| URL: | https://hrinsider.ca/ |
| Full analysis: | https://app.any.run/tasks/23efc6d5-7042-40e5-927c-d4a885b378ec |
| Verdict: | Malicious activity |
| Analysis date: | September 23, 2024, 21:50:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F4A424D83B3AD36AB827EA1E3E14B43A |
| SHA1: | 0FC357BB946E99741FC25B970672D31C9ACED51B |
| SHA256: | EC1710BC055F9051EC2B028ECD4BF967B6C9B80EED82363E414935F0023F3511 |
| SSDEEP: | 3:N8rKKXyj:2bij |
MALICIOUS
Connecting to the Traffic Distribution System (TDS)
- iexplore.exe (PID: 2936)
- svchost.exe (PID: 1060)
SOCGHOLISH has been detected (SURICATA)
- svchost.exe (PID: 1060)
- iexplore.exe (PID: 2936)
SUSPICIOUS
Contacting a server suspected of hosting an Exploit Kit
- svchost.exe (PID: 1060)
- iexplore.exe (PID: 2936)
INFO
Application launched itself
- iexplore.exe (PID: 2016)
Manual execution by a user
- wmpnscfg.exe (PID: 2464)
Reads the computer name
- wmpnscfg.exe (PID: 2464)
Checks supported languages
- wmpnscfg.exe (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://hrinsider.ca/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2016 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
18 425
Read events
18 331
Write events
76
Delete events
18
Modification events
