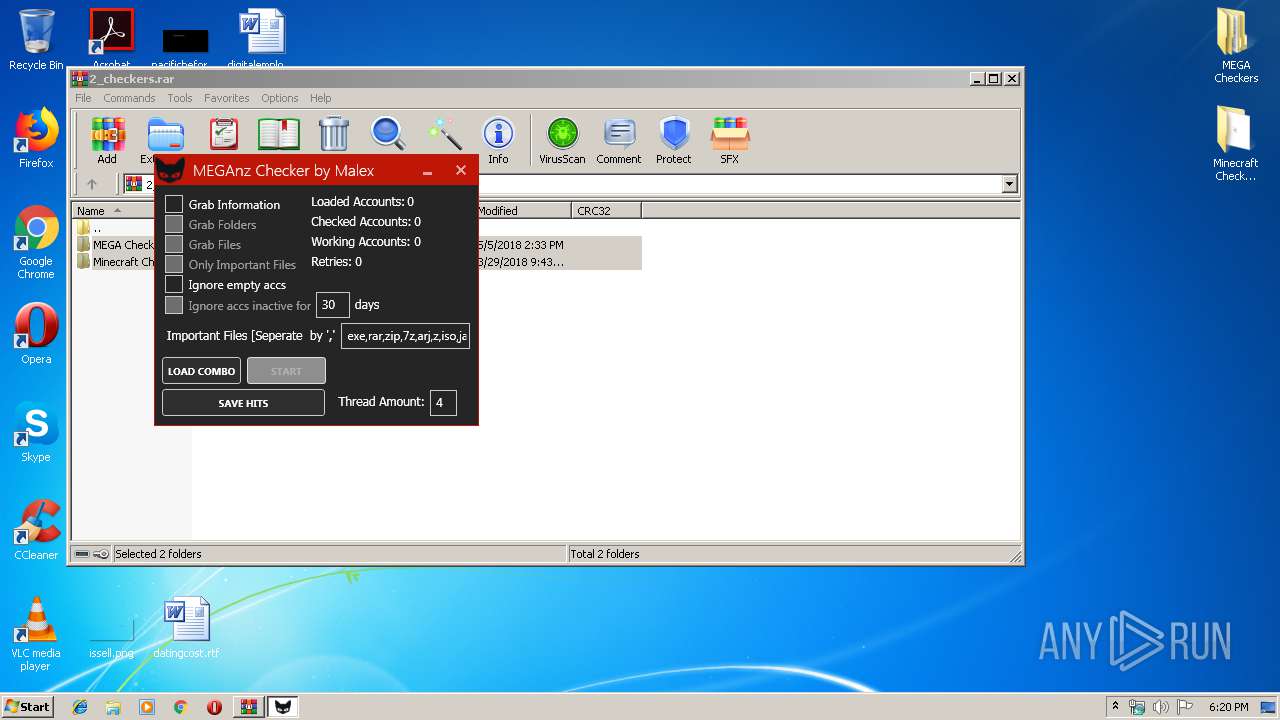
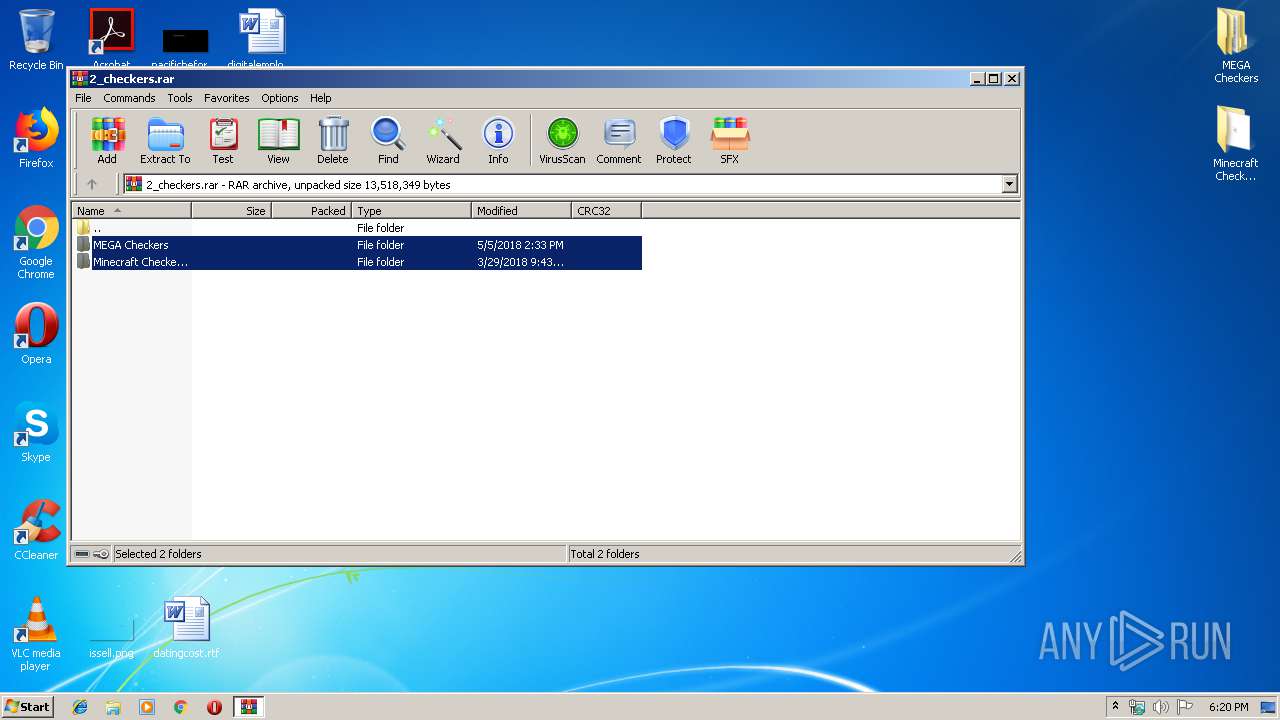
| File name: | 2_checkers.rar |
| Full analysis: | https://app.any.run/tasks/2456ea09-6195-4f5e-b169-cef7a04febef |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2019, 17:19:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F400C2259E57262A657BDF3D16EEA1D1 |
| SHA1: | 3EB5DA62E8E0898A02EFCBC94B3E9B9BE8C34A3E |
| SHA256: | ECABF450BF9EFA8F20108666D96B5B3D4F1B8AFD516702191CCD3894DFFCBA09 |
| SSDEEP: | 196608:sJj3zIZyT83rDvHIDQnwa43ZoiOPu+Jhx3kZcx/DuQpW7rNEPtH:E9T83fQDha8bOPughx3lru4mNc |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 752)
