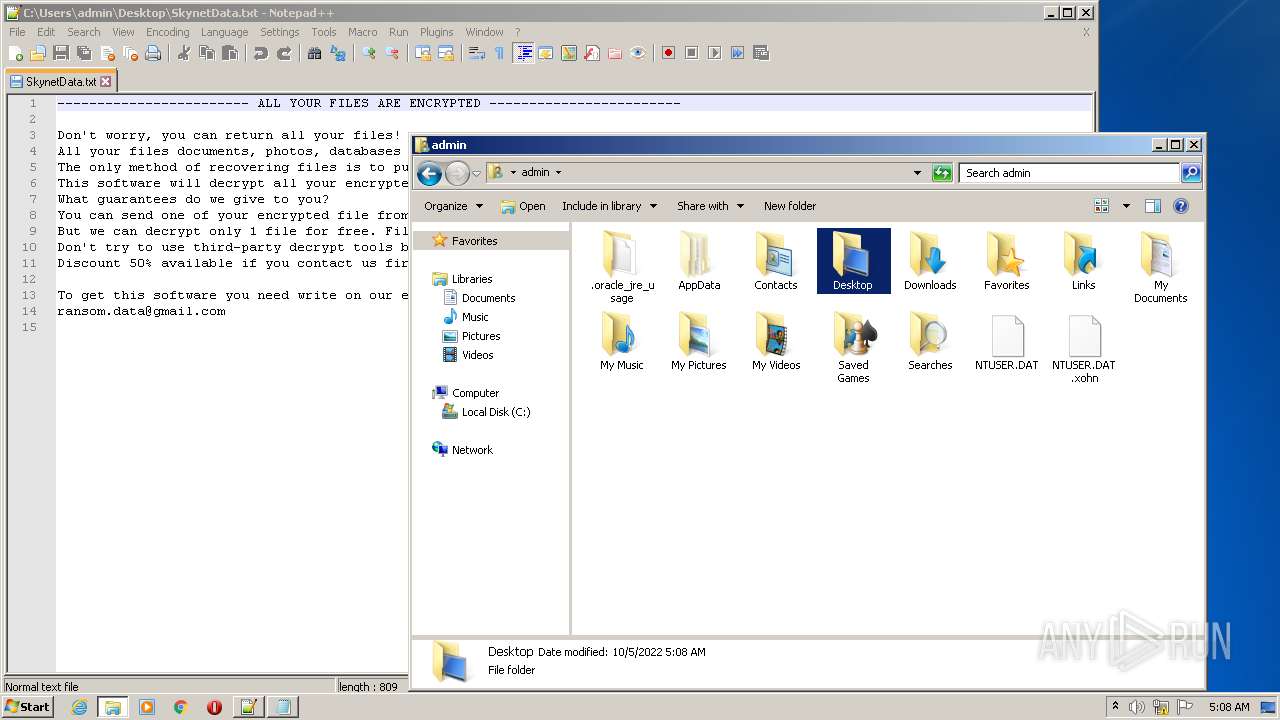
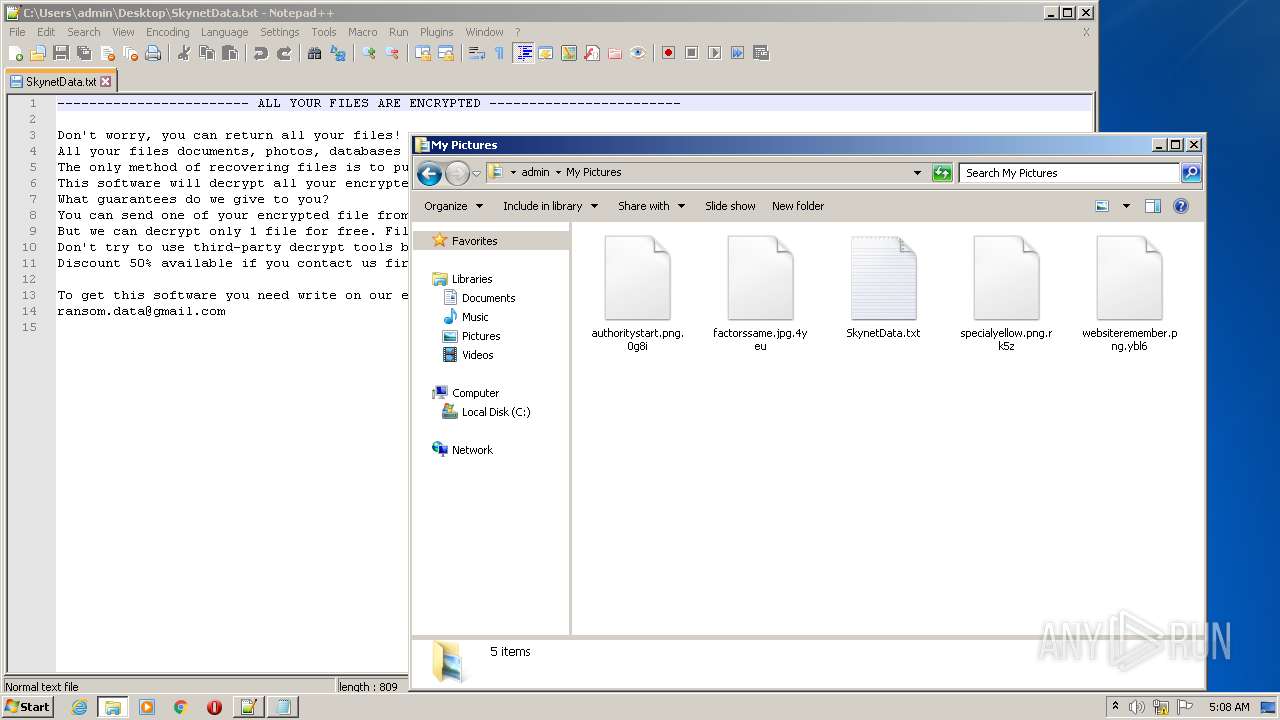
| File name: | ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41 |
| Full analysis: | https://app.any.run/tasks/056f89f7-e1ad-45f1-91f5-a3b36cbf2f02 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 04:08:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | EB9C6ACDEDD1E8A8BFD266403BFD520A |
| SHA1: | C835F8E3FE7F35B7C61CFFE842056BD573CE939B |
| SHA256: | EBC90F7E16EE51150267C78495D59E3A2A2B3880C7541CA3DF0FF287B528FC41 |
| SSDEEP: | 6144:+cVbL0hiIOM8+LDCvzCnQHw67feMv8KiPuTL94:+cVJIOd+vCvnJ8tPuF4 |
MALICIOUS
Changes the autorun value in the registry
- svchost.exe (PID: 312)
Deletes shadow copies
- cmd.exe (PID: 2704)
- cmd.exe (PID: 2856)
Starts BCDEDIT.EXE to disable recovery
- cmd.exe (PID: 1504)
Loads the Task Scheduler COM API
- wbengine.exe (PID: 1532)
Task Manager has been disabled (taskmgr)
- svchost.exe (PID: 312)
Modifies files in Chrome extension folder
- svchost.exe (PID: 312)
SUSPICIOUS
Creates executable files which already exist in Windows
- ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe (PID: 352)
- svchost.exe (PID: 312)
Reads the computer name
- ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe (PID: 352)
- svchost.exe (PID: 312)
Checks supported languages
- ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe (PID: 352)
- svchost.exe (PID: 312)
- cmd.exe (PID: 2704)
- cmd.exe (PID: 1504)
- cmd.exe (PID: 2856)
- notepad++.exe (PID: 460)
Starts itself from another location
- ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe (PID: 352)
Creates files in the user directory
- ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe (PID: 352)
- svchost.exe (PID: 312)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 312)
Executed as Windows Service
- vssvc.exe (PID: 3088)
- vds.exe (PID: 3772)
- wbengine.exe (PID: 1532)
- SearchIndexer.exe (PID: 3824)
Executed via COM
- vdsldr.exe (PID: 2512)
Creates files in the Windows directory
- wbadmin.exe (PID: 3108)
Creates files in the program directory
- SearchIndexer.exe (PID: 3824)
- svchost.exe (PID: 312)
INFO
Reads the computer name
- vssadmin.exe (PID: 2876)
- vssvc.exe (PID: 3088)
- explorer.exe (PID: 3380)
- WMIC.exe (PID: 2132)
- wbadmin.exe (PID: 3108)
- wbengine.exe (PID: 1532)
- vdsldr.exe (PID: 2512)
- SearchIndexer.exe (PID: 3824)
- SearchFilterHost.exe (PID: 2164)
- SearchProtocolHost.exe (PID: 656)
- SearchProtocolHost.exe (PID: 1564)
- vds.exe (PID: 3772)
Checks supported languages
- vssadmin.exe (PID: 2876)
- vssvc.exe (PID: 3088)
- explorer.exe (PID: 3380)
- WMIC.exe (PID: 2132)
- bcdedit.exe (PID: 1748)
- bcdedit.exe (PID: 2804)
- wbengine.exe (PID: 1532)
- vdsldr.exe (PID: 2512)
