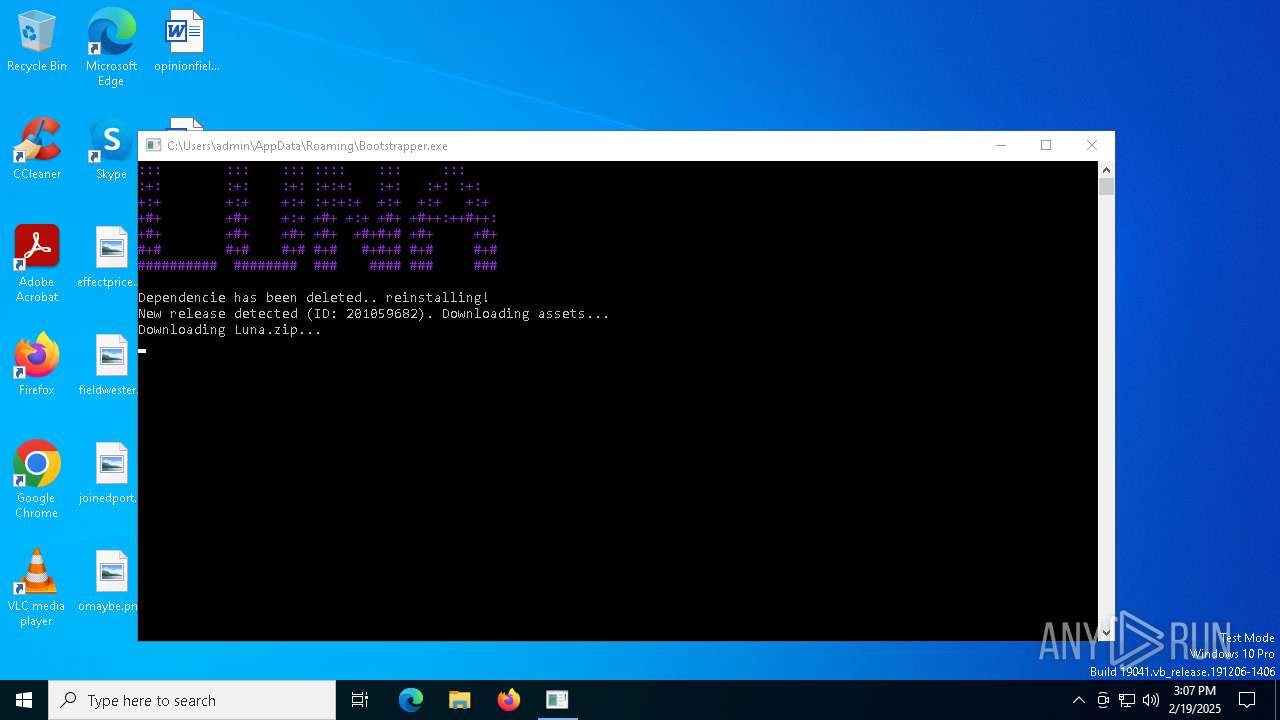
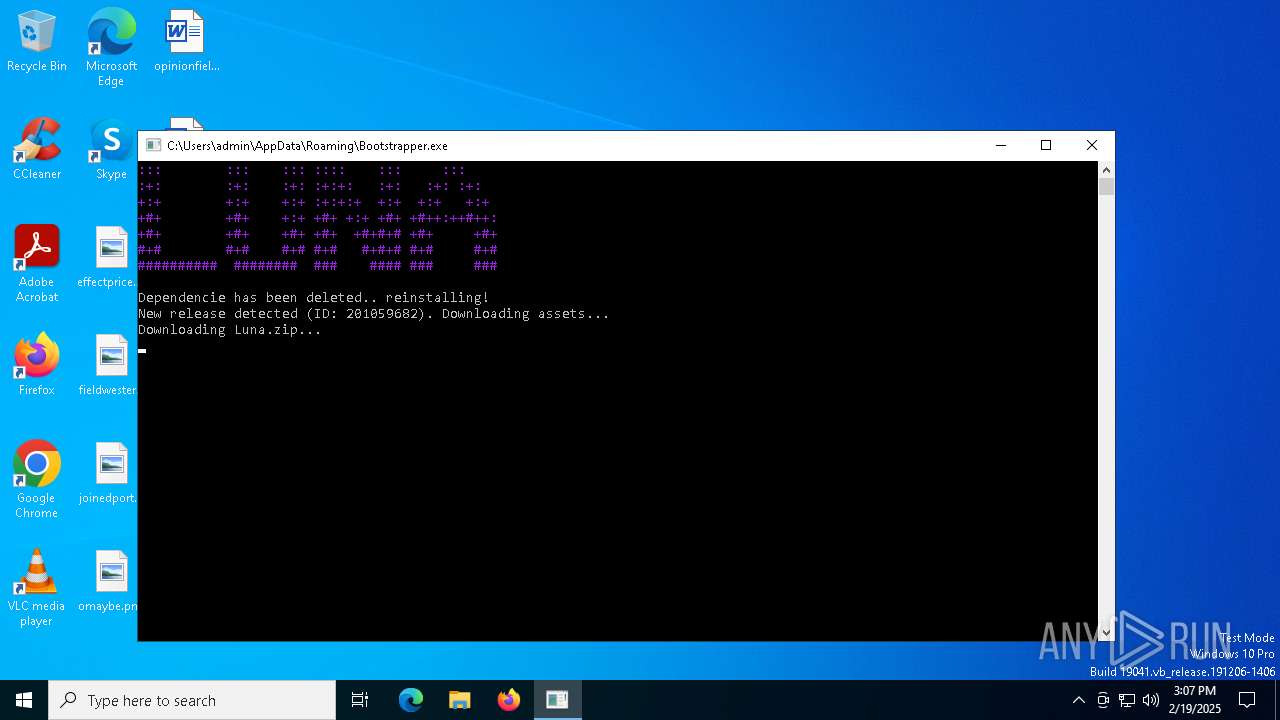
| File name: | Bootstraper.exe |
| Full analysis: | https://app.any.run/tasks/8892df8e-9891-4300-8edb-a95a17567cfc |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | February 19, 2025, 15:07:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 8EFD1EA1AA39ADCC469939BC372D186F |
| SHA1: | 50979C4A6484A37352A01CDA9841D96FA4B9746C |
| SHA256: | EC335EEC1B178582FC357F556984003C97C52D3E01B63D0ED932C9A9681AE262 |
| SSDEEP: | 98304:w16s522jBJsXSLd1CT9Hf+kmFM9/ZFG4QRAZDfQKsgHWdsMSUgKfCKk/5a0i62G1:ub/Tf7vX1eBzqHJi+cG7Y8 |
MALICIOUS
SLIVERFOX has been found (auto)
- Bootstraper.exe (PID: 1744)
DCRAT mutex has been found
- DriverNet.exe (PID: 236)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4052)
Changes the autorun value in the registry
- DriverNet.exe (PID: 236)
Changes the login/logoff helper path in the registry
- DriverNet.exe (PID: 236)
SUSPICIOUS
Executable content was dropped or overwritten
- Bootstraper.exe (PID: 1744)
- TaskBos.exe (PID: 644)
- Bootstrapper.exe (PID: 4536)
- DriverNet.exe (PID: 236)
Reads security settings of Internet Explorer
- TaskBos.exe (PID: 644)
- Bootstraper.exe (PID: 1744)
- DriverNet.exe (PID: 236)
Reads the date of Windows installation
- Bootstraper.exe (PID: 1744)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4052)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4052)
- DriverNet.exe (PID: 236)
Executing commands from a ".bat" file
- wscript.exe (PID: 4052)
- DriverNet.exe (PID: 236)
Executed via WMI
- schtasks.exe (PID: 6004)
- schtasks.exe (PID: 6160)
- schtasks.exe (PID: 4764)
- schtasks.exe (PID: 6268)
- schtasks.exe (PID: 6284)
- schtasks.exe (PID: 6300)
- schtasks.exe (PID: 6324)
- schtasks.exe (PID: 6348)
- schtasks.exe (PID: 6428)
- schtasks.exe (PID: 6364)
- schtasks.exe (PID: 6388)
- schtasks.exe (PID: 6412)
- schtasks.exe (PID: 6452)
- schtasks.exe (PID: 6472)
- schtasks.exe (PID: 6512)
- schtasks.exe (PID: 6536)
- schtasks.exe (PID: 6492)
- schtasks.exe (PID: 6556)
- schtasks.exe (PID: 6580)
- schtasks.exe (PID: 6596)
- schtasks.exe (PID: 6636)
- schtasks.exe (PID: 6664)
- schtasks.exe (PID: 6616)
- schtasks.exe (PID: 6704)
- schtasks.exe (PID: 6680)
- schtasks.exe (PID: 6724)
- schtasks.exe (PID: 6796)
- schtasks.exe (PID: 6772)
- schtasks.exe (PID: 6740)
- schtasks.exe (PID: 6812)
- schtasks.exe (PID: 6860)
- schtasks.exe (PID: 6840)
