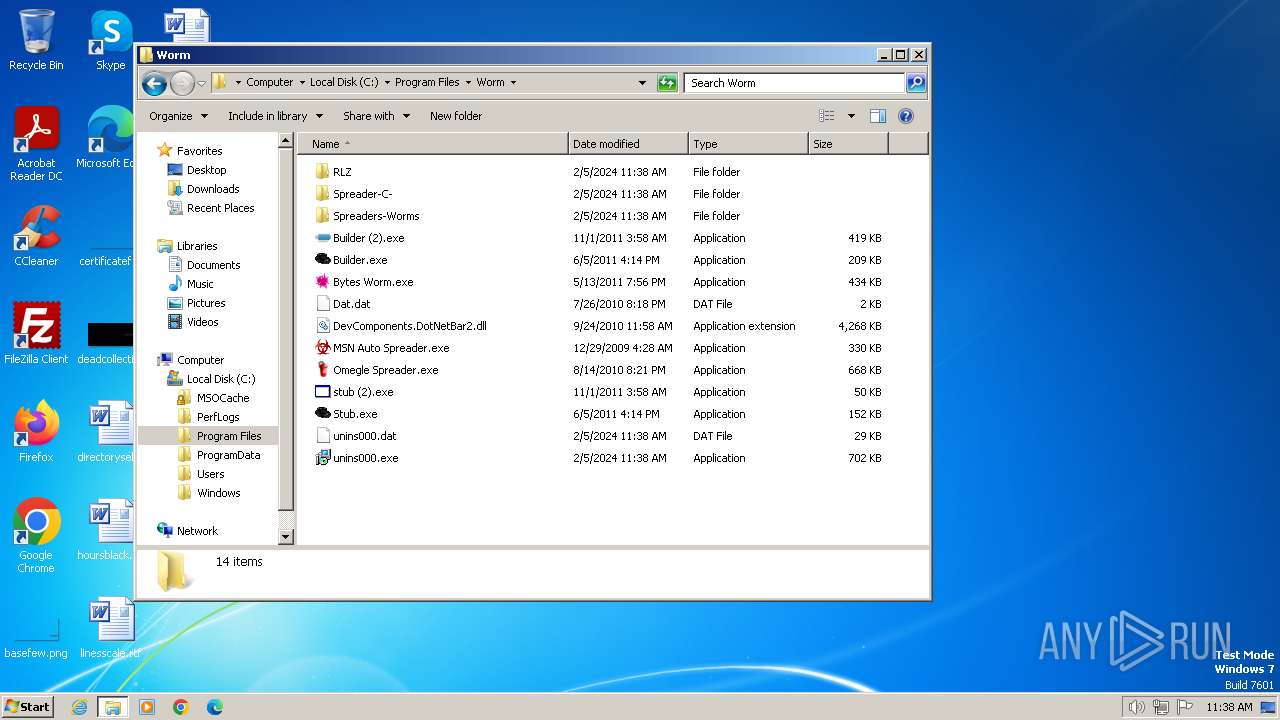
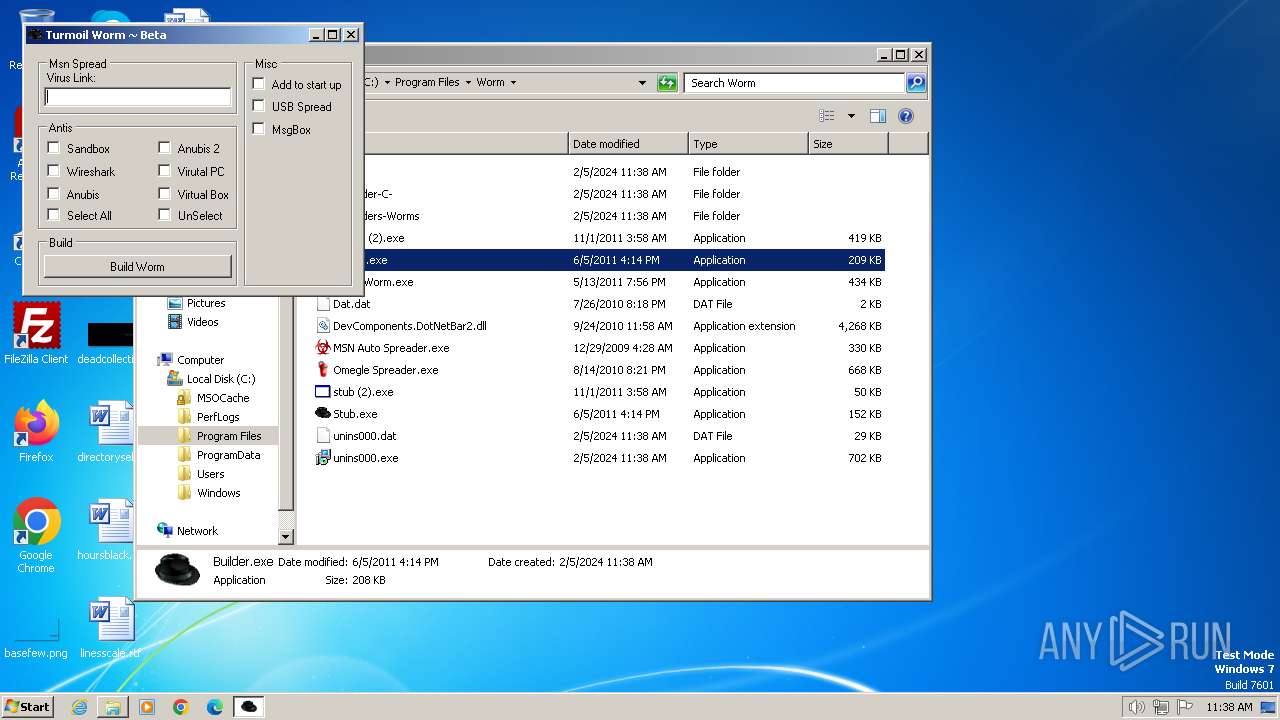
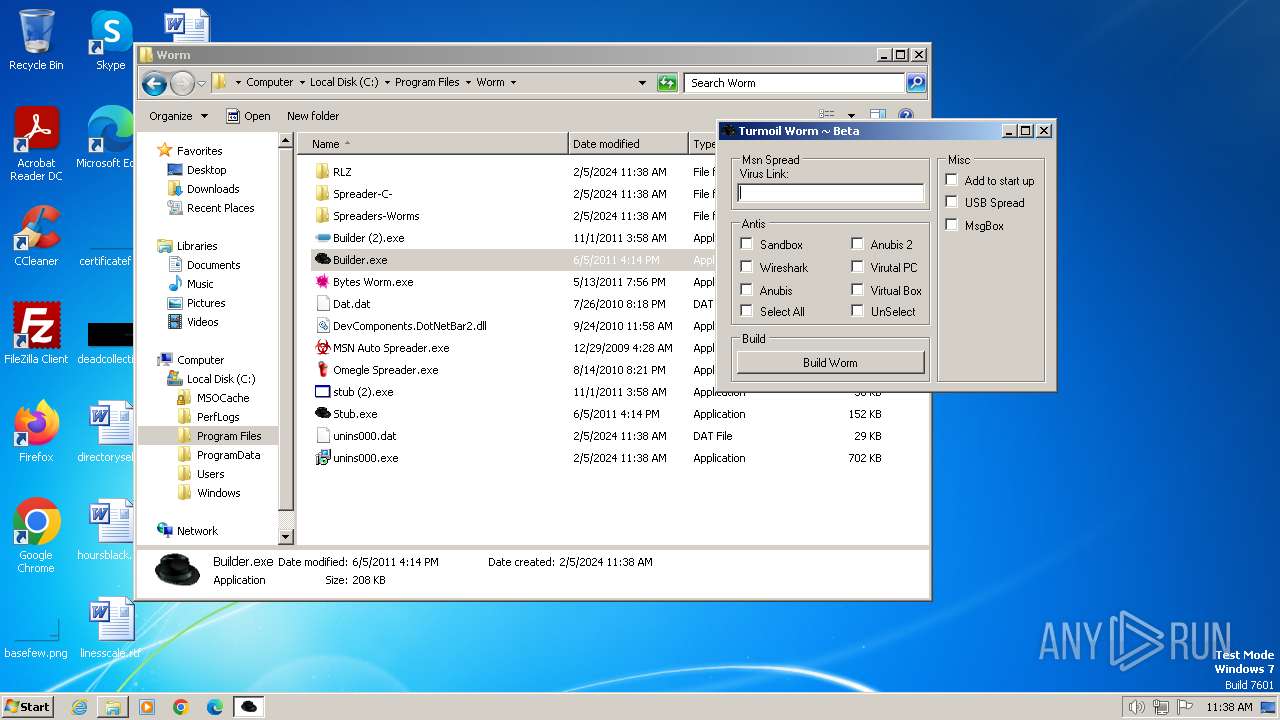
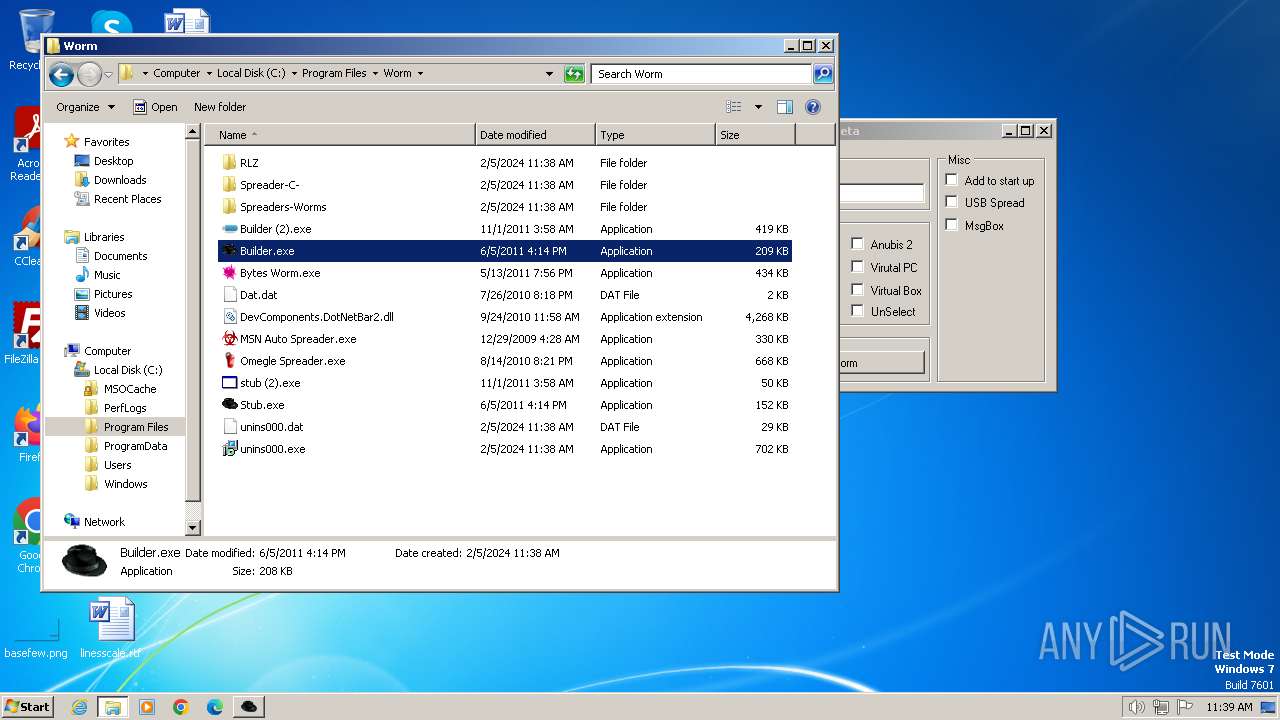
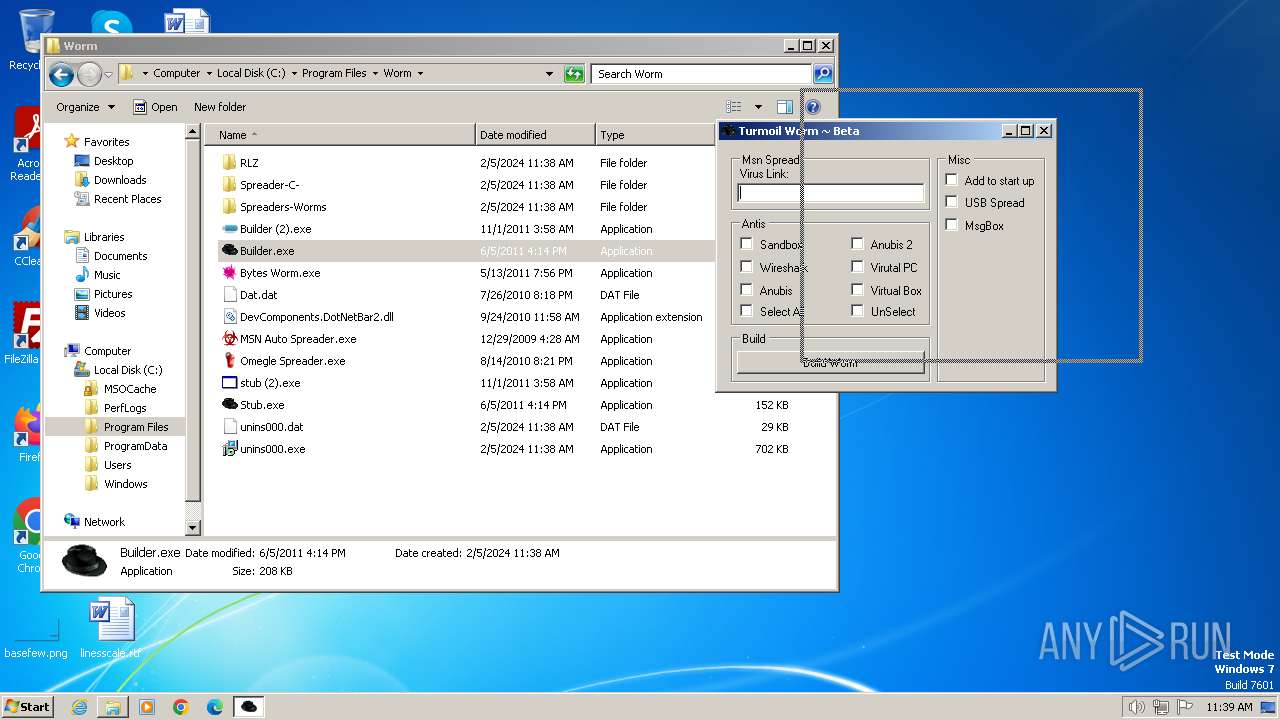
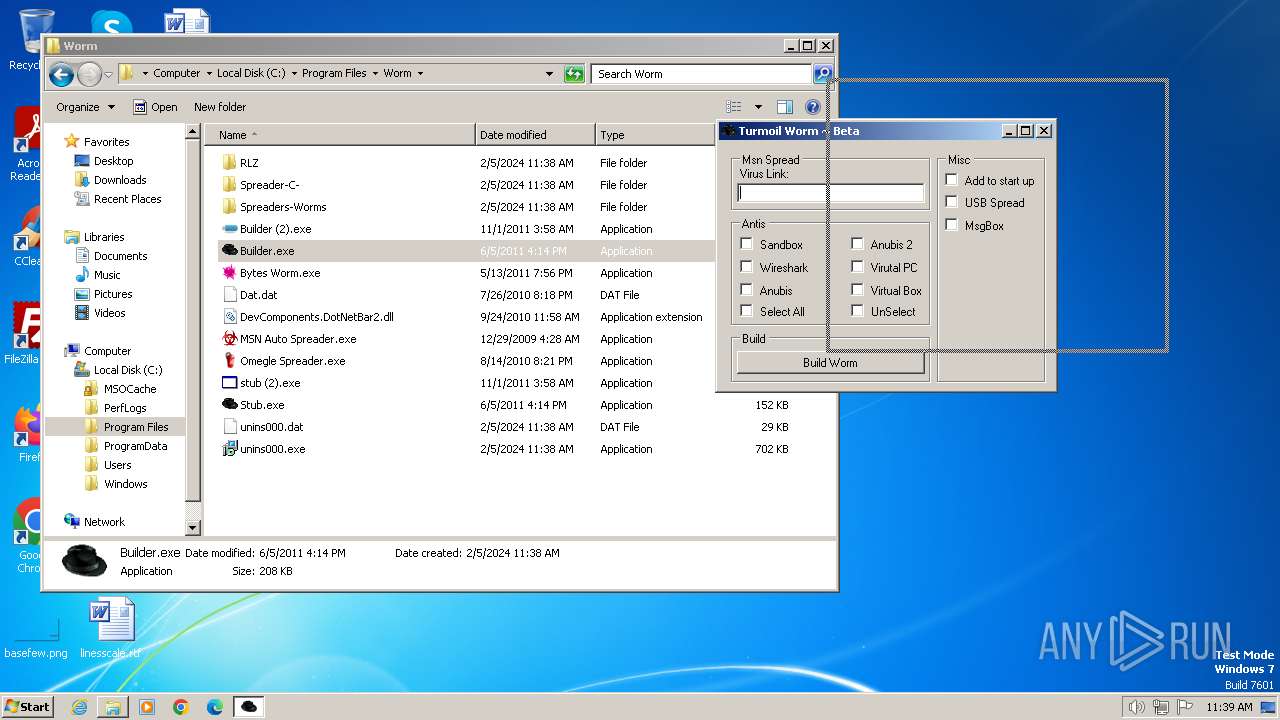
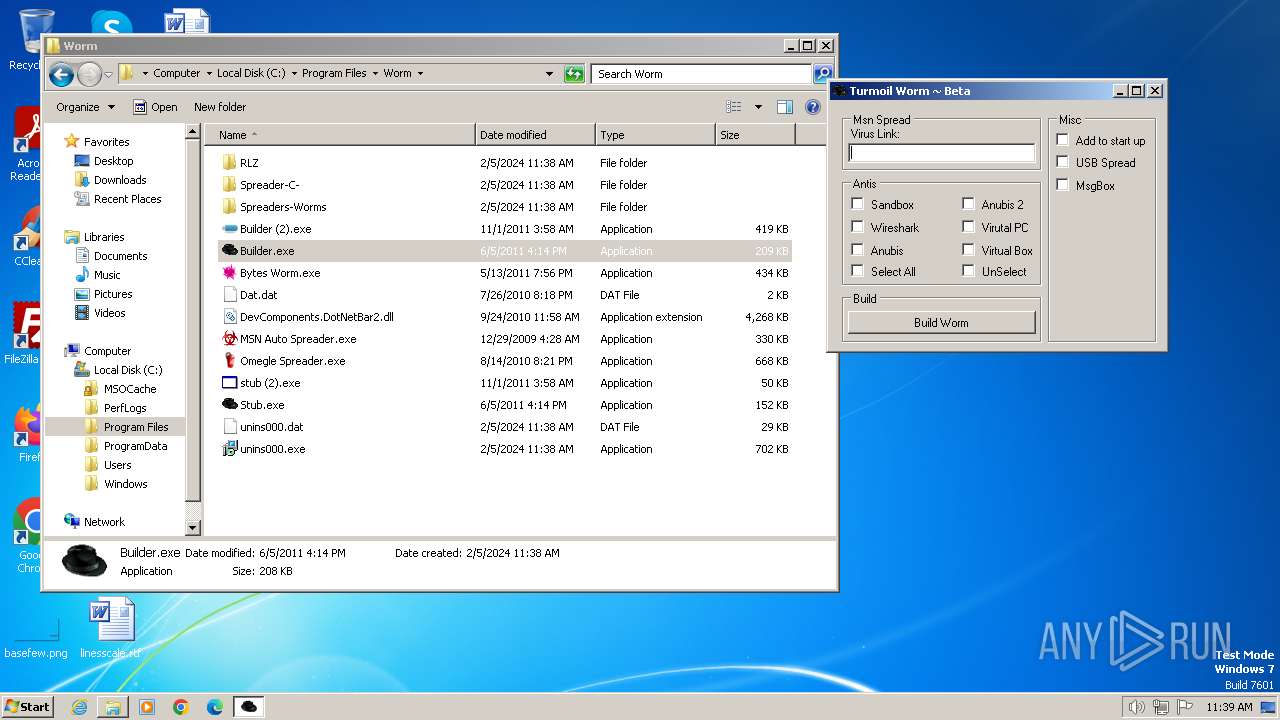
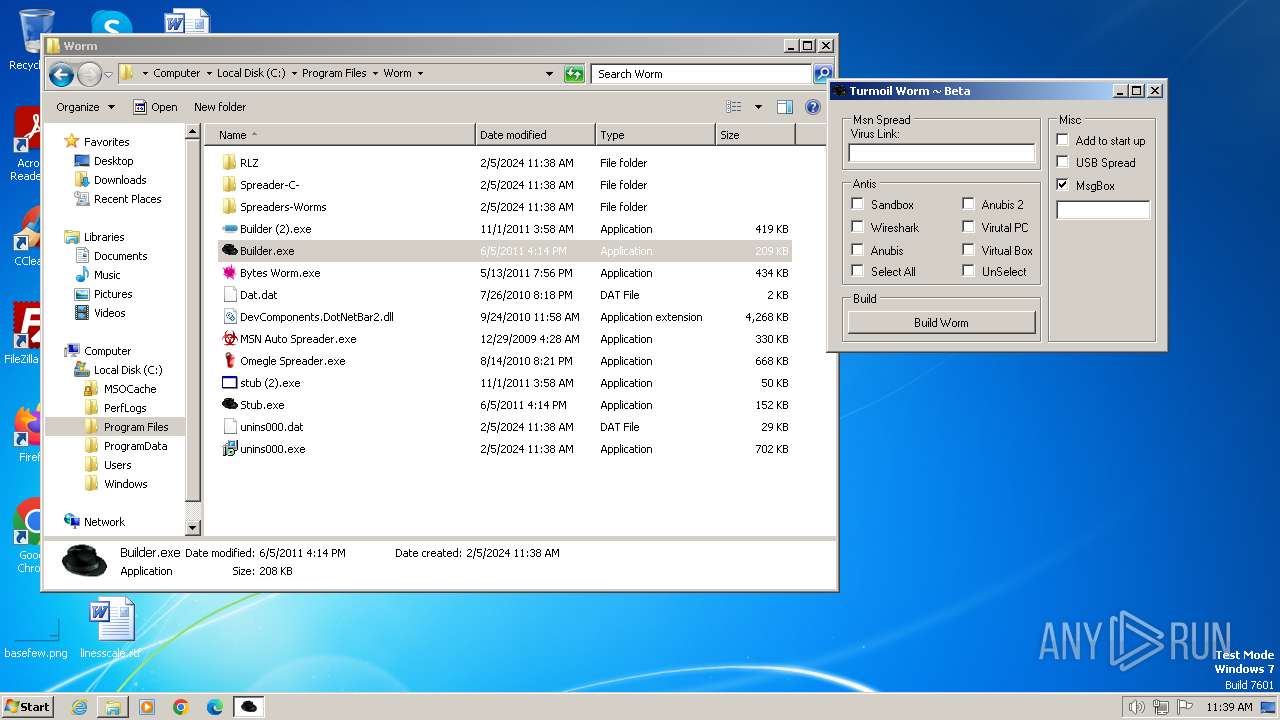
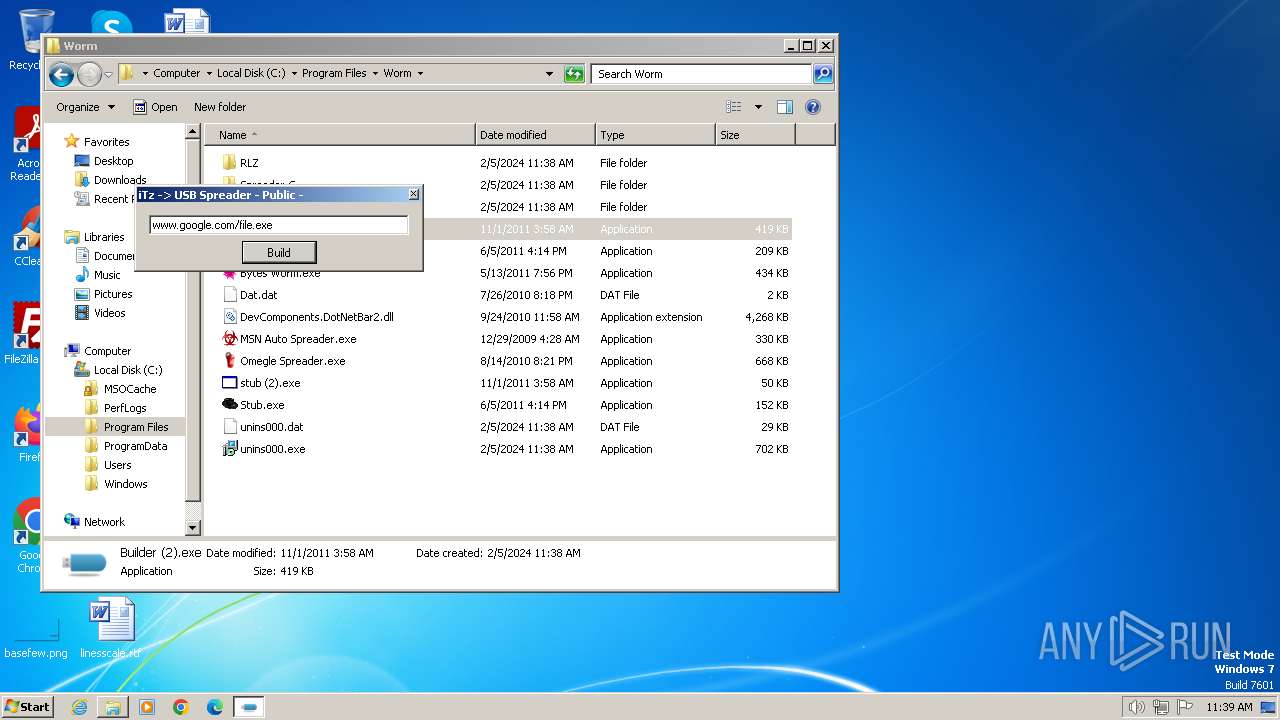
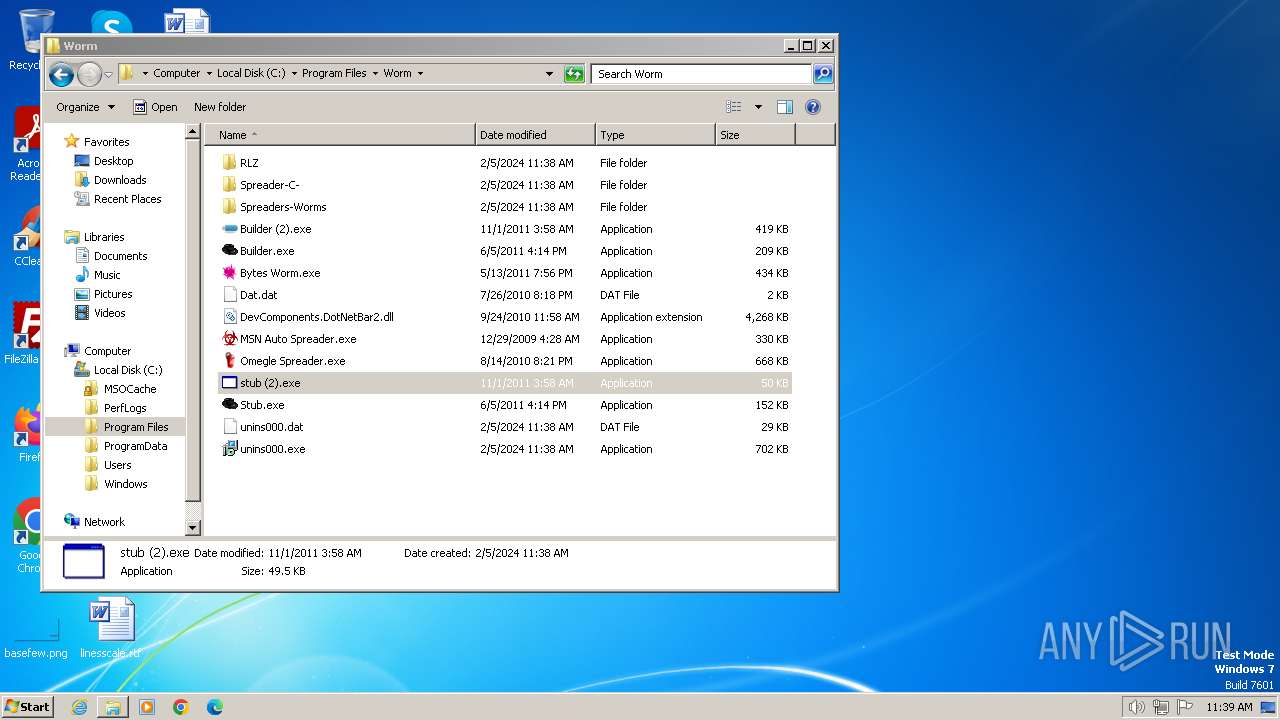
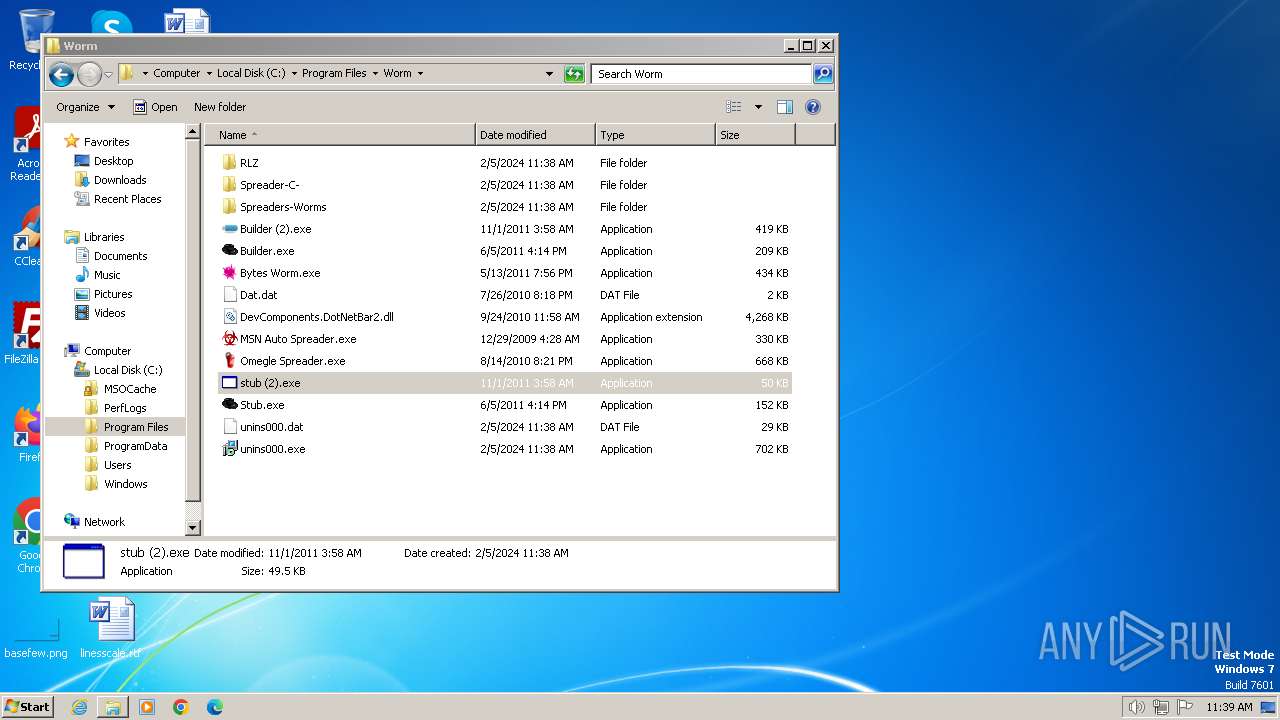
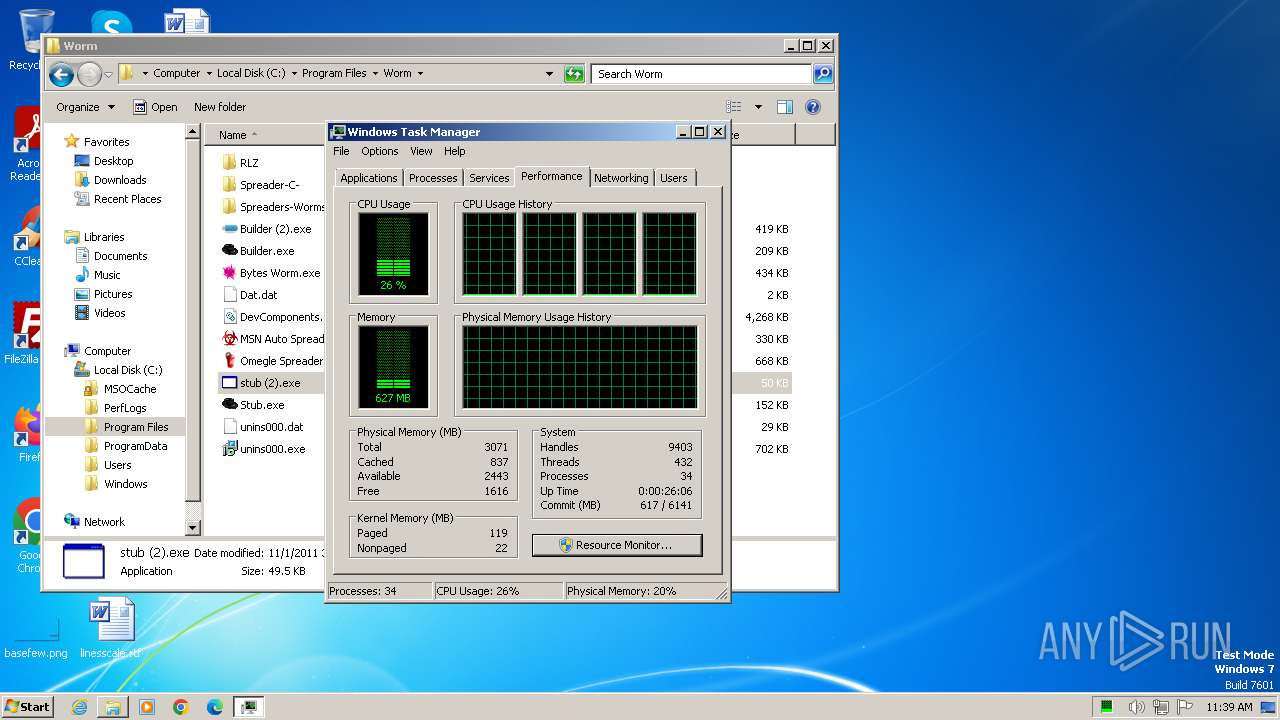
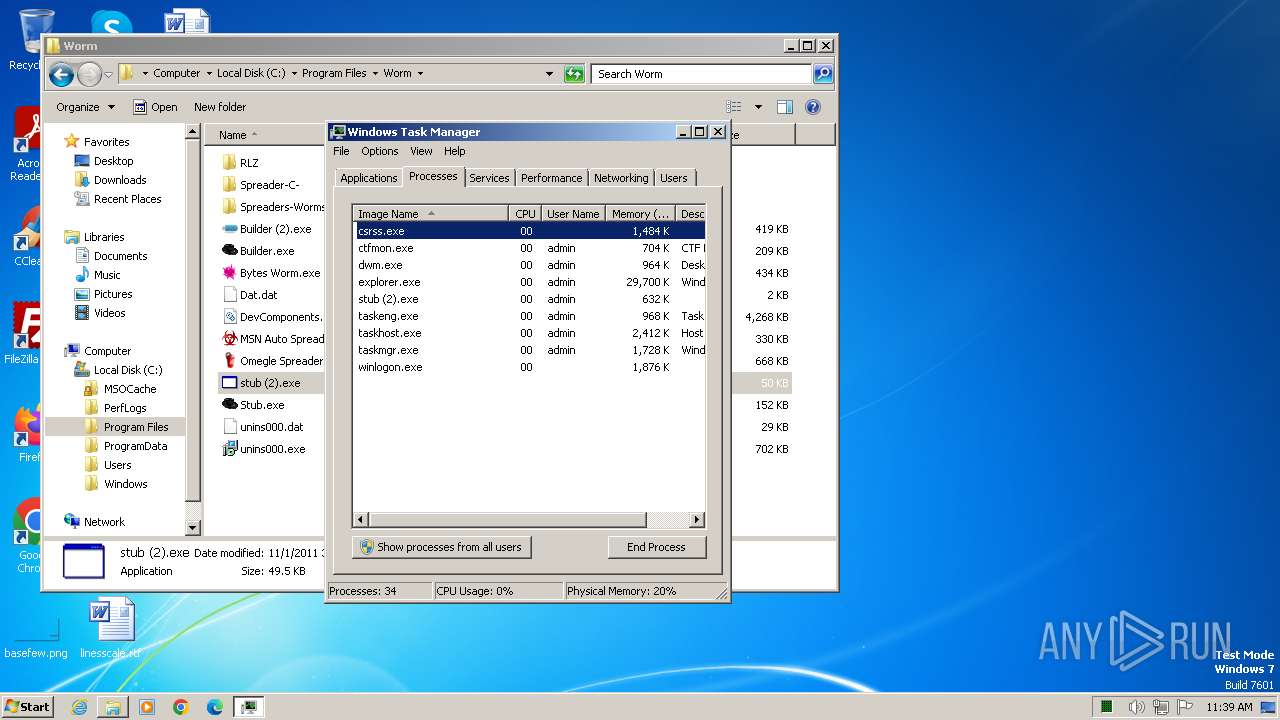
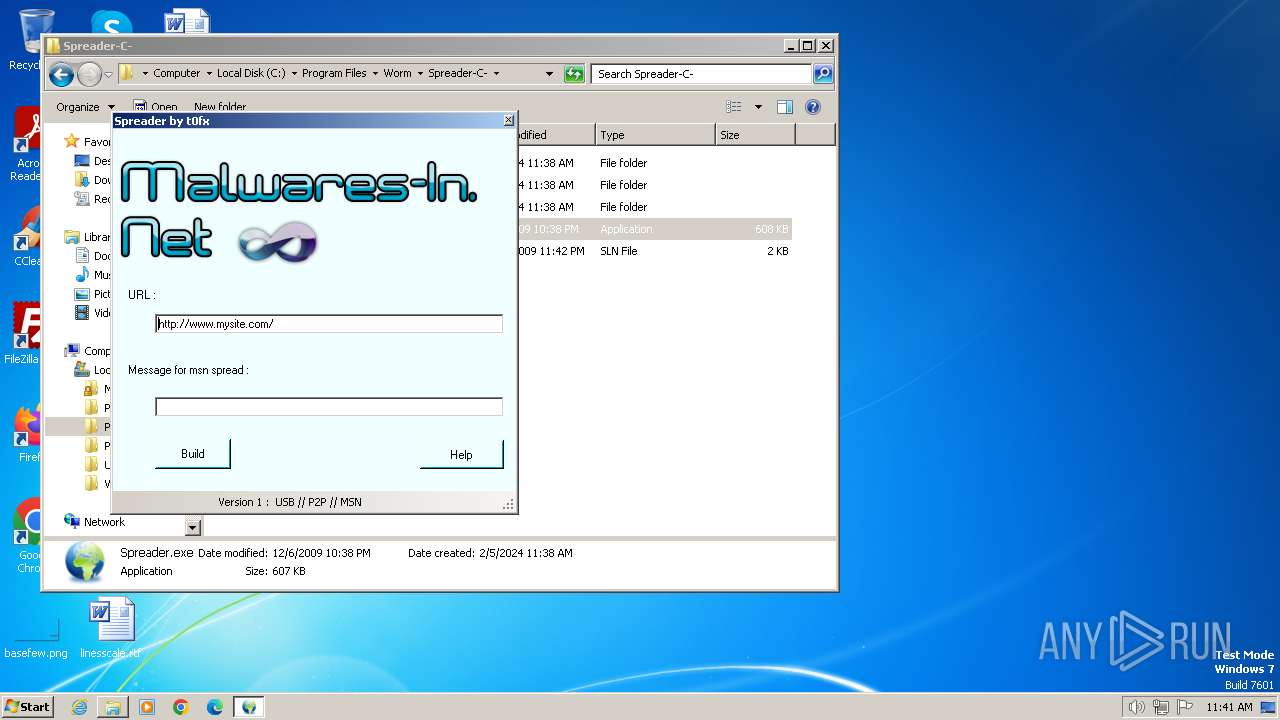
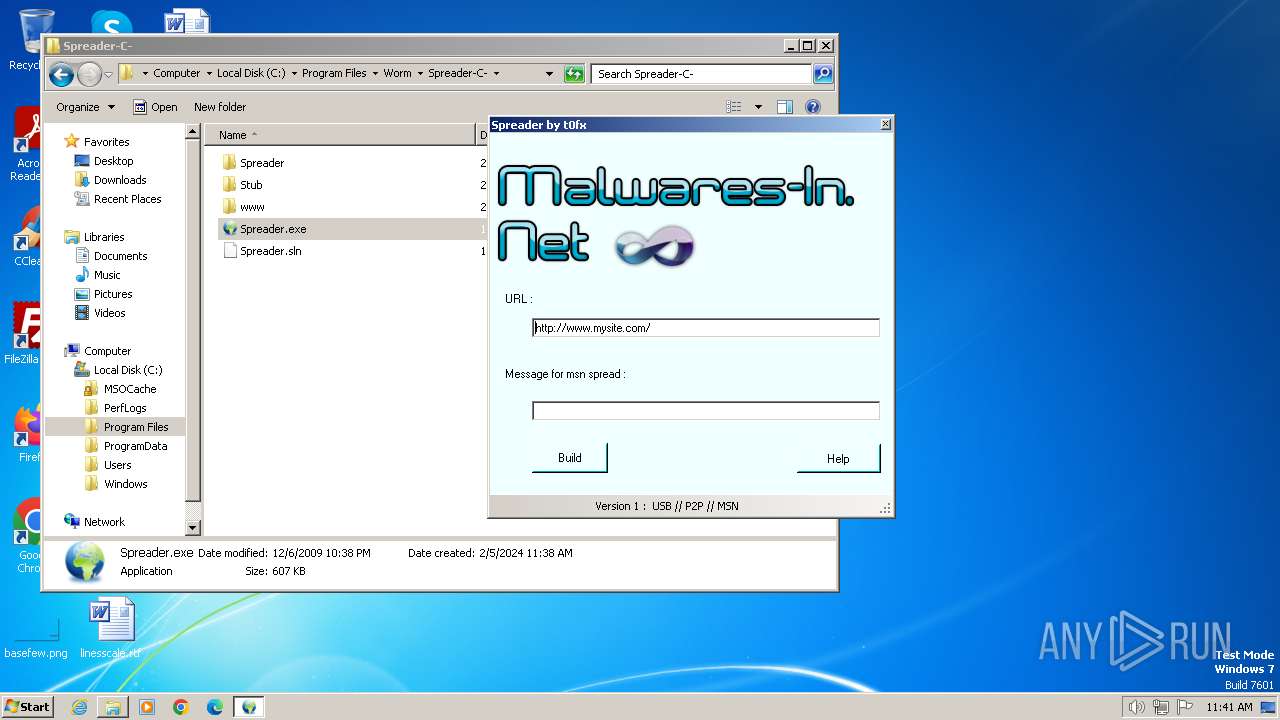
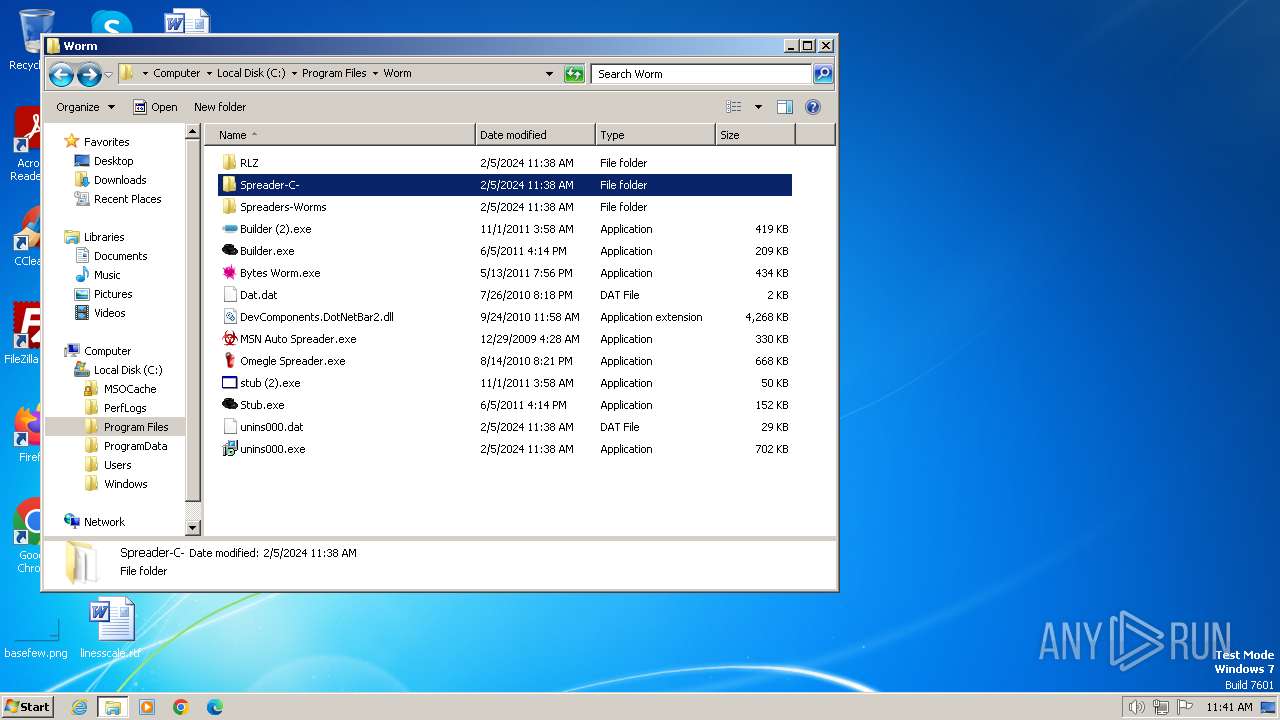
| File name: | Worm.exe |
| Full analysis: | https://app.any.run/tasks/64d35845-215a-4e3a-a7ee-8402ed8edad2 |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2024, 11:37:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0F9EE5D40776B69E4631E8A5AF6A6AA4 |
| SHA1: | 1859F921E7E25EA5F2178E1CB01E96431E637F86 |
| SHA256: | EB6AC5A8248DC2B48A96F4CE116AE6E045E5C09B4F57F1F3D9797EA7C9ADDEFB |
| SSDEEP: | 98304:Y6ZMVLTGqsu0NUIf0qbZnWtXIT6VoFlJn3H19nDq3I1VEK8osW6FCOyWGpI6AkPD:3fPWK7d |
MALICIOUS
Drops the executable file immediately after the start
- Worm.exe (PID: 572)
- Worm.exe (PID: 2088)
- Worm.tmp (PID: 1072)
Actions looks like stealing of personal data
