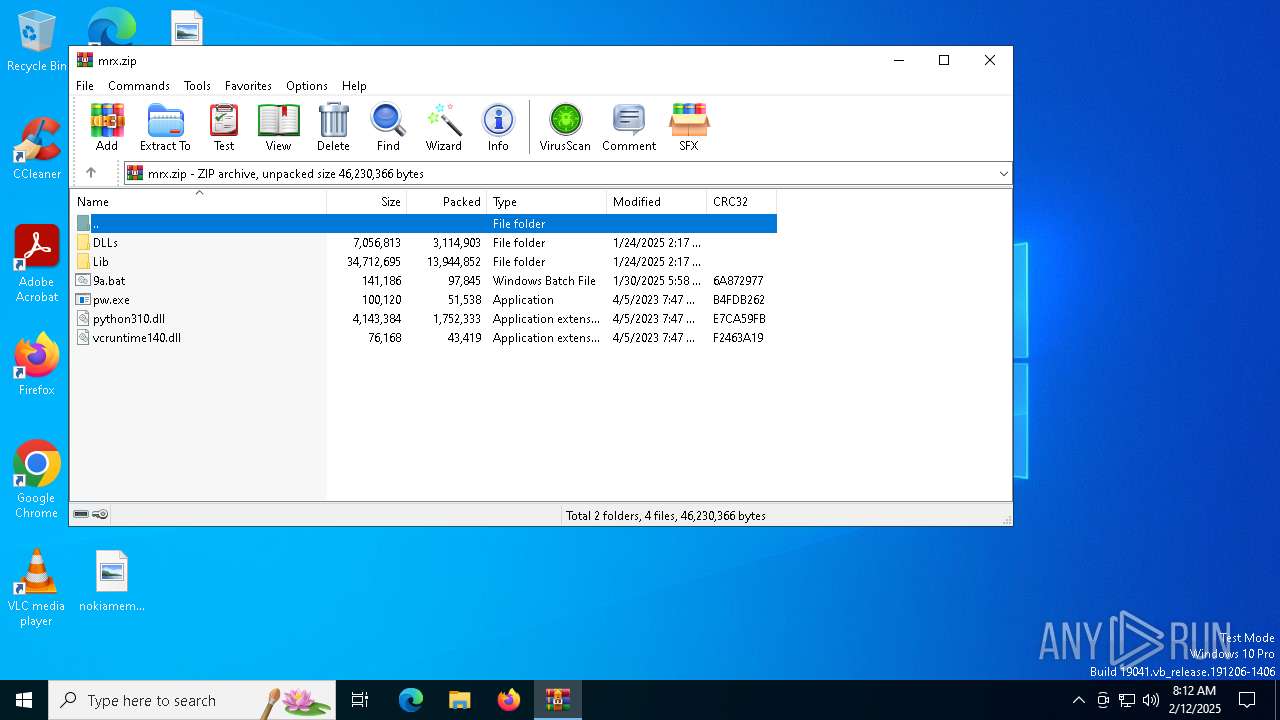
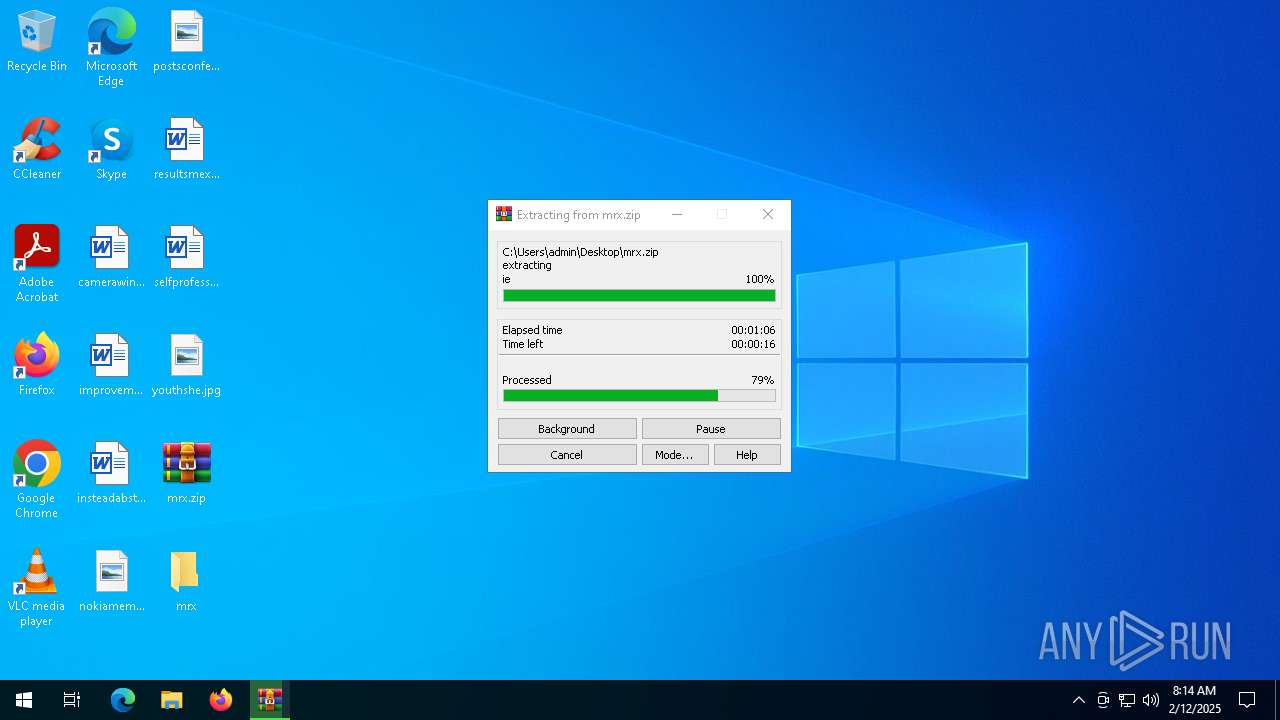
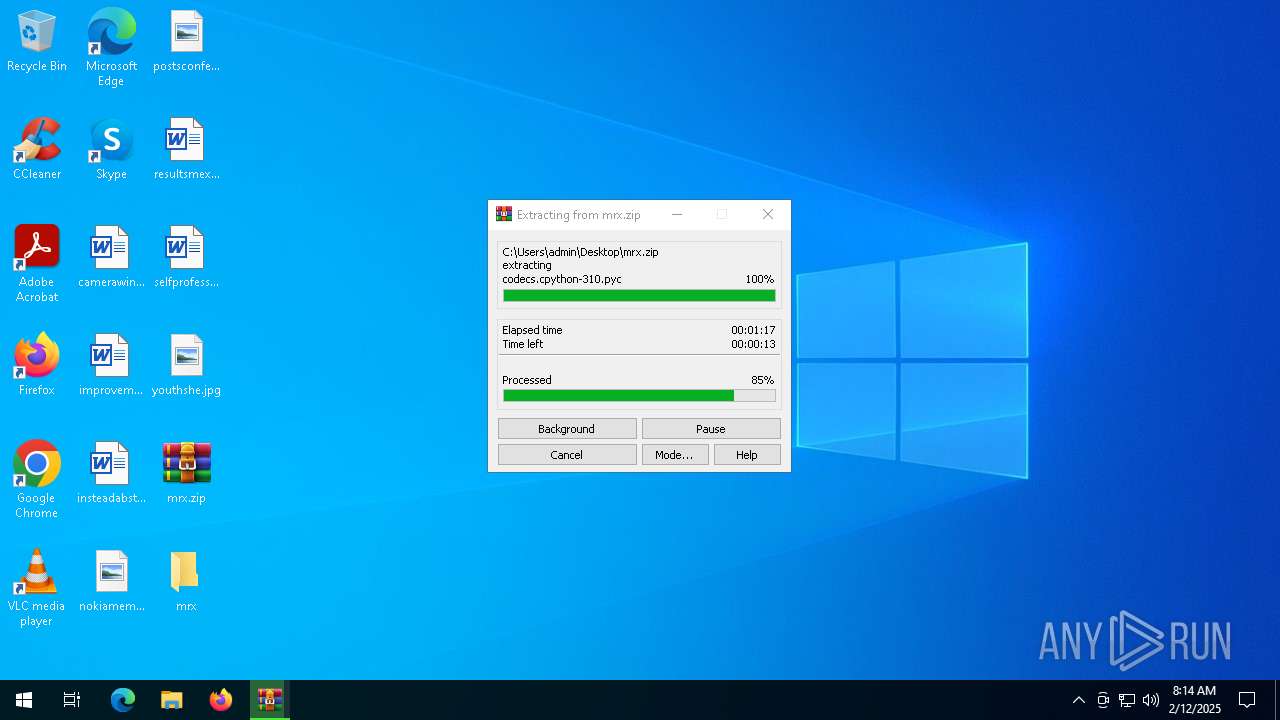
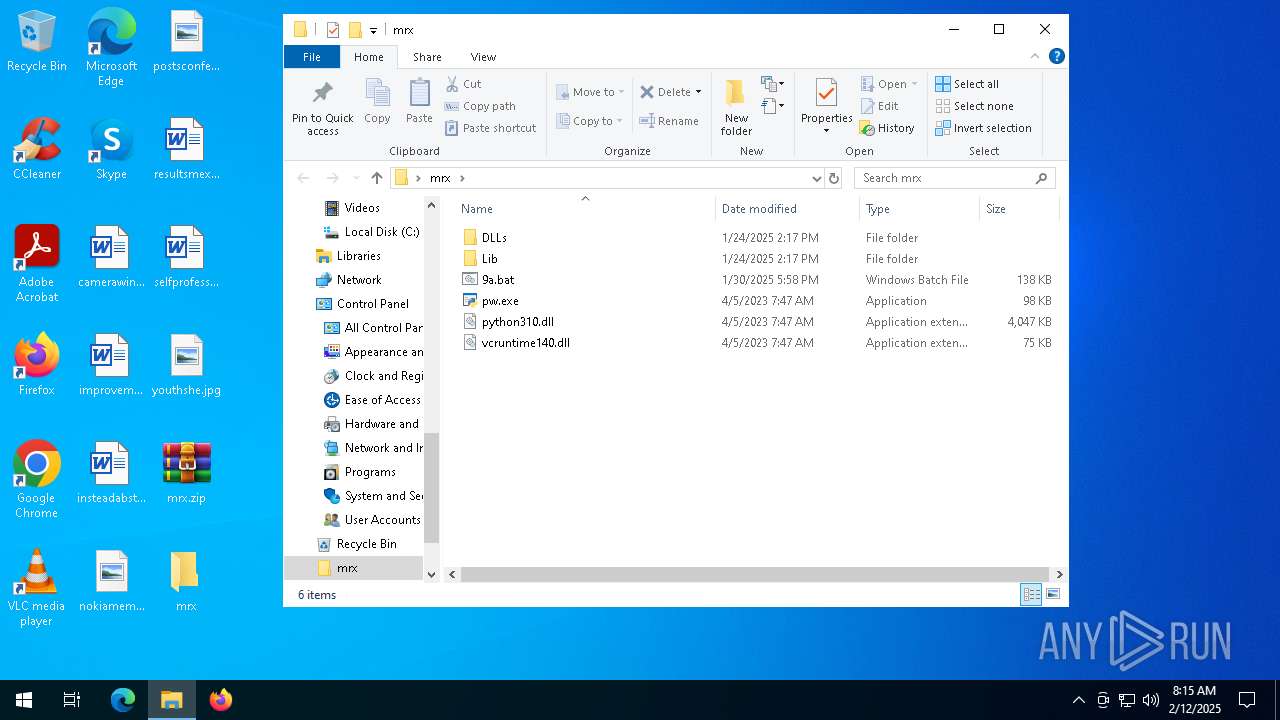
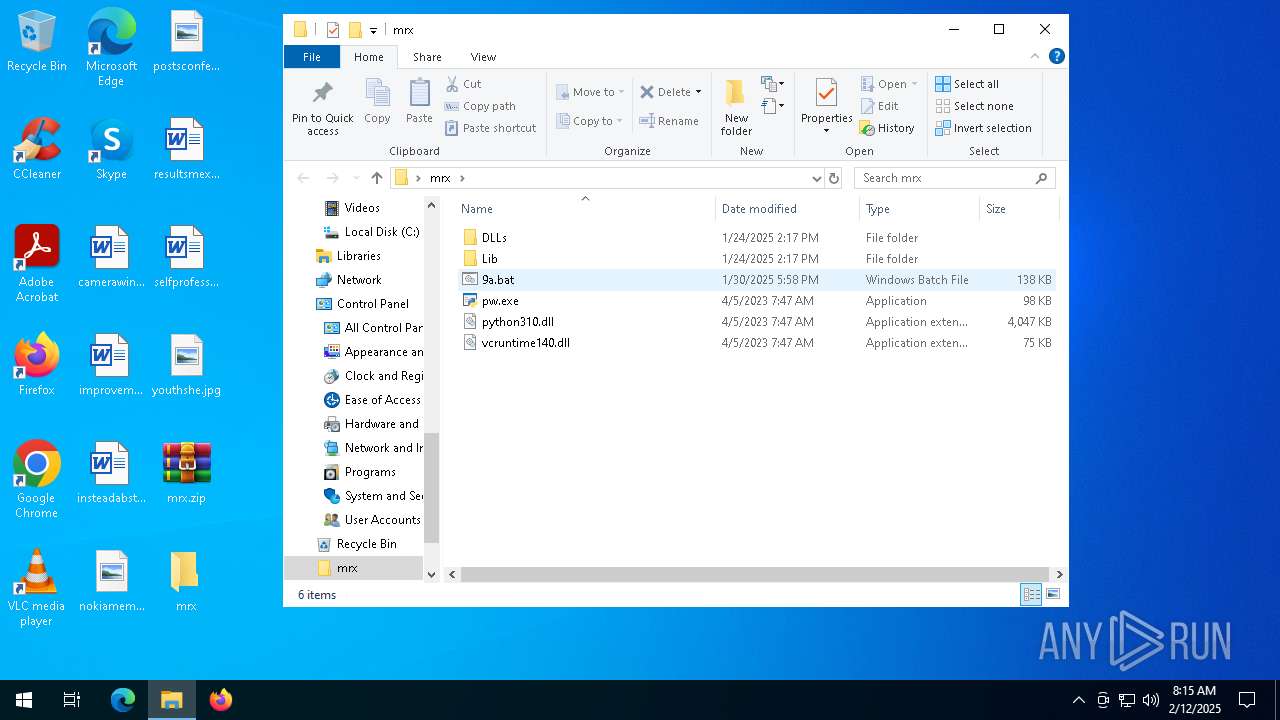
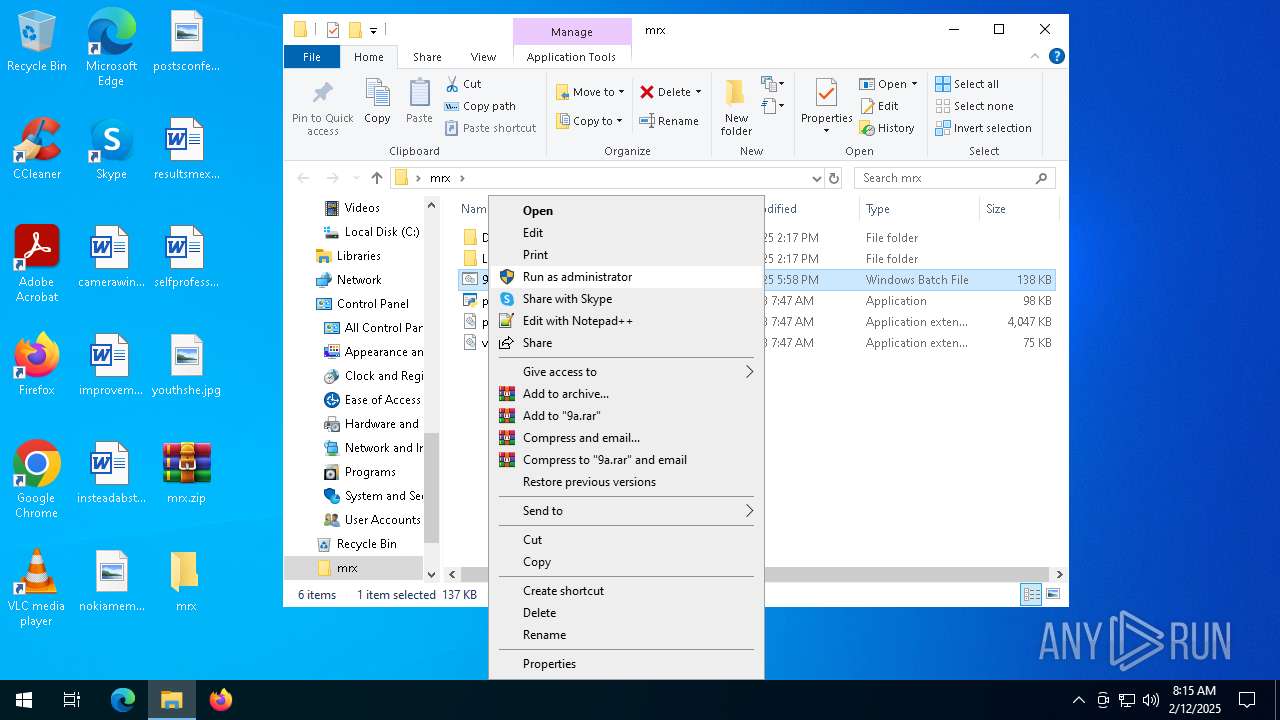
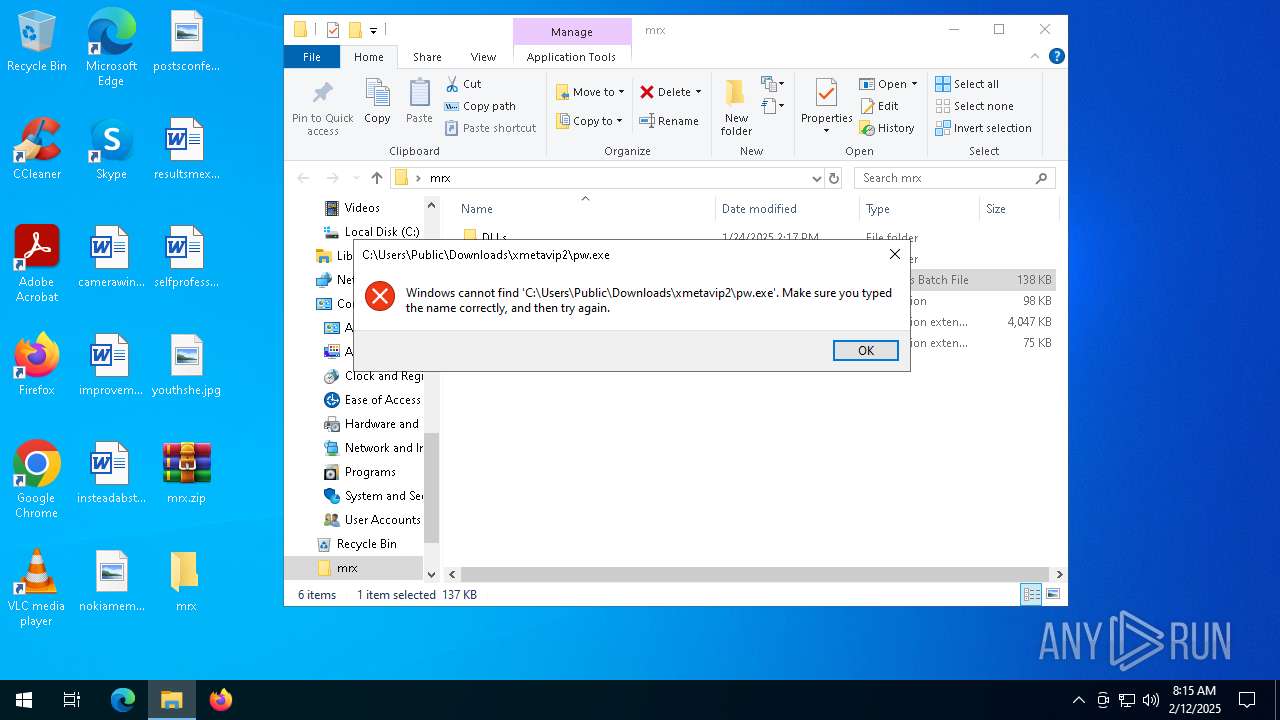
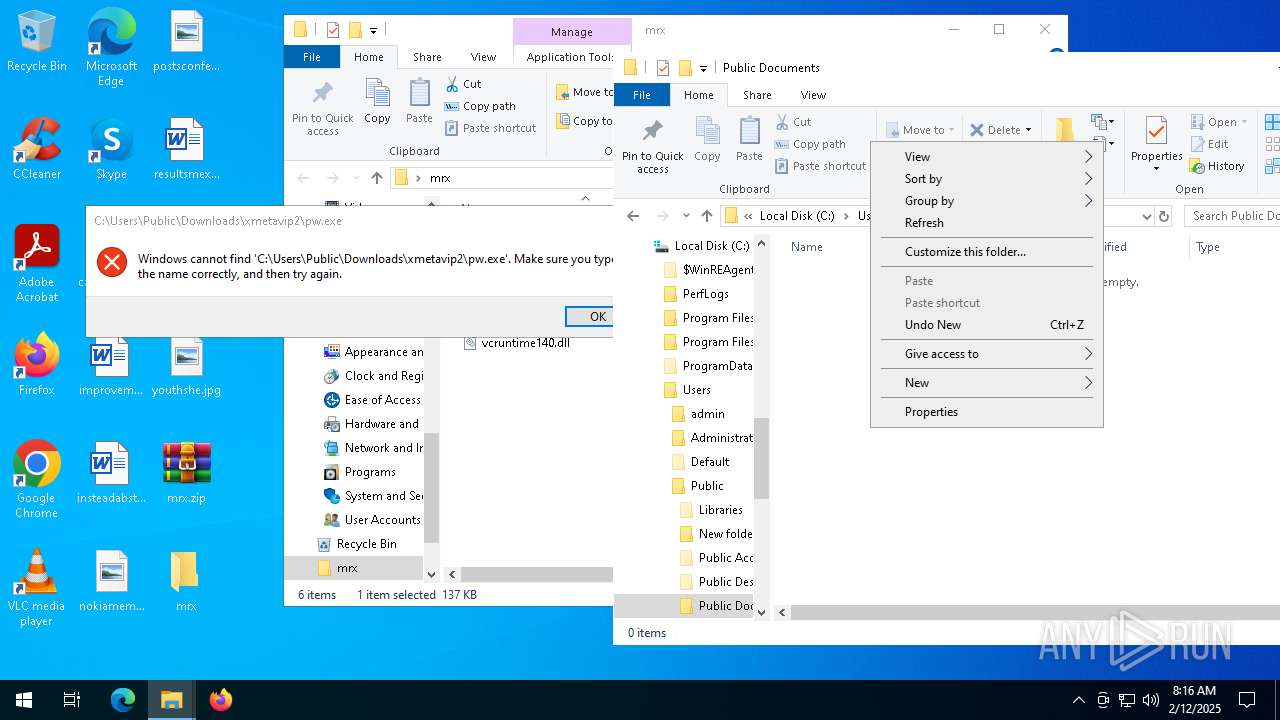
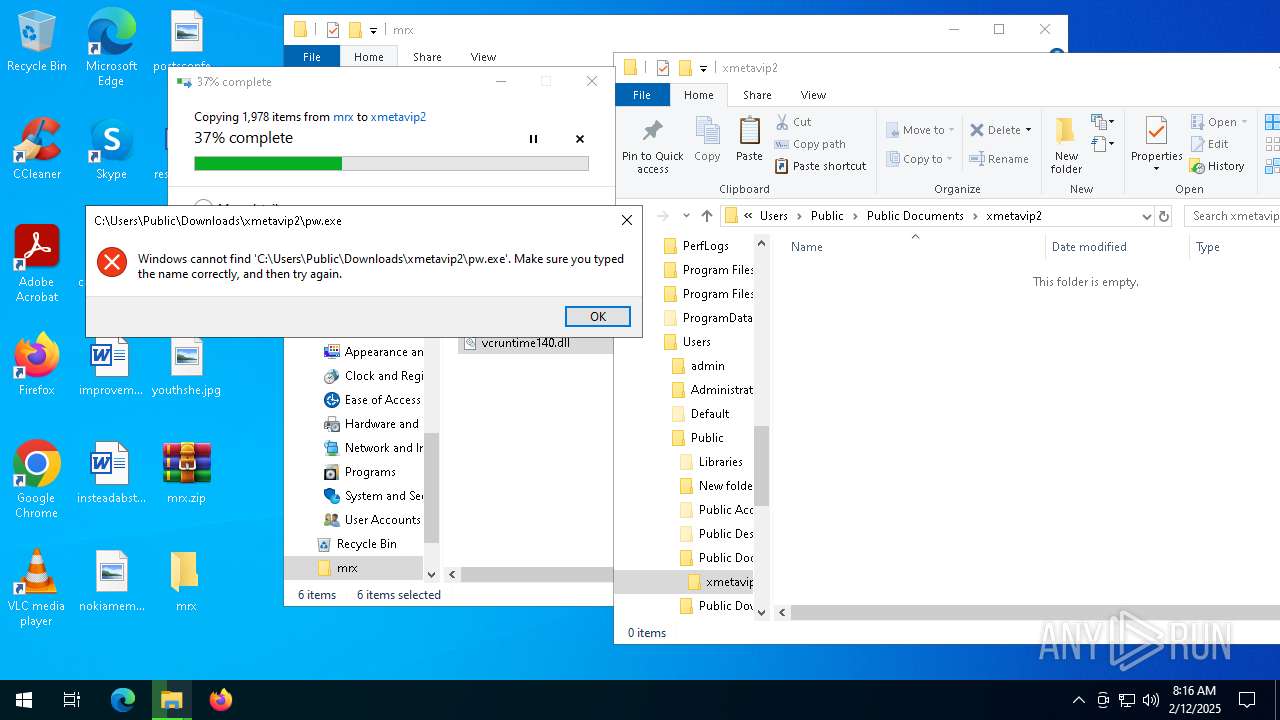
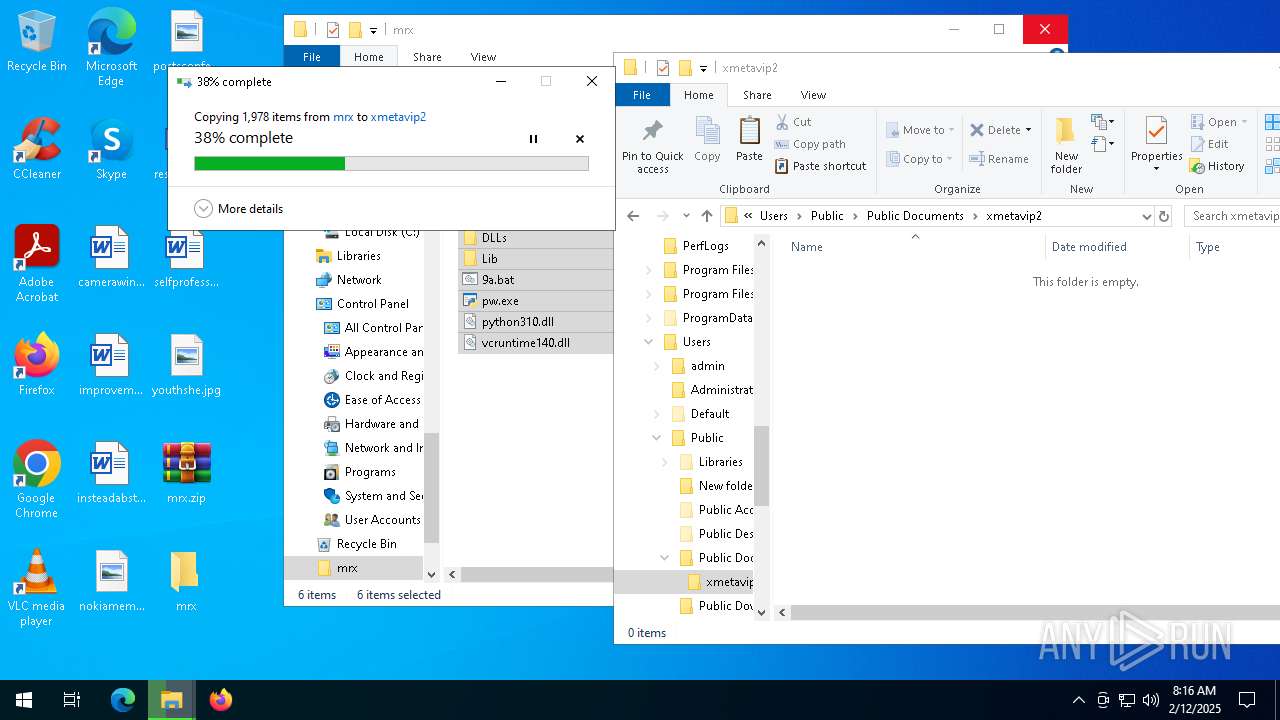
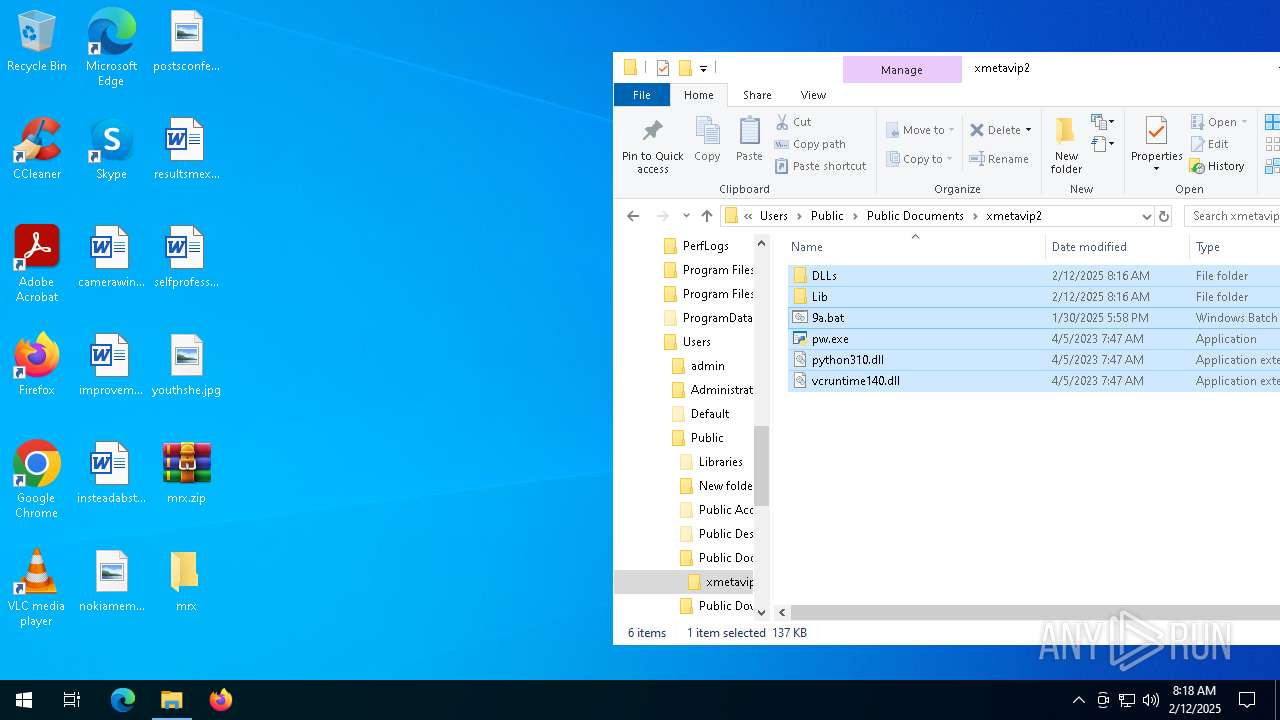
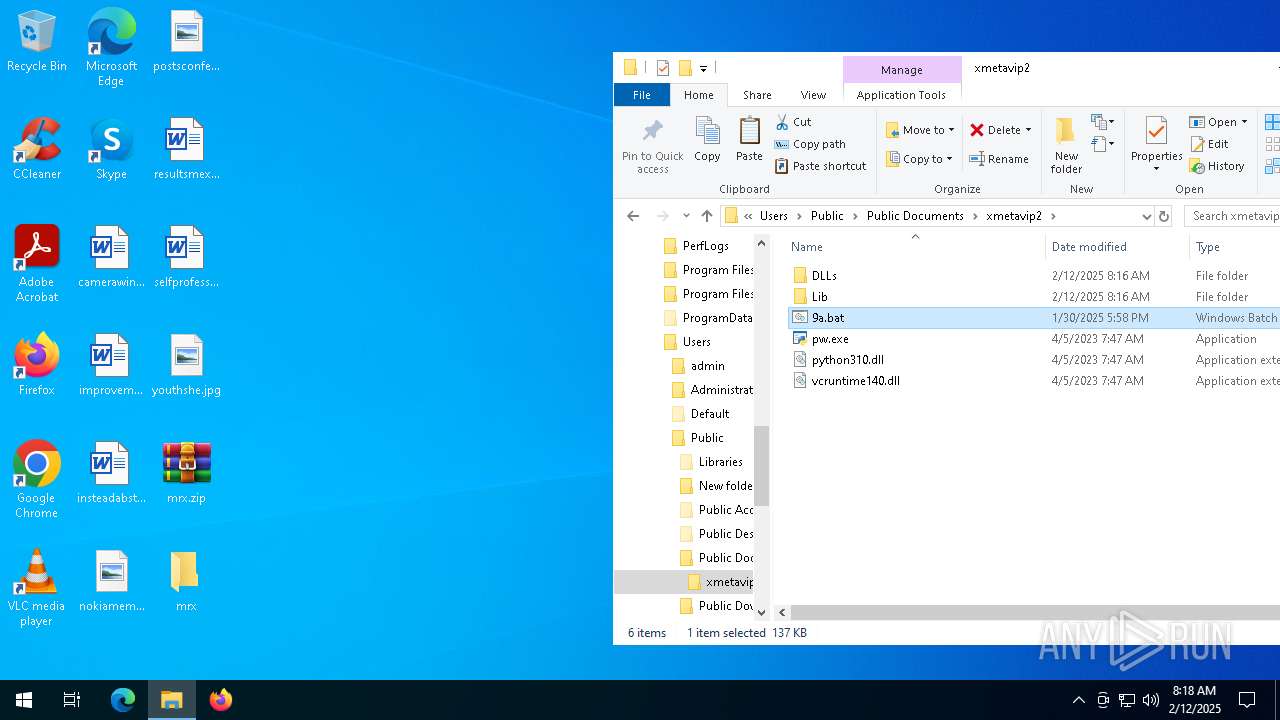
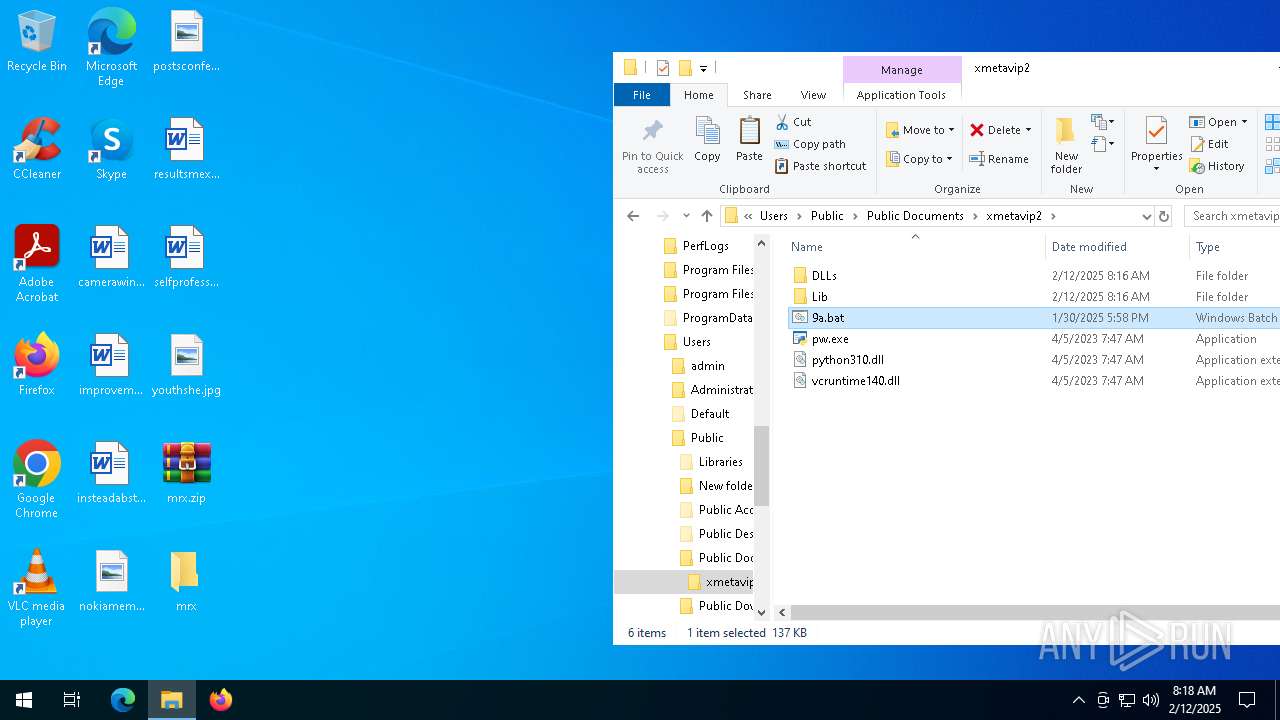
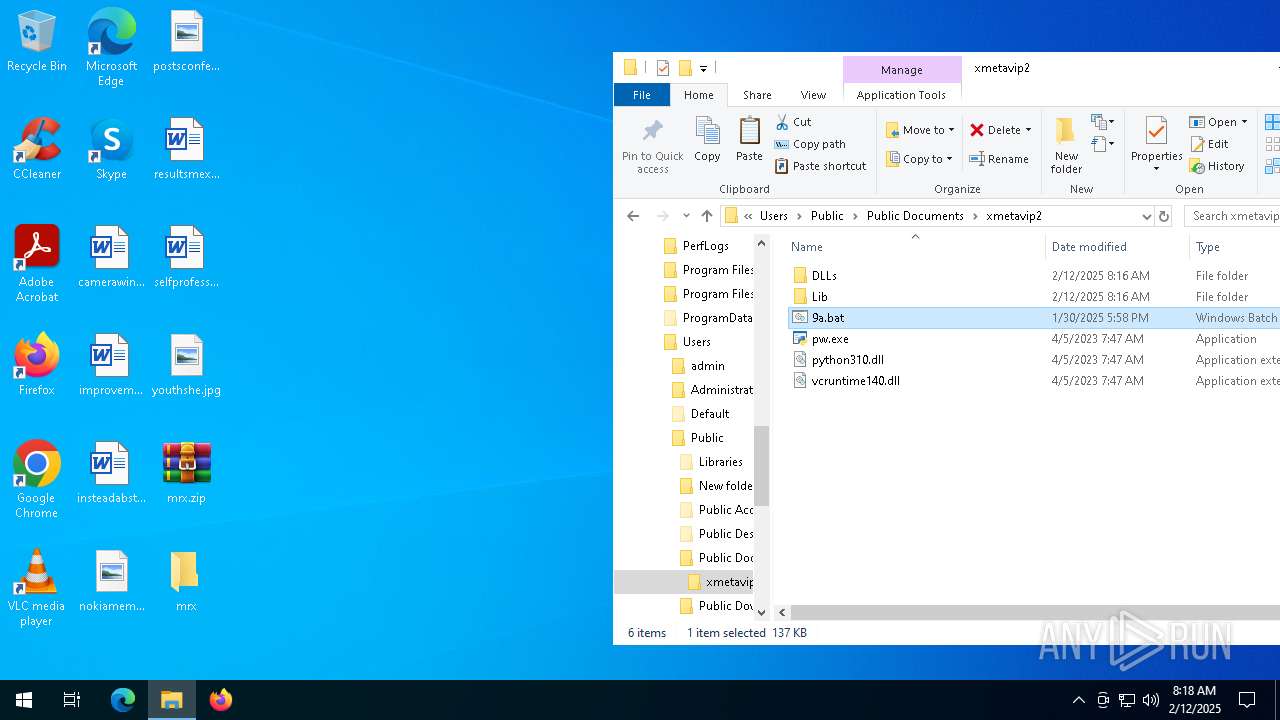
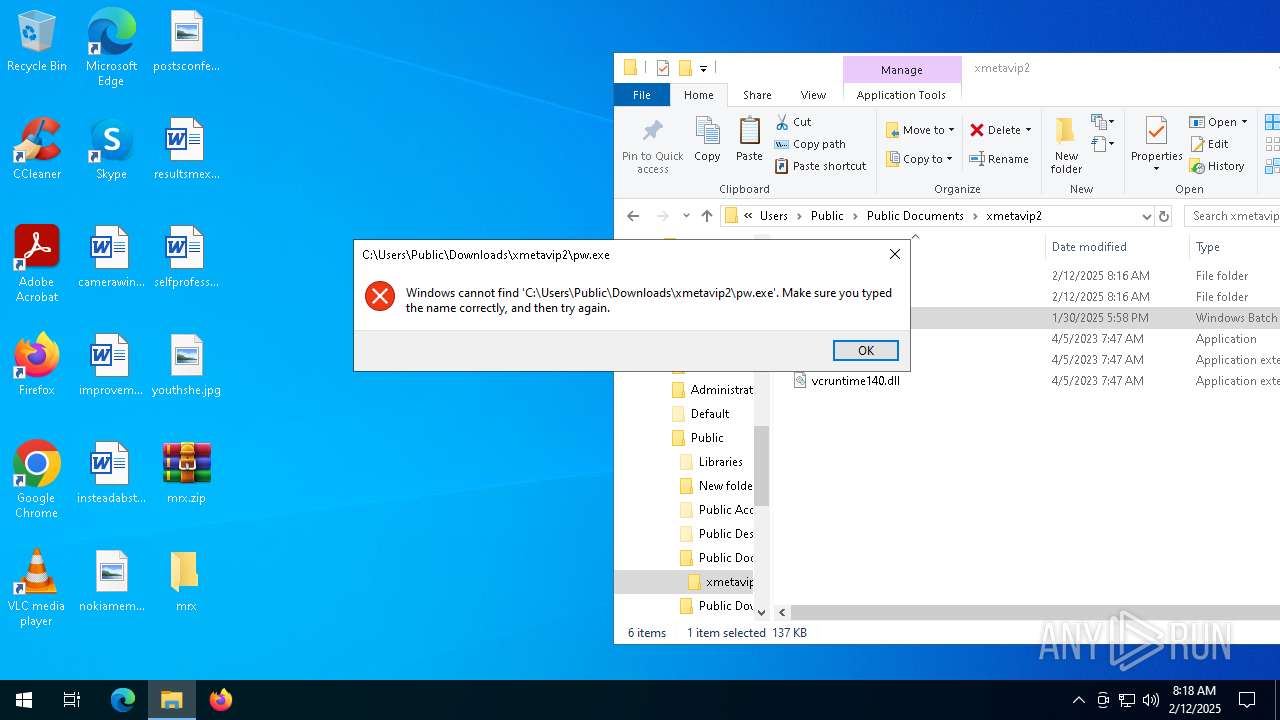
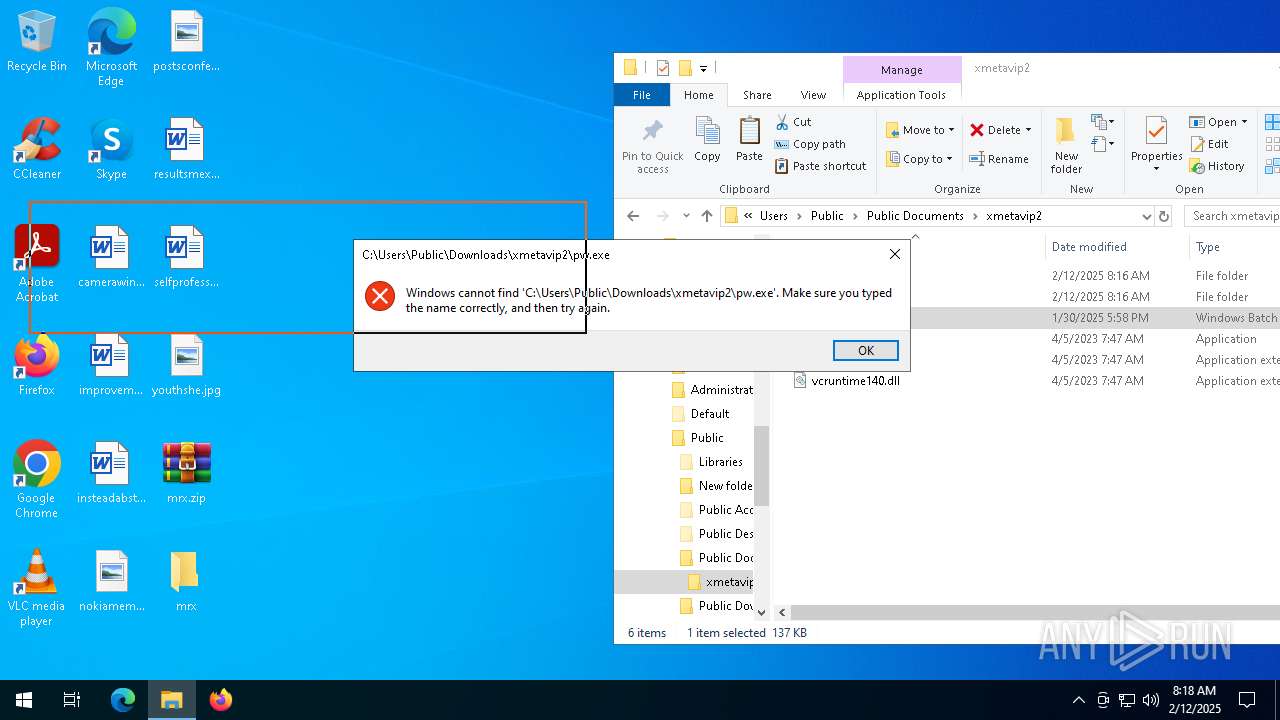
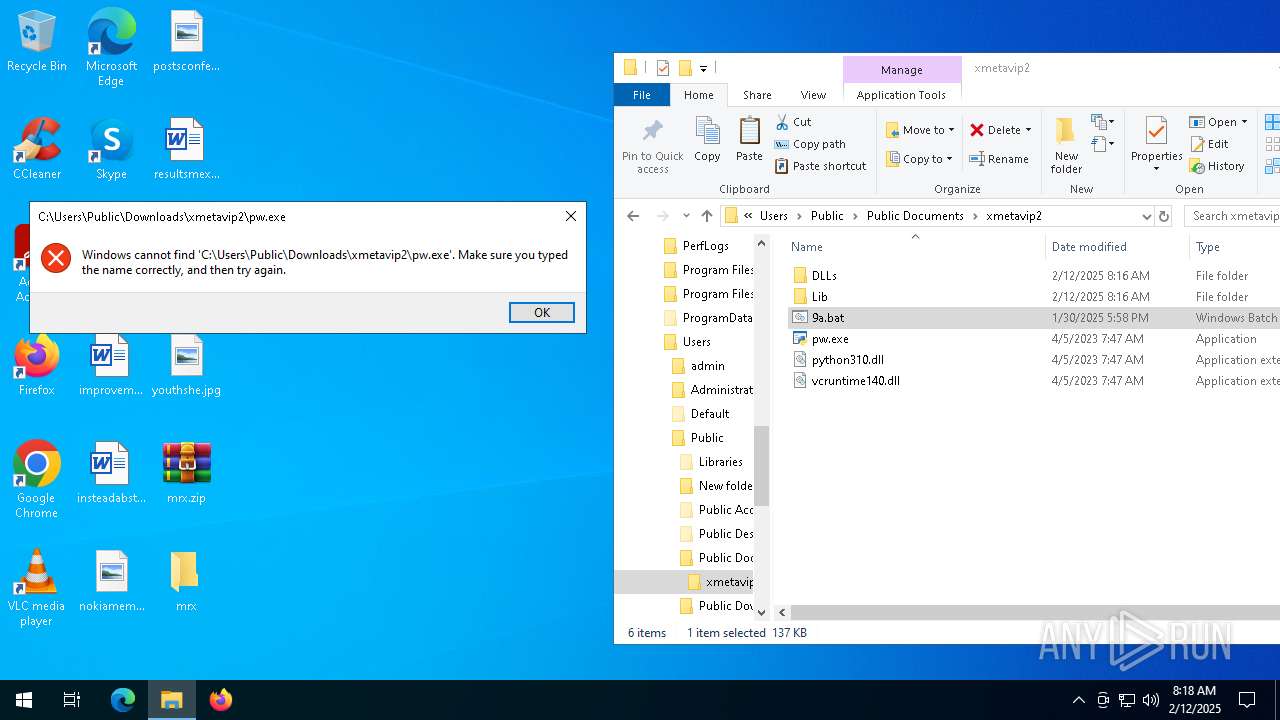
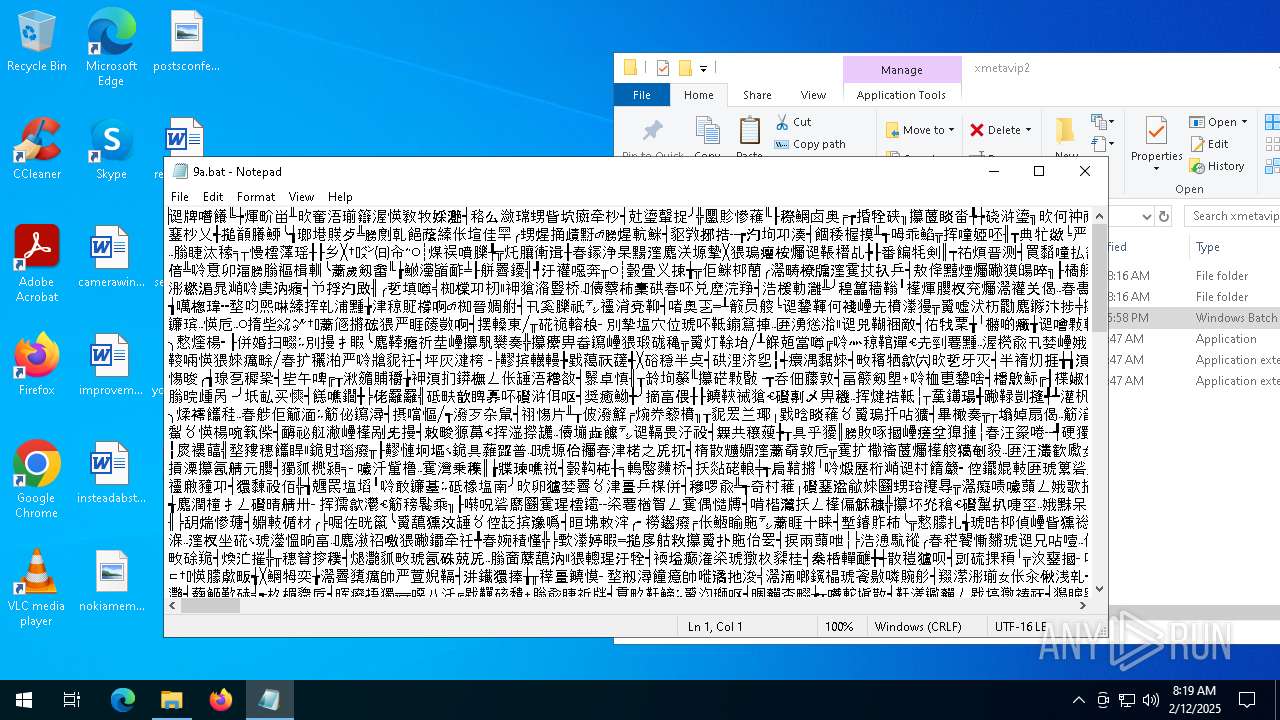
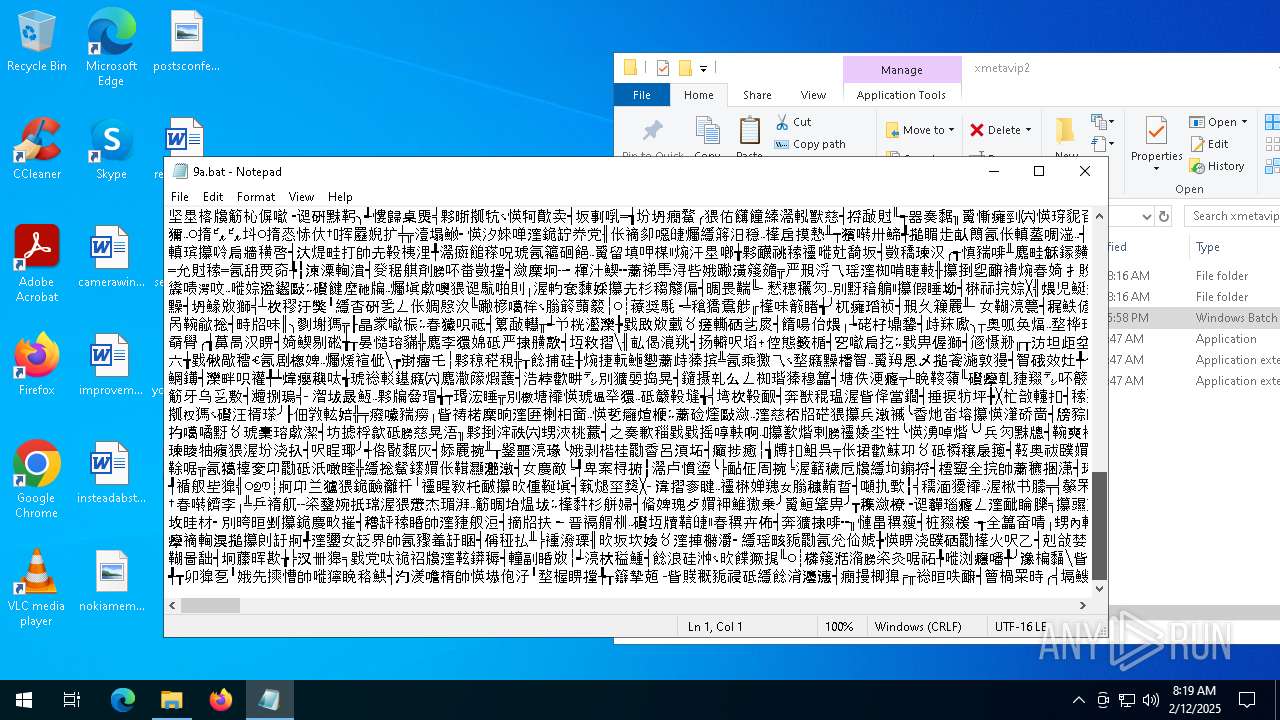
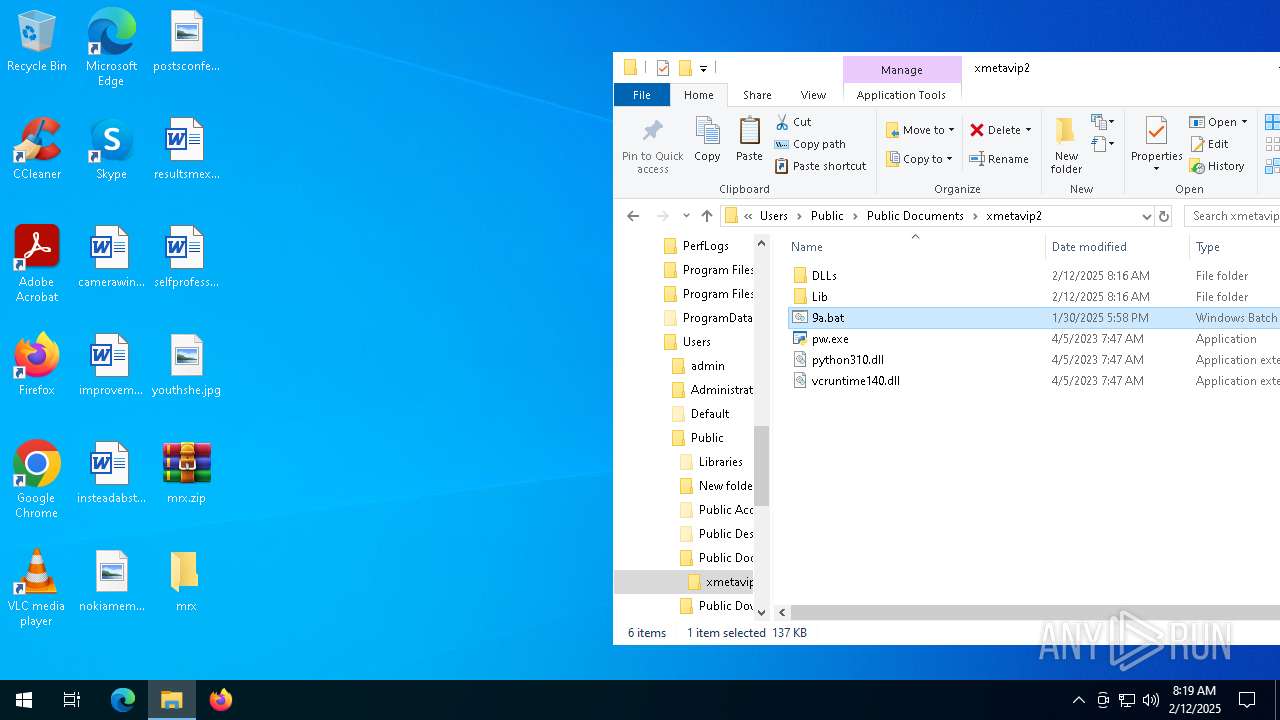
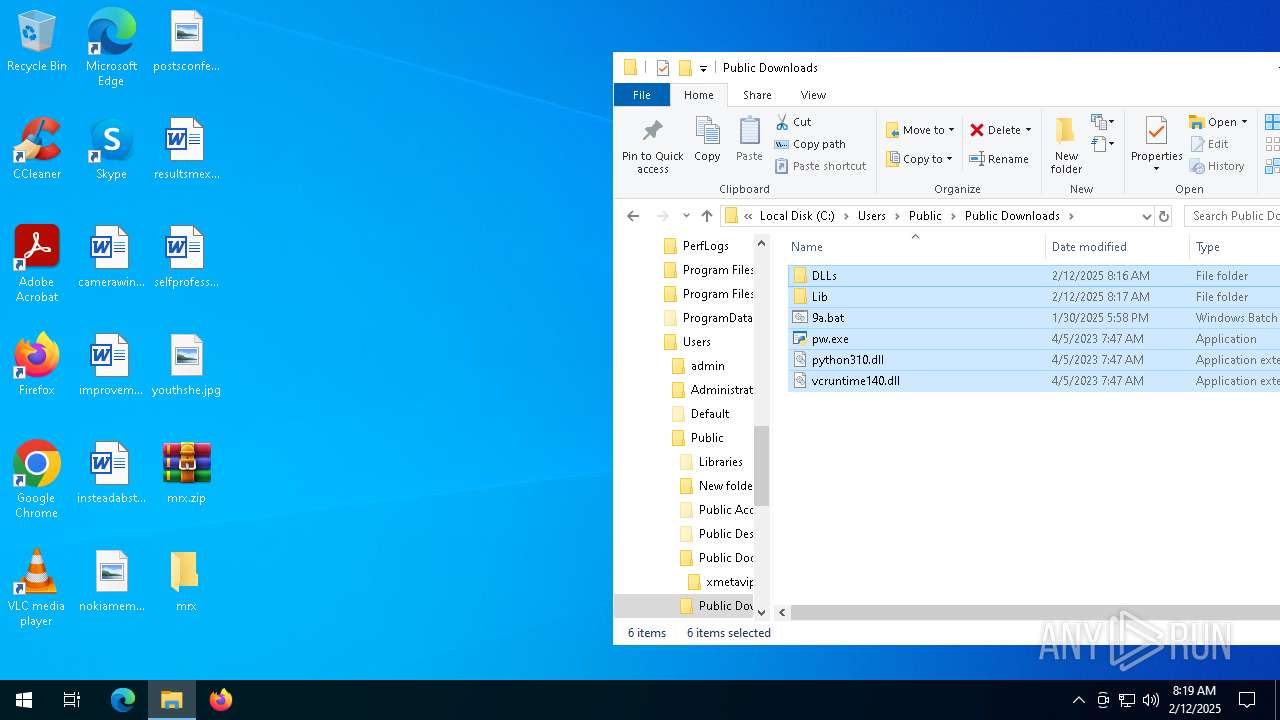
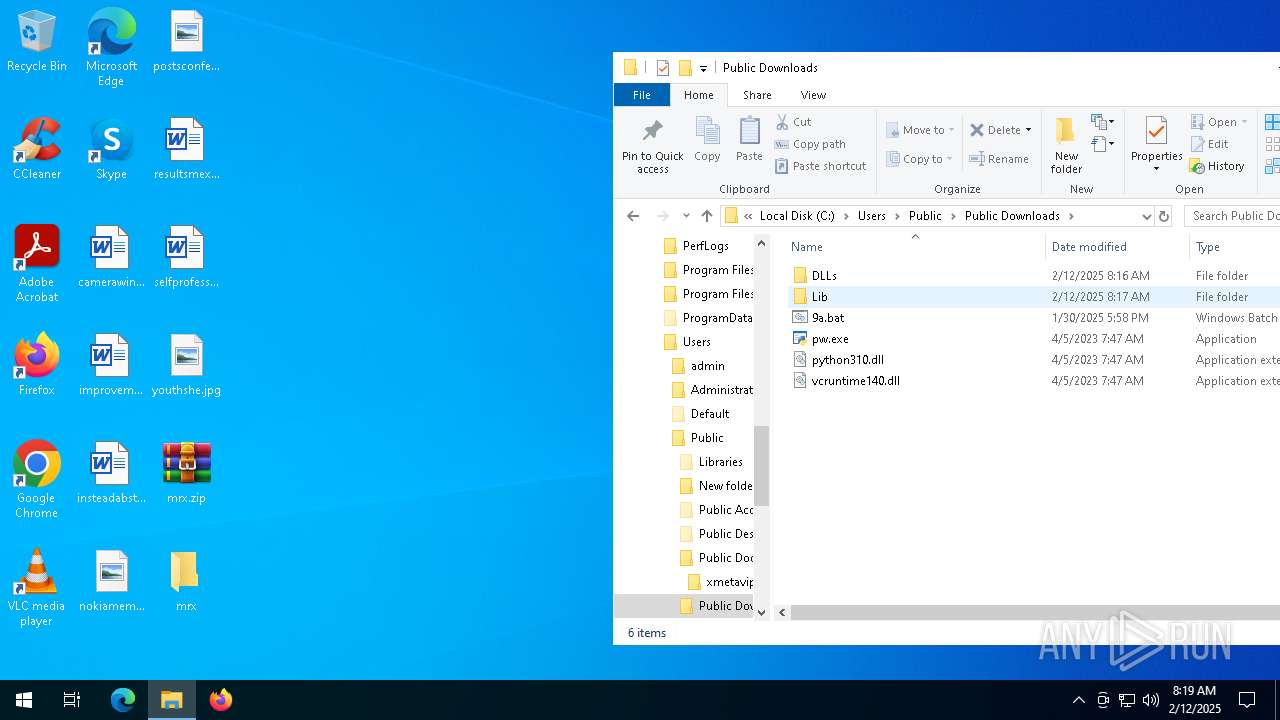
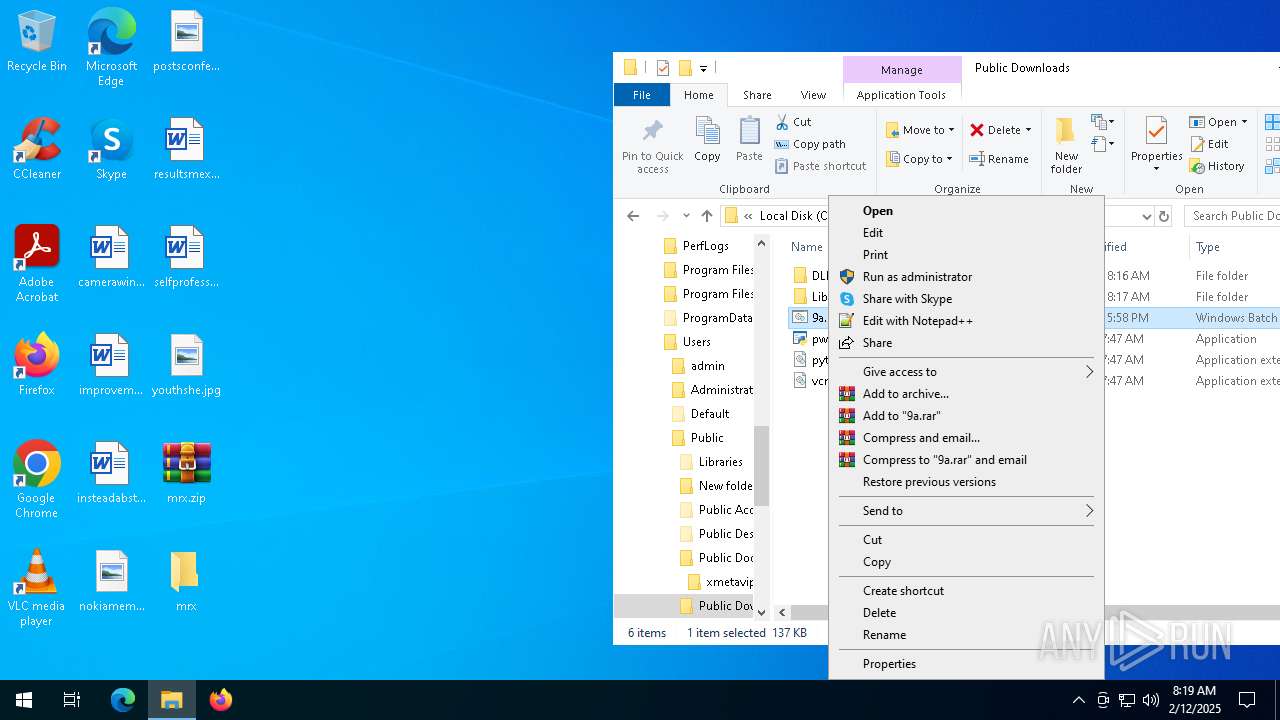
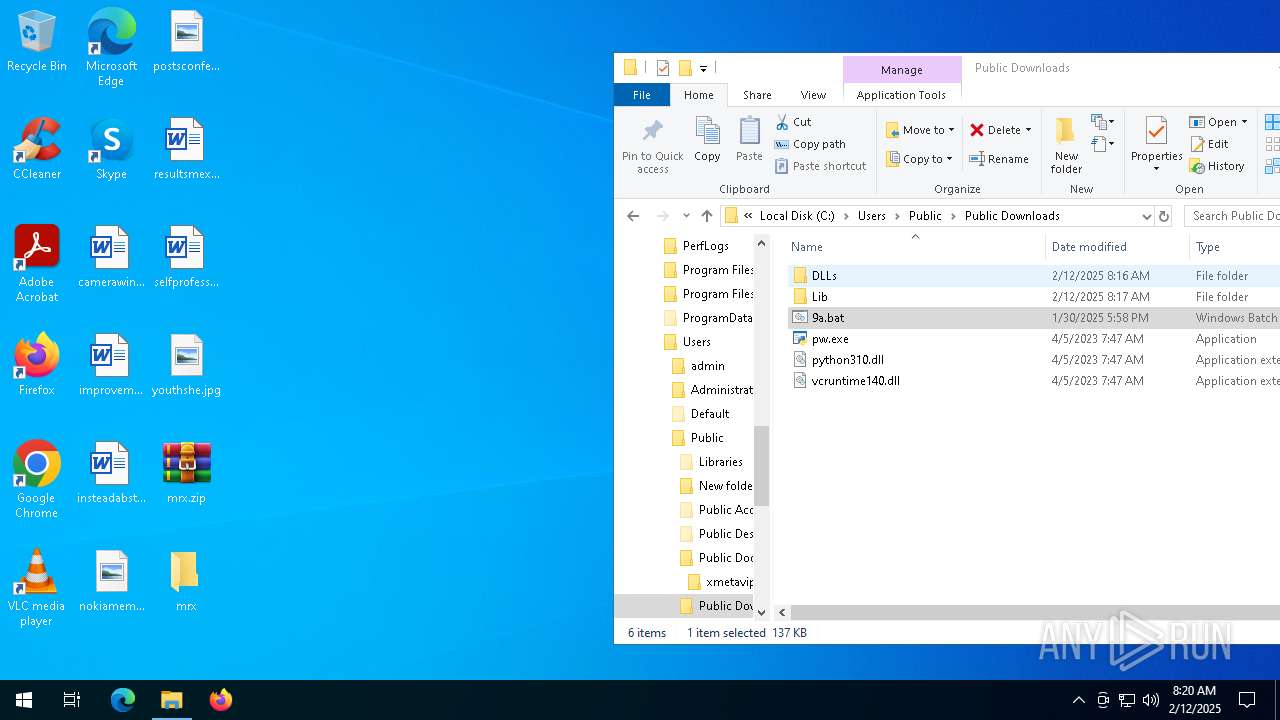
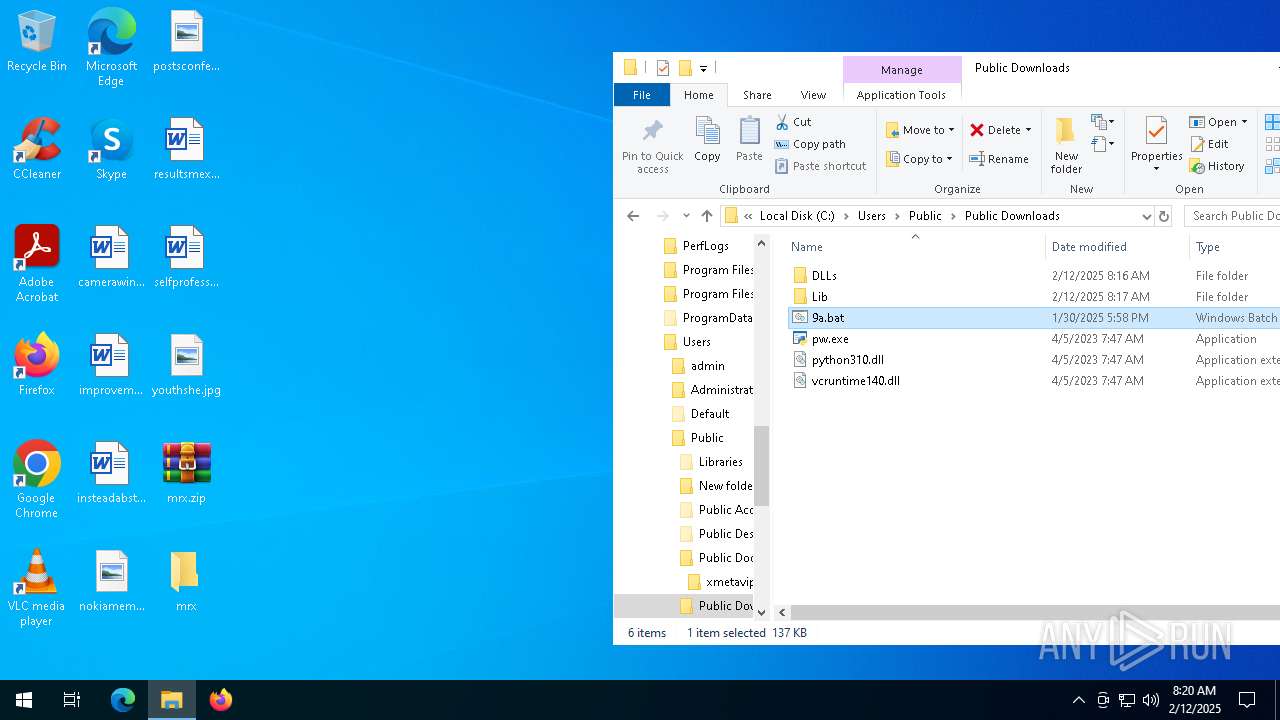
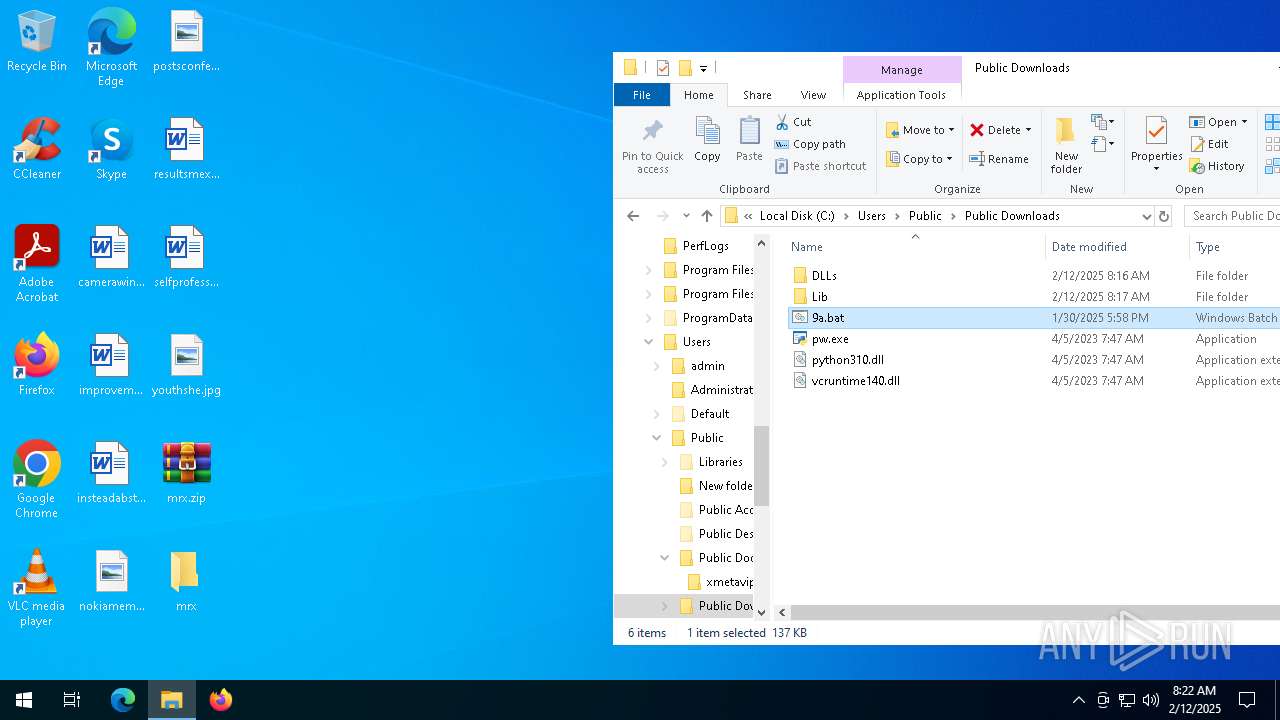
| File name: | mrx.zip |
| Full analysis: | https://app.any.run/tasks/8998fda6-9af8-4f0a-ba64-3077cd35fc08 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 08:12:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 9CBA935E1734B953156C1B3D2586D728 |
| SHA1: | 245CC914071C21043FB21882590C7C0722524171 |
| SHA256: | EB75FFC37F5891F0843F55E6F7B3957A78C277DBF2AD3197ACB630118D84E7D0 |
| SSDEEP: | 196608:T1ZwWRdIuasXd9Hp0ERFq2gYZU+St5SK5RSF5/:T1SWUDsXLmERFqJAG5SKTg5/ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2136)
SUSPICIOUS
Process drops python dynamic module
- WinRAR.exe (PID: 5748)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5748)
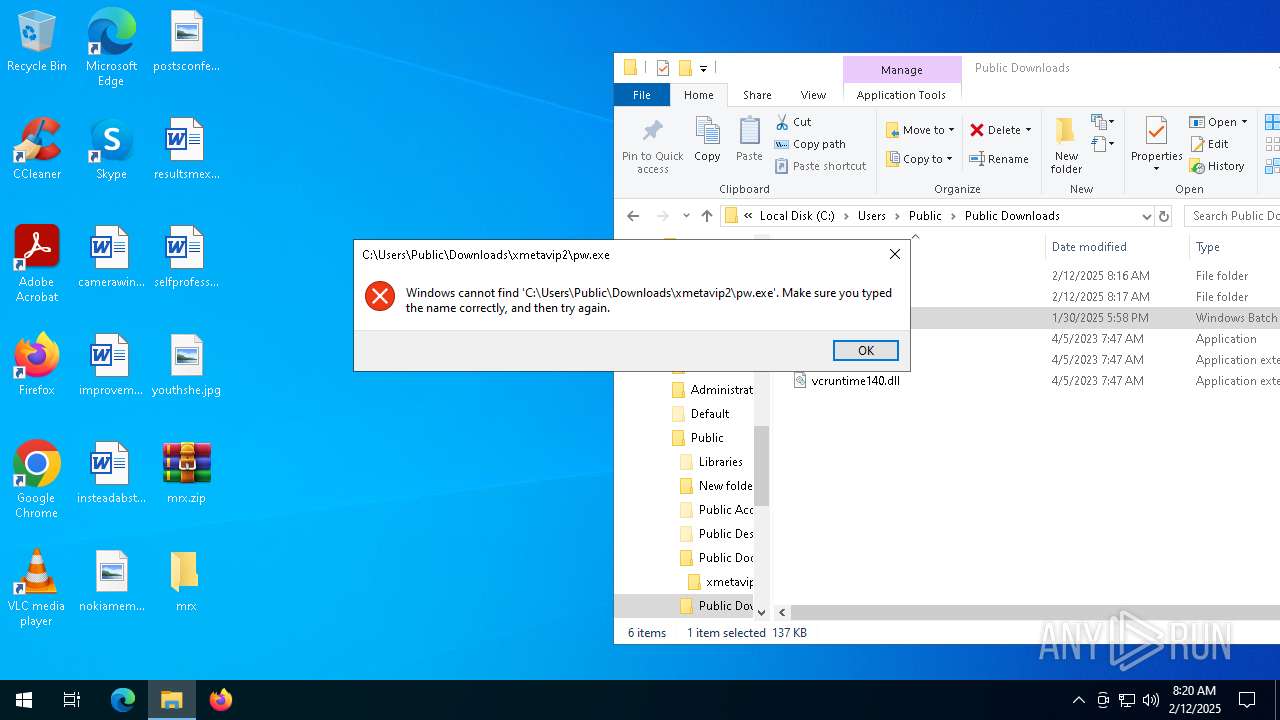
Starts application with an unusual extension
- cmd.exe (PID: 6004)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 1144)
- cmd.exe (PID: 1888)
- cmd.exe (PID: 836)
- cmd.exe (PID: 1344)
Executing commands from a ".bat" file
- mshta.exe (PID: 1792)
- mshta.exe (PID: 4804)
- mshta.exe (PID: 2608)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 1792)
- mshta.exe (PID: 4804)
- cmd.exe (PID: 1144)
- cmd.exe (PID: 836)
- cmd.exe (PID: 1344)
- mshta.exe (PID: 2608)
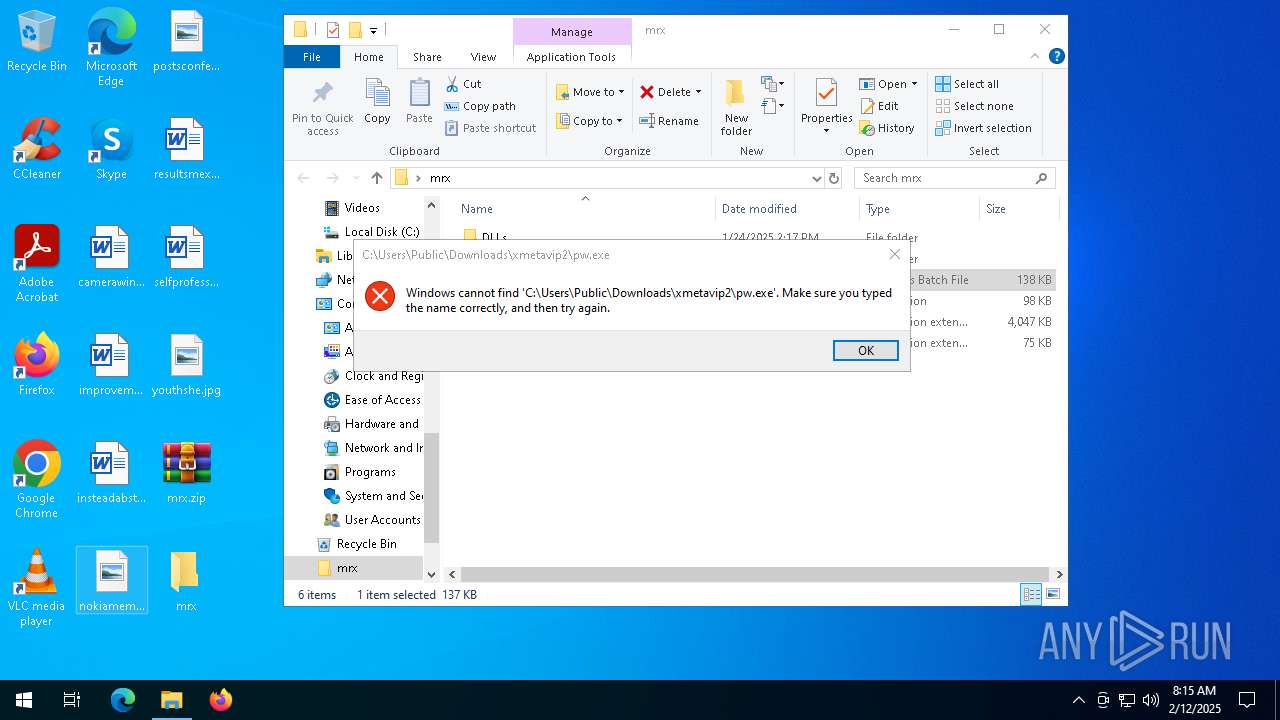
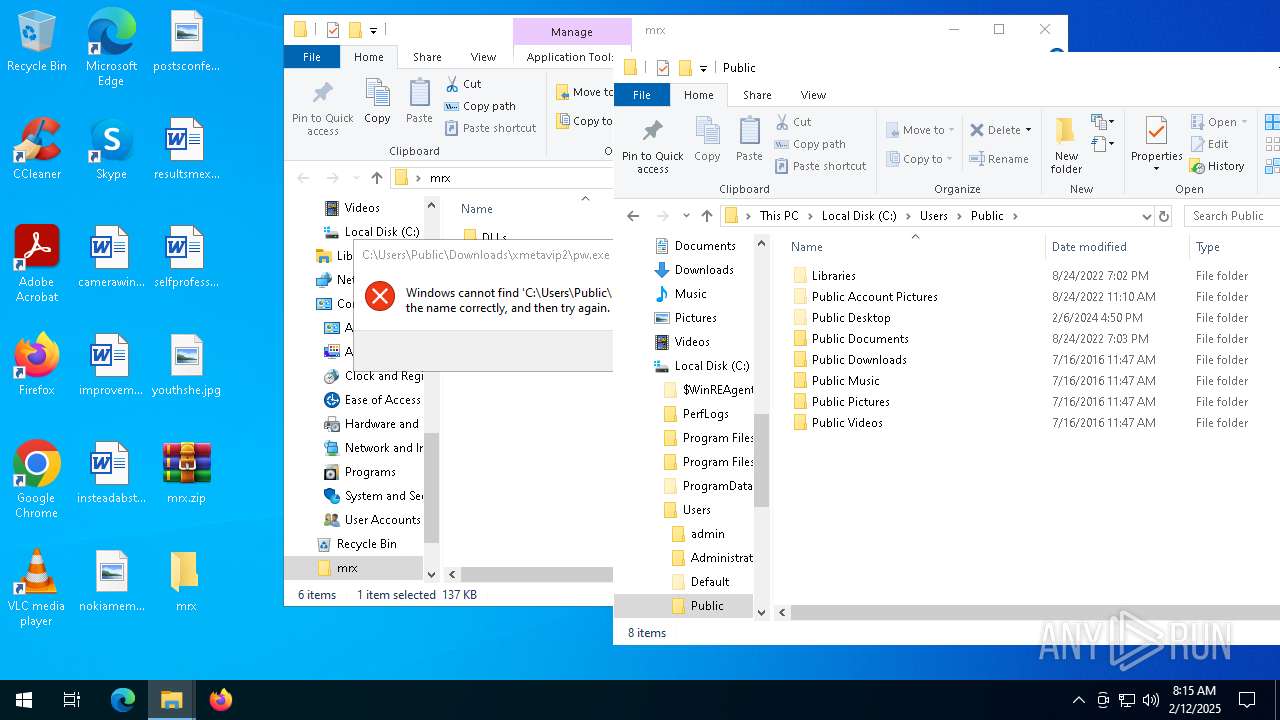
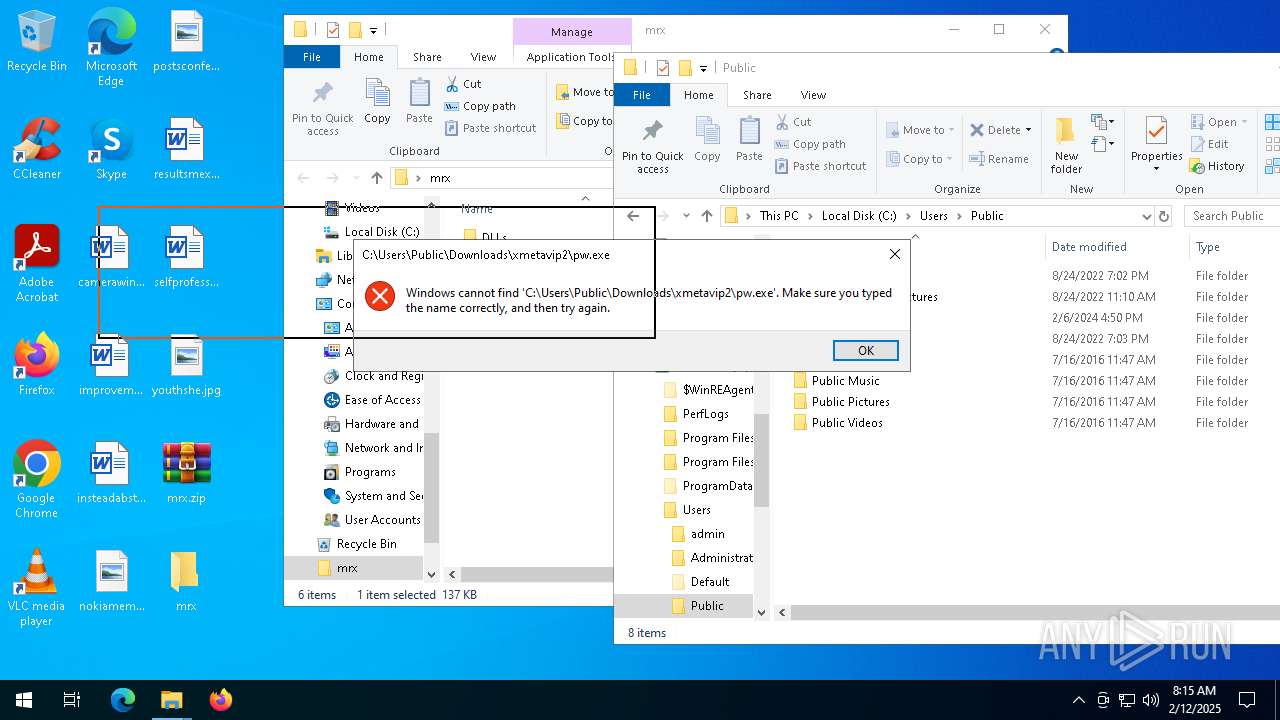
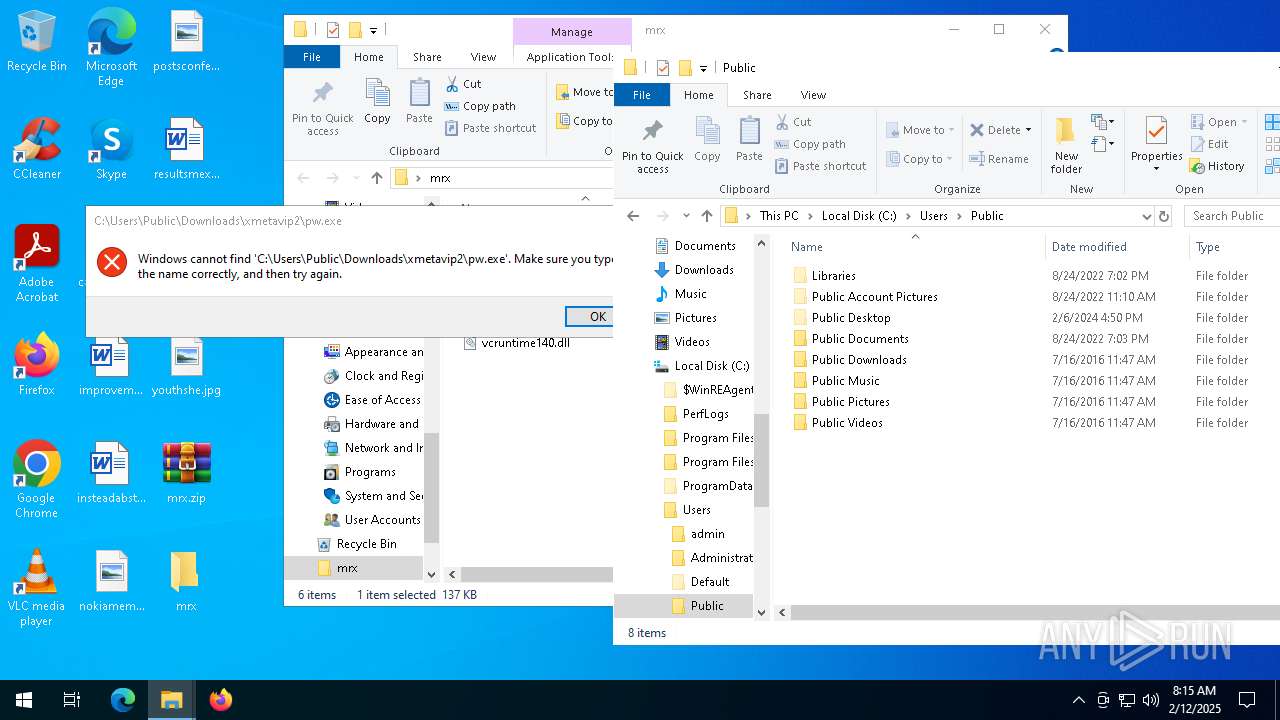
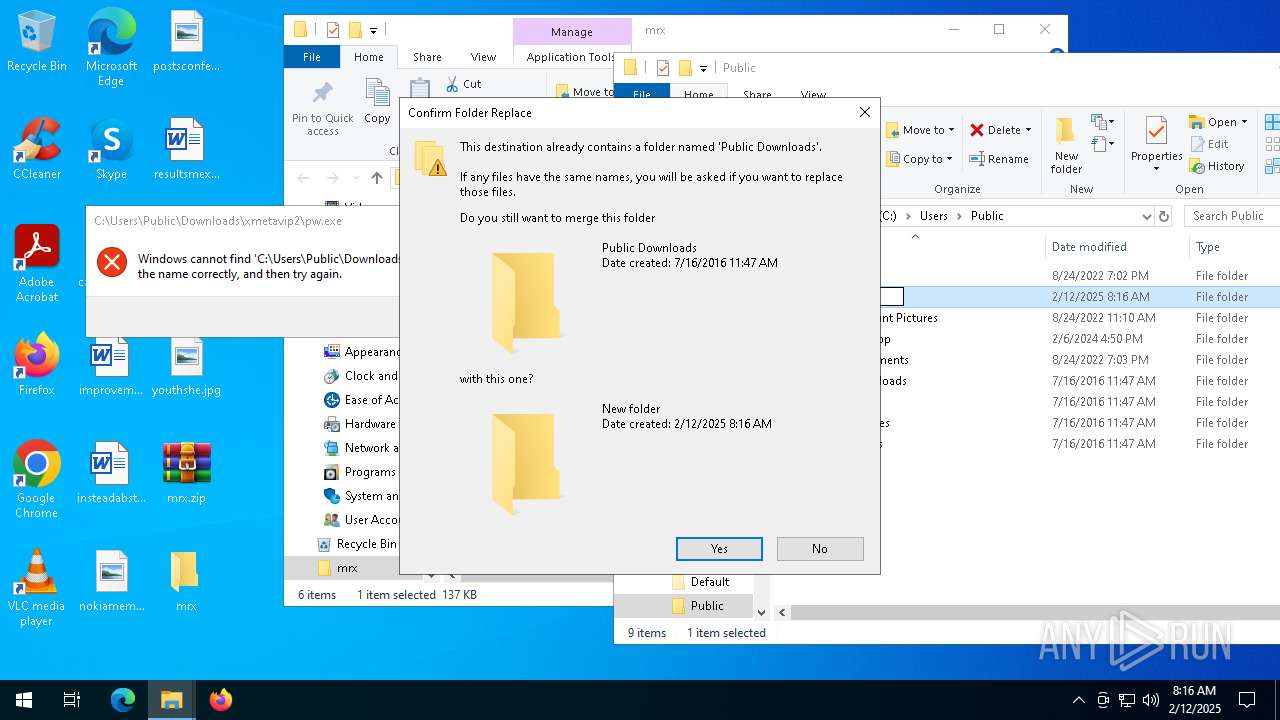
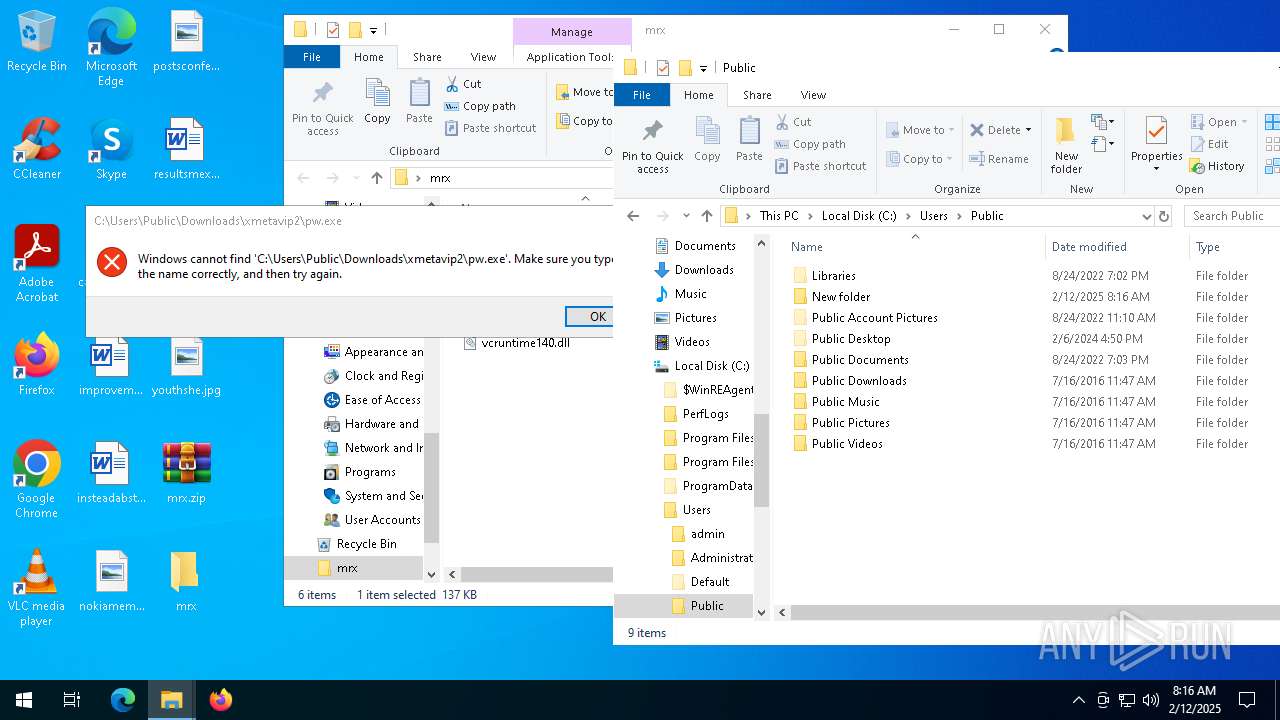
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 4428)
- mshta.exe (PID: 4804)
- cmd.exe (PID: 836)
- cmd.exe (PID: 5728)
- cmd.exe (PID: 5656)
- notepad.exe (PID: 4556)
- cmd.exe (PID: 1888)
- mshta.exe (PID: 2608)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 5556)
Application launched itself
- cmd.exe (PID: 1144)
- cmd.exe (PID: 836)
- cmd.exe (PID: 1344)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5208)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5748)
Manual execution by a user
- WinRAR.exe (PID: 5748)
- cmd.exe (PID: 6004)
- cmd.exe (PID: 4428)
- notepad.exe (PID: 4556)
- cmd.exe (PID: 1888)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5748)
Changes the display of characters in the console
- cmd.exe (PID: 6004)
- cmd.exe (PID: 1144)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 836)
- cmd.exe (PID: 1888)
- cmd.exe (PID: 1344)
Checks supported languages
- chcp.com (PID: 5268)
- ShellExperienceHost.exe (PID: 5208)
- chcp.com (PID: 5592)
- chcp.com (PID: 1544)
- chcp.com (PID: 2212)
- chcp.com (PID: 1888)
- chcp.com (PID: 3260)
Reads Internet Explorer settings
- mshta.exe (PID: 1792)
- mshta.exe (PID: 4804)
- mshta.exe (PID: 2608)
Checks proxy server information
- mshta.exe (PID: 1792)
- mshta.exe (PID: 4804)
- mshta.exe (PID: 2608)
Reads the computer name
- ShellExperienceHost.exe (PID: 5208)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (42.1) |
|---|---|---|
| .zip | | | ZIP compressed archive (21) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:24 21:17:50 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | DLLs/ |
Total processes
169
Monitored processes
30
Malicious processes
0
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\DOCUME~1\XMETAV~1\9a.bat" ::" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\mrx\9a.bat" ::" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\DOWNLO~1\9a.bat" ::" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1792 | mshta vbscript:createobject("wscript.shell").run("""C:\Users\admin\Desktop\mrx\9a.bat"" ::",0)(window.close) | C:\Windows\System32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1888 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1888 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\Public\Downloads\9a.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\mrx.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2212 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2608 | mshta vbscript:createobject("wscript.shell").run("""C:\Users\Public\DOWNLO~1\9a.bat"" ::",0)(window.close) | C:\Windows\System32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 923
Read events
5 892
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\mrx.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
127
Suspicious files
294
Text files
1 350
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\libcrypto-1_1.dll | executable | |
MD5:4633D62F19C0B25318B1C612995F5C21 | SHA256:47376D247AE6033BC30FEE4E52043D3762C1C0C177E3EC27CA46EFF4B95C69B0 | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\libffi-7.dll | executable | |
MD5:BC20614744EBF4C2B8ACD28D1FE54174 | SHA256:0C7EC6DE19C246A23756B8550E6178AC2394B1093E96D0F43789124149486F57 | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\pyexpat.pyd | executable | |
MD5:92C72753FA5C8EAA615B007F89CDB482 | SHA256:EBBDE07AFB2BB356CD400E97D8AFB5ABBC121CC0CC90F99BEC9C3FA5CA60DE14 | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\sqlite3.dll | executable | |
MD5:C60F6C4051EB55350C6EEDF5A87016AA | SHA256:376D80DB08CEC2C8873A4D5EBC7D83F50F26A43EBAA837020874C8586FD85975 | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\python_lib.cat | binary | |
MD5:830E831E1896D35A5E414D518AC05A2B | SHA256:739B93F1ABFD7E6188F0C86172E526DAD72E29E0FC177E4B8C4E3686DD90AE9B | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\py.ico | image | |
MD5:B35F68A3086562C4D5453FAAD5A3474E | SHA256:150C470F9943B806B44312EFDEC85755F22F8D7D52B31F93A9AF3C43E8627381 | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\python_tools.cat | binary | |
MD5:E33C9E857AD27ADBE33B26AB13890657 | SHA256:EDE0345311D5D825BA03E10423CF51515B3F3962F1286E46E1E6198ADFEC67CF | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\libssl-1_1.dll | executable | |
MD5:8845FCF1AE2DE1018DAAAEA01D9BA2D5 | SHA256:B7E16AF3EFF9AB0869CFE60C256394A70A867879B7F56544A724D6AC1CCFAB88 | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\_bz2.pyd | executable | |
MD5:5C952E57426E429F6F4CEC9FEB841815 | SHA256:B682E9E8152036BDEBF4CA5410D3C0F88FA3272A969830F63C7B61BB1F0DA89F | |||
| 5748 | WinRAR.exe | C:\Users\admin\Desktop\mrx\DLLs\pyd.ico | image | |
MD5:1A8230030D821CF8EA57CE03AAEAD737 | SHA256:C4EC1845A5724B2A83500F3BD940355E2FE26EFC6B4FE6C208365359A6130DA1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
77
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.206:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
5404 | SIHClient.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5404 | SIHClient.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5404 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5404 | SIHClient.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5404 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5404 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
132 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.19.96.75:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5404 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5404 | SIHClient.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |