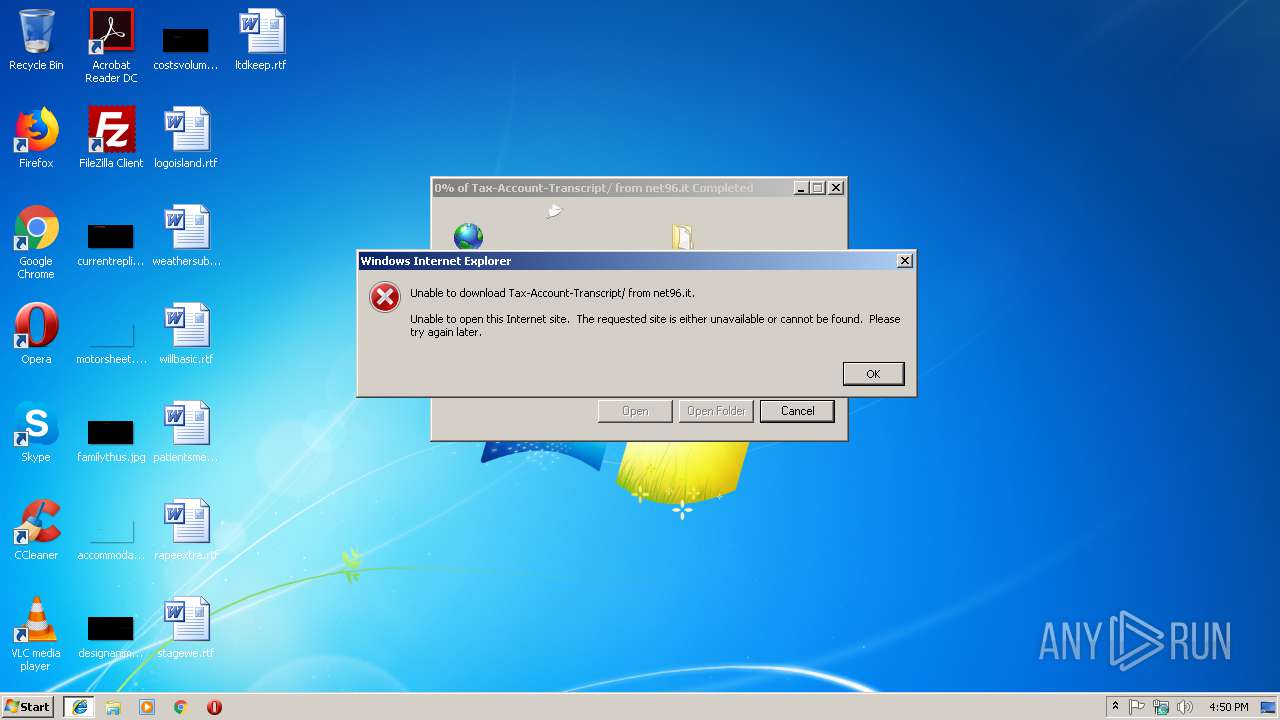
| URL: | http://net96.it/IRS.gov/Tax-Account-Transcript/ |
| Full analysis: | https://app.any.run/tasks/8b23d47a-2b80-4ec4-b361-8130950a19ec |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | December 06, 2018, 16:49:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7B7CA265738AD656DBD14F7A5EF6E91F |
| SHA1: | 8D0085A4546C33ADA998CB1E2F26675788BD75F9 |
| SHA256: | EC45E9CDF0A9EE2C9B7C8B6123A6A31F213E1CADD12267F989338C60382D4DBA |
| SSDEEP: | 3:N1KQ0cTLEG2IK/dQlGA3:CQJoGhKlE3 |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2392)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2392)
Executes PowerShell scripts
- cmd.exe (PID: 556)
Application was dropped or rewritten from another process
- 946.exe (PID: 3604)
- 946.exe (PID: 2700)
- archivesymbol.exe (PID: 3284)
- archivesymbol.exe (PID: 3984)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2780)
Downloads executable files from the Internet
- powershell.exe (PID: 2780)
Changes the autorun value in the registry
- archivesymbol.exe (PID: 3984)
Connects to CnC server
- archivesymbol.exe (PID: 3984)
EMOTET was detected
- archivesymbol.exe (PID: 3984)
SUSPICIOUS
Starts Microsoft Office Application
- chrome.exe (PID: 3872)
- WINWORD.EXE (PID: 2392)
Application launched itself
- WINWORD.EXE (PID: 2392)
- cmd.exe (PID: 3672)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3836)
- cmd.exe (PID: 556)
- cmd.exe (PID: 3672)
Creates files in the user directory
- powershell.exe (PID: 2780)
Executable content was dropped or overwritten
- powershell.exe (PID: 2780)
- 946.exe (PID: 2700)
Starts itself from another location
- 946.exe (PID: 2700)
Connects to unusual port
- archivesymbol.exe (PID: 3984)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2556)
- WINWORD.EXE (PID: 2392)
Creates files in the user directory
- WINWORD.EXE (PID: 2392)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 2828)
Reads Internet Cache Settings
- chrome.exe (PID: 3872)
- iexplore.exe (PID: 3400)
Application launched itself
- chrome.exe (PID: 3872)
- iexplore.exe (PID: 2828)
Reads settings of System Certificates
- chrome.exe (PID: 3872)
Changes internet zones settings
- iexplore.exe (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
24
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | C:\Windows\system32\cmd.exe /S /D /c" FOR /F "delims=7OCsi. tokens=5" %W IN ('assoc.psc1') DO %W -" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,14933916972027242924,3007798729026208280,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=CB442679A8F8C19D8439C352E0ECA7EA --mojo-platform-channel-handle=2564 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,14933916972027242924,3007798729026208280,131072 --enable-features=PasswordImport --service-pipe-token=AF1B3AFEE89020D8BFD61DFE08A56588 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=AF1B3AFEE89020D8BFD61DFE08A56588 --renderer-client-id=5 --mojo-platform-channel-handle=1916 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\Tax Return Transcript - 12 06 2018.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2556 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6f4900b0,0x6f4900c0,0x6f4900cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2700 | "C:\Users\admin\AppData\Local\Temp\946.exe" | C:\Users\admin\AppData\Local\Temp\946.exe | 946.exe | ||||||||||||
User: admin Company: Nexon Corp. Integrity Level: MEDIUM Description: Softpub Specialer DLL Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
| 2780 | PowerShell - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,14933916972027242924,3007798729026208280,131072 --enable-features=PasswordImport --service-pipe-token=FC41DC4478BC5F65582F18E932BC276B --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=FC41DC4478BC5F65582F18E932BC276B --renderer-client-id=3 --mojo-platform-channel-handle=1536 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2828 | "C:\Program Files\Internet Explorer\iexplore.exe" http://net96.it/IRS.gov/Tax-Account-Transcript/ | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 560
Read events
3 040
Write events
505
Delete events
15
Modification events
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {00A675F9-F977-11E8-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2828) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C0004000600100032000F003C02 | |||
Executable files
2
Suspicious files
50
Text files
69
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF2980E62391335805.TMP | — | |
MD5:— | SHA256:— | |||
| 3872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ed76c18e-8bdd-43c8-a43a-af6c535d5019.tmp | — | |
MD5:— | SHA256:— | |||
| 3872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{00A675FA-F977-11E8-BAD8-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF19c8c4.TMP | text | |
MD5:— | SHA256:— | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF879B4893EF19D59.TMP | — | |
MD5:— | SHA256:— | |||
| 2828 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{00A675F9-F977-11E8-BAD8-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
18
DNS requests
12
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2780 | powershell.exe | GET | 301 | 91.186.0.8:80 | http://bethrow.co.uk/lMPE | GB | html | 234 b | malicious |
2780 | powershell.exe | GET | 200 | 91.186.0.8:80 | http://bethrow.co.uk/lMPE/ | GB | executable | 120 Kb | malicious |
3984 | archivesymbol.exe | GET | 200 | 189.223.176.239:7080 | http://189.223.176.239:7080/ | MX | binary | 132 b | malicious |
3872 | chrome.exe | GET | 200 | 40.91.205.36:80 | http://net96.it/IRS.gov/Tax-Account-Transcript/ | NL | document | 143 Kb | suspicious |
3400 | iexplore.exe | GET | 200 | 40.91.205.36:80 | http://net96.it/IRS.gov/Tax-Account-Transcript/ | NL | document | 143 Kb | suspicious |
2828 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3400 | iexplore.exe | 40.91.205.36:80 | net96.it | Microsoft Corporation | NL | suspicious |
2828 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3872 | chrome.exe | 172.217.168.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3872 | chrome.exe | 172.217.168.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3872 | chrome.exe | 172.217.17.68:443 | www.google.com | Google Inc. | US | whitelisted |
3872 | chrome.exe | 172.217.168.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3872 | chrome.exe | 172.217.168.46:443 | clients1.google.com | Google Inc. | US | whitelisted |
3872 | chrome.exe | 172.217.168.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2780 | powershell.exe | 91.186.0.8:80 | bethrow.co.uk | Simply Transit Ltd | GB | malicious |
3872 | chrome.exe | 40.91.205.36:80 | net96.it | Microsoft Corporation | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
net96.it |
| suspicious |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
bethrow.co.uk |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3400 | iexplore.exe | Attempted User Privilege Gain | SC ATTEMPTED_USER Microsoft Word 2016 use after free attempt |
3400 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
3400 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
3872 | chrome.exe | Attempted User Privilege Gain | SC ATTEMPTED_USER Microsoft Word 2016 use after free attempt |
3872 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
3872 | chrome.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
2780 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious loader with tiny header |
2780 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2780 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2780 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1 ETPRO signatures available at the full report