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31133186 | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31133186 | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2016) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
165
Text files
118
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:891FD58F4C3E741FA672B27F2D3432BC | SHA256:01069949CB27F9EE656F35C81282A9BA39D5F75A4E06D8FE3F797AB4B2284983 | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\CabA059.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\TarA05A.tmp | binary | |
MD5:78785956AB4E54D6116D673C3491EDFF | SHA256:C514DBDBB13632CBB378C59086C1EBB0BC9B25FFB0A349F2B052B065C0D913E6 | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\memberpress.min[1].css | text | |
MD5:FDB44808995D67271CC5E730D5128F85 | SHA256:8256CC67832E24AE64F91107126DAD0605B4FB934E647C9FF33433231F826429 | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:125D42263536D9D61C645F6298A82D89 | SHA256:BF818AFA998BD2DB6604A50D18617A21E7A16EDF8994174199A958D979D445E4 | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:BD2BA2EDC48F008D093FE927098A6775 | SHA256:8B43FEB17B76E2D4402BD8866060809BA913AEDD8CC51A1DD52CCBECFC97F0D4 | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | der | |
MD5:7FB5FA1534DCF77F2125B2403B30A0EE | SHA256:33A39E9EC2133230533A686EC43760026E014A3828C703707ACBC150FE40FD6F | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\account[1].css | text | |
MD5:819E8744934568C4F46C181DC810A33B | SHA256:6A6B58DA797EA9BD80D9D16320A70074386ADF51C2D537624E70597BE8E273BD | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:B33F23A9640C8397D18DF1ECA1A9FEE4 | SHA256:F8B449E9B2F6D633CE99F74ABD6E157ABFD97741C754D0418DE01066C136FAE0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
78
DNS requests
40
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2936 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b8207b9ed6f4c065 | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fc6db880c6b3fcec | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.209.170:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 108.138.2.107:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | whitelisted |
2936 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEGmLndtoSYCbEj8Bwl8LkZc%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
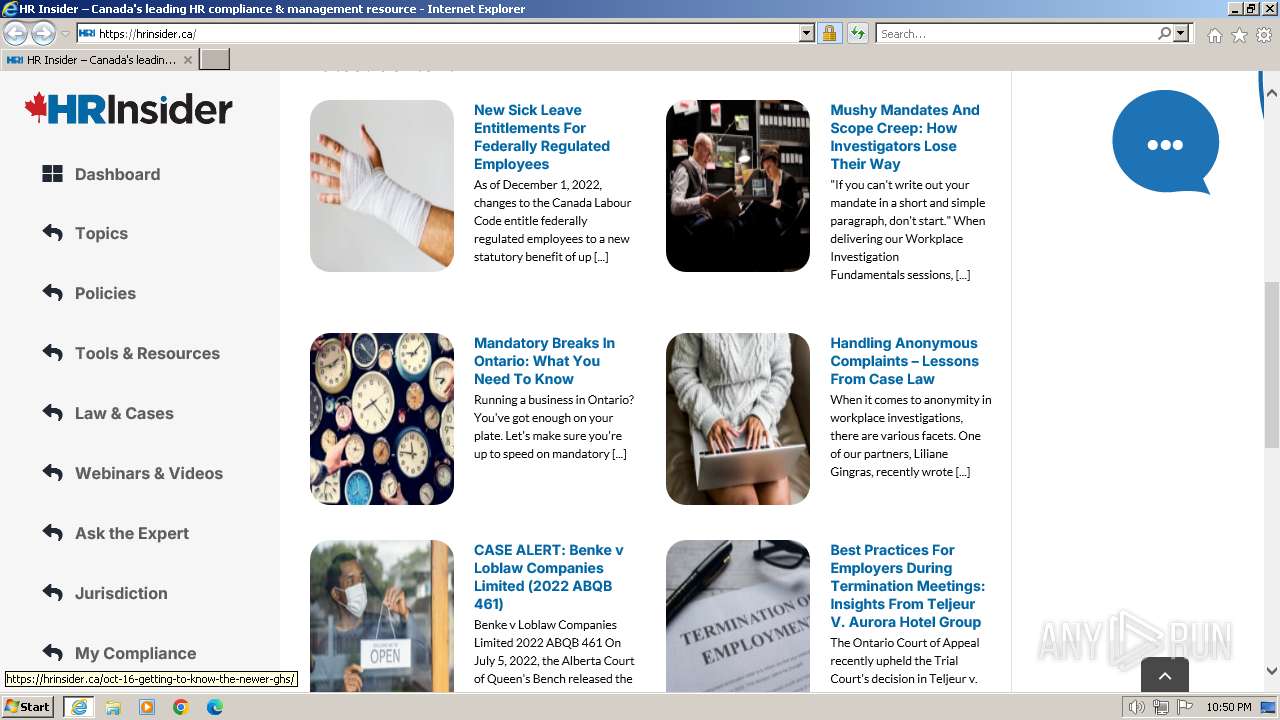
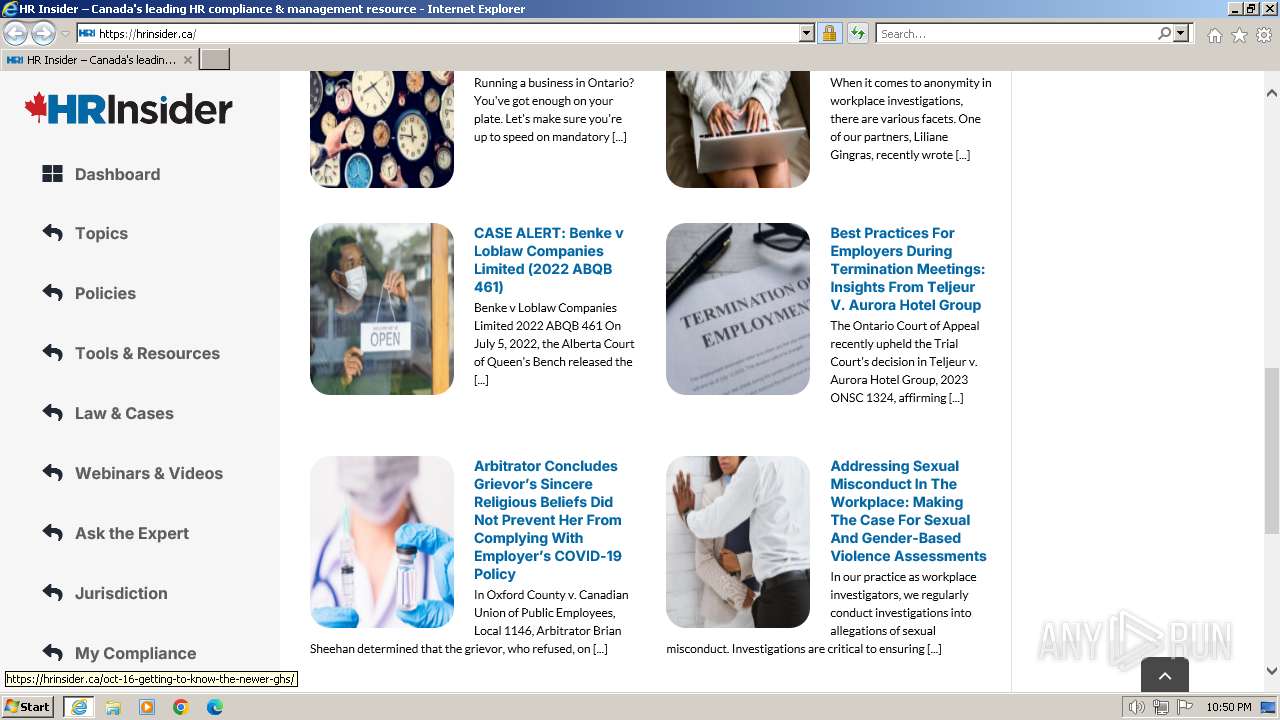
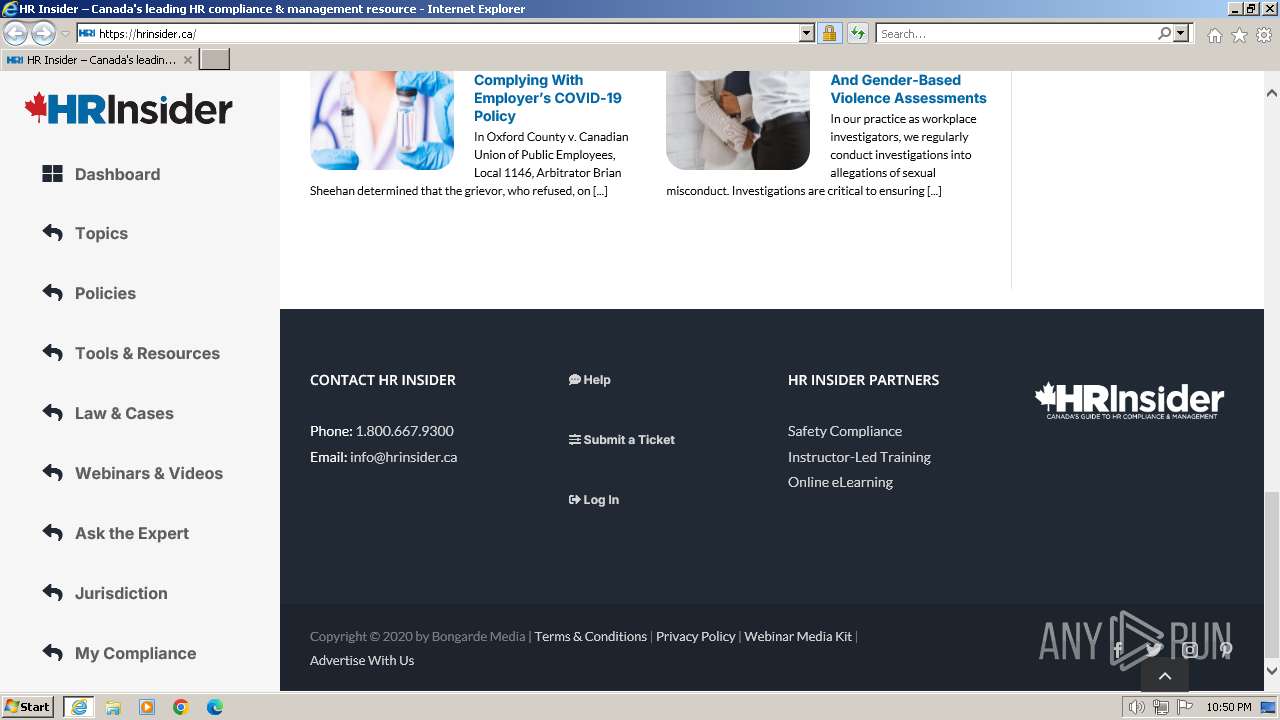
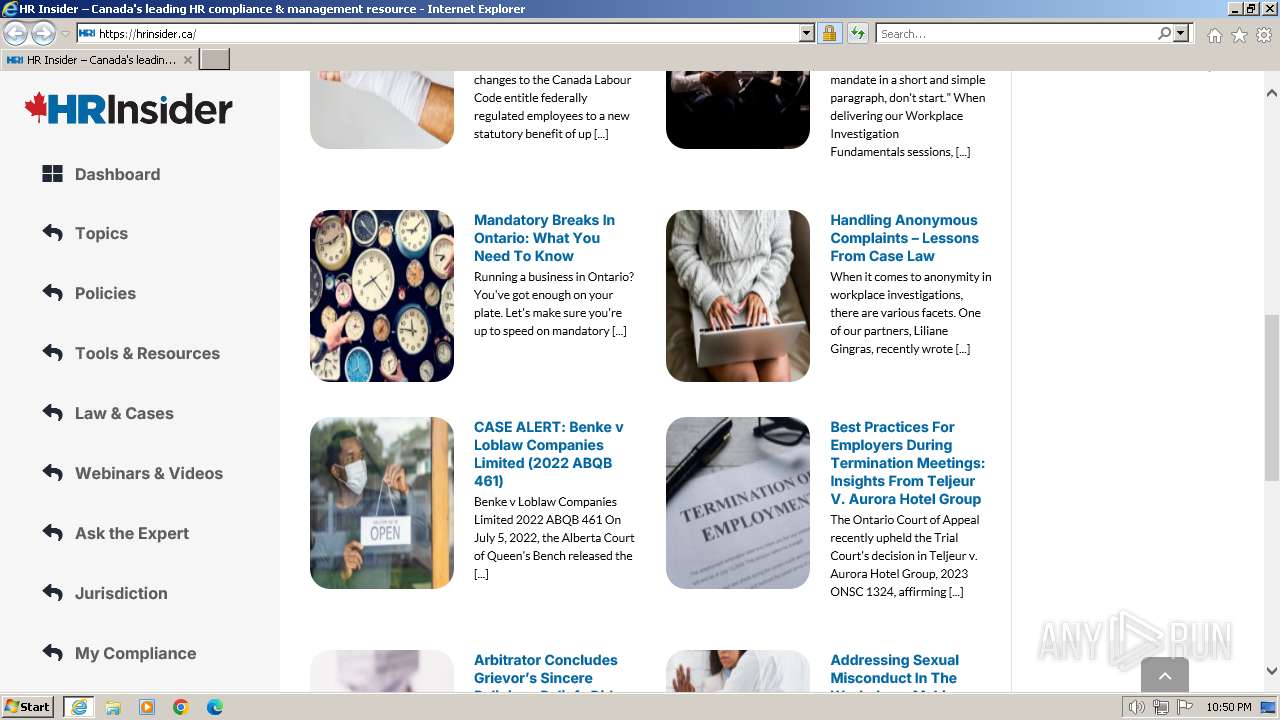
2936 | iexplore.exe | 35.202.225.33:443 | hrinsider.ca | GOOGLE-CLOUD-PLATFORM | US | unknown |
2936 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
— | — | 23.35.209.170:80 | x1.c.lencr.org | AKAMAI-AS | CA | whitelisted |
2936 | iexplore.exe | 104.18.187.31:443 | cdn.jsdelivr.net | CLOUDFLARENET | — | whitelisted |
2936 | iexplore.exe | 142.250.185.170:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
2936 | iexplore.exe | 104.17.24.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | whitelisted |
2936 | iexplore.exe | 104.21.22.102:443 | auth-owlting.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
hrinsider.ca |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
auth-owlting.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
hrinsider.s3.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
1060 | svchost.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT TA569 Middleware Domain in DNS Lookup (auth-owlting .com) |
2936 | iexplore.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT TA569 Middleware Domain in TLS SNI (auth-owlting .com) |
2936 | iexplore.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT TA569 Middleware Domain in TLS SNI (auth-owlting .com) |
1060 | svchost.exe | A Network Trojan was detected | ET MALWARE SocGholish Domain in DNS Lookup (pluralism .themancav .com) |
2936 | iexplore.exe | A Network Trojan was detected | ET MALWARE SocGholish Domain in TLS SNI (pluralism .themancav .com) |
2936 | iexplore.exe | A Network Trojan was detected | ET MALWARE SocGholish Domain in TLS SNI (pluralism .themancav .com) |
2936 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |