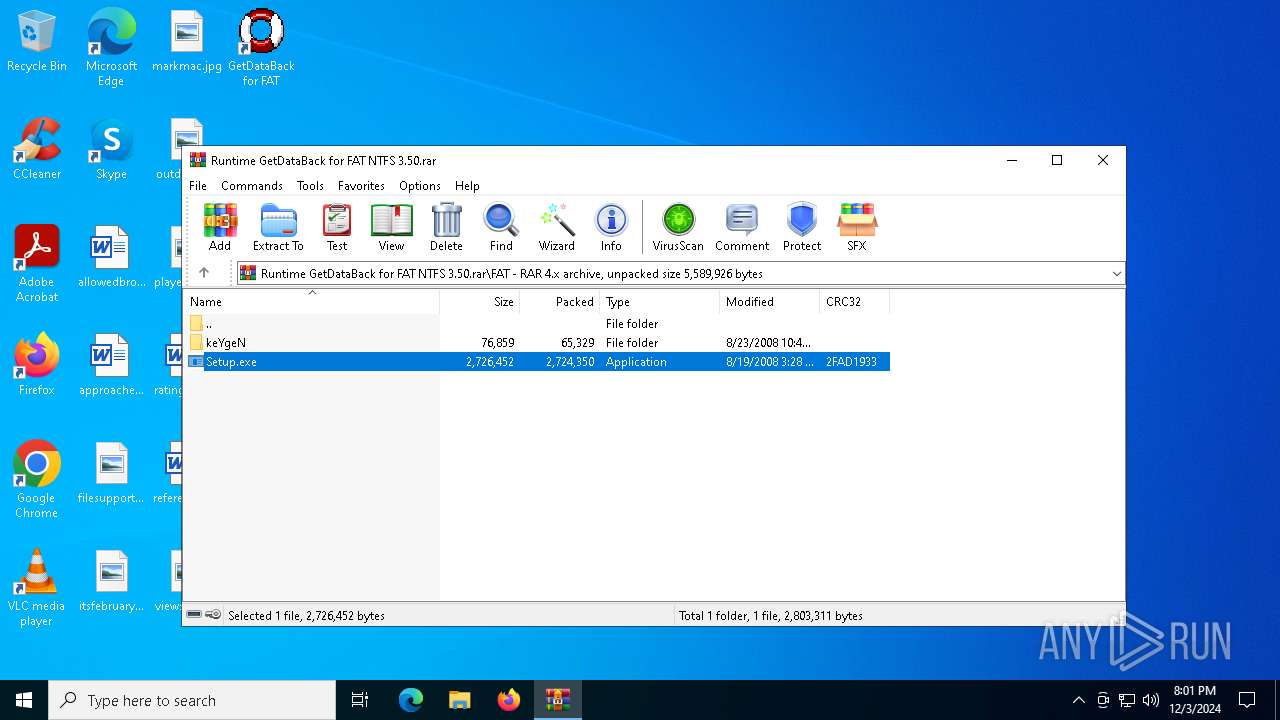
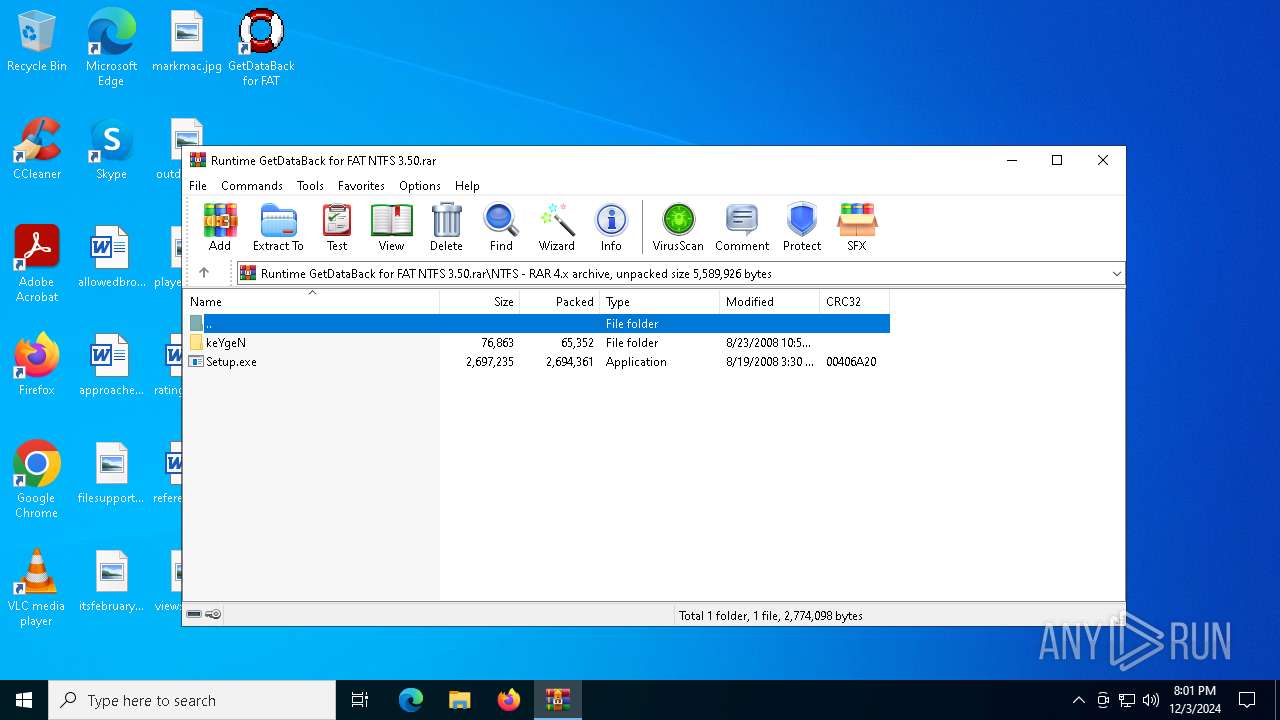
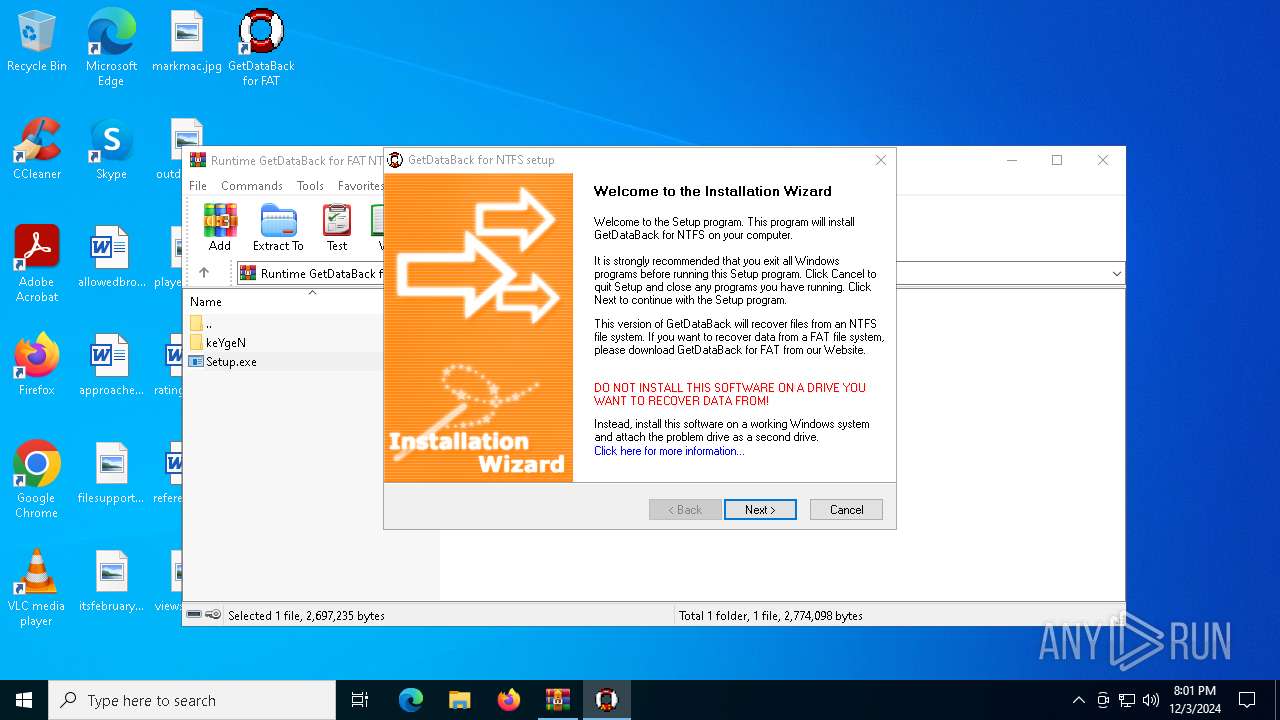
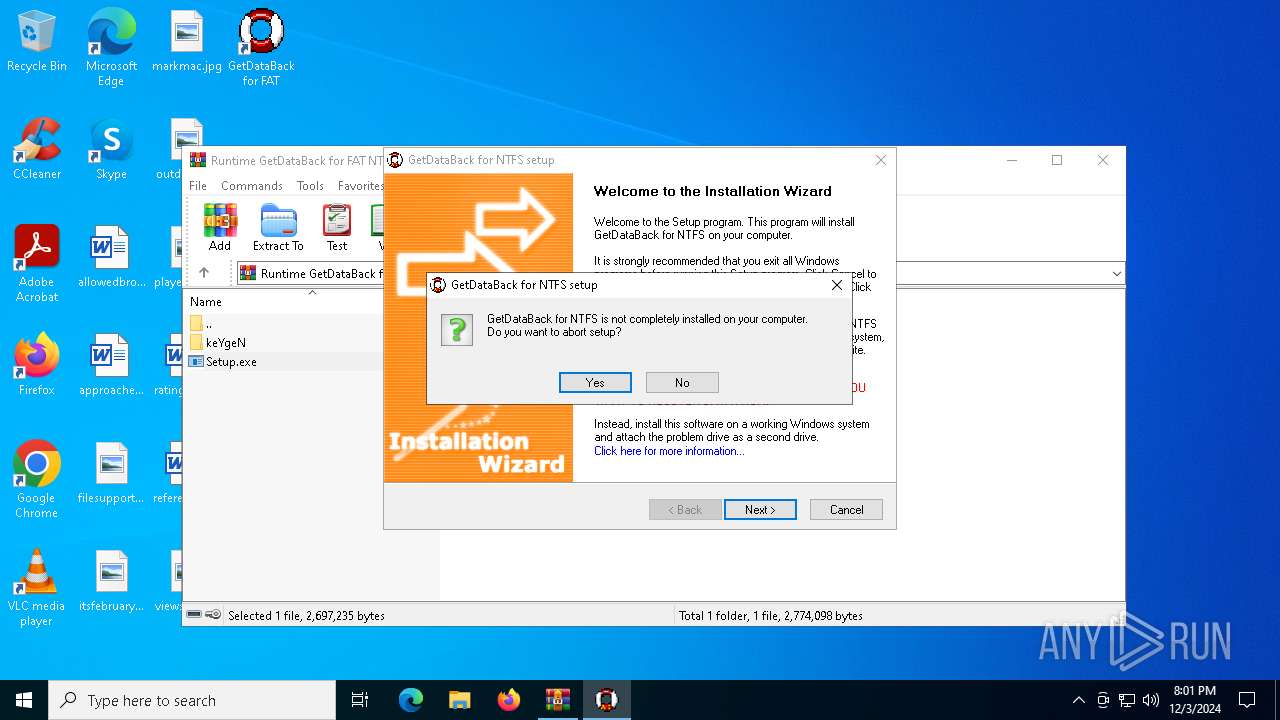
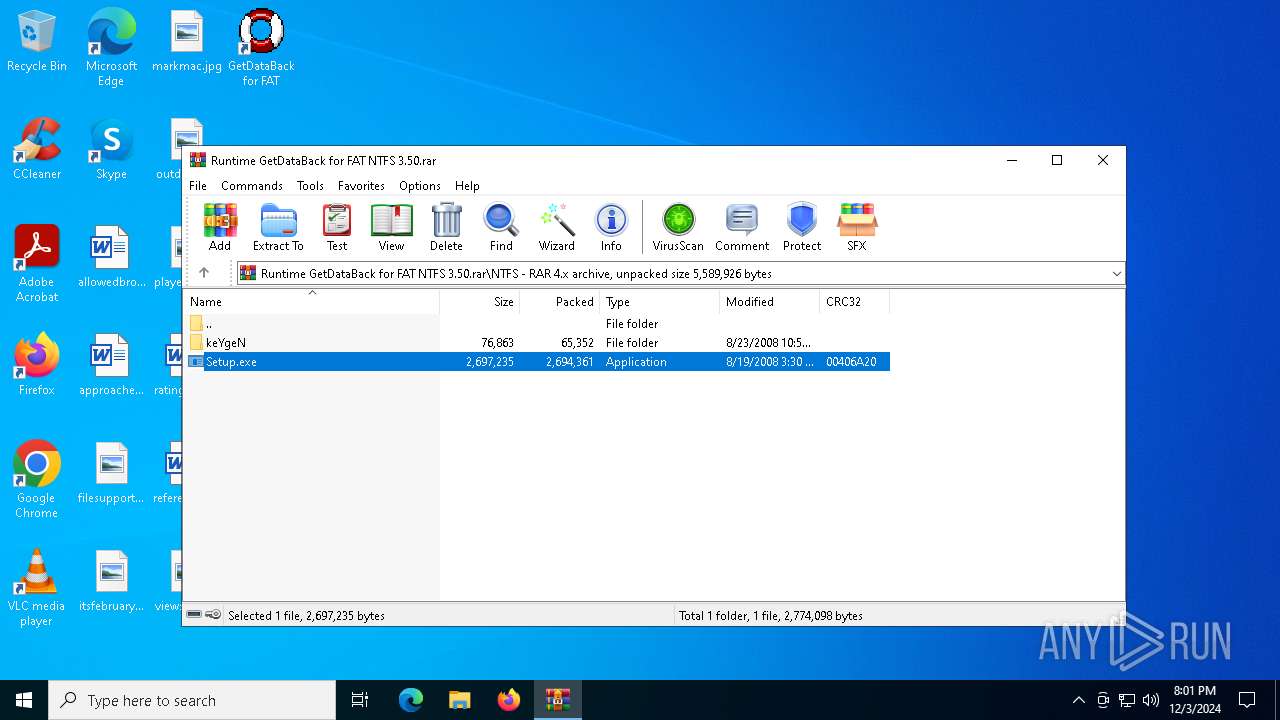
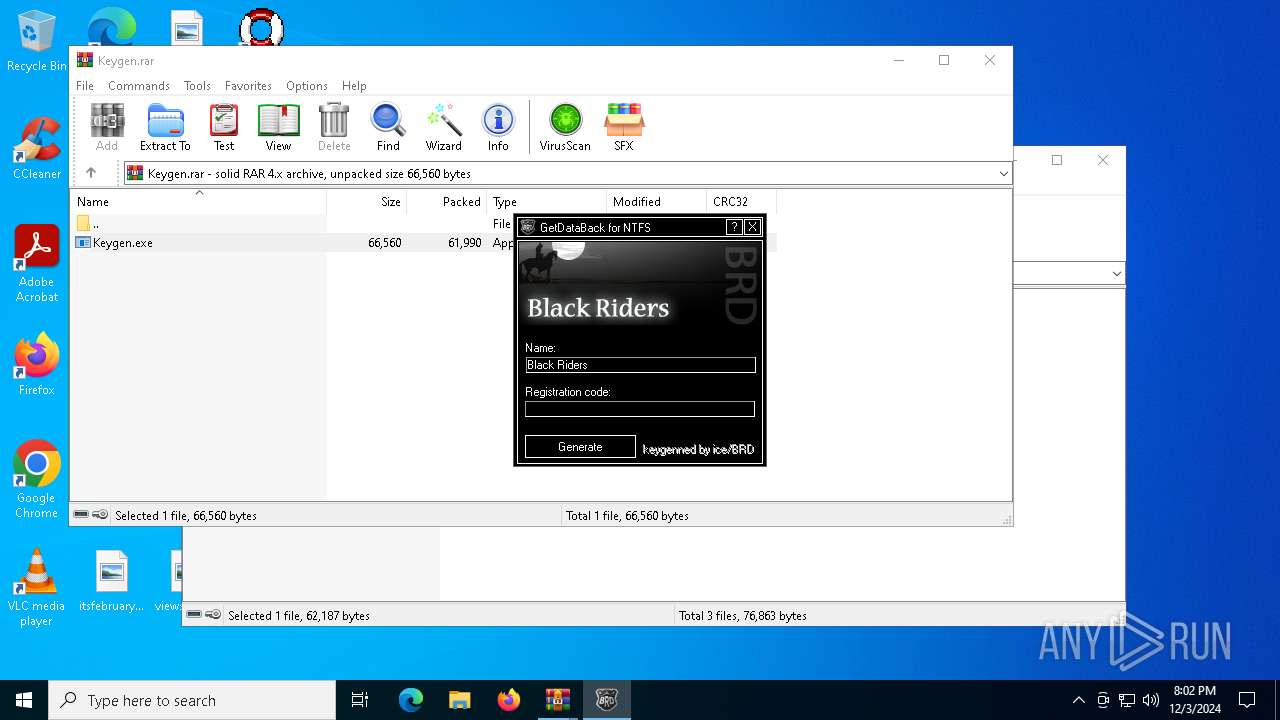
| File name: | Runtime GetDataBack for FAT NTFS 3.50.rar |
| Full analysis: | https://app.any.run/tasks/f0b92042-2c65-4588-89ec-28de8049f036 |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2024, 19:58:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: RecoveryRecordPresent |
| MD5: | 94967FF1FFDF4B77370A84BDCB84D414 |
| SHA1: | 2624587B746F412F2F8EE3DCA698FF2D94A51CD0 |
| SHA256: | ED1FB5075B84AD08E4820E94924CA1BEC0B56D510DC0EBC1BCD6371CB775879E |
| SSDEEP: | 98304:teJ70/bd74yc+Rqz3Mk/kGM36yRmnTZkEtA2XbiA65kbE7UaO48/deTUYHWvQsOX:m3059bl5TcOUFM |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6404)
SUSPICIOUS
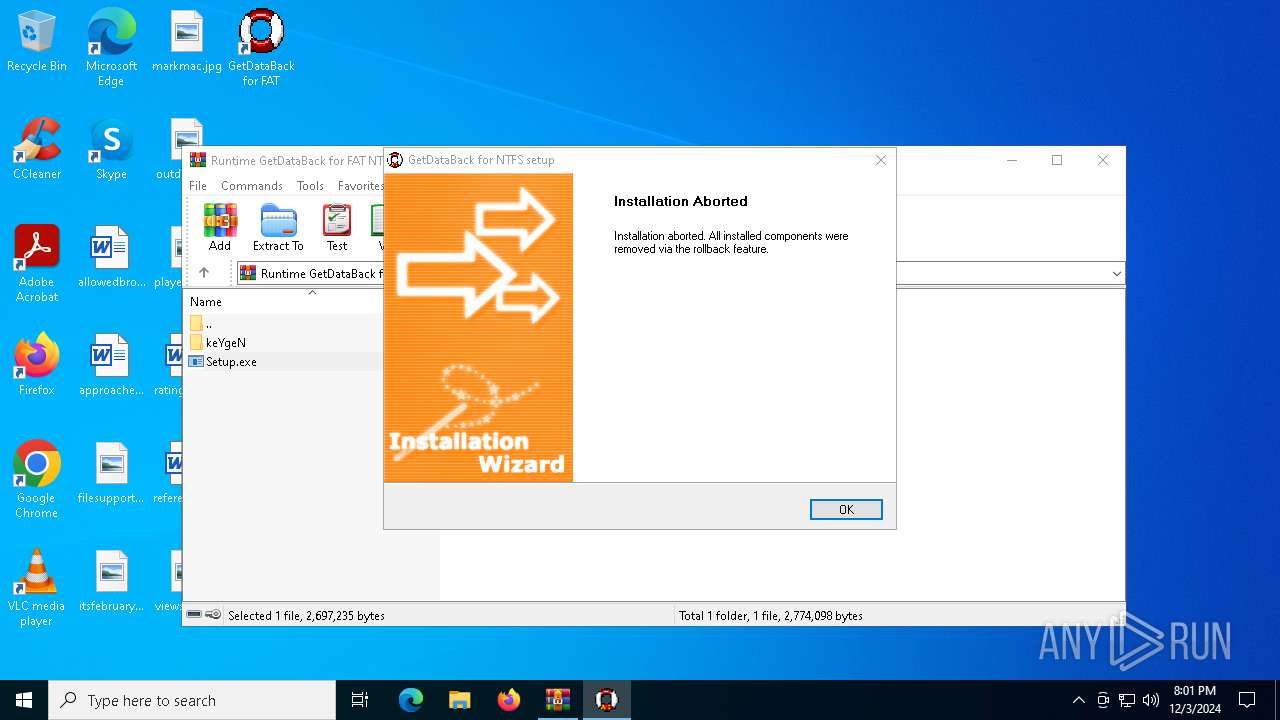
Executable content was dropped or overwritten
- Setup.exe (PID: 6316)
- Setup.exe (PID: 7056)
Application launched itself
- WinRAR.exe (PID: 6404)
There is functionality for communication over UDP network (YARA)
- gdb.exe (PID: 5032)
INFO
UPX packer has been detected
- Keygen.exe (PID: 6168)
- Setup.exe (PID: 7056)
- Setup.exe (PID: 6316)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6016)
- WinRAR.exe (PID: 6404)
Manual execution by a user
- gdb.exe (PID: 5032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 2824 |
| UncompressedSize: | 14207 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2008:07:29 20:28:58 |
| PackingMethod: | Normal |
| ArchivedFileName: | FAT\keYgeN\brd.nfo |
Total processes
144