- vds.exe (PID: 3772)
- wbadmin.exe (PID: 3108)
- SearchProtocolHost.exe (PID: 1564)
- NOTEPAD.EXE (PID: 1024)
- SearchIndexer.exe (PID: 3824)
- SearchProtocolHost.exe (PID: 656)
- SearchFilterHost.exe (PID: 2164)
Manual execution by user
- explorer.exe (PID: 3380)
- notepad++.exe (PID: 460)
Reads Microsoft Office registry keys
- SearchProtocolHost.exe (PID: 1564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2022-Oct-04 21:50:13 |
| Debug artifacts: |
|
| FileDescription: | - |
| FileVersion: | 0.0.0.0 |
| InternalName: | SkynetLocker.exe |
| LegalCopyright: | - |
| OriginalFilename: | SkynetLocker.exe |
| ProductVersion: | 0.0.0.0 |
| Assembly Version: | 0.0.0.0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 3 |
| TimeDateStamp: | 2022-Oct-04 21:50:13 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 8192 | 64120 | 64512 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 4.78342 |
.rsrc | 73728 | 271800 | 271872 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.75296 |
.reloc | 352256 | 12 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.74384 | 270376 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 1.67095 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
1 (#2) | 3.18073 | 604 | UNKNOWN | UNKNOWN | RT_VERSION |
1 (#3) | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
65
Monitored processes
21
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 352 | "C:\Users\admin\Desktop\ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe" | C:\Users\admin\Desktop\ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 1 Version: 0.0.0.0 Modules
| |||||||||||||||
| 460 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\SkynetData.txt" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 656 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe1_ Global\UsGthrCtrlFltPipeMssGthrPipe1 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 1024 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\SkynetData.txt | C:\Windows\system32\NOTEPAD.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Windows\System32\cmd.exe" /C bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1532 | "C:\Windows\system32\wbengine.exe" | C:\Windows\system32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1564 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 1748 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2132 | wmic shadowcopy delete | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 631
Read events
7 944
Write events
1 485
Delete events
202
Modification events
| (PID) Process: | (352) ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (352) ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (352) ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (352) ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (312) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateTask |
Value: C:\Users\admin\AppData\Roaming\svchost.exe | |||
| (PID) Process: | (312) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (312) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (312) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (312) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1748) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\250000e0 |
| Operation: | write | Name: | Element |
Value: 0100000000000000 | |||
Executable files
1
Suspicious files
914
Text files
180
Unknown types
886
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 352 | ebc90f7e16ee51150267c78495d59e3a2a2b3880c7541ca3df0ff287b528fc41.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:— | SHA256:— | |||
| 312 | svchost.exe | C:\Users\Default\NTUSER.DAT | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 312 | svchost.exe | C:\Users\Public\Desktop\Acrobat Reader DC.lnk.6bi2 | gmc | |
MD5:01BEE20559863D06BA57D3F2F6FD7533 | SHA256:40290BB40C62239E589EA5A6442ED1E7D87878E5A9ADEB686BE3BDBD9CD3FA21 | |||
| 312 | svchost.exe | C:\ProgramData\ADOBE\ARM\{291AA914-A987-4CE9-BD63-AC0A92D435E5}\RDRSERVICESUPDATER2.EXE | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 312 | svchost.exe | C:\ProgramData\Adobe\ARM\{291AA914-A987-4CE9-BD63-AC0A92D435E5}\RdrServicesUpdater2.exe.9rg5 | gmc | |
MD5:C771D3ED558F01B3CF09B7DFD4E28E0D | SHA256:E85901F82A3A9AAFDA2FC4B2B0D4FE3EBD6DA3F623DE090FEF319A7CCFCB6859 | |||
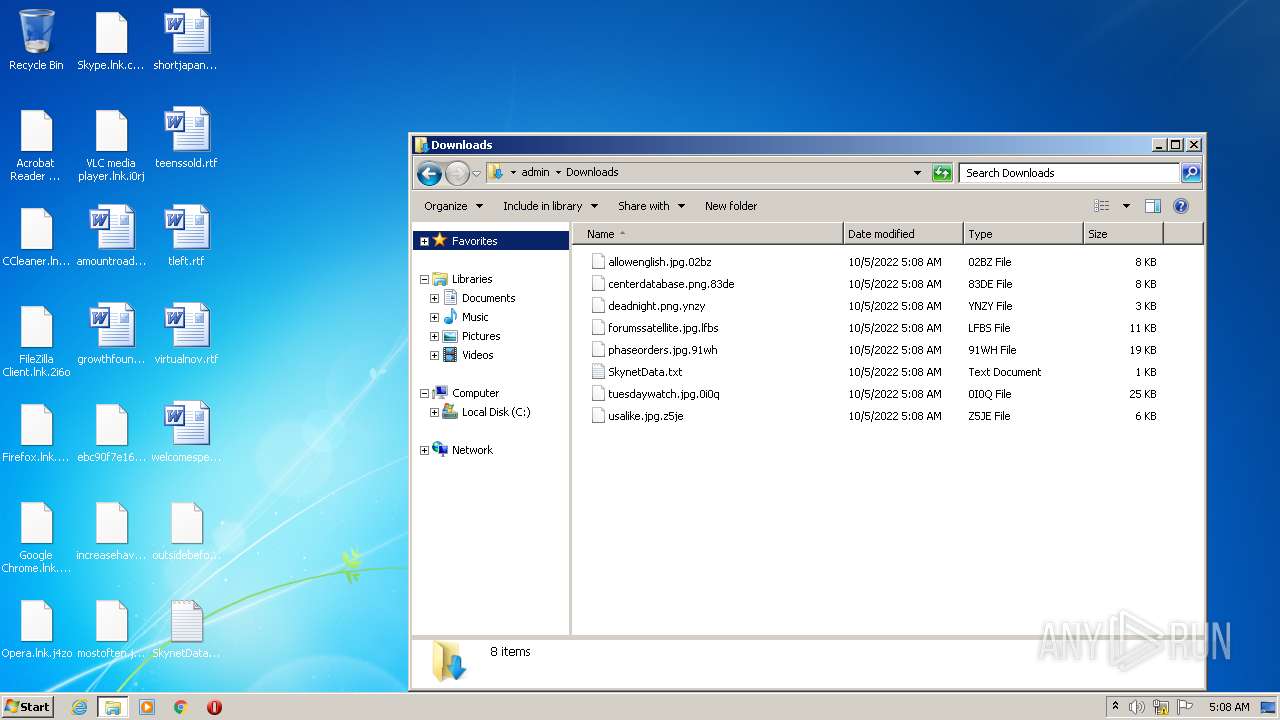
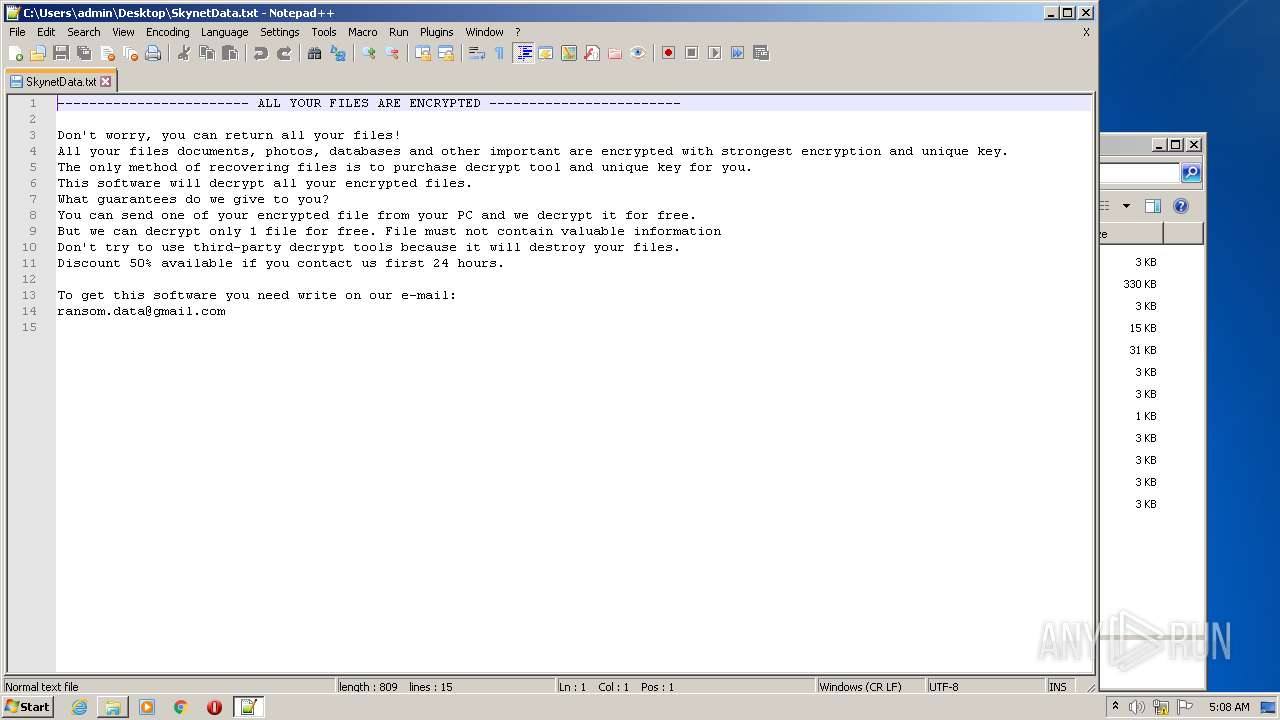
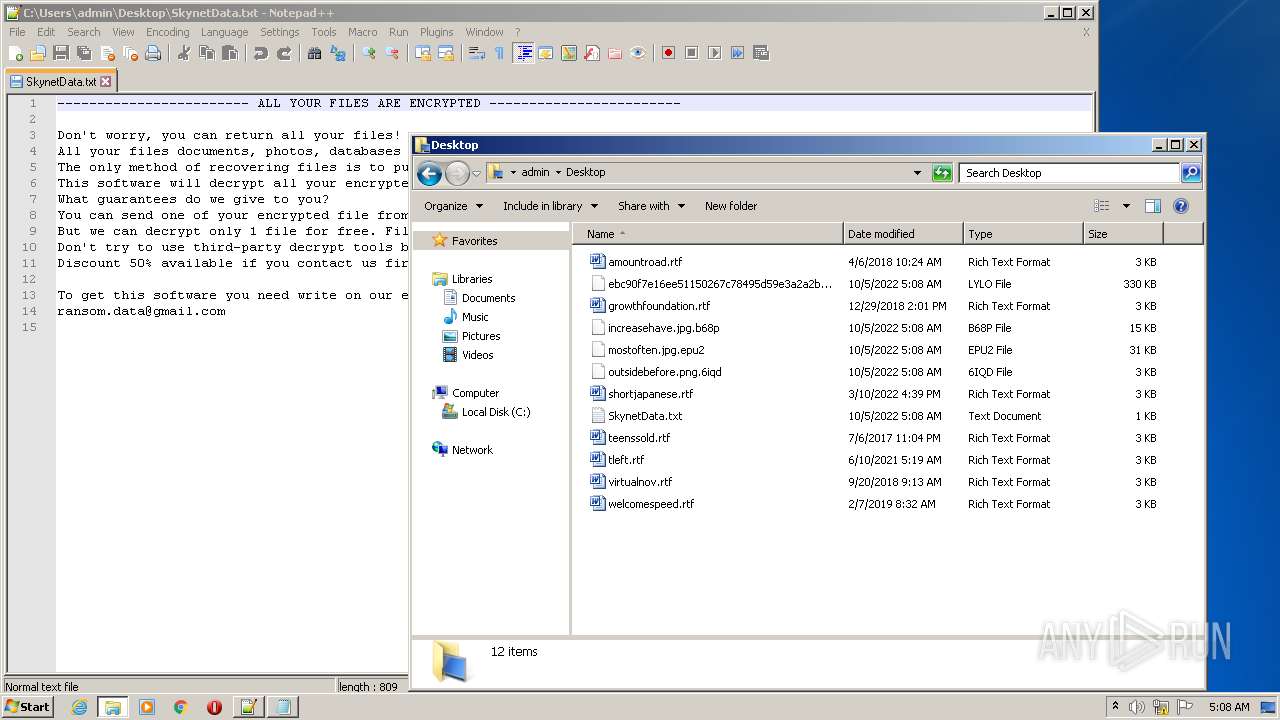
| 312 | svchost.exe | C:\Users\Administrator\SkynetData.txt | text | |
MD5:CA069420F1D43DABBA1630A2477891C7 | SHA256:6763E8A512A14AFEFD3BBA63EF0516DBB378436E2BC7D853EAEB7A6FDF5EB090 | |||
| 312 | svchost.exe | C:\Users\admin\NTUSER.DAT.xohn | gmc | |
MD5:B98F319EBCFE36F416C0B7D9281F85FF | SHA256:96A12DEEBDC8A3421E923D2FC00A649326F0B5167B48FFD231941A415777308C | |||
| 312 | svchost.exe | C:\Users\Default\NTUSER.DAT.z1ep | gmc | |
MD5:EC87A838931D4D5D2E94A04644788A55 | SHA256:8A39D2ABD3999AB73C34DB2476849CDDF303CE389B35826850F9A700589B4A90 | |||
| 312 | svchost.exe | C:\Users\Default\SkynetData.txt | text | |
MD5:CA069420F1D43DABBA1630A2477891C7 | SHA256:6763E8A512A14AFEFD3BBA63EF0516DBB378436E2BC7D853EAEB7A6FDF5EB090 | |||
| 312 | svchost.exe | C:\ProgramData\Adobe\ARM\{291AA914-A987-4CE9-BD63-AC0A92D435E5}\SkynetData.txt | text | |
MD5:CA069420F1D43DABBA1630A2477891C7 | SHA256:6763E8A512A14AFEFD3BBA63EF0516DBB378436E2BC7D853EAEB7A6FDF5EB090 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|