- Worm.tmp (PID: 1072)
SUSPICIOUS
Process drops legitimate windows executable
- Worm.tmp (PID: 1072)
Executable content was dropped or overwritten
- Worm.exe (PID: 572)
- Worm.tmp (PID: 1072)
- Worm.exe (PID: 2088)
Reads the Windows owner or organization settings
- Worm.tmp (PID: 1072)
Reads the Internet Settings
- Omegle Spreader.exe (PID: 2952)
Reads settings of System Certificates
- Omegle Spreader.exe (PID: 2952)
Reads Microsoft Outlook installation path
- Omegle Spreader.exe (PID: 2952)
Reads security settings of Internet Explorer
- Omegle Spreader.exe (PID: 2952)
Reads Internet Explorer settings
- Omegle Spreader.exe (PID: 2952)
Checks Windows Trust Settings
- Omegle Spreader.exe (PID: 2952)
INFO
Create files in a temporary directory
- Worm.exe (PID: 572)
- Worm.exe (PID: 2088)
- Worm.tmp (PID: 1072)
- Omegle Spreader.exe (PID: 2952)
Checks supported languages
- Worm.exe (PID: 572)
- Worm.tmp (PID: 1264)
- Worm.exe (PID: 2088)
- Worm.tmp (PID: 1072)
- Builder.exe (PID: 1556)
- stub (2).exe (PID: 2576)
- Builder (2).exe (PID: 2172)
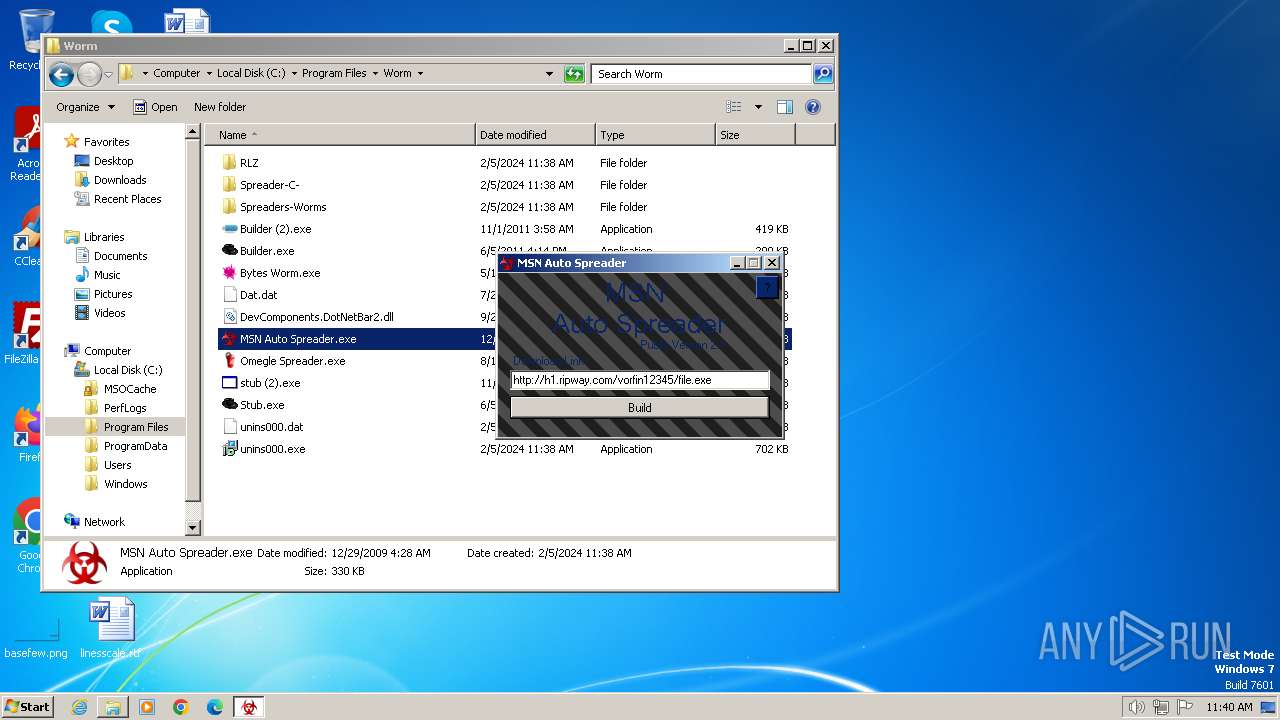
- MSN Auto Spreader.exe (PID: 1652)
- Omegle Spreader.exe (PID: 2952)
- Spreader.exe (PID: 2636)
Reads the computer name
- Worm.tmp (PID: 1264)
- Worm.tmp (PID: 1072)
- Builder.exe (PID: 1556)
- Builder (2).exe (PID: 2172)
- stub (2).exe (PID: 2576)
- MSN Auto Spreader.exe (PID: 1652)
- Omegle Spreader.exe (PID: 2952)
- Spreader.exe (PID: 2636)
Creates files in the program directory
- Worm.tmp (PID: 1072)
Manual execution by a user
- msedge.exe (PID: 1028)
- Builder (2).exe (PID: 2172)
- Builder.exe (PID: 1556)
- stub (2).exe (PID: 2576)
- taskmgr.exe (PID: 1604)
- MSN Auto Spreader.exe (PID: 1652)
- explorer.exe (PID: 2124)
- Omegle Spreader.exe (PID: 2952)
- Spreader.exe (PID: 2636)
Application launched itself
- msedge.exe (PID: 1028)
Reads the machine GUID from the registry
- Builder.exe (PID: 1556)
- Builder (2).exe (PID: 2172)
- stub (2).exe (PID: 2576)
- MSN Auto Spreader.exe (PID: 1652)
- Omegle Spreader.exe (PID: 2952)
- Spreader.exe (PID: 2636)
Creates files or folders in the user directory
- Omegle Spreader.exe (PID: 2952)
Checks proxy server information
- Omegle Spreader.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (71.1) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.1) |
| .scr | | | Windows screen saver (8.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.2) |
| .exe | | | Win32 Executable (generic) (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | My Company, Inc. |
| FileDescription: | Worm Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | Worm |
| ProductVersion: | 1.0 |
Total processes
73
Monitored processes
25
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Users\admin\AppData\Local\Temp\Worm.exe" | C:\Users\admin\AppData\Local\Temp\Worm.exe | explorer.exe | ||||||||||||
User: admin Company: My Company, Inc. Integrity Level: MEDIUM Description: Worm Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://www.example.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\is-RHDRO.tmp\Worm.tmp" /SL5="$1301B4,2786258,56832,C:\Users\admin\AppData\Local\Temp\Worm.exe" /SPAWNWND=$100166 /NOTIFYWND=$F0184 | C:\Users\admin\AppData\Local\Temp\is-RHDRO.tmp\Worm.tmp | Worm.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1264 | "C:\Users\admin\AppData\Local\Temp\is-23L5A.tmp\Worm.tmp" /SL5="$F0184,2786258,56832,C:\Users\admin\AppData\Local\Temp\Worm.exe" | C:\Users\admin\AppData\Local\Temp\is-23L5A.tmp\Worm.tmp | — | Worm.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Worm\Builder.exe" | C:\Program Files\Worm\Builder.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: msn builder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1604 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Worm\MSN Auto Spreader.exe" | C:\Program Files\Worm\MSN Auto Spreader.exe | — | explorer.exe | |||||||||||
User: admin Company: Coded By Vorfin Integrity Level: MEDIUM Description: MSN Auto Spreader© Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Local\Temp\Worm.exe" /SPAWNWND=$100166 /NOTIFYWND=$F0184 | C:\Users\admin\AppData\Local\Temp\Worm.exe | Worm.tmp | ||||||||||||
User: admin Company: My Company, Inc. Integrity Level: HIGH Description: Worm Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2124 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Worm\Builder (2).exe" | C:\Program Files\Worm\Builder (2).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
8 538
Read events
8 473
Write events
58
Delete events
7
Modification events
| (PID) Process: | (1072) Worm.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: EB7AAFD3894470872C884D1C0D171CB995BE2E25F311C5B96EC5A5ED68FB5455 | |||
| (PID) Process: | (1072) Worm.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\Worm\Builder (2).exe | |||
| (PID) Process: | (1072) Worm.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1072) Worm.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: E14AA758339D1C31BE1667F0D0449A57E51ADA75EE1315F904802F9C06021096 | |||
| (PID) Process: | (1072) Worm.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 300400001ECE9FC72758DA01 | |||
| (PID) Process: | (1072) Worm.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1028) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1028) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1028) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1028) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
Executable files
47
Suspicious files
87
Text files
440
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | Worm.tmp | C:\Program Files\Worm\is-NCKD7.tmp | executable | |
MD5:92C00B0F2E9ECBFC5155A7E789E19DEB | SHA256:A9CF3E1218F8E0AB71A81C0F4339C0A6C7047EF04A6AE3A20488AF638CB9F931 | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\unins000.exe | executable | |
MD5:60145B5523F4CADA56F4ECD5B7ABF671 | SHA256:10A30041D45A78C5C13740545007EBDC17930D10AE3E1914222B2746643FBC58 | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\is-OF1PU.tmp | executable | |
MD5:6CFF2B5B9476059689E6F0F28F471D9C | SHA256:98A3D61ED8583703BD6B3D1FE8A3A6F8D31643115DD4825D819A8FCA64064068 | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\Builder (2).exe | executable | |
MD5:6CFF2B5B9476059689E6F0F28F471D9C | SHA256:98A3D61ED8583703BD6B3D1FE8A3A6F8D31643115DD4825D819A8FCA64064068 | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\is-6OQU3.tmp | executable | |
MD5:71CF577CAF188F332C8D6C88B582EF53 | SHA256:FE6031DD64C31D1ABF4DF4A1BEF2F5F3D7EDA0149DD0B89AF27F6F83593526B5 | |||
| 572 | Worm.exe | C:\Users\admin\AppData\Local\Temp\is-23L5A.tmp\Worm.tmp | executable | |
MD5:1305181DE520F125AEABF85DC24A89D6 | SHA256:0E19765B89A1A29AFEE09810DCB3EC5CC7C66053947BE8F1AEBDBB7C801DFEAF | |||
| 1072 | Worm.tmp | C:\Users\admin\AppData\Local\Temp\is-PTU3C.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\is-E6QFK.tmp | executable | |
MD5:5DC53A976446E54C5AE4B46B0C1DE5FD | SHA256:9459AA3177117CF618D64A66FBB1D958692EA1636BA4E038FD9D8D8E565DB514 | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\is-I06S3.tmp | text | |
MD5:360EE0FDC26784CAA46411DAE500A138 | SHA256:308036D74BBE6C52EE379CE01937168DF6930EE11D10B076751B8D4049970AFF | |||
| 1072 | Worm.tmp | C:\Program Files\Worm\MSN Auto Spreader.exe | executable | |
MD5:7556567FD50527CE2DA1607CB49E9C29 | SHA256:8FF93DDAA2C7E417475DE8A49B5D2ED6C42EBAD485B2AF128E1D64C1157DC754 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
19
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2952 | Omegle Spreader.exe | GET | 301 | 104.23.139.25:80 | http://www.omegle.com/ | unknown | — | — | unknown |
2952 | Omegle Spreader.exe | GET | 304 | 23.32.238.232:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f04c9cfb7438e55b | unknown | — | — | unknown |
3548 | msedge.exe | GET | 200 | 93.184.216.34:80 | http://www.example.com/ | unknown | html | 648 b | unknown |
3548 | msedge.exe | GET | 404 | 93.184.216.34:80 | http://www.example.com/favicon.ico | unknown | html | 648 b | unknown |
1080 | svchost.exe | GET | 304 | 23.32.238.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fc91d912a85a08d5 | unknown | — | — | unknown |
2952 | Omegle Spreader.exe | GET | 200 | 23.32.238.232:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?843308bc56197127 | unknown | compressed | 65.2 Kb | unknown |
2952 | Omegle Spreader.exe | GET | 200 | 69.192.161.44:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
2952 | Omegle Spreader.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3548 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1028 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
3548 | msedge.exe | 93.184.216.34:80 | www.example.com | EDGECAST | US | whitelisted |
3548 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3548 | msedge.exe | 184.86.251.4:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1028 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
3548 | msedge.exe | 152.199.21.175:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | EDGECAST | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
www.example.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.iana.org |
| whitelisted |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
www.omegle.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |