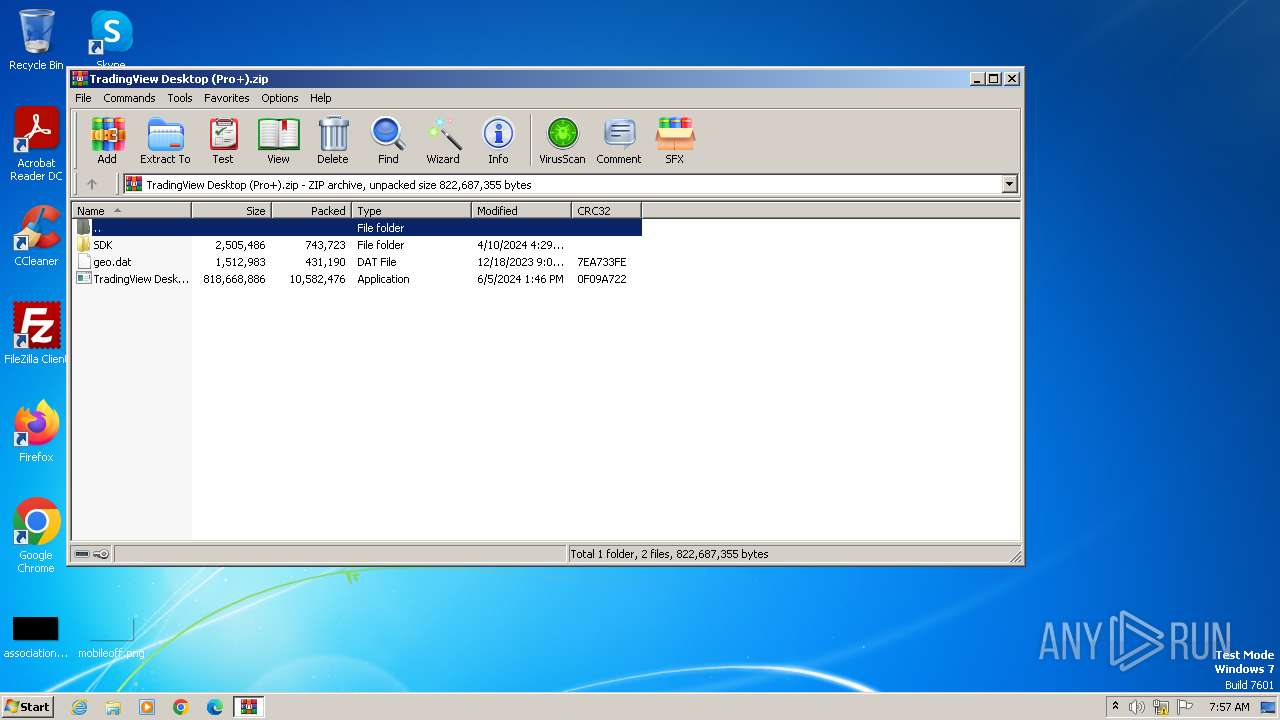
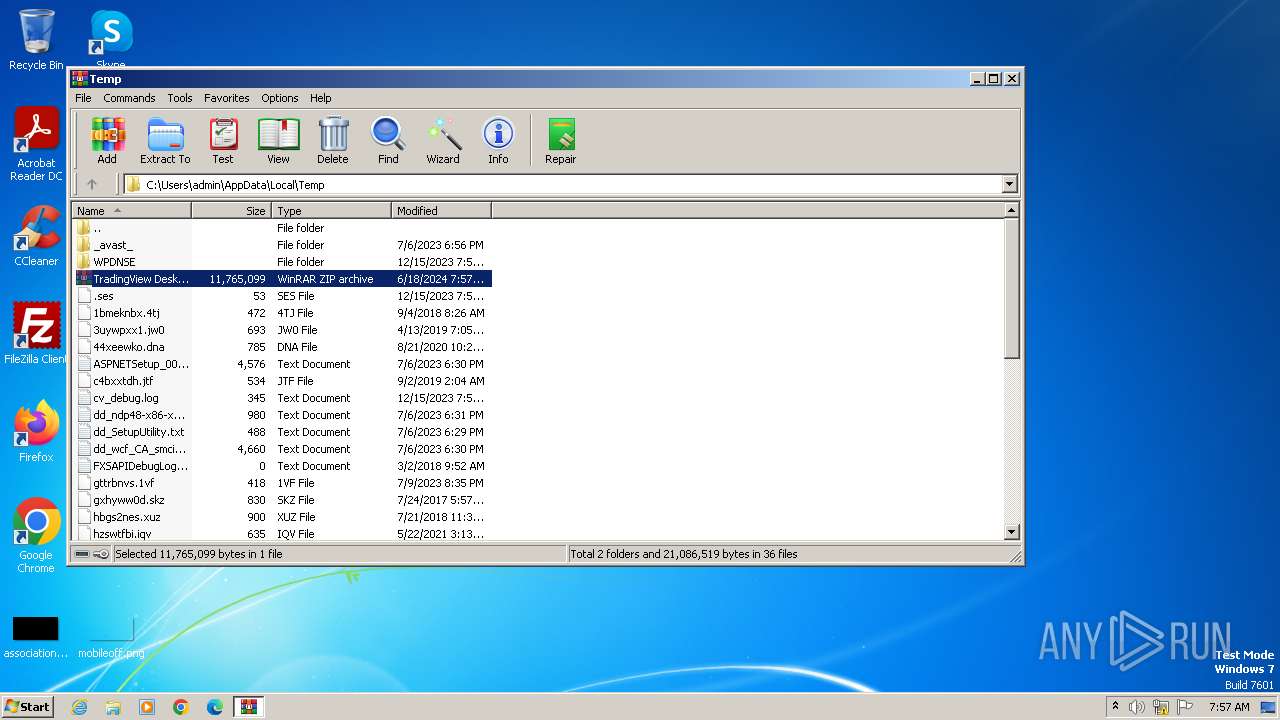
| File name: | TradingView Desktop (Pro+).zip |
| Full analysis: | https://app.any.run/tasks/691afb07-b171-4774-8bcb-0d3810c5a499 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2024, 06:57:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 98F307821BF3FA62F416299785DFEB34 |
| SHA1: | B7BAFC393A7E3D3A2038881833A53BB804E58944 |
| SHA256: | ECA62135DA01C30871FF5F804E3C5AF01AFEF2849C8FA6A45FE81351645780B6 |
| SSDEEP: | 98304:Rhkai+J965iqYD1VweHM9pqMJScQeLwVmJjOPgFe2LJz4OrwuxuwSCwTs7vmn+zg:VY+f9tUa974iK7TJgQ7xA |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3984)
VIDAR has been detected (YARA)
- TradingView Desktop (Pro+).exe (PID: 864)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3984)
Reads the Internet Settings
- TradingView Desktop (Pro+).exe (PID: 864)
Reads security settings of Internet Explorer
- TradingView Desktop (Pro+).exe (PID: 864)
Reads settings of System Certificates
- TradingView Desktop (Pro+).exe (PID: 864)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- TradingView Desktop (Pro+).exe (PID: 864)
Checks Windows Trust Settings
- TradingView Desktop (Pro+).exe (PID: 864)
INFO
Checks supported languages
- TradingView Desktop (Pro+).exe (PID: 864)
- wmpnscfg.exe (PID: 2204)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3984)
Manual execution by a user
- TradingView Desktop (Pro+).exe (PID: 864)
- wmpnscfg.exe (PID: 2204)
Reads the computer name
- TradingView Desktop (Pro+).exe (PID: 864)
- wmpnscfg.exe (PID: 2204)
Creates files in the program directory
- TradingView Desktop (Pro+).exe (PID: 864)
Checks proxy server information
- TradingView Desktop (Pro+).exe (PID: 864)
Reads the machine GUID from the registry
- TradingView Desktop (Pro+).exe (PID: 864)
Reads the software policy settings
- TradingView Desktop (Pro+).exe (PID: 864)
Creates files or folders in the user directory
- TradingView Desktop (Pro+).exe (PID: 864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:10 18:29:28 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SDK/ |
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Users\admin\Desktop\TradingView Desktop (Pro+).exe" | C:\Users\admin\Desktop\TradingView Desktop (Pro+).exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Shell Extension Version: 24.01 Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TradingView Desktop (Pro+).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 651
Read events
7 581
Write events
64
Delete events
6
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TradingView Desktop (Pro+).zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
22
Suspicious files
1
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.Dmf.Adapters.dll | executable | |
MD5:C022FD9C28C1C415F4BD504FDA03D6CC | SHA256:58089B6EF0821CEAEB84ADF2FA8F77A90E418AAFBD0A6EE3D28A8CD6F8A2D74B | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.ConnectionInfo.dll | executable | |
MD5:72B11C28883297CAAFE65E7812266375 | SHA256:D8A81E198A721AD8BAAAB4E4F90103A8407965454CA4FF46C966E9B0D948526D | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.ConnectionInfoExtended.dll | executable | |
MD5:2AF76F89FB11CD819F2FB2B7247A6898 | SHA256:6E034250B84721DD48CF90EB8B62DABC2A341A340EF7B7061CB4F5050A563628 | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\100\KeyFile\1049\sqlsysclrtypes_keyfile.dll | executable | |
MD5:166A4EB063FBFF4D85B7647B9B3819B0 | SHA256:C51A51D4E3734765D1352DBF09511E49A2773B3D6BD9A704EE664FB8E3059E42 | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.Management.Collector.dll | executable | |
MD5:580448288C249572EEFC0C18F9F85EBE | SHA256:9D237665F3F1D3D0B185EC263E35D576A6FF48EEC8274DE24BB5432032C7EBEF | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.Management.Utility.dll | executable | |
MD5:8364112DD878E1431BA9EC985CC29930 | SHA256:BEA7F1DAF7BE52B25EECC290F7C493B1D6DBC105D47AC8A688B048E9C8ED3876 | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.Management.UtilityEnum.dll | executable | |
MD5:85730AF402FF84288706EDB626E726FA | SHA256:96A9D99D31C5190E3880A7E9D6961CD4996CC76D5A3D560D1FB9C558228FC807 | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.Management.CollectorEnum.dll | executable | |
MD5:C6E10BBBC19A9EDD691882550E2AEF38 | SHA256:8C6A8728609F3CD7C94F08D291593F59234A1019E930B74B2085DC849FFF143B | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.RegSvrEnum.dll | executable | |
MD5:67373CC732008E4994D7CFA9394CB0E0 | SHA256:84AA625CE6E72EDC3A6C59630117EF35EF4951F53F828A96026DBA10B653E1FA | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\SDK\Assemblies\Microsoft.SqlServer.Management.XEvent.dll | executable | |
MD5:9B7A765CE1BDEBB515690E72991488A7 | SHA256:6D5FE7BA1077E37EC47E87B82D68BD49CC614FAEF72AB36D31B322E5B2BBE9BB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
864 | TradingView Desktop (Pro+).exe | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | unknown |
864 | TradingView Desktop (Pro+).exe | 104.95.184.164:443 | steamcommunity.com | AKAMAI-AS | DK | unknown |
864 | TradingView Desktop (Pro+).exe | 95.217.135.112:443 | — | Hetzner Online GmbH | FI | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t.me |
| whitelisted |
steamcommunity.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
864 | TradingView Desktop (Pro+).exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
1 ETPRO signatures available at the full report