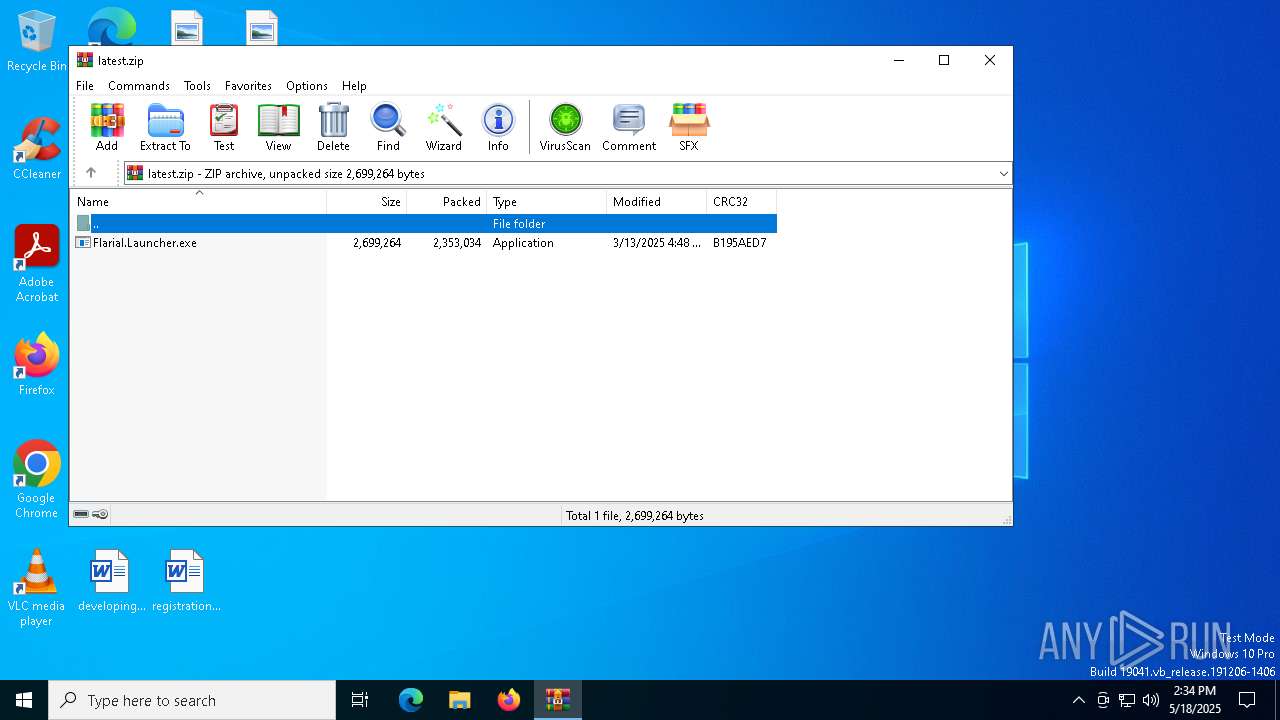
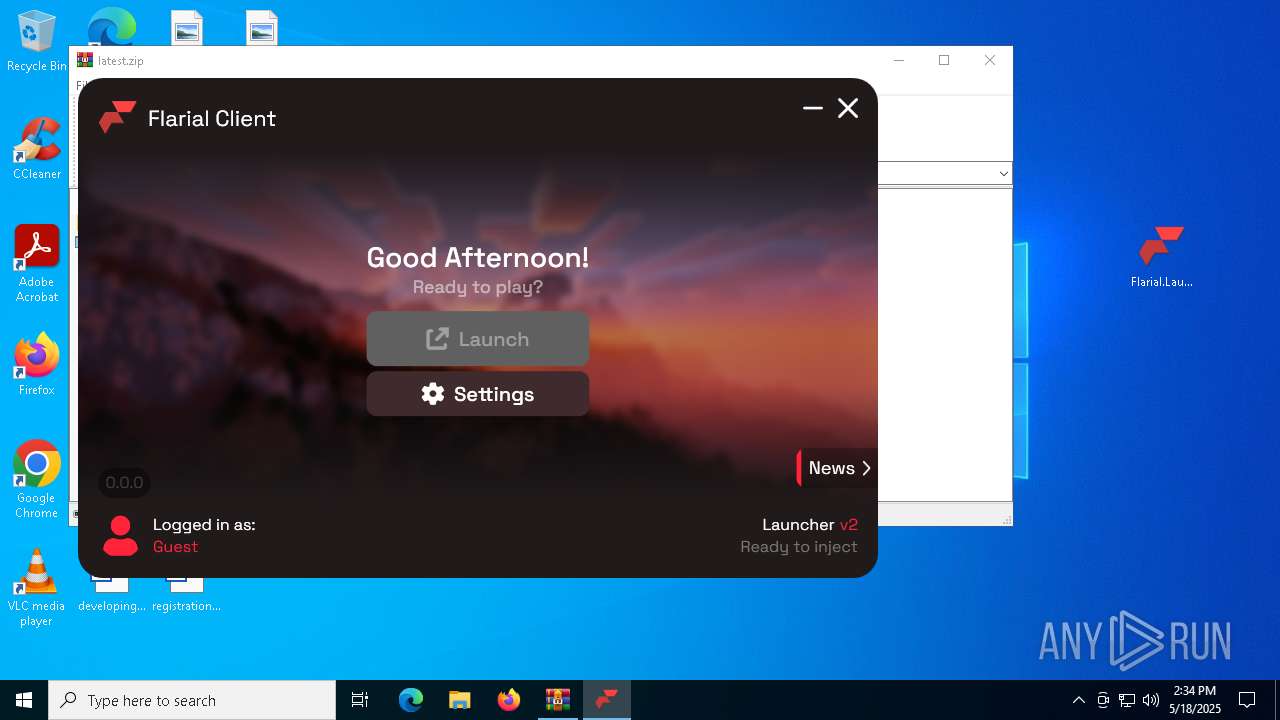
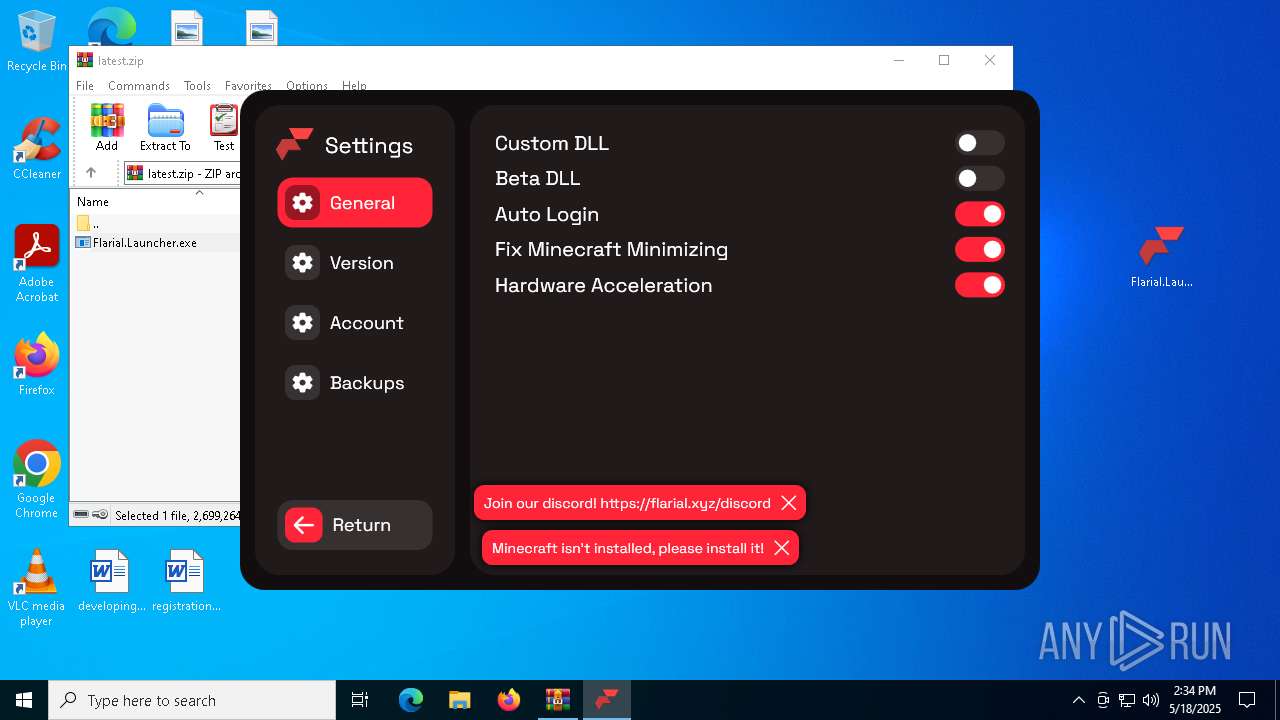
| File name: | latest.zip |
| Full analysis: | https://app.any.run/tasks/b3763919-6f02-4456-b254-4ce8498540c4 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 14:34:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A18EC388BF5F05664C28BDA26ADFA668 |
| SHA1: | 3D925E28D6DE3C019BB44E450812A6139A15C306 |
| SHA256: | EB9FCFA3061118355CF71DBFFBDB5CA9C6815150711BA9B21E07FE0587EF196B |
| SSDEEP: | 98304:ZSqeWa5jJZj351OqTEvlIeC/1v1/jzEM/CSyxXNmDnshoPYAcWnoDlrSYzEez8S/:YAGnuXrl |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2616)
Execute application with conhost.exe as parent process
- cmd.exe (PID: 7740)
SUSPICIOUS
Executable content was dropped or overwritten
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 7716)
Reads security settings of Internet Explorer
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Executing commands from ".cmd" file
- conhost.exe (PID: 7716)
Reads the date of Windows installation
- Flarial.Launcher.exe (PID: 7380)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7740)
Process drops legitimate windows executable
- Flarial.Launcher.exe (PID: 7872)
- Flarial.Launcher.exe (PID: 7380)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2616)
Manual execution by a user
- Flarial.Launcher.exe (PID: 7380)
Reads the software policy settings
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
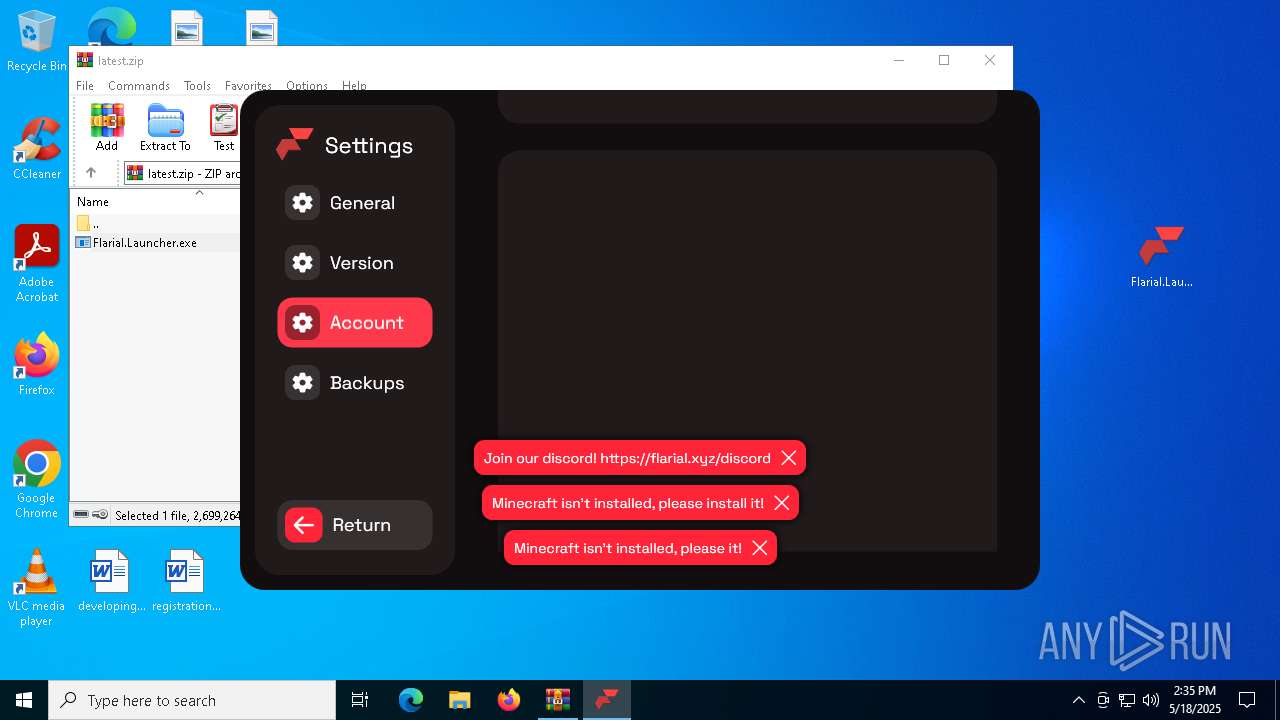
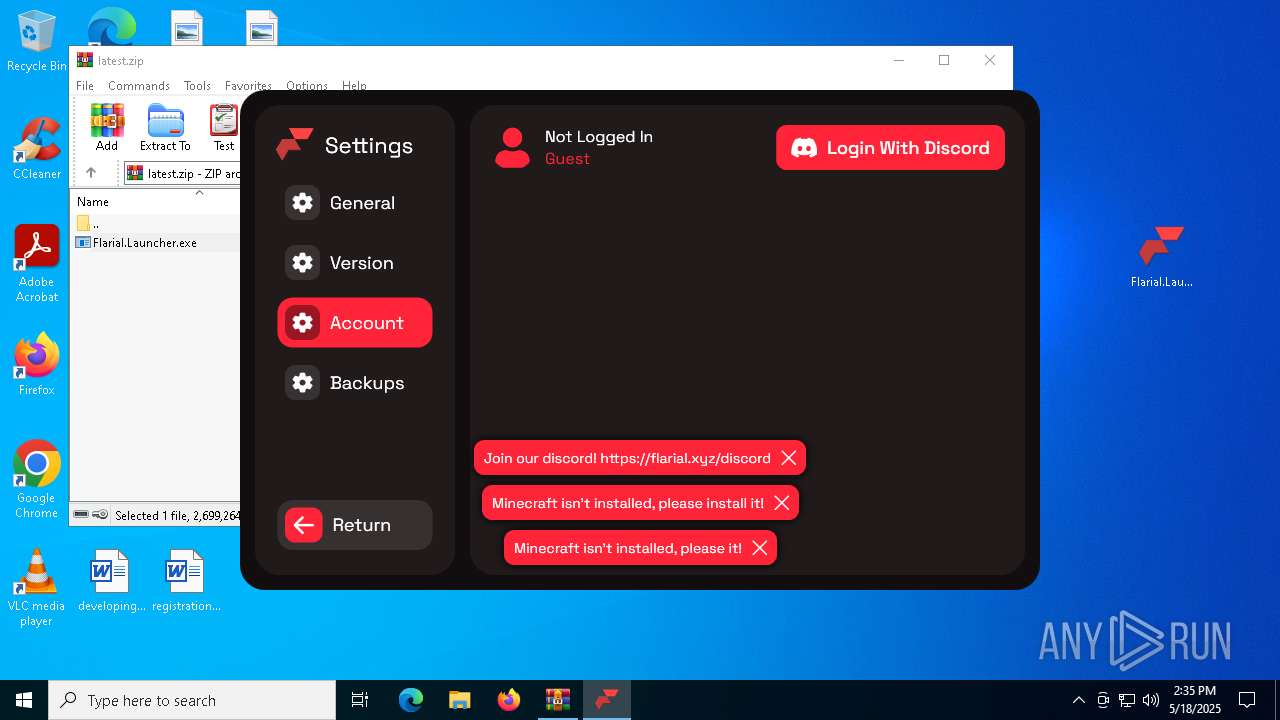
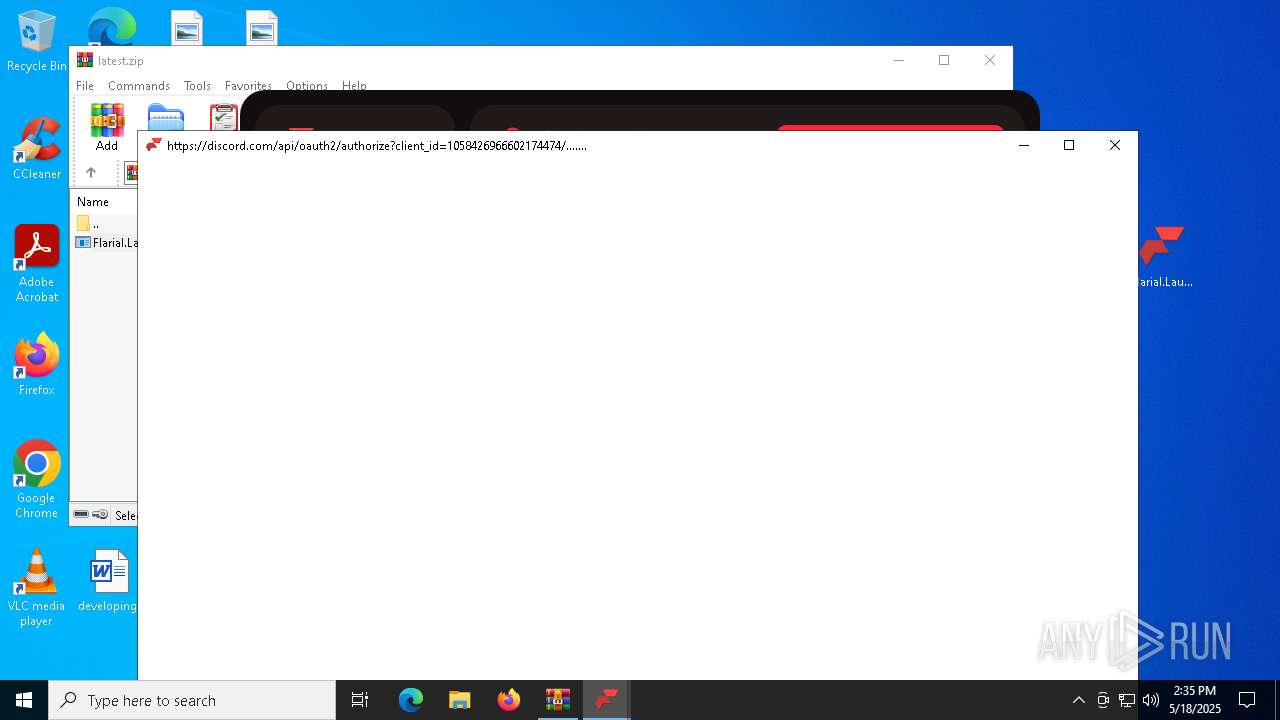
Attempting to use instant messaging service
- Flarial.Launcher.exe (PID: 7380)
Disables trace logs
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Checks proxy server information
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Reads Environment values
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Process checks computer location settings
- Flarial.Launcher.exe (PID: 7380)
Create files in a temporary directory
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Reads the computer name
