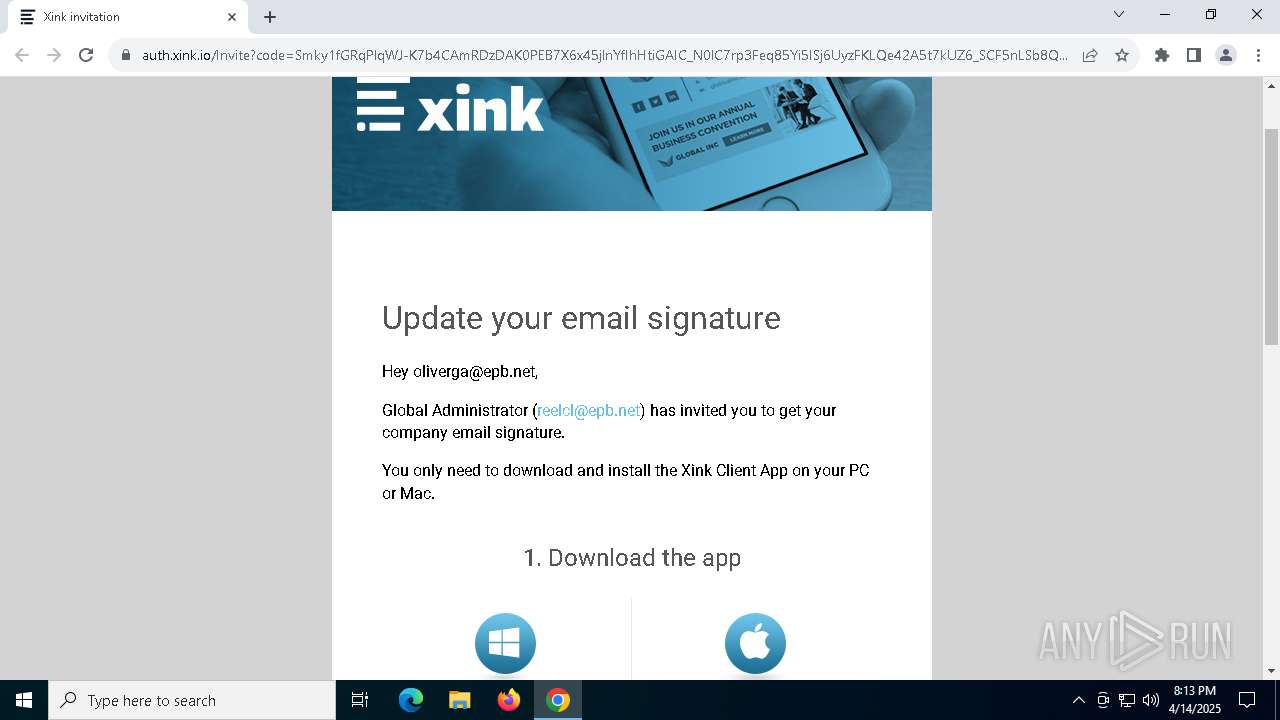
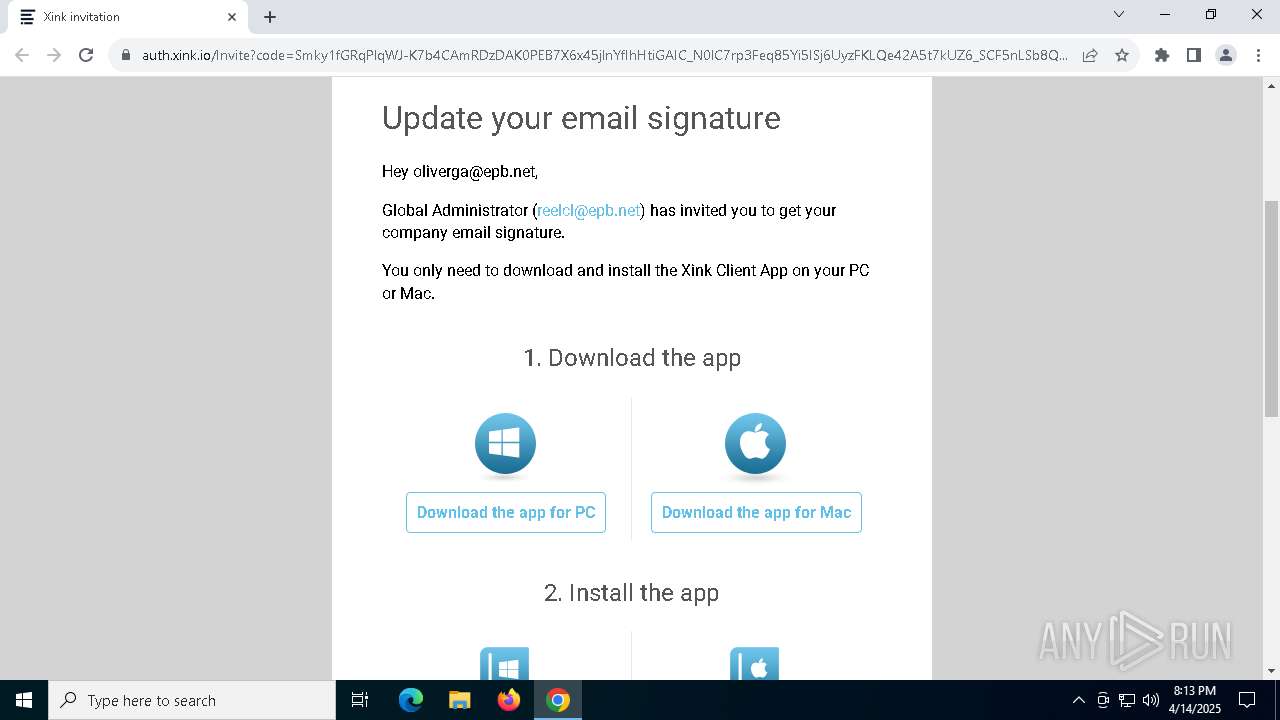
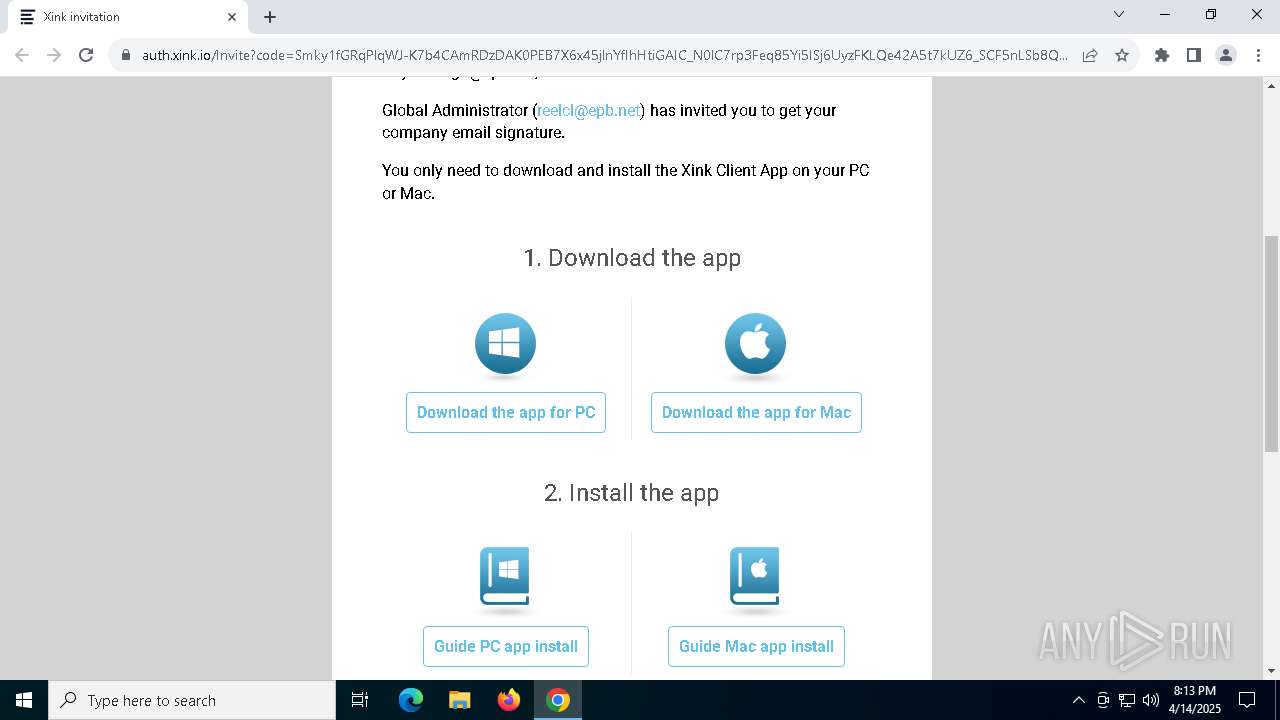
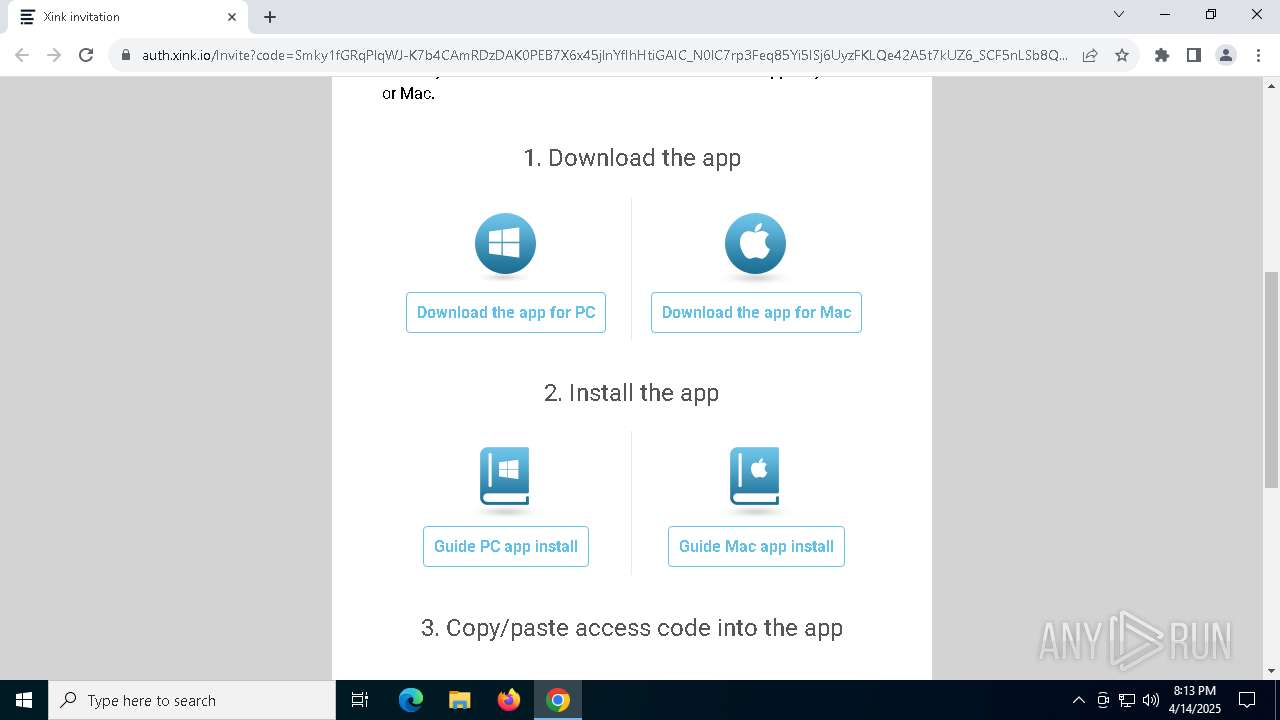
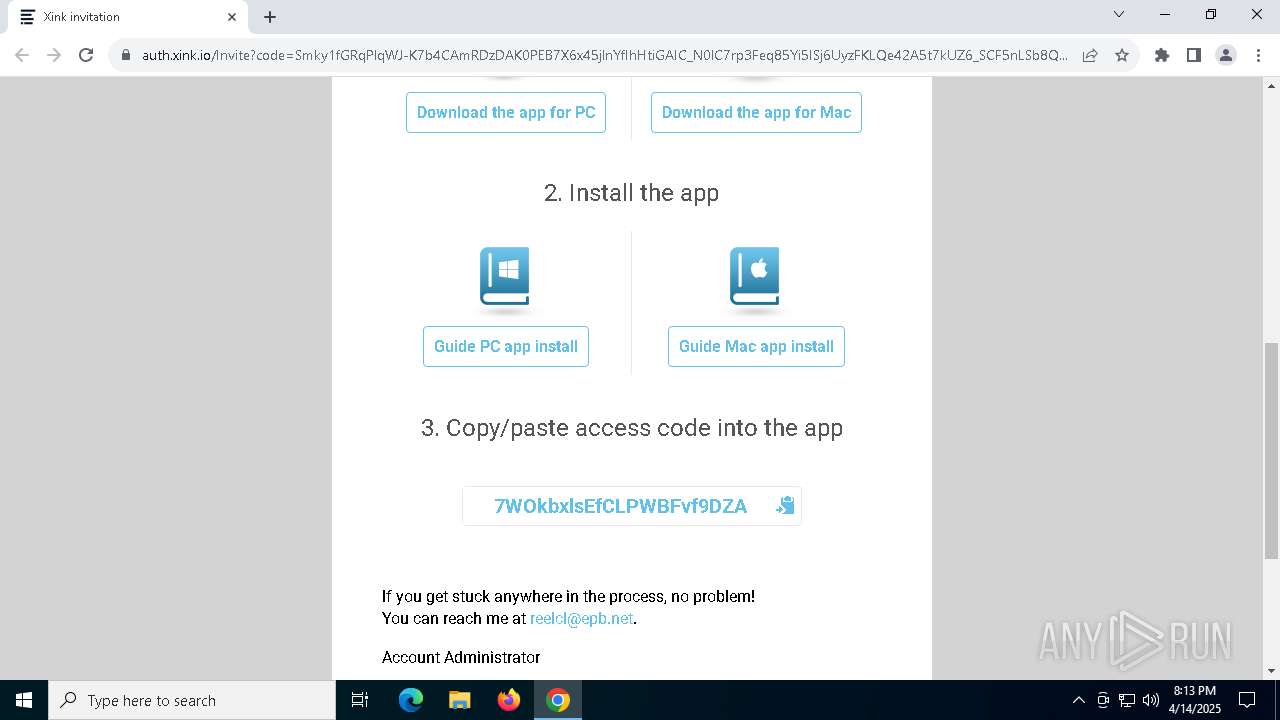
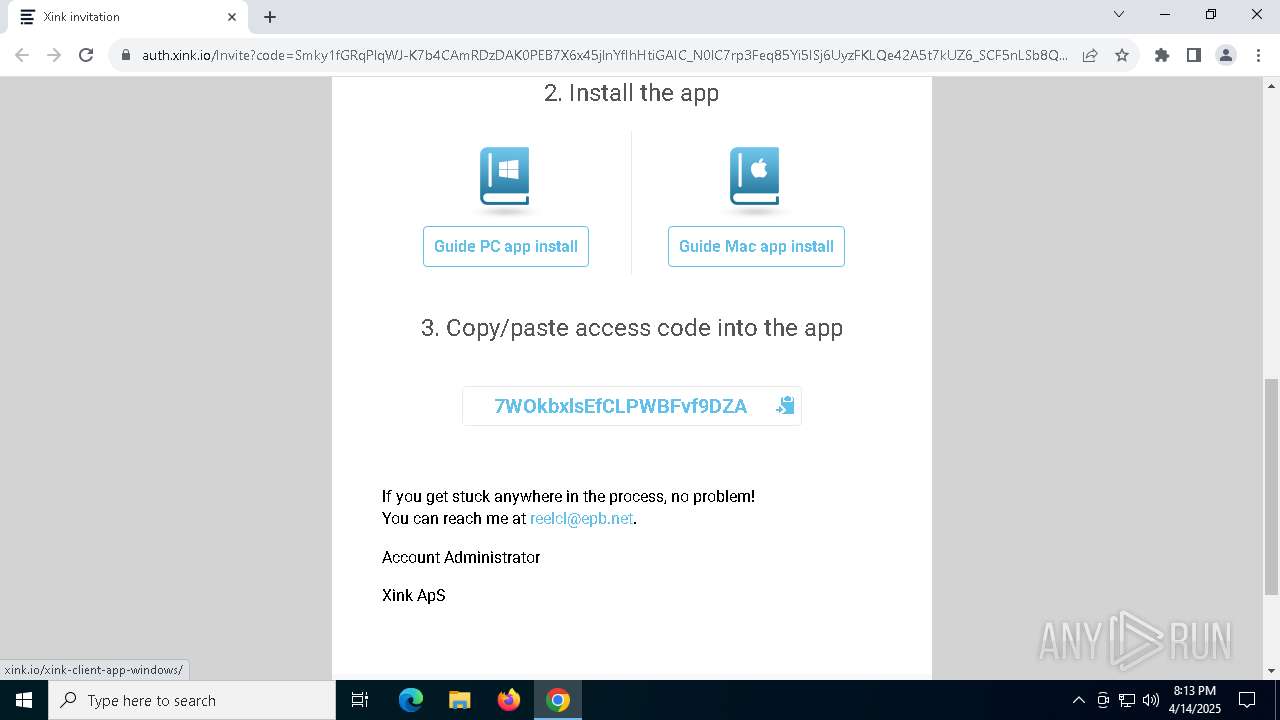
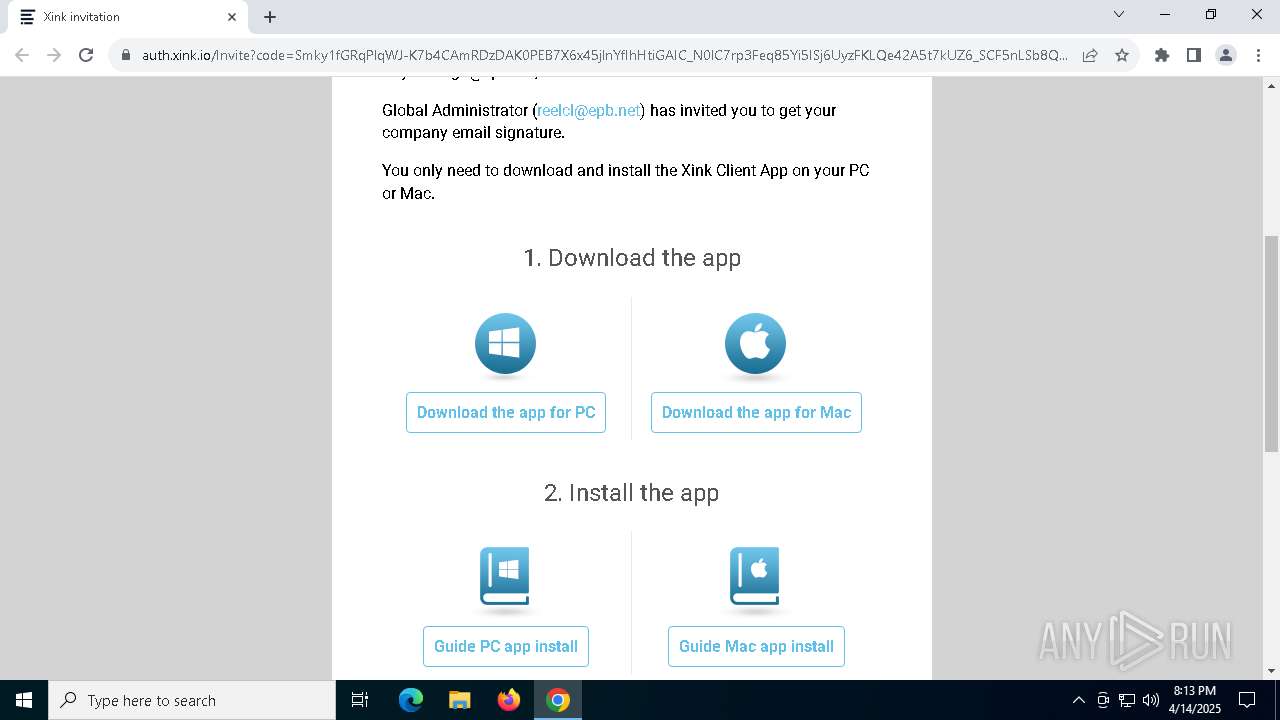
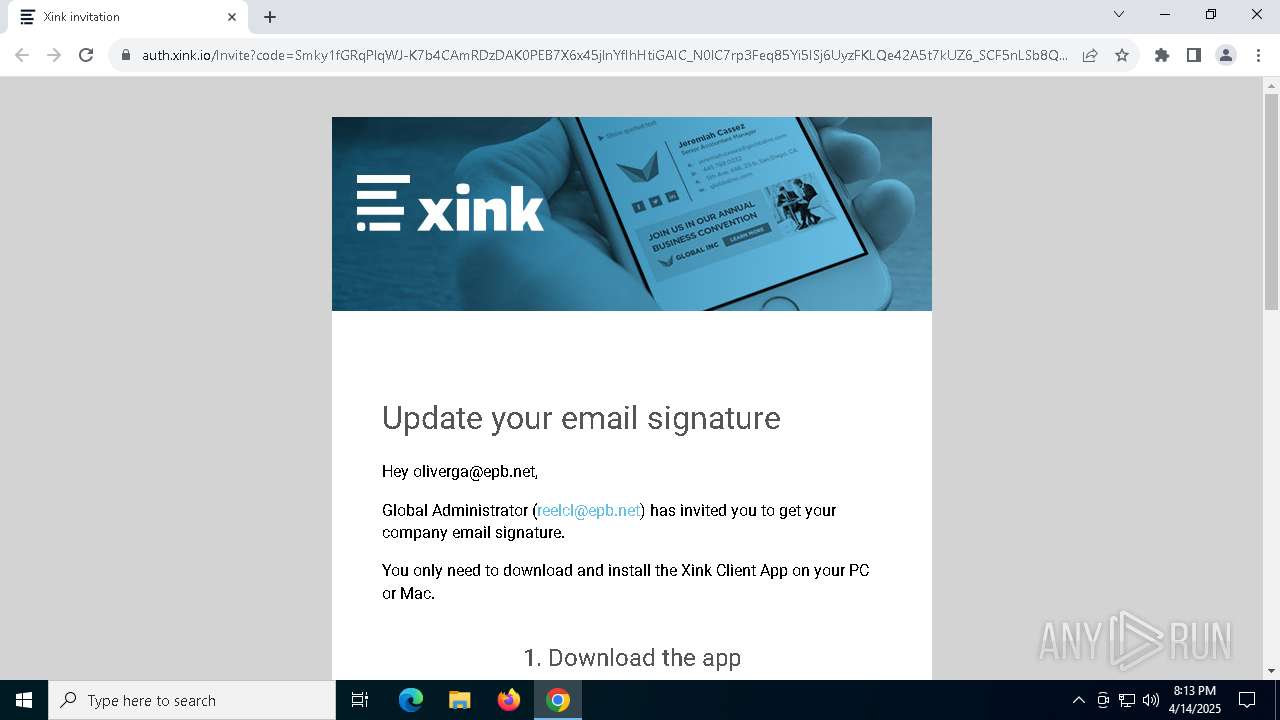
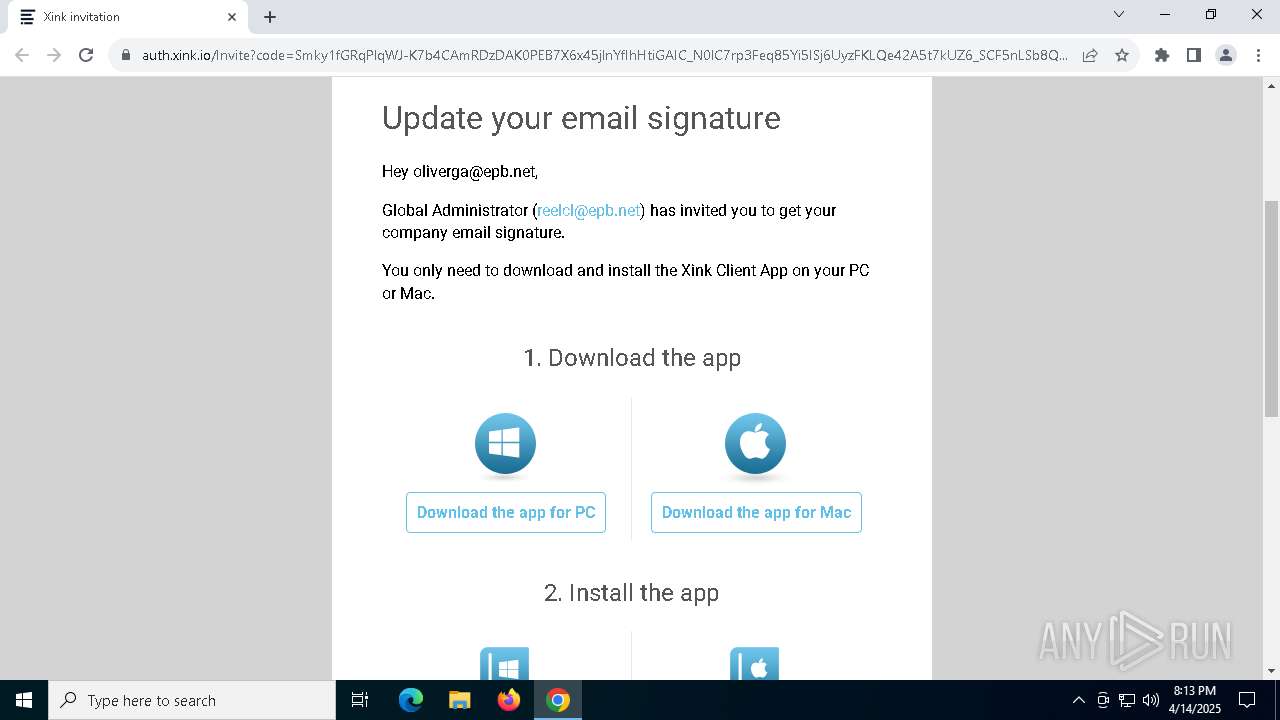
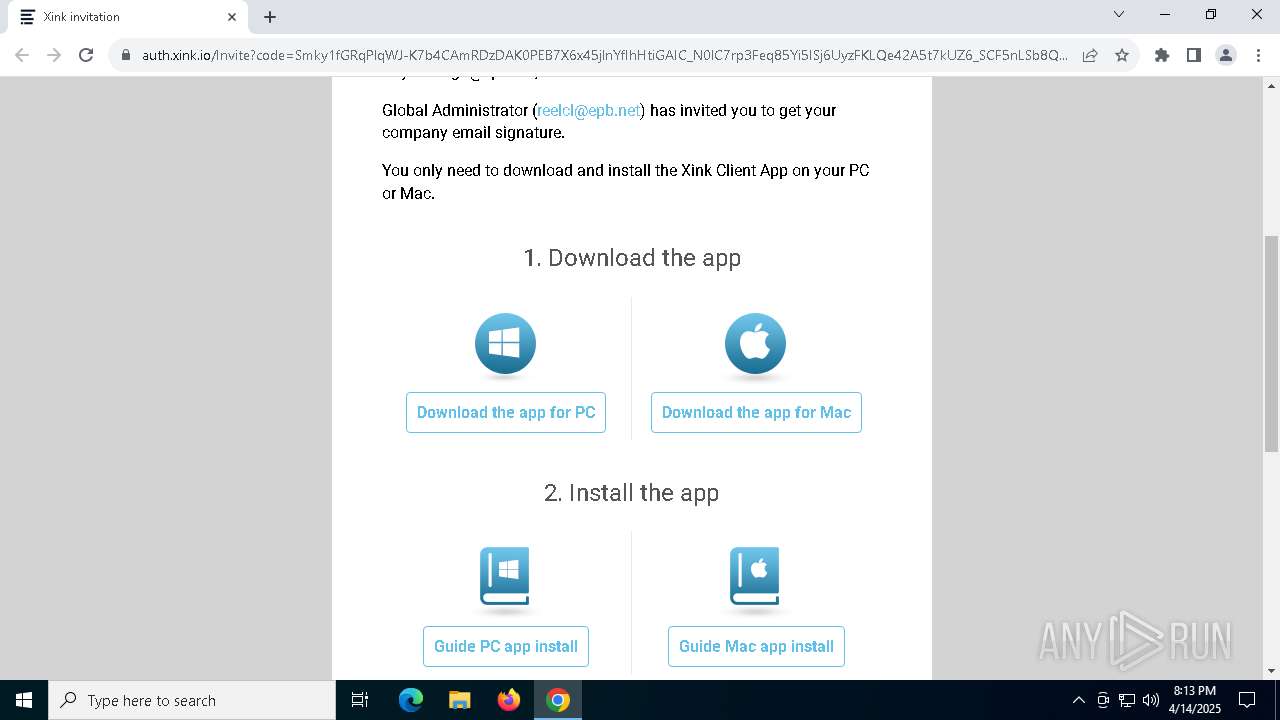
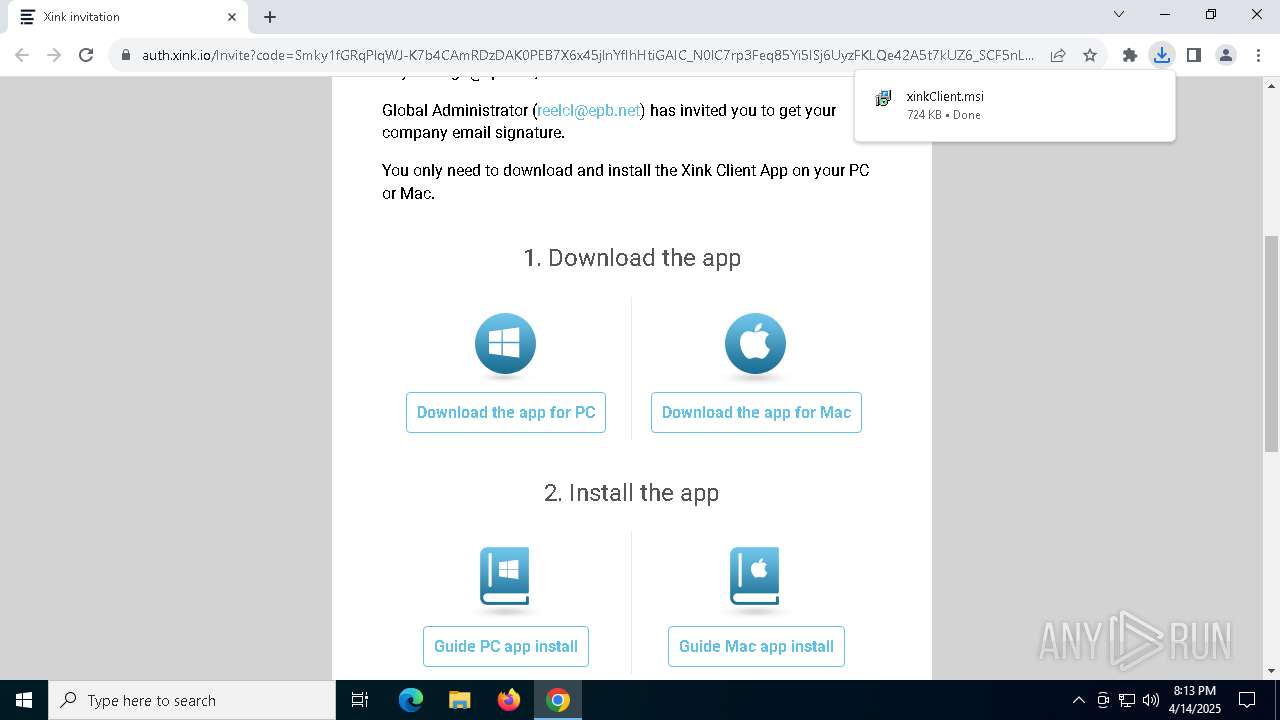
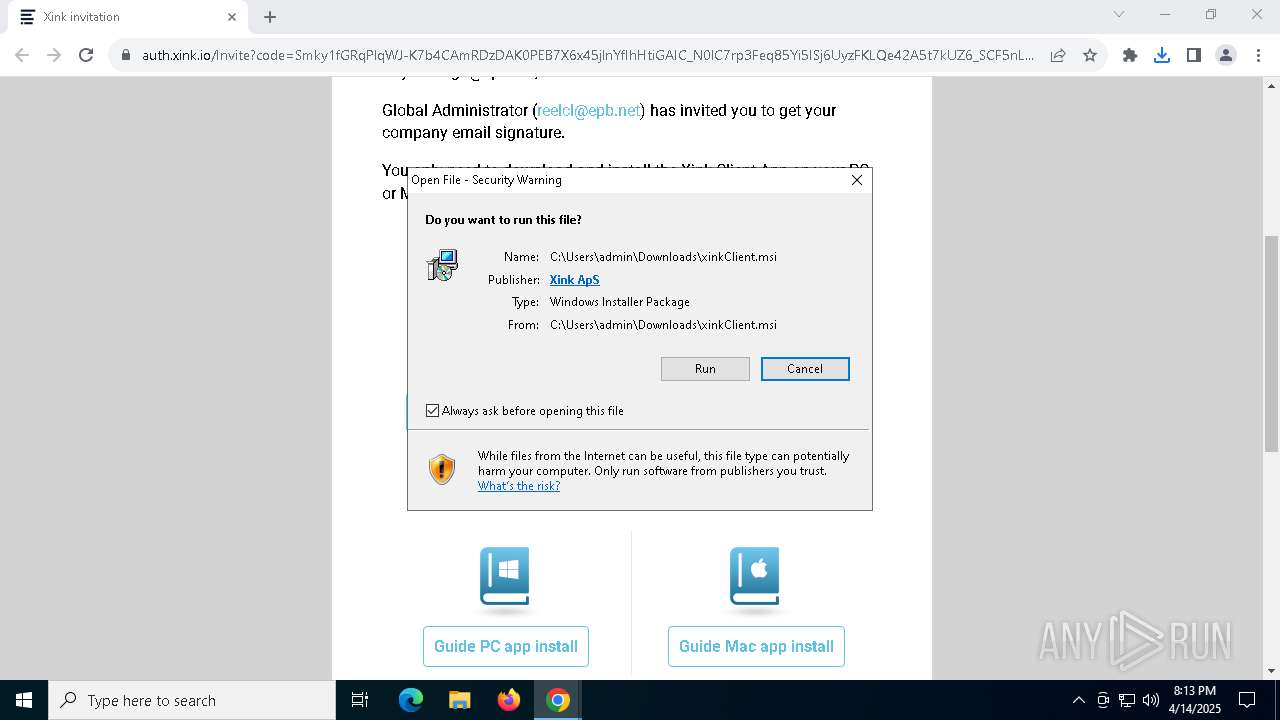
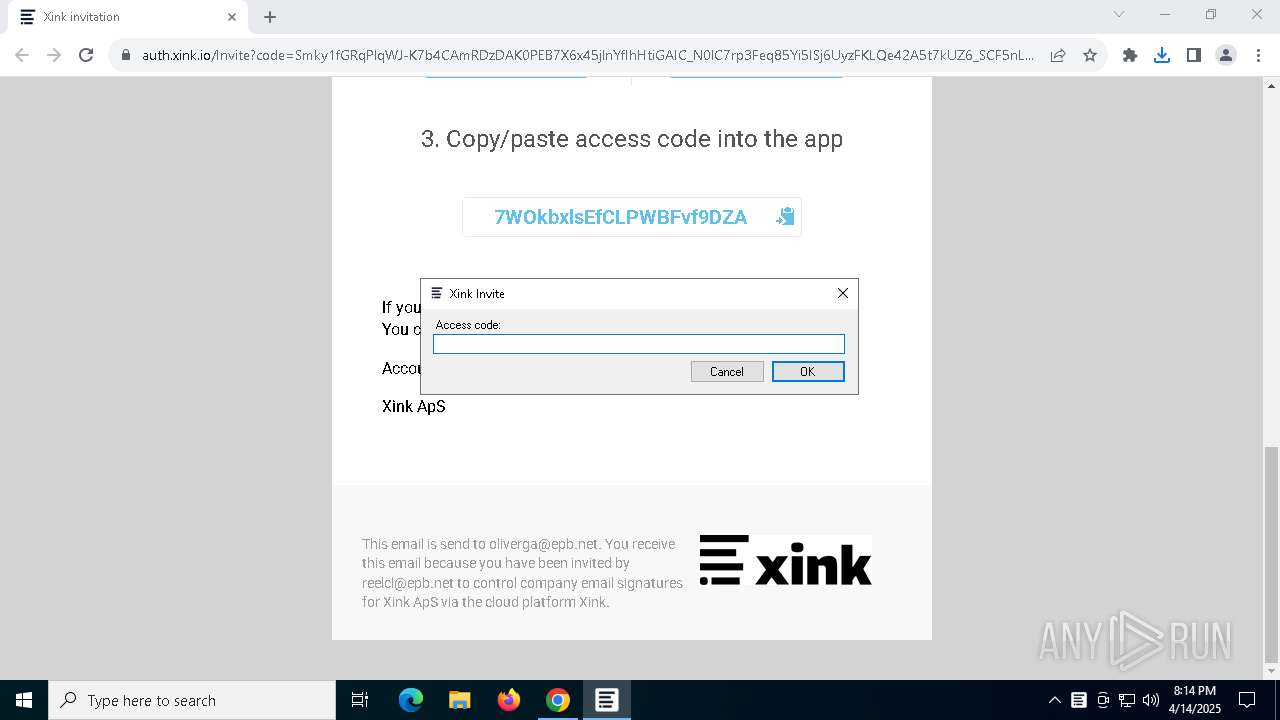
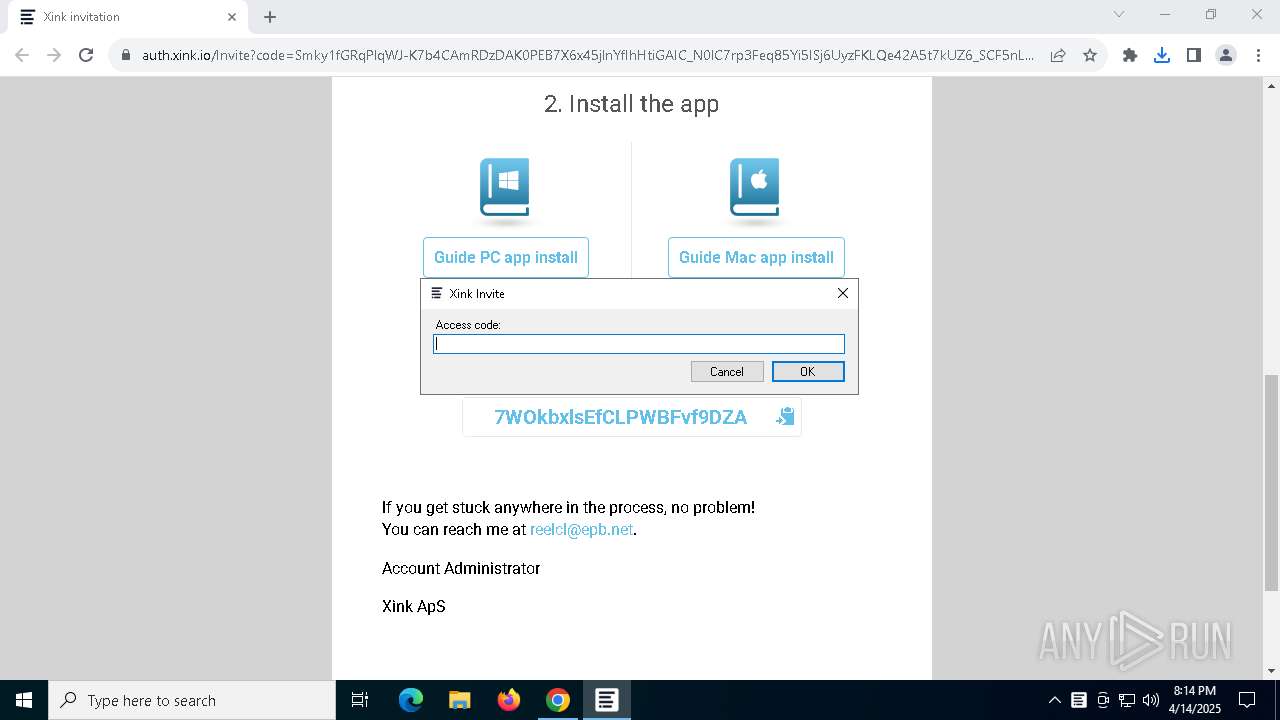
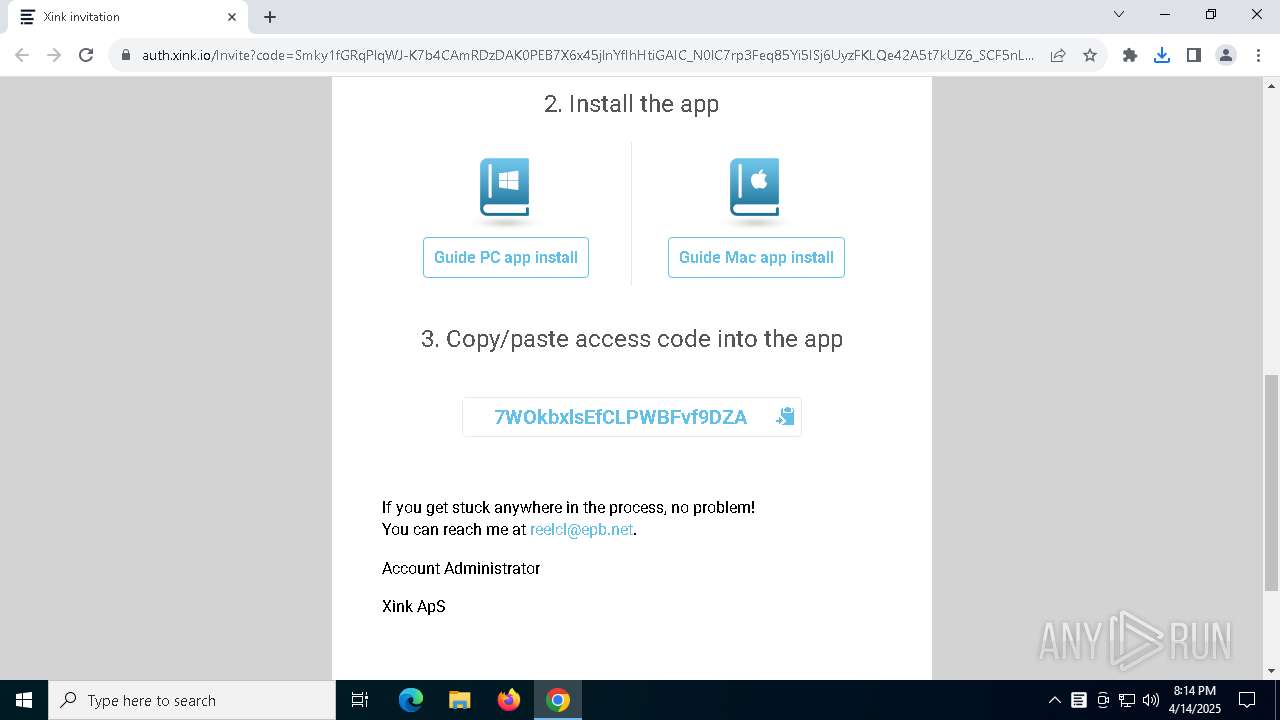
| URL: | https://hello.xink.io/t/n/r-l-0a4ce188195c11f0b10cf7a77984dc4a-l-j-r-l/ |
| Full analysis: | https://app.any.run/tasks/72505667-a9d8-49d2-b371-682c99d6d950 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2025, 20:13:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 83DA59C0FC92BFB8112D24AC054756DB |
| SHA1: | AE61795C688E767B69533002E283995F4D2C52F6 |
| SHA256: | ED12BEB52F6C4FB4BABA888737E75F292AF5EB2754D2C3B60ABF298308AF3604 |
| SSDEEP: | 3:N88qiLO4KK94Gxd0+VHUsFsGRXIJK:28qoFL4Gb0+lqMIJK |
MALICIOUS
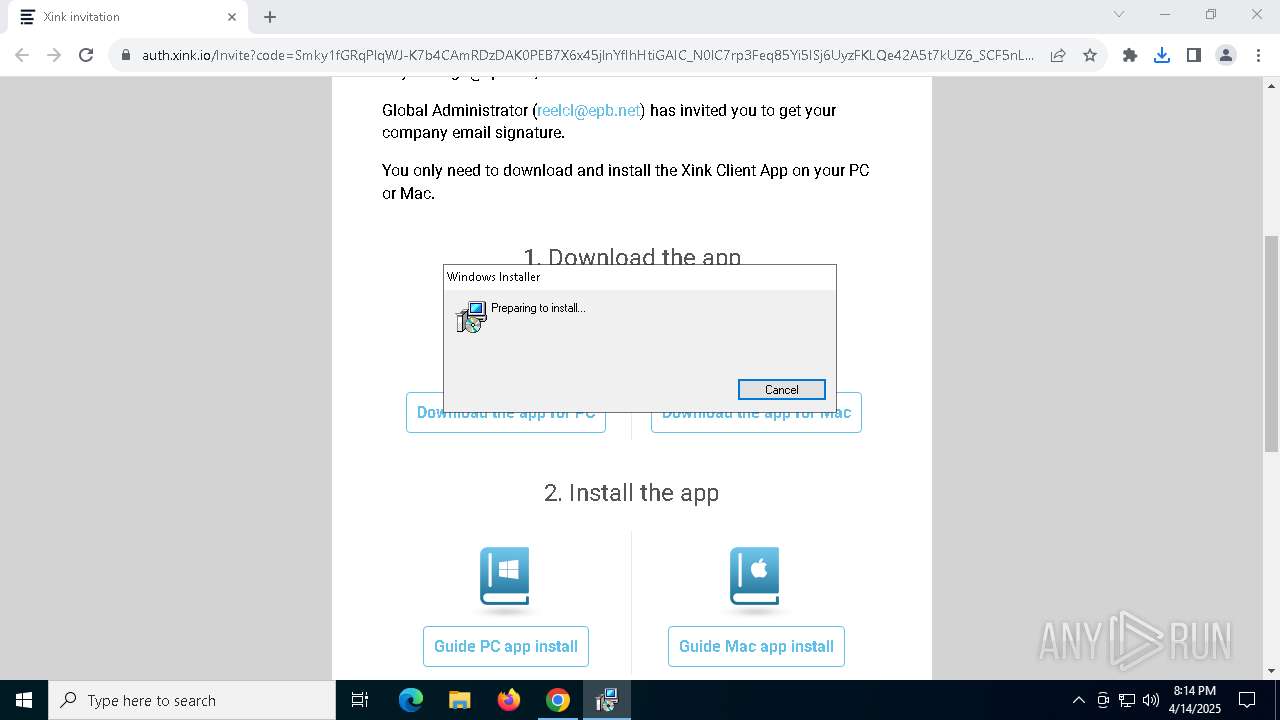
Create files in the Startup directory
- msiexec.exe (PID: 5176)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 4776)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5176)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1676)
- emsclientup.exe (PID: 4180)
INFO
Checks supported languages
- msiexec.exe (PID: 5176)
- msiexec.exe (PID: 1676)
- emsclient.exe (PID: 472)
- emsclientup.exe (PID: 4180)
Creates a software uninstall entry
- msiexec.exe (PID: 5176)
Reads the software policy settings
- msiexec.exe (PID: 7488)