- schtasks.exe (PID: 6900)
- schtasks.exe (PID: 6876)
- schtasks.exe (PID: 6924)
- schtasks.exe (PID: 6940)
- schtasks.exe (PID: 6960)
- schtasks.exe (PID: 7000)
- schtasks.exe (PID: 6984)
- schtasks.exe (PID: 7028)
- schtasks.exe (PID: 7064)
- schtasks.exe (PID: 7092)
- schtasks.exe (PID: 7112)
- schtasks.exe (PID: 7044)
- schtasks.exe (PID: 7148)
- schtasks.exe (PID: 7132)
- schtasks.exe (PID: 4816)
- schtasks.exe (PID: 5536)
- schtasks.exe (PID: 6212)
- schtasks.exe (PID: 6204)
- schtasks.exe (PID: 6172)
- schtasks.exe (PID: 6196)
- schtasks.exe (PID: 6220)
- schtasks.exe (PID: 6236)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6236)
The process creates files with name similar to system file names
- DriverNet.exe (PID: 236)
INFO
Reads the machine GUID from the registry
- Bootstraper.exe (PID: 1744)
- DriverNet.exe (PID: 236)
Reads the computer name
- Bootstraper.exe (PID: 1744)
Checks supported languages
- Bootstraper.exe (PID: 1744)
- TaskBos.exe (PID: 644)
- DriverNet.exe (PID: 236)
Creates files or folders in the user directory
- Bootstraper.exe (PID: 1744)
Create files in a temporary directory
- Bootstrapper.exe (PID: 4536)
Process checks computer location settings
- Bootstraper.exe (PID: 1744)
- TaskBos.exe (PID: 644)
Reads Environment values
- DriverNet.exe (PID: 236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:18 16:51:00+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 11084288 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa9413e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 1.0.0.0 |
| InternalName: | Bootstraper.exe |
| LegalCopyright: | |
| OriginalFileName: | Bootstraper.exe |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
182
Monitored processes
66
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\runtimeBrokerhost\DriverNet.exe" | C:\runtimeBrokerhost\DriverNet.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 644 | "C:\Users\admin\AppData\Roaming\TaskBos.exe" | C:\Users\admin\AppData\Roaming\TaskBos.exe | Bootstraper.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1744 | "C:\Users\admin\AppData\Local\Temp\Bootstraper.exe" | C:\Users\admin\AppData\Local\Temp\Bootstraper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2008 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Time Service Diagnostic Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Bootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3080 | "C:\Users\admin\AppData\Roaming\TaskBos.exe" | C:\Users\admin\AppData\Roaming\TaskBos.exe | — | Bootstraper.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4052 | "C:\WINDOWS\System32\WScript.exe" "C:\runtimeBrokerhost\e2LOYhoRcd7OJoCdR5.vbe" | C:\Windows\SysWOW64\wscript.exe | — | TaskBos.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4536 | "C:\Users\admin\AppData\Roaming\Bootstrapper.exe" | C:\Users\admin\AppData\Roaming\Bootstrapper.exe | Bootstraper.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 4548 | C:\WINDOWS\system32\cmd.exe /c ""C:\runtimeBrokerhost\IvkxCn8eWrhBo2yFUeXgbfEwLLE7X2.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4764 | schtasks.exe /create /tn "ctfmon" /sc ONLOGON /tr "'C:\Recovery\OEM\ctfmon.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 162
Read events
8 103
Write events
59
Delete events
0
Modification events
| (PID) Process: | (644) TaskBos.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | StartMenuExperienceHost |
Value: "C:\Users\All Users\Package Cache\{73F77E4E-5A17-46E5-A5FC-8A061047725F}v14.36.32532\packages\StartMenuExperienceHost.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | StartMenuExperienceHost |
Value: "C:\Users\All Users\Package Cache\{73F77E4E-5A17-46E5-A5FC-8A061047725F}v14.36.32532\packages\StartMenuExperienceHost.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, "C:\Recovery\OEM\ctfmon.exe", "C:\Users\All Users\Package Cache\{73F77E4E-5A17-46E5-A5FC-8A061047725F}v14.36.32532\packages\StartMenuExperienceHost.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ctfmon |
Value: "C:\Recovery\OEM\ctfmon.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ctfmon |
Value: "C:\Recovery\OEM\ctfmon.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, "C:\Recovery\OEM\ctfmon.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | lsass |
Value: "C:\runtimeBrokerhost\lsass.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | lsass |
Value: "C:\runtimeBrokerhost\lsass.exe" | |||
| (PID) Process: | (236) DriverNet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, "C:\Recovery\OEM\ctfmon.exe", "C:\Users\All Users\Package Cache\{73F77E4E-5A17-46E5-A5FC-8A061047725F}v14.36.32532\packages\StartMenuExperienceHost.exe", "C:\runtimeBrokerhost\lsass.exe" | |||
Executable files
23
Suspicious files
2
