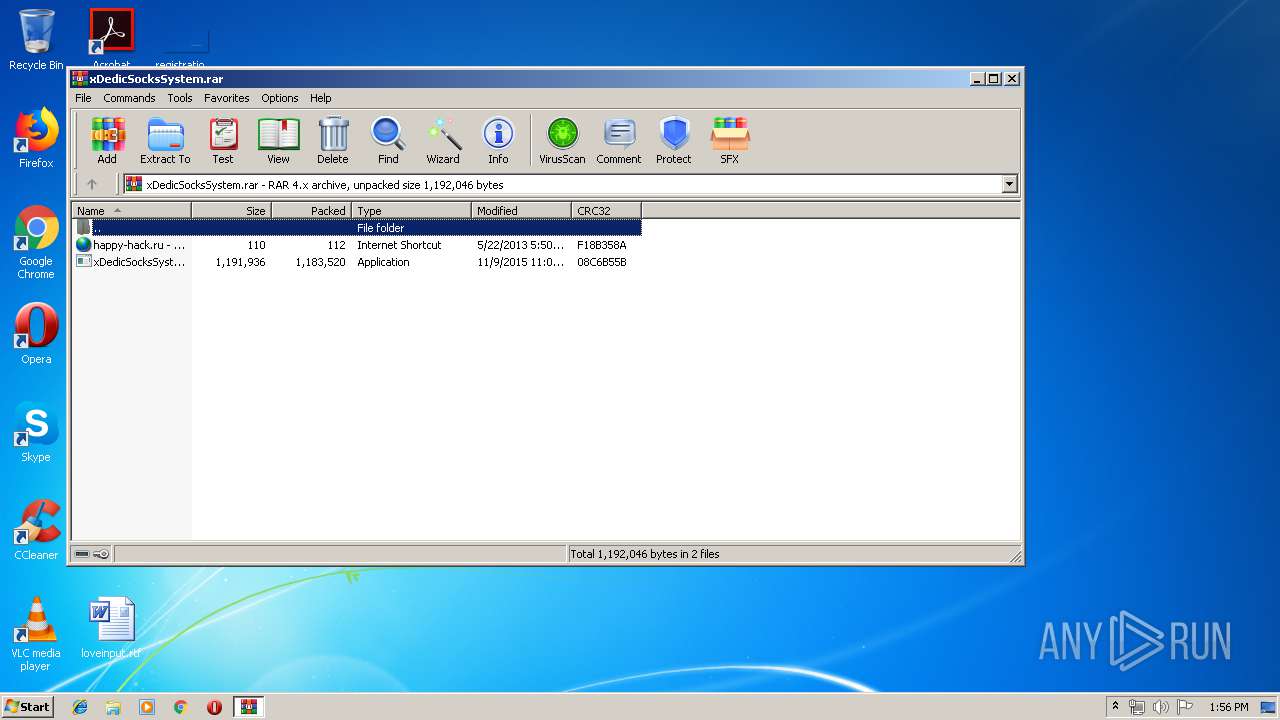
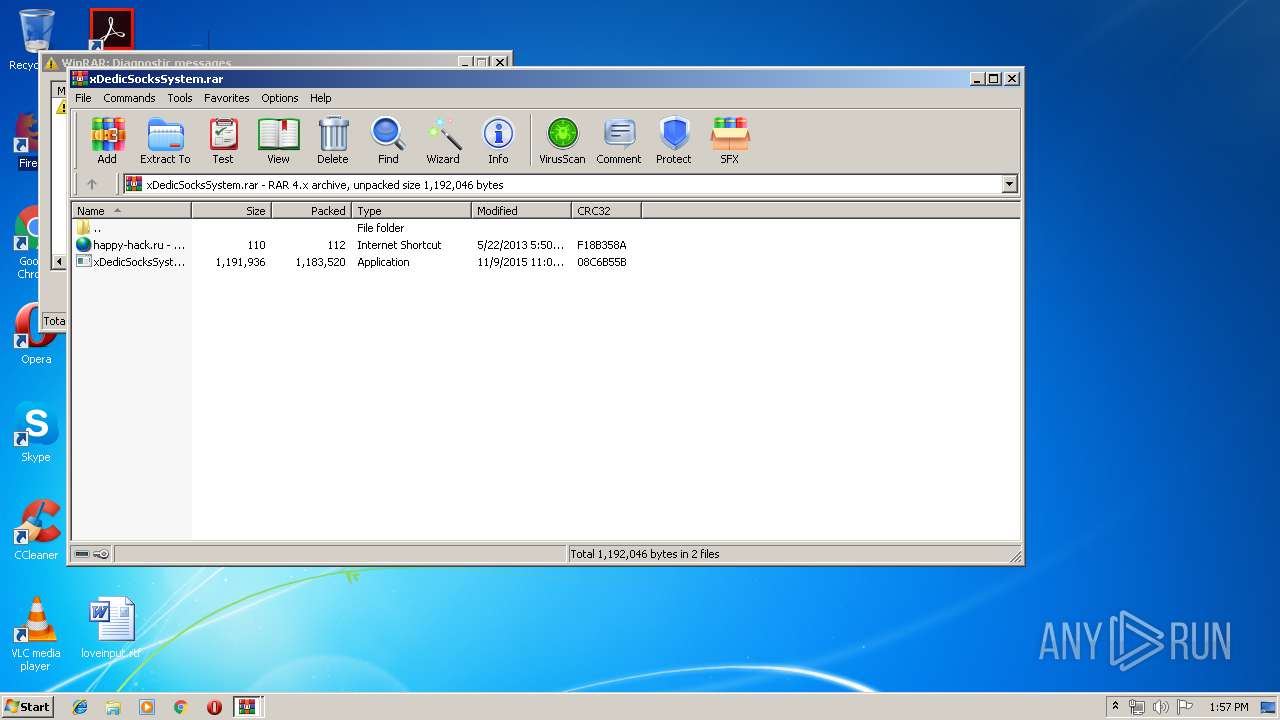
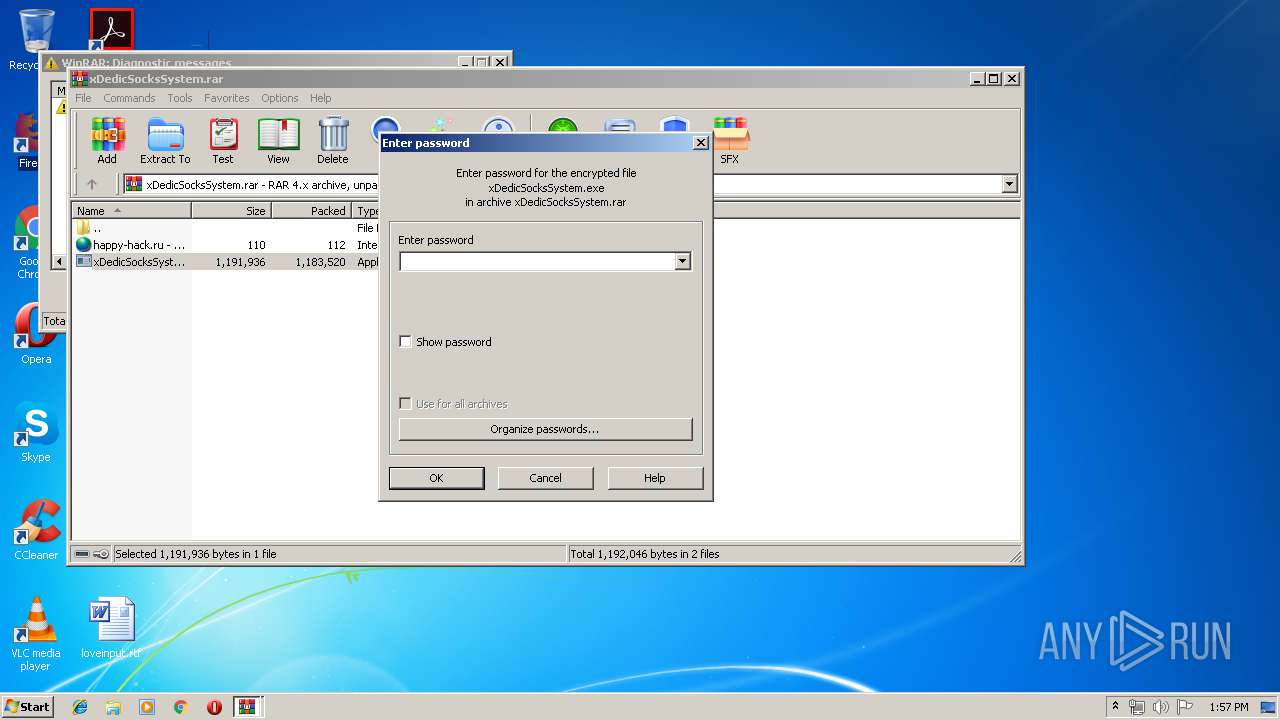
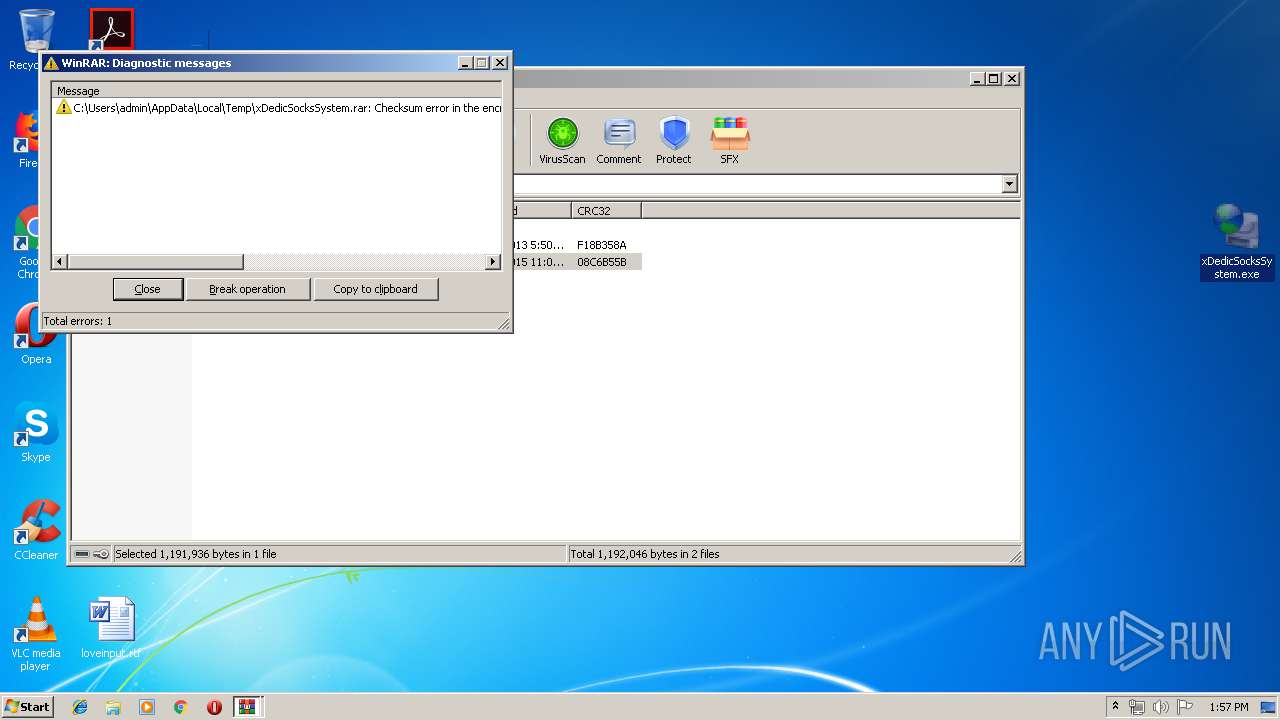
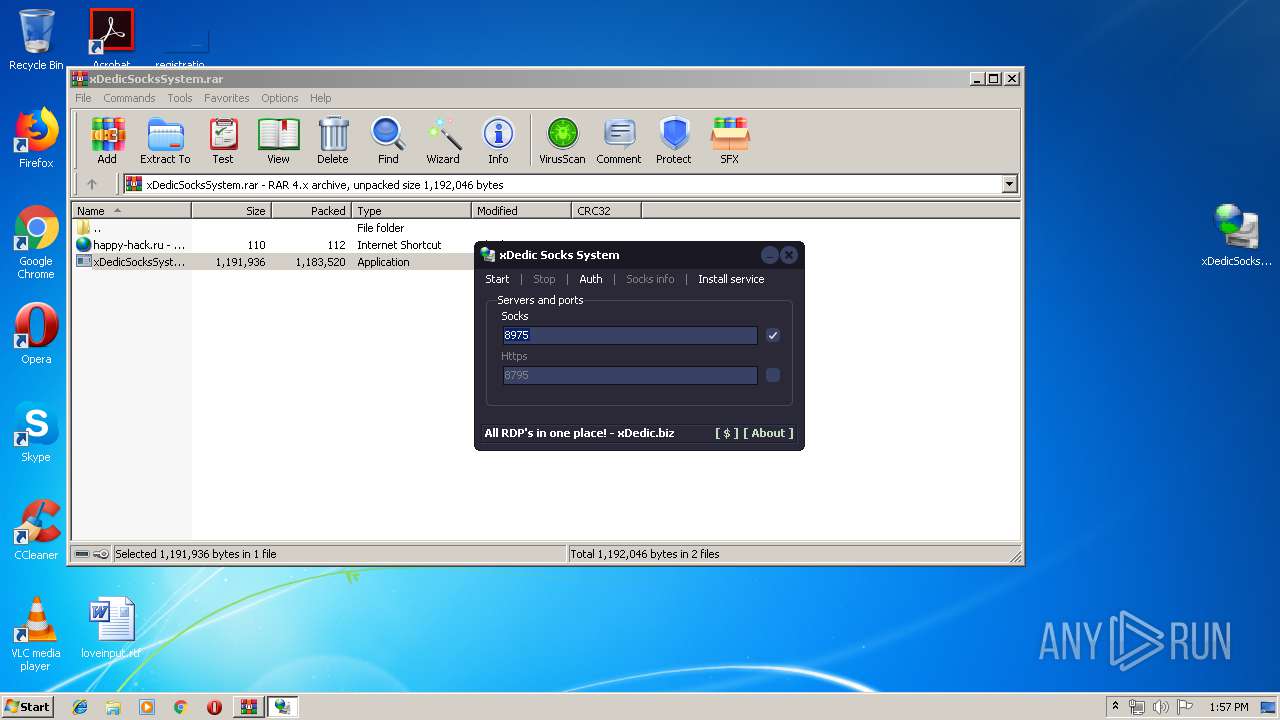
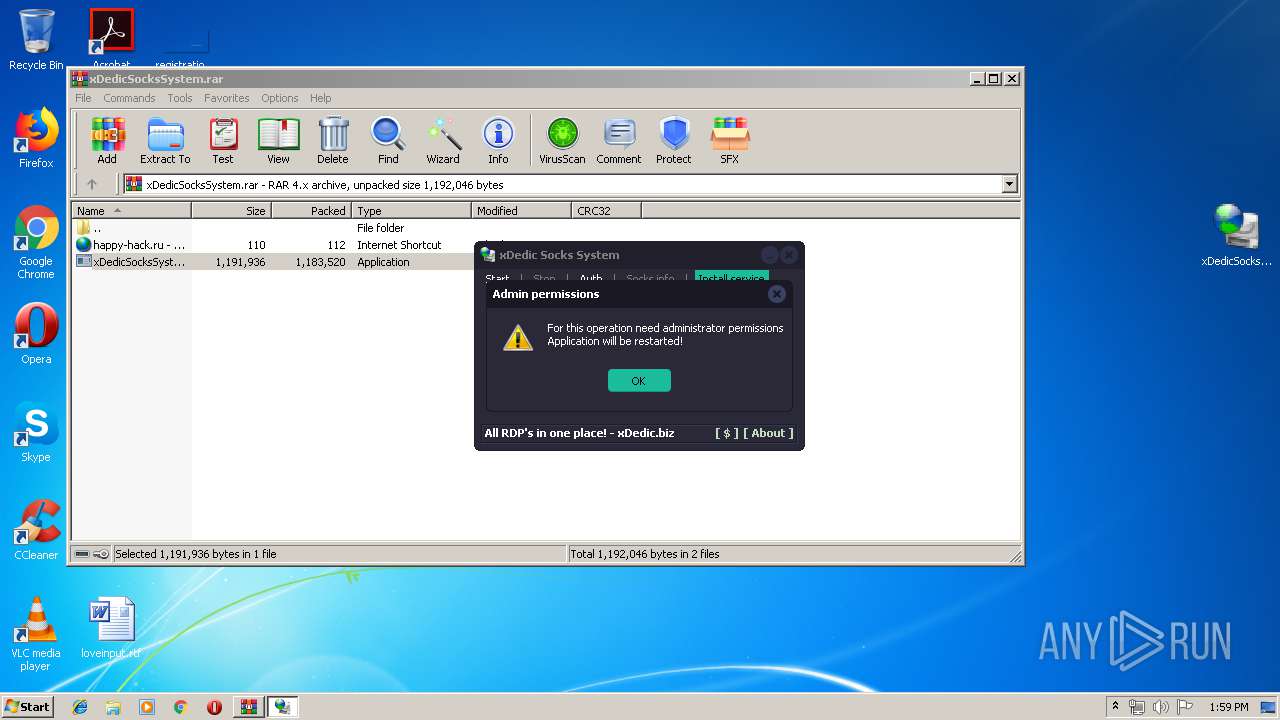
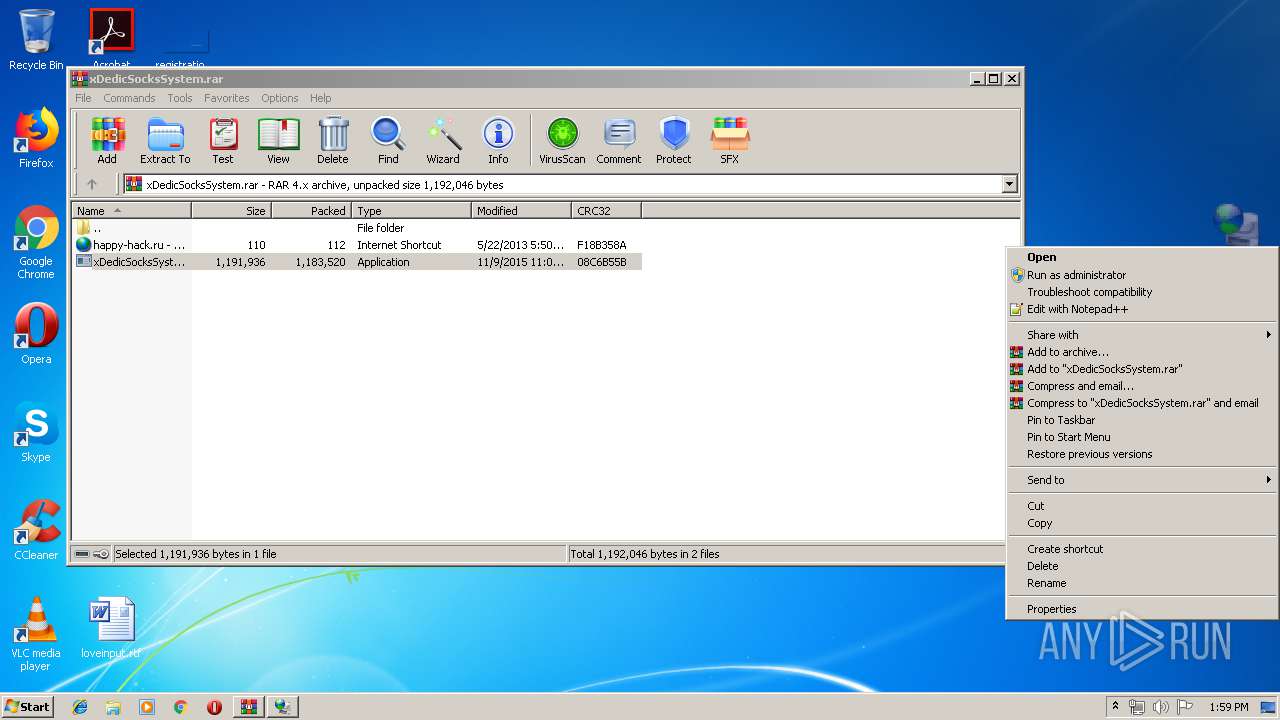
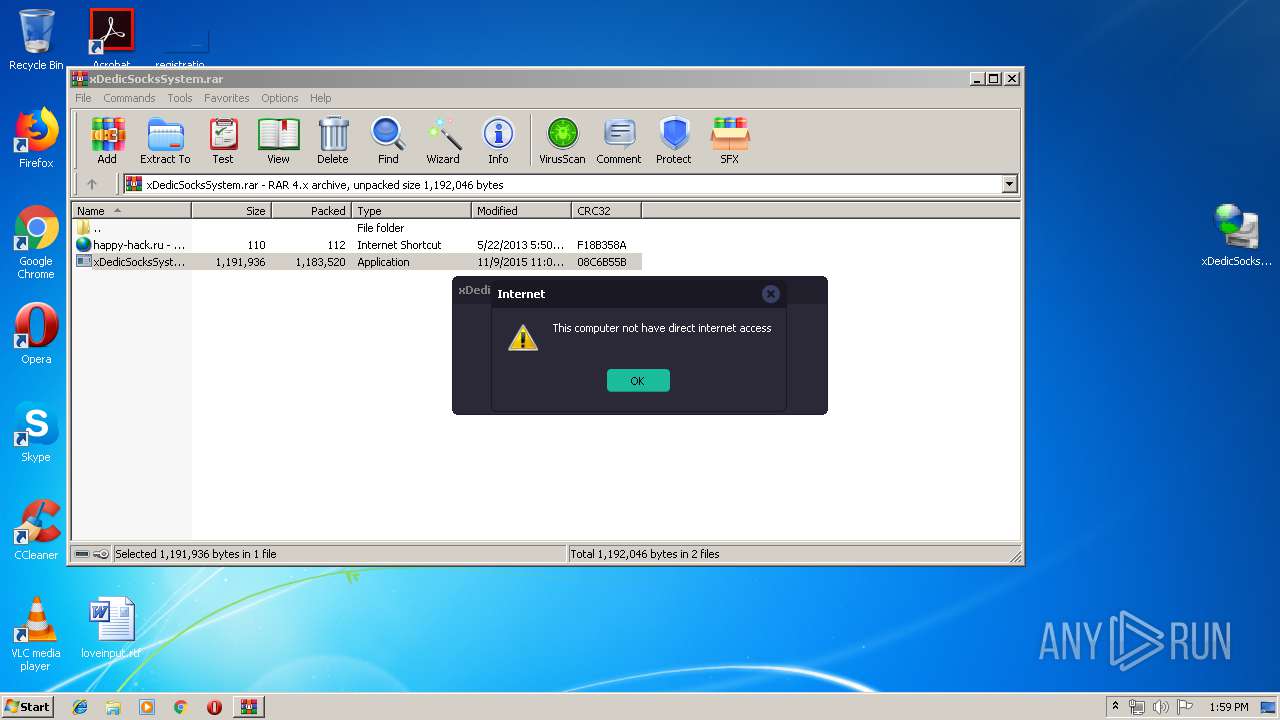
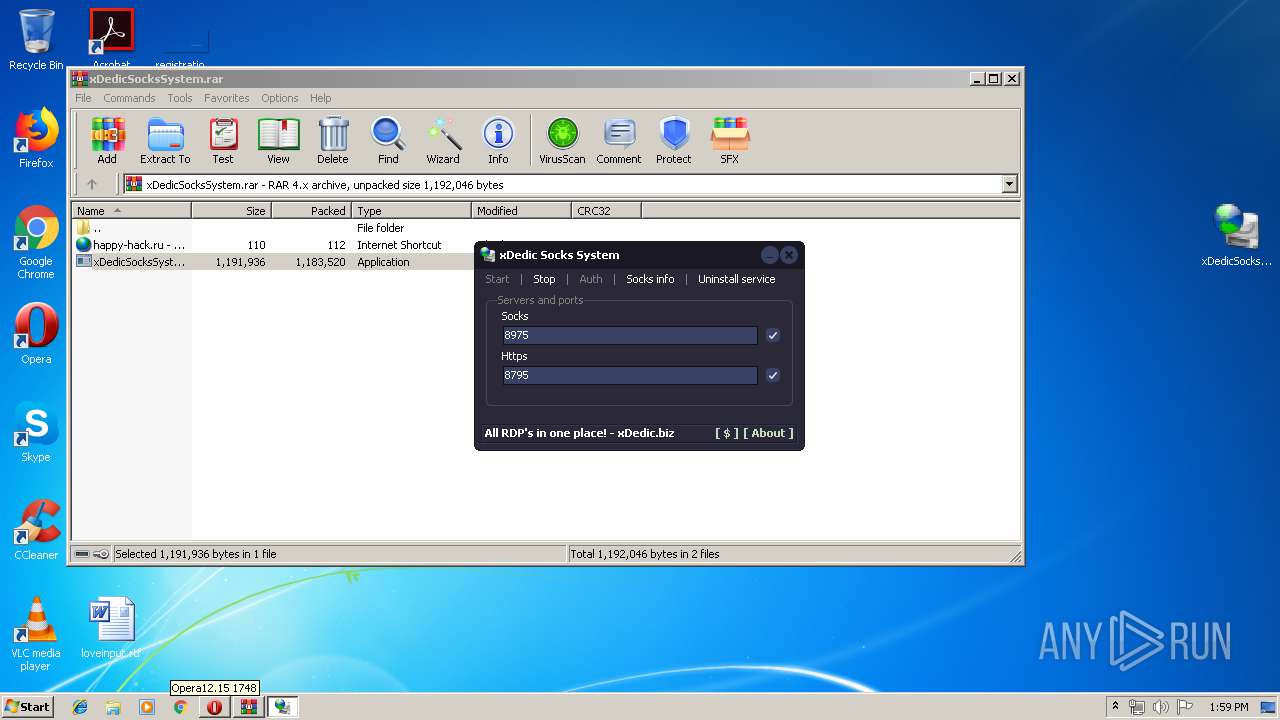
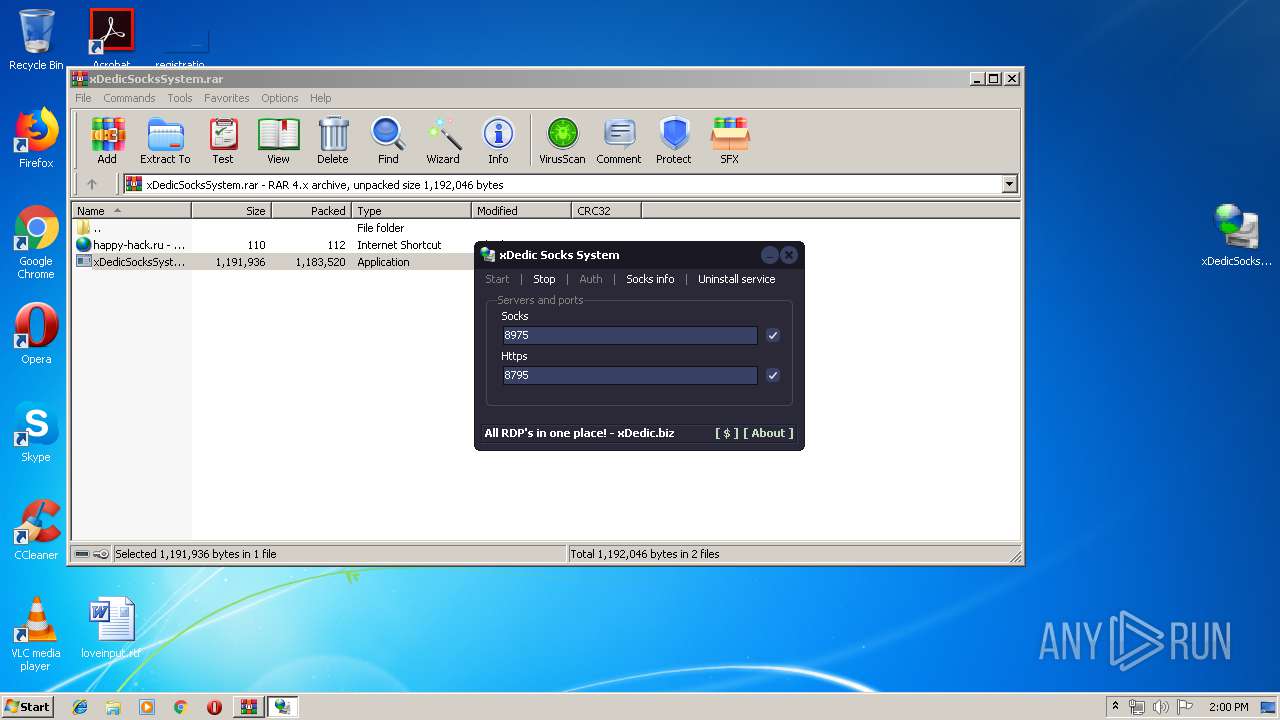
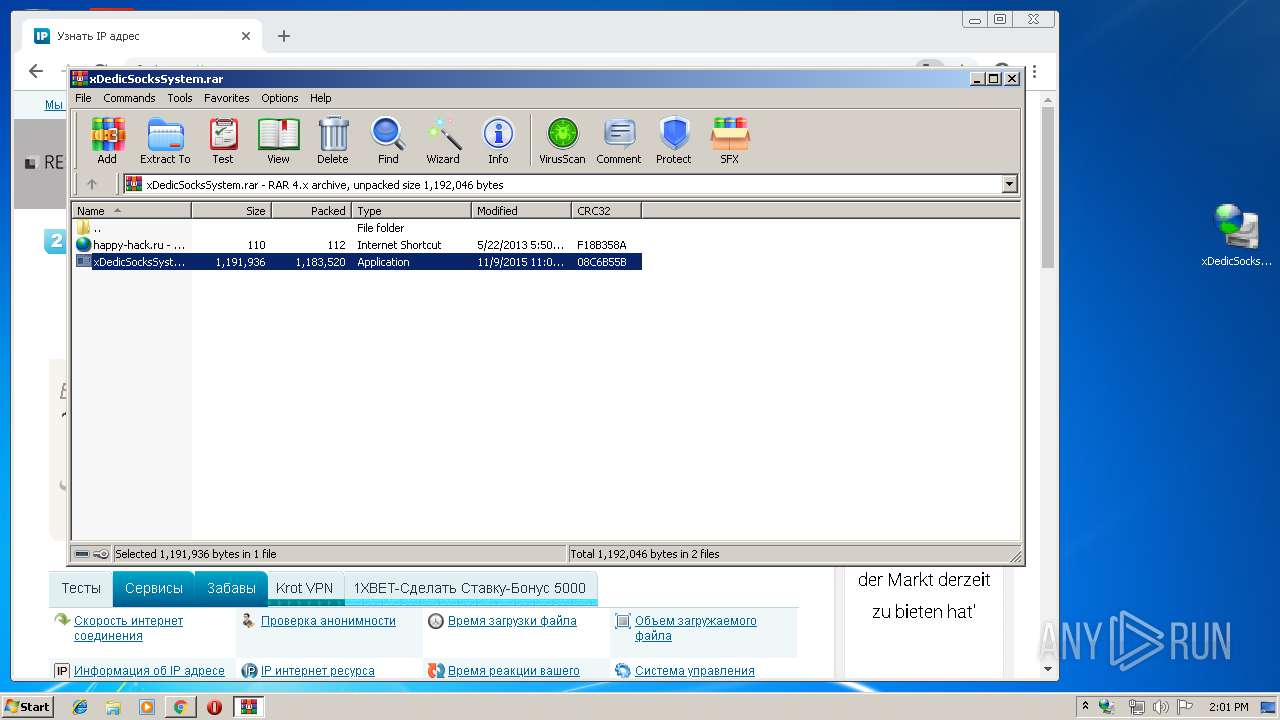
| File name: | xDedicSocksSystem.rar |
| Full analysis: | https://app.any.run/tasks/2c3386bb-863f-41cc-9fcd-062e9b72bb16 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2019, 12:56:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 4274FE190C95A468704D71C3FFD35DBC |
| SHA1: | EC9FE6D6E841FF48E5095B43E4D5D1242FB6DA26 |
| SHA256: | EBA92FA57E767C73303175BB47DDF73AE8850C6514FAF889947E8ED989AEB1EC |
| SSDEEP: | 24576:Du89+kUHuHB/iG4Vpc4BIUP+AtexRKpowXJuMZNo5GgODYhv5:KnksuhUwYrgKxB+vhx |
MALICIOUS
Application was dropped or rewritten from another process
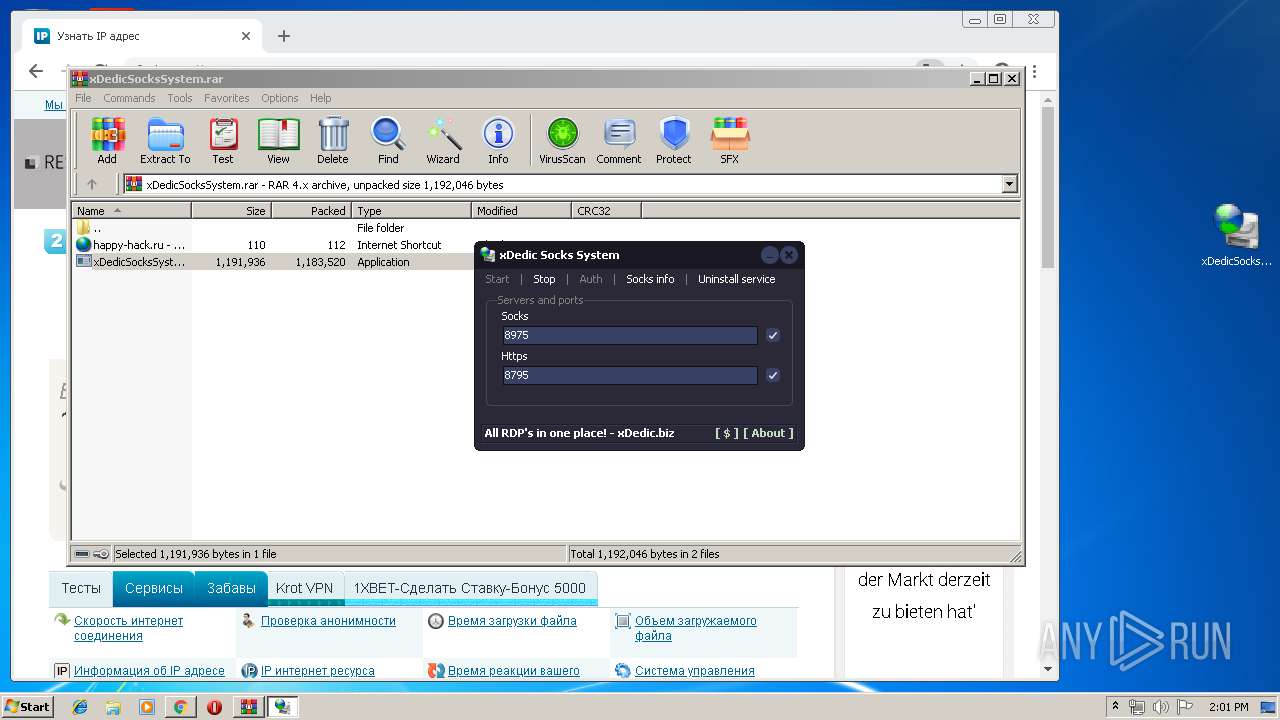
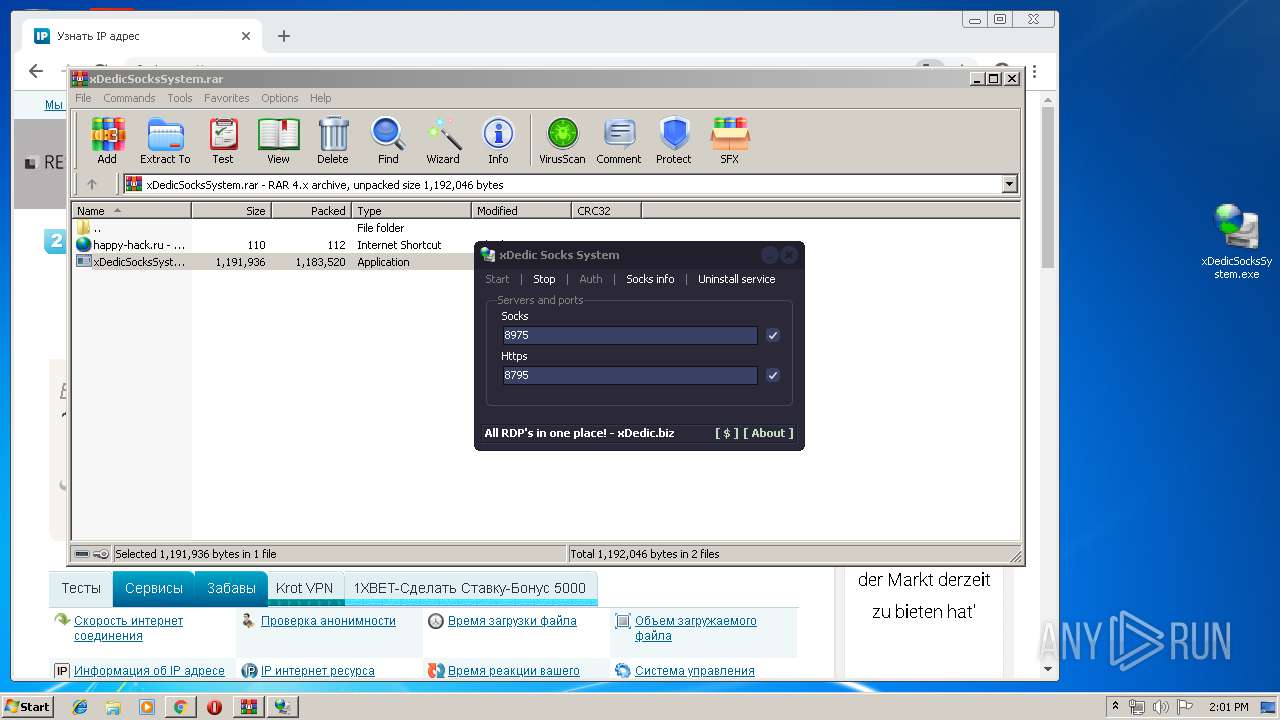
- xDedicSocksSystem.exe (PID: 1868)
- xDedicSocksSystem.exe (PID: 2592)
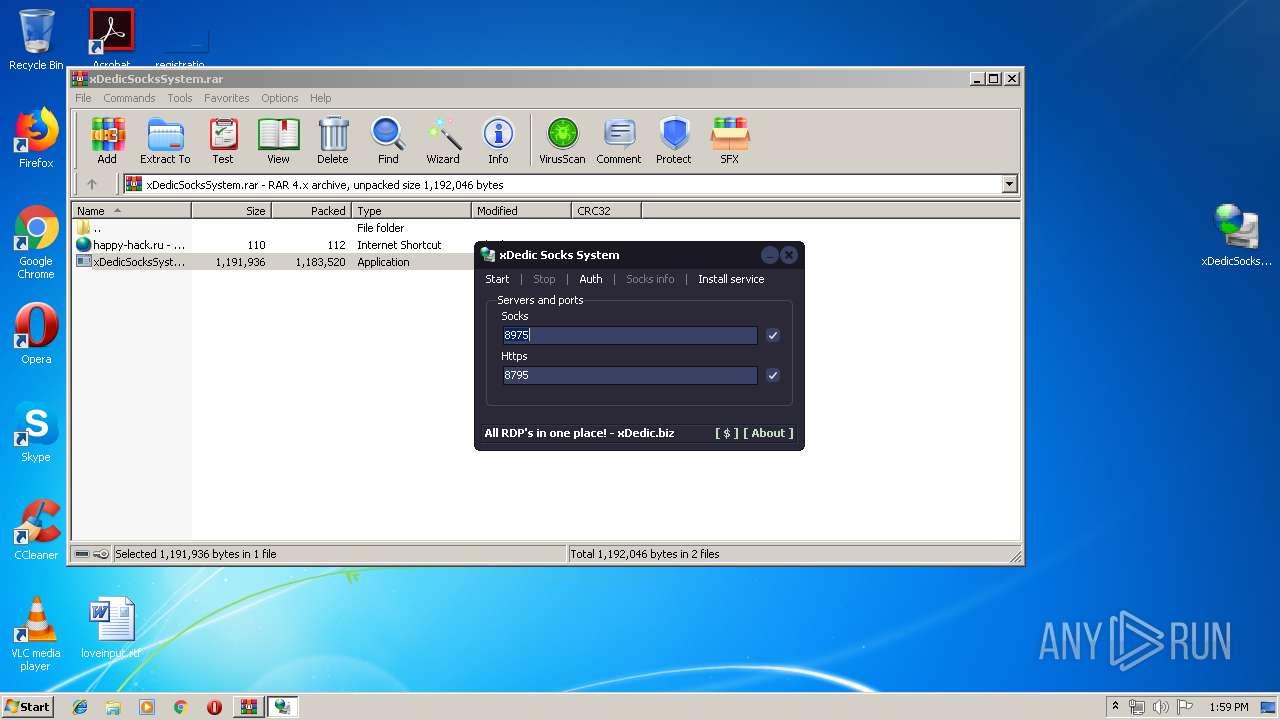
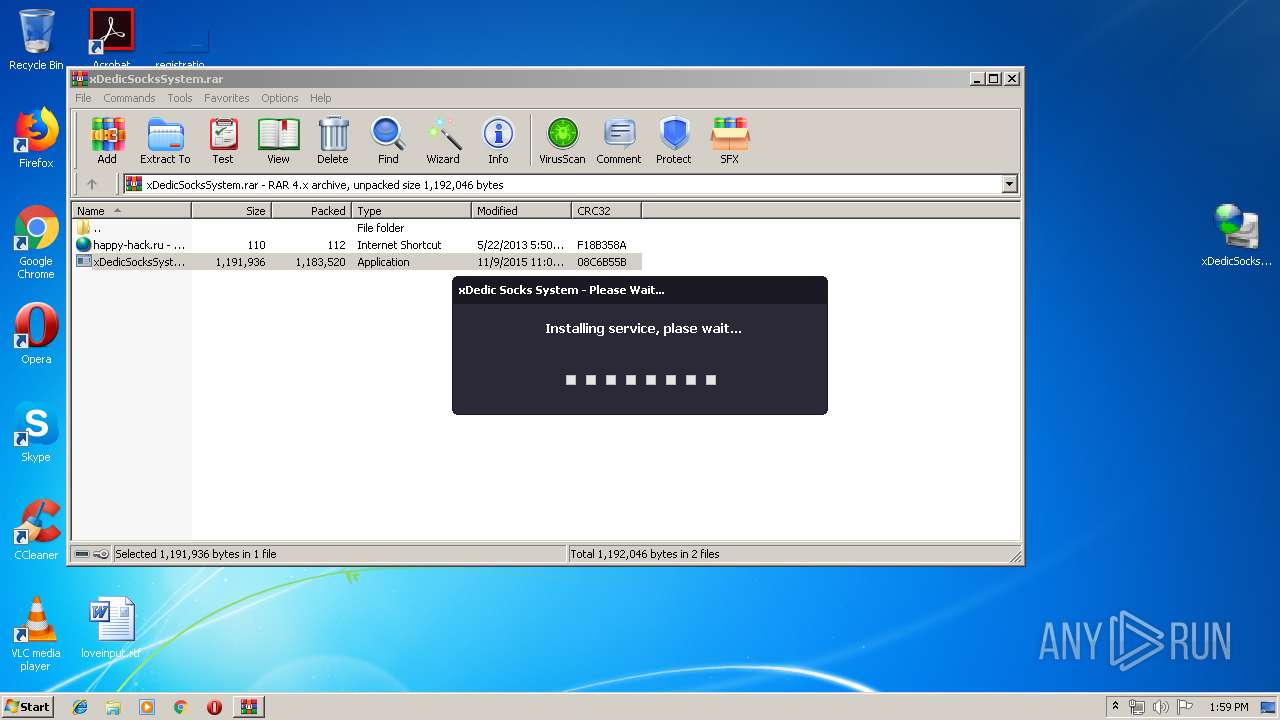
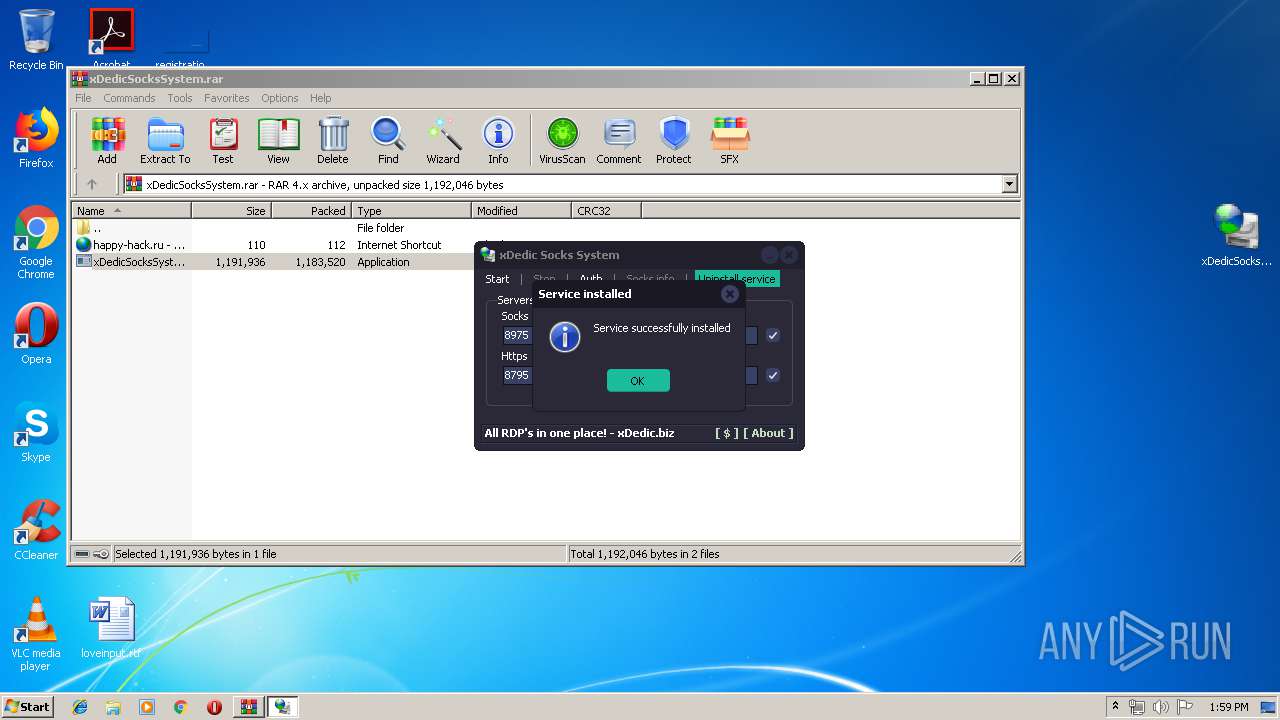
- pxsrvc.exe (PID: 2560)
SUSPICIOUS
Executable content was dropped or overwritten
- xDedicSocksSystem.exe (PID: 1868)
Starts SC.EXE for service management
- cmd.exe (PID: 3468)
- cmd.exe (PID: 2476)
Starts CMD.EXE for commands execution
- xDedicSocksSystem.exe (PID: 1868)
Application launched itself
- xDedicSocksSystem.exe (PID: 2592)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3972)
- cmd.exe (PID: 2816)
Creates files in the Windows directory
- xDedicSocksSystem.exe (PID: 1868)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2196)
INFO
Creates files in the user directory
- opera.exe (PID: 1448)
Reads settings of System Certificates
- chrome.exe (PID: 2196)
Application launched itself
- chrome.exe (PID: 2196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1183575 |
|---|---|
| UncompressedSize: | 1191936 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2015:11:09 23:03:12 |
| PackingMethod: | Normal |
| ArchivedFileName: | xDedicSocksSystem.exe |
Total processes
81
Monitored processes
43
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14319624467611362868,9694720719439931870,131072 --enable-features=PasswordImport --service-pipe-token=1773371460948500948 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1773371460948500948 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2164 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
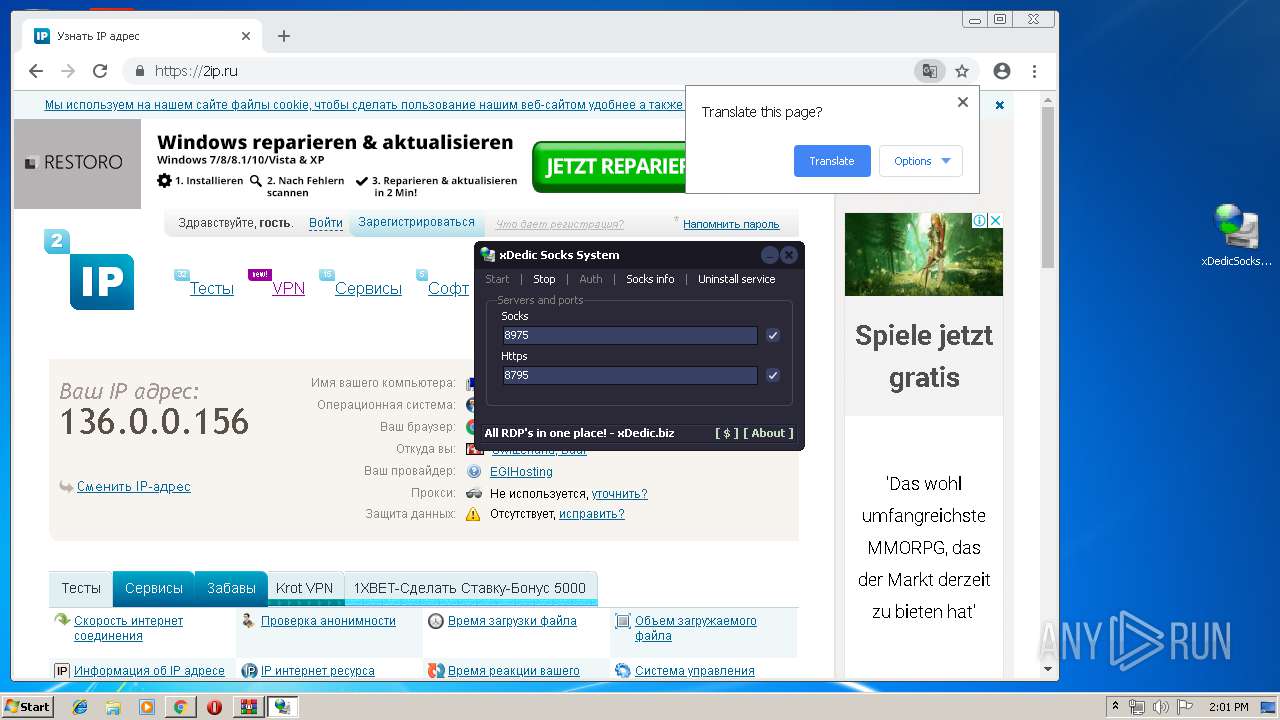
| 288 | netsh firewall add portopening TCP 8795 system | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14319624467611362868,9694720719439931870,131072 --enable-features=PasswordImport --service-pipe-token=9331067013382797684 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9331067013382797684 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1660 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,14319624467611362868,9694720719439931870,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=3143741305351752639 --mojo-platform-channel-handle=5504 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14319624467611362868,9694720719439931870,131072 --enable-features=PasswordImport --service-pipe-token=17544654737585910442 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17544654737585910442 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2172 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14319624467611362868,9694720719439931870,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16172153351662802795 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16172153351662802795 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4224 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1048 | sc create pxsrvc binPath= "C:\Windows\pxsrvc\pxsrvc.exe C:\Windows\pxsrvc\com --service" DisplayName= "COM+ Service Control" start= auto | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,14319624467611362868,9694720719439931870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14901976698302670745 --mojo-platform-channel-handle=2252 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1668 | netsh firewall add portopening TCP 8975 system | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 571
Read events
1 224
Write events
342
Delete events
5
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\xDedicSocksSystem.rar | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-10046 |
Value: Internet Shortcut | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
1
Suspicious files
171
Text files
190
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.42342\xDedicSocksSystem.exe | — | |
MD5:— | SHA256:— | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3976.44091\xDedicSocksSystem.exe | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprCD36.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprCD66.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DDUGH76GWQ9GGNQOZ9R3.temp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr1964.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr253D.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DQFPWRCTBQYOFNBPCFIC.temp | — | |
MD5:— | SHA256:— | |||
| 1448 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr2F50.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
90
DNS requests
59
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
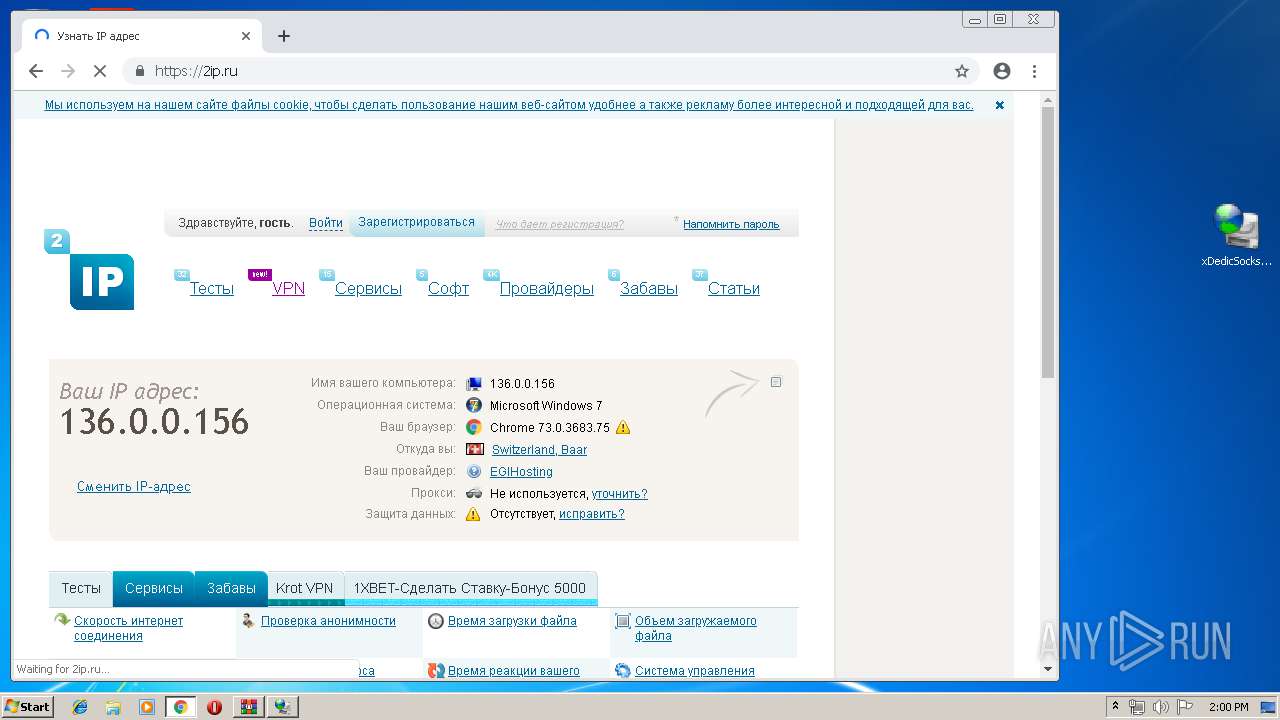
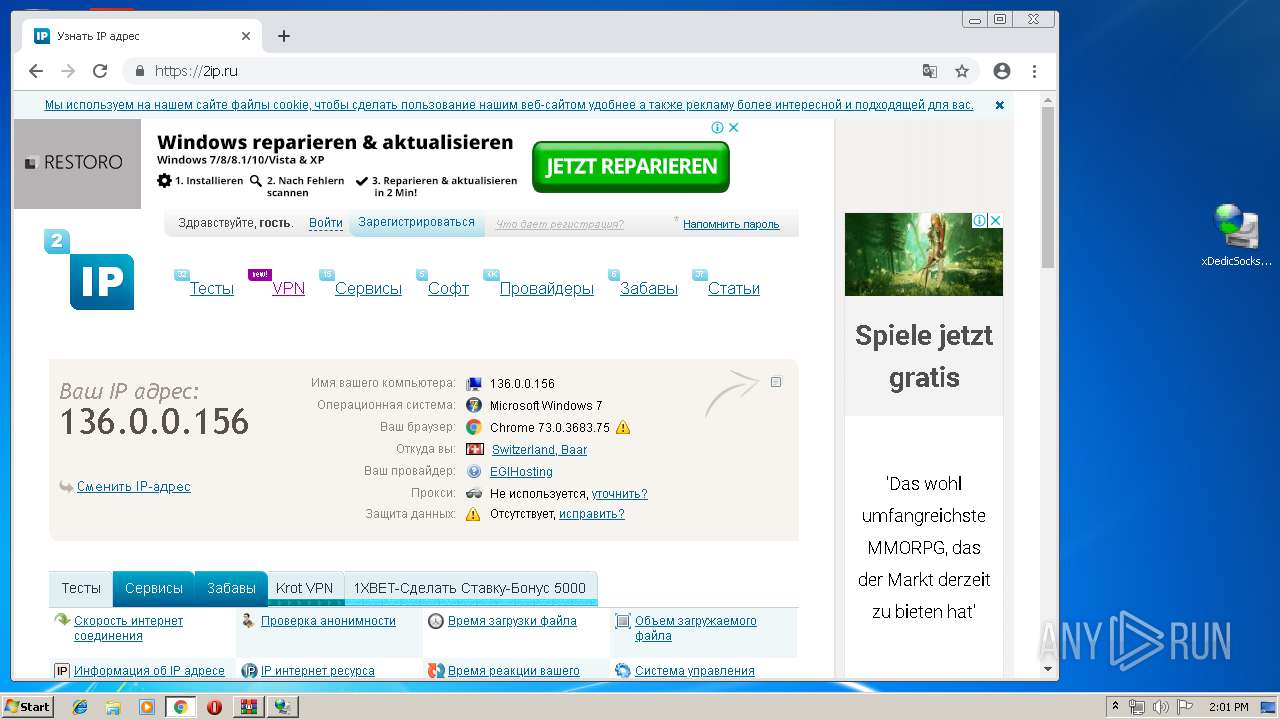
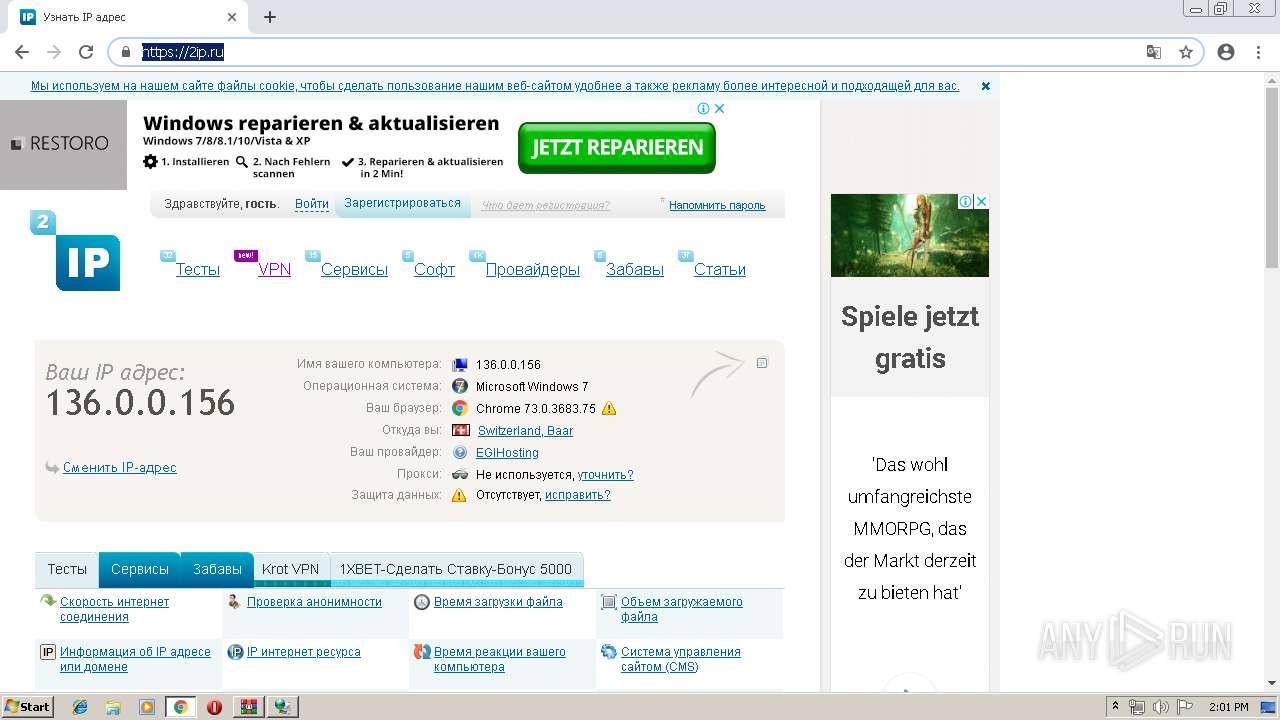
2196 | chrome.exe | GET | 301 | 195.201.201.32:80 | http://2ip.ru/ | RU | — | — | shared |
2592 | xDedicSocksSystem.exe | GET | 301 | 151.101.2.219:80 | http://www.speedtest.net/speedtest-config.php | US | — | — | whitelisted |
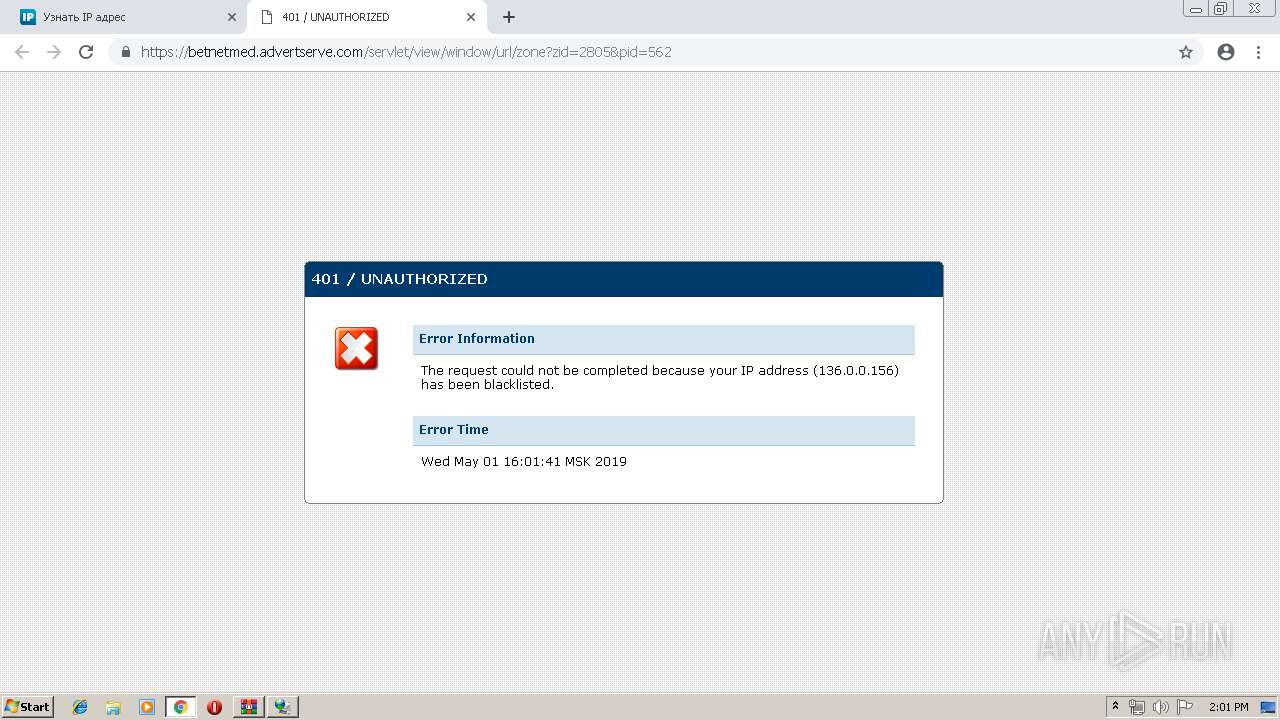
1448 | opera.exe | GET | 301 | 94.142.154.71:80 | http://myip.is/ | IS | html | 297 b | suspicious |
2196 | chrome.exe | GET | 302 | 172.217.21.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 502 b | whitelisted |
1448 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
2196 | chrome.exe | GET | 200 | 217.146.165.206:80 | http://r3---sn-oun-1gie.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=136.0.0.156&mm=28&mn=sn-oun-1gie&ms=nvh&mt=1556714930&mv=u&pl=20&shardbypass=yes | CH | crx | 842 Kb | whitelisted |
1448 | opera.exe | GET | 200 | 216.58.206.14:80 | http://clients1.google.com/complete/search?q=myip&client=opera-suggest-omnibox&hl=de | US | text | 102 b | whitelisted |
1448 | opera.exe | GET | 400 | 185.26.182.93:80 | http://sitecheck2.opera.com/?host=myip.is&hdn=wHt6IgMW24yIRQQaucDUnQ== | unknown | html | 150 b | whitelisted |
1448 | opera.exe | GET | 200 | 216.58.206.14:80 | http://clients1.google.com/complete/search?q=myi&client=opera-suggest-omnibox&hl=de | US | text | 99 b | whitelisted |
1868 | xDedicSocksSystem.exe | GET | 301 | 151.101.2.219:80 | http://www.speedtest.net/speedtest-config.php | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2592 | xDedicSocksSystem.exe | 151.101.2.219:80 | www.speedtest.net | Fastly | US | suspicious |
1868 | xDedicSocksSystem.exe | 151.101.2.219:80 | www.speedtest.net | Fastly | US | suspicious |
1448 | opera.exe | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
1448 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1448 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
1448 | opera.exe | 216.58.206.14:80 | clients1.google.com | Google Inc. | US | whitelisted |
1448 | opera.exe | 94.142.154.71:80 | myip.is | Opin Kerfi ehf | IS | unknown |
— | — | 185.26.182.93:80 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
— | — | 94.142.154.71:443 | myip.is | Opin Kerfi ehf | IS | unknown |
1448 | opera.exe | 94.142.154.71:443 | myip.is | Opin Kerfi ehf | IS | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.speedtest.net |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clients1.google.com |
| whitelisted |
myip.is |
| suspicious |
sitecheck2.opera.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
Threats
5 ETPRO signatures available at the full report