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
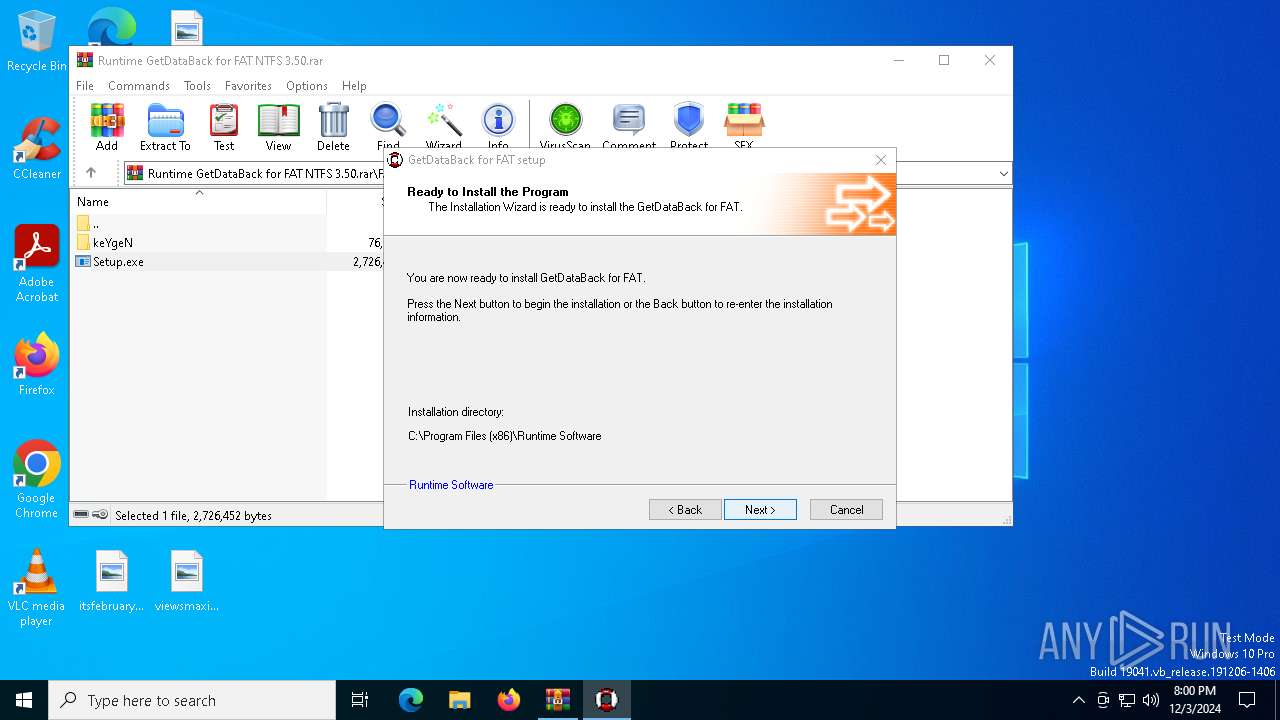
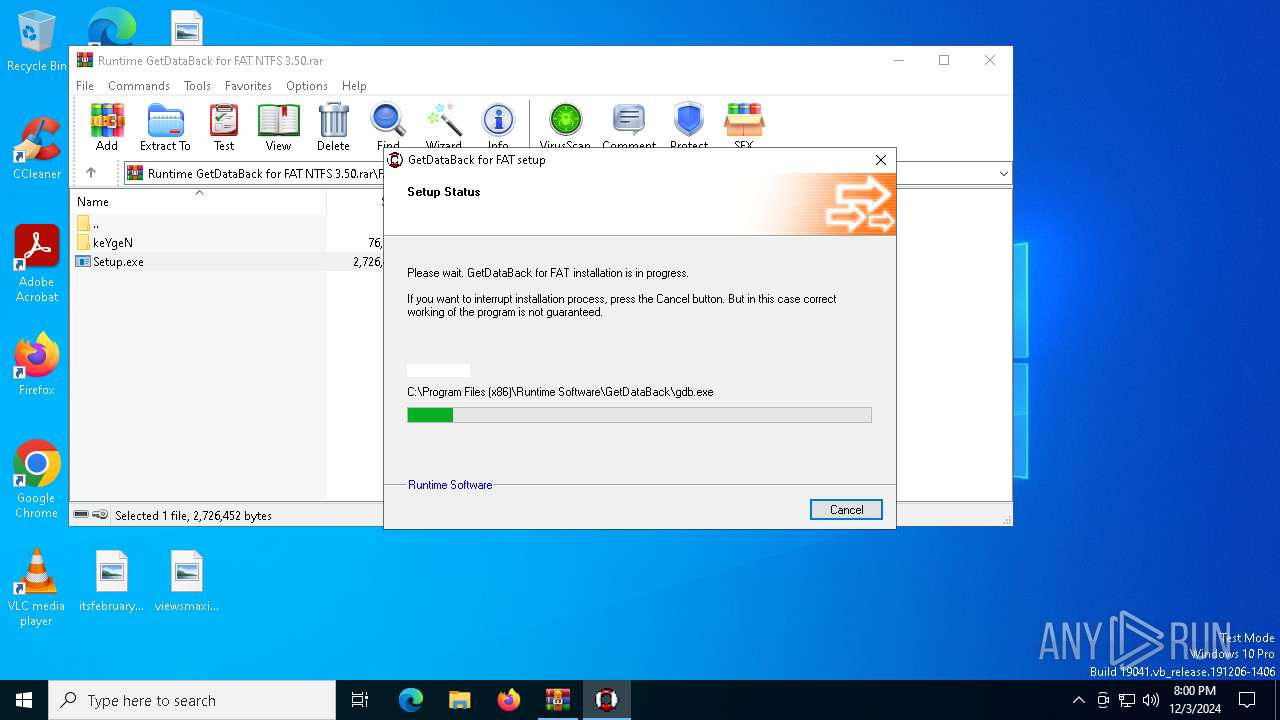
| 5032 | "C:\Program Files (x86)\Runtime Software\GetDataBack\gdb.exe" | C:\Program Files (x86)\Runtime Software\GetDataBack\gdb.exe | explorer.exe | ||||||||||||
User: admin Company: Runtime Software Integrity Level: MEDIUM Description: GetDataBack for FAT Data Recovery Exit code: 0 Version: 3.5.0.0 Modules
| |||||||||||||||
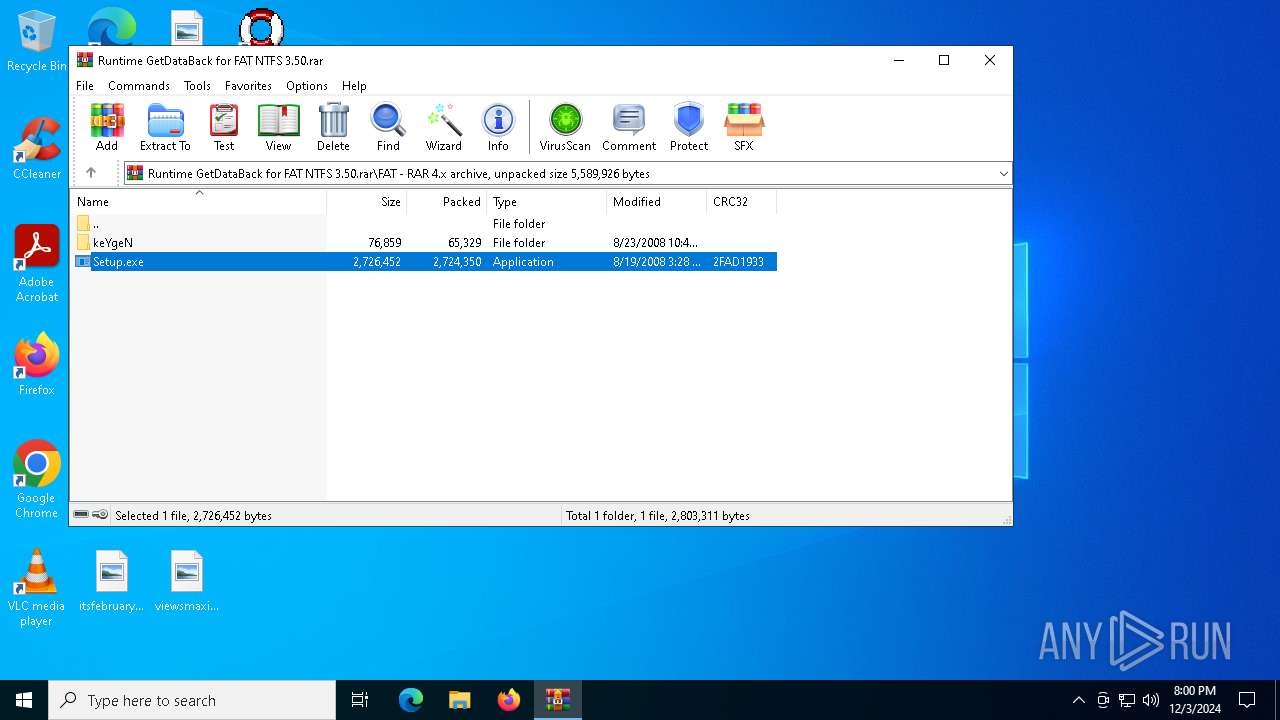
| 6016 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa6404.42070\Keygen.rar | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6168 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6016.45046\Keygen.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6016.45046\Keygen.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
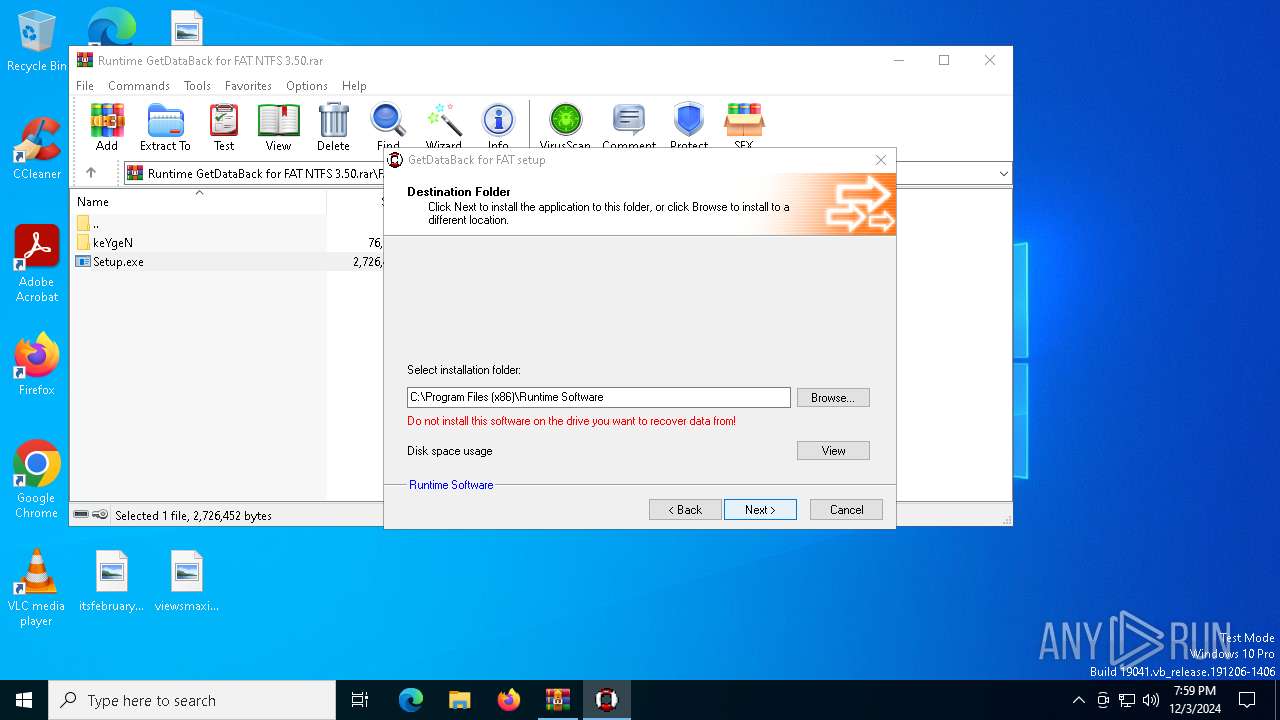
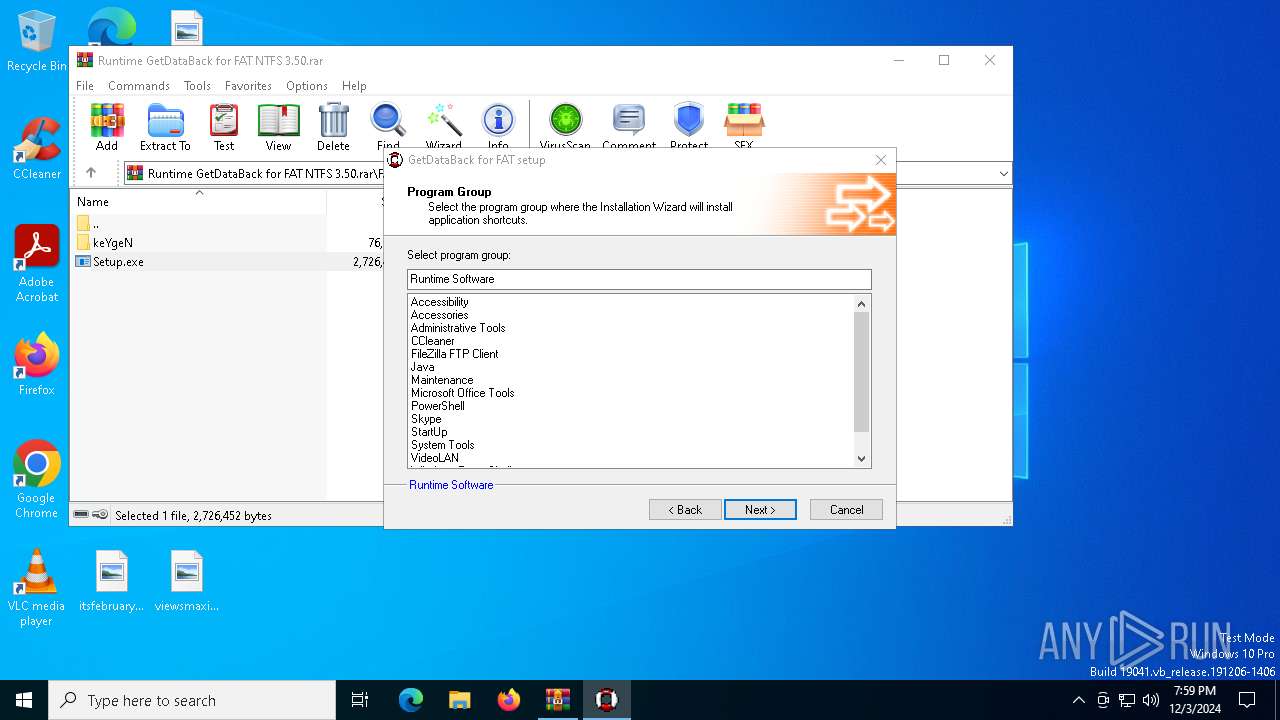
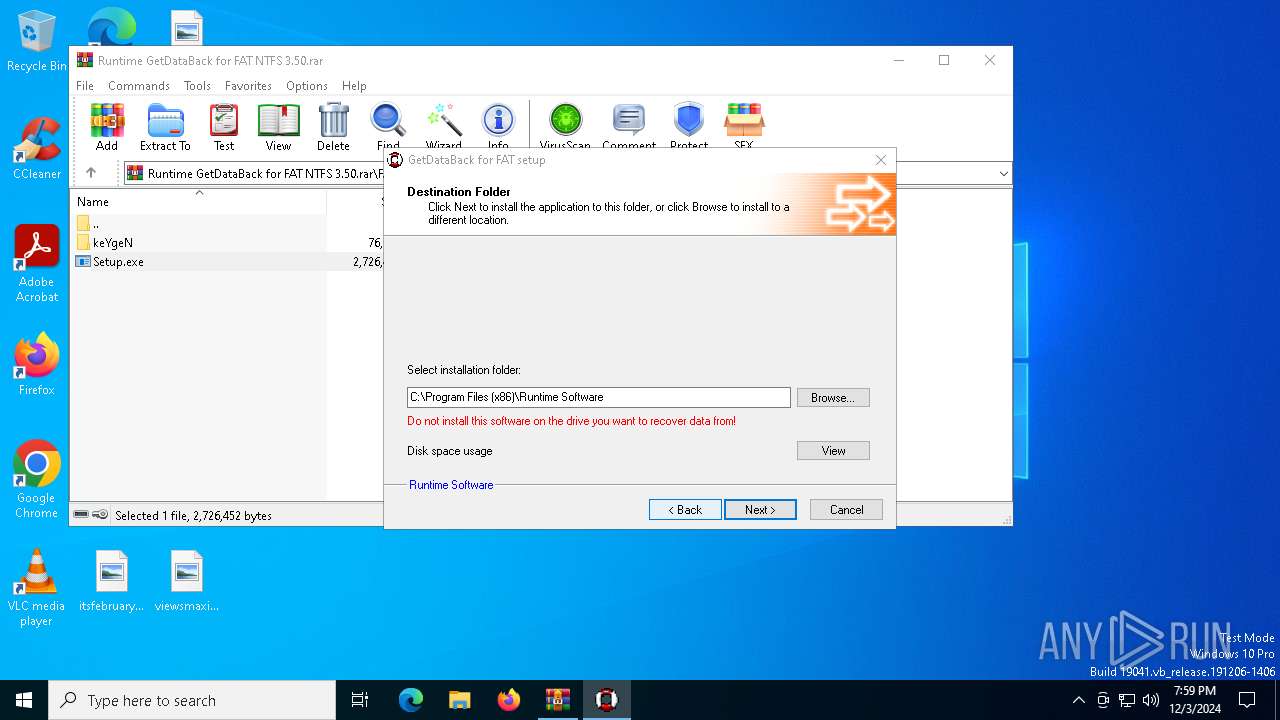
| 6316 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\FAT\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\FAT\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6380 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\FAT\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\FAT\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6404 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Runtime GetDataBack for FAT NTFS 3.50.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6960 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.39782\NTFS\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.39782\NTFS\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.39782\NTFS\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.39782\NTFS\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
