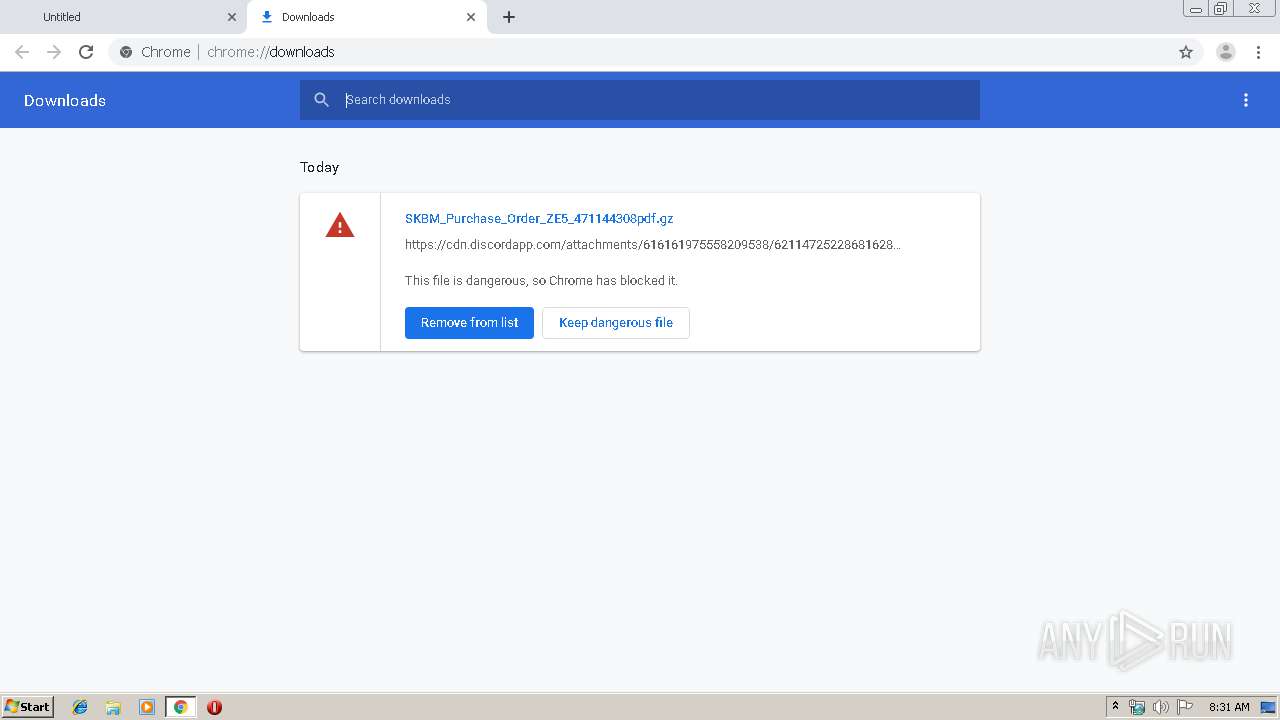
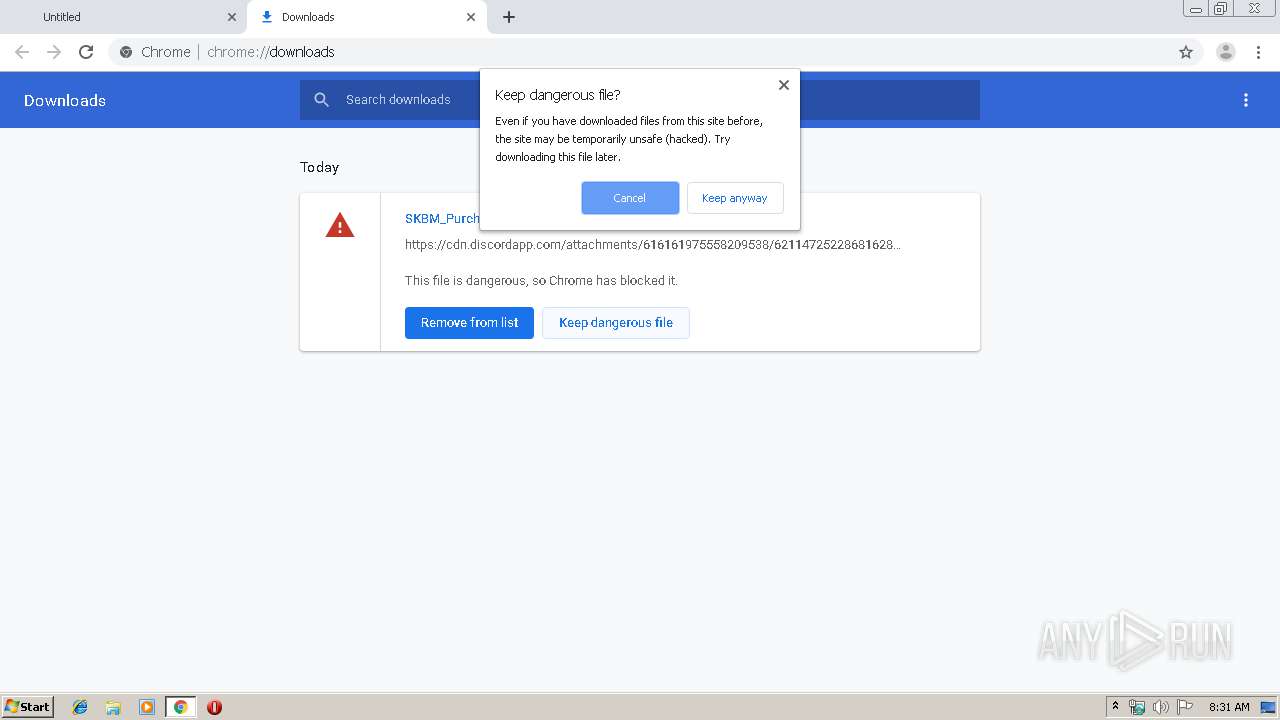
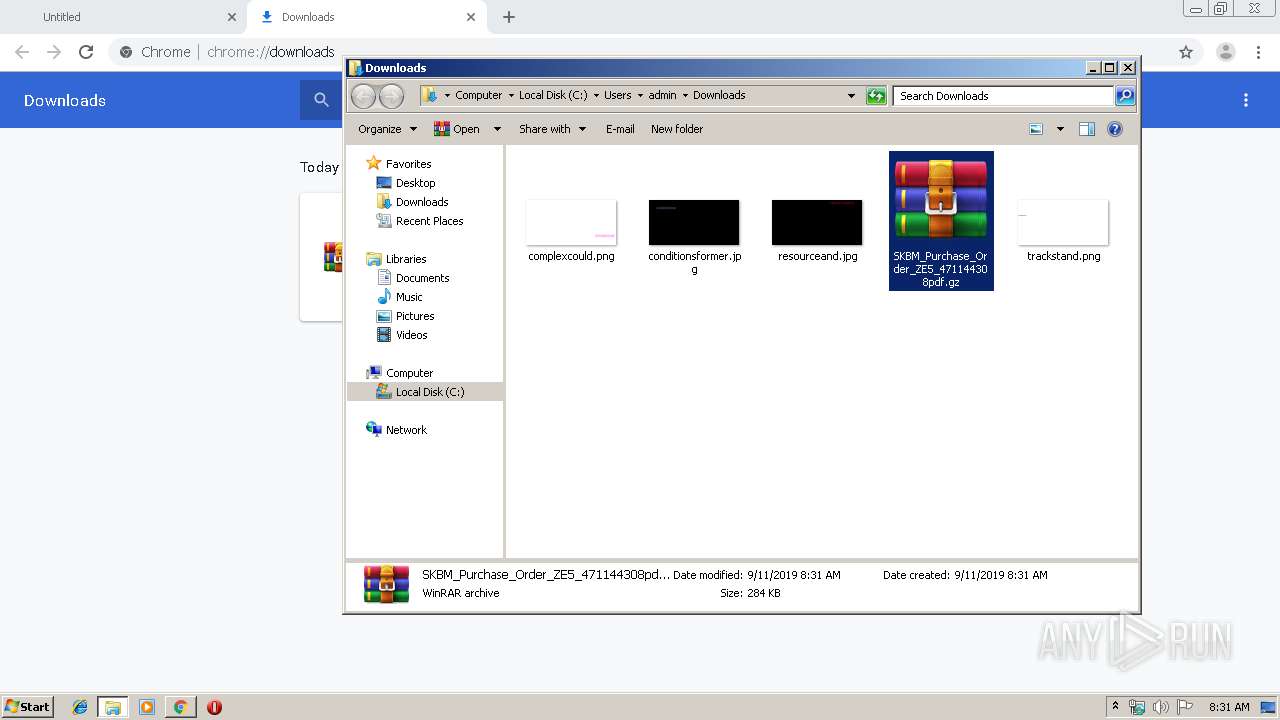
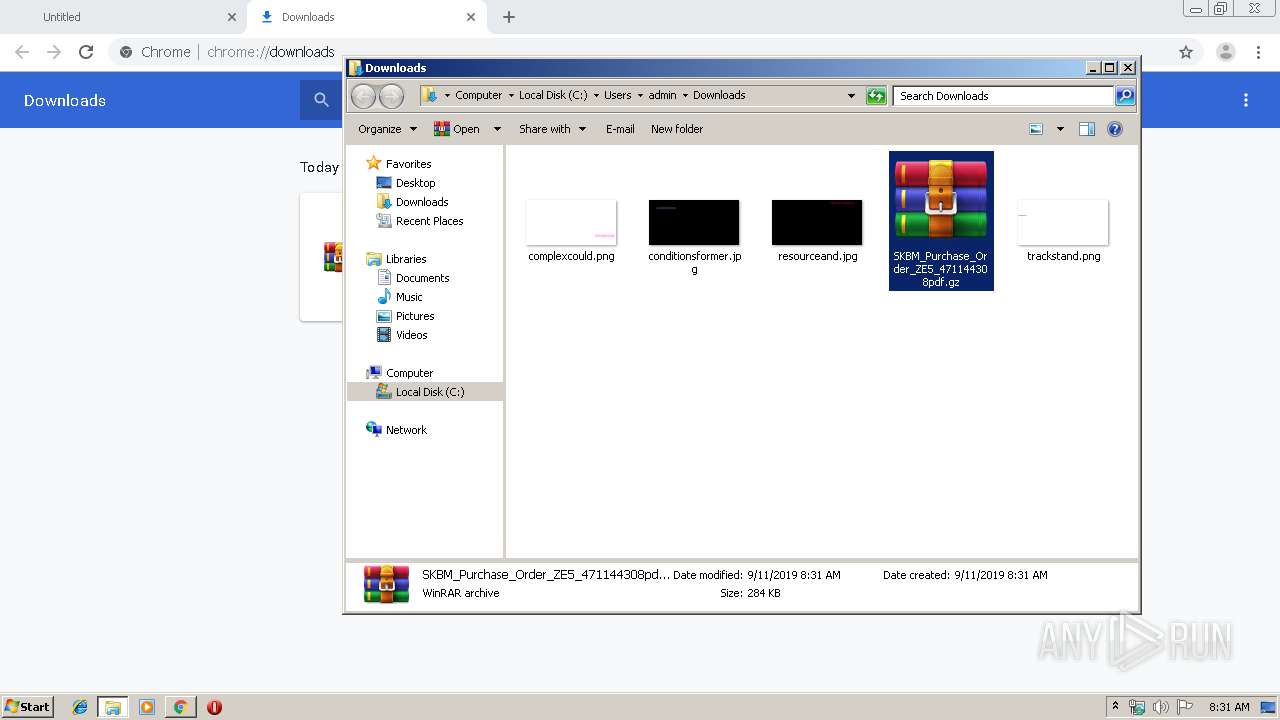
| URL: | https://cdn.discordapp.com/attachments/616161975558209538/621147252286816286/SKBM_Purchase_Order_ZE5_471144308pdf.gz |
| Full analysis: | https://app.any.run/tasks/84e17dbb-9a68-474e-a883-93db4dc999c7 |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 07:30:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2A6D952EA2389C11519DBC3DCF5F2004 |
| SHA1: | 1A738BB5BDE2643CD68D19B24B74FC501807E9A6 |