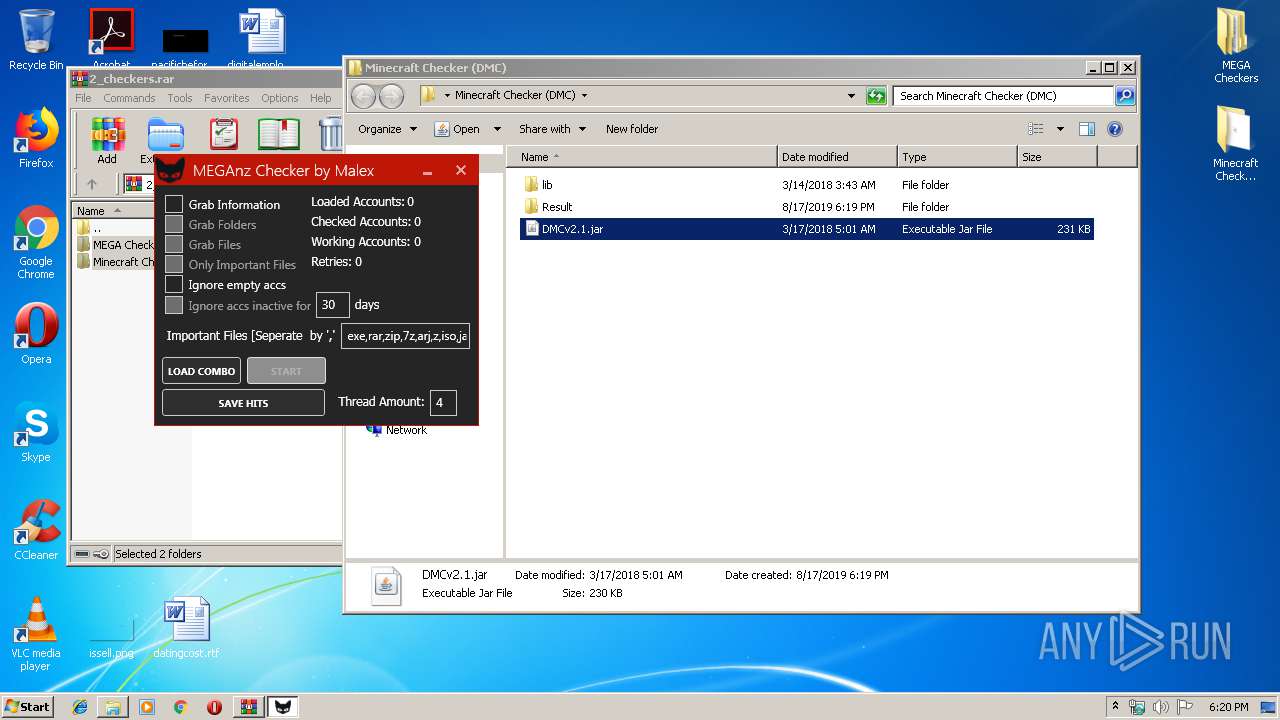
- MEGAnz Cracker by Malex.exe (PID: 2536)
Application was dropped or rewritten from another process
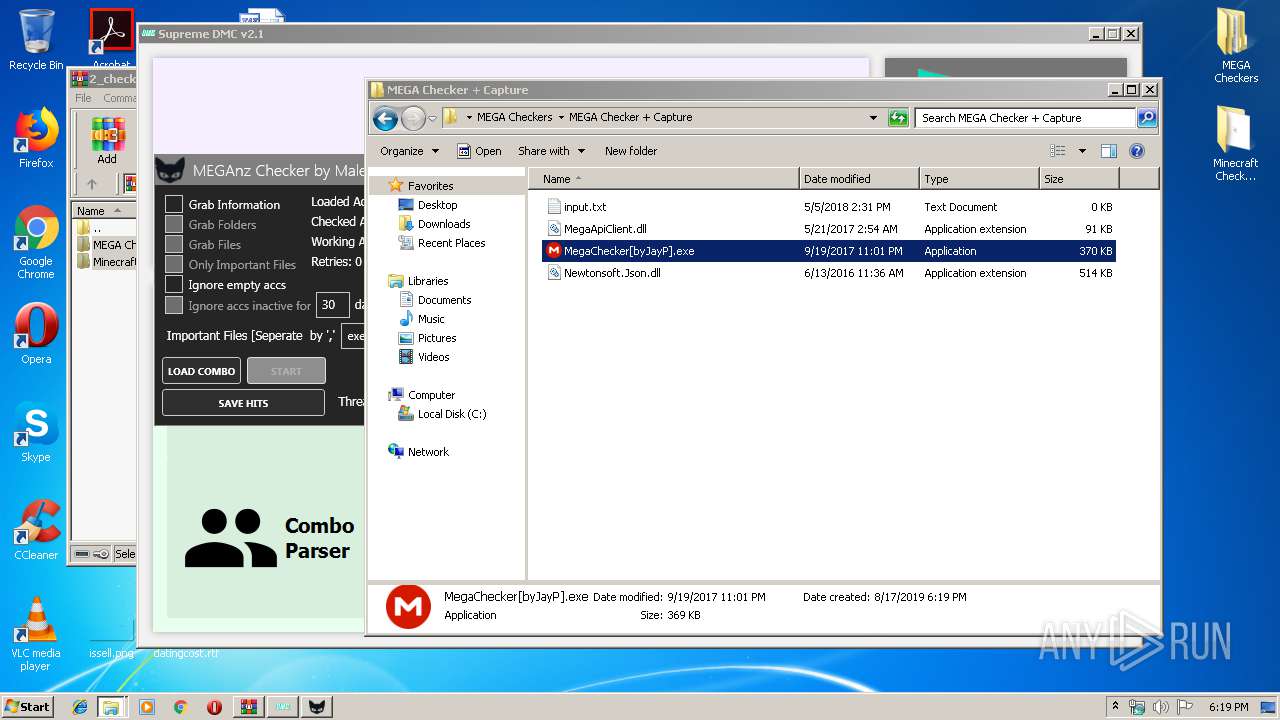
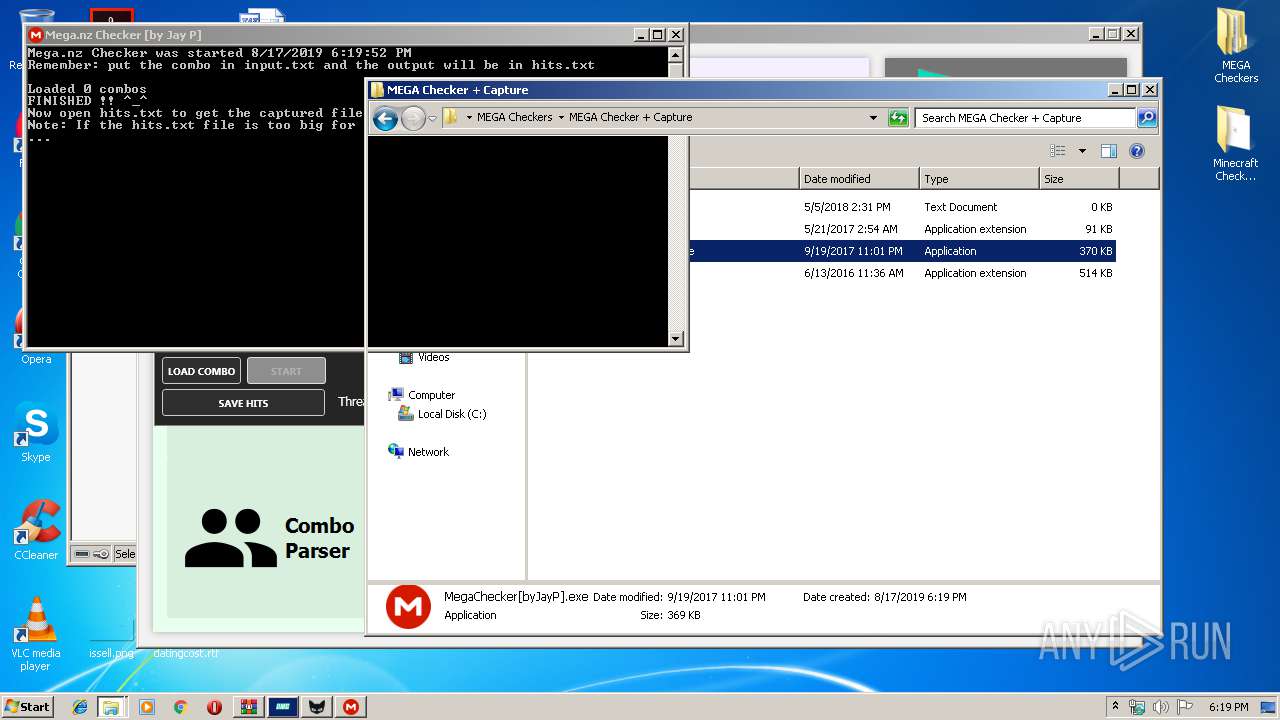
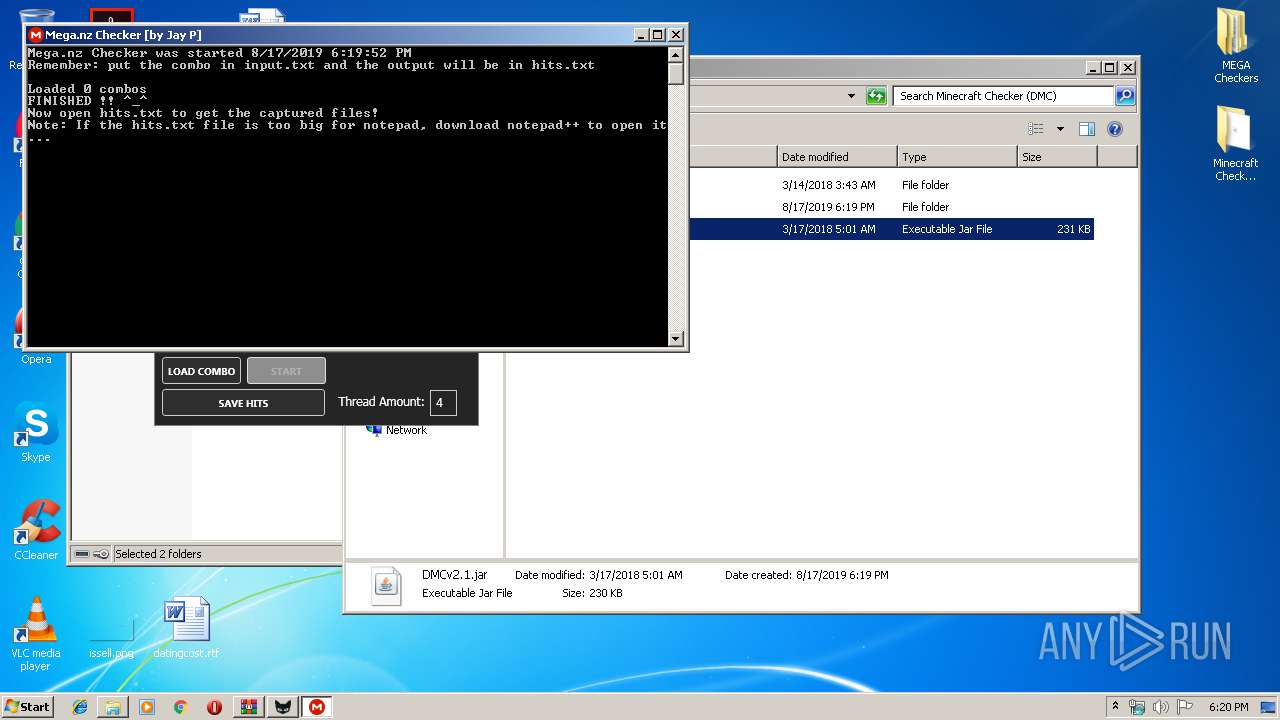
- MegaChecker[byJayP].exe (PID: 3056)
- MEGAnz Cracker by Malex.exe (PID: 2536)
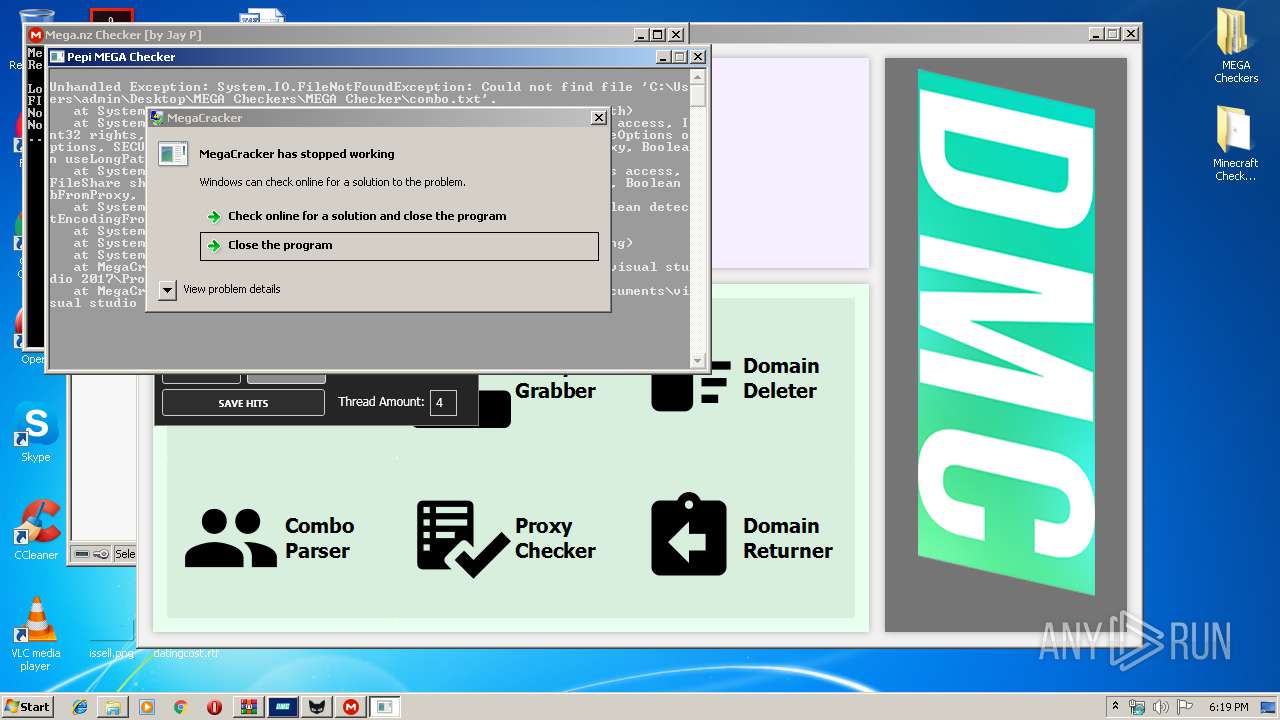
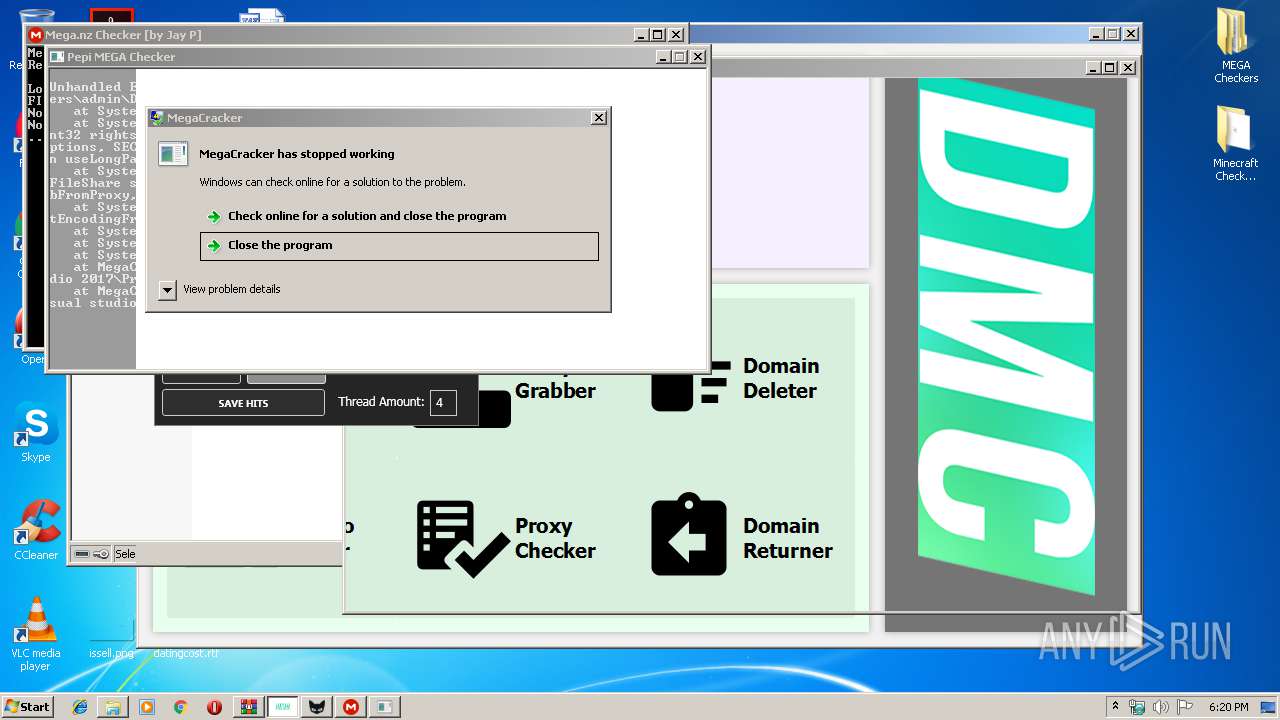
- MegaCracker.exe (PID: 3060)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3768)
Creates files in the user directory
- javaw.exe (PID: 3036)
INFO
Manual execution by user
- MEGAnz Cracker by Malex.exe (PID: 2536)
- javaw.exe (PID: 3036)
- MegaChecker[byJayP].exe (PID: 3056)
- MegaCracker.exe (PID: 3060)
Application was crashed
- MegaCracker.exe (PID: 3060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
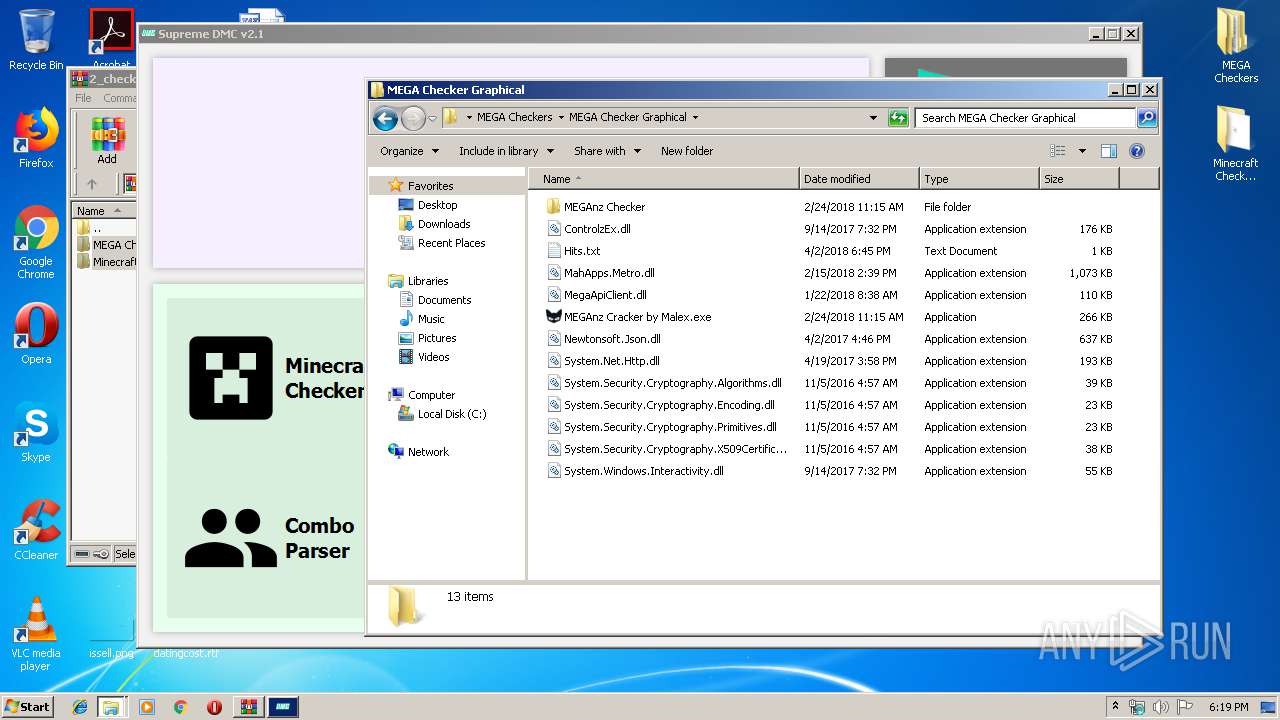
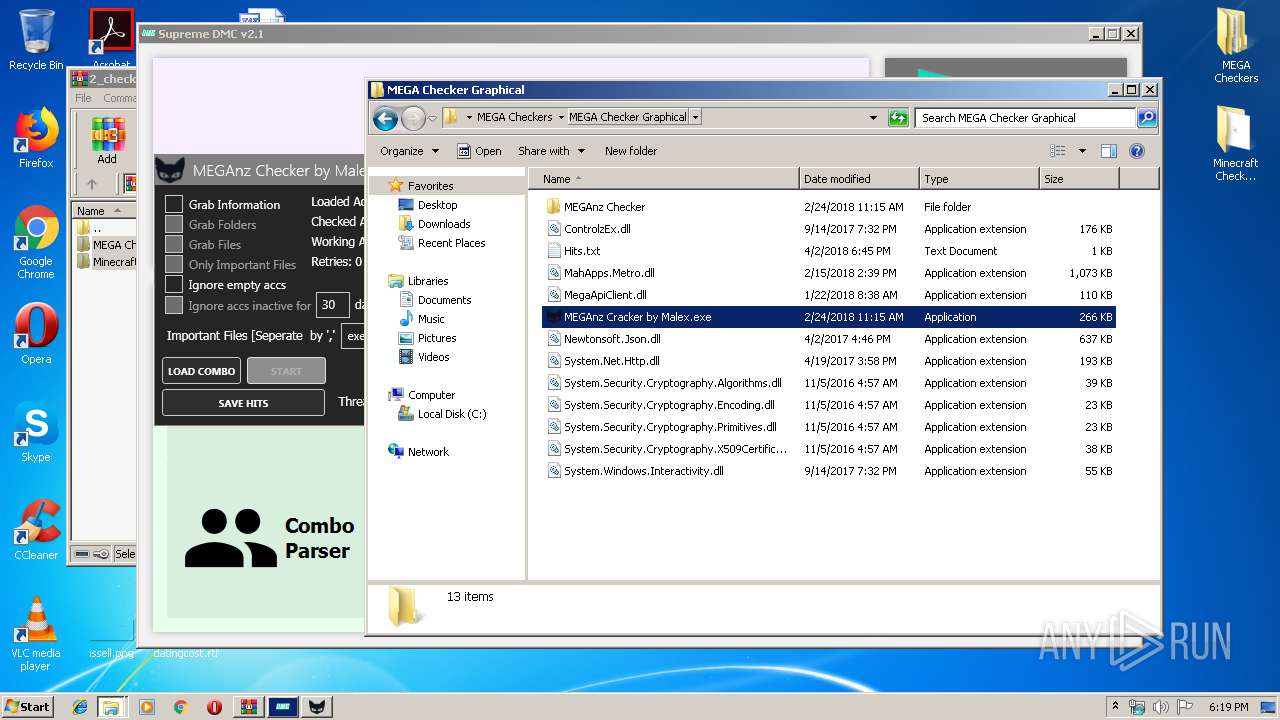
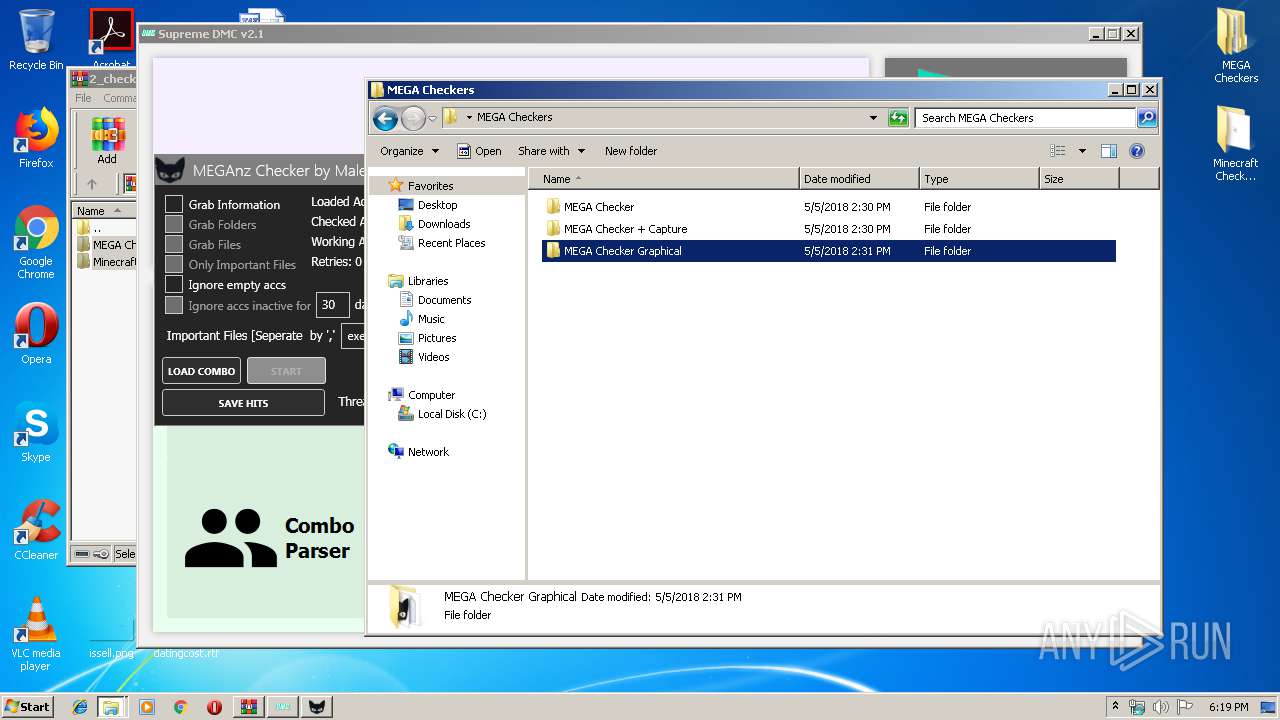
| 2536 | "C:\Users\admin\Desktop\MEGA Checkers\MEGA Checker Graphical\MEGAnz Cracker by Malex.exe" | C:\Users\admin\Desktop\MEGA Checkers\MEGA Checker Graphical\MEGAnz Cracker by Malex.exe | explorer.exe | ||||||||||||
User: admin Company: Malex Integrity Level: MEDIUM Description: MEGACracker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3036 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Minecraft Checker (DMC)\DMCv2.1.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3056 | "C:\Users\admin\Desktop\MEGA Checkers\MEGA Checker + Capture\MegaChecker[byJayP].exe" | C:\Users\admin\Desktop\MEGA Checkers\MEGA Checker + Capture\MegaChecker[byJayP].exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: MegaCrack Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\Desktop\MEGA Checkers\MEGA Checker\MegaCracker.exe" | C:\Users\admin\Desktop\MEGA Checkers\MEGA Checker\MegaCracker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: MegaCracker Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3768 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\2_checkers.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
833
Read events
802
Write events
31
Delete events
0
Modification events
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\2_checkers.rar | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (752) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (752) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msxml3r.dll,-1 |
Value: XML Document | |||
Executable files
19
Suspicious files
13
Text files
9
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\fontawesomefx-materialdesignfont-1.7.22-4.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\fontawesomefx-fontawesome-4.7.0-5.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\fontawesomefx-weathericons-2.0.10-5.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\fontawesomefx-materialstackicons-2.1-5.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\fontawesomefx-materialicons-2.2.0-5.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\jfoenix-1.9.0.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\DMCv2.1.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\Minecraft Checker (DMC)\lib\fontawesomefx-octicons-4.3.0-5.jar | compressed | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\MEGA Checkers\MEGA Checker\HOW TO USE.txt | text | |
MD5:— | SHA256:— | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.38123\MEGA Checkers\MEGA Checker\MegaCracker.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3036 | javaw.exe | 104.25.74.29:443 | ru.namemc.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ru.namemc.com |
| malicious |
Threats
Process | Message |
|---|---|
MEGAnz Cracker by Malex.exe | MahApps.Metro.Behaviours.WindowsSettingBehaviour: Clean up from AssociatedObject closed event.
|
MEGAnz Cracker by Malex.exe | MahApps.Metro.Behaviours.WindowsSettingBehaviour: Clean up from AssociatedObject closed event.
|