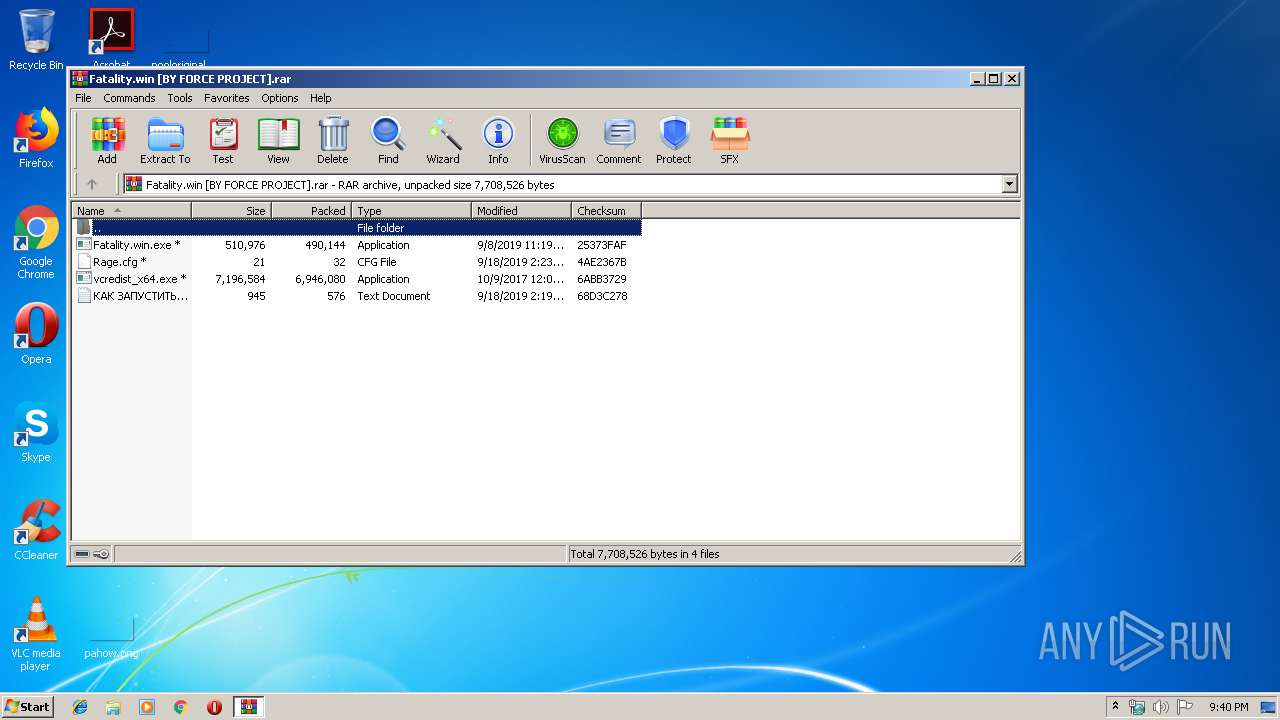
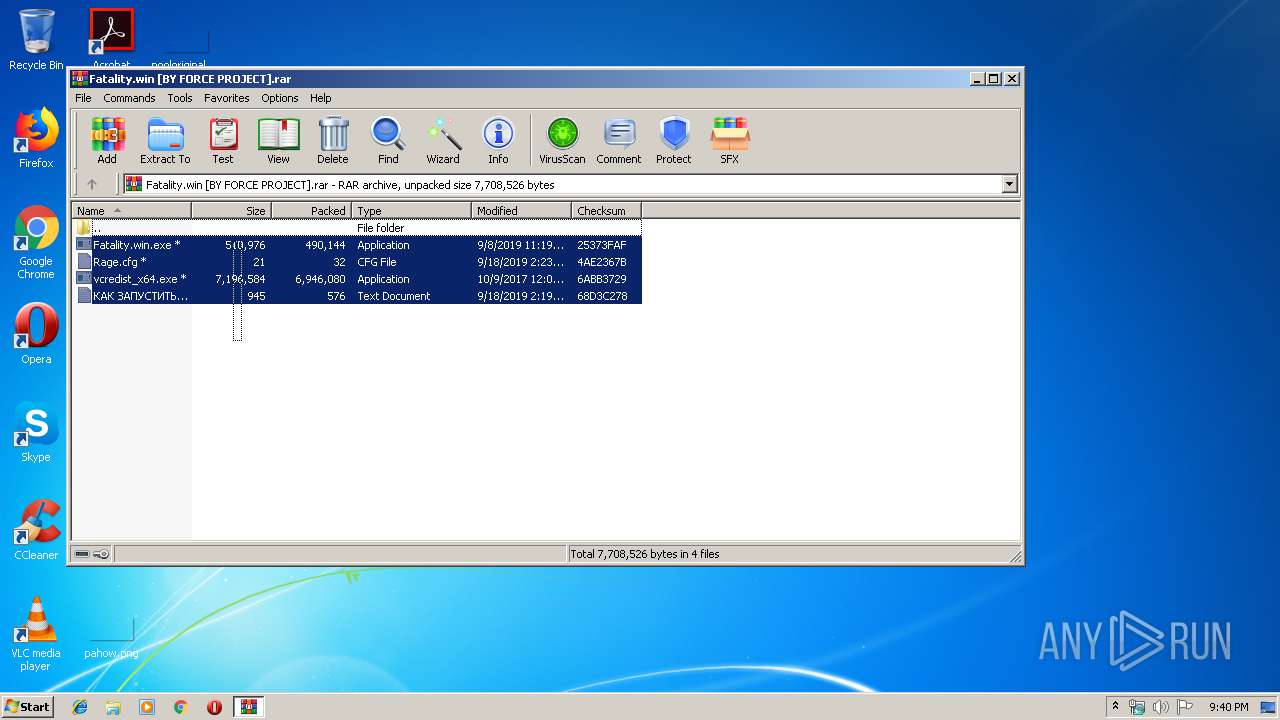
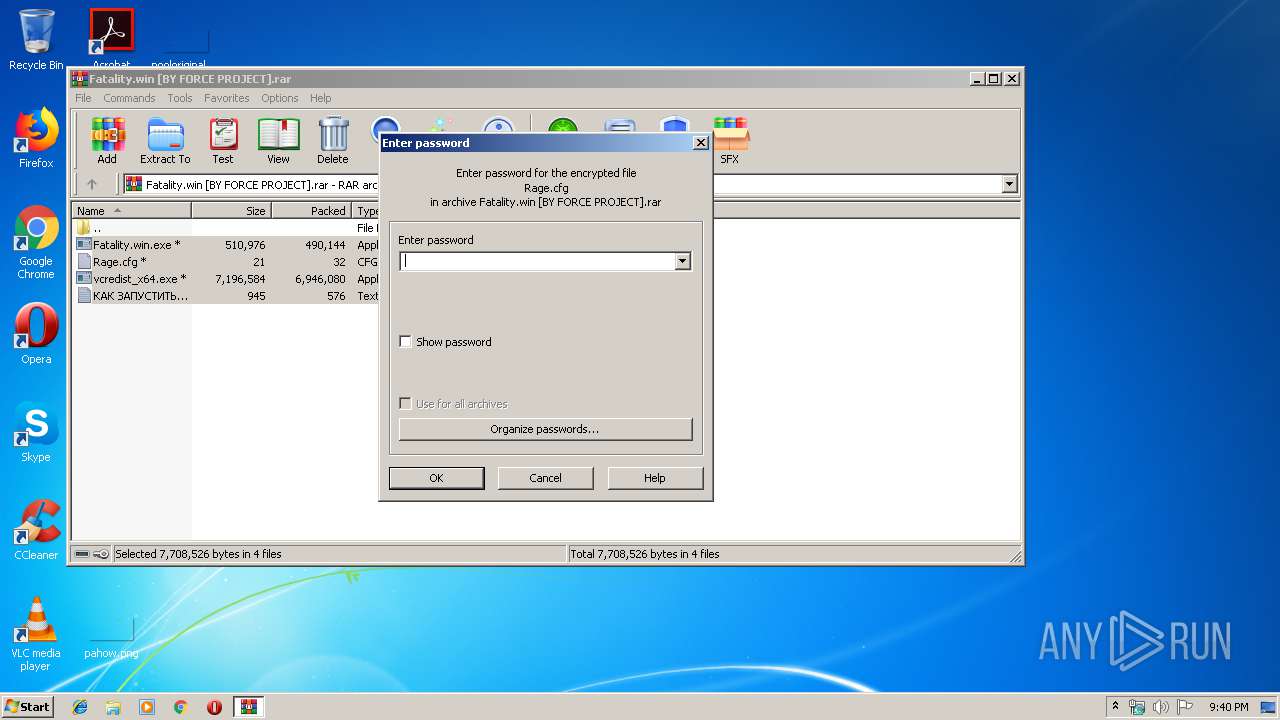
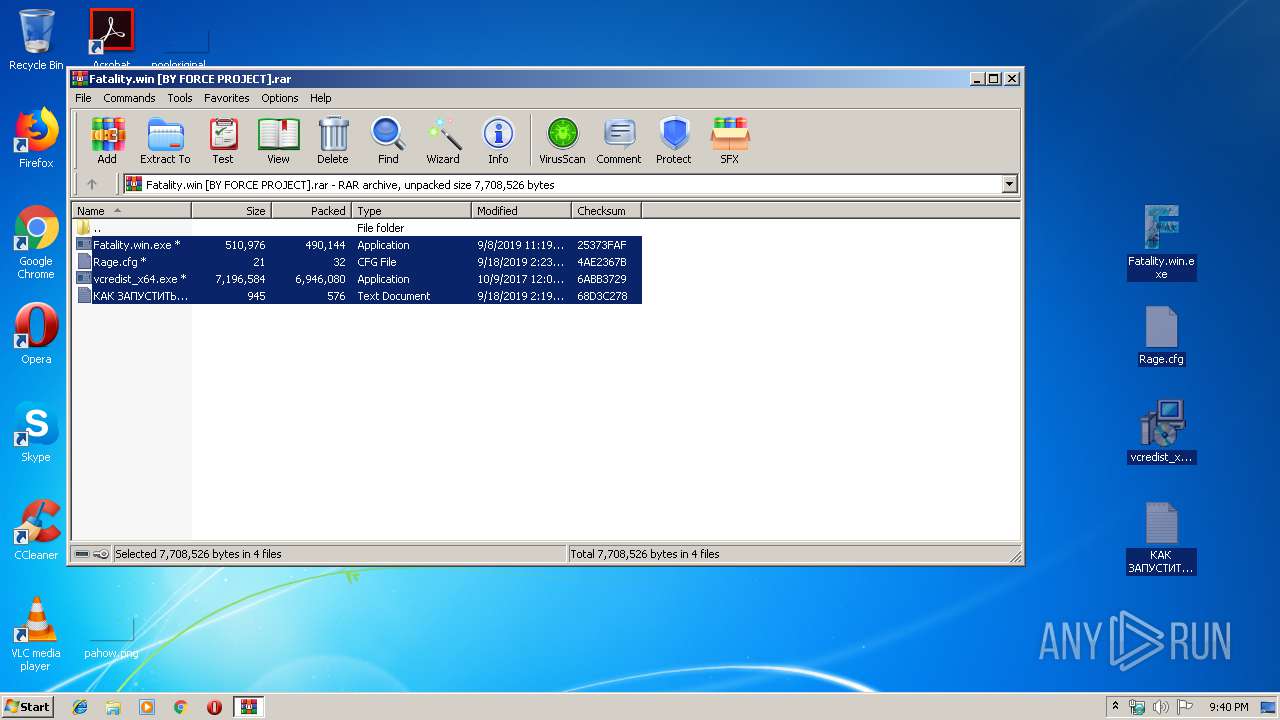
| File name: | Fatality.win [BY FORCE PROJECT].rar |
| Full analysis: | https://app.any.run/tasks/0ca1fd94-8301-45db-81e4-ebeda290b8ea |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2019, 20:39:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | ADBB469A1F9011E79027BF8E609C1A7A |
| SHA1: | CF0D6D0B0F63BAF57E3DD90CA7FD7BEC8ECE6BF9 |
| SHA256: | EBC74A32FD9C76F18E667632EC179CF49A838AE0FC95C89EF0BAC94DB8975A89 |
| SSDEEP: | 196608:xIYH6+Iu0DfjDTaA+Fdwn/2jLEBT5Dg59QtBCn2mK:yYnkXTaZzwujLEPa9QLC2mK |
MALICIOUS
Application was dropped or rewritten from another process
- vcredist_x64.exe (PID: 3800)
Loads dropped or rewritten executable
- vcredist_x64.exe (PID: 3800)
SUSPICIOUS
Searches for installed software
- vcredist_x64.exe (PID: 3800)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3636)
- vcredist_x64.exe (PID: 3800)
INFO
Manual execution by user
- vcredist_x64.exe (PID: 3800)
- NOTEPAD.EXE (PID: 3504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
35
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
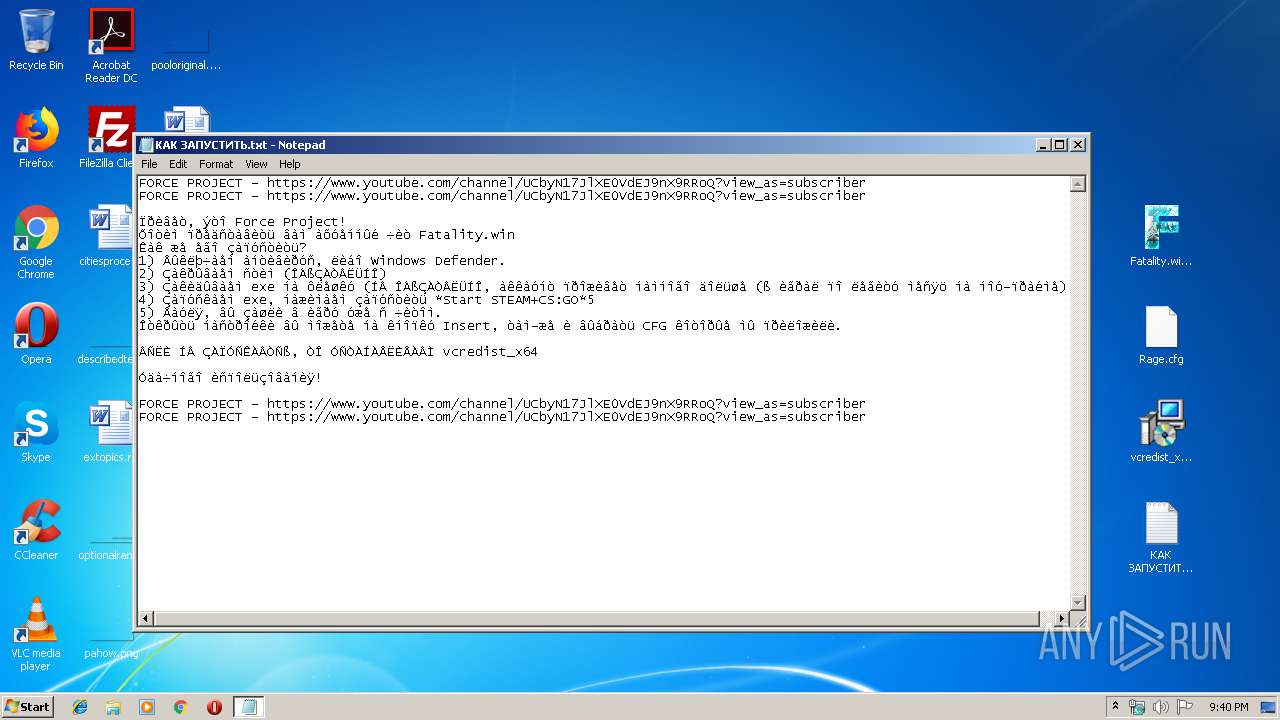
| 3504 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\КАК ЗАПУСТИТЬ.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3636 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Fatality.win [BY FORCE PROJECT].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3800 | "C:\Users\admin\Desktop\vcredist_x64.exe" | C:\Users\admin\Desktop\vcredist_x64.exe | explorer.exe | ||||||||||||
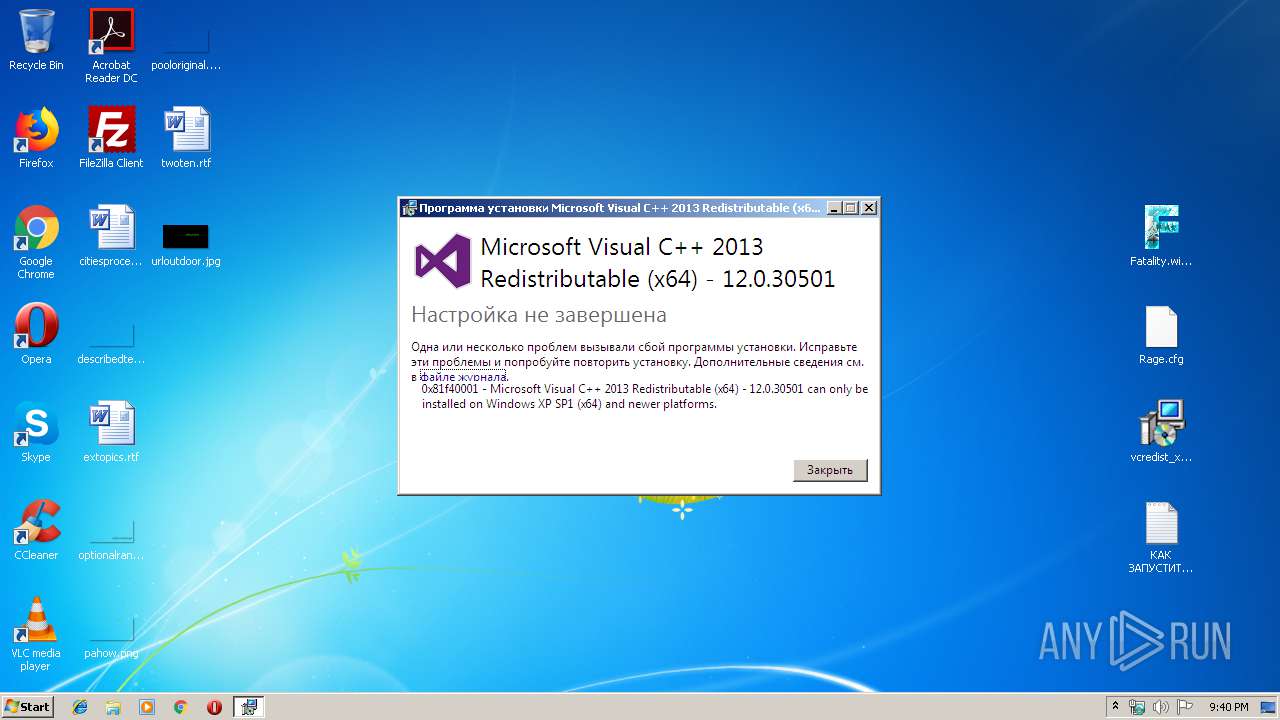
User: admin Company: Корпорация Майкрософт Integrity Level: MEDIUM Description: Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.30501 Exit code: 1 Version: 12.0.30501.0 Modules
| |||||||||||||||
Total events
506
Read events
481
Write events
25
Delete events
0
Modification events
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Fatality.win [BY FORCE PROJECT].rar | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
3
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3800 | vcredist_x64.exe | C:\Users\admin\AppData\Local\Temp\dd_vcredist_amd64_20190918214043.log | text | |
MD5:— | SHA256:— | |||
| 3636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3636.21911\Fatality.win.exe | executable | |
MD5:— | SHA256:— | |||
| 3636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3636.21911\КАК ЗАПУСТИТЬ.txt | text | |
MD5:— | SHA256:— | |||
| 3636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3636.21911\Rage.cfg | text | |
MD5:— | SHA256:— | |||
| 3800 | vcredist_x64.exe | C:\Users\admin\AppData\Local\Temp\{1a63c099-febd-4eaf-83ad-a82ea4fdac49}\.ba1\thm.wxl | xml | |
MD5:FFF536F74A167C218C91C76483248B90 | SHA256:97E9EB74807AA6DB584CB32B60F4D32FAC0C2DC0466222E9B2ABBC2F26D52CF6 | |||
| 3800 | vcredist_x64.exe | C:\Users\admin\AppData\Local\Temp\{1a63c099-febd-4eaf-83ad-a82ea4fdac49}\.ba1\wixstdba.dll | executable | |
MD5:A52E5220EFB60813B31A82D101A97DCB | SHA256:E7C8E7EDD9112137895820E789BAAAECA41626B01FB99FEDE82968DDB66D02CF | |||
| 3800 | vcredist_x64.exe | C:\Users\admin\AppData\Local\Temp\{1a63c099-febd-4eaf-83ad-a82ea4fdac49}\.ba1\thm.xml | xml | |
MD5:0056F10A42638EA8B4BEFC614741DDD6 | SHA256:6B1BA0DEA830E556A58C883290FAA5D49C064E546CBFCD0451596A10CC693F87 | |||
| 3800 | vcredist_x64.exe | C:\Users\admin\AppData\Local\Temp\{1a63c099-febd-4eaf-83ad-a82ea4fdac49}\.ba1\BootstrapperApplicationData.xml | xml | |
MD5:9E027E4B6BEBCDAC32A3DD91EBC8DDD3 | SHA256:A1B31D4316A6E6AF59ADABFB676F8BE0366E8305D9F856A30F85A2D337B73B89 | |||
| 3800 | vcredist_x64.exe | C:\Users\admin\AppData\Local\Temp\{1a63c099-febd-4eaf-83ad-a82ea4fdac49}\.ba1\logo.png | image | |
MD5:D6BD210F227442B3362493D046CEA233 | SHA256:335A256D4779EC5DCF283D007FB56FD8211BBCAF47DCD70FE60DED6A112744EF | |||
| 3636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3636.21911\vcredist_x64.exe | executable | |
MD5:E74F5AC8F39FF69DDDCE07C8E1F7F943 | SHA256:4542BF0E828D4428260B2BC975DA5BC25D69C060E54176DAC1D14B5567EA67D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report