- msiexec.exe (PID: 5176)
- slui.exe (PID: 7352)
- emsclientup.exe (PID: 4180)
Reads Microsoft Office registry keys
- chrome.exe (PID: 7516)
Reads the computer name
- msiexec.exe (PID: 1676)
- msiexec.exe (PID: 5176)
- emsclientup.exe (PID: 4180)
- emsclient.exe (PID: 472)
Executable content was dropped or overwritten
- chrome.exe (PID: 7516)
- msiexec.exe (PID: 5176)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7488)
Application launched itself
- chrome.exe (PID: 7516)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5176)
- emsclientup.exe (PID: 4180)
- emsclient.exe (PID: 472)
Creates files or folders in the user directory
- msiexec.exe (PID: 5176)
- emsclient.exe (PID: 472)
- emsclientup.exe (PID: 4180)
Manages system restore points
- SrTasks.exe (PID: 1912)
Process checks computer location settings
- msiexec.exe (PID: 1676)
Reads Environment values
- emsclientup.exe (PID: 4180)
Checks proxy server information
- emsclientup.exe (PID: 4180)
Disables trace logs
- emsclientup.exe (PID: 4180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
154
Monitored processes
20
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\Users\admin\AppData\Roaming\Xink\Xink Client\emsclient.exe" | C:\Users\admin\AppData\Roaming\Xink\Xink Client\emsclient.exe | — | msiexec.exe | |||||||||||
User: admin Company: Xink Integrity Level: MEDIUM Description: emsclient Version: 3.2.41.1 Modules
| |||||||||||||||
| 1676 | C:\Windows\syswow64\MsiExec.exe -Embedding BC6DC6F62990C3D8B6A79D89264858E9 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\Users\admin\AppData\Roaming\Xink\Xink Client\emsclientup.exe" | C:\Users\admin\AppData\Roaming\Xink\Xink Client\emsclientup.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: emsclientup Version: 3.1.4.1 Modules
| |||||||||||||||
| 4688 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4640 --field-trial-handle=1848,i,12195558408592903389,17408556887397655805,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 7288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5532 --field-trial-handle=1848,i,12195558408592903389,17408556887397655805,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 7352 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 300
Read events
26 010
Write events
272
Delete events
18
Modification events
| (PID) Process: | (7516) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7516) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7516) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7516) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7516) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7288) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000A48A47C079ADDB01 | |||
| (PID) Process: | (7516) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (5176) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000026FC21C379ADDB013814000010130000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5176) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000026FC21C379ADDB013814000010130000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5176) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000DD5E76C379ADDB013814000010130000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
12
Suspicious files
65
Text files
23
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c0a2.TMP | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c0b2.TMP | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c0a2.TMP | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c0b2.TMP | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c0b2.TMP | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7516 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
57
DNS requests
45
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7216 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7216 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7516 | chrome.exe | GET | 200 | 18.173.205.57:80 | http://ocsps.ssl.com/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBQMDtATfnJO6JAXDQoHl8pAaJdhTQQU3QQJB6L1en1SUxKSle44gCUNplkCCGQzUdPHOJ8I | unknown | — | — | whitelisted |
7516 | chrome.exe | GET | 200 | 18.173.205.57:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSOf8DjMnuwFThpZh9bv9IoPvmNMAQUVML%2BEJUAk81q9efA19myS7iPDOMCEEV1DXEmHcHGj7xhG2rtXK4%3D | unknown | — | — | whitelisted |
