| File name: | to_any_run_PowerShall.txt |
| Full analysis: | https://app.any.run/tasks/27f83226-abb2-46b7-a2e4-b3e1268239fc |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2018, 12:58:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | B45B8D5FDDCD48E8B62450BCA12613F8 |
| SHA1: | 89AAB9FDD558F22EAAC8490C19E081BCF6B48DBE |
| SHA256: | EBEC6CB03304E69FA5C76EF37E7252453116A7826EC1AC100859314404B139EA |
| SSDEEP: | 6:oRFe2jIngXIq5lyYjQO0cb2ZzD5vIJSon:oRFjjInwInppcqFVHon |
MALICIOUS
Application was dropped or rewritten from another process
- 7za.exe (PID: 2724)
- 7za.exe (PID: 3292)
Executes PowerShell scripts
- cmd.exe (PID: 3060)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2760)
- 7za.exe (PID: 2724)
- 7za.exe (PID: 3292)
Creates files in the user directory
- powershell.exe (PID: 2760)
- powershell.exe (PID: 3852)
INFO
Reads settings of System Certificates
- powershell.exe (PID: 2760)
- powershell.exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2436 | "C:\Windows\System32\setx.exe" ChocolateyLastPathUpdate "Tue Dec 18 12:58:53 2018" | C:\Windows\System32\setx.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Setx - Sets environment variables Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2664 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES2E17.tmp" "c:\Users\admin\AppData\Local\Temp\CSC2E16.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
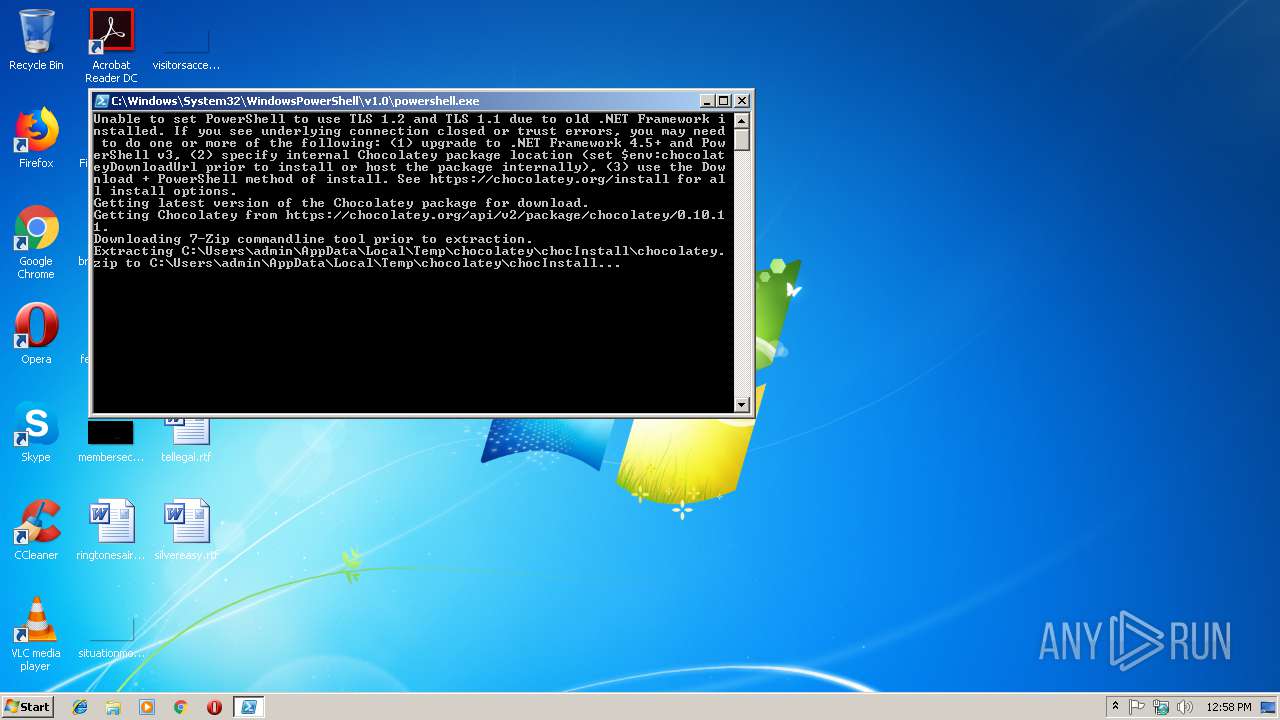
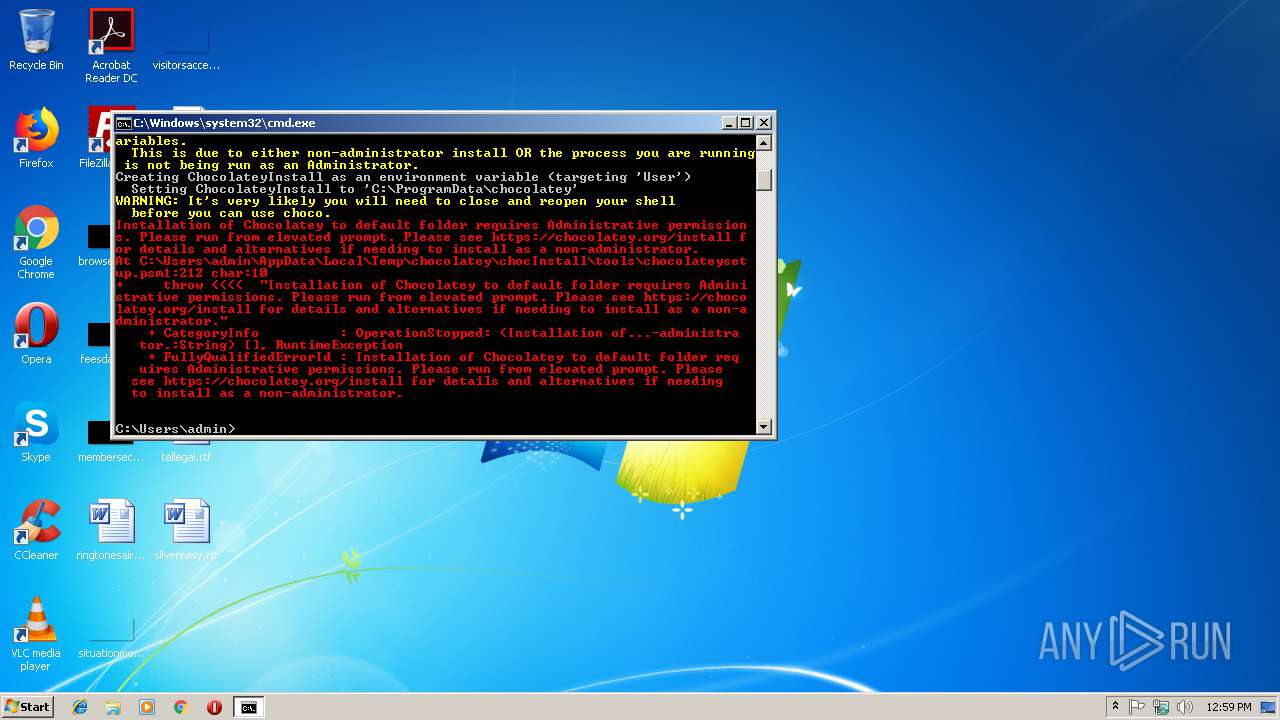
| 2724 | "C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\7za.exe" x -o"C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall" -bd -y "C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\chocolatey.zip" | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\7za.exe | powershell.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
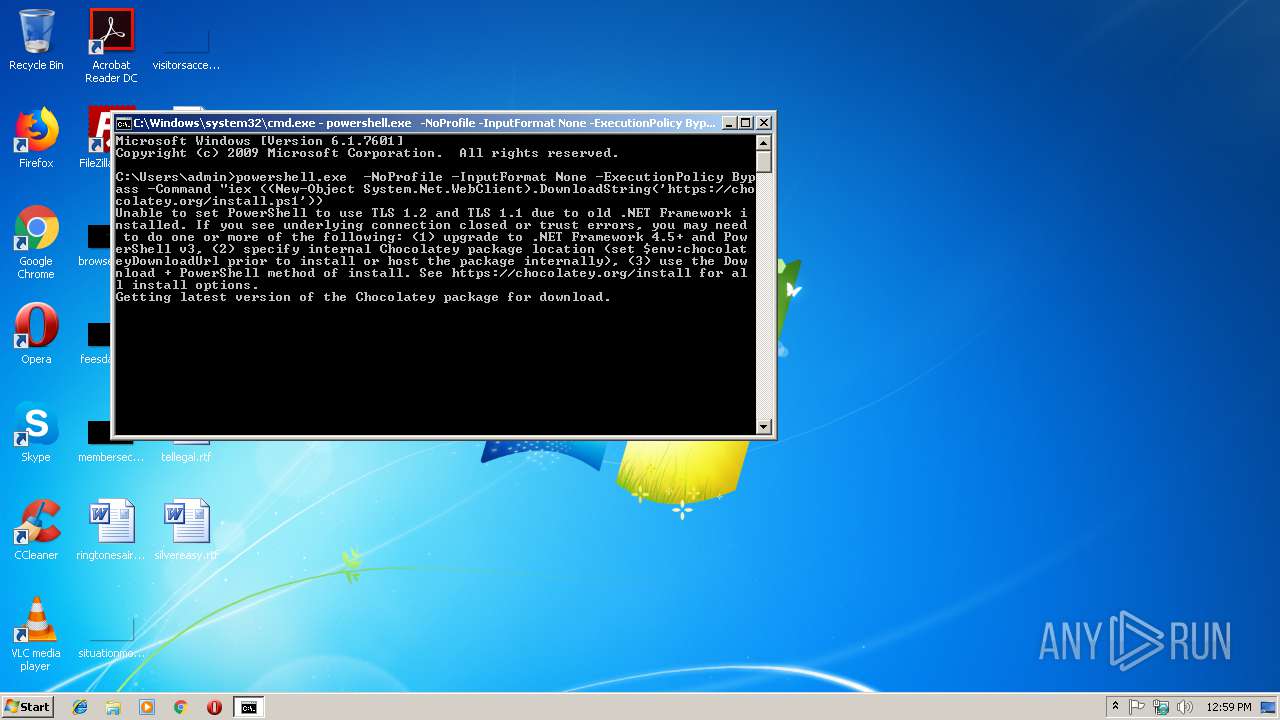
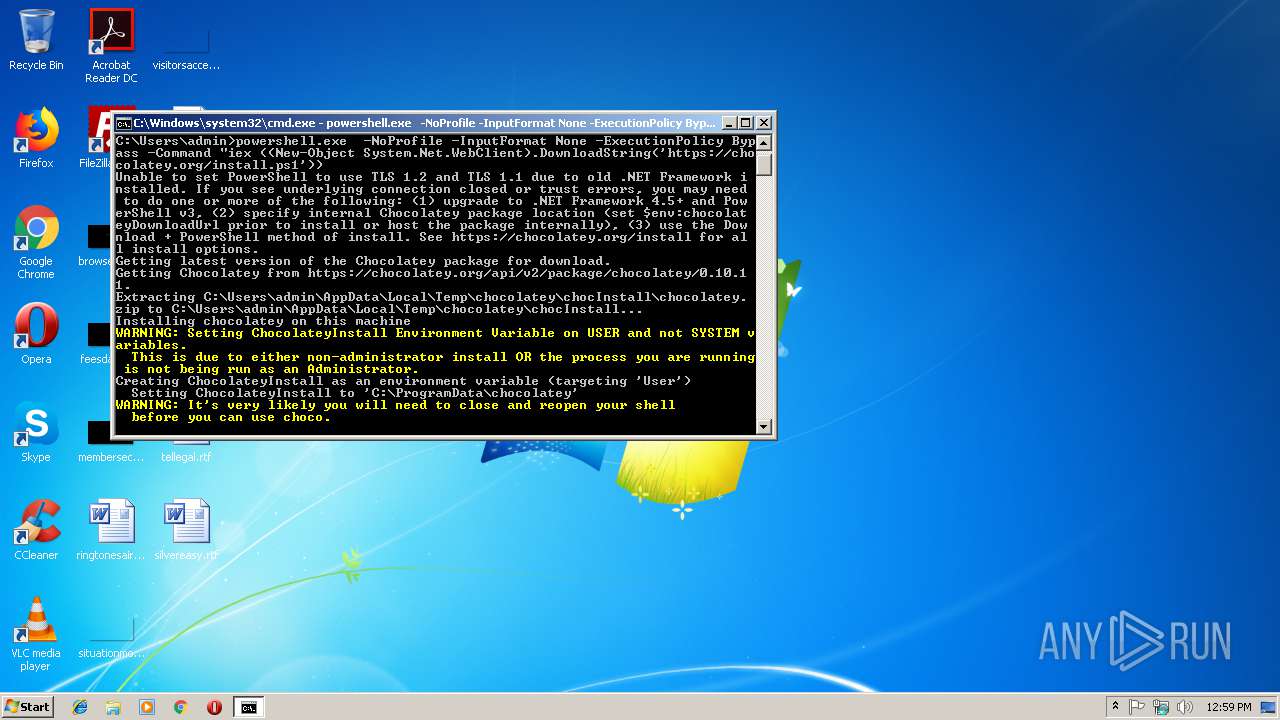
| 2760 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -InputFormat None -ExecutionPolicy Bypass -Command "iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1')) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3016 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\hsvnoc38.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 3060 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3252 | "C:\Windows\System32\setx.exe" ChocolateyLastPathUpdate "Tue Dec 18 12:59:27 2018" | C:\Windows\System32\setx.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Setx - Sets environment variables Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | "C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\7za.exe" x -o"C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall" -bd -y "C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\chocolatey.zip" | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\7za.exe | powershell.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
| 3852 | powershell.exe -NoProfile -InputFormat None -ExecutionPolicy Bypass -Command "iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1')) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3908 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\v80mf7pe.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
Total events
586
Read events
439
Write events
146
Delete events
1
Modification events
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2760) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
29
Suspicious files
6
Text files
130
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\LMWIRFR2RLNGYOUVBTCE.temp | — | |
MD5:— | SHA256:— | |||
| 2760 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF199800.TMP | binary | |
MD5:— | SHA256:— | |||
| 2760 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2724 | 7za.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\chocolatey.nuspec | xml | |
MD5:EF4F3D93A25A14882B5C2BC265AACB4B | SHA256:C20DE5F1045EB23F364C38139E4F6D01BFF28D83690AF269D86C7141A61444E6 | |||
| 2724 | 7za.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\tools\chocolateyInstall\helpers\ChocolateyTabExpansion.ps1 | text | |
MD5:1608021FB1C94705D142EDF7ABE91EE7 | SHA256:CD12832CA479E1B169AFBD5C42D5665B0C2C2A02E9723524A10E37FC53799AB8 | |||
| 2724 | 7za.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\tools\chocolateyInstall.ps1 | text | |
MD5:BA6315B965CD598537CCBCE10E5279CF | SHA256:9E5D5358FCE2C06C27A2DD5DAD9ECD921F58E122CD051CFF01723F93E7CBD3BF | |||
| 2724 | 7za.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\tools\chocolateysetup.psm1 | text | |
MD5:A33EC0E0467EF4DB75AF97FC74F07D9B | SHA256:DF18B15F15AFF41697C8C1C2FD9E4DFA14F46F30AC2749292E2AB82B21FABB91 | |||
| 2724 | 7za.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\tools\chocolateyInstall\helpers\chocolateyInstaller.psm1 | text | |
MD5:C182F16ECA18063977C8884F5F45ADCD | SHA256:49D809792D9B2C48E62E5940830C6E5563104DB78AECAD36B6A29B17B84C9400 | |||
| 2760 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\7za.exe | executable | |
MD5:744D0E63BCB20438DD3EFCD764503490 | SHA256:77613CCA716EDF68B9D5BAB951463ED7FADE5BC0EC465B36190A76299C50F117 | |||
| 2724 | 7za.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocInstall\tools\chocolateyInstall\LICENSE.txt | text | |
MD5:B4ECFC2FF4822CE40435ADA0A02D4EC5 | SHA256:A42AC97C0186E34BDC5F5A7D87D00A424754592F0EC80B522A872D630C1E870A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2760 | powershell.exe | 104.20.73.28:443 | chocolatey.org | Cloudflare Inc | US | shared |
3852 | powershell.exe | 104.20.73.28:443 | chocolatey.org | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
chocolatey.org |
| whitelisted |
packages.chocolatey.org |
| suspicious |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|