| SHA256: | EBB297C8FE60E5356D21A7A777A4BFCC50176BCABA1B7FBA2912A07970C39026 |
| SSDEEP: | 3:N8cCWdy6//HFSQhWYN0yX7MdTtACpQQ6nIgkfn:2cry6XHFNVrctQJI/fn |
MALICIOUS
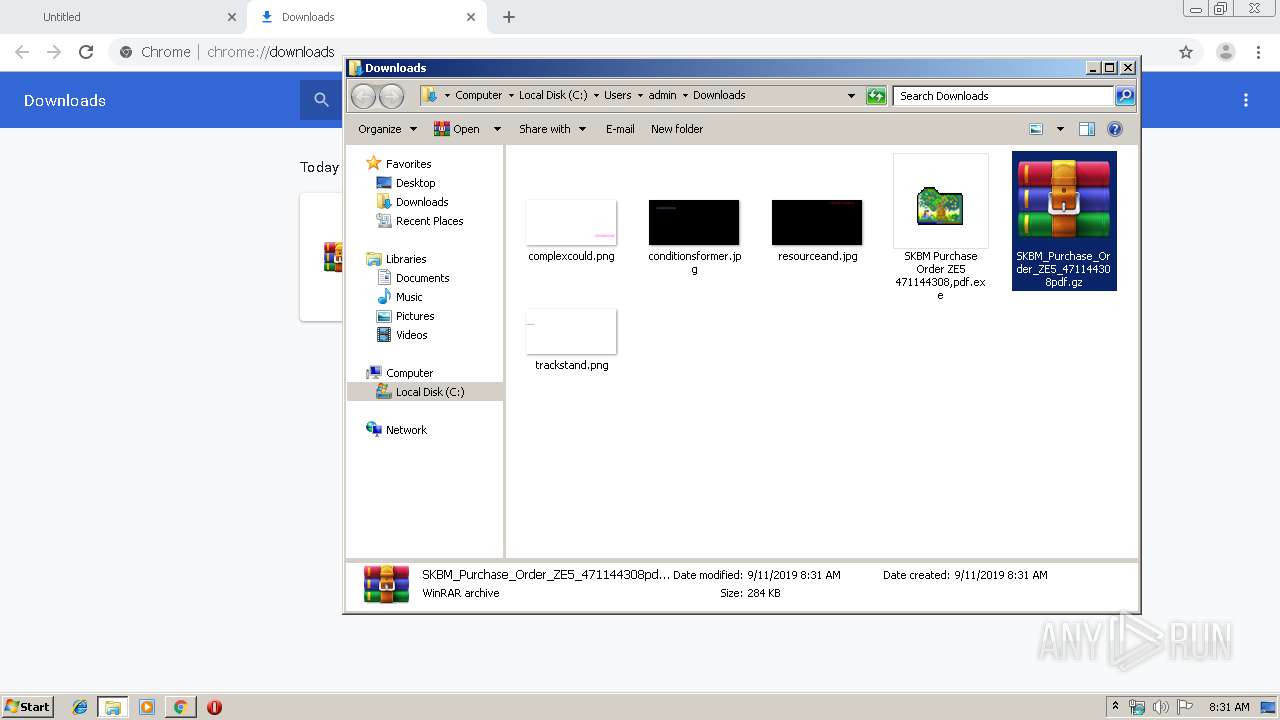
Application was dropped or rewritten from another process
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3584)
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3188)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2520)
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3584)
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3188)
Creates files in the user directory
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3584)
Creates a software uninstall entry
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3188)
INFO
Application launched itself
- chrome.exe (PID: 3552)
Reads the hosts file
- chrome.exe (PID: 3552)
- chrome.exe (PID: 2836)
Manual execution by user
- WinRAR.exe (PID: 2520)
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3584)
- WinRAR.exe (PID: 2820)
- SKBM Purchase Order ZE5 471144308,pdf.exe (PID: 3188)
Reads Internet Cache Settings
- chrome.exe (PID: 3552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6fdea9d0,0x6fdea9e0,0x6fdea9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=13601963712023136194 --mojo-platform-channel-handle=4076 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
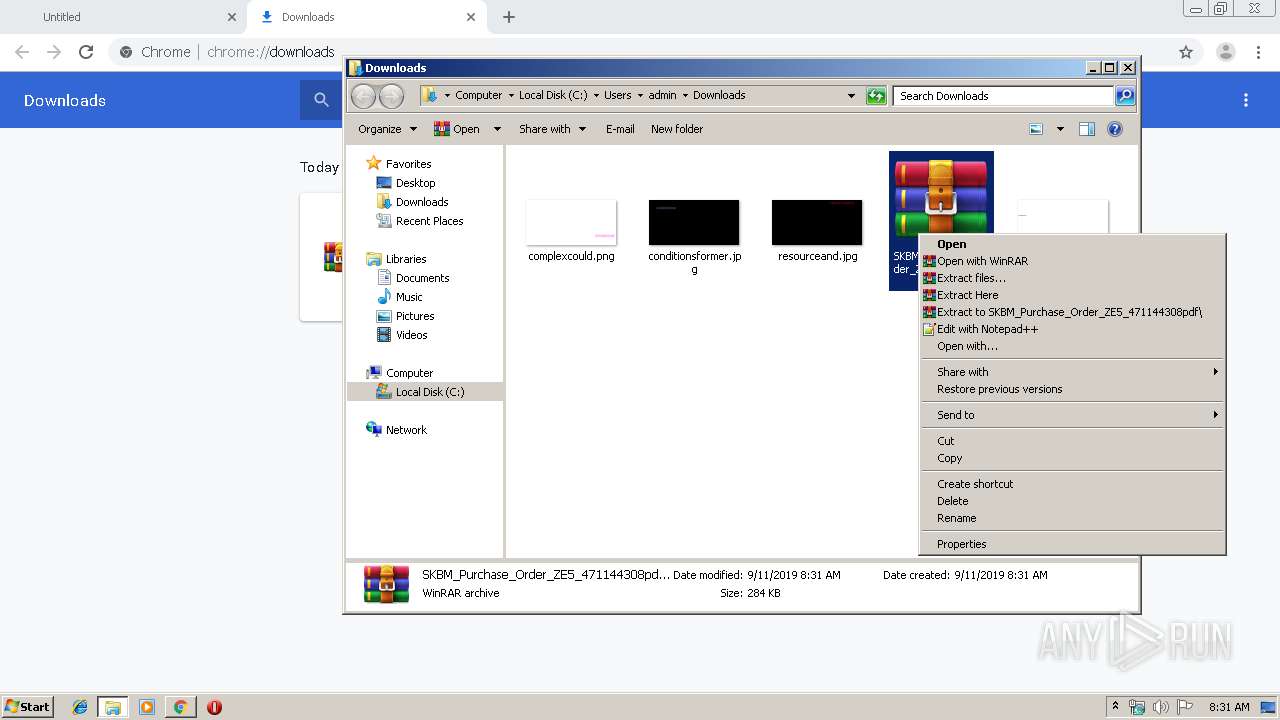
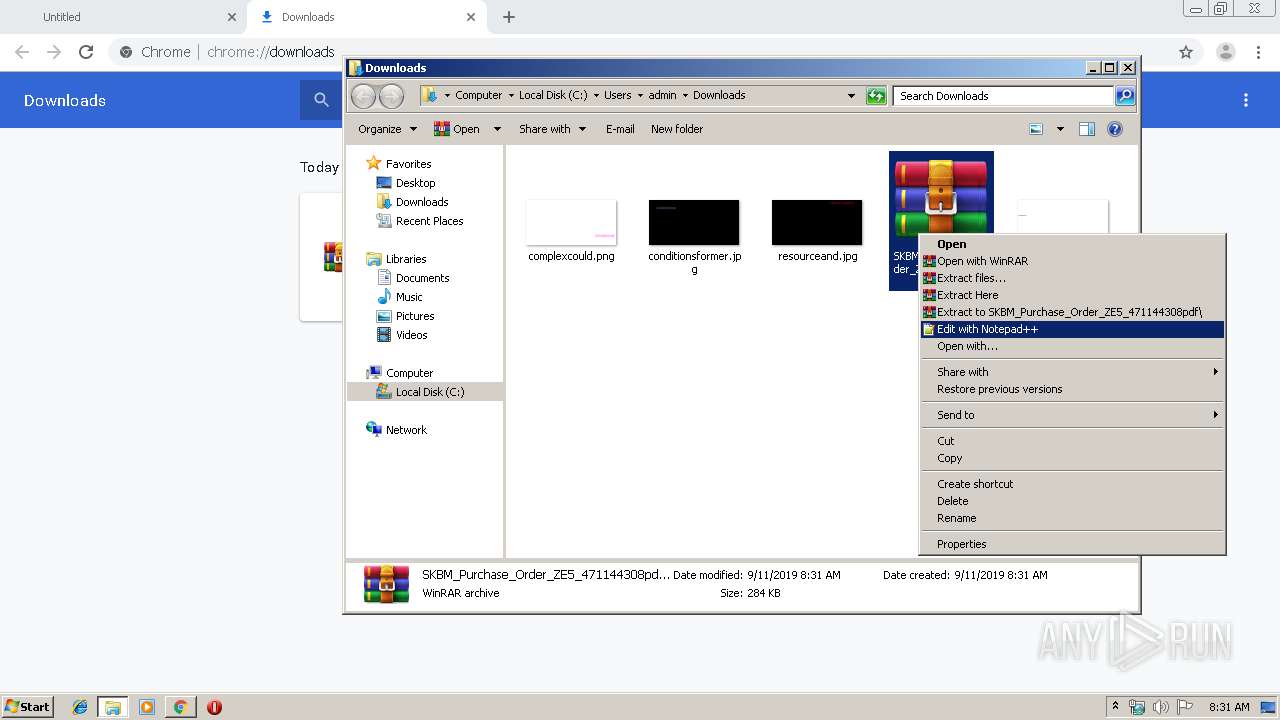
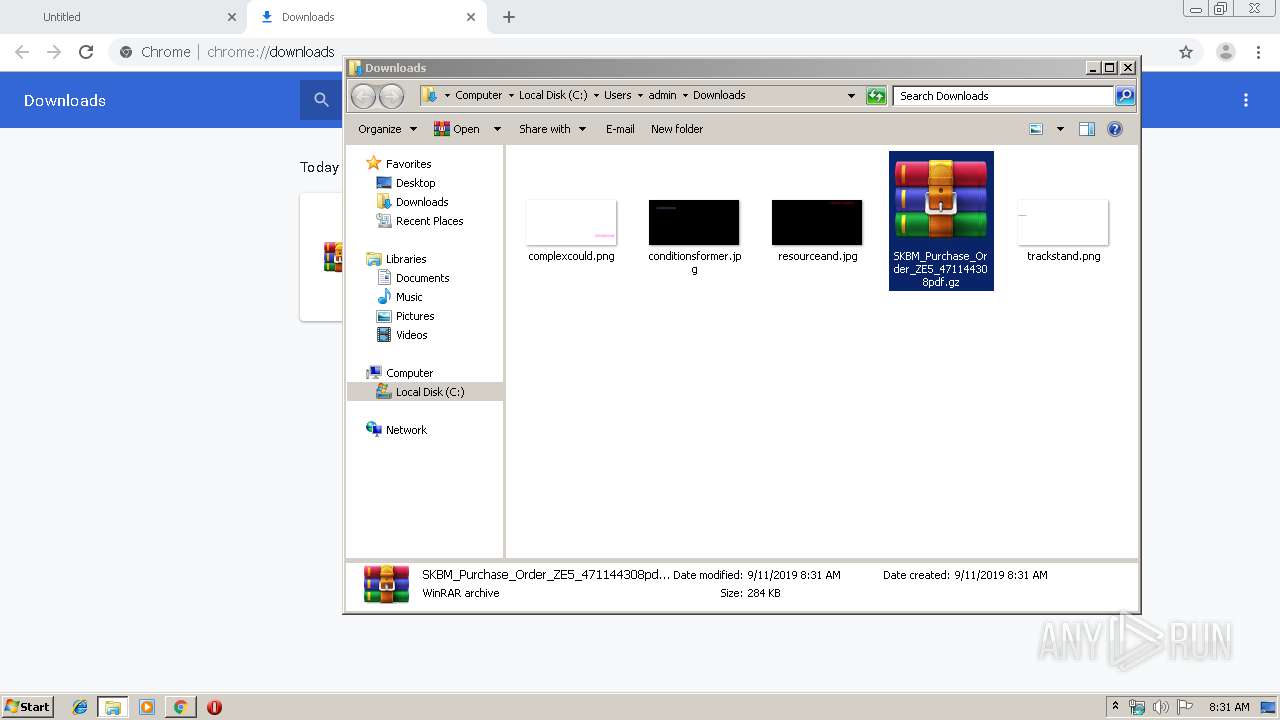
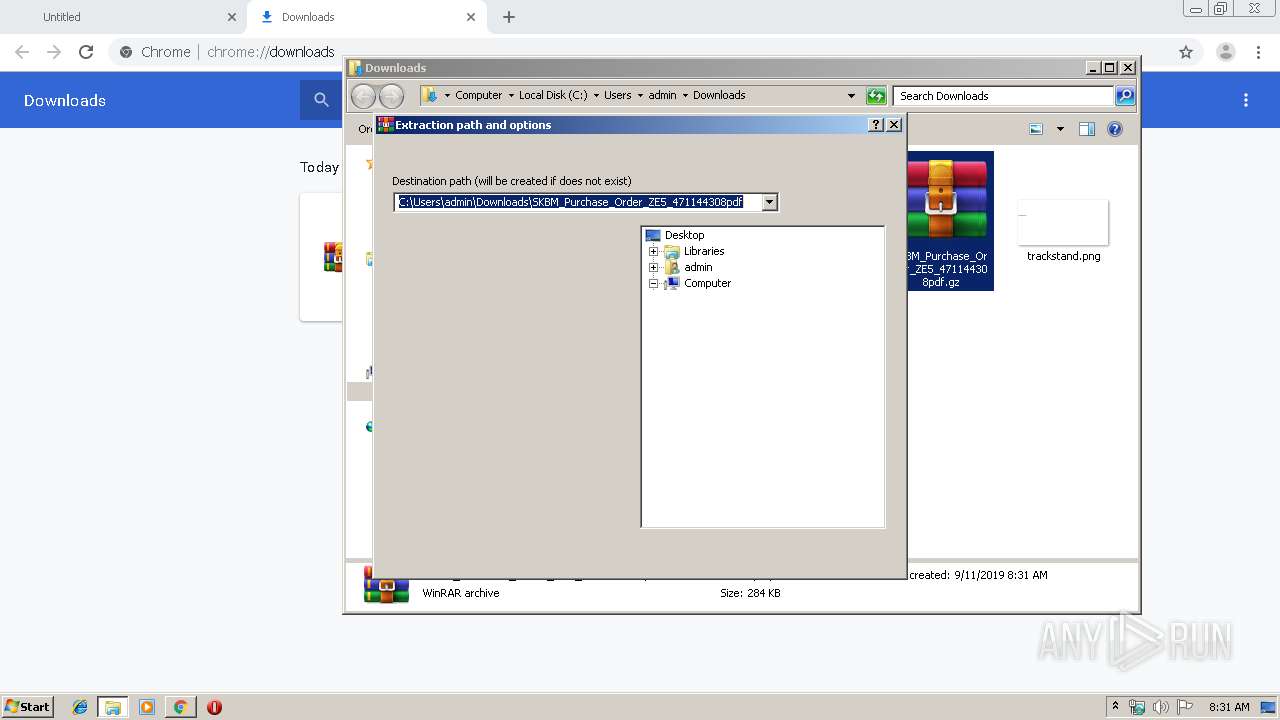
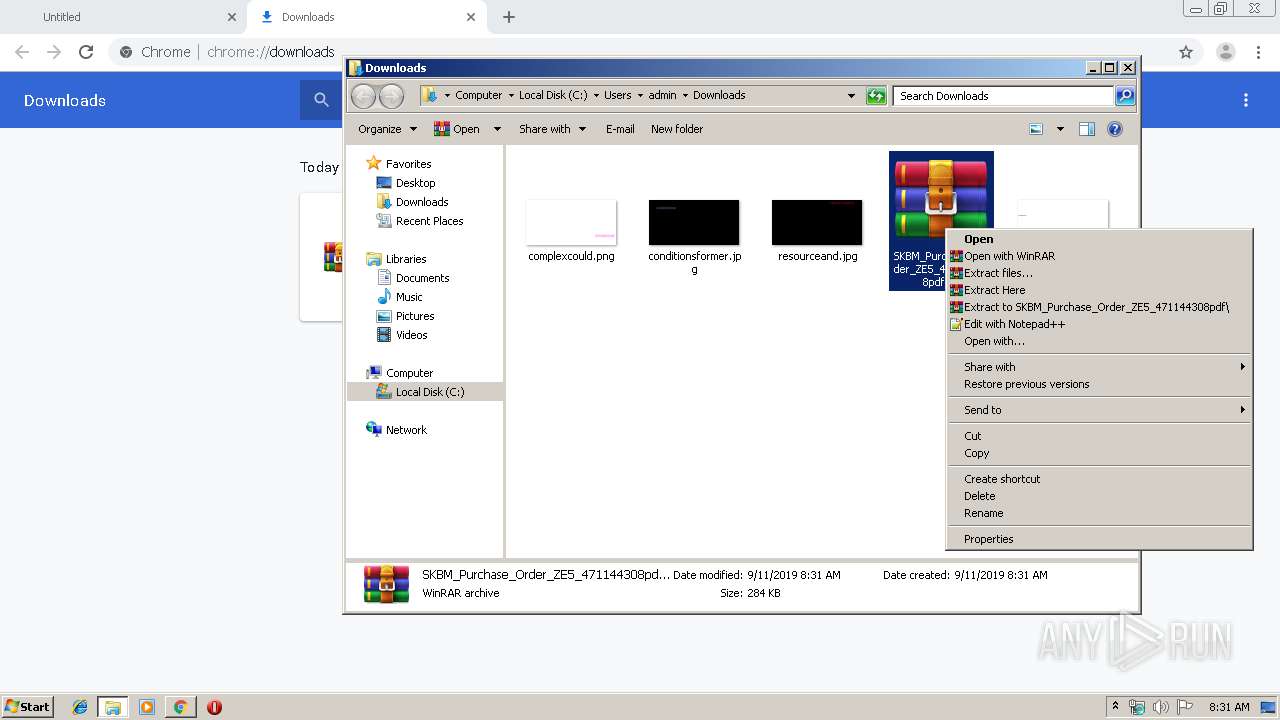
| 2520 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\SKBM_Purchase_Order_ZE5_471144308pdf.gz" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=13264978222520770492 --mojo-platform-channel-handle=936 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7598019412328673344 --mojo-platform-channel-handle=1028 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9437775627099577778 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2820 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\SKBM_Purchase_Order_ZE5_471144308pdf.gz" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=4276736275821492546 --mojo-platform-channel-handle=1548 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3152 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10443743705196379107 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3404 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,17828327642524778717,1700573805475035910,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15776949734814923841 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2264 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
11 140
Read events
2 044
Write events
9 093
Delete events
3
Modification events
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3552-13212660668766125 |
Value: 259 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (3552) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
13
Suspicious files
17
Text files
79
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\93cce119-3bcb-43ae-b847-f587fbe3c4ef.tmp | — | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF169c06.TMP | text | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3552 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\MANIFEST-000001 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
9
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2836 | chrome.exe | 216.58.205.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2836 | chrome.exe | 172.217.18.110:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
2836 | chrome.exe | 172.217.16.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2836 | chrome.exe | 172.217.16.132:443 | www.google.com | Google Inc. | US | whitelisted |
2836 | chrome.exe | 216.58.206.14:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2836 | chrome.exe | 162.159.134.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2836 | chrome.exe | 216.58.207.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| malicious |
safebrowsing.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
dns.msftncsi.com |
| shared |