7192 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
7192 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
7192 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7732 | chrome.exe | 142.251.18.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
7516 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
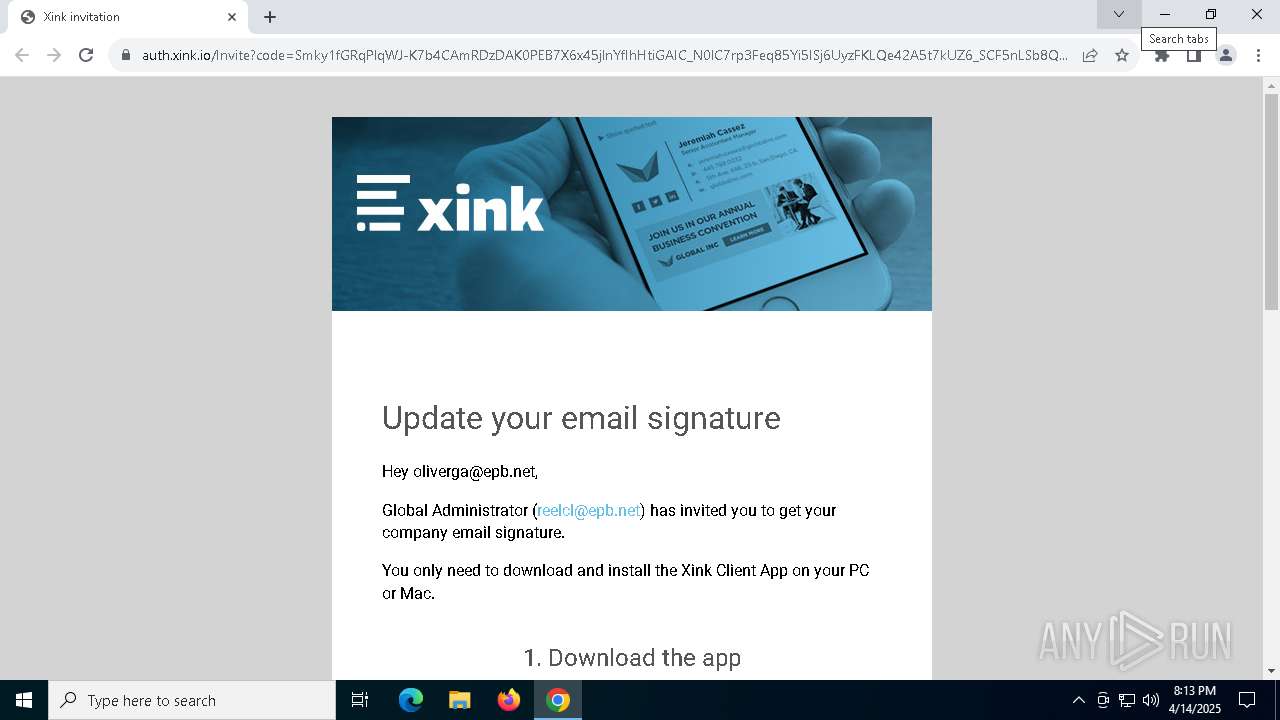
7732 | chrome.exe | 13.52.43.40:443 | hello.xink.io | AMAZON-02 | US | unknown |
7732 | chrome.exe | 40.71.0.179:443 | auth.xink.io | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
7732 | chrome.exe | 216.58.206.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
hello.xink.io |
| unknown |
accounts.google.com |
| whitelisted |
auth.xink.io |
| unknown |
fonts.googleapis.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
js.monitor.azure.com |
| whitelisted |