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 644 | TaskBos.exe | C:\runtimeBrokerhost\e2LOYhoRcd7OJoCdR5.vbe | binary | |
MD5:E963AFD12DD2BFBED0F1A4478E7E2069 | SHA256:7C8C41D477E655450C781AEEF7A9AB95FF703D8AD2AAD508BE5D1CD18812F5D5 | |||
| 1744 | Bootstraper.exe | C:\Users\admin\AppData\Roaming\TaskBos.exe | executable | |
MD5:ECCAFFE72F097705D7ED175B17A2C892 | SHA256:8624D11E1E4040D17729FE3A2B36519C6A7F6B3B09DC6DD65F2024D28562F221 | |||
| 1744 | Bootstraper.exe | C:\Users\admin\AppData\Roaming\Bootstrapper.exe | executable | |
MD5:F2A6133B7F38FC49F792AE799D1B4750 | SHA256:37BDE6655E1272E159B9C2E3A7EEE3F4E9A837C0F04240645D3991D112287F8D | |||
| 4536 | Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\downloads\Luna.zip | compressed | |
MD5:6699992F1A815C490D6EEA19D30A4176 | SHA256:714597D871E4C6CE2BF9CBF5F369CAF3C2951A25069F67DBB6926D48E0AA9176 | |||
| 644 | TaskBos.exe | C:\runtimeBrokerhost\DriverNet.exe | executable | |
MD5:06BE6046BBBD81C71008F62FBA82DB41 | SHA256:7D8CF4A7366244FEFBF18041107D750303A1E06F55632B7CD402D4ECB8122850 | |||
| 236 | DriverNet.exe | C:\Recovery\OEM\26c12092da979c | text | |
MD5:3024FBFDBF6D02DA1C6E059541BE8DC1 | SHA256:D59B4BAA678D564E39AB3E0AAD0FAE6E47DFFC8CFAF1EFA9893F67A513DF3216 | |||
| 644 | TaskBos.exe | C:\runtimeBrokerhost\IvkxCn8eWrhBo2yFUeXgbfEwLLE7X2.bat | text | |
MD5:08E9466FAFA468CE57FAA4914678CF32 | SHA256:AB2CBE7808FF7530A199CDD08F82D6DEC6254ED1E693CE61FC906470B916D0BF | |||
| 236 | DriverNet.exe | C:\Users\Administrator\AppData\Roaming\csrss.exe | executable | |
MD5:06BE6046BBBD81C71008F62FBA82DB41 | SHA256:7D8CF4A7366244FEFBF18041107D750303A1E06F55632B7CD402D4ECB8122850 | |||
| 4536 | Bootstrapper.exe | C:\Users\admin\AppData\Local\Temp\luna\Luna.dll | executable | |
MD5:3A87FB61F757BC7F8AAA333663A55C78 | SHA256:5EA93E328A9D7CB9230ACDDC01B38DC09F3B94792F81F9DB8CA3D30185A94C74 | |||
| 236 | DriverNet.exe | C:\Recovery\OEM\ctfmon.exe | executable | |
MD5:06BE6046BBBD81C71008F62FBA82DB41 | SHA256:7D8CF4A7366244FEFBF18041107D750303A1E06F55632B7CD402D4ECB8122850 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
27
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2144 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.19.96.104:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 2.18.97.227:443 | go.microsoft.com | Akamai International B.V. | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
api.github.com |
| whitelisted |
github.com |
| whitelisted |