Total events
5 862
Read events
5 827
Write events
35
Delete events
0
Modification events
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Runtime GetDataBack for FAT NTFS 3.50.rar | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
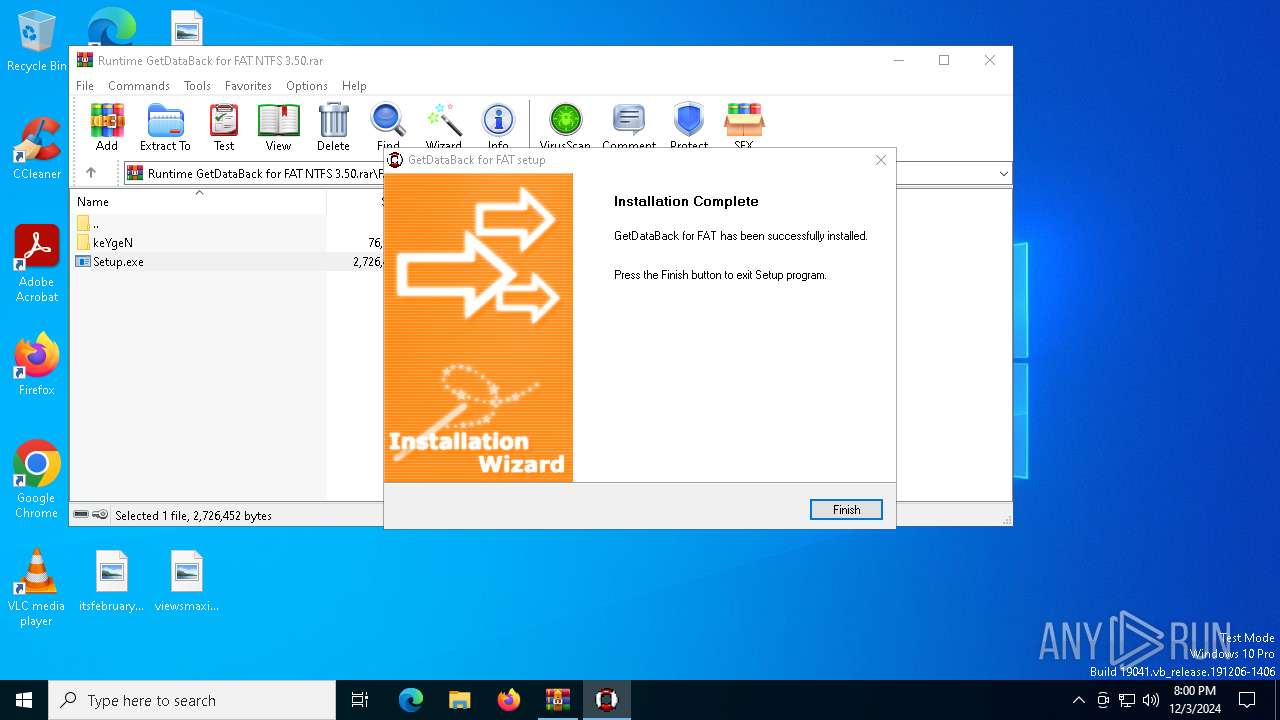
| (PID) Process: | (6316) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Runtime Software\GetDataBack |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files (x86)\Runtime Software\GetDataBack | |||
| (PID) Process: | (6316) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Runtime Software\GetDataBack |
| Operation: | write | Name: | Version |
Value: 3.50.000 | |||
Executable files
19
Suspicious files
25
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
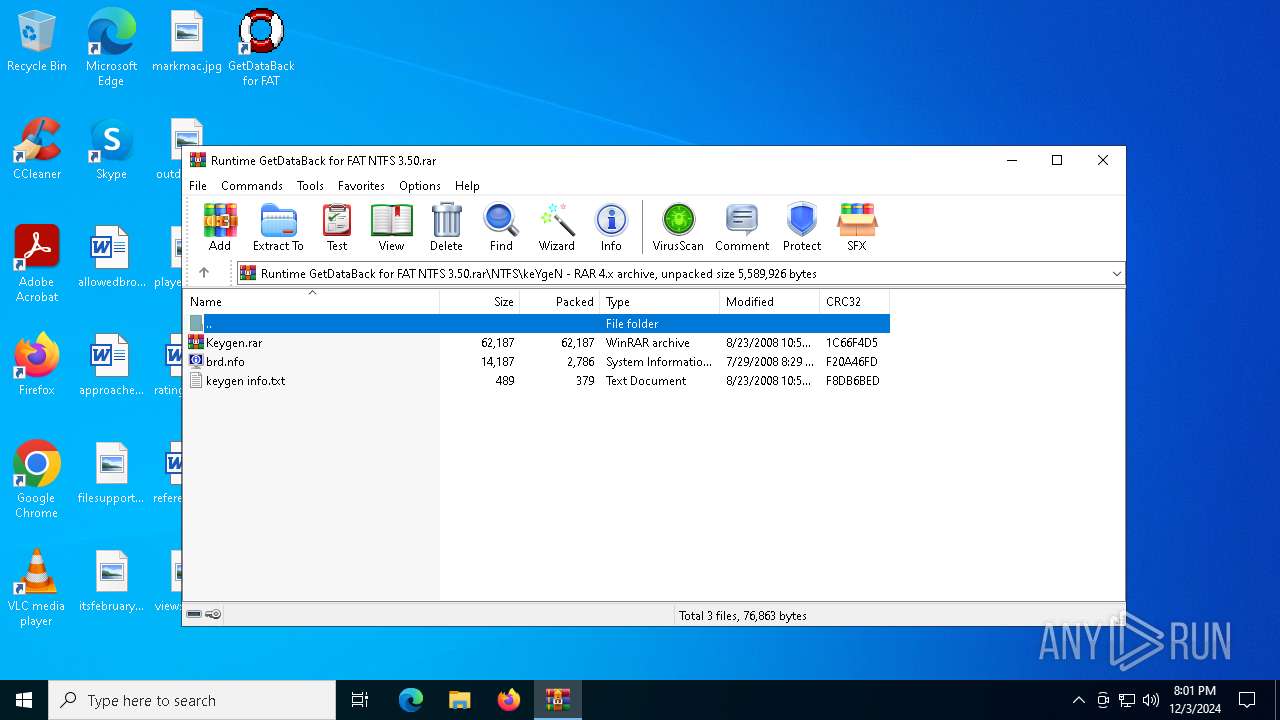
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\FAT\keYgeN\Keygen.rar | compressed | |
MD5:3579F5BD2B24A45D0EF86D23F08EB7F6 | SHA256:6EA72E2BEDCBD5A575B53197F1B6109E468BC234ECF8C859220E001D5304CF6E | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\info.txt | text | |
MD5:3B35D5F5225BD42F1C9D1E611754F737 | SHA256:4CA129A2EC2EDA974F225B492C2488EDC0ABDB8813063A151371B601A0DB6702 | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\NTFS\keYgeN\Keygen.rar | compressed | |
MD5:FAB5D97A0B9E01996981F119F2B84760 | SHA256:12380EC4F2428C2EEAD811093E386F00C744E56D26595C03DDE63208E4D904BB | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\FAT\keYgeN\keygen info.txt | text | |
MD5:5B4B2F154FD24A41BA6E7C991DCEF5E9 | SHA256:4E5CAED92DC454D07FC5E55E12F5A6C48FB509E4AEA546DF07215A3B3A219ECD | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\Runtime GetDataBack for FAT NTFS 3.50.jpg | image | |
MD5:4B6BD581A528819C2ACB58728643A786 | SHA256:D97A73BD49F619D209496C3B88764BE9B0683701459A6CE9CE4555194FBF8C72 | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\NTFS\Setup.exe | executable | |
MD5:A34CC0C4B277F03FDE6EB26D8D2311DD | SHA256:1E3D017B0FDD8388D064F4F8B4A4B5F4D05AD2FC10EB8FD9299F863DC7257419 | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\NTFS\keYgeN\brd.nfo | text | |
MD5:55D7B1B0315FC932E9EE3EDCB5E16EA8 | SHA256:895E63A009BD3DE885A05B7B66462194C66B43873D2CEF1D40DB0DCCE7D1FDC3 | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6404.25268\NTFS\keYgeN\keygen info.txt | text | |
MD5:E786E3855F805E1EBF8CB15BE6D3B88A | SHA256:F70A428A42A52594DC476DDC0171A95ABC87595DC4EDE8EF7A23960043D936DD | |||
| 6316 | Setup.exe | C:\Users\admin\AppData\Local\Temp\1OD6RHP9\unpack.dll | executable | |
MD5:705AA1DC6F5FB72A2182FFD2C95BFA2E | SHA256:EC8361E43F0F83D0DA13261718B8791E5517375FCE67B4055D390353A5B2CA00 | |||
| 6316 | Setup.exe | C:\Users\admin\AppData\Local\Temp\1OD6RHP9\comregc.exe | executable | |
MD5:B1135B4E3A66A57AA43E4DAE7391CBD2 | SHA256:1176A10788BAB070BD20A7D2830698BB37544FCA445385EA70D15113E0B9FF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
524 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
524 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6640 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1488 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
524 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |
gdb.exe | loaded |