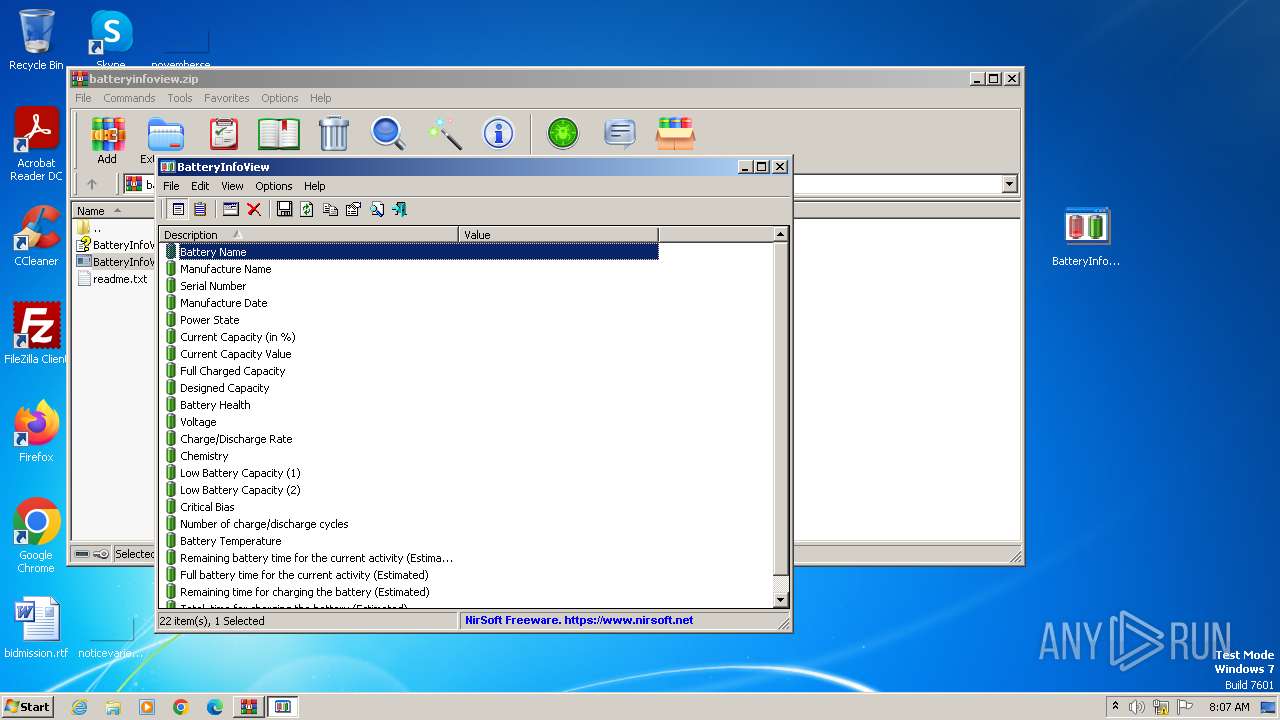
| File name: | batteryinfoview.zip |
| Full analysis: | https://app.any.run/tasks/5037715f-228a-4110-9e89-c9651342f75d |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2024, 07:06:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D7F4BBBF5E82FB320E7B4075400C79F6 |
| SHA1: | 418D5E6C8E15BCF123457ECECB7646B7C24D4CFC |
| SHA256: | ECBF6ECB79D19C821F04C39F5C622ED85C38F5A6DEEEDC442366F175A2D016E1 |
| SSDEEP: | 3072:1AhqJLP7jpi2WTBnuXA/YylXP/LkNDBvGFjQyyPX5W:1AhyDpMTBF/nVPTkNRGF/yPXk |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3968)
SUSPICIOUS
Reads the Internet Settings
- hh.exe (PID: 2108)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2108)
Reads Internet Explorer settings
- hh.exe (PID: 2108)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Manual execution by a user
- BatteryInfoView.exe (PID: 4060)
- hh.exe (PID: 2108)
- notepad.exe (PID: 1756)
Checks supported languages
- BatteryInfoView.exe (PID: 4060)
NirSoft software is detected
- BatteryInfoView.exe (PID: 4060)
Reads the computer name
- BatteryInfoView.exe (PID: 4060)
Create files in a temporary directory
- hh.exe (PID: 2108)
Reads the machine GUID from the registry
- hh.exe (PID: 2108)
Reads security settings of Internet Explorer
- hh.exe (PID: 2108)
Checks proxy server information
- hh.exe (PID: 2108)
Creates files or folders in the user directory
- hh.exe (PID: 2108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:10:25 13:41:12 |
| ZipCRC: | 0xf2760812 |
| ZipCompressedSize: | 39074 |
| ZipUncompressedSize: | 79872 |
| ZipFileName: | BatteryInfoView.exe |
Total processes
38
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\readme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2108 | "C:\Windows\hh.exe" C:\Users\admin\Desktop\BatteryInfoView.chm | C:\Windows\hh.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\batteryinfoview.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4060 | "C:\Users\admin\Desktop\BatteryInfoView.exe" | C:\Users\admin\Desktop\BatteryInfoView.exe | — | explorer.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: BatteryInfoView Version: 1.25 Modules
| |||||||||||||||
Total events
4 787
Read events