- Flarial.Launcher.exe (PID: 7380)
- Flarial.Launcher.exe (PID: 7872)
Checks supported languages
- Flarial.Launcher.exe (PID: 7872)
- Flarial.Launcher.exe (PID: 7380)
The sample compiled with english language support
- Flarial.Launcher.exe (PID: 7872)
- Flarial.Launcher.exe (PID: 7380)
Reads the machine GUID from the registry
- Flarial.Launcher.exe (PID: 7872)
- Flarial.Launcher.exe (PID: 7380)
Creates files or folders in the user directory
- Flarial.Launcher.exe (PID: 7872)
- Flarial.Launcher.exe (PID: 7380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:13 10:48:30 |
| ZipCRC: | 0xb195aed7 |
| ZipCompressedSize: | 2353034 |
| ZipUncompressedSize: | 2699264 |
| ZipFileName: | Flarial.Launcher.exe |
Total processes
134
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2616 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\latest.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7248 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7280 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
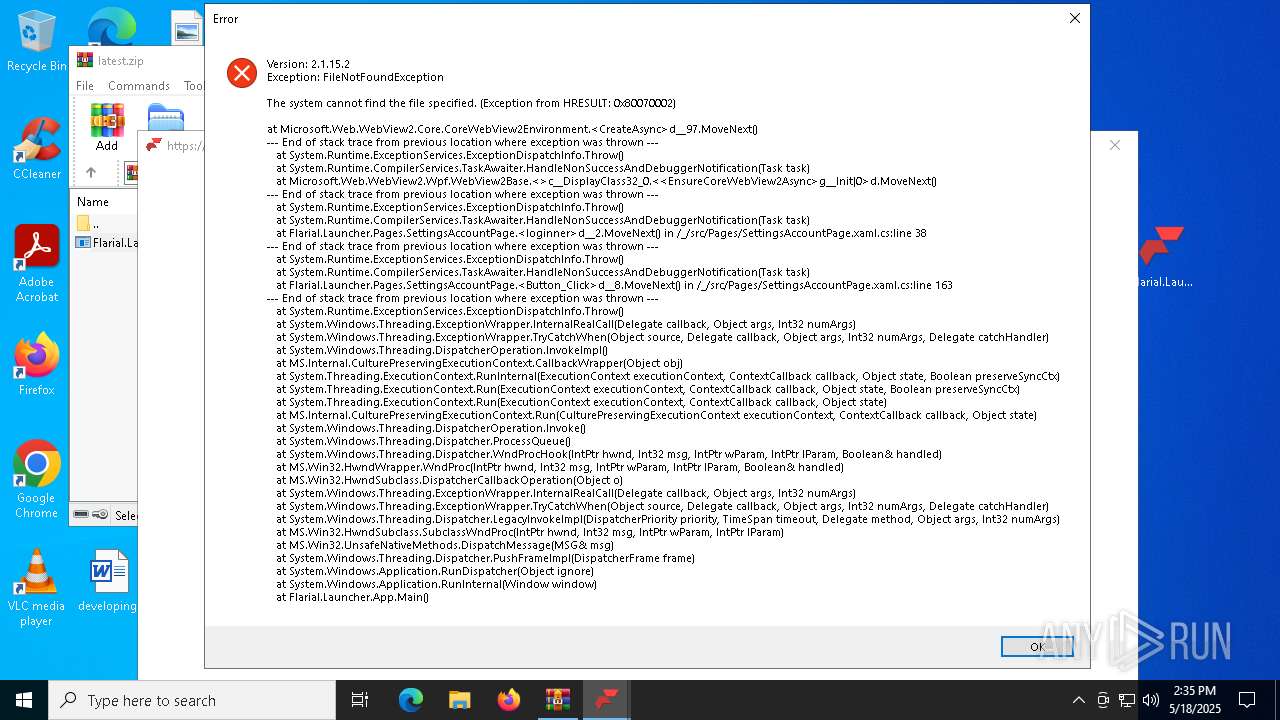
| 7380 | "C:\Users\admin\Desktop\Flarial.Launcher.exe" | C:\Users\admin\Desktop\Flarial.Launcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 1 Version: 2.1.7.0 Modules
| |||||||||||||||
| 7716 | "C:\WINDOWS\system32\conhost.exe" --headless "C:\Users\admin\AppData\Local\Temp\uqugw5aq.cmd" | C:\Windows\System32\conhost.exe | — | Flarial.Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7740 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\uqugw5aq.cmd | C:\Windows\System32\cmd.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7776 | "C:\WINDOWS\System32\TASKKILL.exe" /F /PID 7380 | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7872 | "C:\Users\admin\Desktop\Flarial.Launcher.exe" | C:\Users\admin\Desktop\Flarial.Launcher.exe | cmd.exe | ||||||||||||
User: admin Company: Flarial Integrity Level: MEDIUM Description: Flarial Launcher Exit code: 0 Version: 2.1.15.2 Modules
| |||||||||||||||
Total events
6 649
Read events
6 621
Write events
28
Delete events
0
Modification events
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\latest.zip | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7380) Flarial.Launcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Flarial_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7380) Flarial.Launcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Flarial_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
4
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7380 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Temp\kcatnwti.uiu | executable | |
MD5:C2BA95C79F710AE669130879F6D4F78D | SHA256:BFBAD9D4B1E2C53187D67A03C027DA37268DD6269A9EE816D04BA344999CA36E | |||
| 2616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2616.19030\Flarial.Launcher.exe | executable | |
MD5:1497923F5F7986D7D456EF0766341B8B | SHA256:DA96506154ED30A1A1FB95C715ACD48A9D3791245D69358CC59704B32CC4363F | |||
| 7380 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Temp\uqugw5aq.cmd | text | |
MD5:AB28C2AFCF371AC1F2A284EFB1320C8D | SHA256:C0D24290DC37FCC957DAB084411C5ACDE1307952DB336D2B6EEA99EB4D40C0E6 | |||
| 7380 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial\Launcher\WebView2Loader.dll | executable | |
MD5:0AD9319FA14D39C0812583337546CA20 | SHA256:1D963A02D8A7FA3E7EAC2E936DAD5559C4D63327F35B0A09787FFC1D58F9C18D | |||
| 7872 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\WPFEDCF.tmp | image | |
MD5:E88180CAC9ACB9D5A7DA7A62E4238906 | SHA256:4C07398EC37F9B4A5ADAC14DB448C7D749F08A0C15690C44C2F9D99495EE4EB0 | |||
| 7380 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\WPFE265.tmp | image | |
MD5:E88180CAC9ACB9D5A7DA7A62E4238906 | SHA256:4C07398EC37F9B4A5ADAC14DB448C7D749F08A0C15690C44C2F9D99495EE4EB0 | |||
| 7872 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial\Launcher\Logs\2025-05-18-14-34-49.txt | text | |
MD5:A1D27ED1E28B3F947B2082AAB1908B37 | SHA256:8CA91B336625F90389A16AD0597D257574A7D2A0450CF3C6268BCD4BC0AF298F | |||
| 7872 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial\Launcher\config.txt | binary | |
MD5:7D31380309C890FDA73B5CDBB70AEAB9 | SHA256:64022E10BAF99AAAB90C032D13657C765C15F4C0EFBD13DC39BA3D00AA809932 | |||
| 7872 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Temp\Costura\A60509F4DD2C3060A7DF925552EE073D\win-x64\webview2loader.dll | executable | |
MD5:075E4272F2815B3B6BC7CAF0EBCC65AE | SHA256:1970AE5E398666304483203DAE64F8BC3327811114AE38BB3484ECBCE1386B41 | |||
| 7380 | Flarial.Launcher.exe | C:\Users\admin\AppData\Local\Flarial\Launcher\2025-05-18-14-34-46.txt | text | |
MD5:168AD9BBFDDE2B013D222EF44EA00A08 | SHA256:6253FD834617A6836E336E2D99E11408D8B102B88EC5A8A2CCCA2E1D803B7E58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
30
DNS requests
16
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7380 | Flarial.Launcher.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
media.discordapp.net |
| whitelisted |
cdn.discordapp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7380 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
7380 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
7872 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
7872 | Flarial.Launcher.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |