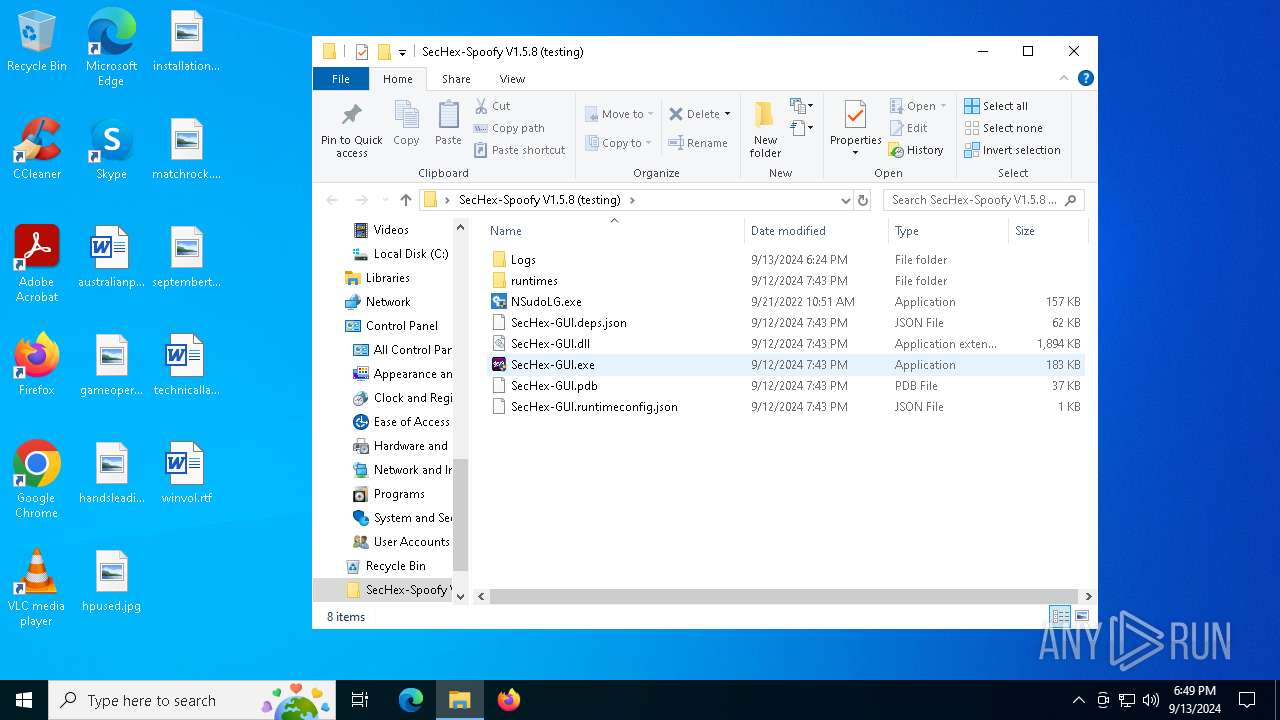
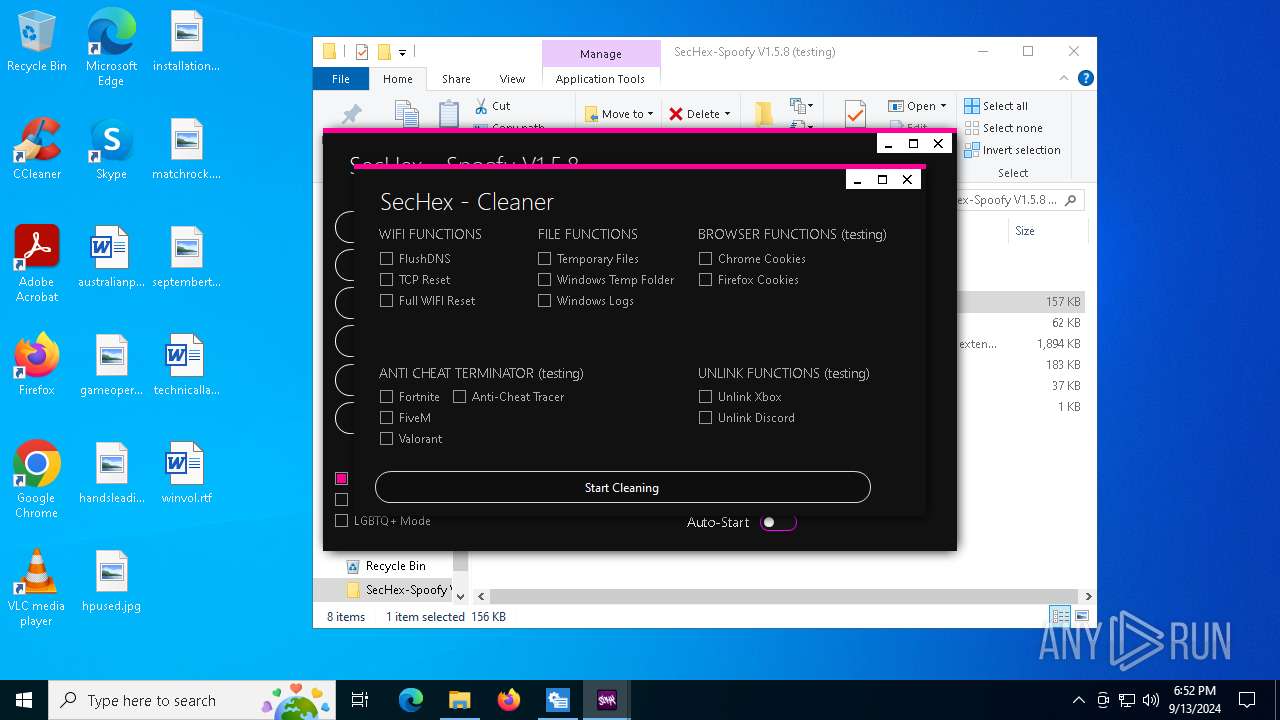
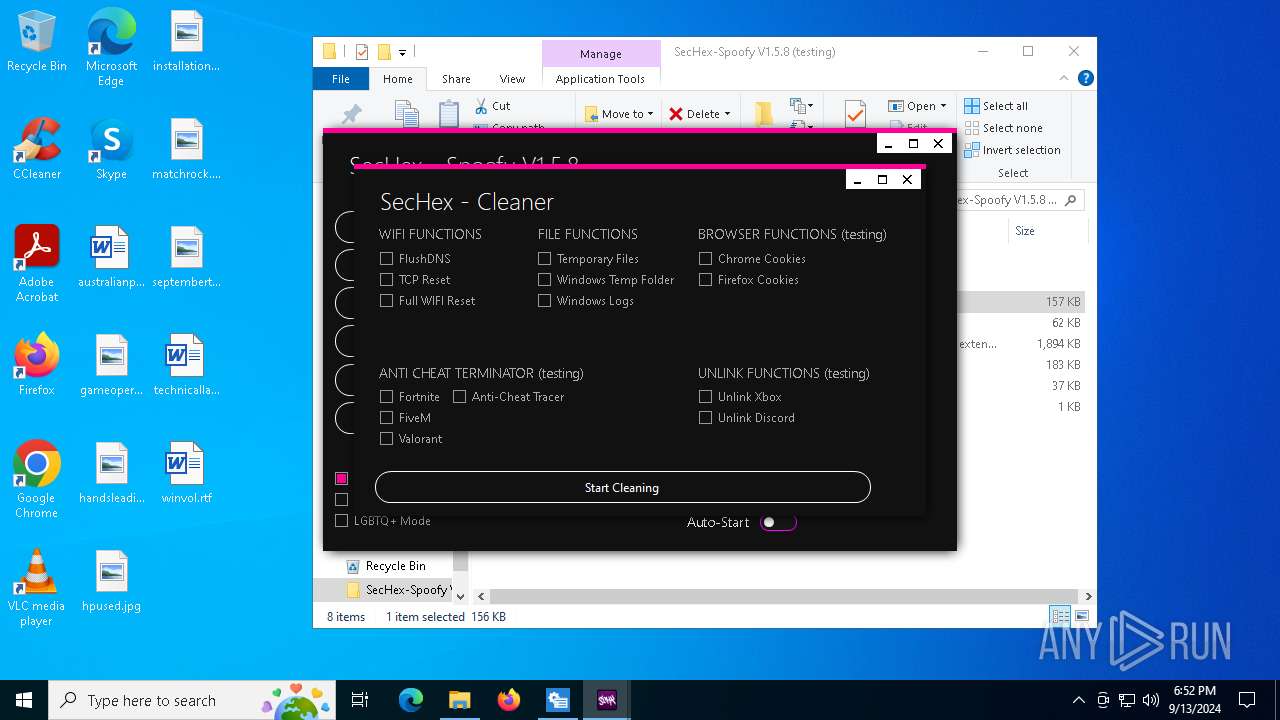
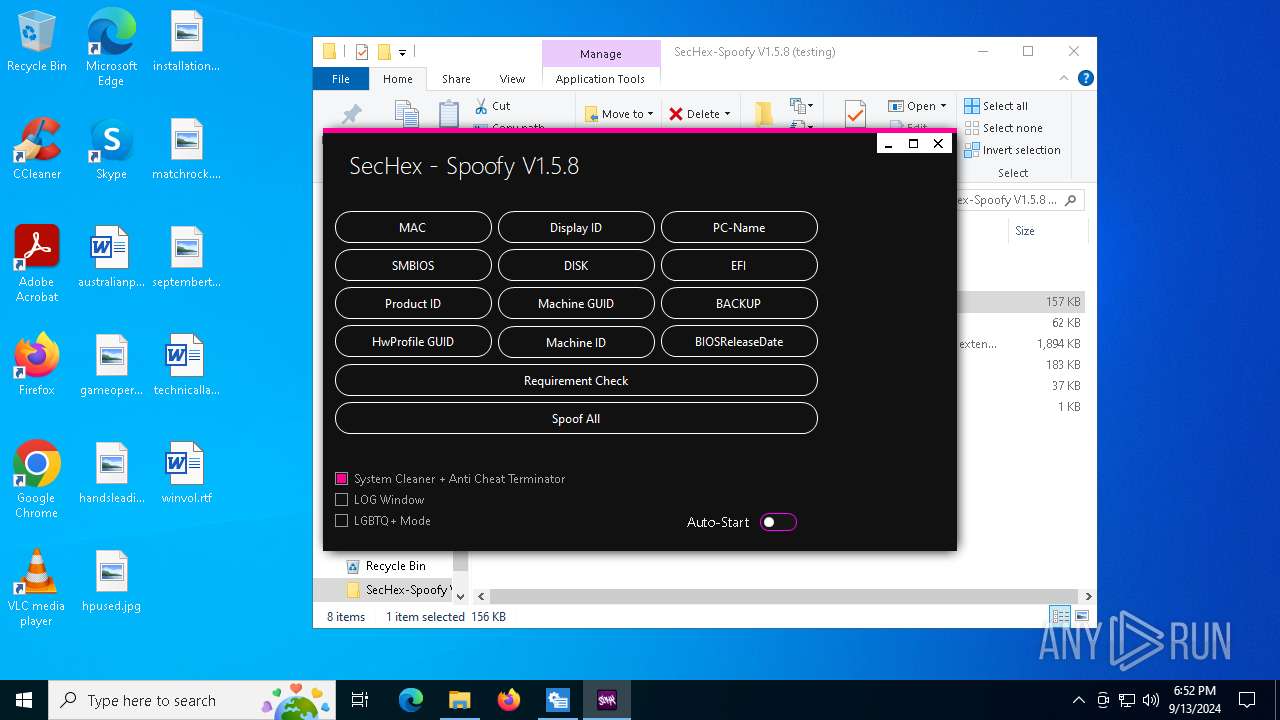
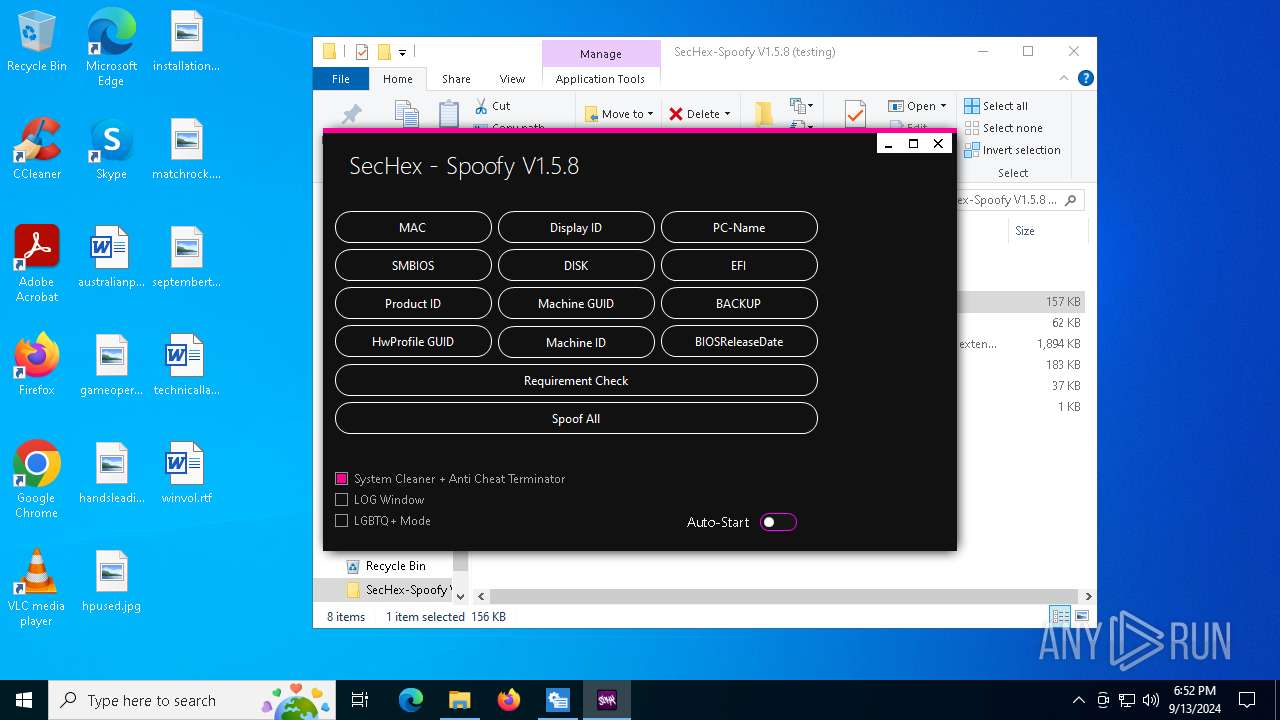
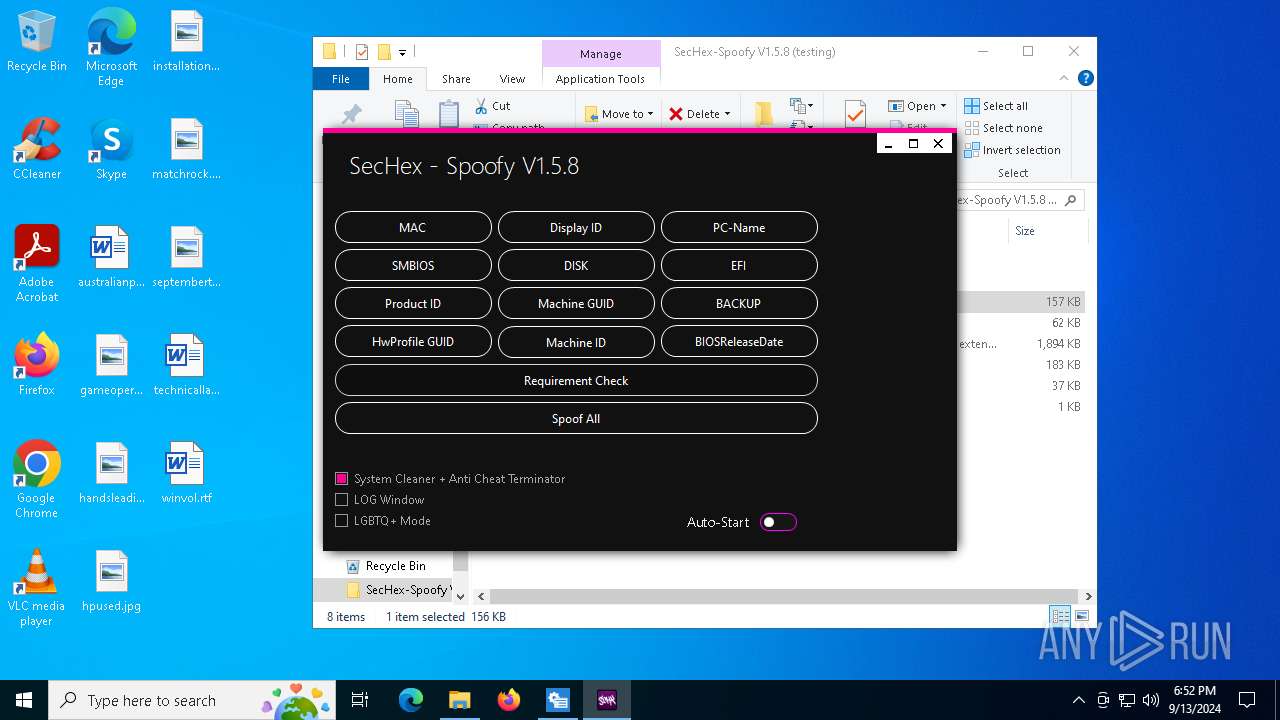
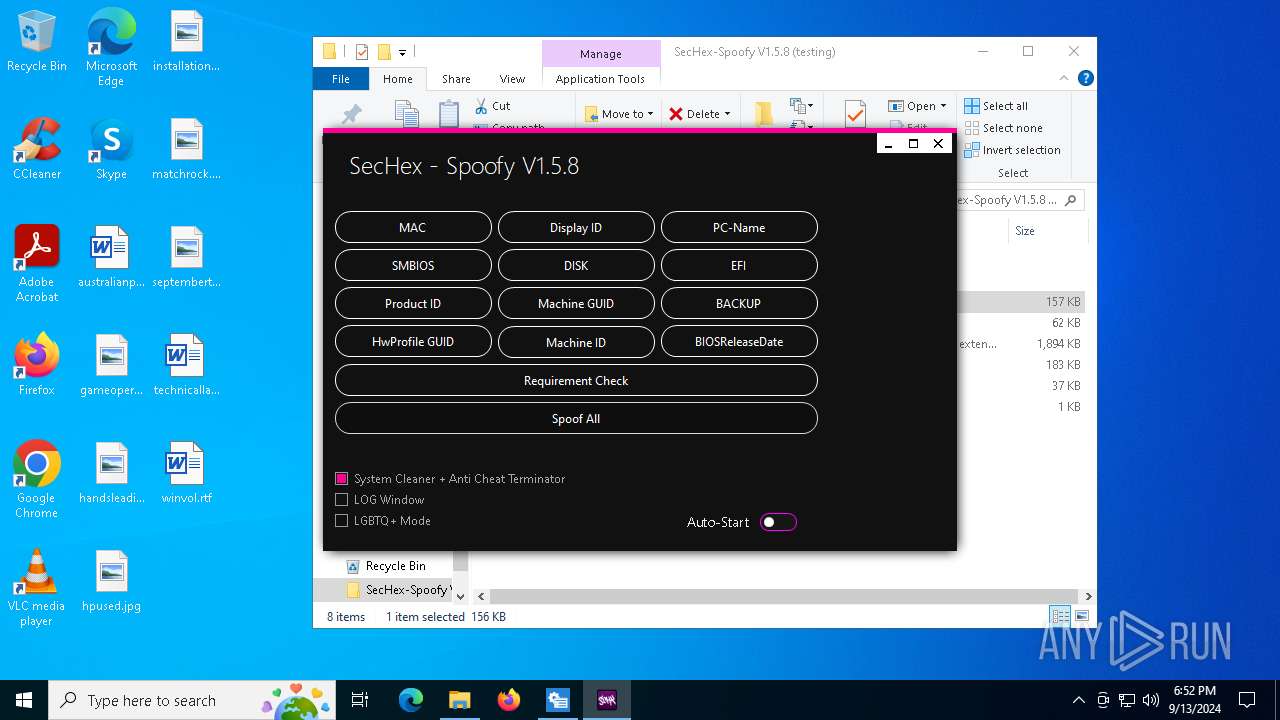
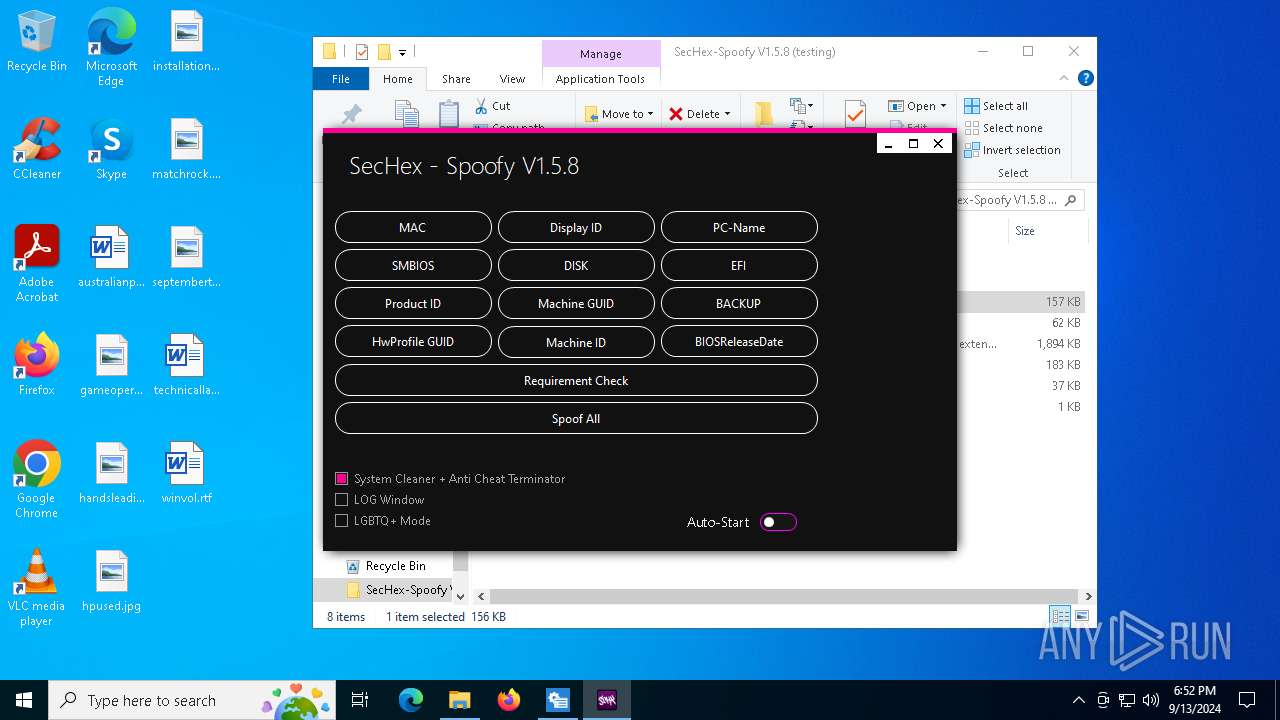
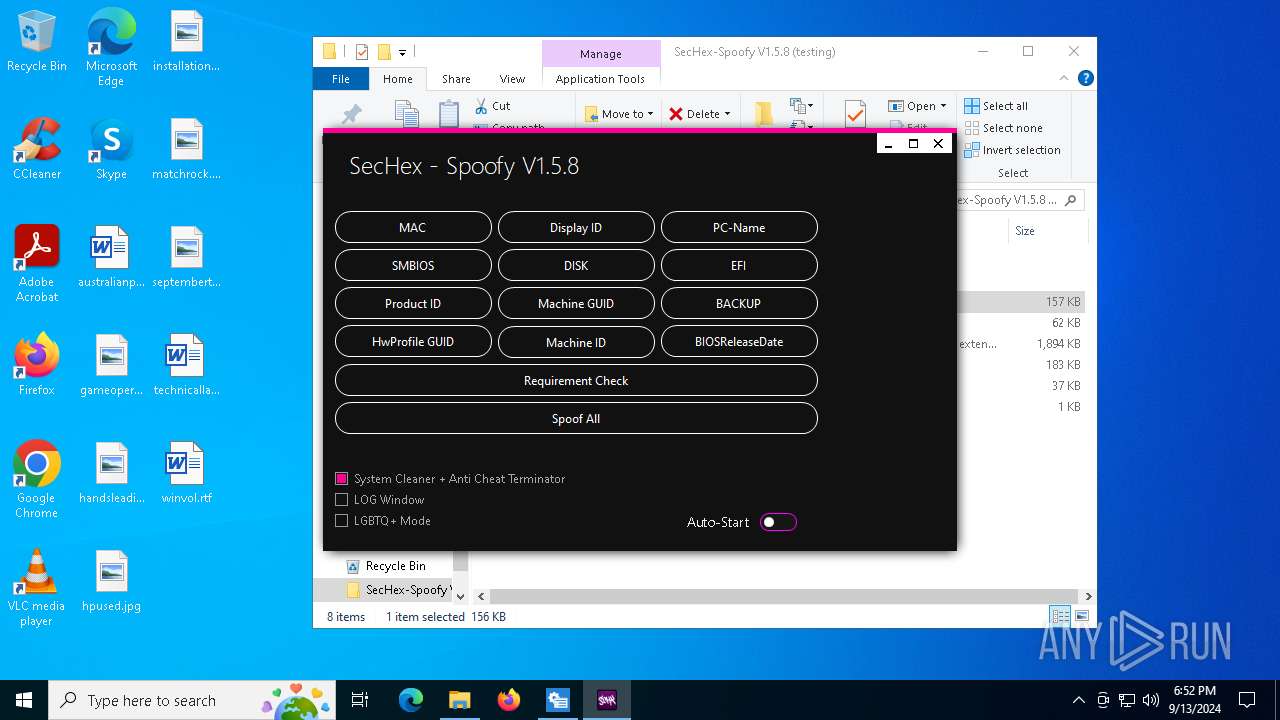
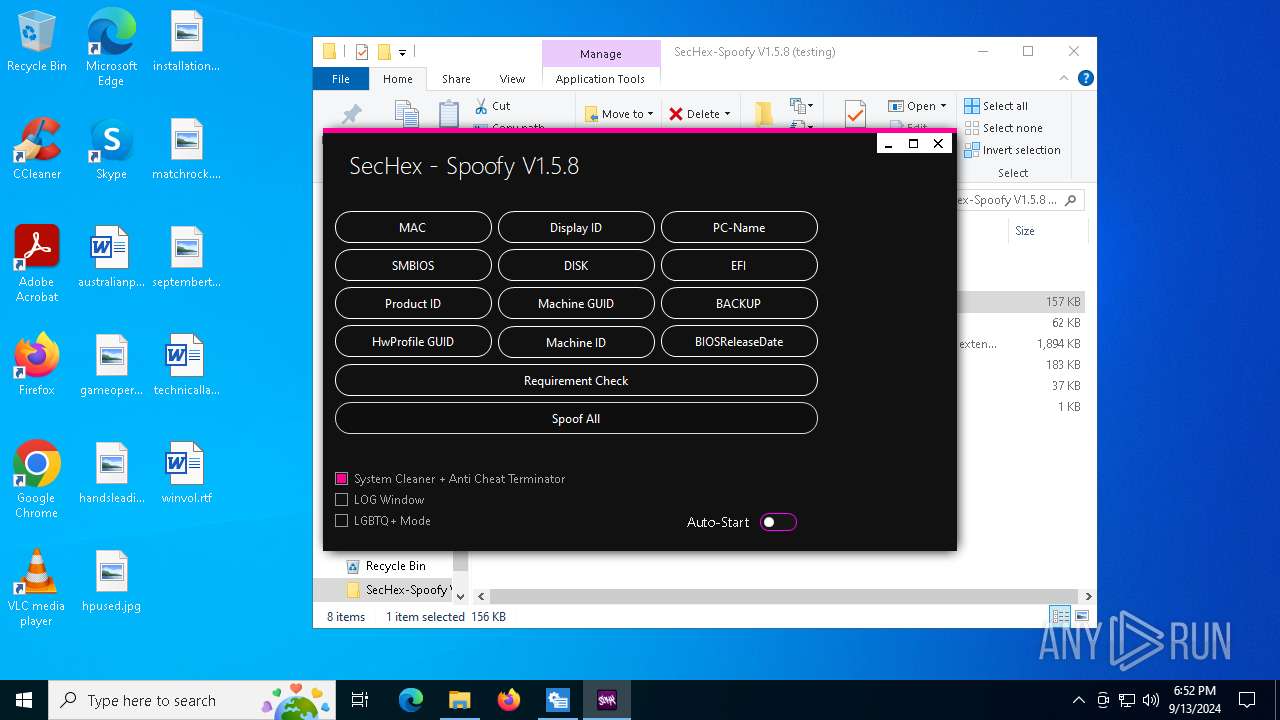
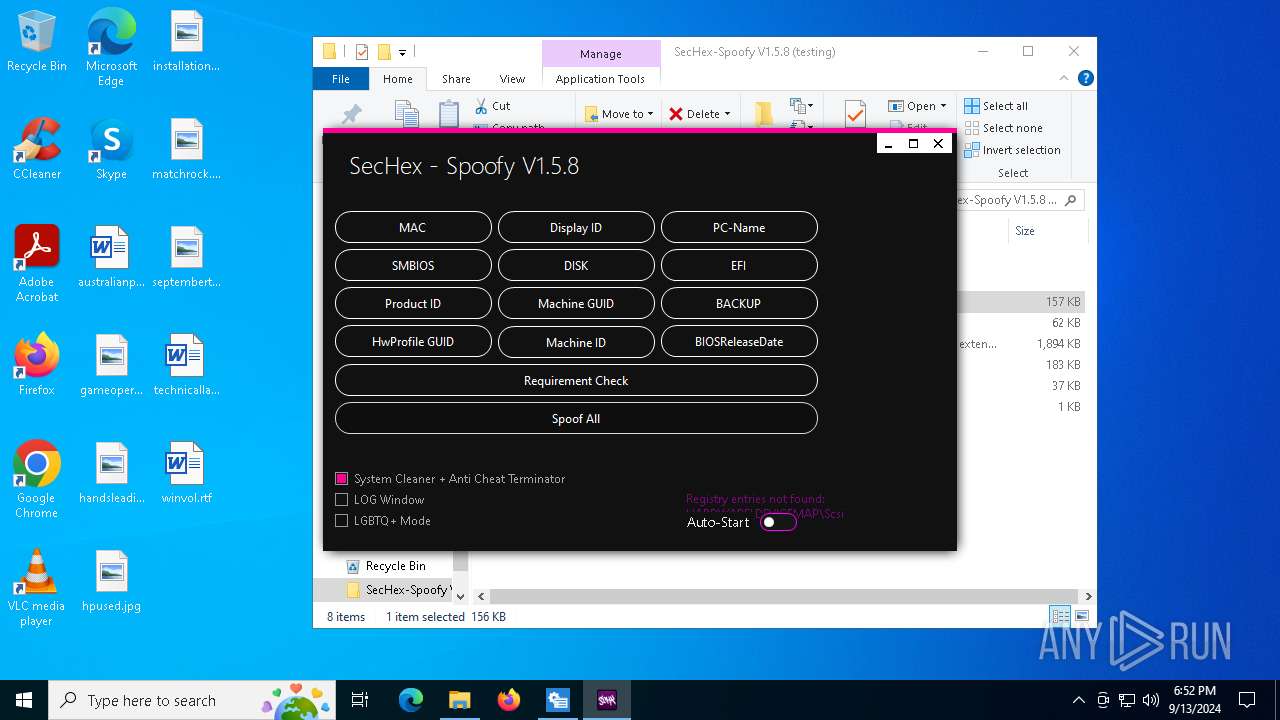
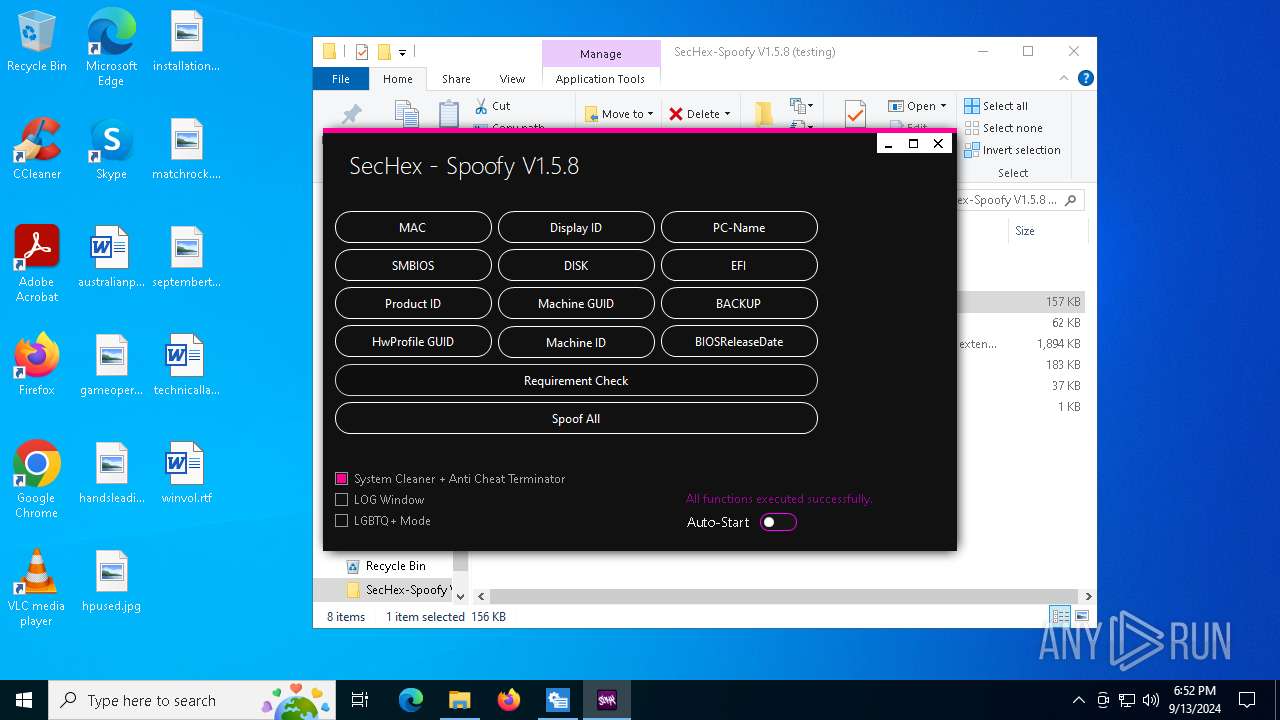
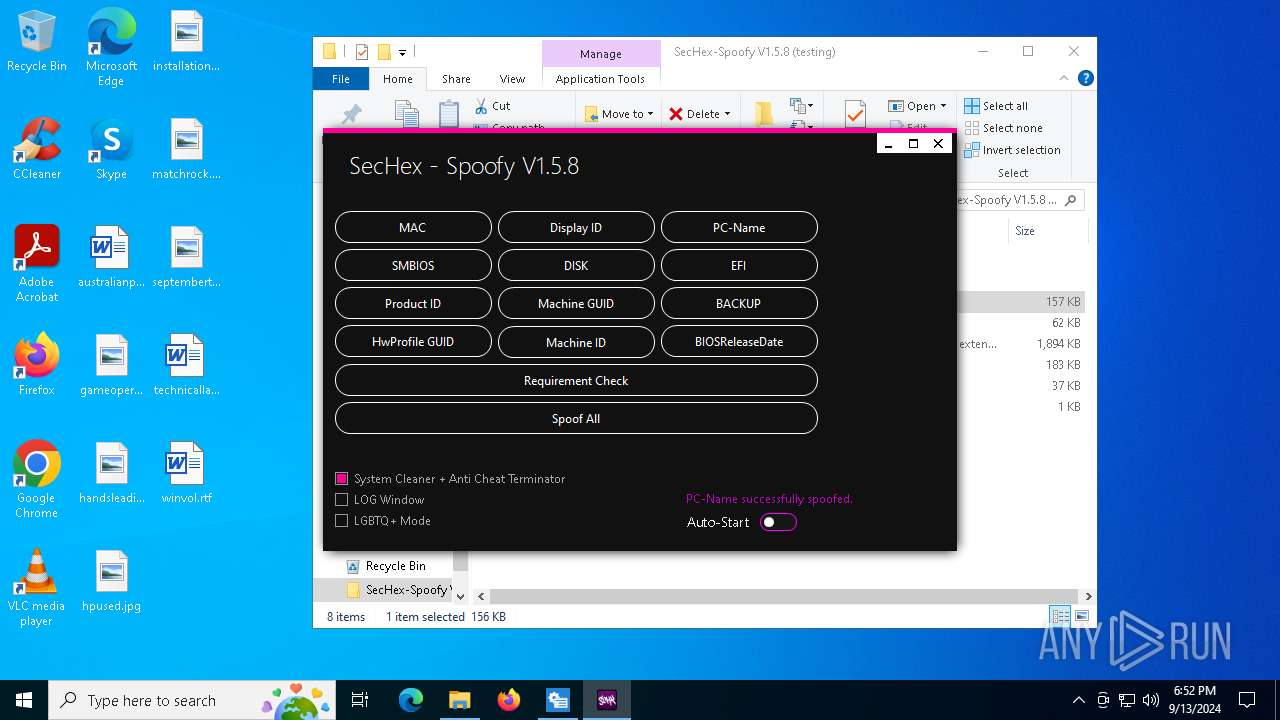
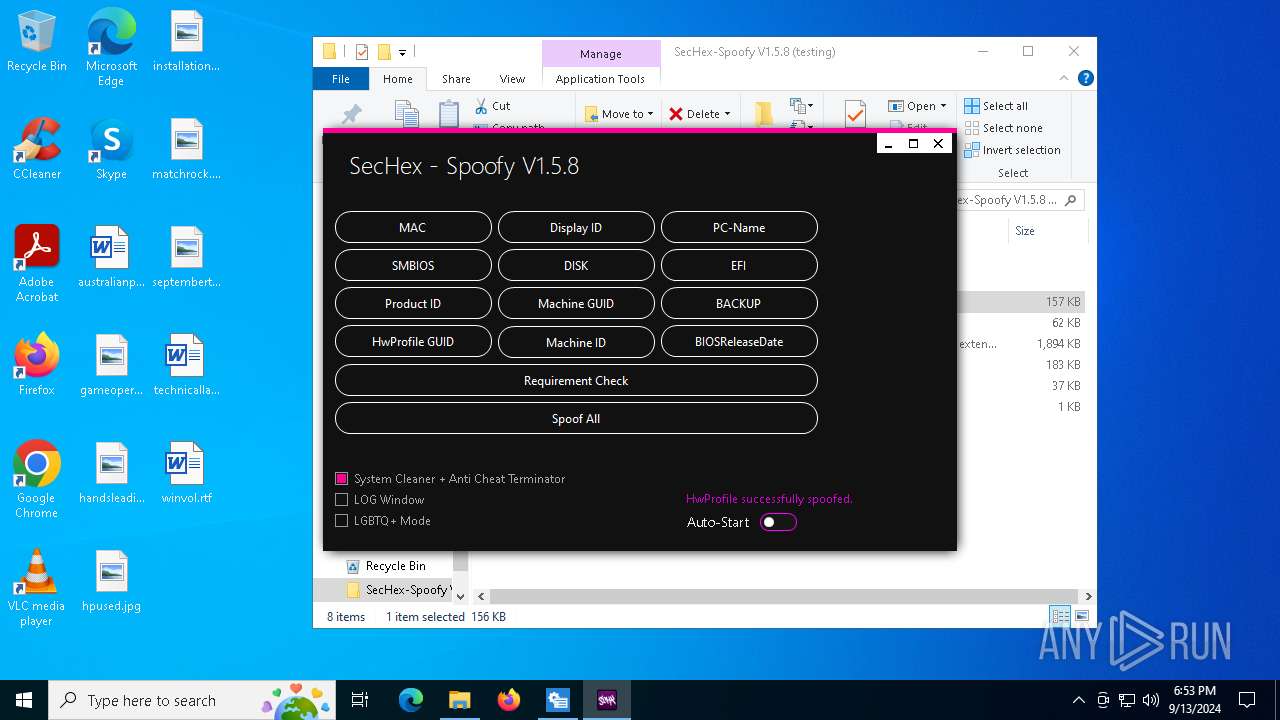
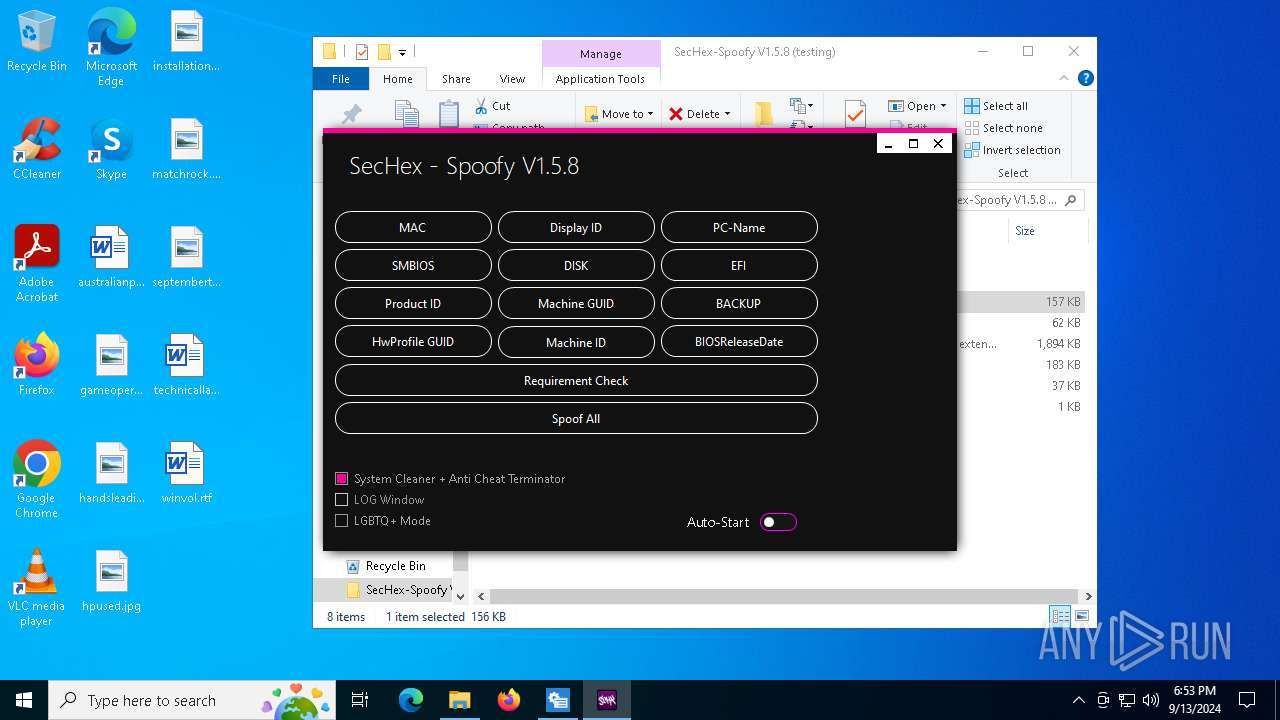
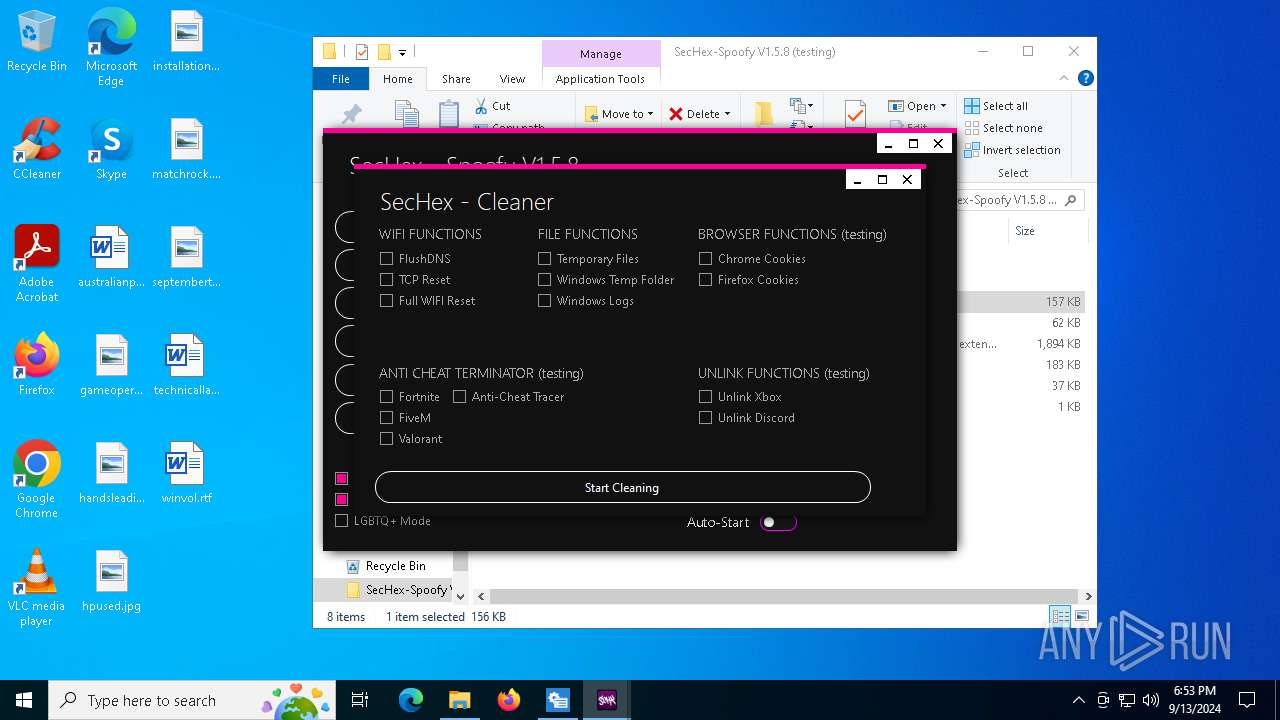
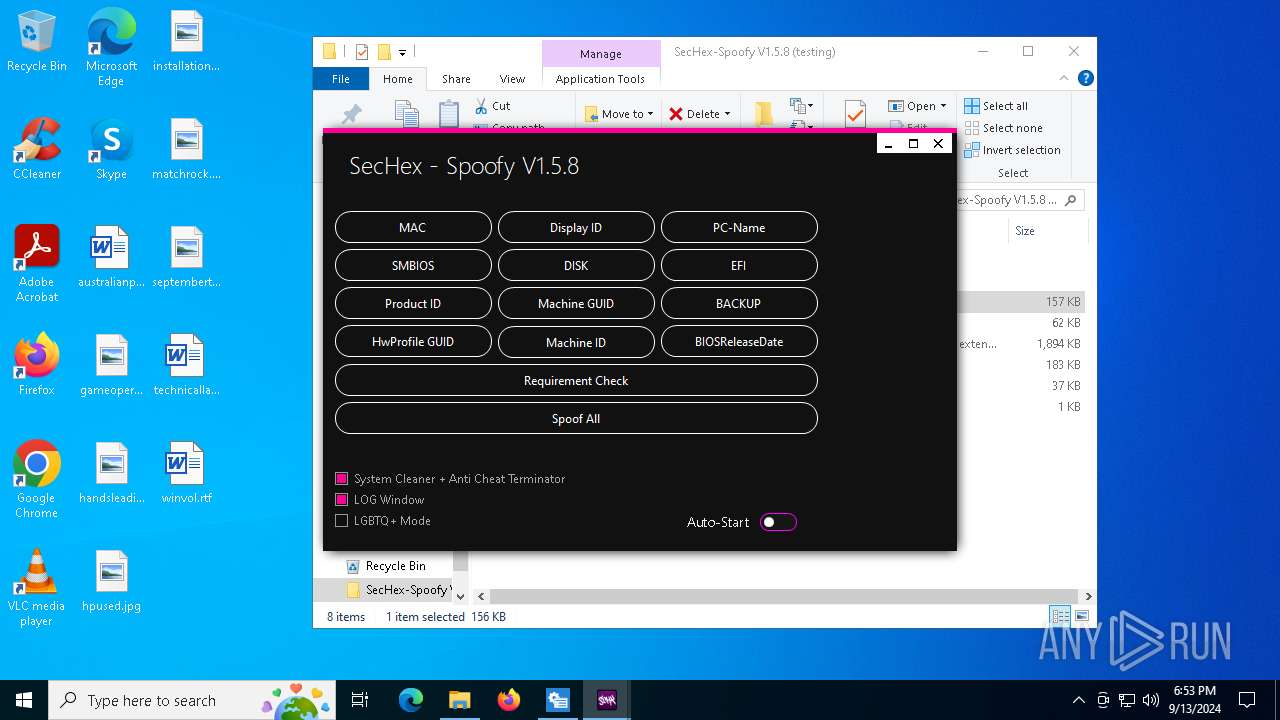
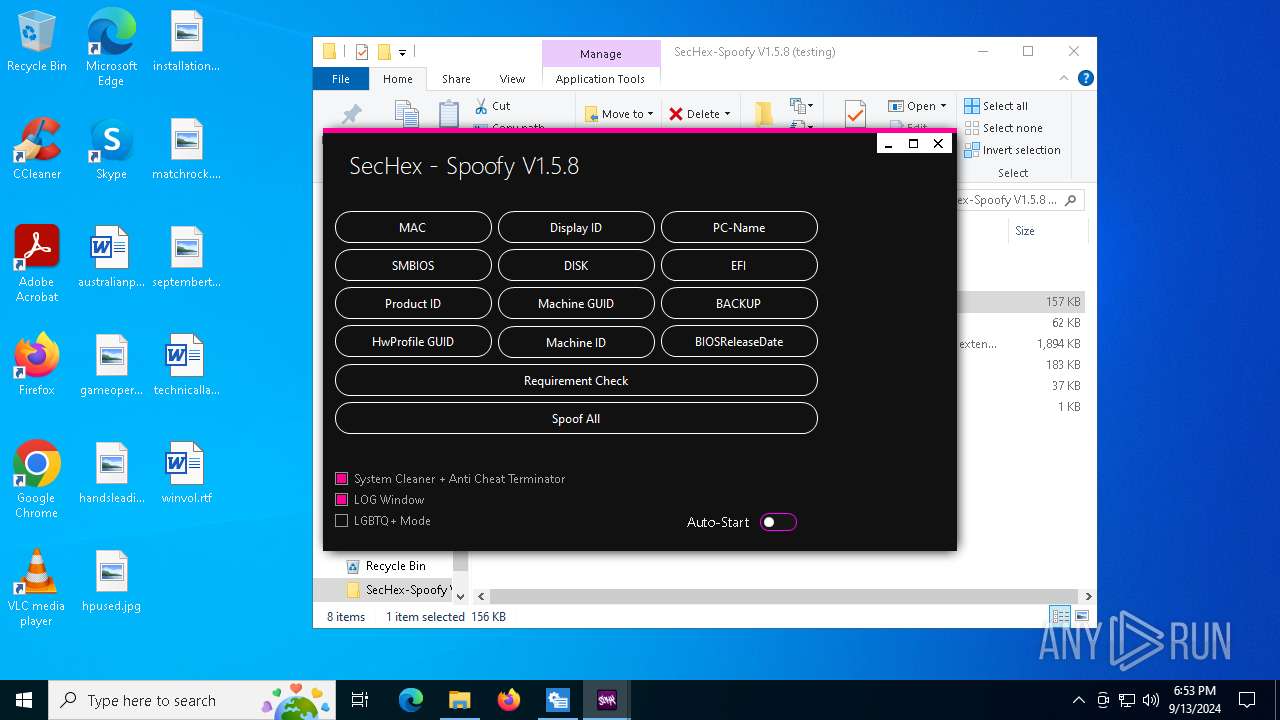
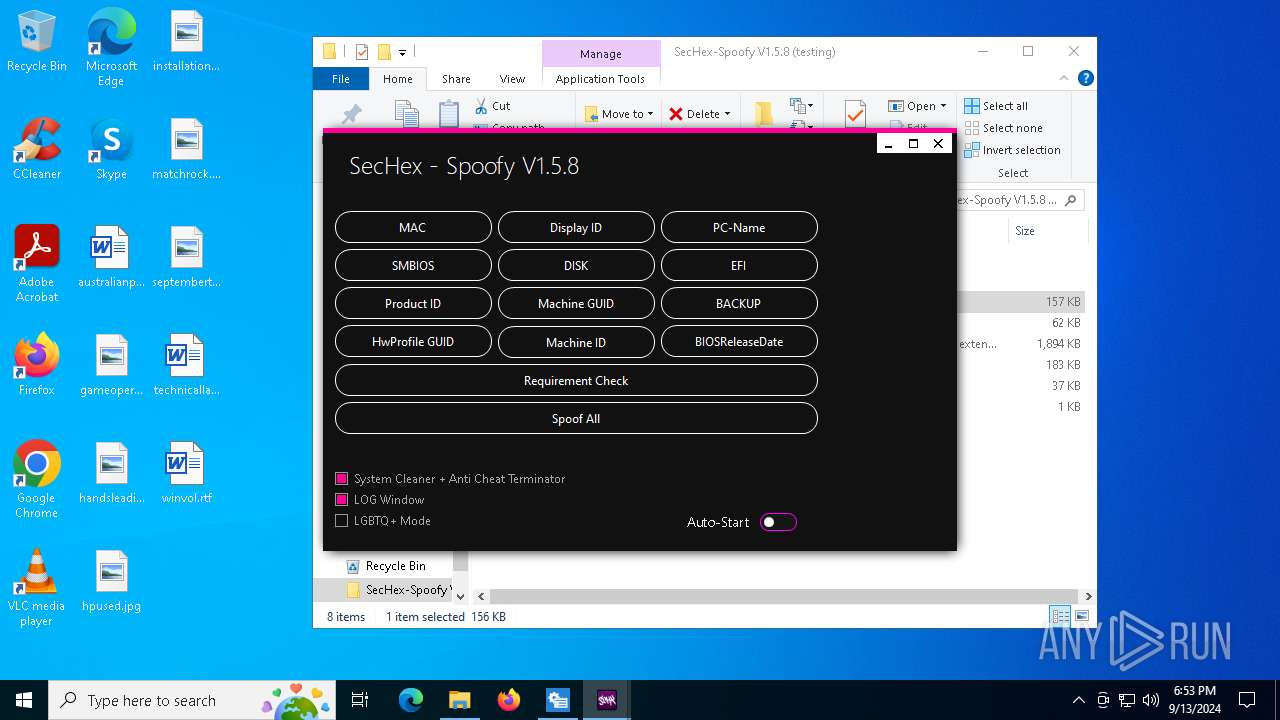
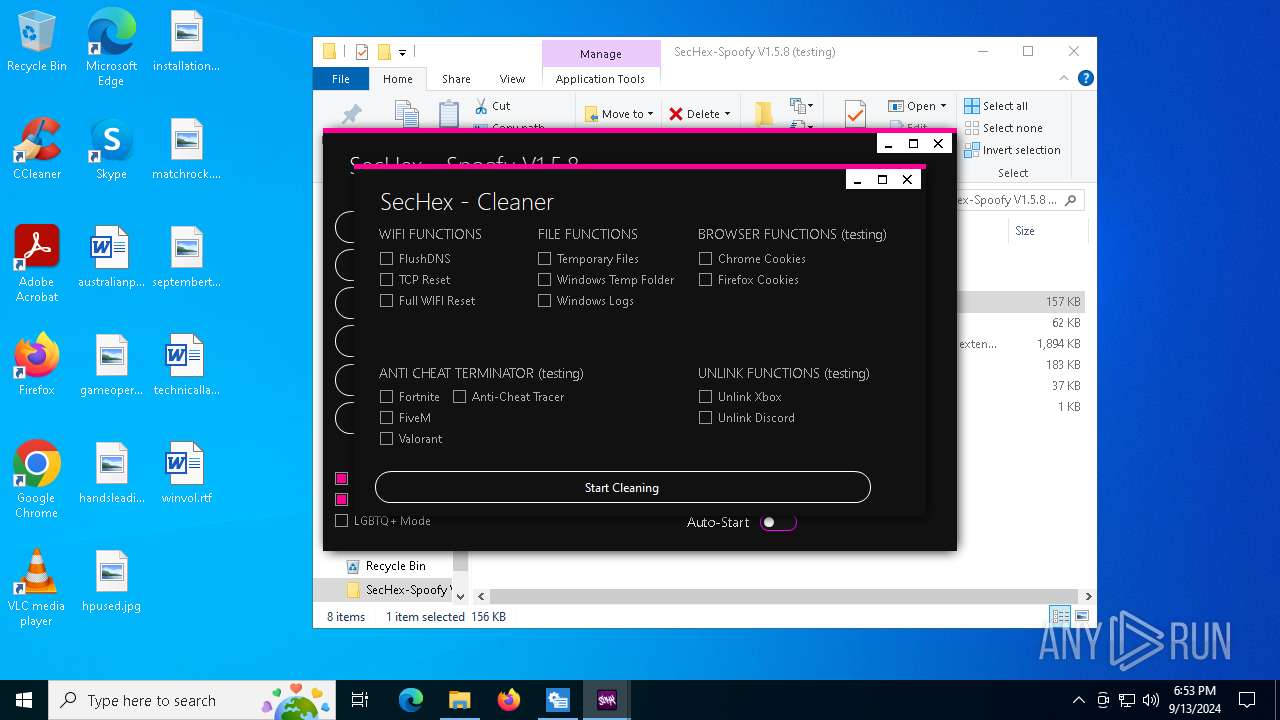
| File name: | SecHex-Spoofy V1.5.8 (testing).zip |
| Full analysis: | https://app.any.run/tasks/c31938f1-ac3e-4105-89ab-66915ff0aecc |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 18:49:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 03FDA68C9939BA123C32CB6A131B7775 |
| SHA1: | 10DD5168E9D8B458BF24CFC0ACBF20232C7BAB36 |
| SHA256: | EB7B4B35DC3CD49EB7DA39F066EC44ADDF499E5F396F1041B70473533B794A8F |
| SSDEEP: | 98304:Bjwy2pSfYBYDYfi6/TgHaaUuEThUuKKCkOQuXnMJSQDhx2q8Hd7g4nQHqzafzlxY:Kfx0T |
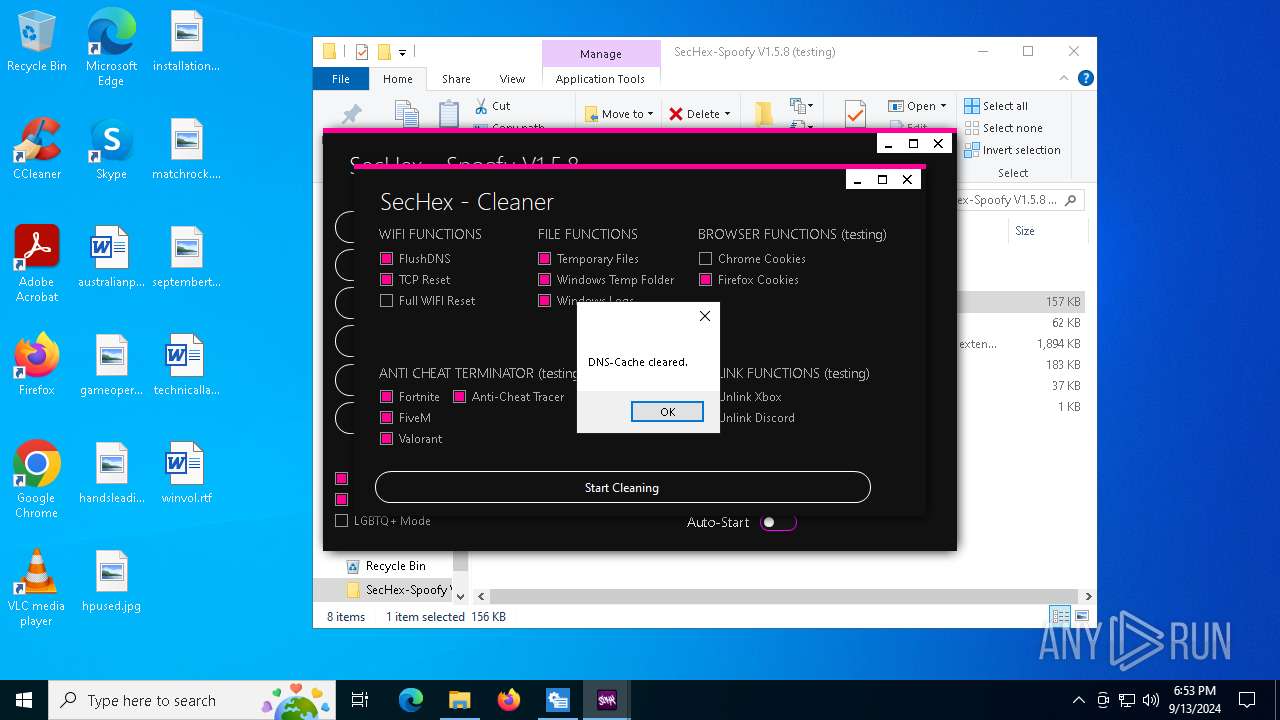
MALICIOUS
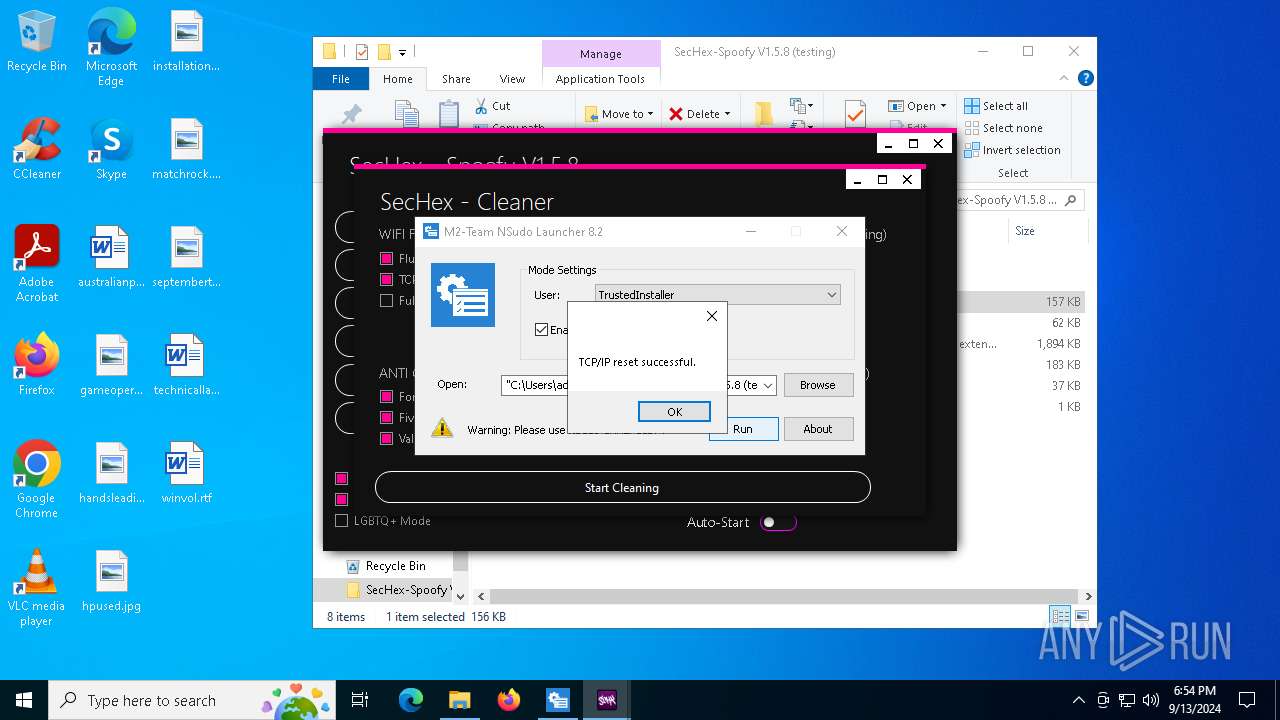
Changes the autorun value in the registry
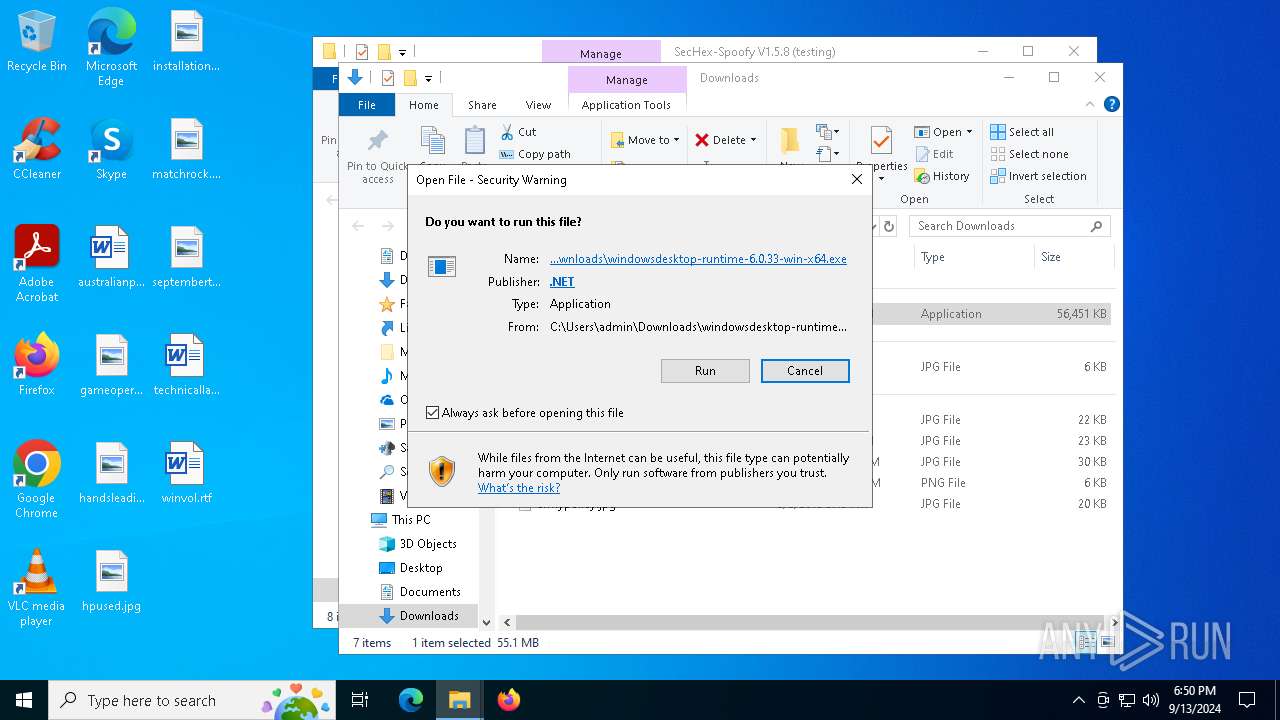
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
Changes powershell execution policy (Bypass)
- SecHex-GUI.exe (PID: 7656)
Bypass execution policy to execute commands
- powershell.exe (PID: 5372)
SUSPICIOUS
Reads security settings of Internet Explorer
- SecHex-GUI.exe (PID: 7132)
- ShellExperienceHost.exe (PID: 7640)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- NSudoLG.exe (PID: 7552)
- SecHex-GUI.exe (PID: 7656)
Executable content was dropped or overwritten
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6316)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
Searches for installed software
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
Starts itself from another location
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
Creates a software uninstall entry
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
Checks Windows Trust Settings
- msiexec.exe (PID: 5548)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5548)
The process creates files with name similar to system file names
- msiexec.exe (PID: 5548)
Creates file in the systems drive root
- explorer.exe (PID: 4552)
Starts CMD.EXE for commands execution
- NSudoLG.exe (PID: 7552)
Starts POWERSHELL.EXE for commands execution
- SecHex-GUI.exe (PID: 7656)
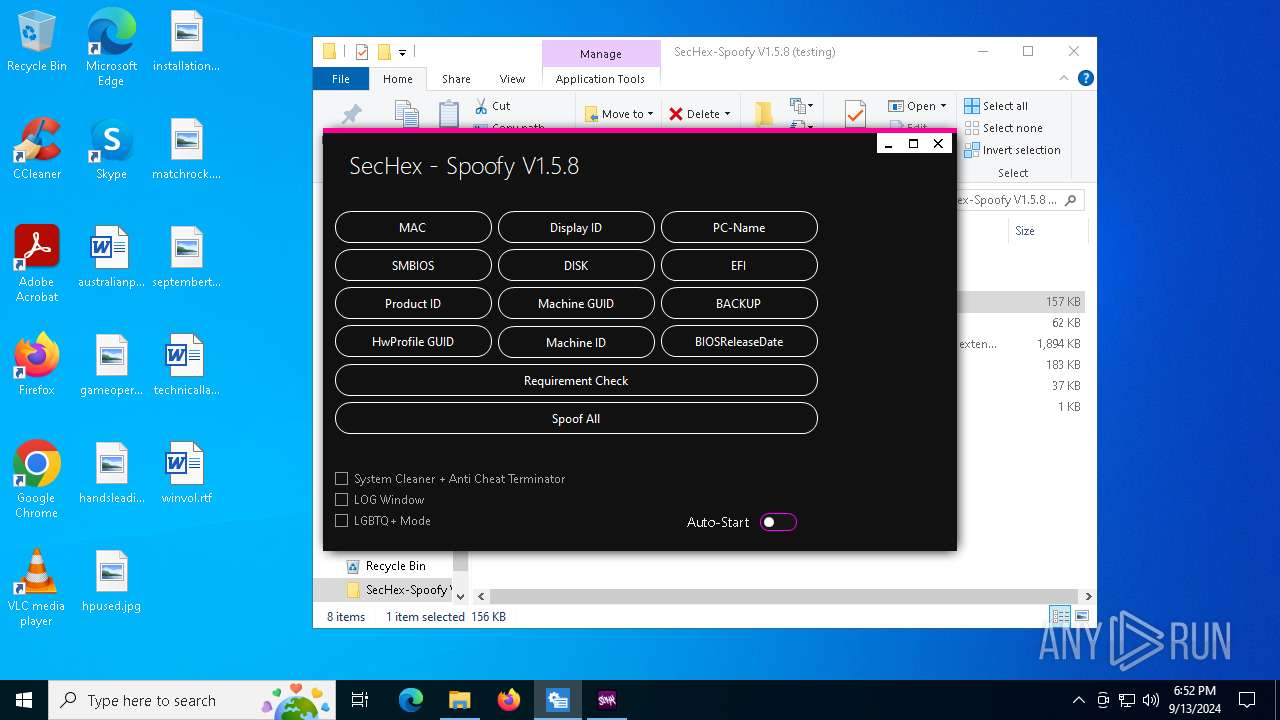
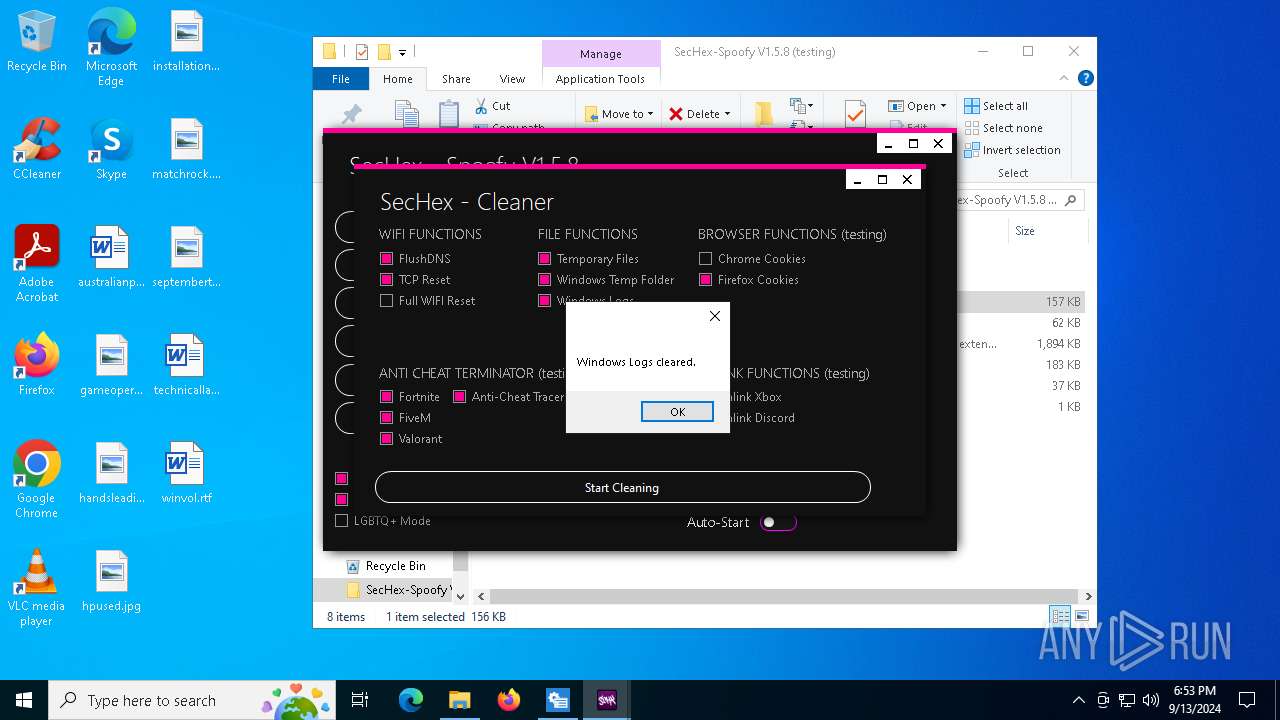
There is functionality for taking screenshot (YARA)
- SecHex-GUI.exe (PID: 7656)
Reads the date of Windows installation
- SecHex-GUI.exe (PID: 7656)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 5760)
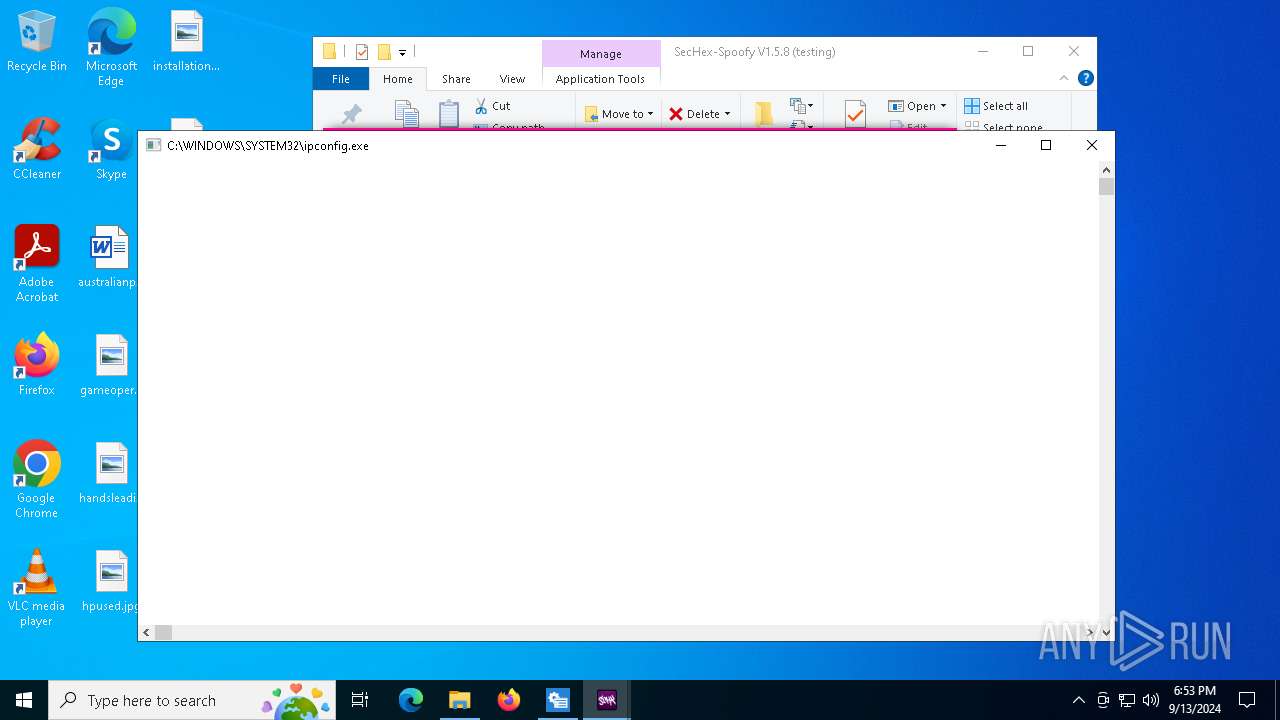
Process uses powershell cmdlet to discover network configuration
- SecHex-GUI.exe (PID: 7656)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 5760)
The process bypasses the loading of PowerShell profile settings
- SecHex-GUI.exe (PID: 7656)
Process uses IPCONFIG to clear DNS cache
- SecHex-GUI.exe (PID: 7656)
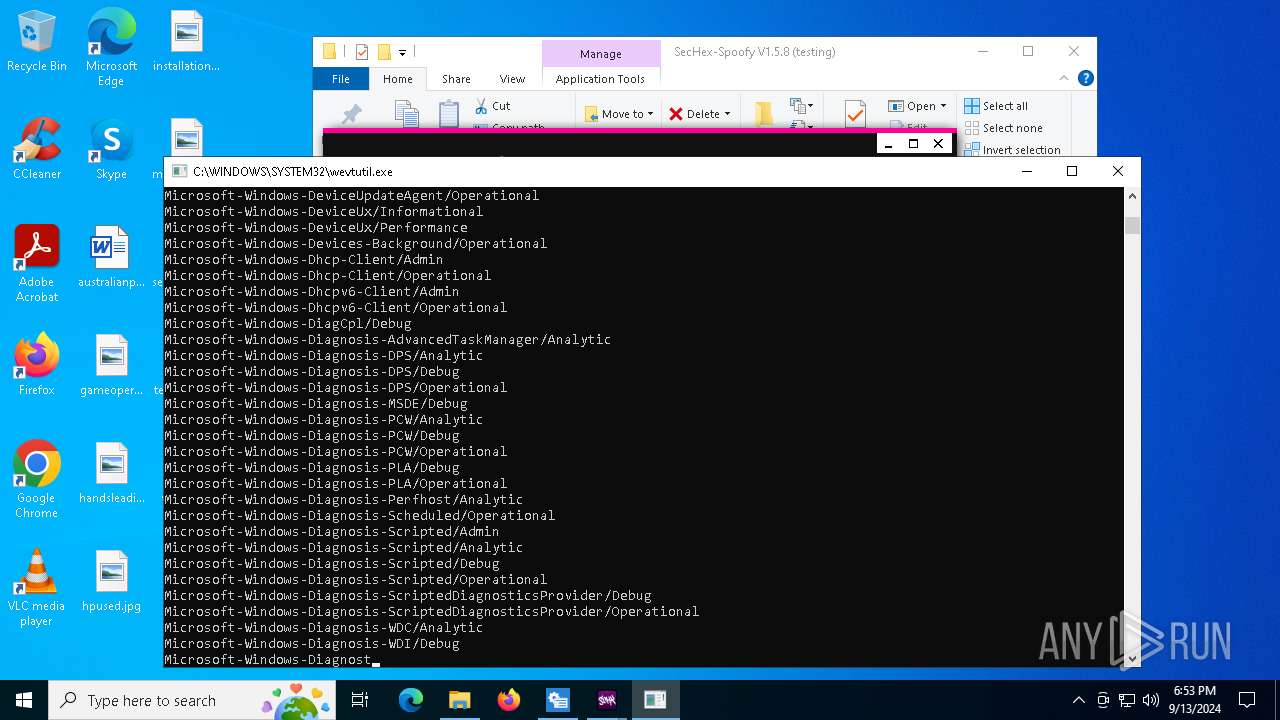
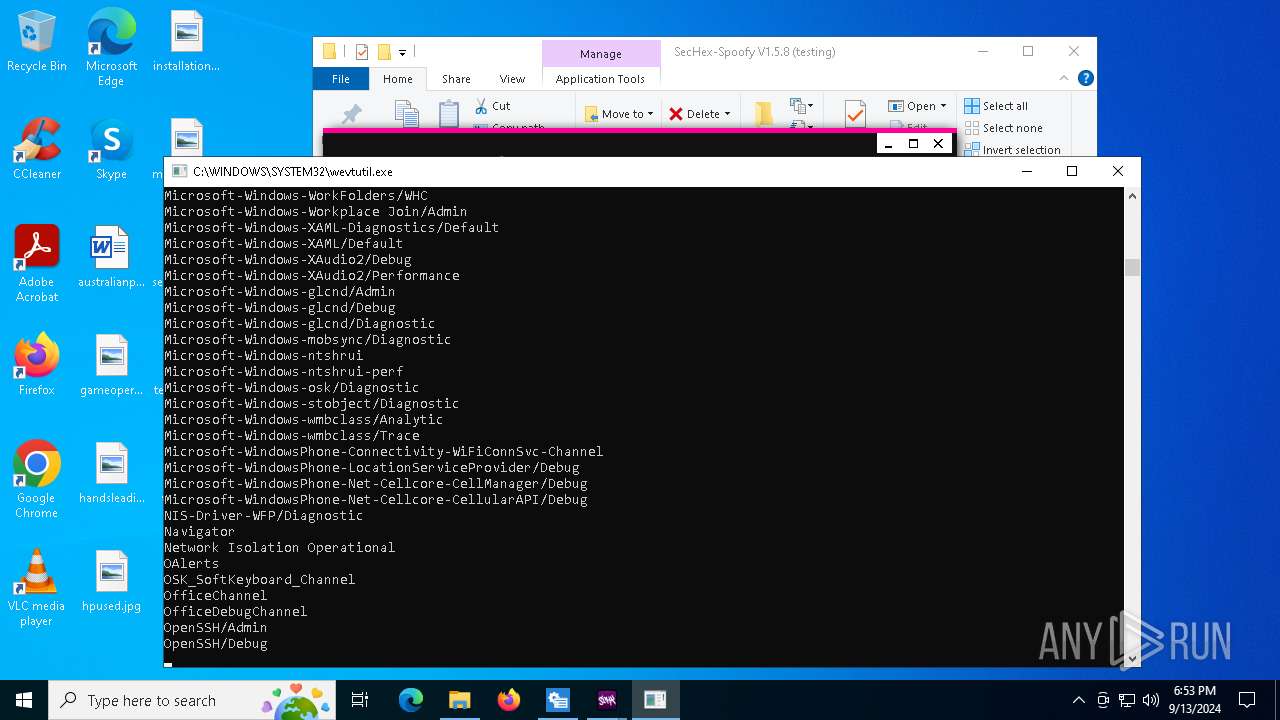
Uses WEVTUTIL.EXE to get a list of log names
- SecHex-GUI.exe (PID: 7656)
Suspicious use of NETSH.EXE
- SecHex-GUI.exe (PID: 7656)
