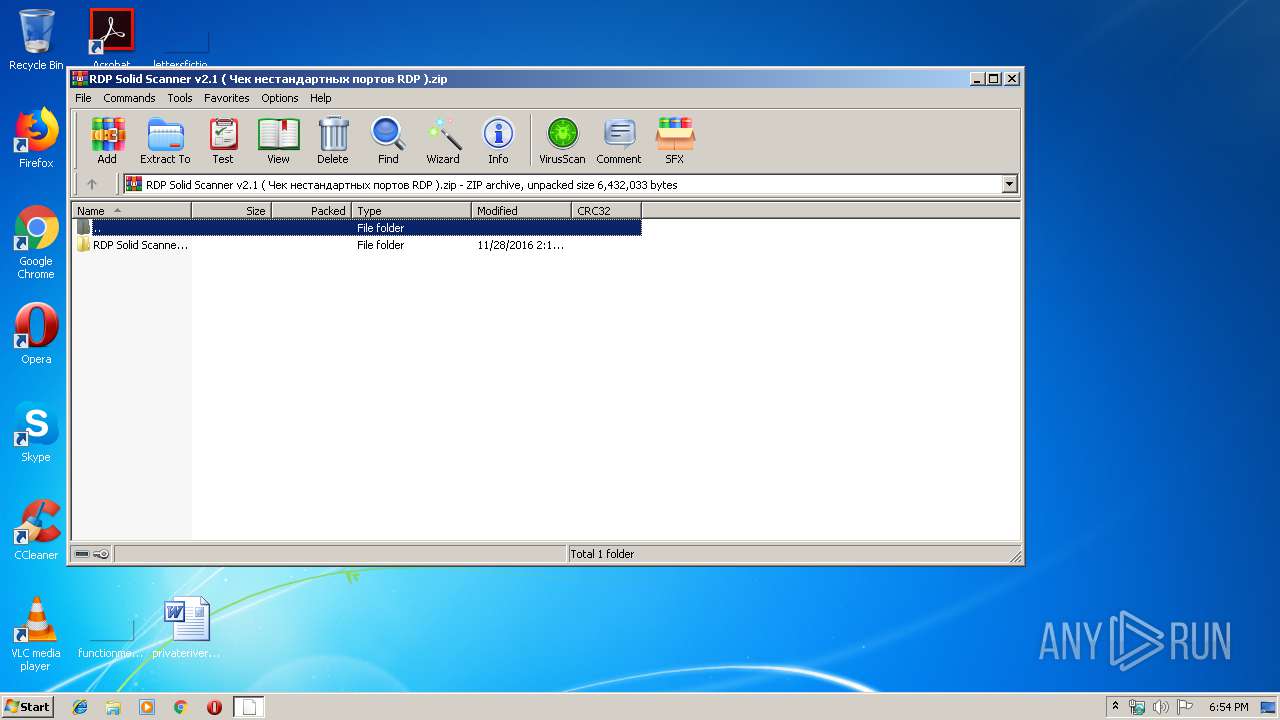
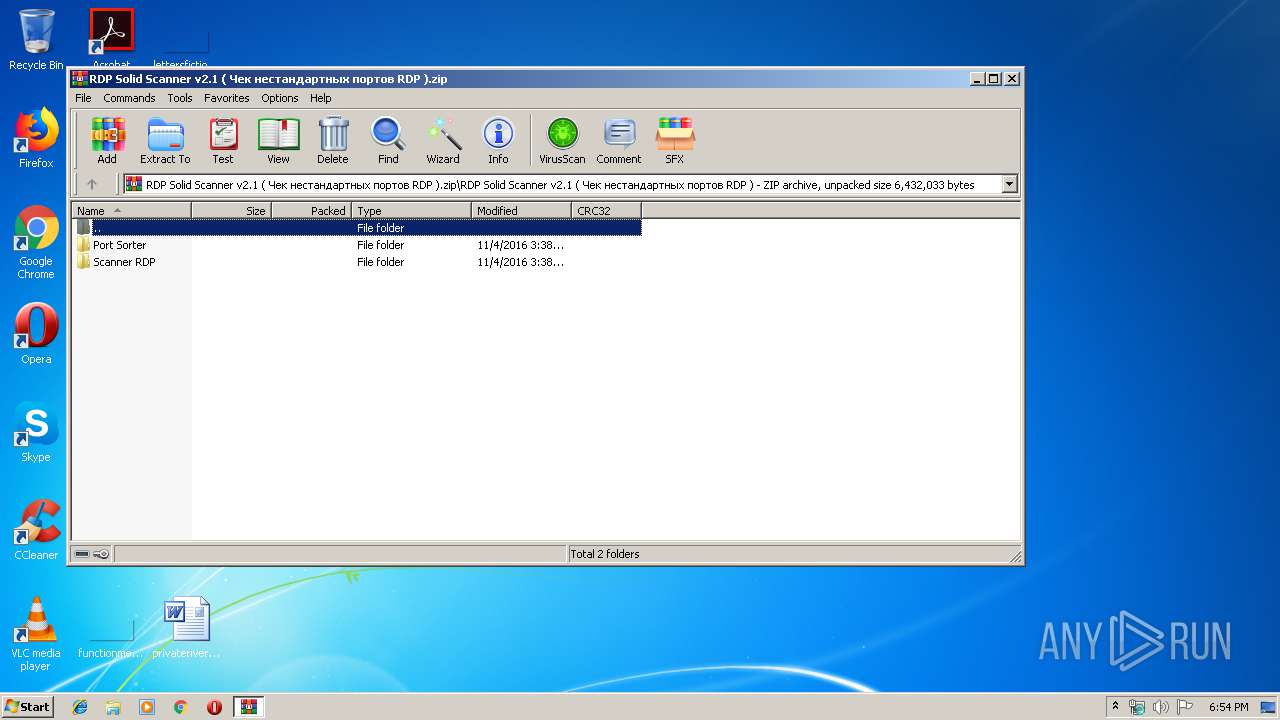
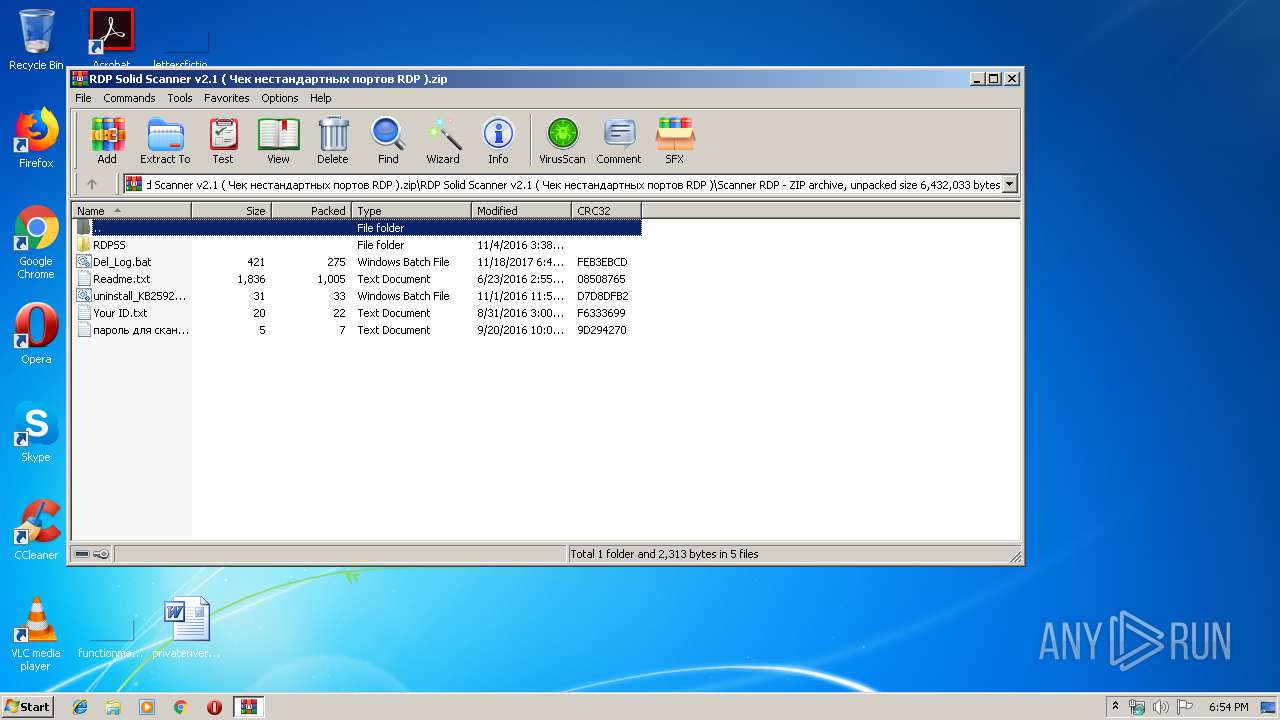
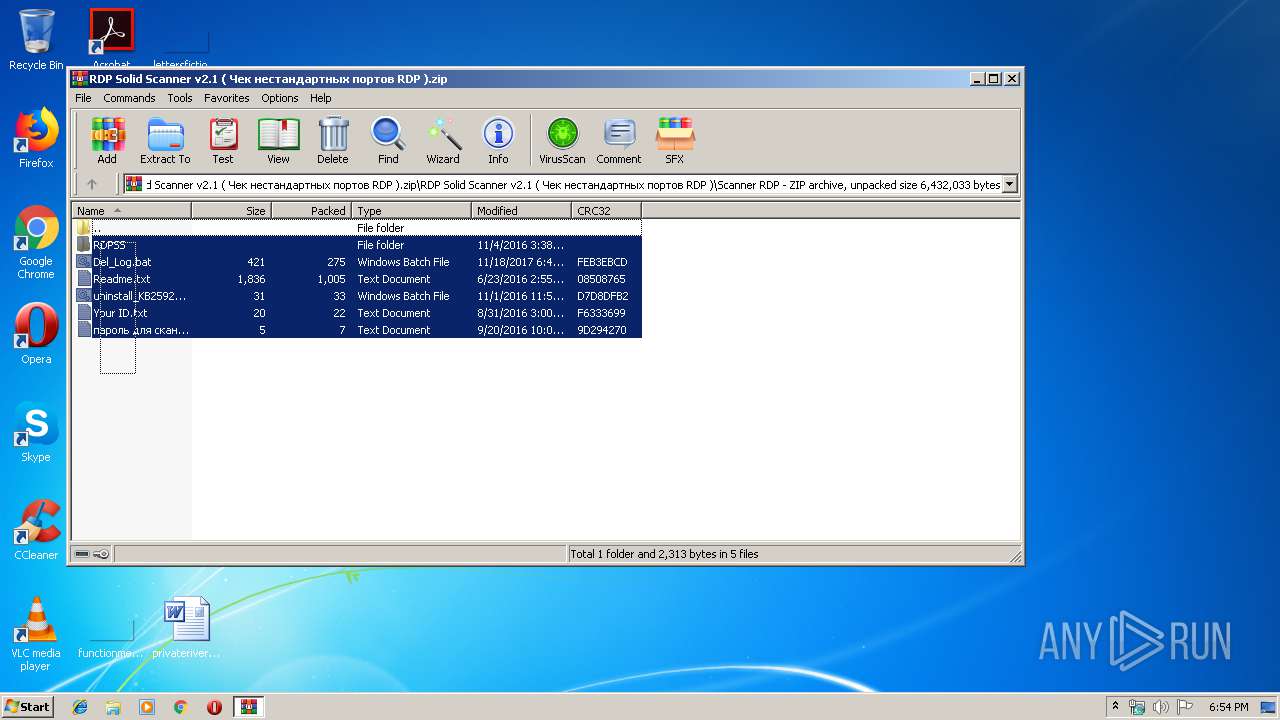
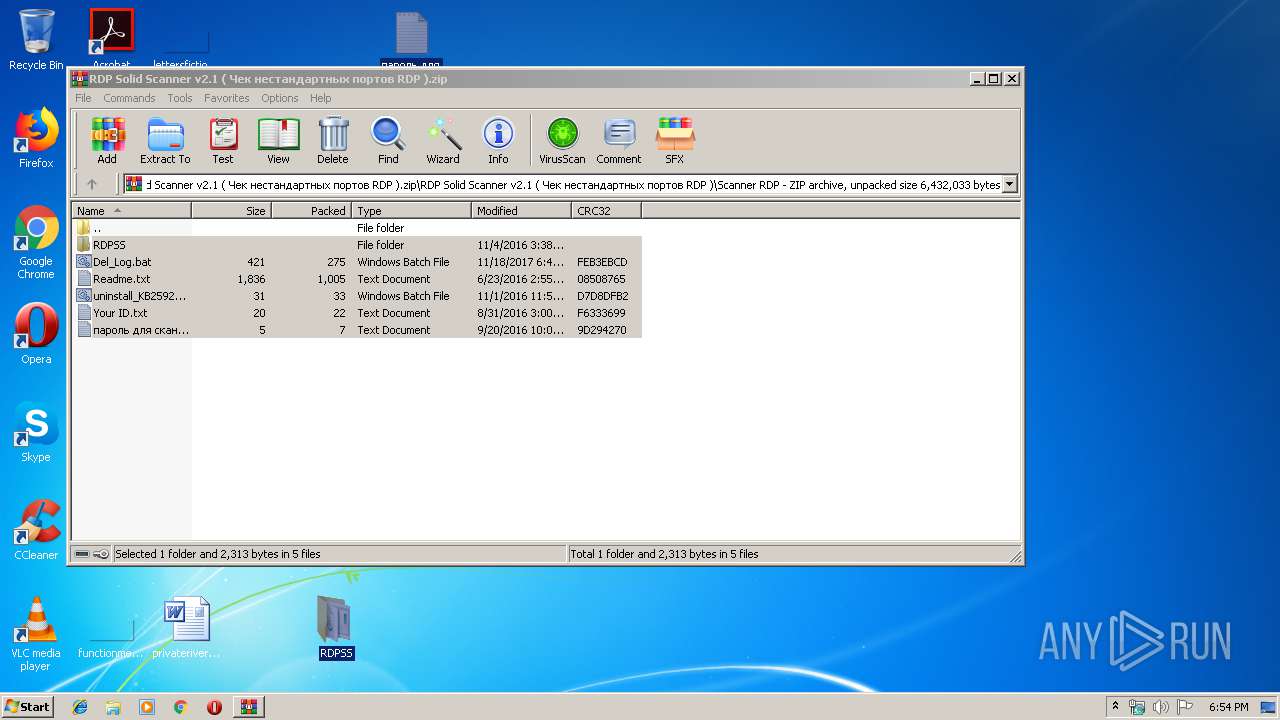
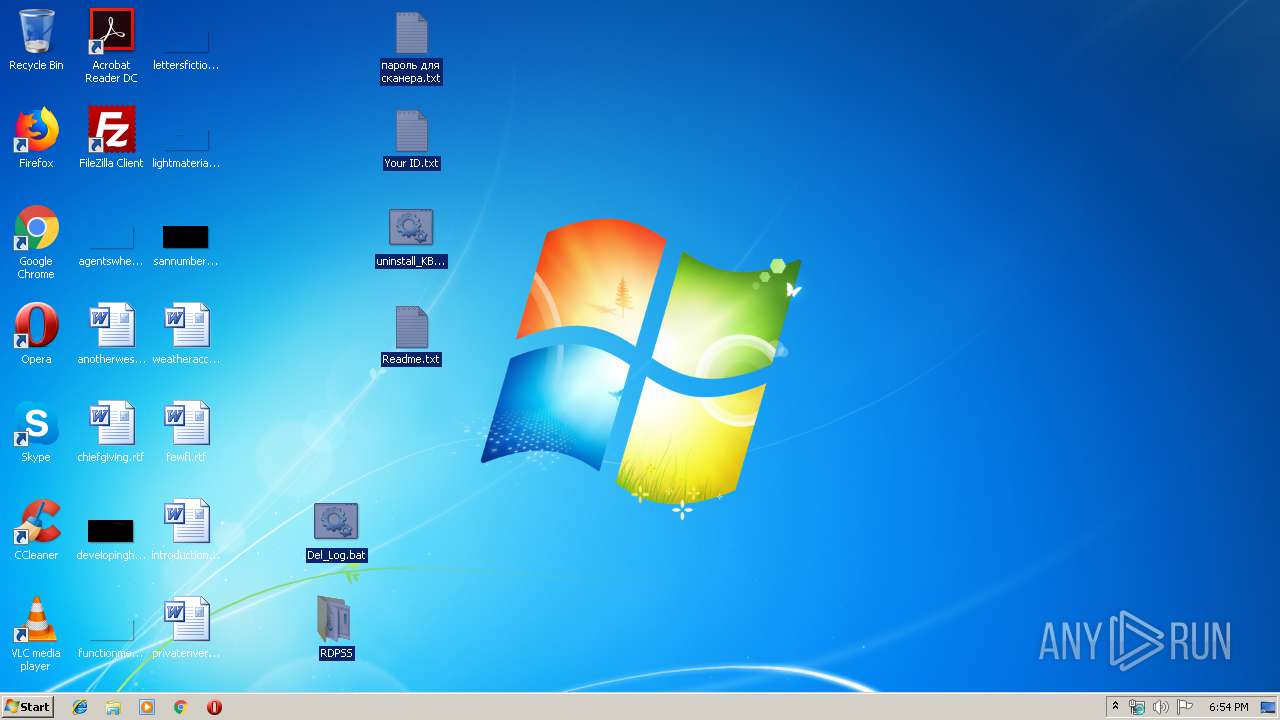
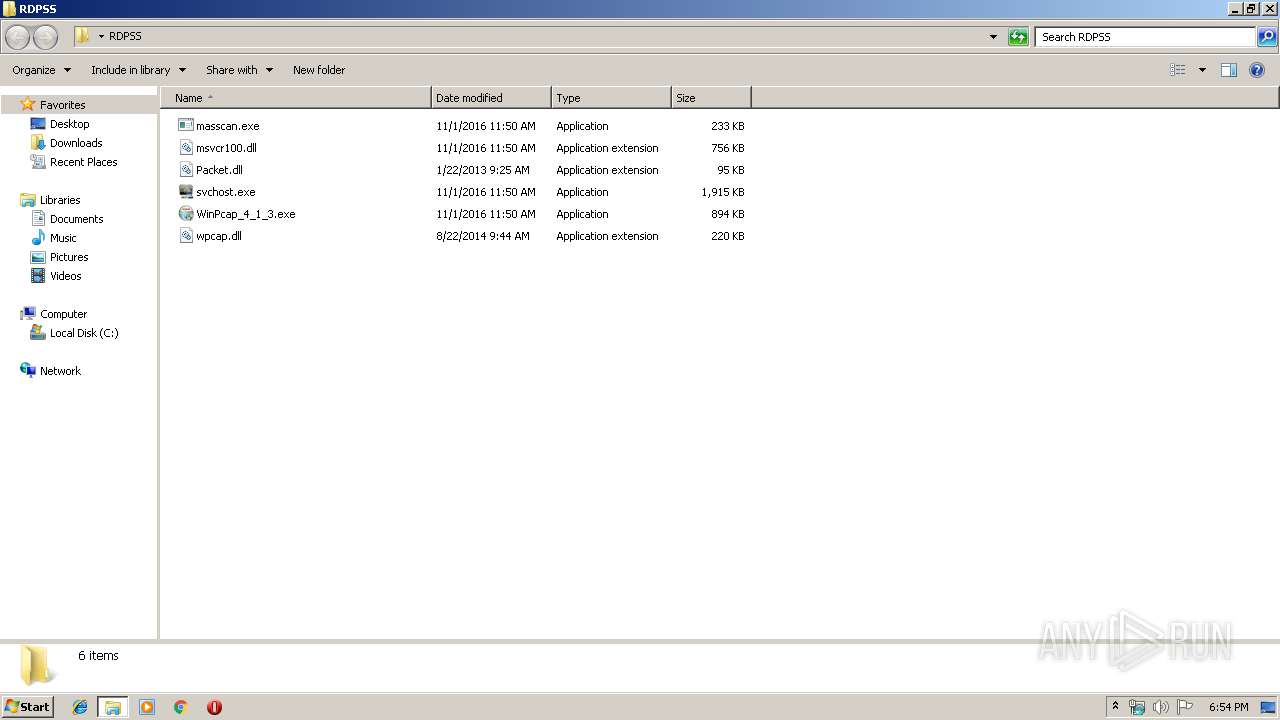
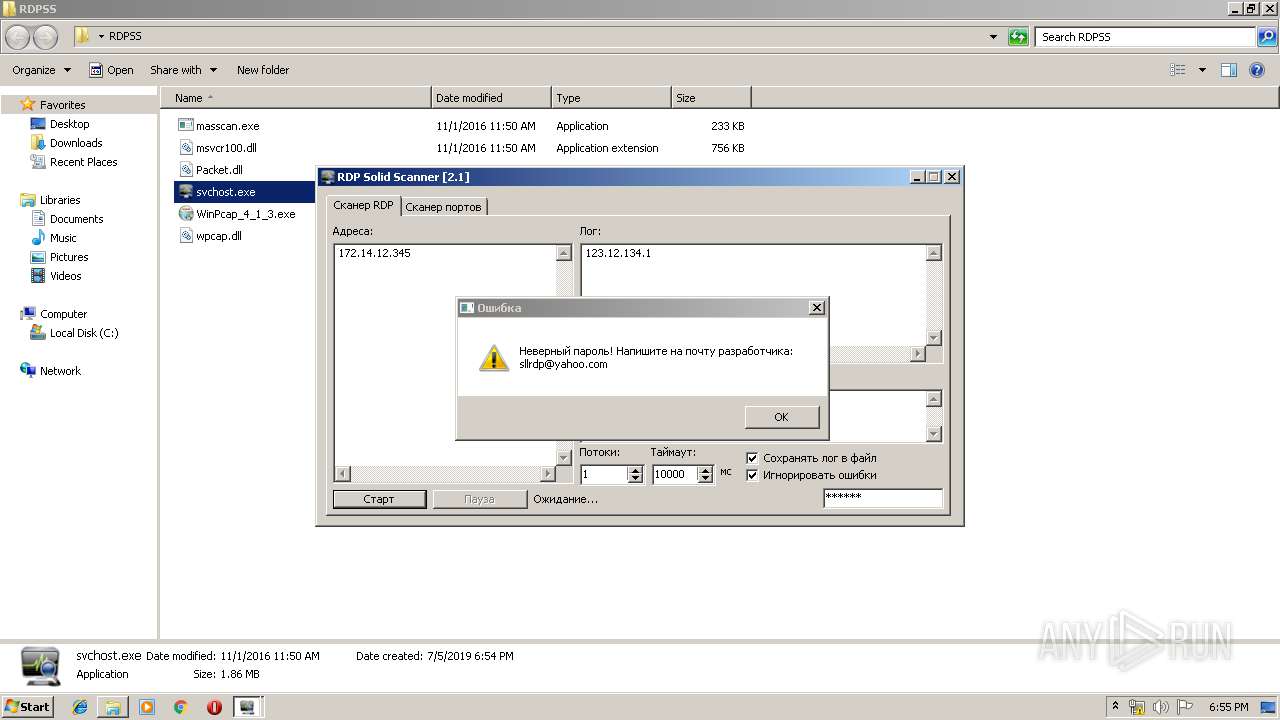
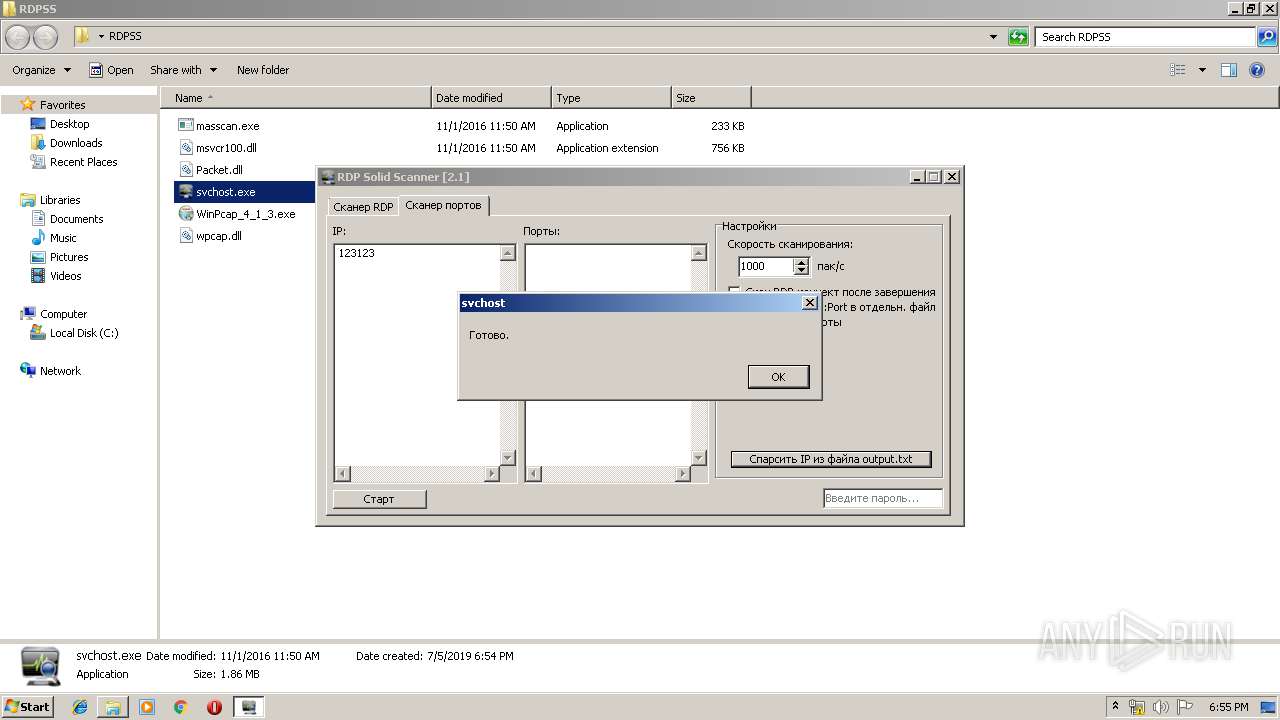
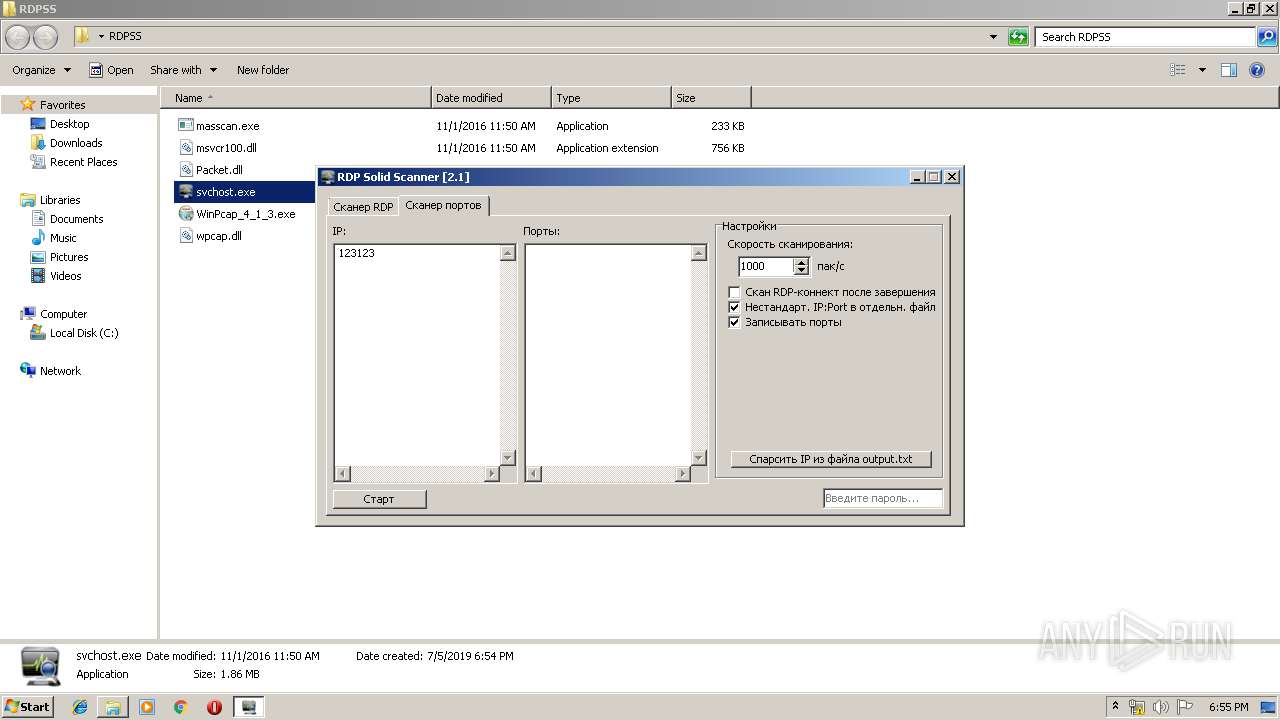
| File name: | RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP ).zip |
| Full analysis: | https://app.any.run/tasks/2e32ad11-8c6e-4161-b648-568ef203b178 |
| Verdict: | Suspicious activity |
| Analysis date: | July 05, 2019, 17:53:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 9E39ED5AD6A4A396067ED3B9AB80C4B0 |
| SHA1: | C5EF1A584B2D03CA8A07318A0ED5D093B3693215 |
| SHA256: | EC9763EEAA93B1AB20386993C7F5664C756569B02E7DF4EAD4C810C5184F7F07 |
| SSDEEP: | 98304:OYlmstO3y5tZUWspFZstJSkhahVIsRTvs+qWyIRai0MvpVK:qsCMUzka1TvpqiRa3WpVK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates executable files which already exist in Windows
- WinRAR.exe (PID: 3268)
Application launched itself
- cmd.exe (PID: 3064)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3064)
Creates files in the Windows directory
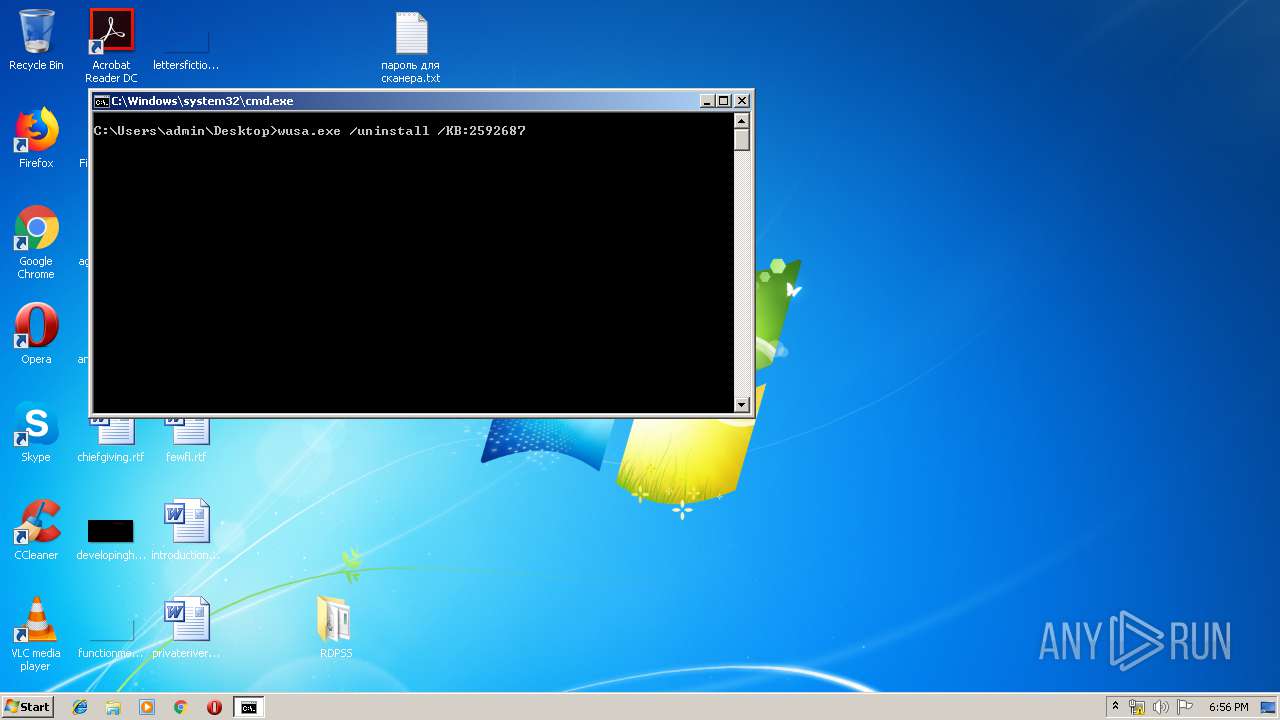
- wusa.exe (PID: 4024)
INFO
Manual execution by user
- svchost.exe (PID: 3176)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 3064)
- masscan.exe (PID: 3456)
- NOTEPAD.EXE (PID: 2648)
- NOTEPAD.EXE (PID: 3580)
- NOTEPAD.EXE (PID: 2580)
- svchost.exe (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2016:11:28 16:18:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | RDP Solid Scanner v2.1 ( ??? ???⠭??????? ???⮢ RDP )/ |
Total processes
59
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
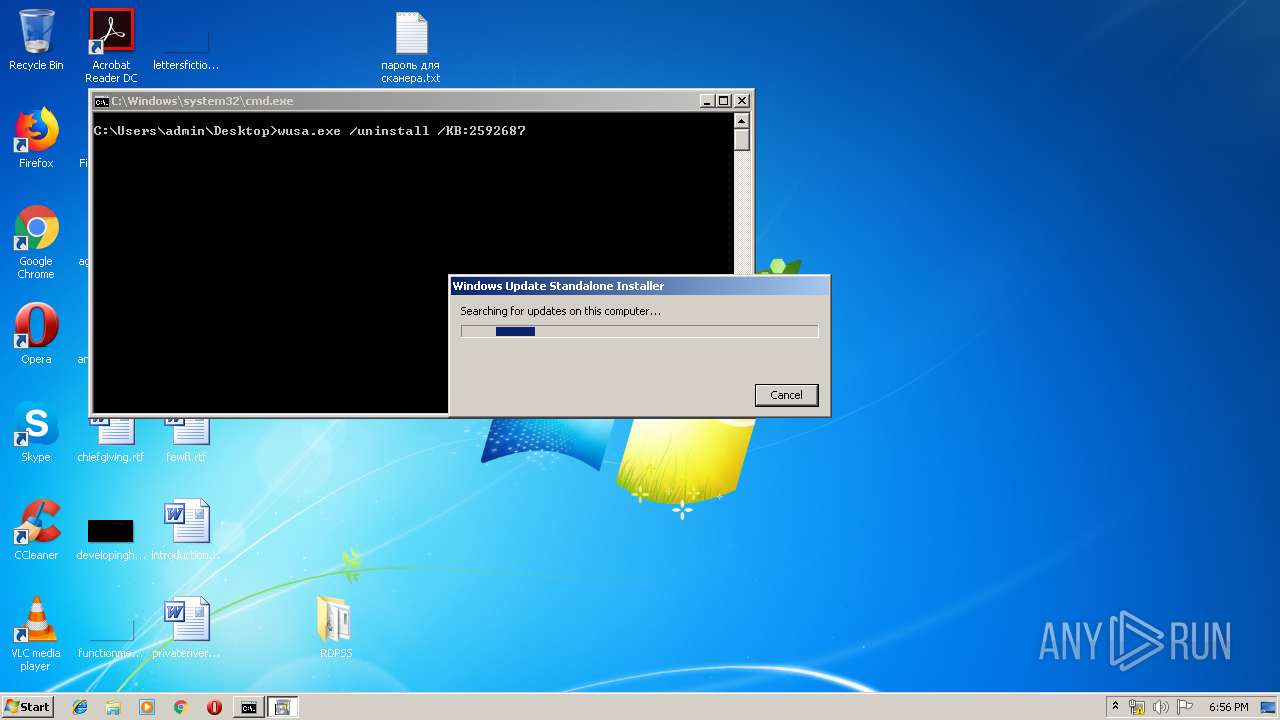
| 2020 | "C:\Windows\system32\wusa.exe" /uninstall /KB:2592687 | C:\Windows\system32\wusa.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Standalone Installer Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2264 | bcdedit | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
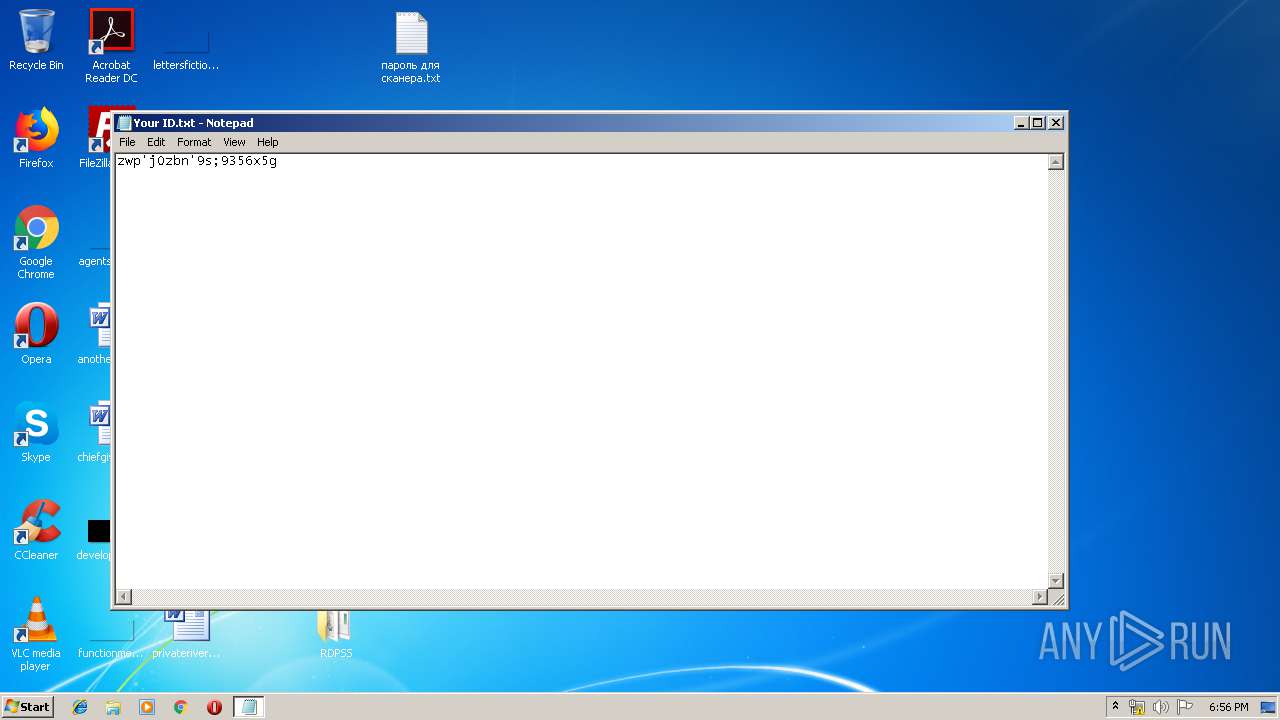
| 2580 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Your ID.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2648 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Readme.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
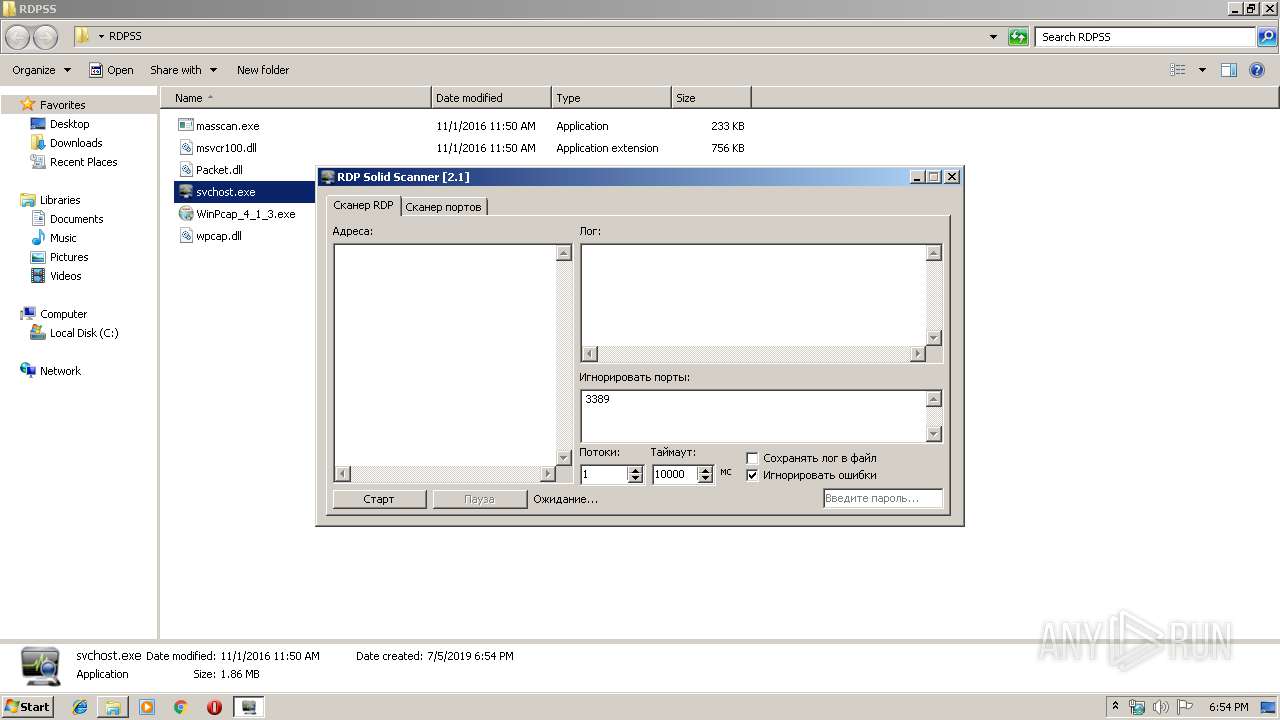
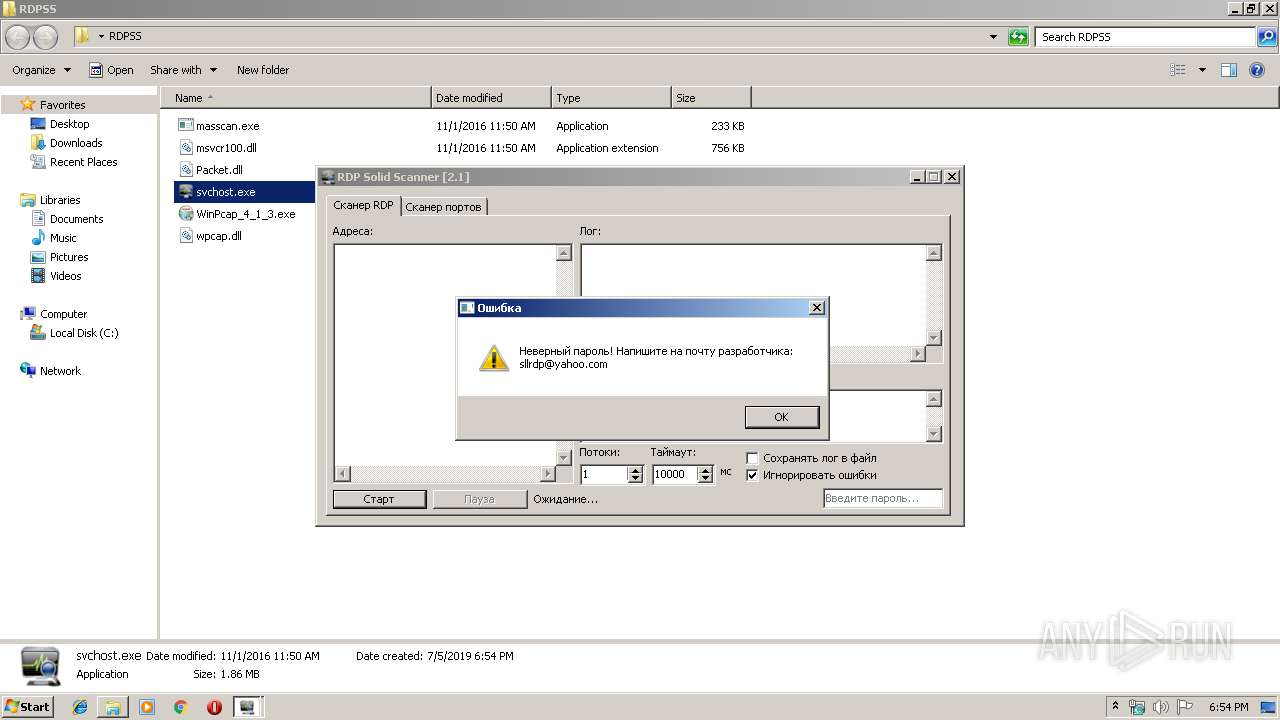
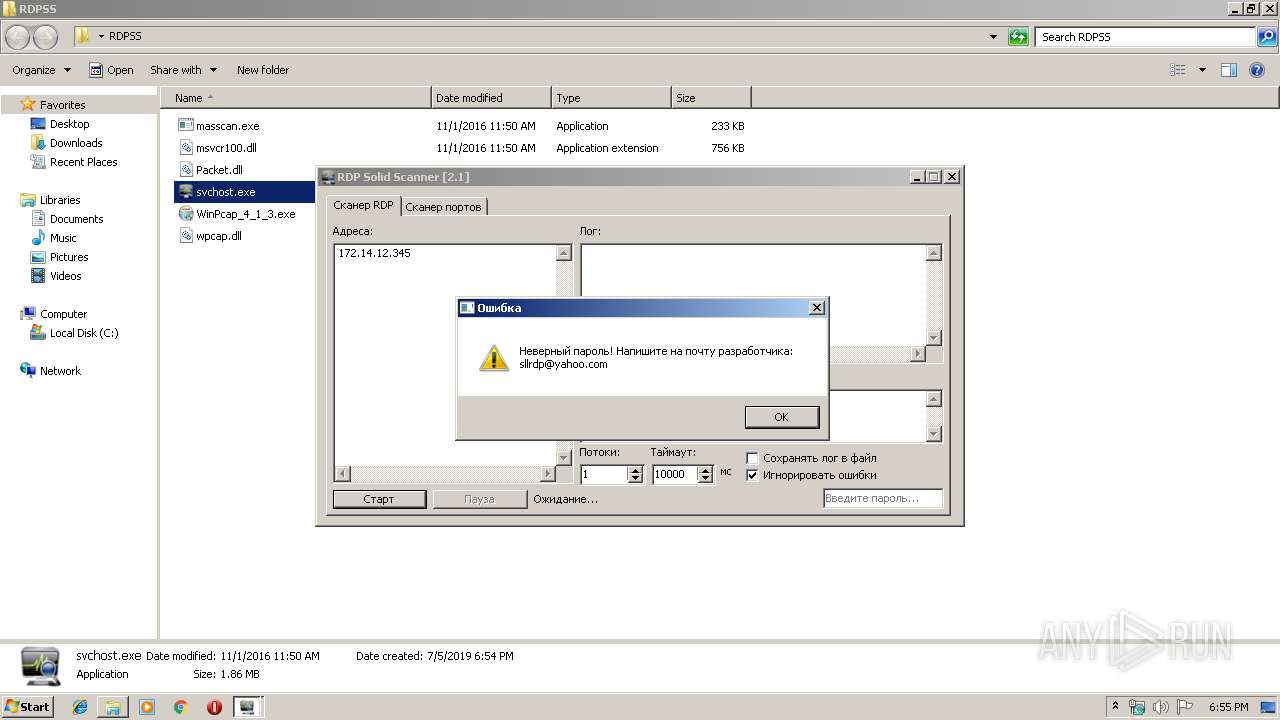
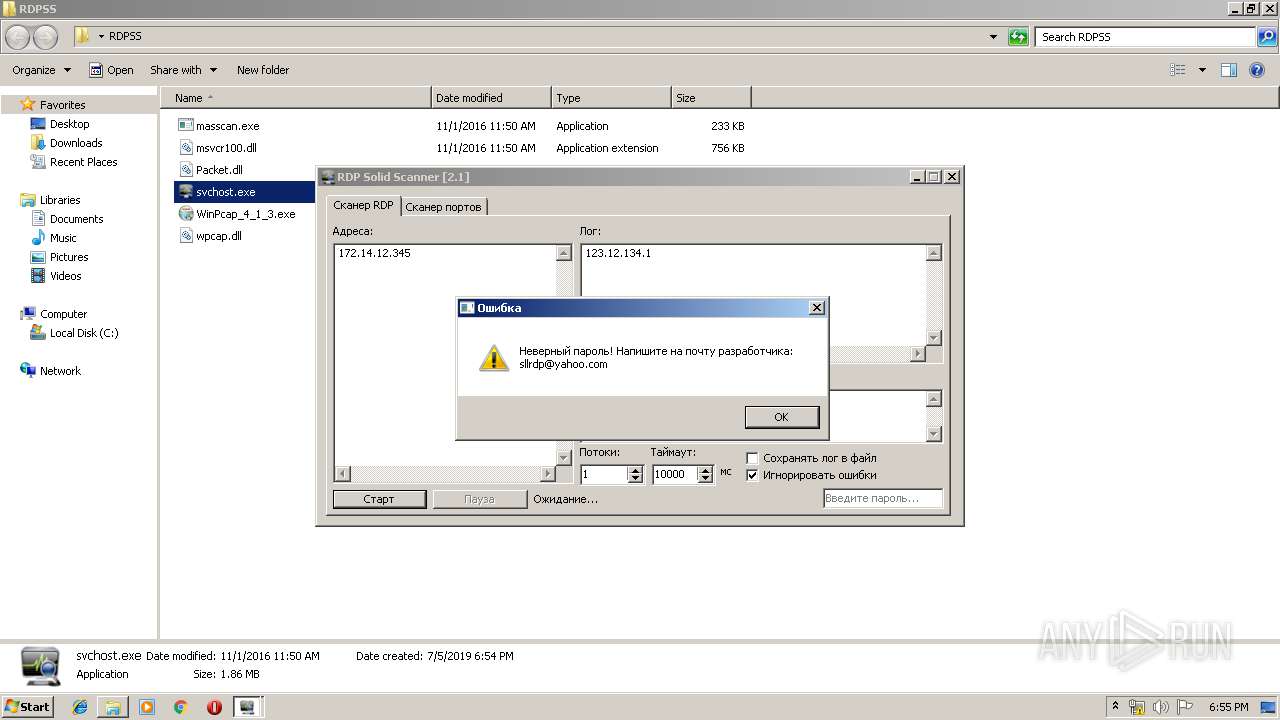
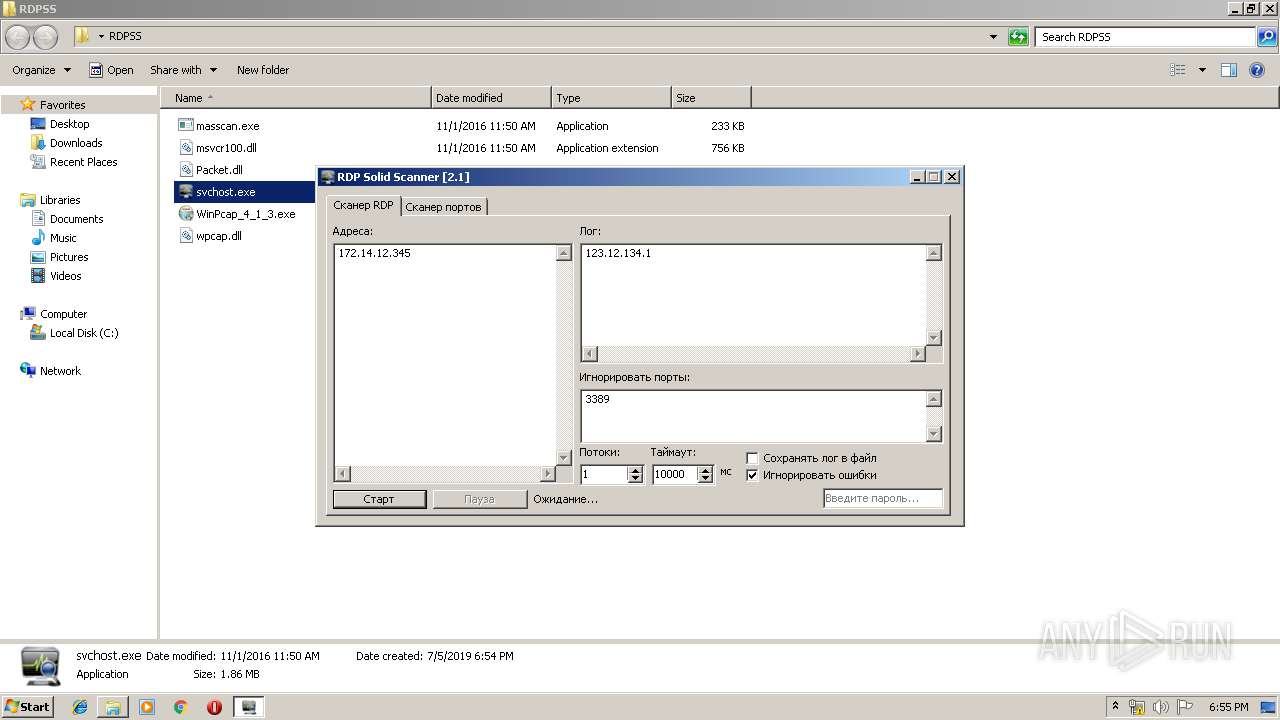
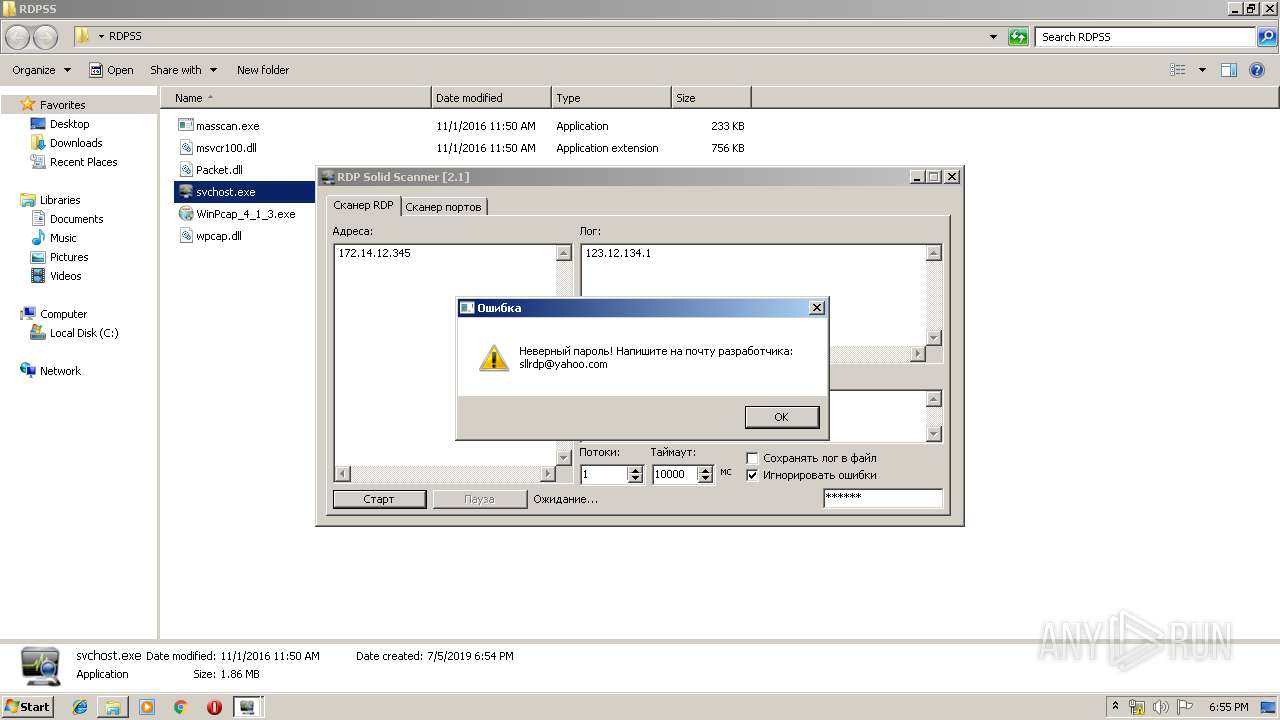
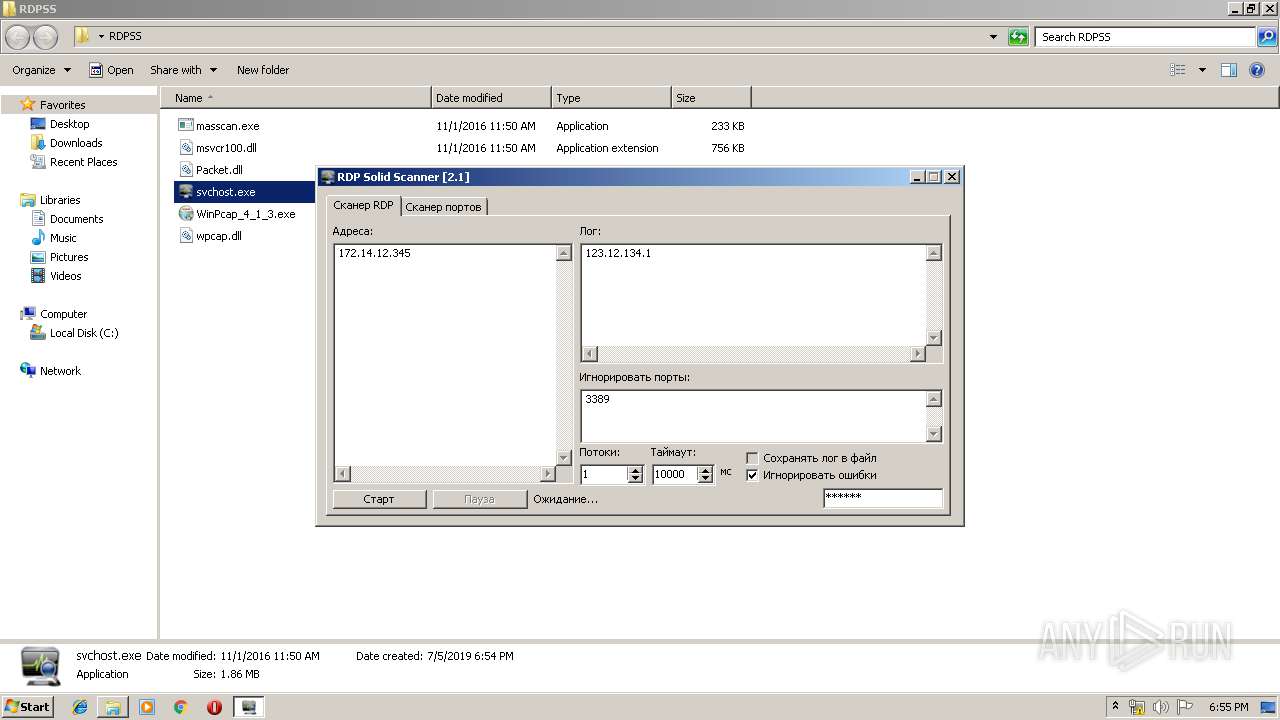
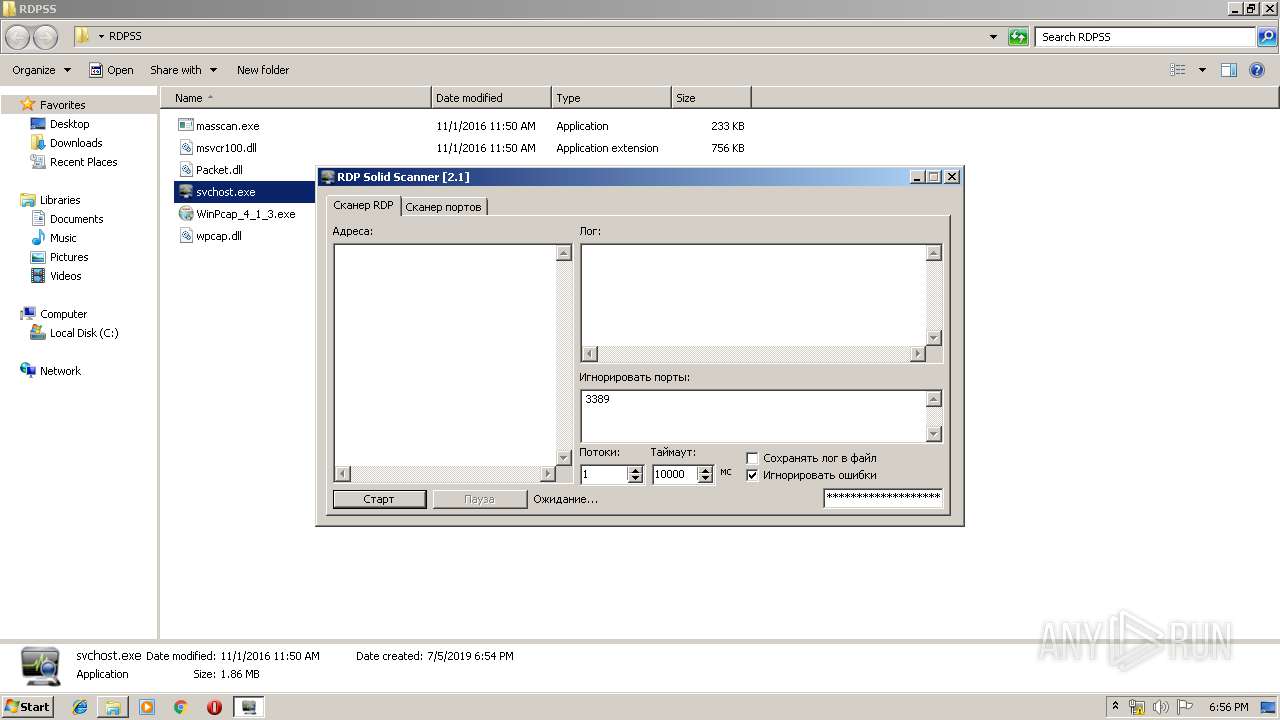
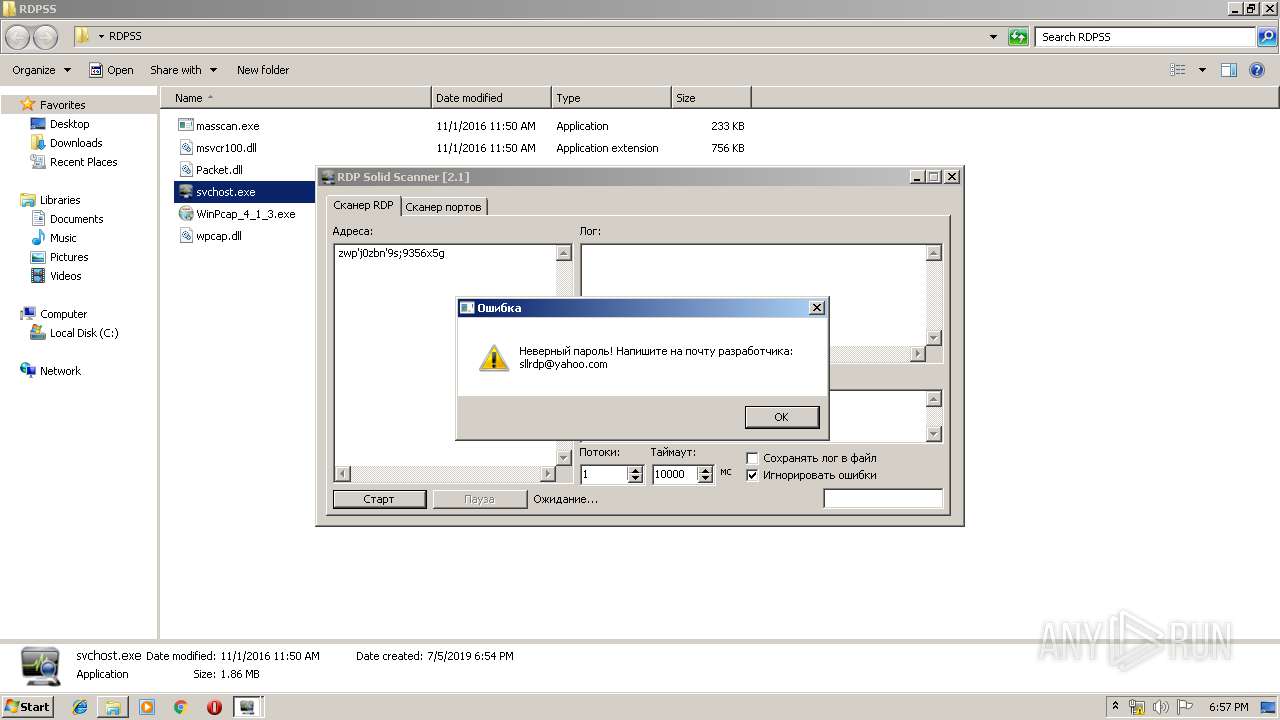
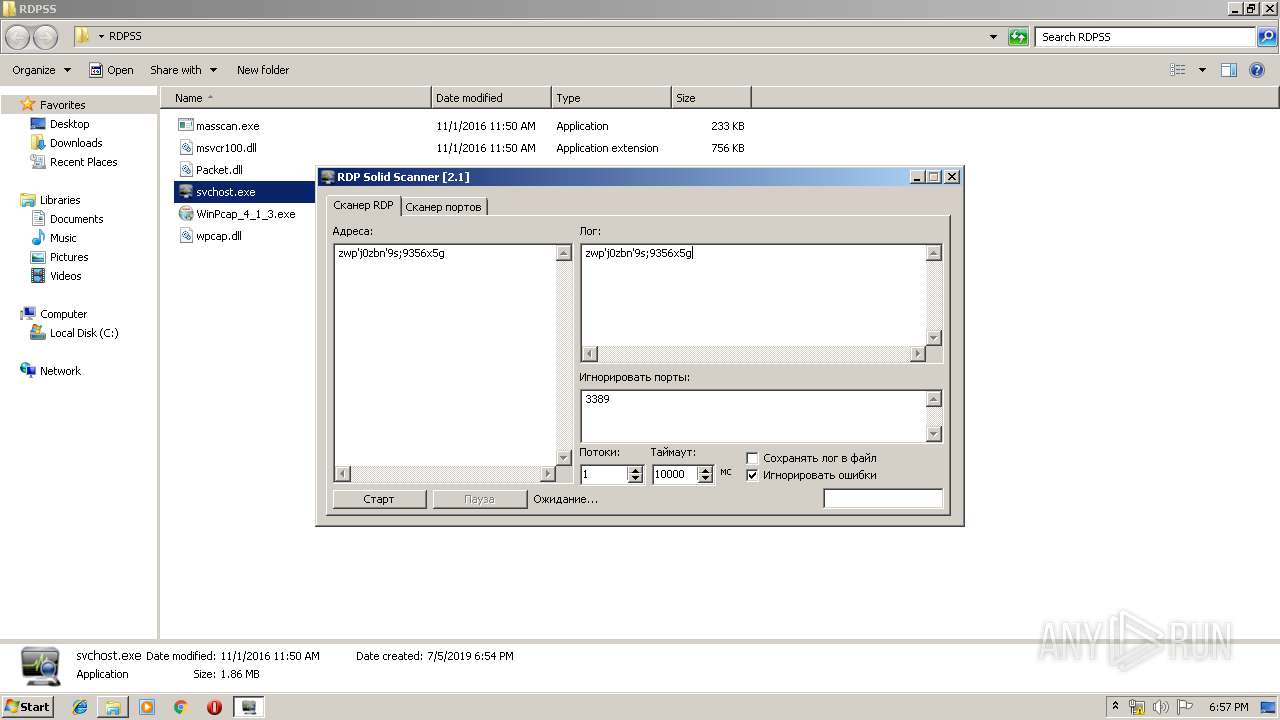
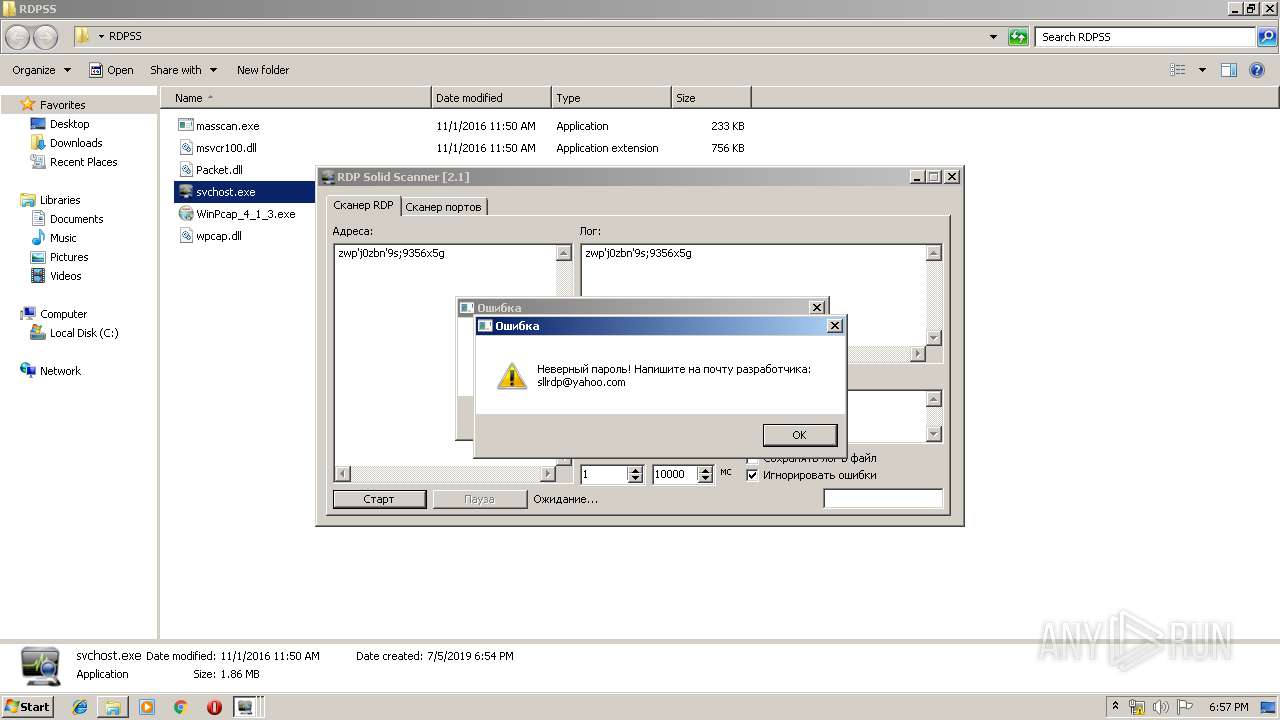
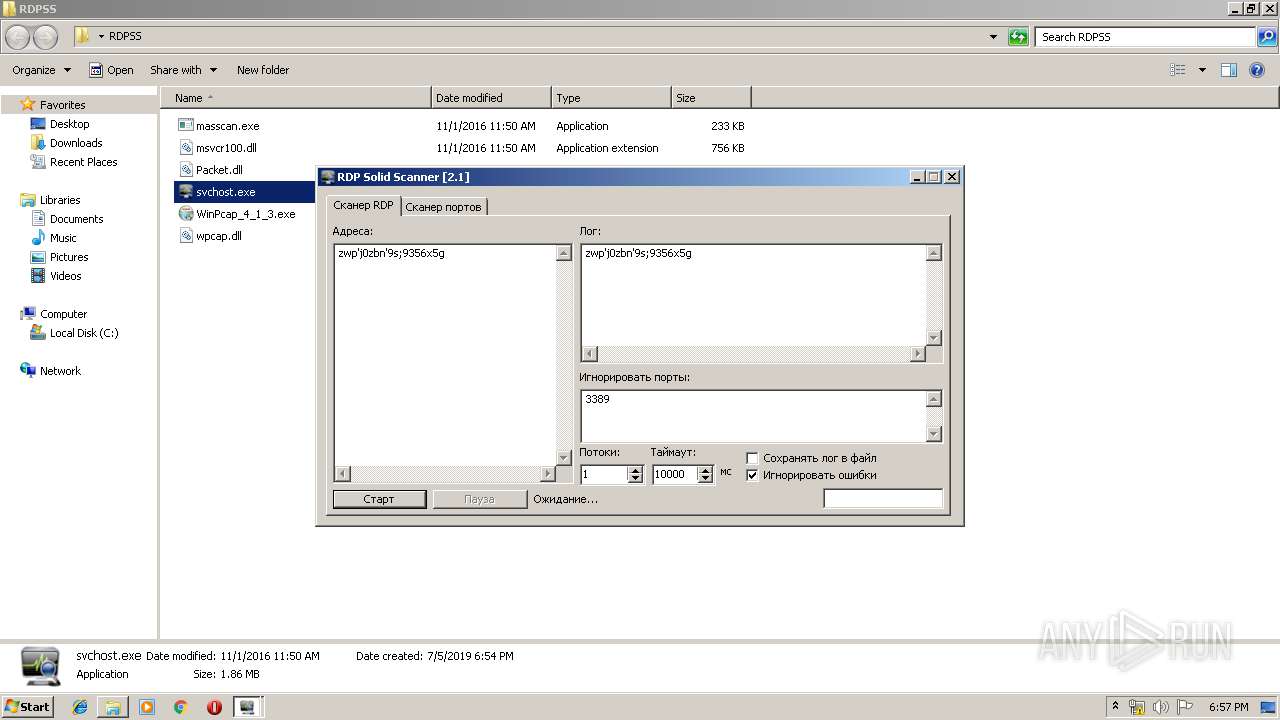
| 2868 | "C:\Users\admin\Desktop\RDPSS\svchost.exe" | C:\Users\admin\Desktop\RDPSS\svchost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3064 | cmd /c ""C:\Users\admin\Desktop\Del_Log.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3092 | wusa.exe /uninstall /KB:2592687 | C:\Windows\system32\wusa.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Standalone Installer Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3176 | "C:\Users\admin\Desktop\RDPSS\svchost.exe" | C:\Users\admin\Desktop\RDPSS\svchost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3268 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP ).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3456 | "C:\Users\admin\Desktop\RDPSS\masscan.exe" | C:\Users\admin\Desktop\RDPSS\masscan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
545
Read events
515
Write events
30
Delete events
0
Modification events
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP ).zip | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (3268) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\RDPSS\masscan.exe | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\RDPSS\msvcr100.dll | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\RDPSS\Packet.dll | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\RDPSS\svchost.exe | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\RDPSS\WinPcap_4_1_3.exe | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\RDPSS\wpcap.dll | — | |
MD5:— | SHA256:— | |||
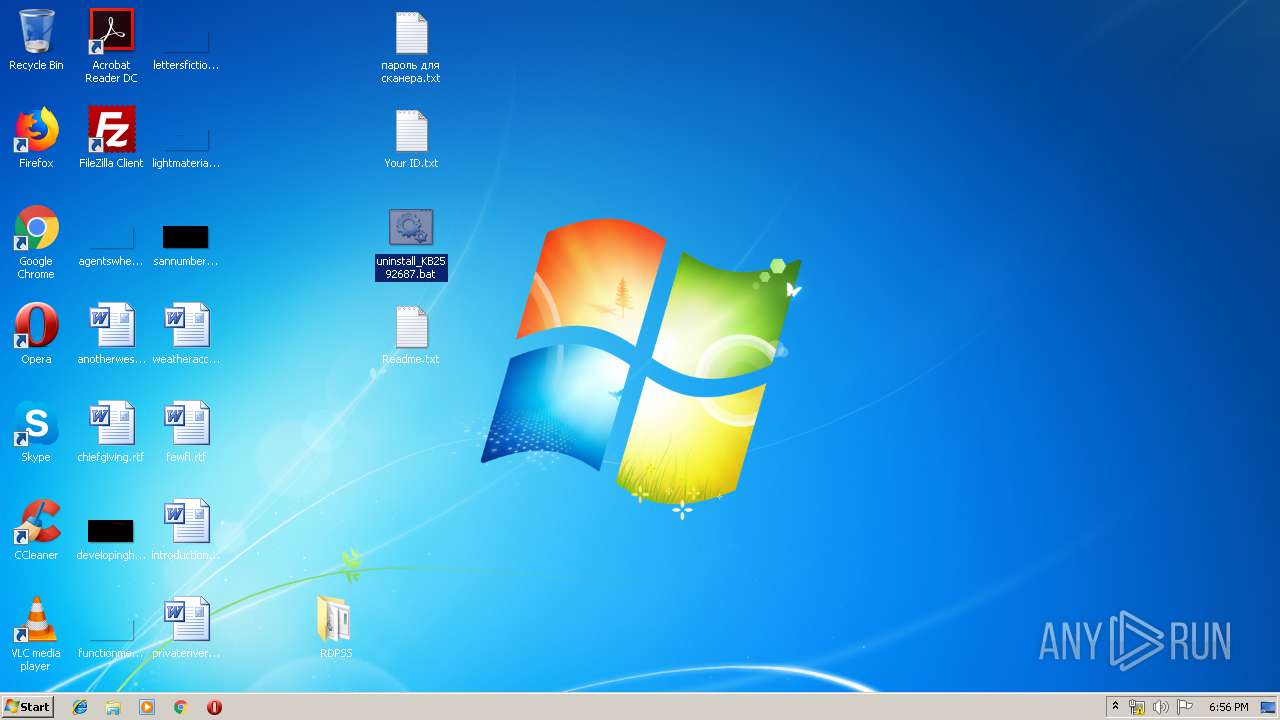
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\Readme.txt | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\uninstall_KB2592687.bat | — | |
MD5:— | SHA256:— | |||
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\Your ID.txt | — | |
MD5:— | SHA256:— | |||
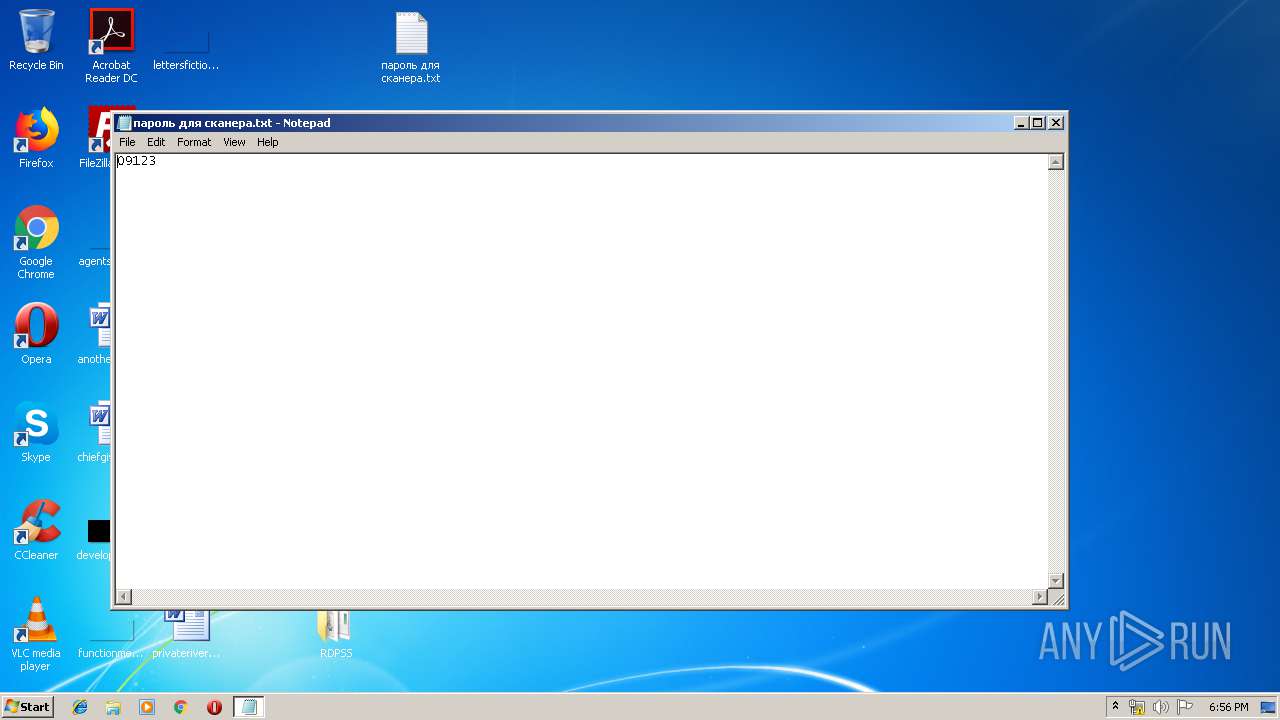
| 3268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3268.27516\RDP Solid Scanner v2.1 ( Чек нестандартных портов RDP )\Scanner RDP\пароль для сканера.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
svchost.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2007 Oreans Technologies ---
------------------------------------------------
|
svchost.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2007 Oreans Technologies ---
------------------------------------------------
|