4 760
Write events
25
Delete events
2
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\batteryinfoview.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3968.43837\BatteryInfoView.exe | executable | |
MD5:BE1B0C0CCE1C61495E49B063F92D9D82 | SHA256:8DFFB52B6826067ED8B56F549CBE53F4F5908E21582A54A9172ECFBAD90AFE37 | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Local\Temp\IMTEA3.tmp | binary | |
MD5:5D0E5693027A0E5ADF1D49847779B65C | SHA256:AC0710AABAAEAAC65507050647FA9D97A82639DA0D1D6B436800B177478C6D6B | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Roaming\Microsoft\HTML Help\hh.dat | binary | |
MD5:D30E324049EF6B7C891359F0E53B7475 | SHA256:124D5CE972A6FE1B31C5CD91D2174DA5DB78B6B4723741536D0AA52BE2EAC6D4 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3968.47158\BatteryInfoView.chm | chm | |
MD5:BEA19BDCEA03095069B3EF115492E44C | SHA256:89D04B42ED29910629185BC6D5B6919C23B217C6BC7A004209BDD93FBAFD93CE | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\main[1].css | text | |
MD5:7B11CD3A728D510B0BD92AD7E49F94FB | SHA256:B3C3AA3425B6601BB8AED17AB9894658D44B381F132A9F3562342EA534BE0BFA | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\batteryinfoview_icon[1].gif | image | |
MD5:0DA587D965985A9F60D57078674170CF | SHA256:4CC0C1D6F3C425CC7427190F22F8899B87E9DA5673D9916A3F596C3167A2167C | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\batteryinfoview[1].gif | image | |
MD5:B01189B32108EFEE5A25D61AF759F1E0 | SHA256:967D25EF6725A88E1988C4BD326CB25D50179487897B6E5AAC375523F1E07417 | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Local\Temp\~DFFAE0605F3DD6A945.TMP | binary | |
MD5:72F5C05B7EA8DD6059BF59F50B22DF33 | SHA256:1DC0C8D7304C177AD0E74D3D2F1002EB773F4B180685A7DF6BBE75CCC24B0164 | |||
| 2108 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\batterylogview[1].gif | image | |
MD5:5CB398D1472F5BD26D47647157934C7A | SHA256:34395619352E44FEB11299D82B6BC82202BEA02E630AF5B586ED6004A7EEF2AD | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3968.47790\readme.txt | text | |
MD5:AF3E401A23B0B5E39E2FF414DC645AAF | SHA256:2639AFCC3B94715EAD28D51CFEDA2F30F5FFFDD4495B68E951880F8E5D87F16B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |