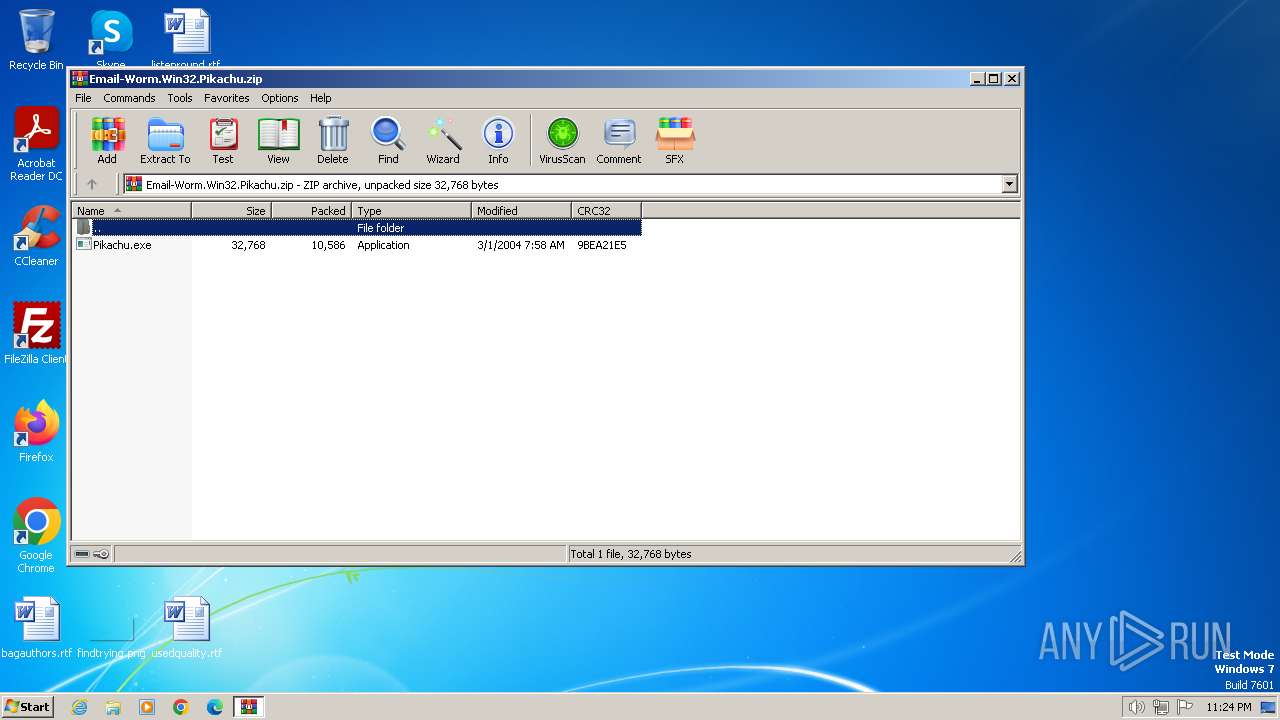
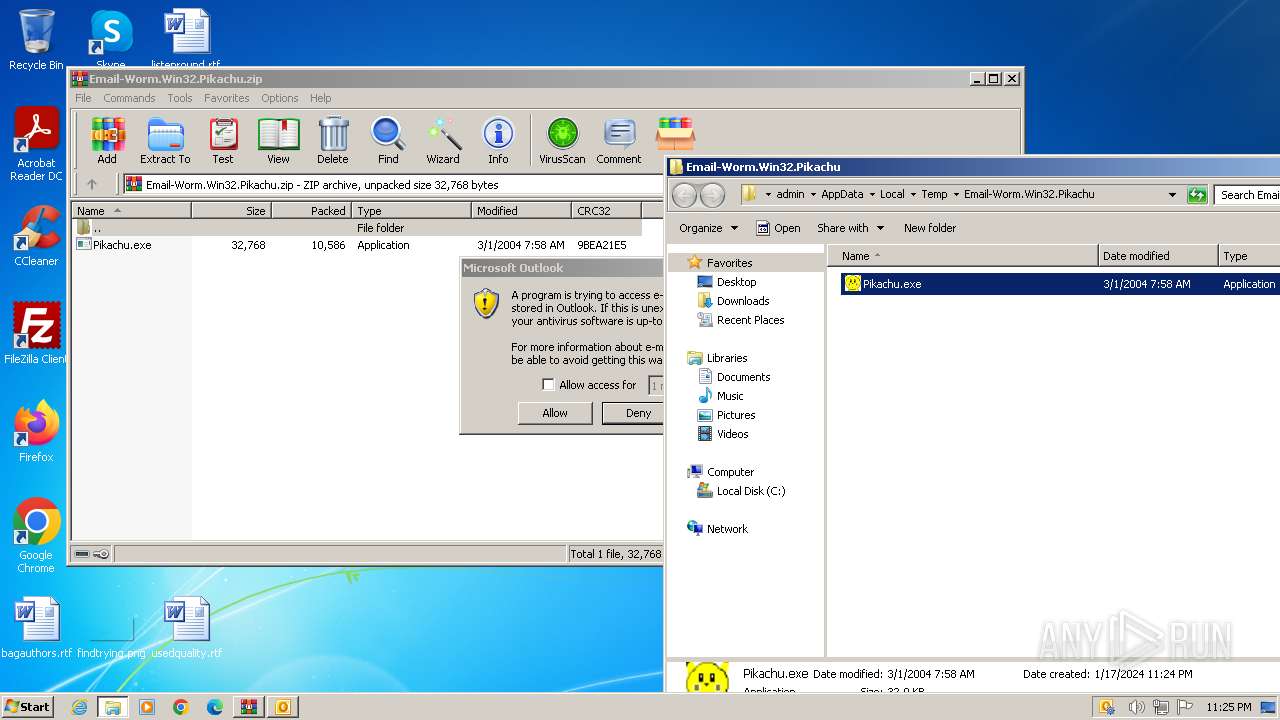
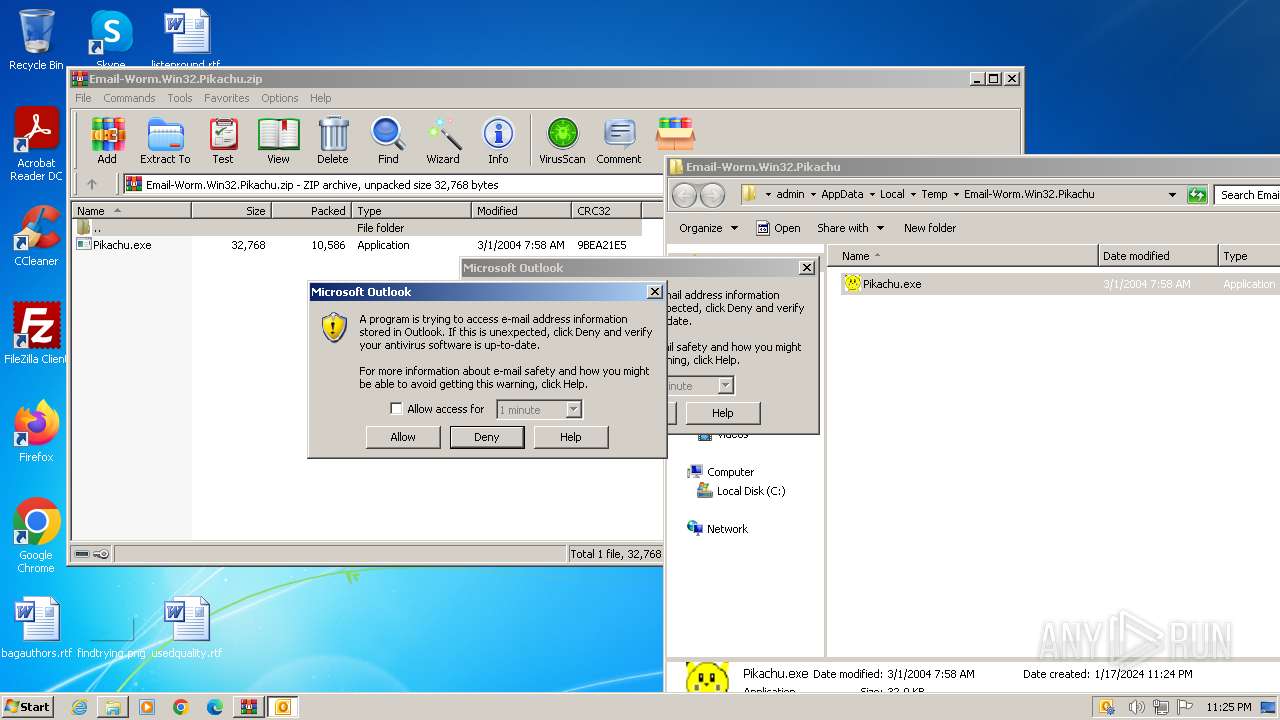
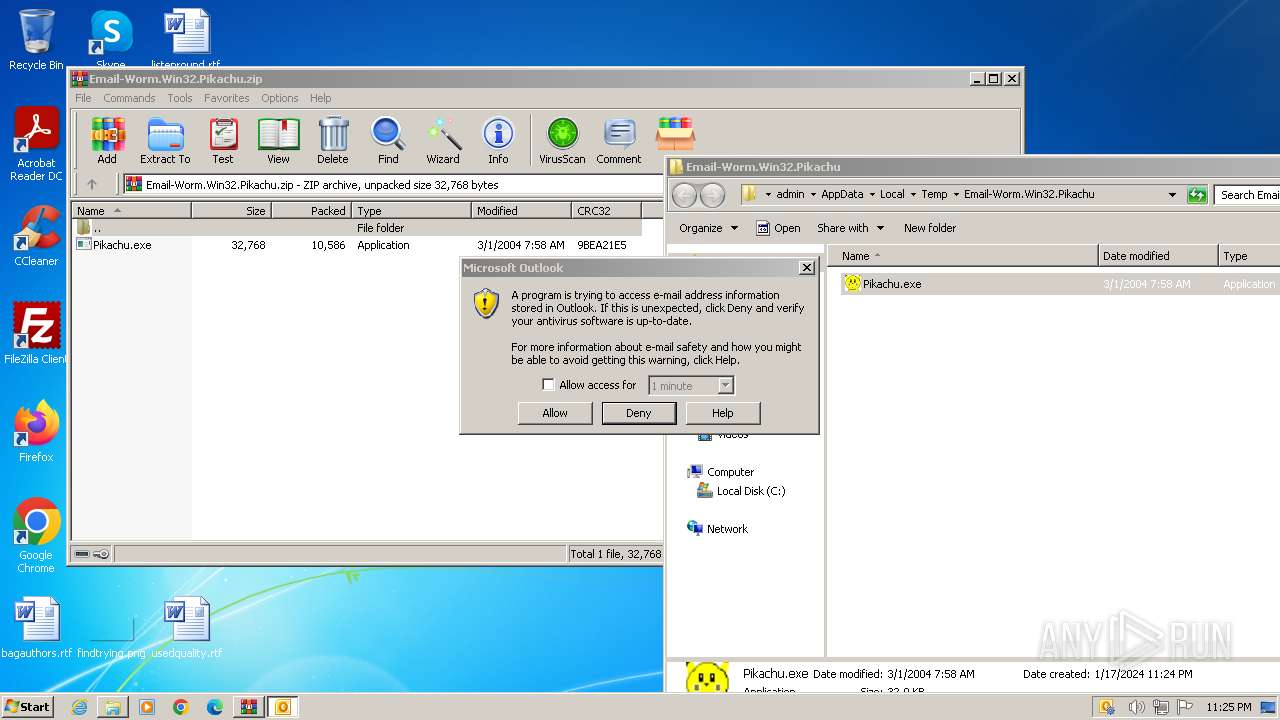
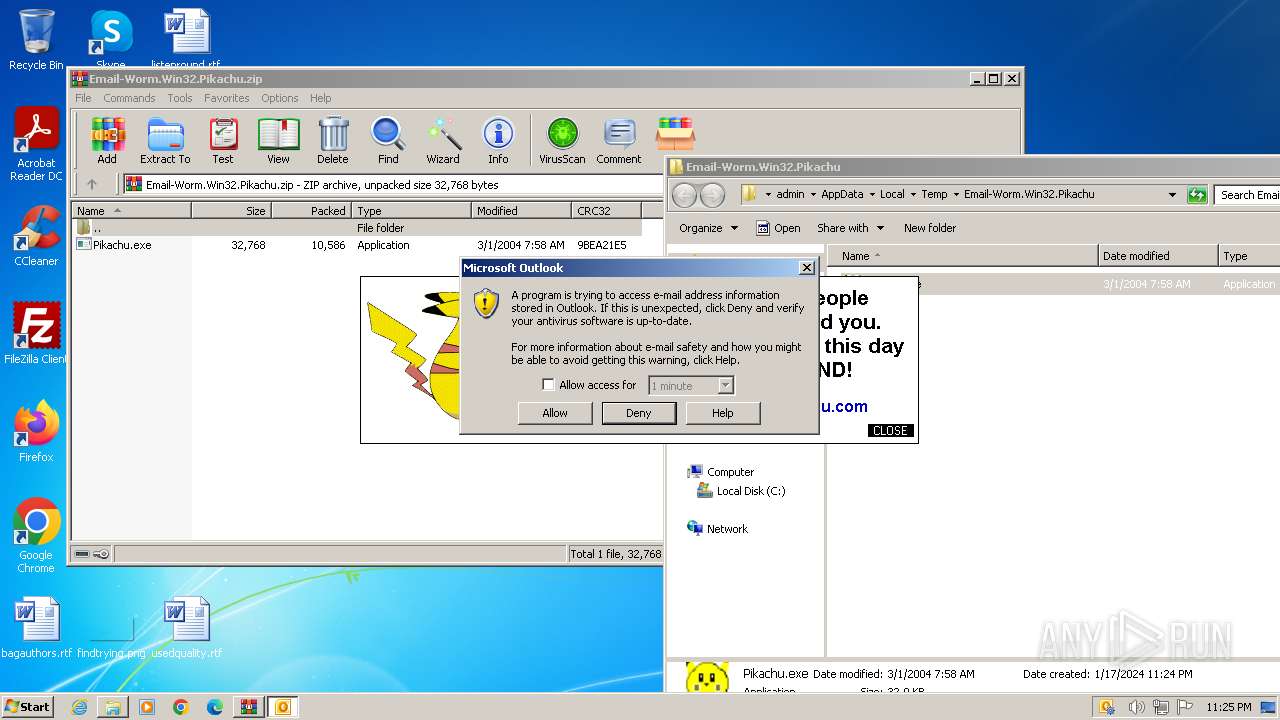
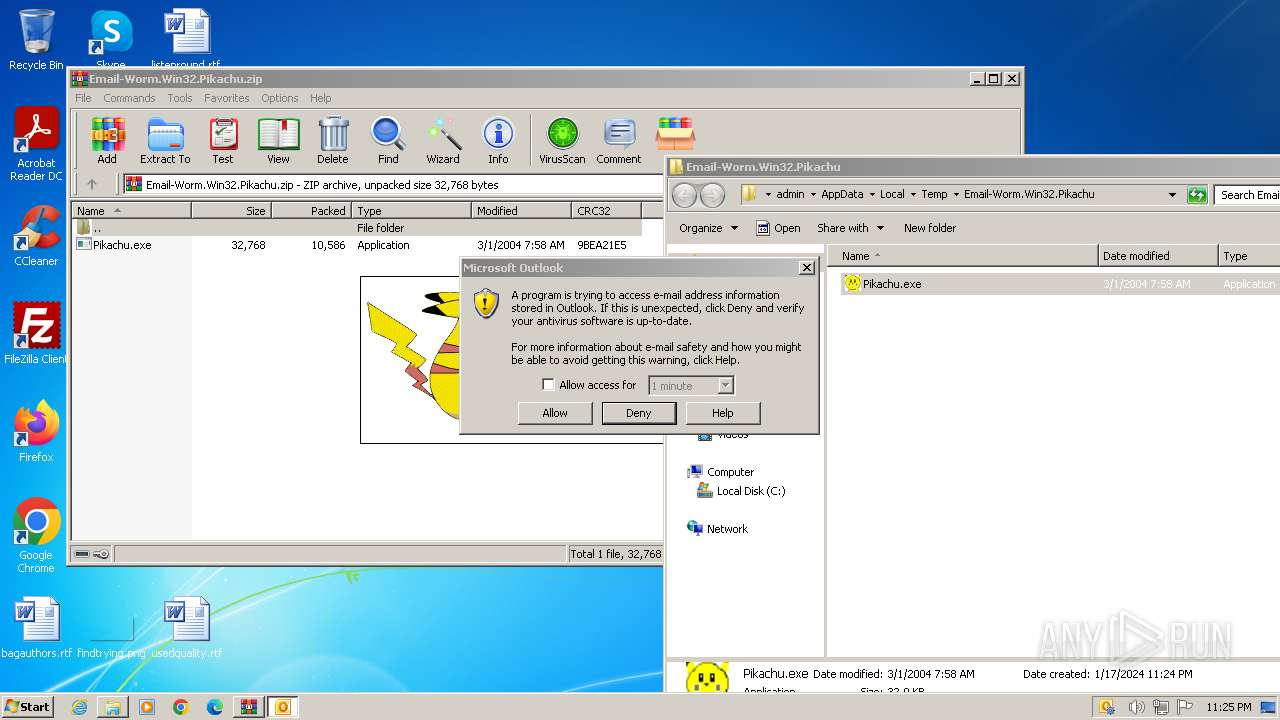
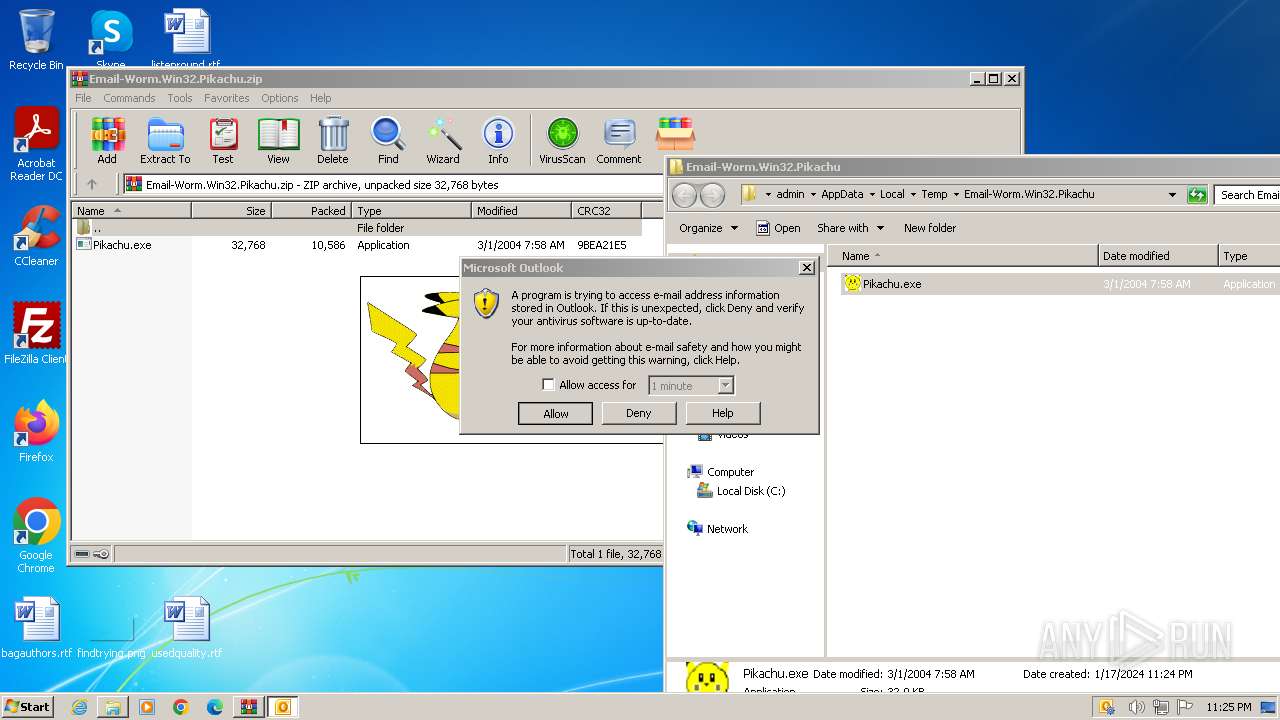
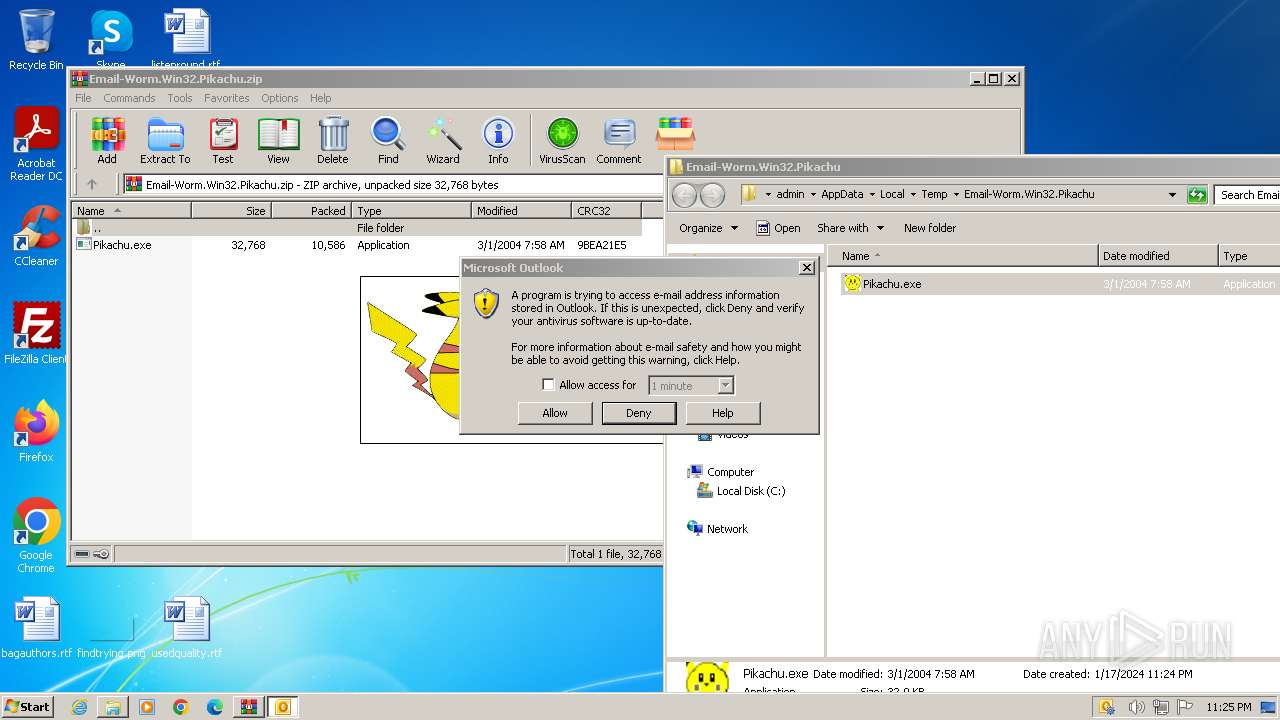
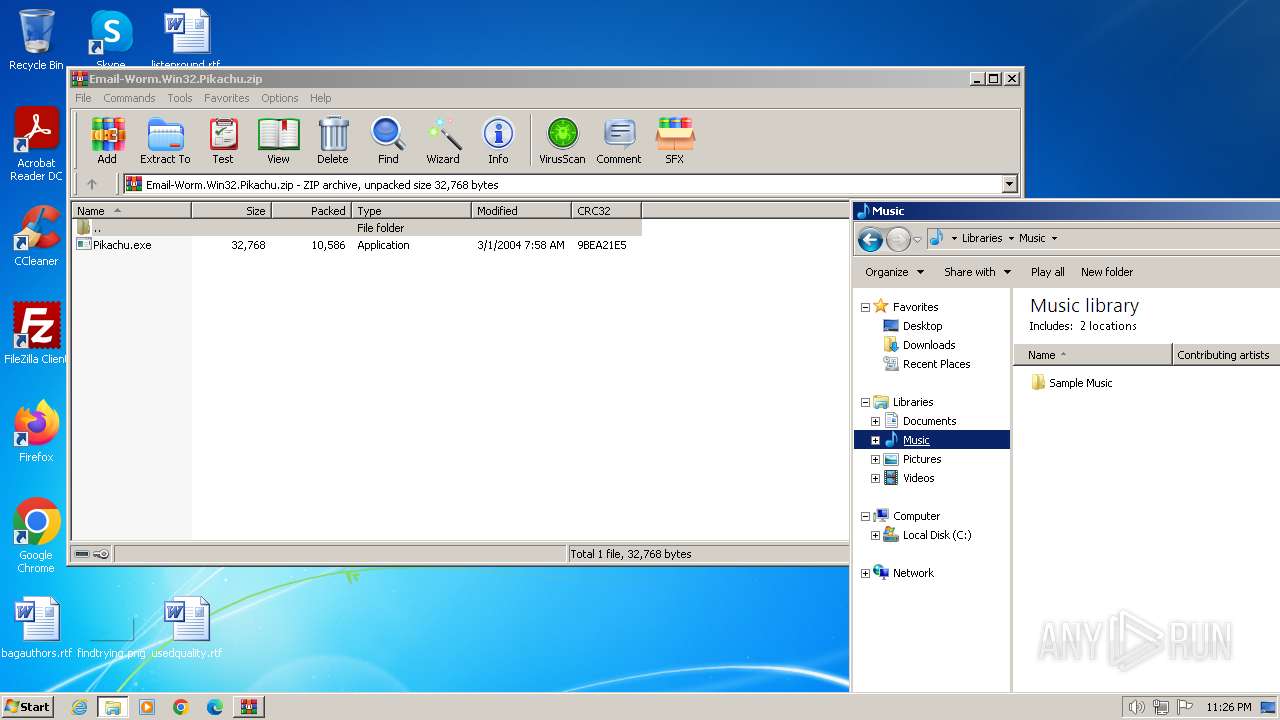
| File name: | Email-Worm.Win32.Pikachu.zip |
| Full analysis: | https://app.any.run/tasks/5d40daa2-42bb-45dd-af53-1eabe5ca95f7 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2024, 23:24:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 709A8C5AA653CDA197C578010A370DEB |
| SHA1: | 478D14969570F06BC61DD3832AE7E0C4ECC92F80 |
| SHA256: | ECDA6CE5DC46E2FF565E22F12F4CAE92D55919879308DF26AA33A0E282ECD740 |
| SSDEEP: | 192:SWAsDvTcYV8aHr6ky959IazImhpzjHdOZnV9tcdrvnCSm2kCr3t0Toa71KmC7EBj:xpV7HrLy1prjH0F2vnrkCx/m7VHog |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
SUSPICIOUS
No suspicious indicators.INFO
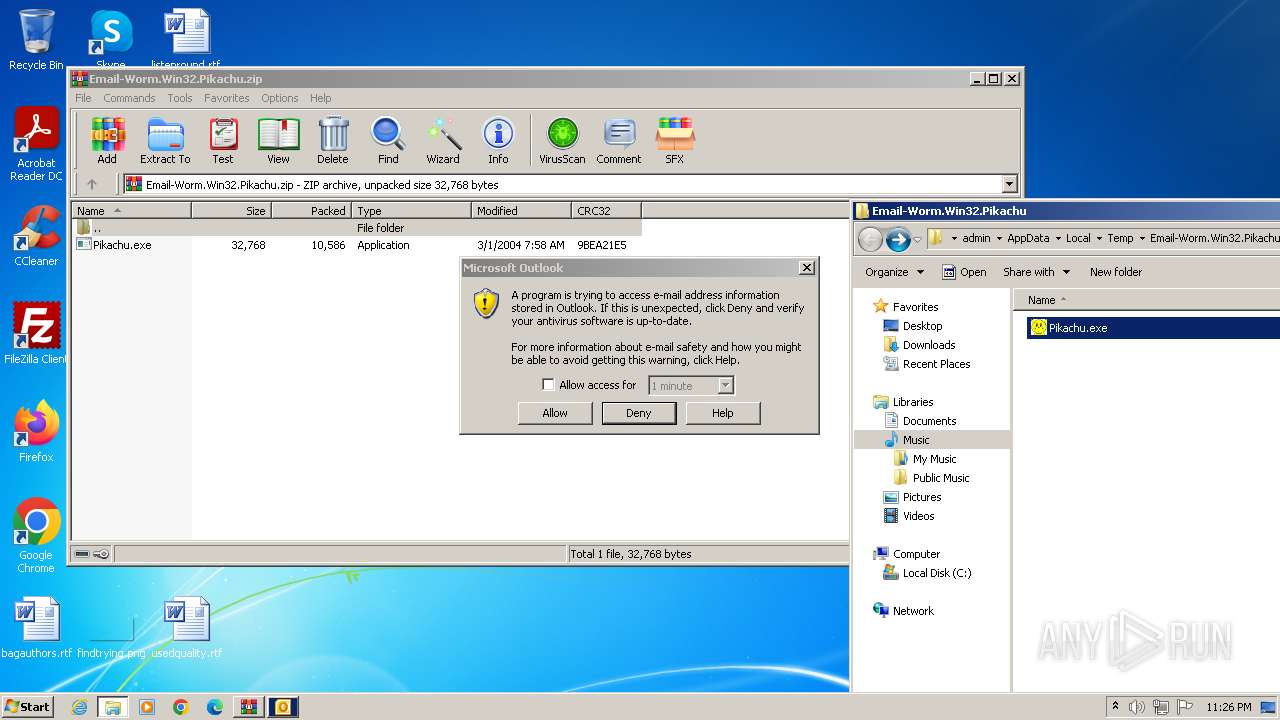
Manual execution by a user
- Pikachu.exe (PID: 2408)
- Pikachu.exe (PID: 1792)
- Pikachu.exe (PID: 2688)
- Pikachu.exe (PID: 2832)
- Pikachu.exe (PID: 880)
- Pikachu.exe (PID: 2648)
Checks supported languages
- Pikachu.exe (PID: 2408)
- Pikachu.exe (PID: 1792)
- Pikachu.exe (PID: 2688)
- Pikachu.exe (PID: 2832)
- Pikachu.exe (PID: 880)
- Pikachu.exe (PID: 2648)
Create files in a temporary directory
- Pikachu.exe (PID: 2408)
- Pikachu.exe (PID: 1792)
- Pikachu.exe (PID: 2688)
- Pikachu.exe (PID: 2832)
- Pikachu.exe (PID: 880)
- Pikachu.exe (PID: 2648)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2040)
Reads the machine GUID from the registry
- Pikachu.exe (PID: 2408)
- Pikachu.exe (PID: 1792)
- Pikachu.exe (PID: 2688)
- Pikachu.exe (PID: 2832)
- Pikachu.exe (PID: 880)
- Pikachu.exe (PID: 2648)
Reads the computer name
- Pikachu.exe (PID: 2408)
- Pikachu.exe (PID: 1792)
- Pikachu.exe (PID: 2688)
- Pikachu.exe (PID: 880)
- Pikachu.exe (PID: 2832)
- Pikachu.exe (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2004:03:01 02:58:38 |
| ZipCRC: | 0x9bea21e5 |
| ZipCompressedSize: | 10586 |
| ZipUncompressedSize: | 32768 |
| ZipFileName: | Pikachu.exe |
Total processes
53
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 880 | "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe" | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe" | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe" | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe" | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2688 | "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe" | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe" | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3144 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
5 999
Read events
5 822
Write events
152
Delete events
25
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
Executable files
1
Suspicious files
3
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6155.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 548 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2800 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRBBF4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVREF48.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2648 | Pikachu.exe | C:\AUTOEXEC.BAT | text | |
MD5:0F1916E9BBF740149210C5FFAA88158D | SHA256:B1D06274DB9B93FDF229E106A4B19B50676F94BEF0762DD0BC26B16F07050705 | |||
| 2800 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{23F4A9DA-7291-447C-B6CF-27ADAD1F0E20}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Email-Worm.Win32.Pikachu\Pikachu.exe | executable | |
MD5:715614E09261B39DFA439FA1326C0CEC | SHA256:E1DFC005D5403FB2F356276F0ABE19DF68249CE10E5035450926D56C2F8D3652 | |||
| 1792 | Pikachu.exe | C:\Users\admin\AppData\Local\Temp\~DFF6A6442815D0B3A3.TMP | binary | |
MD5:B854A181DE38D66CD995EC1E416D7926 | SHA256:66BAFD72B819C5447F0BAC58CB2E66BECB1C190C1038BB578790E02843B78BA7 | |||
| 548 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | binary | |
MD5:A3135C5D9DF1A57308806CB565FE3F74 | SHA256:97B0FBBB2AD193C6C9C0C4701C36587CCAD08826F31D81E21A2AB6D45164B470 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
548 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2800 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |