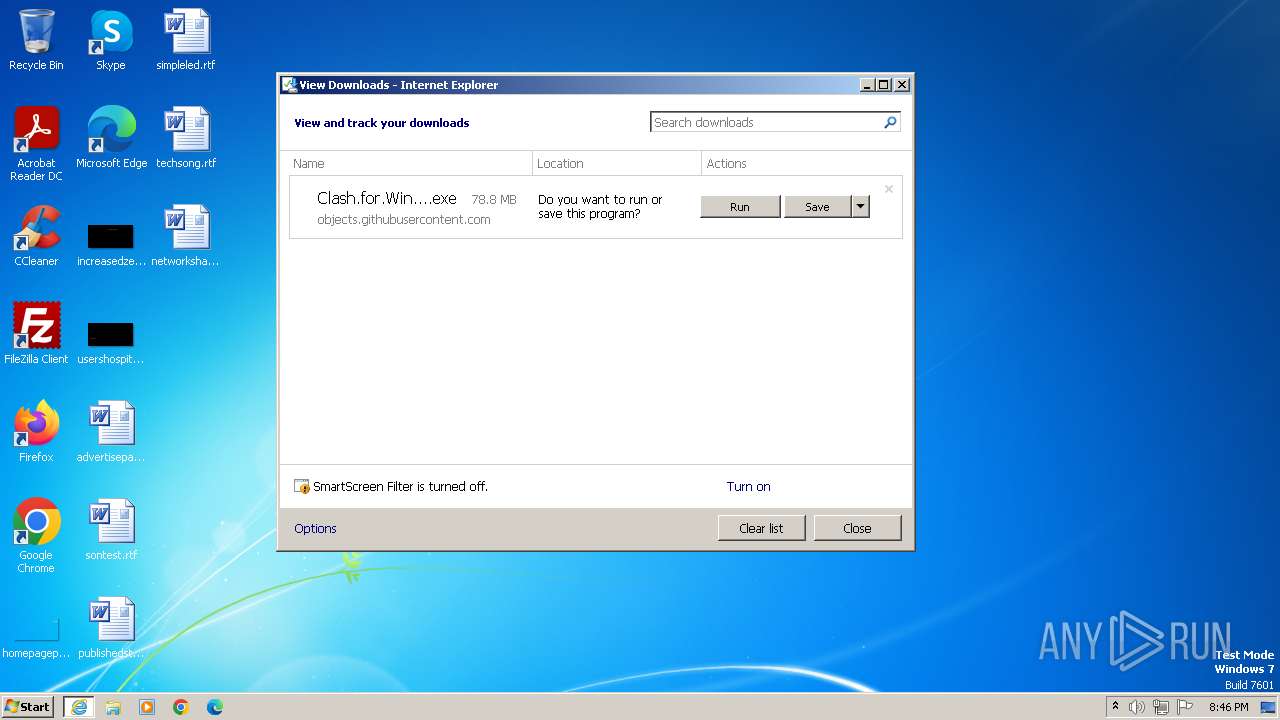
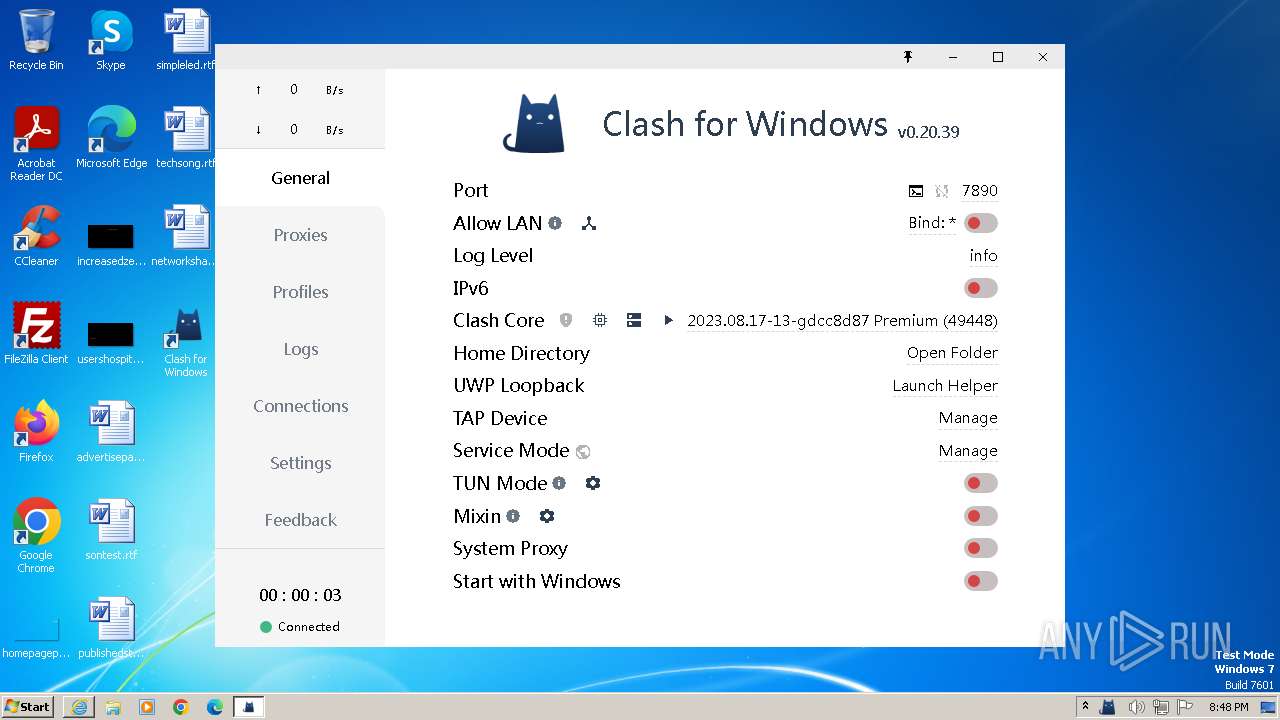
| URL: | https://github.com/Fndroid/clash_for_windows_pkg/releases/download/0.20.39/Clash.for.Windows.Setup.0.20.39.ia32.exe |
| Full analysis: | https://app.any.run/tasks/abe631a9-bb1e-490f-af63-2075fd9b5eab |
| Verdict: | Malicious activity |
| Analysis date: | October 21, 2023, 19:46:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 098D8D2E0EF6510E6963B13FE41246ED4A0BB904 |
| SHA256: | ECE22355FA61933673BA6BAEF063CDF0C45E6835B1E3F3B7EB961EAFA9BC4EDE |
| SSDEEP: | 3:N8tEdHfF6WXSNMdkCVlEK8Lj8SZDMMA:2uiQpdZE5ZgB |
MALICIOUS
Application was dropped or rewritten from another process
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- clash-win32.exe (PID: 3184)
Loads dropped or rewritten executable
- Clash for Windows.exe (PID: 2432)
- Clash for Windows.exe (PID: 3064)
- Clash for Windows.exe (PID: 3400)
- Clash for Windows.exe (PID: 3580)
Drops the executable file immediately after the start
- Clash for Windows.exe (PID: 2432)
- Clash for Windows.exe (PID: 3400)
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3416)
Bypass execution policy to execute commands
- powershell.exe (PID: 2696)
SUSPICIOUS
Process drops legitimate windows executable
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
The process creates files with name similar to system file names
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Malware-specific behavior (creating "System.dll" in Temp)
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Starts application with an unusual extension
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- cmd.exe (PID: 3068)
Get information on the list of running processes
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- nsA449.tmp (PID: 1864)
- cmd.exe (PID: 2124)
Starts CMD.EXE for commands execution
- nsA449.tmp (PID: 1864)
- Clash for Windows.exe (PID: 3400)
Drops 7-zip archiver for unpacking
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Drops a system driver (possible attempt to evade defenses)
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Application launched itself
- Clash for Windows.exe (PID: 2432)
Reads the Internet Settings
- Clash for Windows.exe (PID: 2432)
Reads settings of System Certificates
- Clash for Windows.exe (PID: 2432)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 3068)
Powershell version downgrade attack
- powershell.exe (PID: 2696)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 3920)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3416)
INFO
Application launched itself
- iexplore.exe (PID: 556)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3124)
Loads dropped or rewritten executable
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Checks supported languages
- nsA449.tmp (PID: 1864)
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- Clash for Windows.exe (PID: 3580)
- Clash for Windows.exe (PID: 3064)
- Clash for Windows.exe (PID: 3400)
- Clash for Windows.exe (PID: 2432)
- chcp.com (PID: 2148)
- clash-win32.exe (PID: 3184)
Reads the computer name
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- Clash for Windows.exe (PID: 3580)
- Clash for Windows.exe (PID: 2432)
- Clash for Windows.exe (PID: 3064)
- Clash for Windows.exe (PID: 3400)
- clash-win32.exe (PID: 3184)
The process uses the downloaded file
- iexplore.exe (PID: 556)
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Creates files or folders in the user directory
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- Clash for Windows.exe (PID: 2432)
- Clash for Windows.exe (PID: 3064)
- Clash for Windows.exe (PID: 3400)
Reads the machine GUID from the registry
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
- Clash for Windows.exe (PID: 2432)
Manual execution by a user
- Clash for Windows.exe (PID: 2432)
Create files in a temporary directory
- Clash for Windows.exe (PID: 2432)
- Clash.for.Windows.Setup.0.20.39.ia32.exe (PID: 3528)
Process checks computer location settings
- Clash for Windows.exe (PID: 2432)
- Clash for Windows.exe (PID: 3400)
Reads Environment values
- Clash for Windows.exe (PID: 3400)
Reads product name
- Clash for Windows.exe (PID: 3400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
64
Monitored processes
20
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | tasklist /FI "USERNAME eq admin" /FI "IMAGENAME eq Clash for Windows.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/Fndroid/clash_for_windows_pkg/releases/download/0.20.39/Clash.for.Windows.Setup.0.20.39.ia32.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 576 | route print 0.0.0.0 mask 0.0.0.0 | C:\Windows\System32\ROUTE.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1852 | netsh wlan show interfaces | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1864 | "C:\Users\admin\AppData\Local\Temp\nsu962F.tmp\nsA449.tmp" cmd /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq Clash for Windows.exe" | %SYSTEMROOT%\System32\find.exe "Clash for Windows.exe" | C:\Users\admin\AppData\Local\Temp\nsu962F.tmp\nsA449.tmp | — | Clash.for.Windows.Setup.0.20.39.ia32.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2124 | cmd /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq Clash for Windows.exe" | %SYSTEMROOT%\System32\find.exe "Clash for Windows.exe" | C:\Windows\System32\cmd.exe | — | nsA449.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2148 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\AppData\Local\Programs\Clash for Windows\Clash for Windows.exe" | C:\Users\admin\AppData\Local\Programs\Clash for Windows\Clash for Windows.exe | — | explorer.exe | |||||||||||
User: admin Company: Fndroid Integrity Level: MEDIUM Description: Clash for Windows Exit code: 0 Version: 0.20.39 Modules
| |||||||||||||||
| 2696 | powershell.exe -ExecutionPolicy Bypass -Command "Get-NetFirewallRule -Description \"Work with Clash for Windows.\" | ? {$_.Enabled -eq \"True\"} | Get-NetFirewallApplicationFilter" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3064 | "C:\Users\admin\AppData\Local\Programs\Clash for Windows\Clash for Windows.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\clash_win" --mojo-platform-channel-handle=1292 --field-trial-handle=1040,i,5607249338811547983,18212606736386627263,131072 --disable-features=OutOfBlinkCors,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Users\admin\AppData\Local\Programs\Clash for Windows\Clash for Windows.exe | Clash for Windows.exe | ||||||||||||
User: admin Company: Fndroid Integrity Level: MEDIUM Description: Clash for Windows Exit code: 0 Version: 0.20.39 Modules
| |||||||||||||||
Total events
25 507
Read events
25 339
Write events
168
Delete events
0
Modification events
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
50
Suspicious files
189
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Clash.for.Windows.Setup.0.20.39.ia32.exe.hyvr4e0.partial | — | |
MD5:— | SHA256:— | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Clash.for.Windows.Setup.0.20.39.ia32.exe | — | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:941C9D0D26C17414EF5E9C83C46A53C2 | SHA256:54F45EB4F9A04DECBE30CDB1A03E02B4F2472E654BE7F03F7C44D42E17DAA791 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:BC1BDF78D97DC696D1CE1D8A67DD7377 | SHA256:157F7673D754103CFE454D99C42E46F7988591C0E0441169C25C3EE77F961507 | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD72F141668721105.TMP | binary | |
MD5:E9734B4F6DA470BAF970CF227885D6A5 | SHA256:6FAE0B0310CB5775BE0A7873739849CE5375BE864B03DB4269B14FE1209BE847 | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{91B99FBD-704A-11EE-B150-12A9866C77DE}.dat | binary | |
MD5:9C2559906E391E3BC1D679A9A0EE66DC | SHA256:919A0E7F6085AD195134A4A7326C38602114B8E964C907B96CD39CEF550E0EC8 | |||
| 3528 | Clash.for.Windows.Setup.0.20.39.ia32.exe | C:\Users\admin\AppData\Local\Temp\nsu962F.tmp\app-32.7z | — | |
MD5:— | SHA256:— | |||
| 3528 | Clash.for.Windows.Setup.0.20.39.ia32.exe | C:\Users\admin\AppData\Local\Temp\nsu962F.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 3528 | Clash.for.Windows.Setup.0.20.39.ia32.exe | C:\Users\admin\AppData\Local\Temp\nsu962F.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
25
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3124 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f96a15a63697bdc6 | unknown | compressed | 4.66 Kb | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 314 b | unknown |
3124 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c0b0cfbec41be01e | unknown | compressed | 4.66 Kb | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
556 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
556 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | der | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
556 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | der | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3124 | iexplore.exe | 140.82.121.3:443 | — | GITHUB | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3124 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3124 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3124 | iexplore.exe | 185.199.109.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
556 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
556 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
556 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r2---sn-q4flrn7k.gvt1.com |
| whitelisted |