Modifies existing scheduled task
- schtasks.exe (PID: 7032)
- schtasks.exe (PID: 5096)
Starts SC.EXE for service management
- SecHex-GUI.exe (PID: 7656)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
The process uses the downloaded file
- explorer.exe (PID: 4552)
- WinRAR.exe (PID: 7164)
- msedge.exe (PID: 7544)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- SecHex-GUI.exe (PID: 7656)
- powershell.exe (PID: 5760)
- powershell.exe (PID: 5372)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7164)
- msedge.exe (PID: 6920)
- msiexec.exe (PID: 5548)
- msedge.exe (PID: 7264)
Manual execution by a user
- SecHex-GUI.exe (PID: 7132)
- SecHex-GUI.exe (PID: 7028)
- msedge.exe (PID: 6920)
Sends debugging messages
- SecHex-GUI.exe (PID: 7132)
- ShellExperienceHost.exe (PID: 7640)
- SecHex-GUI.exe (PID: 7656)
Application launched itself
- msedge.exe (PID: 2028)
- msedge.exe (PID: 6920)
- msedge.exe (PID: 7720)
Checks supported languages
- identity_helper.exe (PID: 7304)
- identity_helper.exe (PID: 7232)
- SecHex-GUI.exe (PID: 7132)
- ShellExperienceHost.exe (PID: 7640)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6316)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
- msiexec.exe (PID: 5692)
- msiexec.exe (PID: 5548)
- msiexec.exe (PID: 5184)
- msiexec.exe (PID: 5464)
- msiexec.exe (PID: 5136)
- NSudoLG.exe (PID: 7552)
- SecHex-GUI.exe (PID: 7656)
Reads Environment values
- identity_helper.exe (PID: 7304)
- identity_helper.exe (PID: 7232)
Reads the computer name
- SecHex-GUI.exe (PID: 7132)
- identity_helper.exe (PID: 7304)
- identity_helper.exe (PID: 7232)
- ShellExperienceHost.exe (PID: 7640)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
- msiexec.exe (PID: 5548)
- msiexec.exe (PID: 5692)
- msiexec.exe (PID: 5184)
- msiexec.exe (PID: 5464)
- msiexec.exe (PID: 5136)
- NSudoLG.exe (PID: 7552)
- SecHex-GUI.exe (PID: 7656)
Reads the software policy settings
- explorer.exe (PID: 4552)
- msiexec.exe (PID: 5548)
- slui.exe (PID: 8076)
- slui.exe (PID: 7496)
Checks proxy server information
- explorer.exe (PID: 4552)
- slui.exe (PID: 7496)
Create files in a temporary directory
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6316)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
Creates files or folders in the user directory
- explorer.exe (PID: 4552)
Process checks computer location settings
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6128)
- SecHex-GUI.exe (PID: 7656)
Creates files in the program directory
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
- SecHex-GUI.exe (PID: 7656)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5548)
- windowsdesktop-runtime-6.0.33-win-x64.exe (PID: 6332)
- SecHex-GUI.exe (PID: 7656)
Creates a software uninstall entry
- msiexec.exe (PID: 5548)
Reads Windows Product ID
- SecHex-GUI.exe (PID: 7656)
Disables trace logs
- netsh.exe (PID: 6424)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5760)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:13 13:20:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SecHex-Spoofy V1.5.8 (testing)/ |
Total processes
273
Monitored processes
129
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x314,0x318,0x31c,0x30c,0x308,0x7fffd32c5fd8,0x7fffd32c5fe4,0x7fffd32c5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 320 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5468 --field-trial-handle=2488,i,17636197737091817987,13646250574282416891,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 320 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4180 --field-trial-handle=2372,i,7041296713676010224,8219347963635843941,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
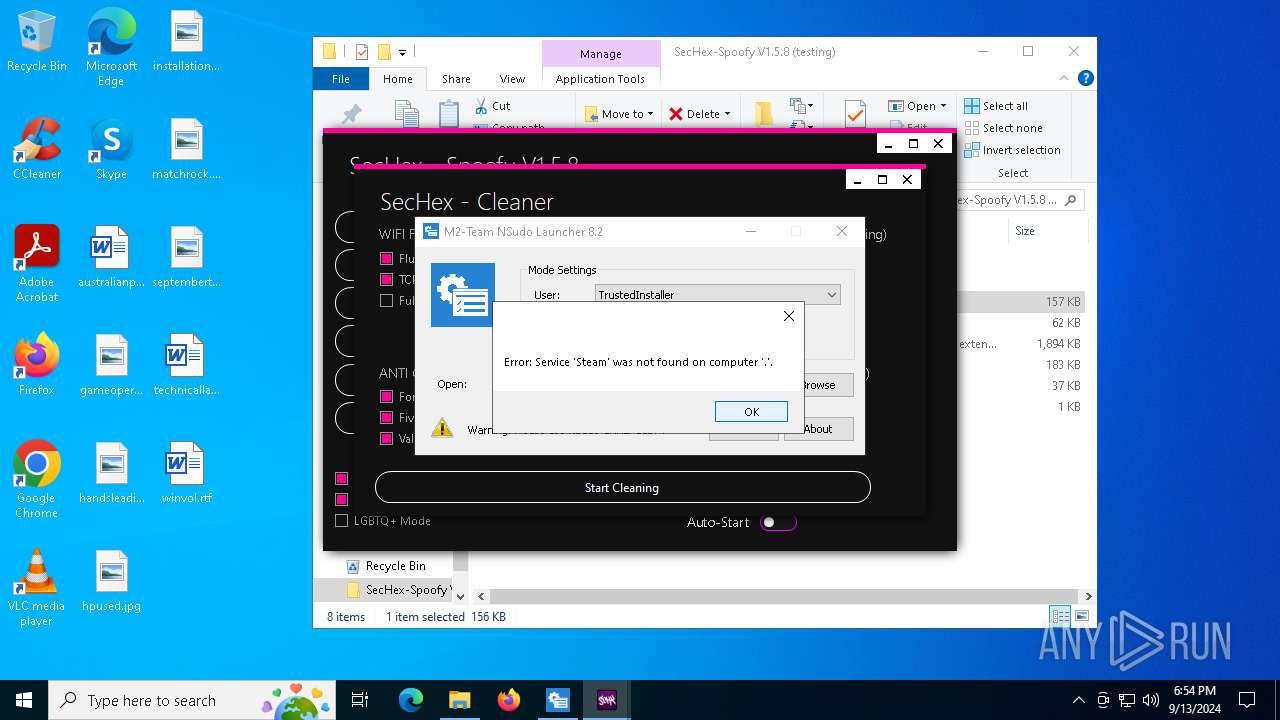
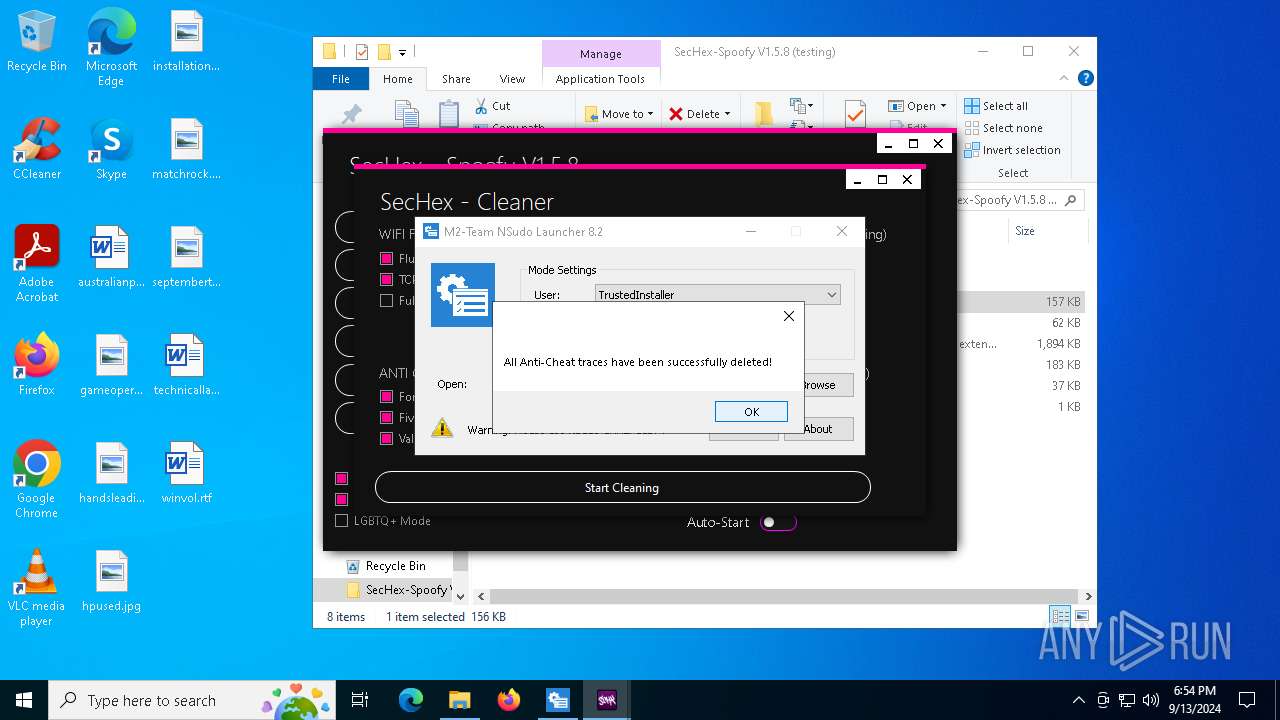
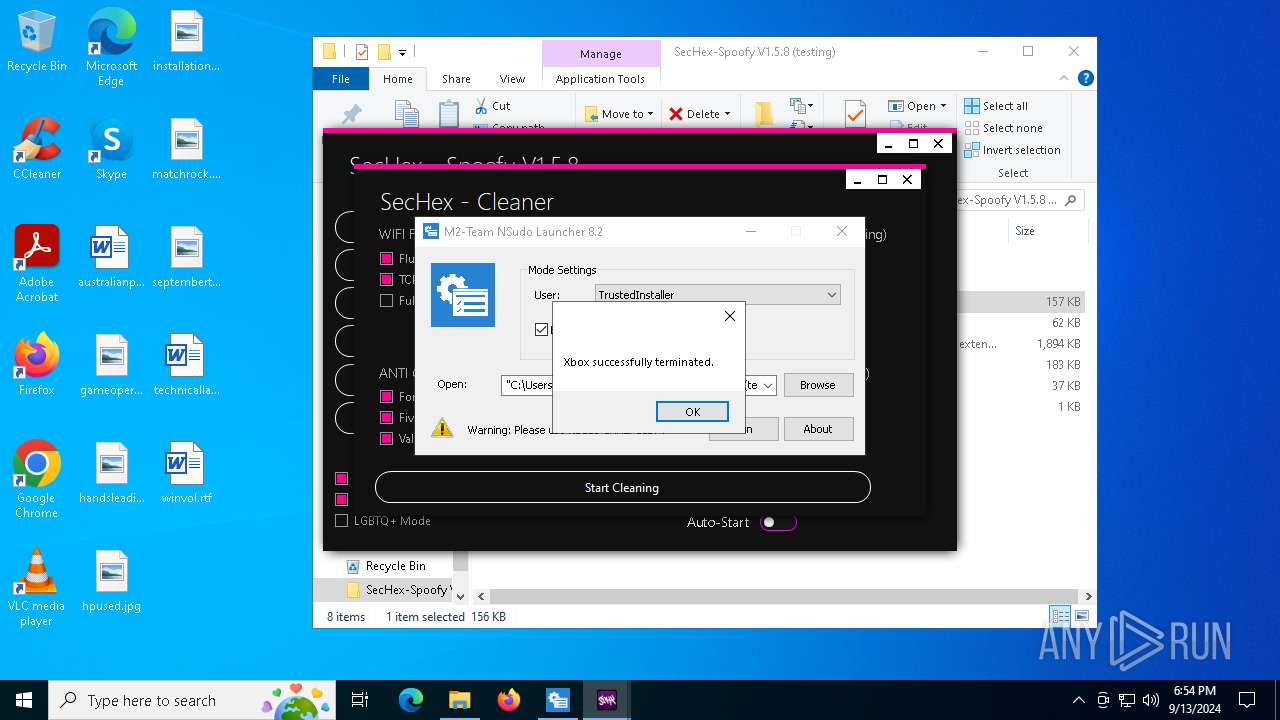
| 448 | "sc" stop XboxGipSvc | C:\Windows\System32\sc.exe | — | SecHex-GUI.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
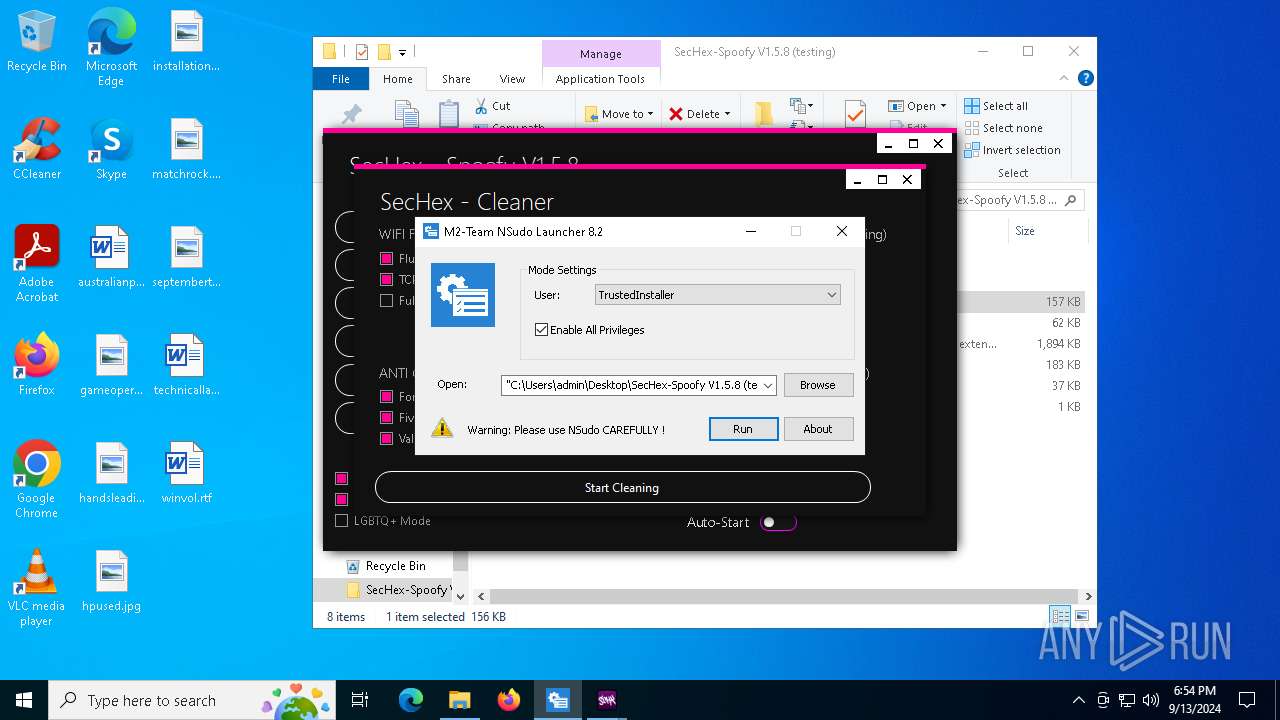
| 964 | "C:\Users\admin\Desktop\SecHex-Spoofy V1.5.8 (testing)\NSudoLG.exe" | C:\Users\admin\Desktop\SecHex-Spoofy V1.5.8 (testing)\NSudoLG.exe | — | explorer.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: MEDIUM Description: NSudo Launcher Exit code: 3221226540 Version: 8.2.0.0 Modules
| |||||||||||||||
| 1084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5296 --field-trial-handle=2372,i,7041296713676010224,8219347963635843941,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3852 --field-trial-handle=2488,i,17636197737091817987,13646250574282416891,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5704 --field-trial-handle=2488,i,17636197737091817987,13646250574282416891,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1496 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5332 --field-trial-handle=2488,i,17636197737091817987,13646250574282416891,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
60 133
Read events
58 740
Write events
1 310
Delete events
83
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000A02EE |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SecHex-Spoofy V1.5.8 (testing).zip | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010012000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000018000000000000006100750073007400720061006C00690061006E0070006C0065006100730065002E007200740066003E002000200000001500000000000000670061006D0065006F007000650072006100740069006E0067002E0070006E0067003E002000200000001400000000000000680061006E00640073006C0065006100640069006E0067002E006A00700067003E002000200000000E000000000000006800700075007300650064002E006A00700067003E00200020000000160000000000000069006E007300740061006C006C006100740069006F006E0066006C002E0070006E0067003E0020002000000011000000000000006D00610074006300680072006F0063006B002E006A00700067003E002000200000001400000000000000730065007000740065006D00620065007200740077006F002E0070006E0067003E00200020000000160000000000000074006500630068006E006900630061006C006C0061007200670065002E007200740066003E002000200000000E00000000000000770069006E0076006F006C002E007200740066003E0020002000000022000000000000005300650063004800650078002D00530070006F006F00660079002000560031002E0035002E00380020002800740065007300740069006E00670029003E005C0020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001200000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000005041000040401100 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 3E89E46600000000 | |||
Executable files
536
Suspicious files
551
Text files
204
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\Logs\2024-09-13_13-20-49.txt | text | |
MD5:DC95E02F274EB5FD31091F78E6AF2309 | SHA256:51975B17045AF756D8A93A122B1789F6A82AD3B62A8CD1E280DAB459D0859F3B | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\runtimes\win\lib\net6.0\System.ServiceProcess.ServiceController.dll | executable | |
MD5:1C710EF8481E54352A4E1F66A8F7AD8C | SHA256:D11B97C114101961BCC7ACB0BB17E536708593C0321B6107942FBA20CB430C65 | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\Logs\2024-09-13_13-24-17.txt | text | |
MD5:ED06E3C3C87CCE1142EFB33325004CF7 | SHA256:EFEEB2451D4D97CCFD26369D7E9D938A1573BB07939246A0CFDE8D037E5CA15D | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.runtimeconfig.json | binary | |
MD5:D720176A229E9D969B40FABEB0BAF62E | SHA256:321B4E463BBACD6113AA337511BDEBF5E7356E9971744346B28424607C7B483A | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\runtimes\win\lib\netcoreapp3.0\System.Runtime.WindowsRuntime.dll | executable | |
MD5:0198A79063C865ED21C95B7400DDD9FC | SHA256:BE26699765F700A29C3928E10F6D1E02A297DFF3BA6EB7AFB6EC41003CB3D665 | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\NSudoLG.exe | executable | |
MD5:7AACFD85B8DFF0AA6867BEDE82CFD147 | SHA256:871E4F28FE39BCAD8D295AE46E148BE458778C0195ED660B7DB18EB595D00BD8 | |||
| 2028 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:04E3F29A62D8BFE314652697DE334A9C | SHA256:62F1F368DA991B1B7964570CBE0C0D6F6ADAB80A628C139B8DB54D1FB71D5A16 | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.exe | executable | |
MD5:C252A43B1D357D08308690545C617031 | SHA256:B779B45849A4AB5BD8FF296E6C95638C5BE4DA18B67F1FD195B31795BC21CDFC | |||
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7164.18316\SecHex-Spoofy V1.5.8 (testing)\Logs\2024-09-13_13-20-04.txt | text | |
MD5:A99B68AC810CBF9F09FA76BB0B1BF51A | SHA256:B899D90772824EA04A815F08189698F9AD06E33A8F9786B2B15AF10594699BC7 | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:FEB6E2712B51F2C45347BA951729A555 | SHA256:481FE96B4F84B0941A0C9FE61C5DEDEEECE53CE29076D9832A9D1EA5D7937738 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
87
DNS requests
90
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6880 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1280 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7396 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7396 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7888 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1726546771&P2=404&P3=2&P4=Gx6HwH6RHR%2bO9ZvOeRZxHOudEhuhxUAWH9CsE2DWk8ccdliakNZcaudALCOolqkSg5KzRmTjCF8TrsQd8YJYKA%3d%3d | unknown | — | — | whitelisted |
4552 | explorer.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
7888 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1726546771&P2=404&P3=2&P4=Gx6HwH6RHR%2bO9ZvOeRZxHOudEhuhxUAWH9CsE2DWk8ccdliakNZcaudALCOolqkSg5KzRmTjCF8TrsQd8YJYKA%3d%3d | unknown | — | — | whitelisted |
7888 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1726546771&P2=404&P3=2&P4=Gx6HwH6RHR%2bO9ZvOeRZxHOudEhuhxUAWH9CsE2DWk8ccdliakNZcaudALCOolqkSg5KzRmTjCF8TrsQd8YJYKA%3d%3d | unknown | — | — | whitelisted |
7888 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1726546771&P2=404&P3=2&P4=Gx6HwH6RHR%2bO9ZvOeRZxHOudEhuhxUAWH9CsE2DWk8ccdliakNZcaudALCOolqkSg5KzRmTjCF8TrsQd8YJYKA%3d%3d | unknown | — | — | whitelisted |
7888 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1726546771&P2=404&P3=2&P4=Gx6HwH6RHR%2bO9ZvOeRZxHOudEhuhxUAWH9CsE2DWk8ccdliakNZcaudALCOolqkSg5KzRmTjCF8TrsQd8YJYKA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6880 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6232 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6880 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1280 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
aka.ms |
| whitelisted |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
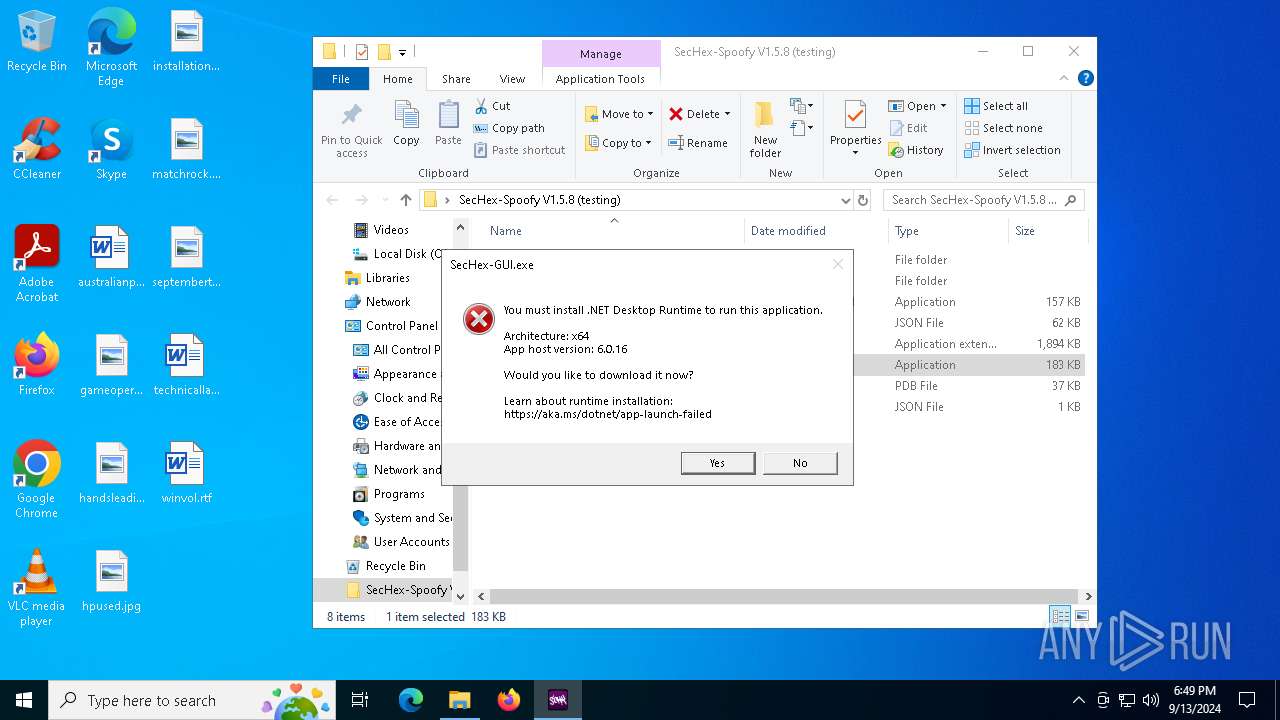
SecHex-GUI.exe | You must install .NET to run this application.
App: C:\Users\admin\Desktop\SecHex-Spoofy V1.5.8 (testing)\SecHex-GUI.exe
Architecture: x64
App host version: 6.0.16
.NET location: Not found
Learn about runtime installation:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win10-x64&apphost_version=6.0.16 |
SecHex-GUI.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 7656. Message ID: [0x2509].
|