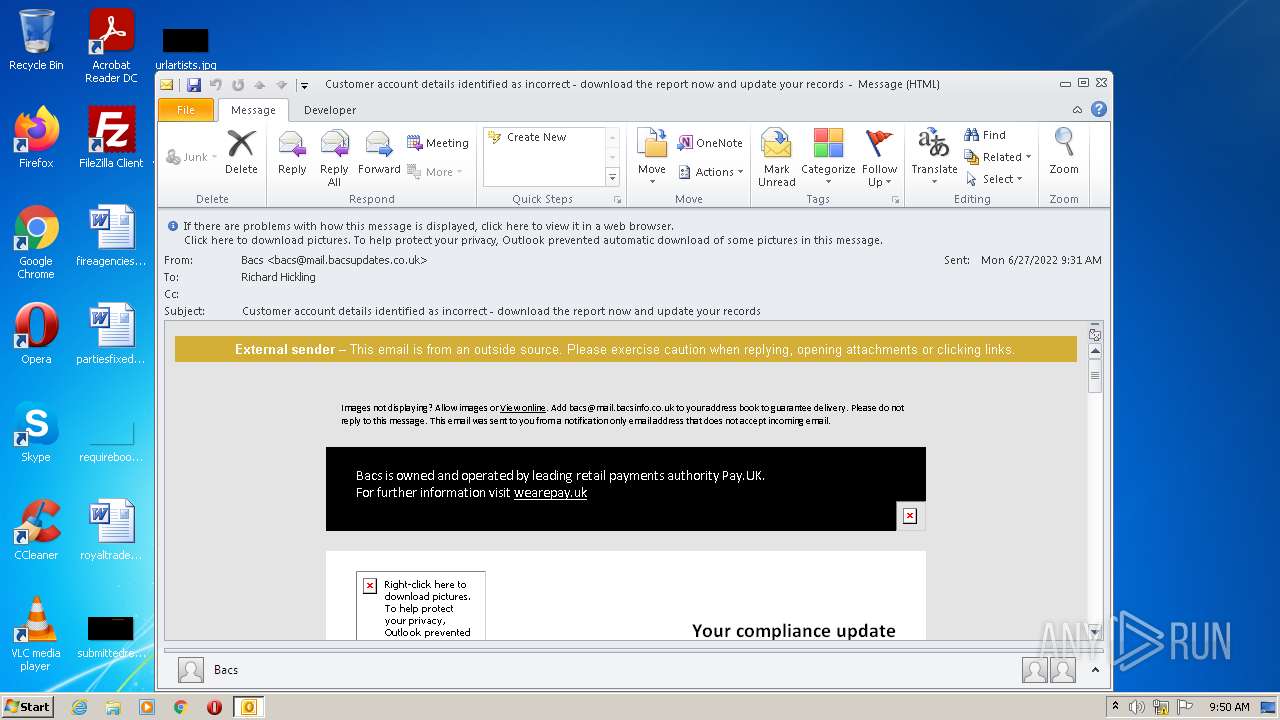
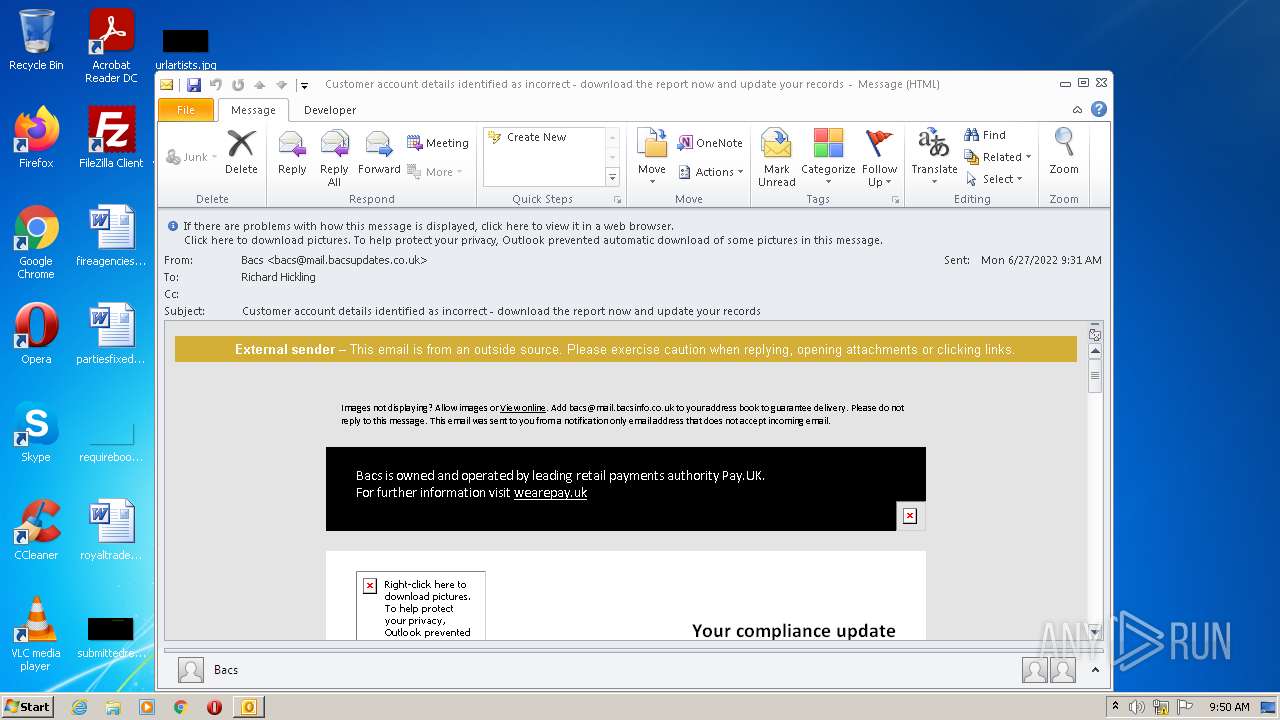
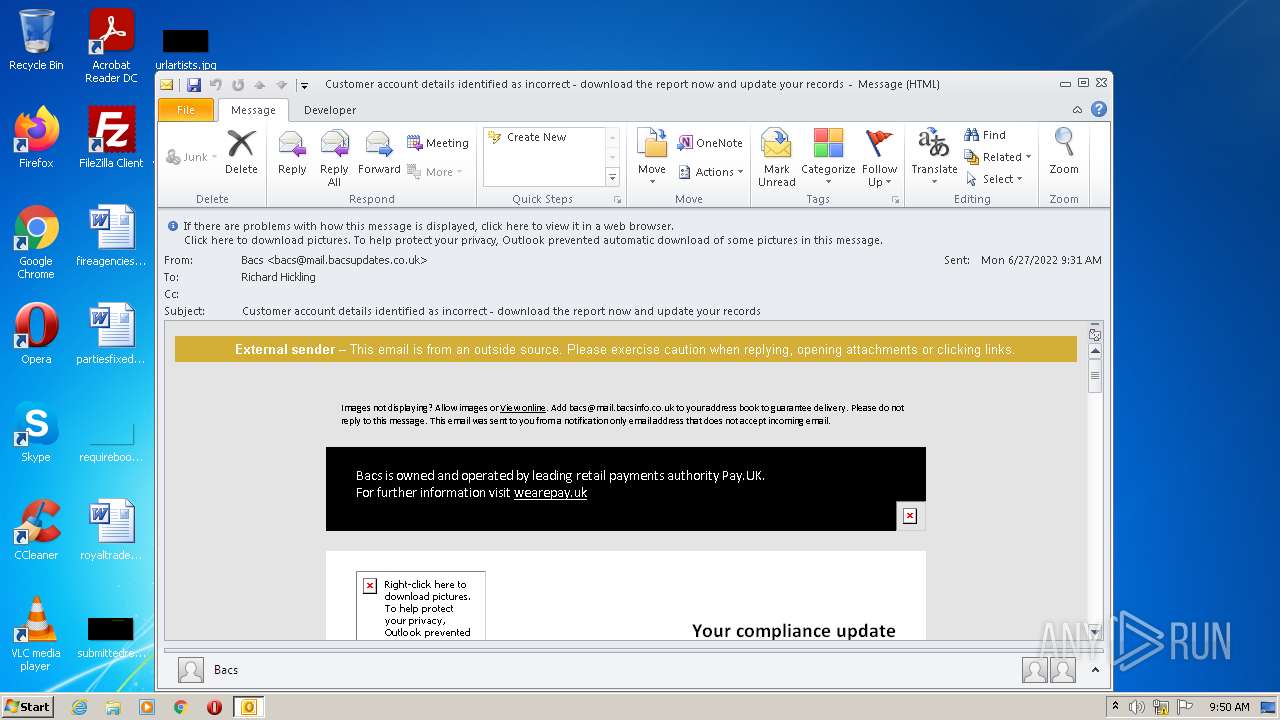
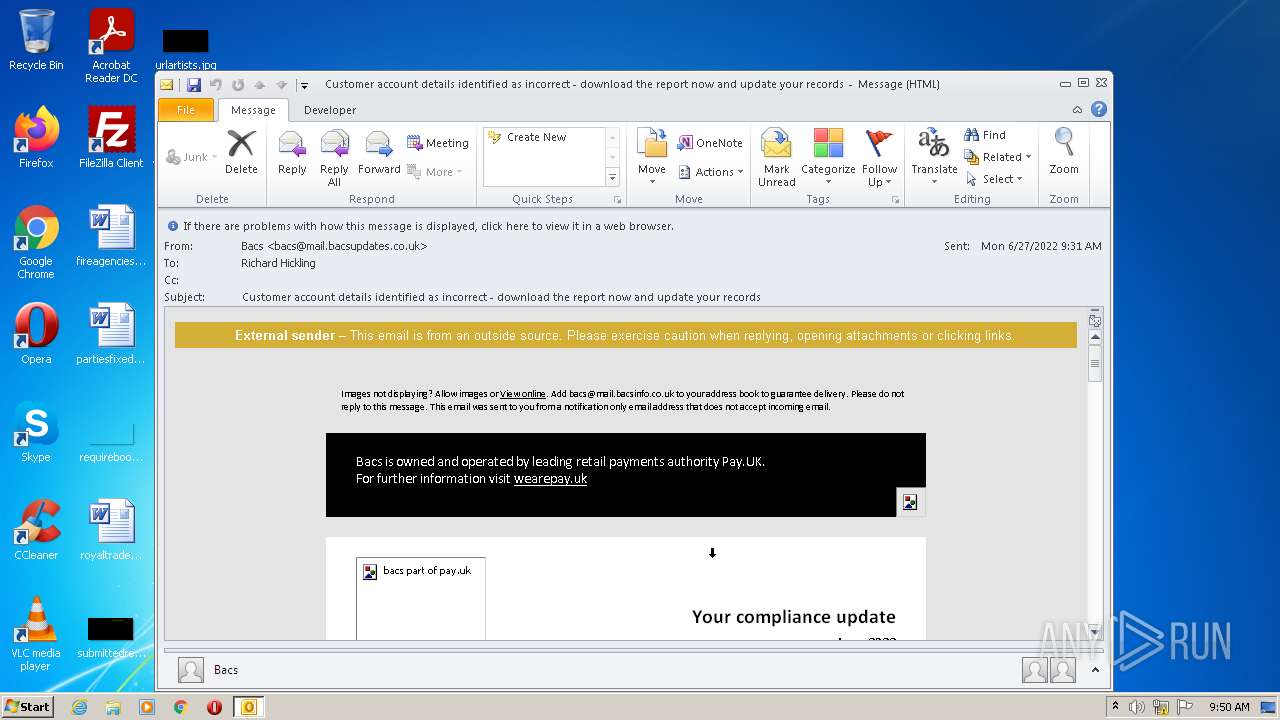
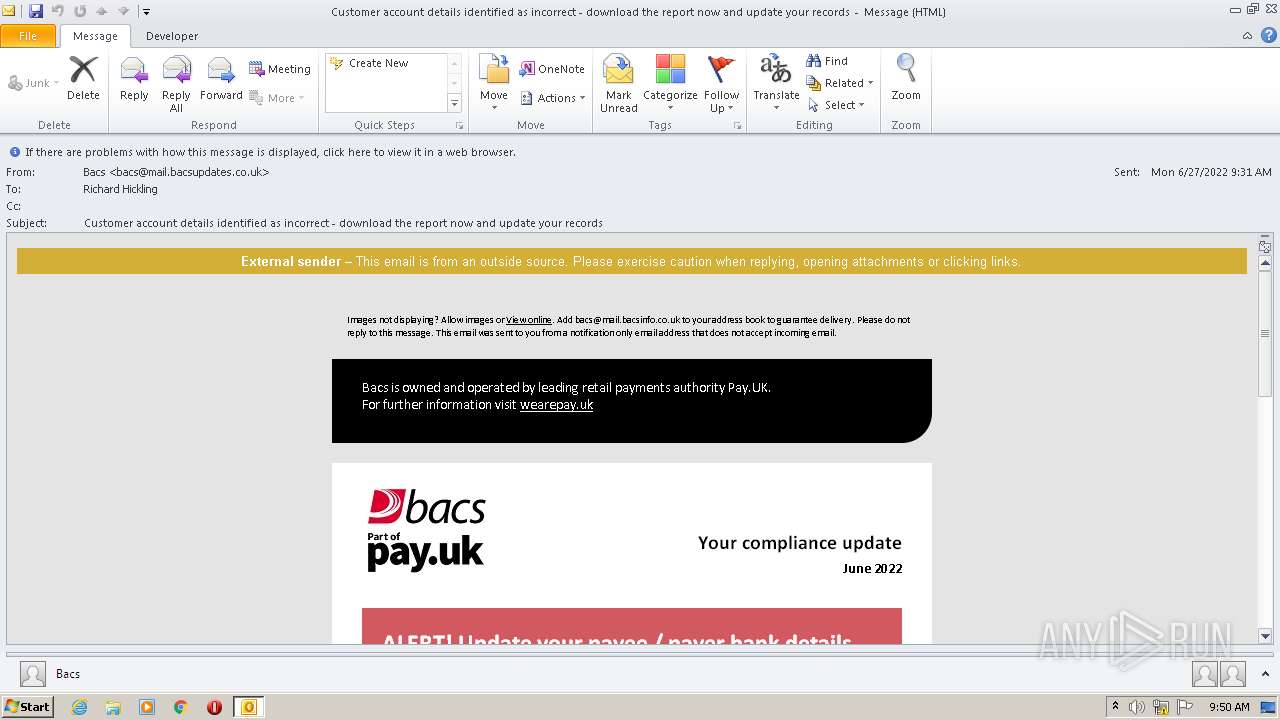
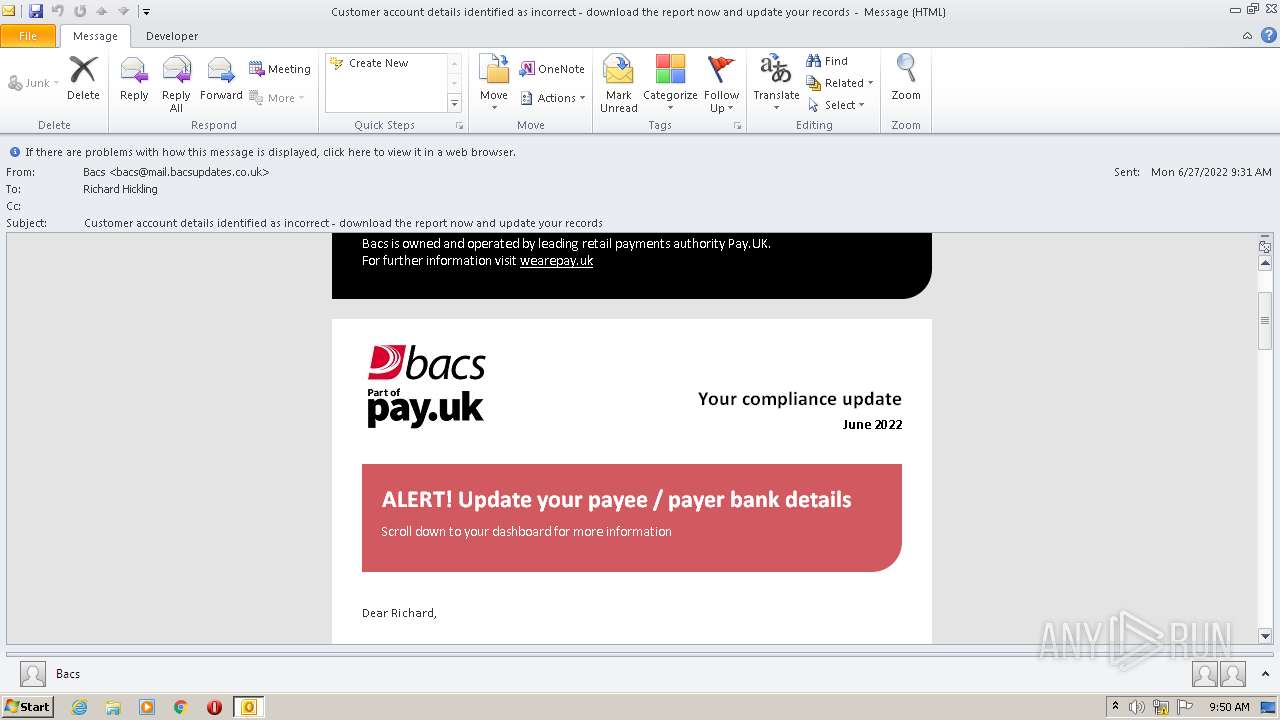
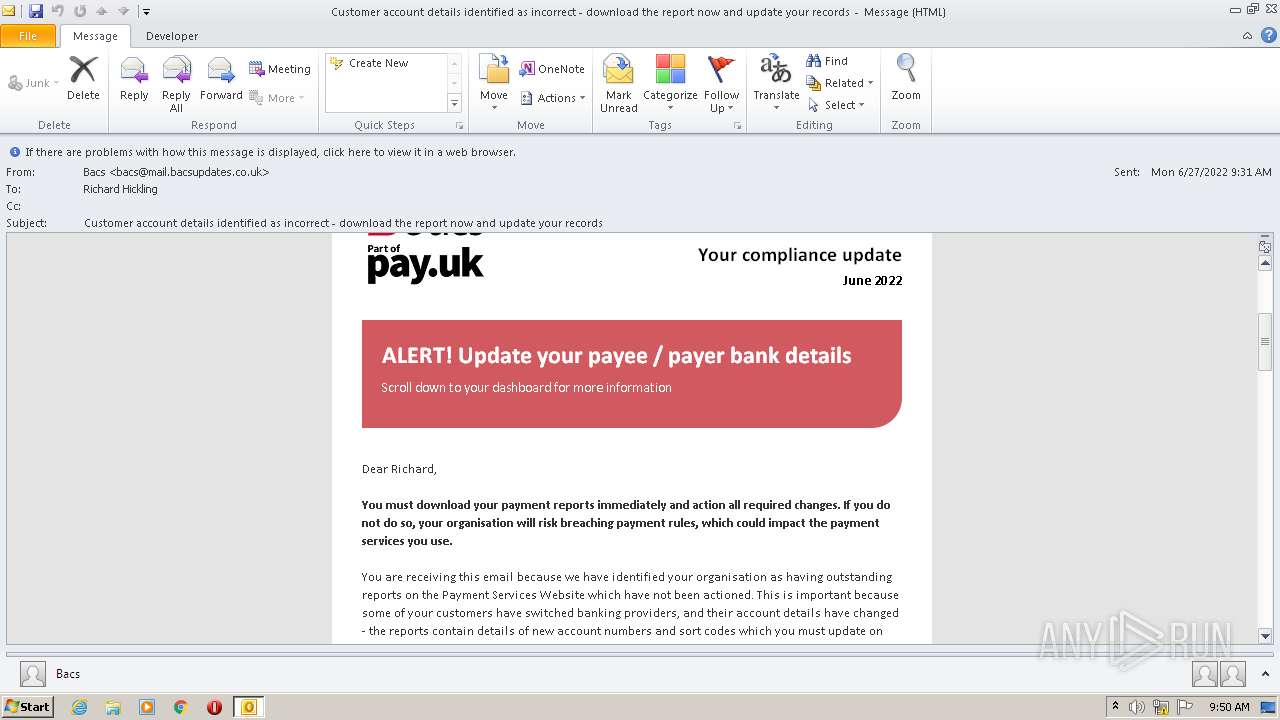
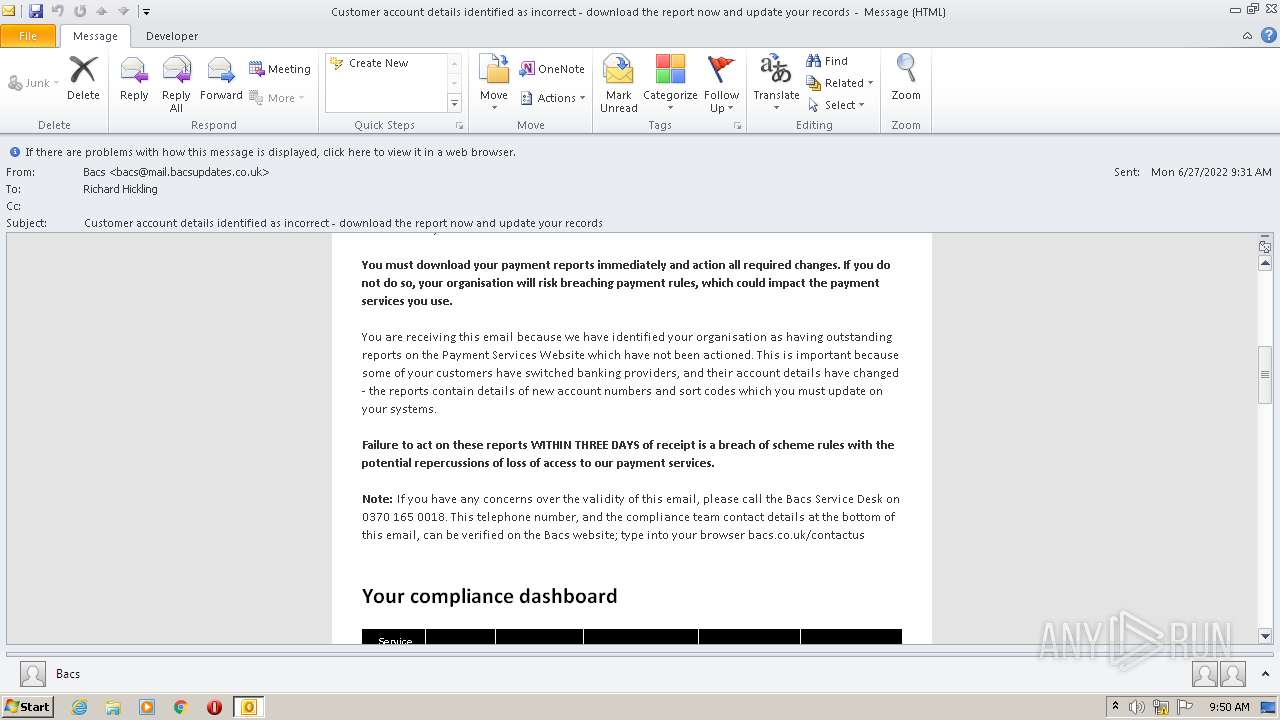
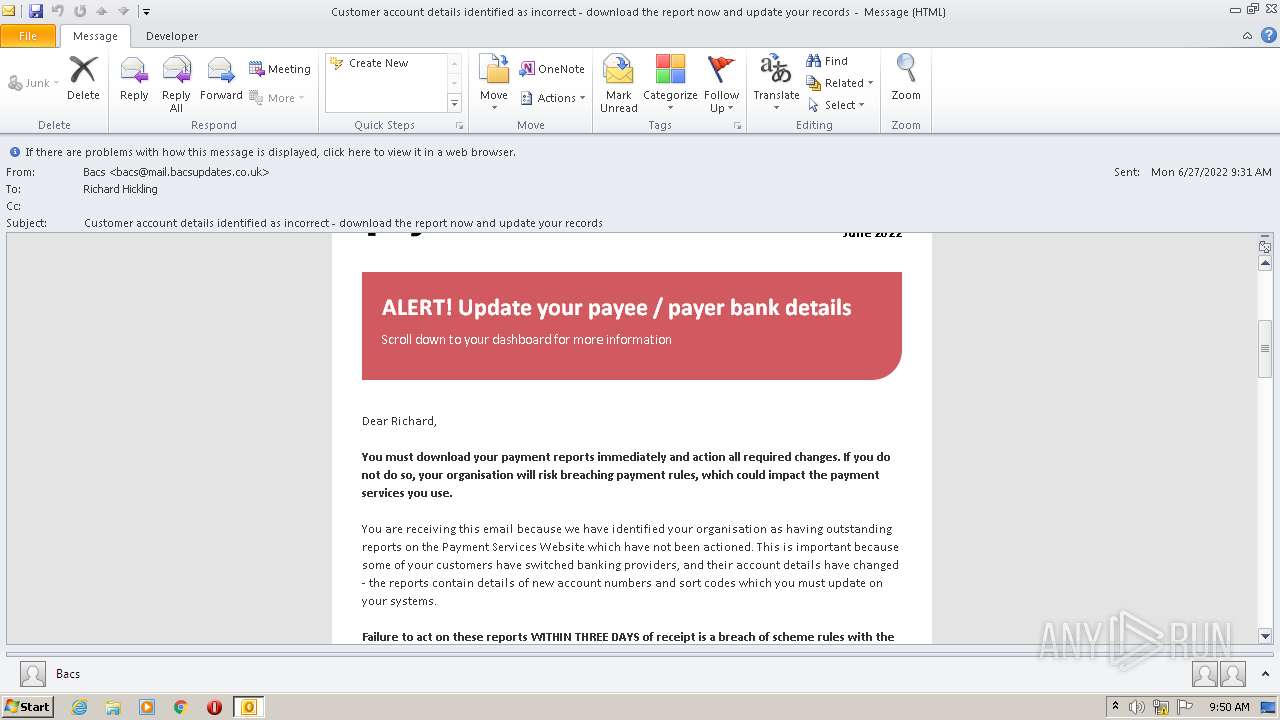
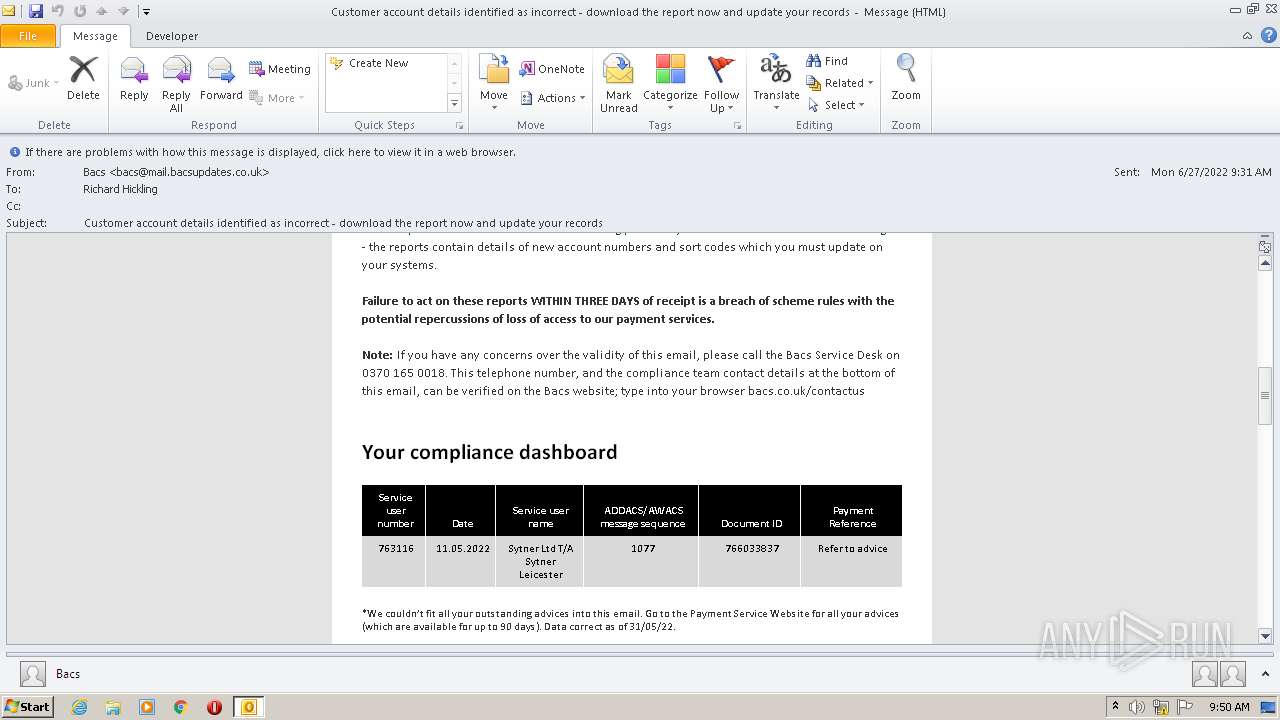
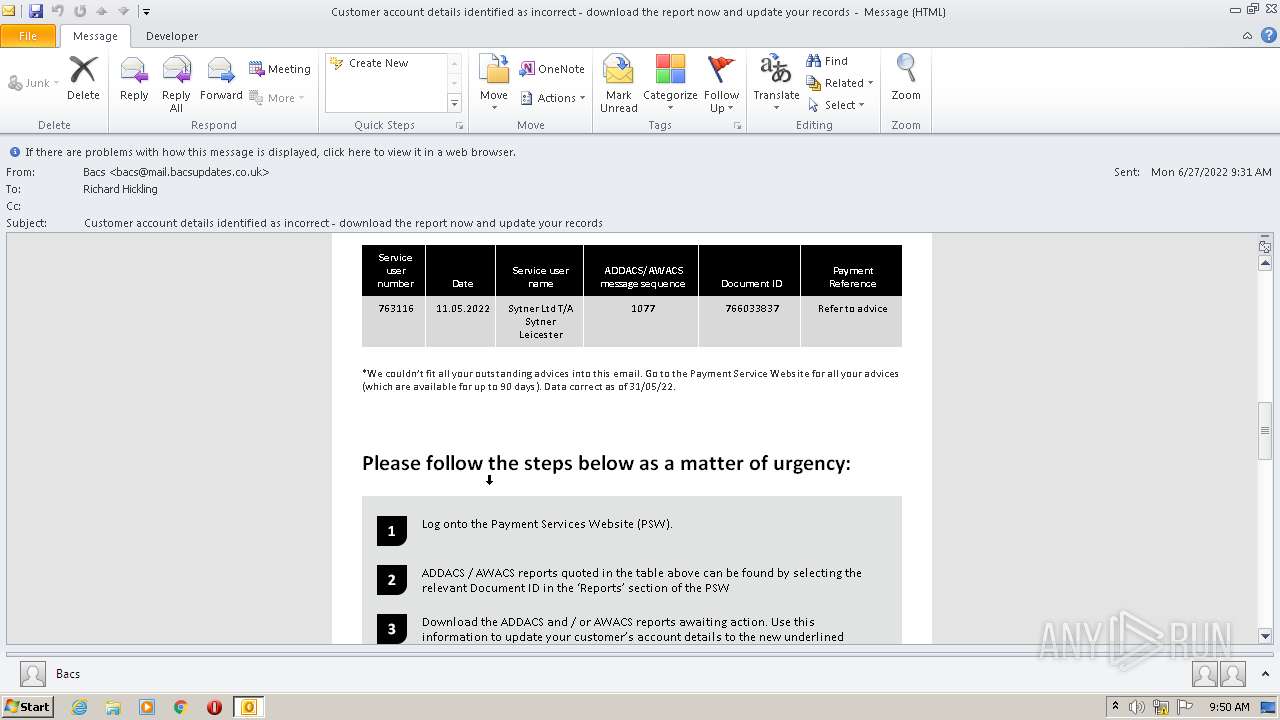
| File name: | Potential Phish - 2022-06-27T093947.361.eml |
| Full analysis: | https://app.any.run/tasks/4e45897d-2134-4504-818a-d0fd347bff1e |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 08:49:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | multipart/alternative; boundary="===============4065689632319861873==", ASCII text, with very long lines, with CRLF line terminators |
| MD5: | FFB228412B92A827766EE53EDF603A3C |
| SHA1: | 3A72EC804CA7BA7F173ABD2AB68E611C09B1BEF3 |
| SHA256: | EBD56EA6E53219C3683C13B4B4D0A9F914511FCCC0164999A8EFC84A3021BA79 |
| SSDEEP: | 1536:o/hnE5kvpzo66YdrwBkke/BB3rt1FKC6Rl:KnEK6ceSr14C6Rl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 1396)
Searches for installed software
- OUTLOOK.EXE (PID: 1396)
Reads the computer name
- OUTLOOK.EXE (PID: 1396)
Reads Microsoft Outlook installation path
- OUTLOOK.EXE (PID: 1396)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 1396)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1396)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3872)
INFO
Checks supported languages
- control.exe (PID: 2548)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 3872)
- chrome.exe (PID: 2912)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 1992)
- chrome.exe (PID: 3340)
- chrome.exe (PID: 3264)
- chrome.exe (PID: 3252)
- chrome.exe (PID: 920)
- chrome.exe (PID: 2064)
- chrome.exe (PID: 3816)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 3336)
- chrome.exe (PID: 1776)
- chrome.exe (PID: 1368)
- chrome.exe (PID: 3864)
Manual execution by user
- control.exe (PID: 2548)
Application launched itself
- chrome.exe (PID: 3872)
Reads the computer name
- chrome.exe (PID: 2728)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 3872)
- control.exe (PID: 2548)
- chrome.exe (PID: 3340)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 3816)
- chrome.exe (PID: 1368)
- chrome.exe (PID: 3864)
Reads the hosts file
- chrome.exe (PID: 3872)
- chrome.exe (PID: 2780)
Reads settings of System Certificates
- chrome.exe (PID: 2780)
Reads the date of Windows installation
- chrome.exe (PID: 3816)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 6) (100) |
|---|
Total processes
59
Monitored processes
19
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3388 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1036 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1396 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Potential Phish - 2022-06-27T093947.361.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=536 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2304 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3008 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2548 | "C:\Windows\system32\control.exe" /name Microsoft.DefaultPrograms | C:\Windows\system32\control.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1064 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1052,12571149182876173701,9503528578143003216,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1220 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6edcd988,0x6edcd998,0x6edcd9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
17 941
Read events
17 241
Write events
677
Delete events
23
Modification events
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
140
Text files
133
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9570.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\corner-30-red[1].png | image | |
MD5:— | SHA256:— | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\corner-30-black[1].png | image | |
MD5:— | SHA256:— | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ConversationPrefs_2_0F242EEAA0585B468D62D25D2E18C8E8.dat | xml | |
MD5:57F30B1BCA811C2FCB81F4C13F6A927B | SHA256:612BAD93621991CB09C347FF01EC600B46617247D5C041311FF459E247D8C2D3 | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TCPrefs_2_32F083B0352A6746ACEDD11F1831987F.dat | xml | |
MD5:F194B1FA12F9B6F46A47391FAE8BEEC2 | SHA256:FCD8D7E030BE6EA7588E5C6CB568E3F1BDFC263942074B693942A27DF9521A74 | |||
| 1396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\number-black-3[1].png | image | |
MD5:600D8AE4B29F2E48108CD86F201BCD92 | SHA256:99E920E027373E08751DC8C0C4C8776DDCE852C8B0D80AB4631626E405A879BD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
53
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
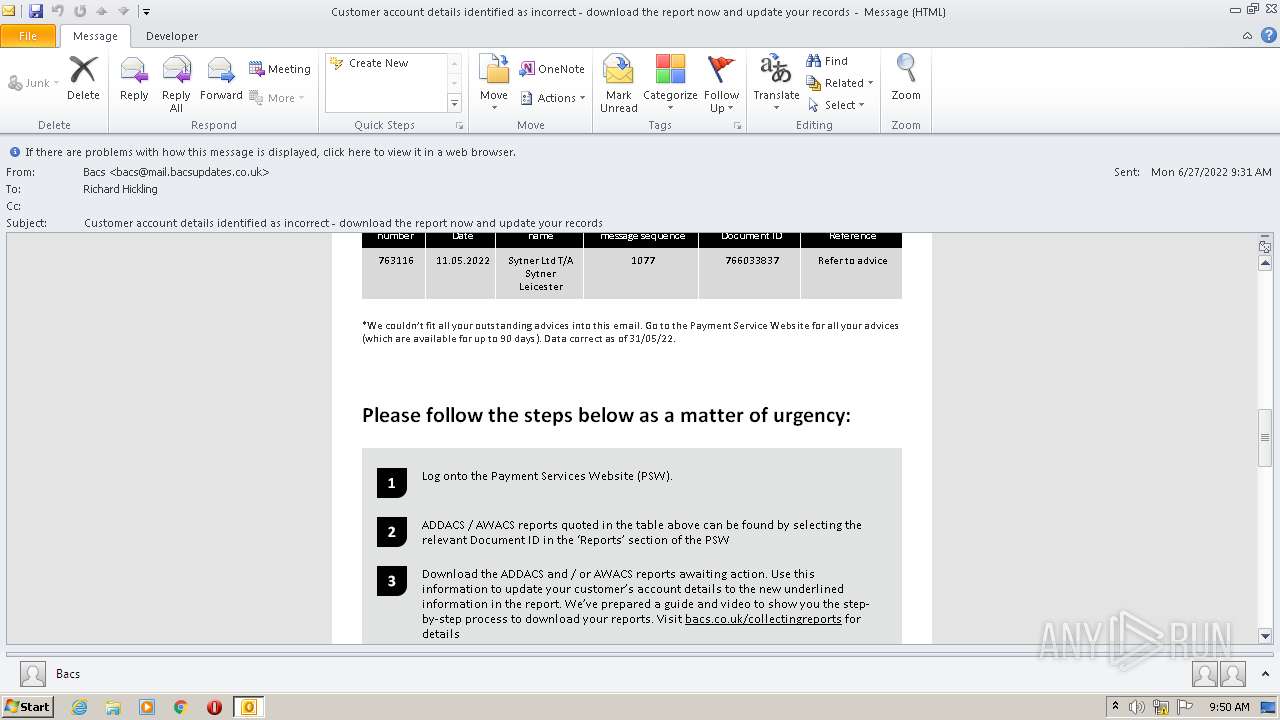
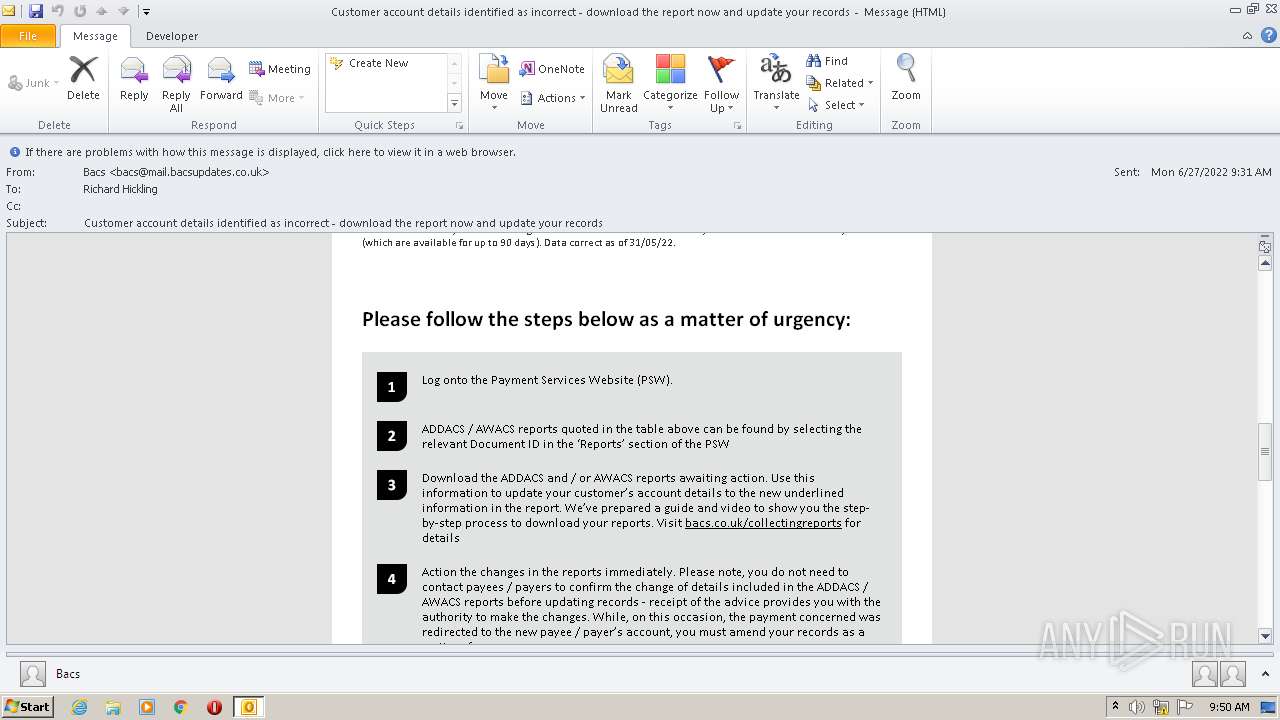
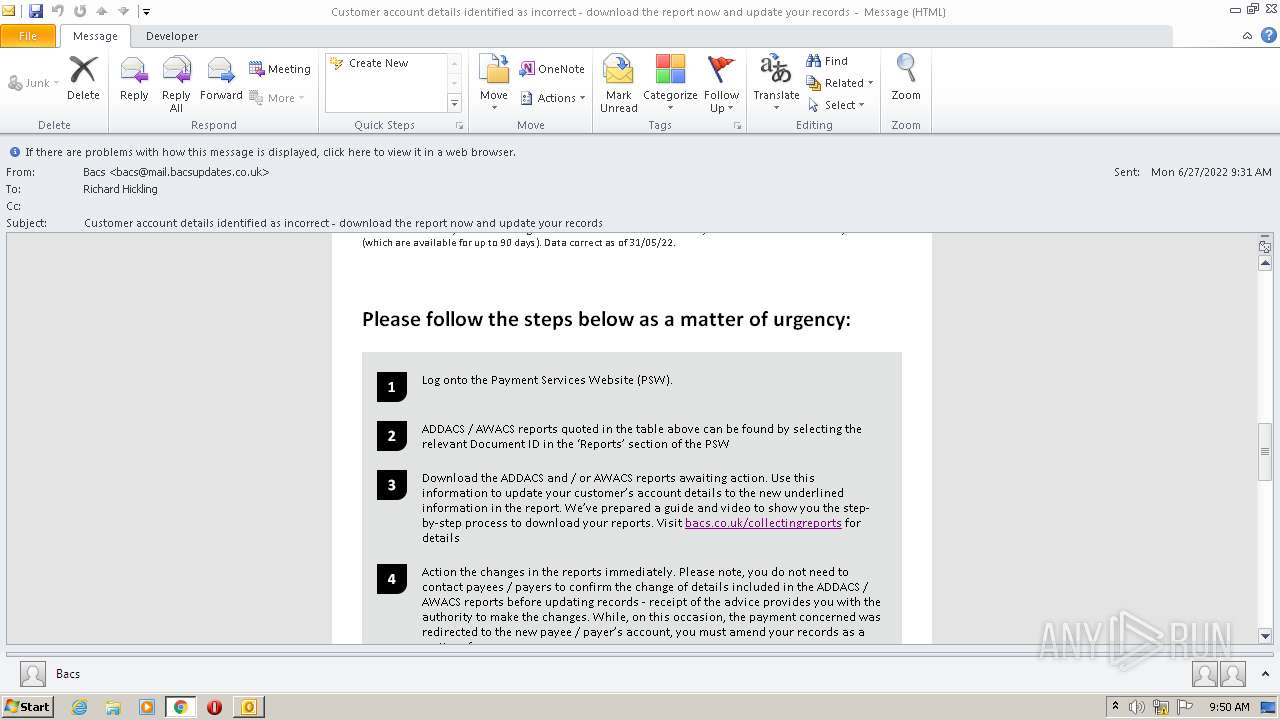
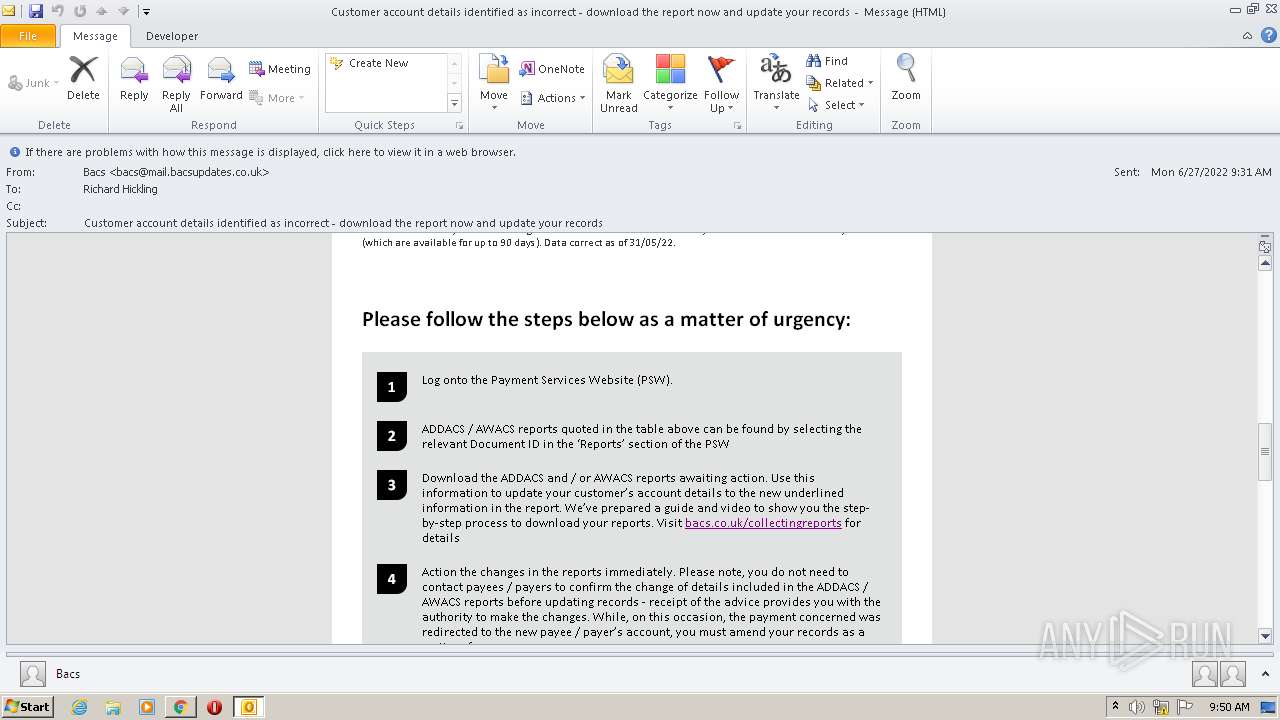
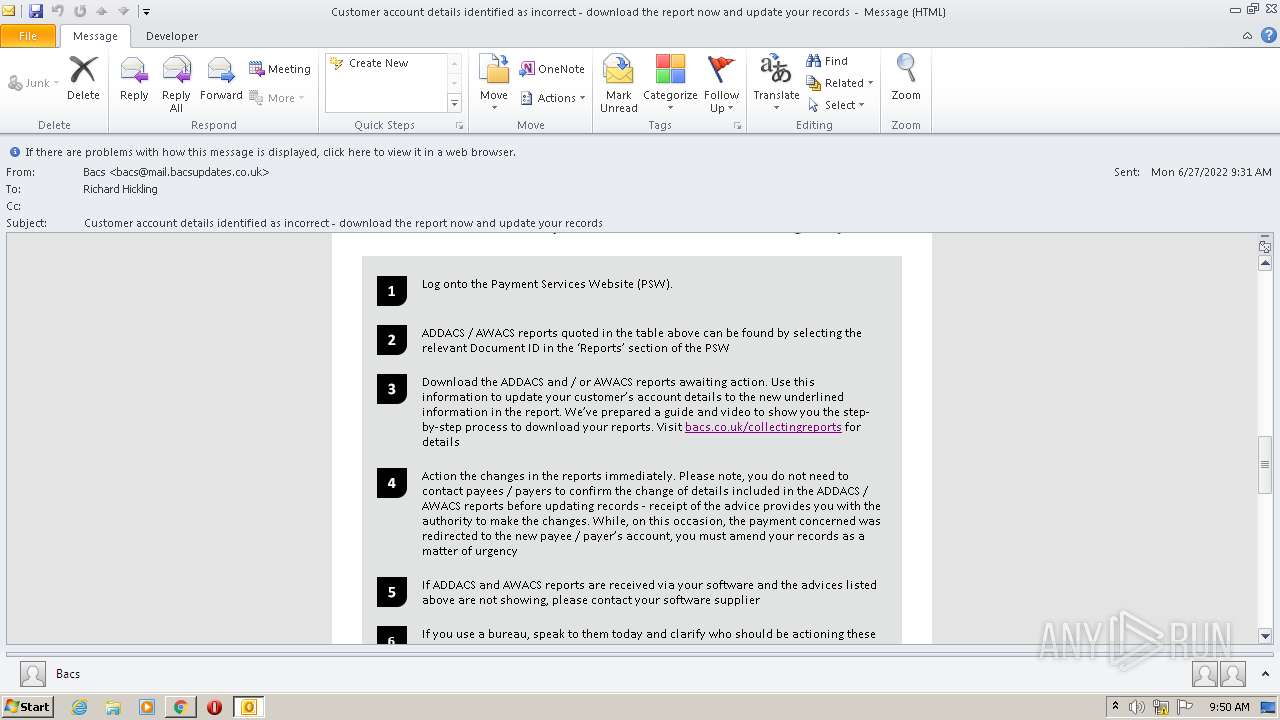
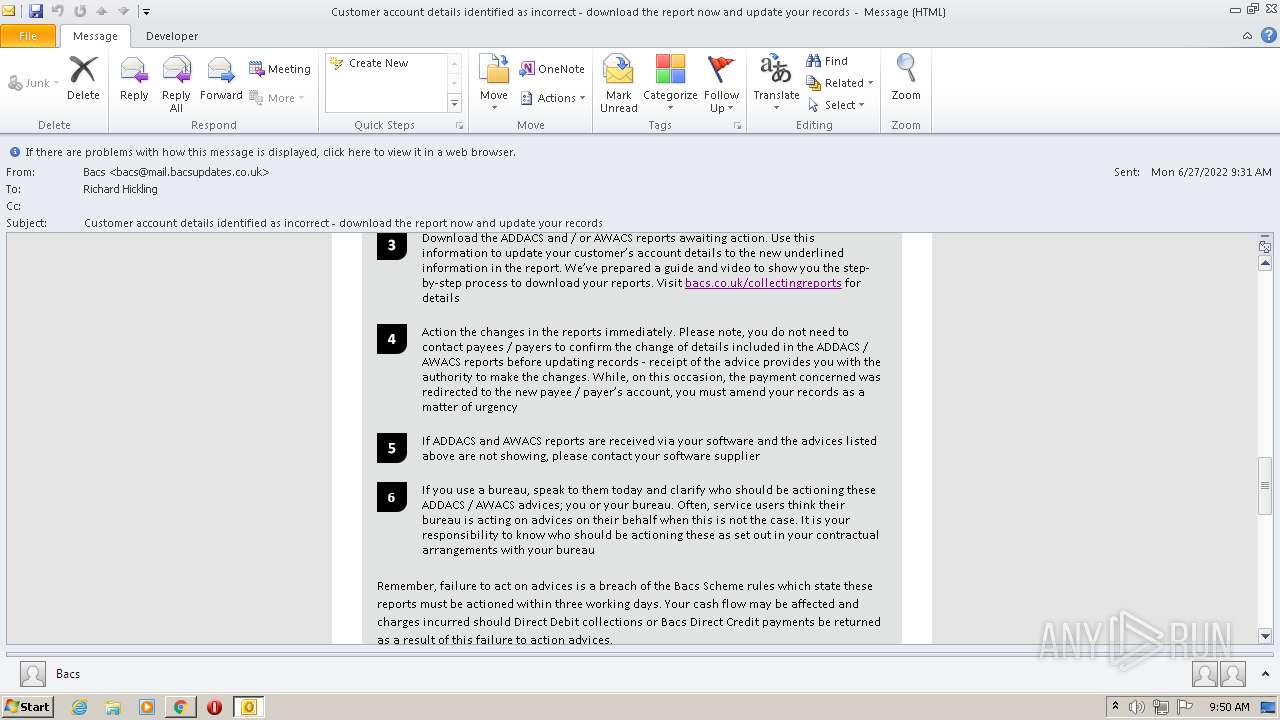
2780 | chrome.exe | GET | 302 | 195.140.186.103:80 | http://mail.bacsupdates.co.uk/re?l=D0Iytmfz7I9ne1qozI2ITl4whc0p0&s=FGJHFHGFCKAKEOHH | DE | — | — | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827202/corner-30-black.png | DE | image | 554 b | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827210/corner-30-green.png | DE | image | 542 b | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827211/corner-30-yellow.png | DE | image | 544 b | whitelisted |
2780 | chrome.exe | GET | 200 | 8.247.116.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?771d3864b35f5c2a | US | compressed | 60.0 Kb | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827208/number-black-4.png | DE | image | 524 b | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827203/Bacs+logo+new+email+templates+2.jpg | DE | image | 8.00 Kb | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827213/linkedin.png | DE | image | 818 b | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827215/payuk-logo-2x.png | DE | image | 9.32 Kb | whitelisted |
1396 | OUTLOOK.EXE | GET | 200 | 195.140.186.100:80 | http://mail.bacsupdates.co.uk/imgproxy/img/769827202/corner-30-black.png | DE | image | 554 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1396 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
1396 | OUTLOOK.EXE | 195.140.186.100:80 | mail.bacsupdates.co.uk | Global Access Internet Services GmbH | DE | suspicious |
2780 | chrome.exe | 195.140.186.103:80 | mail.bacsupdates.co.uk | Global Access Internet Services GmbH | DE | suspicious |
— | — | 195.140.186.103:80 | mail.bacsupdates.co.uk | Global Access Internet Services GmbH | DE | suspicious |
2780 | chrome.exe | 142.251.37.109:443 | accounts.google.com | Google Inc. | US | unknown |
— | — | 195.140.186.100:80 | mail.bacsupdates.co.uk | Global Access Internet Services GmbH | DE | suspicious |
2780 | chrome.exe | 142.250.184.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
2780 | chrome.exe | 172.217.18.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2780 | chrome.exe | 142.251.36.131:443 | clientservices.googleapis.com | Google Inc. | US | unknown |
2780 | chrome.exe | 142.251.36.65:443 | clients2.googleusercontent.com | Google Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
mail.bacsupdates.co.uk |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
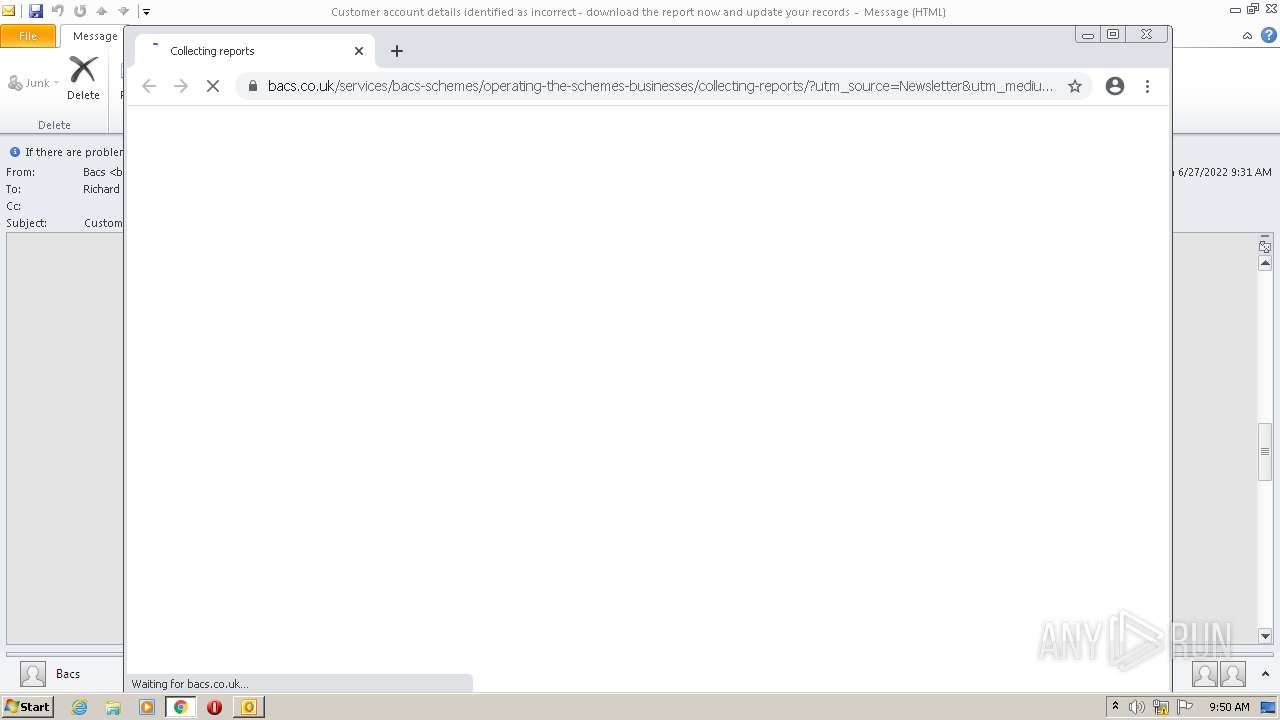
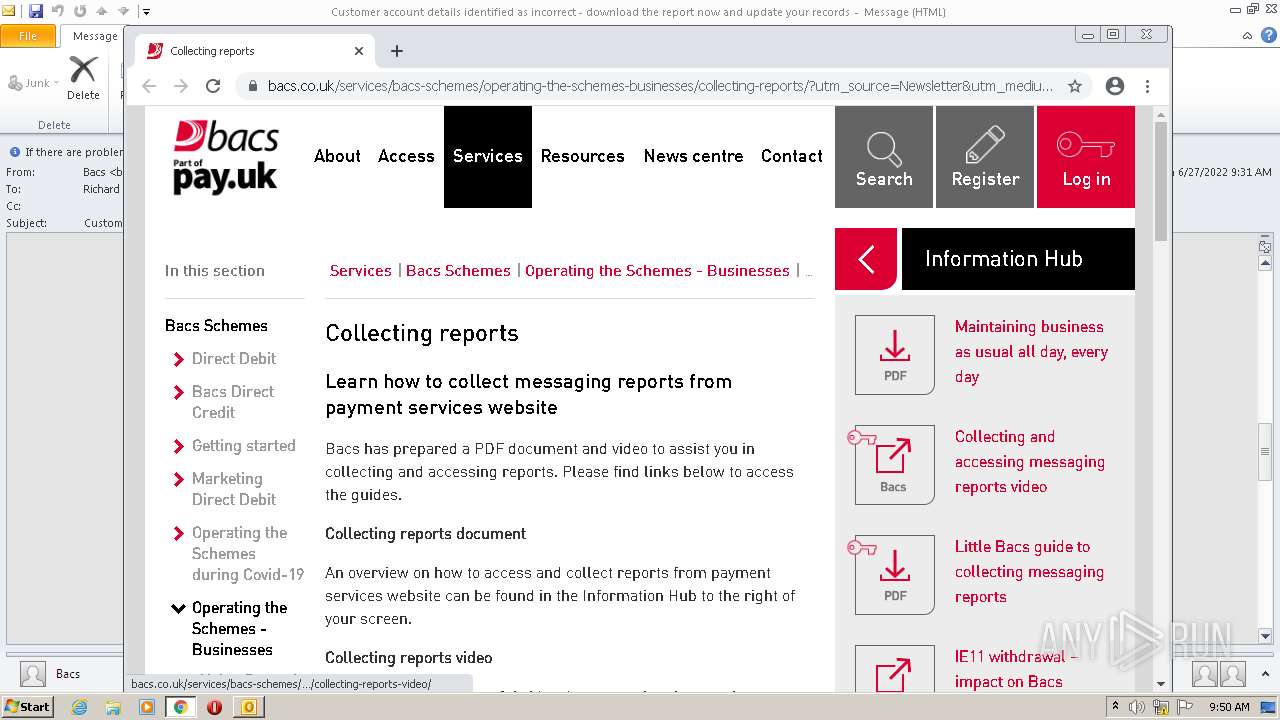
bacs.co.uk |
| unknown |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cc.cdn.civiccomputing.com |
| shared |